量子安全 IPsec VPN
了解如何在 IKED 过程中使用和配置带外密钥检索机制,以便与量子安全 IKE 和 IPsec SA 进行协商。
量子安全概述
IPsec 通信通道依赖于互联网密钥交换 (IKE) 协议。IKE 维护安全参数以保护数据流量。安全参数包括加密和身份验证算法以及关联的密钥。
安全协议依赖于非对称加密算法,如Diffie Hellman(DH)或椭圆曲线Diffie Hellman(ECDH)来确定密钥容易受到攻击。
为避免安全攻击, RFC8784 引入了带外方法。带外方法在发起方和响应方处添加一个密钥。密钥是后量子预共享密钥 (PPK)。
-
除了 IKEv2 中的身份验证方法之外,您还可以使用 PPK。
-
PPK 为初始协商的 IPsec SA 和任何后续重新建立的 IPsec SA 中的任何子 SA 提供量子抗性。
-
使用 PPK 和对等身份验证密钥,发起方和响应方可以检测到密钥不匹配。
Junos 密钥管理器概述
您可以使用 Junos 密钥管理器 (JKM) 配置静态密钥或动态密钥来保护数据平面和控制平面。
JKM 进程充当客户端或加密应用程序之间的密钥存储和代理。客户端或加密应用程序需要一个密钥来与对等方或应用程序建立加密且经过身份验证的量子安全会话。量子保险箱使用带外密钥检索机制,让两个对等方拥有密钥。不同的带外机制将具有不同的协议或通信方法。JKM 为客户端或加密应用程序提供了一个通用的统一接口进行通信。
密钥检索机制
IKED 进程中的两种带外密钥检索机制,用于与量子安全 IKE 和 IPsec SA 进行协商。
-
静态密钥 — 使用静态密钥配置文件,您可以配置静态密钥 ID 和相应的密钥。每次通过静态密钥配置文件向 JKM 发出请求时,都会生成相同的静态密钥 ID 和密钥。
-
量子密钥管理器 — 使用量子密钥管理器密钥配置文件,您可以访问量子密钥分发 (QKD) 设备和量子网络。量子网络在对等方之间生成和交换量子密钥。每次通过量子密钥管理器密钥配置文件向 JKM 发出请求时,都会生成不同的密钥 ID 和密钥。
将密钥配置文件用于量子安全 IPsec VPN
使用静态密钥配置文件,您可以配置静态密钥 ID 和相应的密钥。要建立量子安全 IPsec SA,请在 IPsec-VPN 配置中使用静态密钥配置文件作为后量子预共享密钥 (PPK) 配置文件。使用相同的密钥和密钥 ID 重新验证现有 IKE SA。
使用量子密钥管理器密钥配置文件,要访问量子网络,您需要访问 QKD 设备。量子网络在对等方之间生成和交换量子密钥。您可以配置所有必要的参数,例如本地 SAE ID、QKD 设备的 URL 等。要建立 IPsec SA,请在 IPsec VPN 配置中使用量子密钥管理器密钥配置文件作为后量子预共享密钥 (PPK) 配置文件。使用不同的密钥和密钥 ID 重新验证现有 IKE SA。
量子密钥分发
量子密钥分发 (QKD) 是一种使用量子的安全密钥分发方法。网络使用量子通道在两端生成相同的密钥,并监控对等方之间的量子通道。这些密钥是动态的,用于保护数据平面和控制平面。
密钥管理实体 (KME) 是我们用来指代管理或控制层上的 QKD 设备的术语。QKD 设备通过其量子或 QKD 网络相互连接。KME 通过安全通道在公共网络上进行连接,以交换任何控制消息。应用程序、安全应用程序实体 (SAE) 和设备通过符合 ETSI 规范的安全通道与 KME 交互。HTTPS 与相互 TLS 身份验证相结合,并通过 QKD 网络实现安全操作。
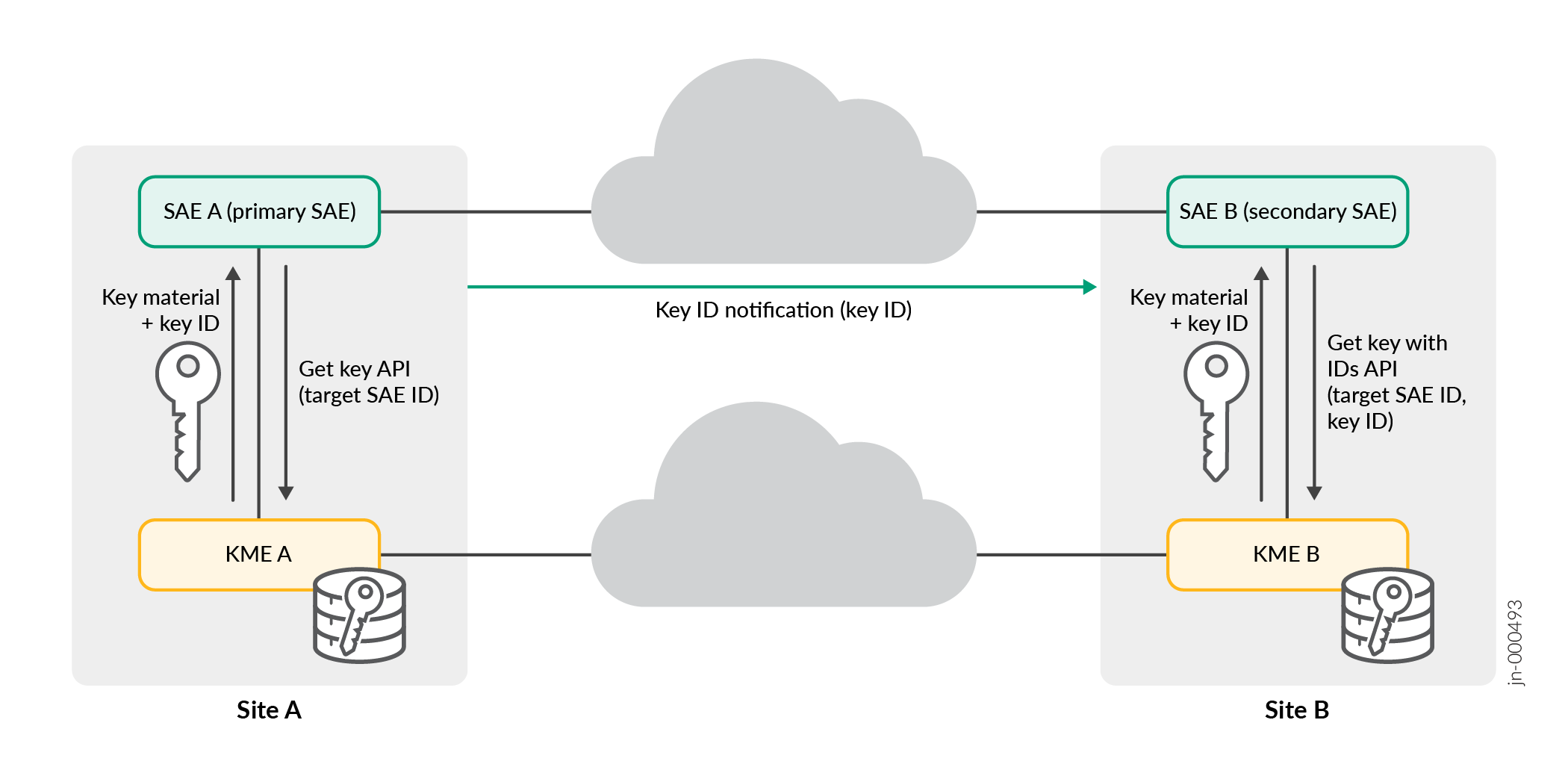
在 图 1 中,介绍了两台设备如何与其对应的 QKD 设备交互以建立量子安全会话
-
SAE A 角色是主要角色。SAE A 充当与 SAE B 建立量子安全会话的发起方。
-
SAE B 角色是次要角色。SAE B 充当响应方。
-
SAE A 通过获取密钥 API 请求 KME A,以生成新的量子密钥,并与目标 SAE ID 的 SAE B 共享。
-
KME A 执行操作,并使用生成的密钥 ID 和密钥材料响应 SAE A。
-
KME B 通过 QKD 网络接收密钥材料和生成的 ID 密钥。
-
SAE A 使用相同的密钥和密钥 ID 直接启动与 SAE B 的安全会话。
-
消息交换可与 SAE B 建立安全会话。
-
SAE A 以明文形式发送密钥 ID,或者针对用于保护与 SAE B 的会话的相应量子密钥进行加密。
-
SAE B 收到密钥 ID 后,SAE B 会通过包含 ID 的获取密钥 API 联系 KME B,以获取给定密钥 ID 和目标 SAE ID 或 SAE A 的相应量子密钥。
-
SAE B 获得密钥后,将在 SAE A 和 SAE B 之间建立完全量子安全会话。
为 Junos 密钥管理器配置静态密钥配置文件
此示例说明如何为 Junos 密钥管理器配置静态密钥配置文件。在相关网关上配置静态密钥,无需通过互联网共享静态密钥即可建立 IPsec 隧道。
要求
-
硬件要求 —瞻博网络® SRX1500防火墙和更高编号的设备型号或瞻博网络®vSRX 虚拟防火墙 (vSRX3.0)。
-
软件要求 - Junos OS 22.4R1 或更高版本,带有 JUNOS ike 软件 JUNOS Key Manager 包。
概述
对于基于静态密钥的配置文件,您需要配置静态密钥 ID 和对应的密钥。如果在 IPsec VPN 对象中使用静态密钥配置文件,则在对现有 IKE SA 进行重新身份验证时,将使用相同的密钥和密钥 ID。
配置
为 Junos 密钥管理器配置静态密钥配置文件。
user@host# set security key-manager profiles km_profile_1 static key-id ascii-text test-ppk-id user@host# set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
验证
目的
验证静态密钥配置文件和密钥。
操作
在操作模式下,输入 request security key-manager profiles get profile-keys name km_profile_1 以查看静态密钥配置文件和密钥。
user@host> request security key-manager profiles get profile-keys name km_profile_1
- Response:
- Status: SUCCESS
- Name: km_profile_1
- Type: Static
- Key-size: 280 bits
- Key-count: 1
- Key-ids:
- test-ppk-id
- Keys:
- 716a776264697031333975356d637938396d32387063676f77657265666e6b6a736467在操作模式下,输入 show security key-manager profiles name km_profile_1 detail 以查看静态密钥配置文件的详细信息。
user@host> show security key-manager profiles name km_profile_1 detail
Name: km_profile_1, Index: 1, Type: Static
Configured-at: 10.09.23 (20:16:34)
Time-elapsed: 0 hrs 2 mins 21 secs
Request stats:
Received: 1
In-progress: 0
Success: 1
Failed: 0
意义
显示 request security key-manager profiles get profile-keys name km_profile_1 状态、静态密钥配置文件名称、类型、密钥大小、密钥 ID 和密钥。
显示 show security key-manager profiles name km_profile_1 detail 静态密钥配置文件名称、类型和请求状态。
示例:为站点到站点 VPN 配置静态密钥配置文件
使用此配置示例可以配置静态密钥配置文件。您可以使用静态密钥配置文件来保护 IPsec 站点到站点 VPN 基础架构。
您可以通过配置静态密钥配置文件来保护 IPsec 站点到站点 VPN 基础架构。
在此配置示例中,SRX1 和 SRX2 设备使用静态密钥配置文件获取 IPsec VPN 上的 QKD 密钥。QKD 密钥有助于在互联网上安全地发送流量。
|
阅读时间 |
不到一个小时 |
|
配置时间 |
不到一个小时 |
先决条件示例
|
硬件要求 |
® 瞻博网络SRX1500防火墙或更高编号的设备型号或瞻博网络®vSRX 虚拟防火墙 (vSRX3.0) |
|
软件要求 |
Junos OS 22.4R1 或更高版本。 |
开始之前
|
优势 |
|
|
实用资源 |
|
|
了解更多 |
|
|
实践经验 |
|
|
了解更多 |
功能概述
| IPsec VPN |
部署一个 IPsec VPN 拓扑,其中 SRX 系列防火墙设备通过 VPN 隧道连接,这些 VPN 隧道通过 IPsec VPN 隧道发送流量。VPN 隧道稍后配置为使用量子密钥,使其成为量子安全 VPN 隧道。 |
| IKE 网关 |
建立安全连接时,IKE 网关使用 IKE 策略将自身限制为已配置的 CA 组(CA 配置文件),同时验证证书。 |
| 建议 | |
| IKE 提案 |
定义用于与对等安全网关建立安全 IKE 连接的算法和密钥。 IKE 创建动态 SA 并就 IPsec 对其进行协商。 |
| IPsec 提议 |
列出要与远程 IPsec 对等方协商的协议、算法和安全服务。 |
| 策略 | |
| IKE 策略 |
定义在 IKE 协商期间要使用的安全参数(IKE 提议)组合。 |
| IPsec 策略 |
包含规则和安全策略,以允许在指定区域之间分组 VPN 流量。 |
| 安全策略 |
允许您选择要通过 IPsec SA 保护的数据流量类型。
|
|
配置文件 |
|
|
密钥配置文件 |
定义 SRX 系列防火墙设备如何使用静态密钥配置文件在 IPsec VPN 上获取 QKD 密钥,以便通过互联网安全地发送流量。
|
| PPK 信息 |
通过引用 IKE 网关下的密钥配置文件,指明用于建立量子安全 IKE 或 IPsec SA 的密钥配置文件。 |
| 证书 | |
| CA 证书 | 验证设备的身份并验证它们之间的通信链路。 |
| 本地证书 | 生成 PKI 并使用 CA 证书注册以进行验证。 |
| KME证书 | 供应商生成的第三方证书 |
| 安全区域 | |
| trust |
主机区域的网段 |
| untrust |
目标服务器区域的网络分段 |
| vpn |
SRX1 和 SRX2 设备通过其交互的网段。 |
|
主要验证任务 |
验证已建立的 IKE 和 IPsec SA 是否为量子安全。 |
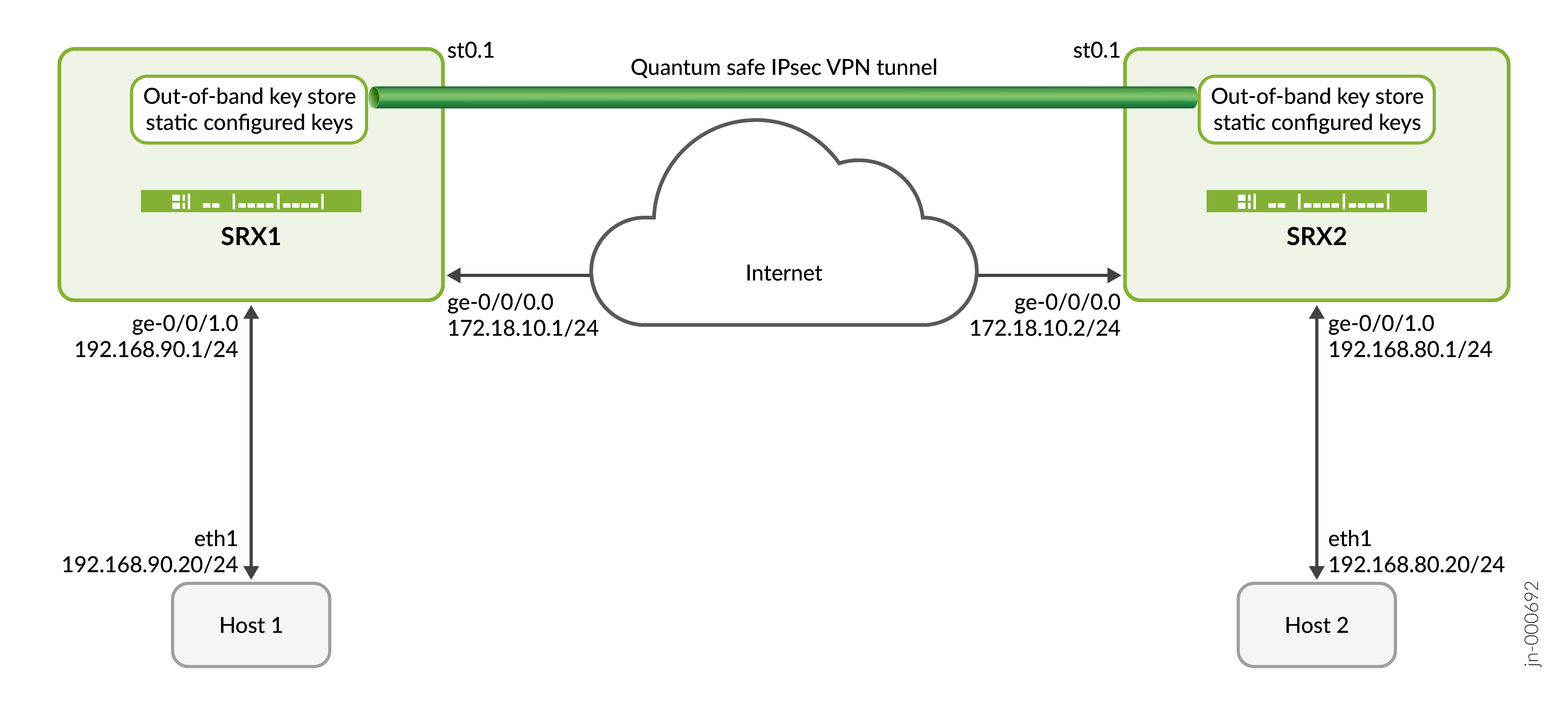
拓扑概述
在此示例中,SRX1 使用 CLI 配置的静态密钥与 SRX2 启动量子安全 IPsec 隧道协商。SRX2 通过验证 SRX1 的身份和密钥来响应此请求,并建立量子安全 IPsec VPN。隧道建立后,将使用建立的 IPsec 隧道保护 Host1 和 Host2 之间的数据流量。
|
主机名 |
角色 |
功能 |
|---|---|---|
| SRX1 |
能够建立 IPsec 隧道的 SRX 系列防火墙 |
使用 SRX1 上配置的静态密钥发起 IKE 或 IPsec SA 协商,并与 SRX2 建立量子安全 IPsec 隧道。 |
| SRX2 | 能够建立 IPsec 隧道的 SRX 系列防火墙 | 响应 SRX1 发起的 IKE 或 IPsec SA 协商,并使用 SRX2 上配置的静态密钥建立量子安全 IPsec 隧道。 |
| 主机1 | SRX1 的可信区域或 LAN 端内的主机 | 发起流向 Host2 的客户端流量 |
| 主机2 | SRX2 的可信区域或 LAN 端内的主机 | 响应来自 Host1 的客户端流量 |
拓扑图示
SRX 系列防火墙设备上的分步配置
-
配置接口。
[edit interfaces] user@srx# set ge-0/0/0 unit 0 family inet address 172.18.10.1/24 user@srx# set st0 unit 1 family inet user@srx# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24
-
使用密钥 ID 和对应的密钥配置静态类型的密钥配置文件。
[edit security key-manager profiles] user@srx# set km_profile_1 static key-id ascii-text test-key-id user@srx# set km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
-
配置安全区域。
[edit security zones] user@srx# set security-zone untrust host-inbound-traffic system-services ike user@srx# set security-zone untrust interfaces ge-0/0/0.0 user@srx# set security-zone vpn interfaces st0.1 user@srx# set security-zone trust host-inbound-traffic system-services ping user@srx# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@srx# set from-zone trust to-zone vpn policy vpn_out match source-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match application any user@srx# set from-zone trust to-zone vpn policy vpn_out then permit user@srx# set from-zone vpn to-zone trust policy vpn_in match source-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match application any user@srx# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security ike proposal] user@srx# set IKE_PROP authentication-method pre-shared-keys user@srx# set IKE_PROP dh-group group14 user@srx# set IKE_PROP authentication-algorithm sha-256 user@srx# set IKE_PROP encryption-algorithm aes-256-cbc user@srx# set IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@srx# set IKE_POL proposals IKE_PROP user@srx# set IKE_POL pre-shared-key ascii-text ipsec-test
[edit security ike gateway] user@srx# set IKE_GW ike-policy IKE_POL user@srx# set IKE_GW address 172.18.10.2 user@srx# set IKE_GW external-interface ge-0/0/0.0 user@srx# set IKE_GW local-address 172.18.10.1 user@srx# set IKE_GW version v2-only user@srx# set IKE_GW ppk-profile km_profile_1
[edit security ipsec proposal] user@srx# set IPSEC_PROP protocol esp user@srx# set IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx# set IPSEC_PROP encryption-algorithm aes-256-cbc user@srx# set IPSEC_PROP lifetime-seconds 2400
[edit security ipsec policy] user@srx# set IPSEC_POL proposals IPSEC_PROP
[edit security ipsec vpn] user@srx# set IPSEC_VPN bind-interface st0.1 user@srx# set IPSEC_VPN ike gateway IKE_GW user@srx# set IPSEC_VPN ike ipsec-policy IPSEC_POL user@srx# set IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@srx# set IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 user@srx# set IPSEC_VPN establish-tunnels immediately
验证
本部分提供可用于验证此示例中的功能的 show 命令列表。
|
命令 |
验证任务 |
|---|---|
|
显示安全 IKE 安全关联详细信息 |
|
|
显示安全 IPsec 安全关联详细信息 |
|
|
显示安全 IPsec 统计信息 |
|
|
显示安全密钥管理器配置文件详细信息 |
|
|
ping 192.168.80.20 源 192.168.90.20 计数 4 |
验证 IKE SA
目的
验证 IKE SA
操作
在操作模式下,输入 show security ike security-associations detail 命令,以查看 IKE SA。
user@srx> show security ike security-associations detail IKE peer 172.18.10.2, Index 1, Gateway Name: IKE_GW
Role: Initiator, State: UP
Initiator cookie: dee592254e808a2b, Responder cookie: 51f6b1d4a8618332 Exchange type: IKEv2, Authentication method: Pre-shared-keys
Local gateway interface: ge-0/0/2.0 Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 1286 seconds Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576 SRG ID: 0
Remote Access Client Info: Unknown Client Peer ike-id: 172.18.10.2
AAA assigned IP: 0.0.0.0
PPK-profile: km_profile_1 Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc Pseudo random function: hmac-sha256 Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 1058
Output bytes : 1074
Input packets: 4
Output packets: 4
Input fragmented packets: 0
Output fragmented packets: 0
IPSec security associations: 4 created, 1 deleted Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500002
Negotiation type: Quick mode, Role: Initiator, Message ID: 0 Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: 172.18.10.1
Remote identity: 172.18.10.2 Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 1
Response In : 0 Response Out : 1
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0 Res Verify SA Fail : 0
Res Verify DH Group Fail: 0 Res Verify TS Fail : 0
意义
、Role: Initiator, State: UPPPK-profile: km_profile_1 Optional: No、IPSec security associations: 4 createdFlags: IKE SA is created和字段表示 IKE SA 创建成功。
验证 IPsec SA
目的
验证 IPsec SA
操作
在操作模式下,输入 show security ipsec security-associations detail 命令,以查看 IPsec SA。
user@srx> show security ipsec security-associations detail ID: 500002 Virtual-system: root, VPN Name: IPSEC_VPN Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2 Traffic Selector Name: ts1 Local Identity: ipv4(192.168.90.0-192.168.90.255) Remote Identity: ipv4(192.168.80.0-192.168.80.255) TS Type: traffic-selector Version: IKEv2 Quantum Secured: Yes PFS group: N/A SRG ID: 0 DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: IPSEC_POL Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0 Multi-sa, Configured SAs# 0, Negotiated SAs#: 0 Tunnel events: Thu Mar 30 2023 23:43:42: IPsec SA negotiation succeeds (1 times) Location: FPC 0, PIC 0, KMD-Instance 0 Anchorship: Thread 1 Distribution-Profile: default-profile Direction: inbound, SPI: 0x983a0221, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1330 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 662 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1 Direction: outbound, SPI: 0x4112746b, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1330 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 662 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1
意义
Version: IKEv2 Quantum Secured: Yes和 tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1 字段表示 IPsec SA 创建成功。
示例输出确认 IPsec SA。
验证 IPsec 统计信息
目的
验证 IPsec 统计信息。
操作
在操作模式下,输入 show security ipsec statistics 命令,以查看 IPsec 统计信息。
user@srx> show security ipsec statistics ESP Statistics: Encrypted bytes: 624 Decrypted bytes: 624 Encrypted packets: 4 Decrypted packets: 4 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
意义
ESP Statistics和 AH Statistics 字段显示 IPsec 统计信息。
验证密钥管理器配置文件
目的
验证密钥管理器配置文件。
操作
在操作模式下,输入 show security key-manager profiles 详细信息以查看密钥管理器配置文件。
user@srx> show security key-manager profiles detail Name: km_profile_1, Index: 1, Type: Static Configured-at: 30.03.23 (23:22:43) Time-elapsed: 1 hrs 16 mins 3 secs Request stats: Received: 1 In-progress: 0 Success: 1 Failed: 0
意义
Name: km_profile_1和 Type: Static 字段显示密钥管理器配置文件。
从 HOST 1 到 HOST 2 的 Ping
目的
验证从主机 1 到主机 2 的连接。
操作
在操作模式下,输入 ping 192.168.80.20 源 192.168.90.20 计数 4 以查看从主机 1 到主机 2 的连接。
user@HOST1# ping 192.168.80.20 source 192.168.90.20 count 4 PING 192.168.80.20 (192.168.80.20): 56 data bytes 64 bytes from 192.168.80.1: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.80.1: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.80.1: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.80.1: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.80.1 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
意义
确认 PING 192.168.80.20 (192.168.80.20): 56 data bytes 从主机 1 到主机 2 的连接。
附录1:在所有设备上设置命令
在所有设备上设置命令输出。
在 SRX1 上设置命令
set security key-manager profiles km_profile_1 static key-id ascii-text test-key-id set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.1/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.2 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.1 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
在 SRX2 上设置命令
set security key-manager profiles km_profile_1 static key-id ascii-text test-key-id set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.2/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text “ipsec-test” set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.1 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.2 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
附录2:显示 DUT 上的配置输出
SRX1
在配置模式下,输入show security key-manager profiles、、show security key-manager、 show security zonesshow security ipsec policy IPSEC_POLshow interfacesshow security ike proposal IKE_PROPshow security ipsec vpn IPSEC_VPNshow security policiesshow security ike policy IKE_POLshow security ike gateway IKE_GWshow security ipsec proposal IPSEC_PROP和命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@srx1# show security key-manager profiles
km_profile_1 {
static {
key-id ascii-text "$9$.mz6pu1hyKBI8X-boajHqmF/hcylK836"; ## SECRET-DATA
key ascii-text "$9$5Q6AhclXNbtuIcyeXxGDikfT369A0Bn/vWLNY2aZUjPQAp0BEcFnyleMXxGDi.mT9CuhSeIElMLXwsaZUikPpu1hSen/eW8XbwJGD"; ## SECRET-DATA
}
}
user@srx1# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$.mz6pu1hyKBI8X-boajHqmF/hcylK836"; ## SECRET-DATA
key ascii-text "$9$5Q6AhclXNbtuIcyeXxGDikfT369A0Bn/vWLNY2aZUjPQAp0BEcFnyleMXxGDi.mT9CuhSeIElMLXwsaZUikPpu1hSen/eW8XbwJGD"; ## SECRET-DATA
}
}
}
user@srx1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.2/24;
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.80.1/24;
address 192.168.90.1/24;
}
family mpls;
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}
user@srx1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
user@srx1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
user@srx1# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx1# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$z0C63/tp0Icrvz39p0Ihcs24aZjqmTn9p"; ## SECRET-DATA
user@srx1# show security ike gateway IKE_GW ike-policy IKE_POL; address [ 172.18.10.1 172.18.10.2 ]; external-interface ge-0/0/0.0; local-address 172.18.10.1; version v2-only; ppk-profile km_profile_1;
user@srx1# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srx1# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srx1# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 192.168.80.0/24;
}
establish-tunnels immediately;
SRX2
在配置模式下,输入show security key-manager profiles、、show security key-manager、 show security zonesshow security ipsec policy IPSEC_POLshow interfacesshow security ike proposal IKE_PROPshow security ipsec vpn IPSEC_VPNshow security policiesshow security ike policy IKE_POLshow security ike gateway IKE_GWshow security ipsec proposal IPSEC_PROP和命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@srx2# show security key-manager profiles
km_profile_1 {
static {
key-id ascii-text "$9$Hk5FCA0IhruOvWx-2gGDikT3IRhSrvQF"; ## SECRET-DATA
key ascii-text "$9$zDD33CuyrvNVY0BhreMN-jHqmQF/Ctu1R9A8X7V4oGDikT3uO1RSr69evMLN-jHqf5FtpBylMhSvL7N2gGDiqmTOBEylM9AMXxNY2UjH"; ## SECRET-DATA
}
}user@srx2# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$Hk5FCA0IhruOvWx-2gGDikT3IRhSrvQF"; ## SECRET-DATA
key ascii-text "$9$zDD33CuyrvNVY0BhreMN-jHqmQF/Ctu1R9A8X7V4oGDikT3uO1RSr69evMLN-jHqf5FtpBylMhSvL7N2gGDiqmTOBEylM9AMXxNY2UjH"; ## SECRET-DATA
}
}
}user@srx2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}user@srx2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srx2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srx2# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx2# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$zTi03/tp0Icrvz39p0Ihcs24aZjqmTn9p"; ## SECRET-DATA
user@srx2# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.1; external-interface ge-0/0/0.0; local-address 172.18.10.2; version v2-only; ppk-profile km_profile_1;
user@srx2# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srx2# show security ipsec policy IPSEC_POL
proposals IPSEC_PROP;
[edit]
user@srx2# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}
establish-tunnels immediately;
示例:为 AutoVPN 配置静态密钥配置文件
使用此配置示例可以通过配置静态密钥配置文件来保护 IPsec AutoVPN 基础架构。
您可以通过配置静态密钥配置文件来保护 IPsec AutoVPN 基础架构。
在此配置示例中,集线器、分支 1 和分支 2 使用静态密钥配置文件获取 IPsec VPN 上的 QKD 密钥。QKD 密钥有助于在互联网上安全地发送流量。
|
阅读时间 |
不到一个小时 |
|
配置时间 |
不到一个小时 |
先决条件示例
|
硬件要求 |
|
|
软件要求 |
Junos OS 22.4R1 或更高版本。 |
开始之前
|
优势 |
|
|
实用资源 |
|
|
了解更多 |
|
|
实践经验 |
|
|
了解更多 |
RFC 8784 - 在互联网密钥交换协议第 2 版 (IKEv2) 中混合预共享密钥以实现后量子安全 获取证书颁发机构 (CA) 的地址及其所需的信息(如质询密码),然后提交本地证书请求。请参阅 了解本地证书请求。 在每个设备中注册数字证书。请参阅 示例:手动加载 CA 和本地证书。 |
功能概述
| IPsec VPN |
部署中心辐射型 IPsec VPN 拓扑,其中分支通过通过中枢发送流量的 VPN 隧道连接。这些 VPN 隧道稍后会配置为使用量子密钥,使其成为量子安全 VPN 隧道。 |
| IKE 网关 |
建立安全连接时,IKE 网关在验证证书时,使用 IKE 策略将自身限制为已配置的 CA 组(CA 配置文件)。 |
| 建议 | |
| IKE 提案 |
定义用于与对等方安全网关建立安全 IKE 连接的算法和密钥。 IKE 创建动态 SA 并就 IPsec 对其进行协商。 |
| IPsec 提议 |
列出要与远程 IPsec 对等方协商的协议、算法和安全服务。 |
| 策略 | |
| IKE 策略 |
定义在 IKE 协商期间要使用的安全参数(IKE 提议)组合。 |
| IPsec 策略 |
包含允许在指定区域之间分组 VPN 流量的规则和安全策略。 |
| 安全策略 |
允许您选择要通过 IPsec SA 保护的数据流量类型。
|
|
配置文件 |
|
|
密钥配置文件 |
定义 SRX 系列防火墙设备如何与 KME 设备通信,以便从外部 KME 服务器检索 QKD 密钥。密钥配置文件分别配置在集线器 (HUB_KM_PROFILE_1) 和分支(SPOKE_1_KM_PROFILE_1 和 SPOKE_2_KM_PROFILE_1)上。
|
| PPK 信息 |
通过引用 IKE 网关下的密钥配置文件,指示用于建立量子安全 IKE 或 IPsec SA 的密钥配置文件。 |
| 证书 | |
| CA 证书 | 验证设备的身份并验证设备之间的通信链路。 |
| 本地证书 | 生成 PKI 并使用 CA 证书注册以进行验证。 |
| KME证书 | 供应商生成的第三方证书。 |
| 安全区域 | |
| trust |
主机区域的网段。 |
| untrust |
目标服务器区域的网段。 |
| vpn |
中心辐射型交换机交互的网段。 |
|
主要验证任务 |
验证已建立的 IKE 和 IPsec SA 是否为量子安全。 |
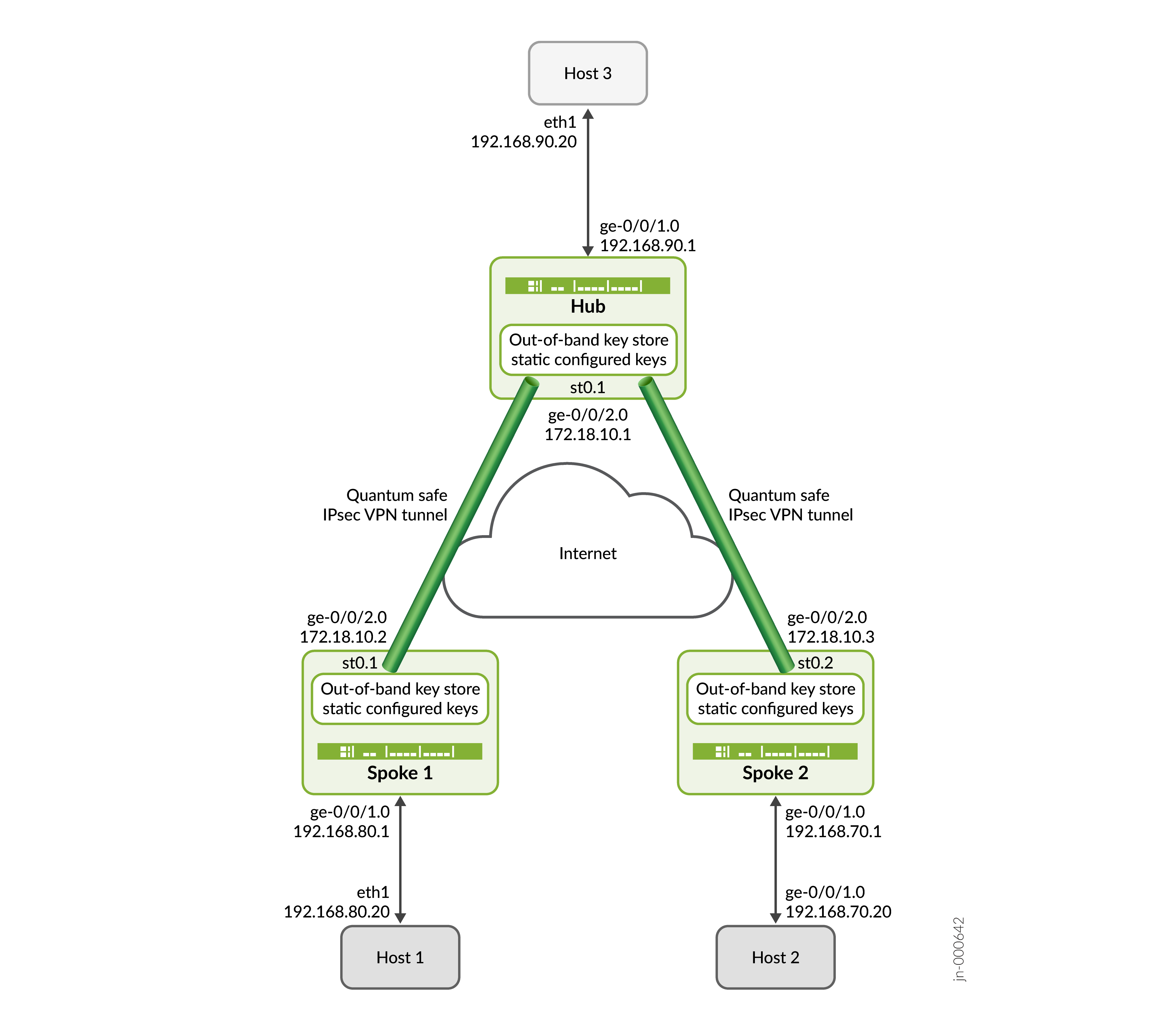
拓扑概述
在此示例中,分支 1 和 SPOKE 2 使用 CLI 配置的静态密钥启动与集线器的量子安全 IPsec 隧道协商。中枢通过验证分支 1 和分支 2 的身份及其各自的密钥来响应请求,并使用这两个分支建立量子安全 IPsec VPN。隧道建立后,将使用建立的 IPsec 隧道保护主机 1 和主机 3 之间以及主机 2 和主机 3 之间的数据流量。
|
主机名 |
角色 |
功能 |
|---|---|---|
| 枢纽 | 能够建立 IPsec 隧道的 SRX 系列防火墙 | 响应由 SPOKE 1 和 SPOKE 2 发起的 IKE 或 IPsec SA 协商,并使用中枢设备上配置的静态密钥建立量子安全 IPsec 隧道。 |
| 辐条 1 | 能够建立 IPsec 隧道的 SRX 系列防火墙 | 使用在分支 1 上配置的静态密钥启动 IKE/IPsec SA 协商并与集线器建立量子安全 IPsec 隧道。 |
| 辐条 2 | 能够建立 IPsec 隧道的 SRX 系列防火墙 | 启动 IKE 或 IPsec SA 协商,并使用在分支 2 上配置的静态密钥与中枢建立量子安全 IPsec 隧道。 |
| 主机 1 | 托管在受信任区域或分支 1 的 LAN 端内 | 发起流向主机 3 的客户端流量。 |
| 主机 2 | 位于辐射型 2 的可信区域或 LAN 端内的主机 | 发起流向主机 3 的客户端流量。 |
| 主机 3 | 托管在 HUB 的可信区域或 LAN 端 | 响应来自主机 1 和主机 2 的客户端流量。 |
拓扑图示
在 Hub 上进行分步配置
-
配置中枢接口。
[edit interfaces] user@hub# set ge-0/0/2 unit 0 family inet address 172.18.10.1/24 user@hub# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24 user@hub# set st0 unit 1 family inet
-
配置 CA 配置文件和 CA 证书。
[edit security pki] user@hub# set ca-profile Root-CA ca-identity Root-CA user@hub# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@hub# set ca-profile Root-CA revocation-check disable
-
在操作模式下,将 CA 证书绑定到 CA 配置文件。
user@hub> request security pki ca-certificate enroll ca-profile Root-CA user@hub> request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa user@hub> request security pki local-certificate enroll certificate-id HUB_CRT challenge-password <different> domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA
-
配置静态密钥管理器配置文件。
[edit security key-manager profiles] user@hub# set HUB_KM_PROFILE_1 static key-id ascii-text test-key-id user@hub# set HUB_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
在 IPsec VPN 上配置中心辐射型。这包括配置安全区域、安全策略和相关证书,以验证设备身份及其通信链路。
[edit security ike proposal] user@hub# set HUB_IKE_PROP authentication-method rsa-signatures user@hub# set HUB_IKE_PROP dh-group group14 user@hub# set HUB_IKE_PROP authentication-algorithm sha-256 user@hub# set HUB_IKE_PROP encryption-algorithm aes-256-cbc user@hub# set HUB_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@hub# set HUB_IKE_POL proposals HUB_IKE_PROP user@hub# set HUB_IKE_POL certificate local-certificate HUB_CRT
[edit security ike gateway] user@hub# set HUB_IKE_GW local-address 172.18.10.1 user@hub# set HUB_IKE_GW ike-policy HUB_IKE_POL user@hub# set HUB_IKE_GW external-interface ge-0/0/2.0 user@hub# set HUB_IKE_GW local-identity distinguished-name user@hub# set HUB_IKE_GW dynamic ike-user-type group-ike-id user@hub# set HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper user@hub# set HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 user@hub# set HUB_IKE_GW version v2-only
[edit security ipsec proposal] user@hub# set HUB_IPSEC_PROP protocol esp user@hub# set HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@hub# set HUB_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec policy] user@hub# set HUB_IPSEC_POL proposals HUB_IPSEC_PROP
[edit security ipsec vpn] user@hub# set HUB_IPSEC_VPN bind-interface st0.1 user@hub# set HUB_IPSEC_VPN ike gateway HUB_IKE_GW user@hub# set HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL user@hub# set HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@hub# set HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0
[edit security zones] user@hub# set security-zone untrust host-inbound-traffic system-services ike user@hub# set security-zone untrust interfaces ge-0/0/2.0 user@hub# set security-zone vpn interfaces st0.1 user@hub# set security-zone trust host-inbound-traffic system-services ping user@hub# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@hub# set from-zone trust to-zone vpn policy vpn_out match source-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match application any user@hub# set from-zone trust to-zone vpn policy vpn_out then permit user@hub# set from-zone vpn to-zone trust policy vpn_in match source-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match application any user@hub# set from-zone vpn to-zone trust policy vpn_in then permit
分支设备上的分步配置
-
配置分支接口。
[edit interfaces] user@spoke# set ge-0/0/2 unit 0 family inet address 172.18.10.2/24 user@spoke# set ge-0/0/1 unit 0 family inet address 192.168.80.1/24 user@spoke# set st0 unit 1 family inet
-
在 IPsec VPN 上配置中心辐射型。这包括配置安全区域、安全策略和相关证书,以验证设备身份及其通信链路。
[edit security ike proposal] user@spoke# set SPOKE_1_IKE_PROP authentication-method rsa-signatures user@spoke# set SPOKE_1_IKE_PROP dh-group group14 user@spoke# set SPOKE_1_IKE_PROP authentication-algorithm sha-256 user@spoke# set SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc user@spoke# set SPOKE_1_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@spoke# set SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP user@spoke# set SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW address 172.18.10.1 user@spoke# set SPOKE_1_IKE_GW local-address 172.18.10.2 user@spoke# set SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL user@spoke# set SPOKE_1_IKE_GW external-interface ge-0/0/2.0 user@spoke# set SPOKE_1_IKE_GW local-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW remote-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 user@spoke# set SPOKE_1_IKE_GW version v2-only
[edit security ipsec proposal] user@spoke# set SPOKE_1_IPSEC_PROP protocol esp user@spoke# set SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@spoke# set SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec policy] user@spoke# set SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP
[edit security ipsec vpn] user@spoke# set SPOKE_1_IPSEC_VPN bind-interface st0.1 user@spoke# set SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW user@spoke# set SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24
[edit security zones] user@spoke# set security-zone untrust host-inbound-traffic system-services ike user@spoke# set security-zone untrust interfaces ge-0/0/2.0 user@spoke# set security-zone vpn interfaces st0.1 user@spoke# set security-zone trust host-inbound-traffic system-services ping user@spoke# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@spoke# set from-zone trust to-zone vpn policy vpn_out match source-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match application any user@spoke# set from-zone trust to-zone vpn policy vpn_out then permit user@spoke# set from-zone vpn to-zone trust policy vpn_in match source-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match application any user@spoke# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki ] user@spoke# set ca-profile Root-CA ca-identity Root-CA user@spoke# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@spoke# set ca-profile Root-CA revocation-check disable
user@spoke> request security pki ca-certificate enroll ca-profile Root-CA user@spoke> request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa user@spoke> request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <different> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA
-
配置静态密钥管理器配置文件。
[edit security key-manager profiles] user@spoke# set SPOKE_1_KM_PROFILE_1 static key-id ascii-text test-key-id user@spoke# set SPOKE_1_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
验证
本部分提供可用于验证此示例中的功能的 show 命令列表。
| 命令 | 验证任务 |
|---|---|
|
显示安全 IKE 安全关联详细信息 |
|
|
显示安全 IPsec 安全关联详细信息 |
|
|
显示安全 IPsec 统计信息 |
|
|
显示安全密钥管理器配置文件详细信息 |
|
|
ping 192.168.90.20 源 192.168.80.20 计数 4 |
验证 IKE SA
目的
验证 IKE SA。
操作
在操作模式下,输入 show security ike security-associations detail 命令,以查看 IKE SA。
user@hub> show security ike security-associations detail
IKE peer 172.18.10.2, Index 2123, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 0e40ccdcee1b54bd, Responder cookie: 43964f5cc4d4491c
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 2840 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2610
Output bytes : 2571
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500440
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
IKE peer 172.18.10.3, Index 2124, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 651bf4a52a9375ec, Responder cookie: d9a9c95c27e3f929
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Lifetime: Expires in 2901 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2610
Output bytes : 2571
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500441
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
意义
、Role: Responder, State: UPPPK-profile: HUB_KM_PROFILE_1、IPSec security associations: 2 created, 0 deletedFlags: IKE SA is created和字段表示 IKE SA 创建成功。
验证 IPsec SA
目的
验证 IPsec SA。
操作
在操作模式下,输入 show security ipsec security-associations detail 命令,以查看 IPsec SA。
user@hub> show security ipsec security-associations detail
ID: 500440 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.80.0-192.168.80.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Thu Jul 20 2023 10:44:19: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x649d371f, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2840 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2183 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2123
Direction: outbound, SPI: 0xd5ef611e, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2840 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2183 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2123
ID: 500441 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.3
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.70.0-192.168.70.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Thu Jul 20 2023 10:45:19: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0xa0d3ba32, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2901 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2258 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2124
Direction: outbound, SPI: 0xe54414e3, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2901 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2258 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2124
意义
、Quantum Secured: YesPassive mode tunneling: DisabledPolicy-name: HUB_IPSEC_POLIPsec SA negotiation succeeds (1 times)、和字段表示 IPsec SA 创建成功。
验证 IPsec 统计信息
目的
验证 IPsec 统计信息。
操作
在操作模式下,输入 show security ipsec statistics 命令,以查看 IPsec 统计信息。
user@hub> show security ipsec statistics ESP Statistics: Encrypted bytes: 1248 Decrypted bytes: 1248 Encrypted packets: 8 Decrypted packets: 8 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
意义
ESP Statistics和 AH Statistics 字段显示 IPsec 统计信息。
验证密钥管理器配置文件
目的
验证密钥管理器配置文件。
操作
在操作模式下,输入 show security key-manager profiles detail 命令以查看密钥管理器配置文件。
user@hub> show security key-manager profiles detail
Name: HUB_KM_PROFILE_1, Index: 4, Type: Static
Configured-at: 20.07.23 (09:59:06)
Time-elapsed: 1 hrs 2 mins 7 secs
Request stats:
Received: 2
In-progress: 0
Success: 2
Failed: 0意义
Name: HUB_KM_PROFILE_1和 Type: Static 字段显示密钥管理器配置文件
从主机 1 到主机 3 的 Ping,反之亦然
目的
验证从主机 1 到主机 3 的连接。
操作
在操作模式下,输入 ping 192.168.90.20 source 192.168.80.20 count 4 命令以查看从主机 1 到主机 3 的连接。
user@HOST1# ping 192.168.90.20 source 192.168.80.20 count 4 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.90.20 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
意义
确认 PING 192.168.80.20 (192.168.80.20): 56 data bytes 从主机 1 到主机 3 的连接。
从主机 2 到主机 3 的 Ping,反之亦然
目的
验证从主机 2 到主机 3 的连接。
操作
在操作模式下,输入 ping 192.168.90.20 source 192.168.80.20 count 4 查看从主机 2 到主机 3 的连接。
user@HOST1# ping 192.168.90.20 source 192.168.70.20 count 4 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.90.20 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
意义
确认 PING 192.168.80.20 (192.168.80.20): 56 data bytes 从主机 2 到主机 3 的连接。
附录1:在所有设备上设置命令
在所有设备上设置命令输出。
在集线器上设置命令
set security ike proposal HUB_IKE_PROP dh-group group14 set security ike proposal HUB_IKE_PROP authentication-algorithm sha-256 set security ike proposal HUB_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal HUB_IKE_PROP lifetime-seconds 3600 set security ike policy HUB_IKE_POL proposals HUB_IKE_PROP set security ike policy HUB_IKE_POL certificate local-certificate HUB_CRT set security ike gateway HUB_IKE_GW local-address 172.18.10.1 set security ike gateway HUB_IKE_GW ike-policy HUB_IKE_POL set security ike gateway HUB_IKE_GW external-interface ge-0/0/2.0 set security ike gateway HUB_IKE_GW local-identity distinguished-name set security ike gateway HUB_IKE_GW dynamic ike-user-type group-ike-id set security ike gateway HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper set security ike gateway HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 set security ike gateway HUB_IKE_GW version v2-only set security ipsec proposal HUB_IPSEC_PROP protocol esp set security ipsec proposal HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal HUB_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP set security ipsec vpn HUB_IPSEC_VPN bind-interface st0.1 set security ipsec vpn HUB_IPSEC_VPN ike gateway HUB_IKE_GW set security ipsec vpn HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.1/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
在分支 1 上设置命令
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <different> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA set security key-manager profiles SPOKE_1_KM_PROFILE_1 static key-id ascii-text test-key-id set security key-manager profiles SPOKE_1_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_1_IKE_PROP dh-group group14 set security ike proposal SPOKE_1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_1_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP set security ike policy SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT set security ike gateway SPOKE_1_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_1_IKE_GW local-address 172.18.10.2 set security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL set security ike gateway SPOKE_1_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_1_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 set security ike gateway SPOKE_1_IKE_GW version v2-only set security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP set security ipsec vpn SPOKE_1_IPSEC_VPN bind-interface st0.1 set security ipsec vpn SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW set security ipsec vpn SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.2/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
在分支 2 上设置命令
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_2_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_2_CRT challenge-password <different> domain-name spoke_2.juniper.net email spoke_2@juniper.net subject DC=juniper,CN=spoke_2.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA set security key-manager profiles SPOKE_2_KM_PROFILE_1 static key-id ascii-text test-key-id set security key-manager profiles SPOKE_2_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_2_IKE_PROP dh-group group14 set security ike proposal SPOKE_2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_2_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_2_IKE_POL proposals SPOKE_IKE_PROP set security ike policy SPOKE_2_IKE_POL certificate local-certificate SPOKE_2_CRT set security ike gateway SPOKE_2_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_2_IKE_GW local-address 172.18.10.3 set security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL set security ike gateway SPOKE_2_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_2_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW ppk-profile SPOKE_2_KM_PROFILE_1 set security ike gateway SPOKE_2_IKE_GW version v2-only set security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_2_IPSEC_POL proposals SPOKE_2_IPSEC_PROP set security ipsec vpn SPOKE_2_IPSEC_VPN bind-interface st0.2 set security ipsec vpn SPOKE_2_IPSEC_VPN ike gateway SPOKE_2_IKE_GW set security ipsec vpn SPOKE_2_IPSEC_VPN ike ipsec-policy SPOKE_2_IPSEC_POL set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 local-ip 192.168.70.0/24 set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.3/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.70.1/24 set interfaces st0 unit 2 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.2 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
附录2:显示 DUT 上的配置输出
枢纽
在配置模式下,输入 show security ike proposal HUB_IKE_PROP、 show security ike policy HUB_IKE_POL、 show security ipsec vpn HUB_IPSEC_VPNshow security ike gateway HUB_IKE_GWshow security ipsec policy HUB_IPSEC_POLshow interfacesshow security ipsec proposal HUB_IPSEC_PROPshow security zones和show security policies命令来确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@hub# show security ike proposal HUB_IKE_PROP dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@hub# show security ike policy HUB_IKE_POL
proposals HUB_IKE_PROP;
certificate {
local-certificate HUB_CRT;user@hub# show security ike gateway HUB_IKE_GW
ike-policy HUB_IKE_POL;
dynamic {
distinguished-name {
wildcard C=us,DC=juniper;
}
ike-user-type group-ike-id;
}
local-identity distinguished-name;
external-interface ge-0/0/2.0;
local-address 172.18.10.1;
version v2-only;
ppk-profile HUB_KM_PROFILE_1;user@hub# show security ipsec proposal HUB_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@hub# show security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP;
user@hub# show security ipsec vpn HUB_IPSEC_VPN
bind-interface st0.1;
ike {
gateway HUB_IKE_GW;
ipsec-policy HUB_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 0.0.0.0/0;
}user@hub# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}user@hub# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
user@hub# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}辐条 1
在配置模式下,输入show security pki ca-profile Root-CA、、show security key-manager profiles SPOKE_1_KM_PROFILE_1、show security ike gateway SPOKE_1_IKE_GWshow security ipsec proposal SPOKE_1_IPSEC_PROPshow security ipsec policy SPOKE_1_IPSEC_POLshow security ike policy SPOKE_1_IKE_POLshow security ike proposal SPOKE_1_IKE_PROPshow interfacesshow security zonesshow security ipsec vpn SPOKE_1_IPSEC_VPNshow security policies和show security pki命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@spoke1# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
user@spoke1# show security key-manager profiles SPOKE_1_KM_PROFILE_1
static {
key-id ascii-text "$9$cJ5SvLdVYoZjs2qmTFAt1RhSMXoaZUjqWL"; ## SECRET-DATA
key ascii-text "$9$mfF/IRSWX-9AORhyW8aZUj.PQFn/tuz3lKMXbwgoJGqf/Ctu1RTzhSyeW8aZUHkPn6AIEyO1SeMWdVgoJUjqCA0IEyz3yKvW-d4aZ"; ## SECRET-DATA
}
user@spoke1# show security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke1# show security ike policy SPOKE_1_IKE_POL
proposals SPOKE_1_IKE_PROP;
certificate {
local-certificate SPOKE_1_CRT;
}
user@spoke1# show security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.2; version v2-only; ppk-profile SPOKE_1_KM_PROFILE_1;
user@spoke1# show security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke1# show security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP;
user@spoke1# show security ipsec vpn SPOKE_1_IPSEC_VPN
bind-interface st0.1;
ike {
gateway SPOKE_1_IKE_GW;
ipsec-policy SPOKE_1_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}user@spoke1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}
user@spoke1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@spoke1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
user@spoke1# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
}辐条 2
在配置模式下,输入show security pki、、show security key-manager、show security ipsec proposal SPOKE_2_IPSEC_PROPshow security ike policy SPOKE_2_IKE_POLshow security ike proposal SPOKE_2_IKE_PROPshow security ipsec vpn SPOKE_2_IPSEC_VPNshow interfacesshow security ike gateway SPOKE_2_IKE_GWshow security zones和show security policies命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@spoke2# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
}
user@spoke2# show security key-manager
profiles {
SPOKE_2_KM_PROFILE_1 {
static {
key-id ascii-text "$9$C4Y8ABEleWx-wM8goGjPf369A1hx7-VwgIE"; ## SECRET-DATA
key ascii-text "$9$15SRyKdVYGjqvW7Vw2GUn/CtBIcylK8XSr4aZjPfz369ORKM8X-VhSwY2oGUn/Cu0IleWdb27-YoZG.mz36CtOMWxdb2Sr2aJGq.Fn/"; ## SECRET-DATA
}
}
}
user@spoke2# show security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke2# show security ike policy SPOKE_2_IKE_POL
proposals SPOKE_IKE_PROP;
certificate {
local-certificate SPOKE_2_CRT;
}
user@spoke2# show security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.3; version v2-only; ppk-profile SPOKE_2_KM_PROFILE_1;
user@spoke2# show security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke2# show security ipsec vpn SPOKE_2_IPSEC_VPN
bind-interface st0.2;
ike {
gateway SPOKE_2_IKE_GW;
ipsec-policy SPOKE_2_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.70.0/24;
remote-ip 192.168.90.0/24;
}user@spoke2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@spoke2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.2;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@spoke2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}为 Junos Key Manager 配置 Quantum Key Manager 密钥配置文件
此示例说明如何为 Junos 密钥管理器配置量子密钥配置文件。配置量子密钥管理器密钥配置文件,以生成并发送生成的密钥,以建立量子安全 IPsec VPN 隧道。
要求
-
硬件要求 —瞻博网络® SRX1500防火墙和更高编号的设备型号或瞻博网络®vSRX 虚拟防火墙 (vSRX3.0)。
-
软件要求 - Junos OS 22.4R1 或更高版本,带有 JUNOS ike 软件 JUNOS Key Manager 包。
-
使用任何支持 ETSI 量子密钥分发 (QKD) REST API 标准的 QKD 设备进行通信。
-
在设备上加载本地证书。建议提供证书的完整路径。
概述
SRX 系列防火墙设备使用 IPsec VPN 通过互联网安全地发送流量。在 IPsec VPN 中配置量子密钥管理器密钥配置文件,以重新验证现有 IKE SA 以及新的密钥和密钥。
量子密钥管理器密钥配置文件使用基于 QKD 的安全密钥分配方法来生成和分发量子安全的密钥。这些键是动态的。
配置
-
配置 CA 证书。
user@host# set security pki ca-profile Root-CA ca-identity Root-CA user@host# set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@host# set security pki ca-profile Root-CA revocation-check disable
-
加载 CA 证书。
user@host> request security pki local-certificate load certificate-id SAE_A filename SAE_A.cert key SAE_A.key
-
注册 CA 证书。
user@host> request security pki ca-certificate enroll ca-profile Root-CA
-
配置量子密钥管理器配置文件。
user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager url https://kme.juniper.net user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager local-sae-id SAE_A user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_A_CERT user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
验证
目的
验证量子密钥管理器密钥配置文件和密钥。
操作
在操作模式下,输入 show security pki ca-certificate ca-profile Root-CA ,查看 CA 配置文件和 CA 证书。
user@host> show security pki ca-certificate ca-profile Root-CA
LSYS: root-logical-system
CA profile: Root-CA
Certificate identifier: Root-CA
Issued to: Root-CA, Issued by: C = IN, ST = WestBengal, O = JuniperNetworks, CN = Root-CA
Validity:
Not before: 09-11-2023 09:03 UTC
Not after: 03-24-2044 09:03 UTC
Public key algorithm: rsaEncryption(4096 bits)
Keypair Location: Keypair generated locally在操作模式下,输入 show security pki local-certificate certificate-id SAE_A_CERT ,查看 PKI 本地证书。
user@host> show security pki local-certificate certificate-id SAE_A_CERT
LSYS: root-logical-system
Certificate identifier: SAE_A_CERT
Issued to: SAE_A, Issued by: C = IN, ST = WestBengal, O = JuniperNetworks, CN = ROOT_CA
Validity:
Not before: 08-28-2023 04:54 UTC
Not after: 03-10-2044 04:54 UTC
Public key algorithm: rsaEncryption(2048 bits)
Keypair Location: Keypair generated locally在操作模式下,输入 request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B 以查看对等设备密钥管理器配置文件和密钥。
user@host> request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B
- Response:
- Status: SUCCESS
- Name: km_profile_1
- Type: quantum-key-manager
- Key-size: 256 bits
- Key-count: 1
- Key-ids:
- 002420bd-7a03-4725-9c41-6969d8e1815a
- Keys:
- 728d21c4a05fe2f73c7b2f58d1e3631dc68fcfaca16be12ca3fc7715079db0f9在操作模式下,输入 show security key-manager profiles name KM_PROFILE_1 detail 以查看密钥管理器配置文件的详细信息。
user@host> show security key-manager profiles name KM_PROFILE_1 detail
Name: KM_PROFILE_1, Index: 2, Type: quantum-key-manager
Configured-at: 11.09.23 (02:04:32)
Time-elapsed: 0 hrs 20 mins 23 secs
Url: https://kme.juniper.net
Local-sae-id: SAE_A
Local-certificate-id: SAE_A_CERT
Trusted-cas: [ Root-CA ]
Peer-sae-ids: N/A
Default-key-size: N/A
Request stats:
Received: 0
In-progress: 0
Success: 0
Failed: 0意义
显示 show security pki ca-certificate ca-profile Root-CA PKI CA 配置文件名称、证书标识符、有效性、公钥算法等。
显示 show security pki local-certificate certificate-id SAE_A_CERT 本地 CA 配置文件名称、证书标识符、有效性、公钥算法等。
显示 request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B 对等设备密钥管理器配置文件和密钥。
显示 show security key-manager profiles name KM_PROFILE_1 detail 安全密钥管理器配置文件名称、URL、请求等。
示例:为站点到站点 IPsec VPN 配置 Quantum Key Manager 密钥配置文件
使用此配置示例可以通过配置量子密钥管理器密钥配置文件来保护 IPsec 站点到站点 VPN 基础架构。
您可以通过配置量子密钥管理器密钥配置文件来保护 IPsec 站点到站点 VPN 基础架构。
在此配置示例中, SRX1 和 SRX2 设备使用量子密钥管理器配置文件获取 IPsec VPN 上的 QKD 密钥。QKD 密钥有助于在互联网上安全地发送流量。
|
阅读时间 |
不到一个小时 |
|
配置时间 |
不到一个小时 |
先决条件示例
|
硬件要求 |
® 瞻博网络SRX1500防火墙或更高编号的设备型号或瞻博网络®vSRX 虚拟防火墙 (vSRX3.0) |
|
软件要求 |
Junos OS 22.4R1 或更高版本。 |
开始之前
|
优势 |
|
|
实用资源 |
|
|
了解更多 |
|
|
实践经验 |
|
|
了解更多 |
功能概述
| IPsec VPN |
部署中心辐射型 IPsec VPN 拓扑,其中分支通过通过中枢发送流量的 VPN 隧道连接。这些 VPN 隧道稍后会配置为使用量子密钥,使其成为量子安全 VPN 隧道。 |
| IKE 网关 |
建立安全连接。在验证证书时,IKE 网关使用 IKE 策略将自身限制为已配置的证书颁发机构 (CA) 配置文件组。 |
| 建议 | |
| IKE 提案 |
定义用于与对等方安全网关建立安全 IKE 连接的算法和密钥。 IKE 创建动态安全关联 (SA),并针对 IPsec 对其进行协商。 |
| IPsec 提议 |
列出要与远程 IPsec 对等方协商的协议、算法和安全服务。 |
| 策略 | |
| IKE 策略 |
定义在 IKE 协商期间要使用的安全参数(IKE 提议)组合。 |
| IPsec 策略 |
包含允许在指定区域之间分组 VPN 流量的规则和安全策略。 |
| 安全策略 |
允许您选择要通过 IPsec SA 保护的数据流量类型。
|
|
配置文件 |
|
|
密钥配置文件 |
定义 SRX 系列防火墙设备如何与 KME 设备通信以从外部 KME 服务器检索 QKD 密钥。密钥配置文件分别配置在集线器 (HUB_KM_PROFILE_1) 和分支(SPOKE_1_KM_PROFILE_1 和 SPOKE_2_KM_PROFILE_1)上。
|
| PPK 信息 |
通过引用 IKE 网关下的密钥配置文件,指示用于建立量子安全 IKE 或 IPsec SA 的密钥配置文件。 |
| 证书 | |
| CA 证书 | 验证设备的身份并验证通信链路。 |
| 本地证书 | 生成 PKI 并使用 CA 证书注册以进行验证。 |
| KME证书 | 供应商生成的第三方证书。 |
| 安全区域 | |
| trust |
主机区域的网段。 |
| untrust |
目标服务器区域的网段。 |
| vpn |
中心辐射公司通过它进行交互的网段。 |
|
主要验证任务 |
验证已建立的 IKE 和 IPsec SA 是否为量子安全。 |
拓扑概述
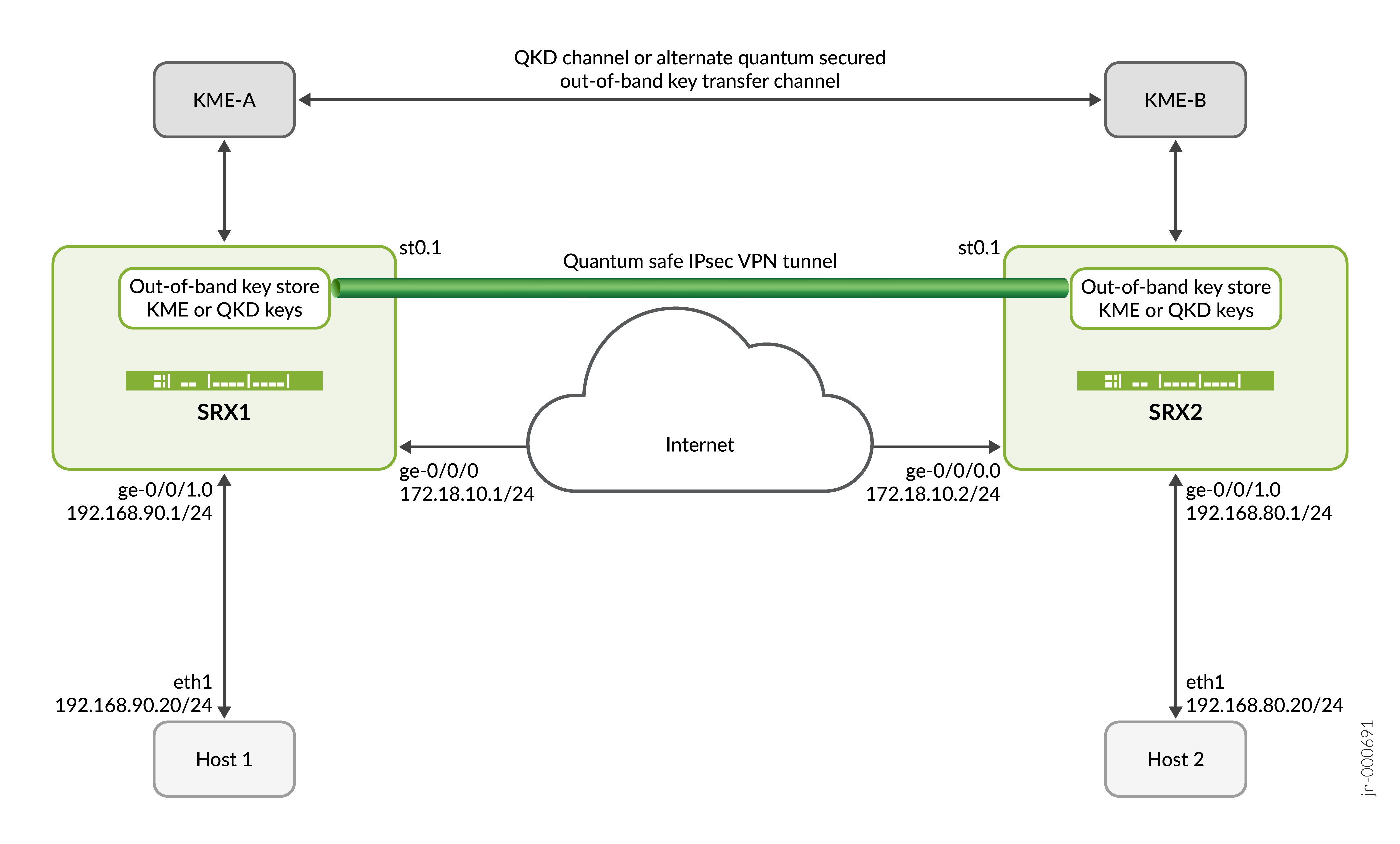
在此示例中,我们使用第三方 KME 设备生成的量子密钥保护 SRX1 和 SRX2 IPsec VPN 隧道。KME 设备(KME-A 和 KME-B)通过高度安全且能够识别威胁的量子通道相互连接。利用此通道,SRX1 和 SRX2 设备从对应的 KME 设备检索量子密钥,并将其与现有密钥合并,从而实现量子安全 VPN 隧道。
|
主机名 |
角色 |
功能 |
|---|---|---|
| SRX1 | 能够建立 IPsec 隧道的 SRX 系列防火墙设备 | 启动 IKE 或 IPsec SA 协商,并使用从 KME-A QKD 设备获取的 QKD 密钥与 SRX2 建立量子安全 IPsec 隧道。 |
| SRX2 | 能够建立 IPsec 隧道的 SRX 系列防火墙设备 | 响应 IKE 或 IPsec SA 协商,并使用 KME-B QKD 设备的 QKD 密钥建立量子安全 IPsec 隧道。 |
| HOST1 | SRX1 的可信区域或 LAN 端内的主机 | 启动流向主机 2 的客户端流量 |
| HOST2 | SRX2 的可信区域或 LAN 端内的主机 | 响应来自主机 1 的客户端流量。 |
| KME-A | 第三方供应商 QKD 设备 | 提供 QKD 密钥以响应来自 SRX1 的密钥请求。 |
| KME-B | 第三方供应商 QKD 设备 | 提供 QKD 密钥以响应来自 SRX2 的密钥请求。 |
拓扑图示
SRX 系列防火墙设备上的分步配置
-
配置接口。
[edit interfaces] user@srx# set ge-0/0/0 unit 0 family inet address 172.18.10.1/24 user@srx# set st0 unit 1 family inet user@srx# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24
-
使用必须参数或推荐参数配置 quantum-key-manager 类型的密钥配置文件。
定义CA证书,配置KME服务器的URL,配置本地端使用的SAE-ID,为本地SAE-ID配置相应的证书,配置之前定义的CA证书。
[edit security pki] user@srx# set ca-profile ROOT_CA_CERT ca-identity RootCA
[edit security key-manager profiles] user@srx# set km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net
[edit security key-manager profiles] user@srx# set km_profile_1 quantum-key-manager local-sae-id SAE_A user@srx# set km_profile_1 quantum-key-manager local-certificate-id SAE_A_CERT user@srx# set km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT
配置站点到站点 IPsec VPN。这包括配置安全区域、安全策略和相关证书,以验证设备身份及其通信链路。
[edit security zones] user@srx# set security-zone untrust host-inbound-traffic system-services ike user@srx# set security-zone untrust interfaces ge-0/0/0.0 user@srx# set security-zone vpn interfaces st0.1 user@srx# set security-zone trust host-inbound-traffic system-services ping user@srx# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@srx# set from-zone trust to-zone vpn policy vpn_out match source-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match application any user@srx# set from-zone trust to-zone vpn policy vpn_out then permit user@srx# set from-zone vpn to-zone trust policy vpn_in match source-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match application any user@srx# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security ike proposal] user@srx# set IKE_PROP authentication-method pre-shared-keys user@srx# set IKE_PROP dh-group group14 user@srx# set IKE_PROP authentication-algorithm sha-256 user@srx# set IKE_PROP encryption-algorithm aes-256-cbc user@srx# set IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@srx# set IKE_POL proposals IKE_PROP user@srx# set IKE_POL pre-shared-key ascii-text ipsec-test
[edit security ike gateway] user@srx# set IKE_GW ike-policy IKE_POL user@srx# set IKE_GW address 172.18.10.2 user@srx# set IKE_GW external-interface ge-0/0/0.0 user@srx# set IKE_GW local-address 172.18.10.1 user@srx# set IKE_GW version v2-only user@srx# set IKE_GW ppk-profile km_profile_1
[edit security ipsec proposal] user@srx# set IPSEC_PROP protocol esp user@srx# set IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx# set IPSEC_PROP encryption-algorithm aes-256-cbc user@srx# set IPSEC_PROP lifetime-seconds 2400
[edit security ipsec policy] user@srx# set IPSEC_POL proposals IPSEC_PROP
[edit security ipsec vpn] user@srx# set IPSEC_VPN bind-interface st0.1 user@srx# set IPSEC_VPN ike gateway IKE_GW user@srx# set IPSEC_VPN ike ipsec-policy IPSEC_POL user@srx# set IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@srx# set IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 user@srx# set IPSEC_VPN establish-tunnels immediately
验证
本部分提供可用于验证此示例中的功能的 show 命令列表。
| 命令 | 验证任务 |
|---|---|
|
显示安全 IKE 安全关联详细信息 |
|
|
显示安全 IPsec 安全关联详细信息 |
|
|
显示安全 IPsec 统计信息 |
验证 IPsec 加密和解密统计信息。 |
|
显示安全密钥管理器配置文件详细信息 |
验证密钥配置文件统计信息。 |
|
ping 192.168.80.20 源 192.168.90.20 计数 5 |
从 HOST 1 到 HOST 2 的 Ping,反之亦然。 |
验证 IKE SA
目的
验证 IKE SA。
操作
在操作模式下,输入 show security ike security-associations detail 命令,以查看 IKE SA。
user@srx> show security ike security-associations detail IKE peer 172.18.10.2, Index 21, Gateway Name: IKE_GW Role: Initiator, State: UP Initiator cookie: 5a417d46cef3207d, Responder cookie: 57b9a17516bee31b Exchange type: IKEv2, Authentication method: Pre-shared-keys Local gateway interface: ge-0/0/2.0 Routing instance: default Local: 172.18.10.1:500, Remote: 172.18.10.2:500 Lifetime: Expires in 3445 seconds Reauth Lifetime: Disabled IKE Fragmentation: Enabled, Size: 576 SRG ID: 0 Remote Access Client Info: Unknown Client Peer ike-id: 172.18.10.2 AAA assigned IP: 0.0.0.0 PPK-profile: km_profile_1 Optional: No State : Used Algorithms: Authentication : hmac-sha256-128 Encryption : aes256-cbc Pseudo random function: hmac-sha256 Diffie-Hellman group : DH-group-14 Traffic statistics: Input bytes : 783 Output bytes : 831 Input packets: 2 Output packets: 2 Input fragmented packets: 0 Output fragmented packets: 0 IPSec security associations: 2 created, 0 deleted Phase 2 negotiations in progress: 1 IPSec Tunnel IDs: 500003 Negotiation type: Quick mode, Role: Initiator, Message ID: 0 Local: 172.18.10.1:500, Remote: 172.18.10.2:500 Local identity: 172.18.10.1 Remote identity: 172.18.10.2 Flags: IKE SA is created IPsec SA Rekey CREATE_CHILD_SA exchange stats: Initiator stats: Responder stats: Request Out : 0 Request In : 0 Response In : 0 Response Out : 0 No Proposal Chosen In : 0 No Proposal Chosen Out : 0 Invalid KE In : 0 Invalid KE Out : 0 TS Unacceptable In : 0 TS Unacceptable Out : 0 Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0 Res Verify SA Fail : 0 Res Verify DH Group Fail: 0 Res Verify TS Fail : 0
意义
、Role: Initiator, State: UPPPK-profile: km_profile_1、IPSec security associations: 2 created, 0 deleted Phase 2 negotiations in progress: 1Flags: IKE SA is created和字段表示 IKE SA 创建成功。
验证 IPsec SA
目的
验证 IPsec SA。
操作
在操作模式下,输入 show security ipsec security-associations detail 命令,以查看 IPsec SA。
user@srx> show security ipsec security-associations detail ID: 500003 Virtual-system: root, VPN Name: IPSEC_VPN Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2 Traffic Selector Name: ts1 Local Identity: ipv4(192.168.90.0-192.168.90.255) Remote Identity: ipv4(192.168.80.0-192.168.80.255) TS Type: traffic-selector Version: IKEv2 Quantum Secured: Yes PFS group: N/A SRG ID: 0 DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: IPSEC_POL Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0 Multi-sa, Configured SAs# 0, Negotiated SAs#: 0 Tunnel events: Fri Mar 31 2023 01:41:52: IPsec SA negotiation succeeds (1 times) Location: FPC 0, PIC 0, KMD-Instance 0 Anchorship: Thread 1 Distribution-Profile: default-profile Direction: inbound, SPI: 0xd1e1549c, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1916 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1349 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21 Direction: outbound, SPI: 0xb5883167, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1916 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1349 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21
意义
、Quantum Secured: YesPolicy-name: IPSEC_POLIPsec SA negotiation succeeds (1 times)tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21、和字段表示 IPsec SA 创建成功。
验证 IPsec 统计信息
目的
验证 IPsec 统计信息。
操作
在操作模式下,输入 show security ipsec statistics 命令,以查看 IPsec 统计信息。
user@srx> show security ipsec statistics ESP Statistics: Encrypted bytes: 780 Decrypted bytes: 780 Encrypted packets: 5 Decrypted packets: 5 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
意义
ESP Statistics和 AH Statistics 字段显示 IPsec 统计信息。
验证密钥管理器配置文件
目的
验证密钥管理器配置文件。
操作
在操作模式下,输入 show security key-manager profiles detail 命令以查看密钥管理器配置文件。
user@srx> show security key-manager profiles detail Name: km_profile_1, Index: 3, Type: Quantum-key-manager Configured-at: 31.03.23 (01:40:50) Time-elapsed: 0 hrs 11 mins 30 secs Url: https://www.kme_a-qkd-server.net Local-sae-id: SAE_A Local-certificate-id: SAE_A_CERT Trusted-cas: [ ROOT_CA_CERT ] Peer-sae-ids: N/A Default-key-size: N/A Request stats: Received: 1 In-progress: 0 Success: 1 Failed: 0
意义
Name: km_profile_1和 Quantum-key-manager 字段显示密钥管理器配置文件。
从 HOST 1 到 HOST 2 的 Ping,反之亦然
目的
验证从主机 1 到主机 2 的连接。
操作
在操作模式下,输入 ping 192.168.80.20 source 192.168.90.20 计数 5 以查看从主机 1 到主机 2 的连接。
user@HOST1# ping 192.168.80.20 source 192.168.90.20 count 5 PING 192.168.80.20 (192.168.80.20): 56 data bytes count 5 64 bytes from 192.168.80.1: icmp_seq=0 ttl=64 time=0.998 ms 64 bytes from 192.168.80.1: icmp_seq=1 ttl=64 time=1.594 ms 64 bytes from 192.168.80.1: icmp_seq=2 ttl=64 time=1.395 ms 64 bytes from 192.168.80.1: icmp_seq=3 ttl=64 time=1.536 ms 64 bytes from 192.168.80.1: icmp_seq=4 ttl=64 time=1.838 ms --- 192.168.80.1 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.998/1.472/1.838/0.277 ms Data traffic is successfully flowing between the HOSTs
意义
确认 PING 192.168.80.20 (192.168.80.20): 56 data bytes count 5 从主机 1 到主机 2 的连接。
附录1:在所有设备上设置命令
在所有设备上设置命令输出。
在 SRX1 上设置命令
set security pki ca-profile ROOT_CA_CERT ca-identity RootCA set security key-manager profiles km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net set security key-manager profiles km_profile_1 quantum-key-manager local-sae-id SAE_A set security key-manager profiles km_profile_1 quantum-key-manager local-certificate-id SAE_A_CERT set security key-manager profiles km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.1/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.2 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.1 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
在 SRX2 上设置命令
set security pki ca-profile ROOT_CA_CERT ca-identity RootCA set security key-manager profiles km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net set security key-manager profiles km_profile_1 quantum-key-manager local-sae-id SAE_B set security key-manager profiles km_profile_1 quantum-key-manager local-certificate-id SAE_B_CERT set security key-manager profiles km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.2/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.1 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.2 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
附录2:显示 DUT 上的配置输出
在 DUT 上显示命令输出。
SRX1
user@srk1# show security pki
ca-profile ROOT_CA_CERT {
ca-identity RootCA;
}
user@srk1# show security key-manager
profiles {
km_profile_1 {
quantum-key-manager {
url https://www.kme_a-qkd-server.net;
local-sae-id SAE_A;
local-certificate-id SAE_A_CERT;
trusted-cas ROOT_CA_CERT;
}
}
}user@srk1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@srk1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srk1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srk1# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srk1# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$Nadwg4aUH.5Nds4aUiHuO1RhrvWxVs4"; ## SECRET-DATA
user@srk1# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.2; external-interface ge-0/0/0.0; local-address 172.18.10.1; version v2-only; ppk-profile km_profile_1;
user@srk1# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srk1# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srk1# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 192.168.80.0/24;
}
establish-tunnels immediately;SRX 2
user@srx2# show security key-manager
profiles {
km_profile_1 {
quantum-key-manager {
url https://www.kme_a-qkd-server.net;
local-sae-id SAE_B;
local-certificate-id SAE_B_CERT;
trusted-cas ROOT_CA_CERT;
}
}
}user@srx2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@srx2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srx2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srx2# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx2# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.1; external-interface ge-0/0/0.0; local-address 172.18.10.2; version v2-only; ppk-profile km_profile_1;
user@srx2# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$P5z6/Cu1EyP5F/CuB1-VwYgJDi.TF/"; ## SECRET-DATA
user@srx2# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srx2# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}
establish-tunnels immediately;示例:使用 Quantum Key Manager 密钥配置文件配置量子安全 IPsec AutoVPN 拓扑
使用此配置示例可以通过配置量子密钥管理器密钥配置文件来保护 IPsec AutoVPN 基础架构。
Hub、Spoke 1 和 Spoke 2 使用量子密钥管理器密钥配置文件与 KME Hub、KME Spoke 1 和 KME Spoke 2 通信,以获取 QKD 密钥并建立 IPsec VPN 隧道。
阅读时间 |
不到一个小时。 |
配置时间 |
不到一个小时。 |
先决条件示例
硬件要求 |
|
软件要求 |
Junos OS 22.4R1 或更高版本。 |
开始之前
优势 |
|
实用资源 |
|
了解更多 |
|
实践经验 |
|
了解更多 |
功能概述
表 20 提供此示例中部署的配置组件的快速摘要。
| IPsec VPN | 部署中心辐射型 IPsec VPN 拓扑,其中分支通过通过中枢发送流量的 VPN 隧道连接。这些 VPN 隧道稍后会配置为使用量子密钥,使其成为量子安全 VPN 隧道。 |
| IKE 网关 | 建立安全连接时,IKE 网关使用 IKE 策略将自身限制为已配置的 CA 组(CA 配置文件),同时验证证书。 |
| 建议 | |
| IKE 提案 | 定义用于与对等安全网关建立安全 IKE 连接的算法和密钥。 IKE 创建动态 SA 并就 IPsec 对其进行协商。 |
| IPsec 提议 | 列出要与远程 IPsec 对等方协商的协议、算法和安全服务。 |
| 策略 | |
| IKE 策略 | 定义在 IKE 协商期间要使用的安全参数(IKE 提议)组合。 |
| IPsec 策略 | 包含规则和安全策略,以允许在指定区域之间分组 VPN 流量。 |
| 安全策略 | 允许您选择要通过 IPsec SA 保护的数据流量类型。
|
配置文件 |
|
| 密钥配置文件 | 定义 SRX 设备如何与 KME 设备通信,以便从外部 KME 服务器检索 QKD 密钥。密钥配置文件分别配置在集线器 (HUB_KM_PROFILE_1) 和分支(SPOKE_1_KM_PROFILE_1 和 SPOKE_2_KM_PROFILE_1)上。 为应用和服务配置 SPOKE-1 和 SPOKE-2 以从外部服务器检索 QKD 密钥。
|
| PPK 信息 | 通过引用 IKE 网关下的密钥配置文件,指明用于建立量子安全 IKE 或 IPsec SA 的密钥配置文件。 |
| 证书 | |
| CA 证书 | 验证设备的身份并验证它们之间的通信链路。 |
| 本地证书 | 生成 PKI 并使用 CA 证书注册以进行验证。 |
| KME证书 | 供应商生成的第三方证书。 |
| 安全区域 | |
| trust | 主机区域的网段。 |
| untrust | 目标服务器区域的网段。 |
| vpn | 中心辐射公司通过它进行交互的网段。 |
主要验证任务 |
验证已建立的 IKE 和 IPsec SA 是否为量子安全。 |
拓扑概述
在此示例中,我们使用第三方 KME 设备生成的量子密钥保护中心辐射型 IPsec VPN 隧道。KME 设备(KME-Hub、KME-Spoke 1 和 KME-Spoke 2)通过高度安全且能够识别威胁的量子通道相互连接。使用此通道,中心辐射型设备从相应的 KME 设备检索量子密钥,并将其与现有密钥合并,以使 VPN 隧道实现量子安全。
拓扑组件 |
角色 |
功能 |
|---|---|---|
Hub |
能够建立 IPsec 隧道的 SRX 系列防火墙 | 响应 IKE 或 IPsec SA 协商,并使用 KME-HUB QKD 设备的 SPOKE-1SPOKE-2QKD 密钥建立量子安全 IPsec 隧道。 |
SPOKE-1 |
能够建立 IPsec 隧道的 SRX 系列防火墙 | 启动 IKE 或 IPsec SA 协商,并使用 QKD 设备中的 QKD 密钥 KME-SPOKE-1 与集线器建立量子安全 IPsec 隧道。 |
SPOKE-2 |
能够建立 IPsec 隧道的 SRX 系列防火墙 | 启动 IKE 或 IPsec SA 协商,并使用 QKD 设备中的 QKD 密钥 KME-SPOKE-2 与集线器建立量子安全 IPsec 隧道。 |
HOST-1 |
受信任区域或 的 SPOKE 1Host 1 LAN 端内的主机受 SPOKE 1保护。 |
将客户端流量引导至以下 HOST-3 |
HOST-2 |
受信任区域或 的 SPOKE 2Host 2 LAN 端内的主机受 SPOKE 2保护。 |
将客户端流量引导至以下 HOST-3 |
HOST- 3 |
托管在集线器的可信区域或 LAN 端。 Host 3 受 Hub保护。 |
响应来自 HOST-1 和 的客户端流量 HOST-2 |
KME-HUB |
第三方 QKD 设备 | 提供 QKD 密钥以响应来自 HUB |
KME-SPOKE-1 |
第三方 QKD 设备 | 提供 QKD 密钥以响应来自 SPOKE-1 |
KME-SPOKE-2 |
第三方 QKD 设备 | 提供 QKD 密钥以响应来自 SPOKE-2 |
拓扑图示
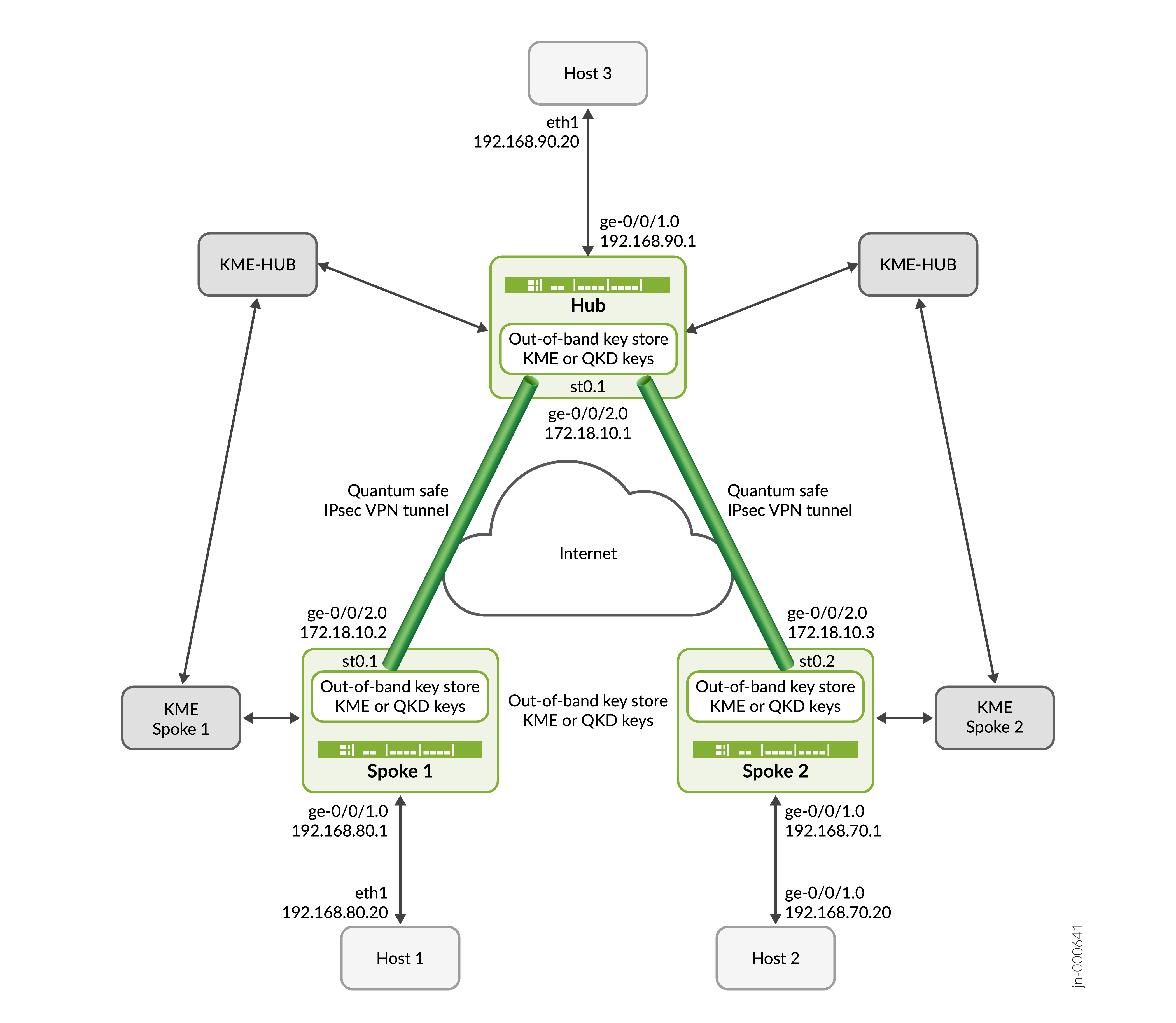
在 Hub 上进行分步配置
配置中枢接口。
[edit interfaces] user@hub# set ge-0/0/2 unit 0 family inet address 172.18.10.1/24 user@hub# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24 user@hub# set st0 unit 1 family inet
配置中心辐射型 IPsec VPN。这包括配置安全区域、安全策略和相关证书,以验证设备身份及其通信链路。
将集线器配置为从 CA 服务器获取 CA 证书,或从设备加载本地可用的 CA 证书。
注:KME 证书需要按照第三方供应商的说明进行配置。
配置 IPsec 提议和策略。为 IPsec VPN 配置 IKE 策略、提议和网关。
[edit security zones] user@hub# set security-zone untrust host-inbound-traffic system-services ike user@hub# set security-zone untrust interfaces ge-0/0/2.0 user@hub# set security-zone vpn interfaces st0.1 user@hub# set security-zone trust host-inbound-traffic system-services ping user@hub# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@hub# set from-zone trust to-zone vpn policy vpn_out match source-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match application any user@hub# set from-zone trust to-zone vpn policy vpn_out then permit user@hub# set from-zone vpn to-zone trust policy vpn_in match source-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match application any user@hub# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki] user@hub# set ca-profile Root-CA ca-identity Root-CA user@hub# set ca-profile Root-CA enrollment url url-to-CA-server user@hub# set ca-profile Root-CA revocation-check disable
user@hub> request security pki ca-certificate enroll ca-profile Root-CA
user@hub> request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa user@hub> request security pki local-certificate enroll certificate-id HUB_CRT challenge-password password domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA user@hub> request security pki local-certificate load certificate-id SAE_HUB filename SAE_HUB.cert key SAE_HUB.key
[edit security ike proposal] user@hub# set HUB_IKE_PROP authentication-method rsa-signatures user@hub# set HUB_IKE_PROP dh-group group14 user@hub# set HUB_IKE_PROP authentication-algorithm sha-256 user@hub# set HUB_IKE_PROP encryption-algorithm aes-256-cbc user@hub# set HUB_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@hub# set HUB_IKE_POL proposals HUB_IKE_PROP user@hub# set HUB_IKE_POL certificate local-certificate HUB_CRT
[edit security ike gateway] user@hub# set HUB_IKE_GW local-address 172.18.10.1 user@hub# set HUB_IKE_GW ike-policy HUB_IKE_POL user@hub# set HUB_IKE_GW external-interface ge-0/0/2.0 user@hub# set HUB_IKE_GW local-identity distinguished-name user@hub# set HUB_IKE_GW dynamic ike-user-type group-ike-id user@hub# set HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper user@hub# set HUB_IKE_GW version v2-only
[edit security ipsec proposal] user@hub# set HUB_IPSEC_PROP protocol esp user@hub# set HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@hub# set HUB_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec vpn] user@hub# set HUB_IPSEC_VPN bind-interface st0.1 user@hub# set HUB_IPSEC_VPN ike gateway HUB_IKE_GW user@hub# set HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL user@hub# set HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@hub# set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0
[edit security ipsec policy] user@hub# set HUB_IPSEC_POL proposals HUB_IPSEC_PROP
配置量子密钥管理器密钥配置文件,以从相应的 KME-Hub 设备检索量子密钥。
[edit security key-manager profiles] user@hub# set HUB_KM_PROFILE_1 quantum-key-manager url kme-server-urlset security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_HUB user@hub# set HUB_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_HUB_CERT user@hub# set HUB_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
将量子密钥管理器密钥配置文件绑定为 IKE 网关 ppk-profile,以使 VPN 隧道实现量子安全。
[edit security ike gateway] user@hub# set HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1
如果完成设备配置,请从配置模式输入 commit。
分支设备上的分步配置
配置分支接口。
[edit interfaces] user@spoke# set ge-0/0/2 unit 0 family inet address 172.18.10.2/24 user@spoke# set ge-0/0/1 unit 0 family inet address 192.168.80.1/24 user@spoke# set st0 unit 1 family inet
配置中心辐射型 IPsec VPN。这包括配置安全区域、安全策略和相关证书,以验证设备身份及其通信链路。
将集线器配置为从 CA 服务器获取 CA 证书,或从设备加载本地可用的 CA 证书。
注:KME 证书需要按照第三方供应商的说明进行配置。
配置 IPsec 提议和策略。为 IPsec VPN 配置 IKE 策略、提议和网关。
[edit security zones] user@spoke# set security-zone untrust host-inbound-traffic system-services ike user@spoke# set security-zone untrust interfaces ge-0/0/2.0 user@spoke# set security-zone vpn interfaces st0.1 user@spoke# set security-zone trust host-inbound-traffic system-services ping user@spoke# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@spoke# set from-zone trust to-zone vpn policy vpn_out match source-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match application any user@spoke# set from-zone trust to-zone vpn policy vpn_out then permit user@spoke# set from-zone vpn to-zone trust policy vpn_in match source-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match application any user@spoke# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki] user@spoke# set ca-profile Root-CA ca-identity Root-CA user@spoke# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@spoke# set ca-profile Root-CA revocation-check disable
user@spoke> request security pki ca-certificate enroll ca-profile Root-CA
user@spoke> request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa user@spoke> request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <password> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA user@spoke> request security pki local-certificate load certificate-id SAE_SPOKE_1 filename SAE_SPOKE_1.cert key SAE_SPOKE_1.key
[edit security ike proposal] user@spoke# set SPOKE_1_IKE_PROP authentication-method rsa-signatures user@spoke# set SPOKE_1_IKE_PROP dh-group group14 user@spoke# set SPOKE_1_IKE_PROP authentication-algorithm sha-256 user@spoke# set SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc user@spoke# set SPOKE_1_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@spoke# set SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP user@spoke# set SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW address 172.18.10.1 user@spoke# set SPOKE_1_IKE_GW local-address 172.18.10.2 user@spoke# set SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL user@spoke# set SPOKE_1_IKE_GW external-interface ge-0/0/2.0 user@spoke# set SPOKE_1_IKE_GW local-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW remote-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW version v2-only
[edit security ipsec proposal] user@spoke# set SPOKE_1_IPSEC_PROP protocol esp user@spoke# set SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@spoke# set SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec vpn] user@spoke# set SPOKE_1_IPSEC_VPN bind-interface st0.1 user@spoke# set SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW user@spoke# set SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24
[edit security ipsec policy] user@spoke# set SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP
配置量子密钥管理器密钥配置文件,以从相应的分支设备检索量子密钥。
[edit security key-manager profiles] user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_1-qkd-server.net user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_1 user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_1_CERT user@spoke# set profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
将量子密钥管理器密钥配置文件绑定为 IKE 网关 ppk-profile,以使 VPN 隧道实现量子安全。
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1
如果完成设备配置,请从配置模式输入 commit。
验证
本部分提供可用于验证此示例中的功能的 show 命令列表。
| 命令 | 验证任务 |
|---|---|
|
显示安全 IKE 安全关联详细信息 |
验证 IKE SA。 |
|
显示安全 IPsec 安全关联详细信息 |
验证 IPsec SA。 |
|
显示安全 IPsec 统计信息 |
验证 IPsec 加密和解密统计信息。 |
|
显示安全密钥管理器配置文件详细信息 |
验证密钥配置文件统计信息。 |
|
ping 192.168.90.20 源 192.168.80.20 计数 4 |
从主机 1 到主机 3 的 Ping。 |
|
ping 192.168.90.20 源 192.168.70.20 计数 4 |
从主机 2 到主机 3 的 Ping。 |
验证 IKE SA
目的
验证 IKE SA。
操作
在操作模式下,输入 show security ike security-associations detail 命令,以查看 IKE SA。
user@hub> show security ike security-associations detail
IKE peer 172.18.10.3, Index 2161, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: bccc74c70f0b81b9, Responder cookie: 872d364f15b29c28
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Lifetime: Expires in 3464 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2661
Output bytes : 2586
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500446
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
IKE peer 172.18.10.2, Index 2162, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 5e17d5924c619788, Responder cookie: 15f1e3c4252ba6f8
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 3464 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2645
Output bytes : 2586
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500447
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0 意义
示例输出确认 IKE SA。
验证 IPsec SA
目的
验证 IPsec SA。
操作
在操作模式下,输入 show security ipsec security-associations detail 命令,以查看 IPsec SA。
user@hub> show security ipsec security-associations detail
ID: 500446 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.3
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.70.0-192.168.70.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Fri Jul 21 2023 00:31:08: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0xcf48c0c9, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2778 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2161
Direction: outbound, SPI: 0x86c9ba76, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2778 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2161
ID: 500447 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.80.0-192.168.80.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Fri Jul 21 2023 00:31:08: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x4275d756, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2772 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2162
Direction: outbound, SPI: 0xe37b5568, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2772 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2162意义
示例输出确认 IPsec SA。
验证 IPsec 统计信息
目的
验证 IPsec 统计信息。
操作
在操作模式下,输入 show security ipsec statistics 命令,以查看 IPsec 统计信息。
user@hub> show security ipsec statistics ESP Statistics: Encrypted bytes: 1560 Decrypted bytes: 1560 Encrypted packets: 10 Decrypted packets: 10 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
意义
示例输出确认 IPsec 统计信息。
验证密钥管理器配置文件
目的
验证密钥管理器配置文件。
操作
在操作模式下,输入 show security key-manager profiles detail 命令并验证 Success 选项中的 Request stats 字段。
user@hub> show security key-manager profiles detail
Name: HUB_KM_PROFILE_1, Index: 6, Type: Quantum-key-manager
Configured-at: 21.07.23 (00:14:00)
Time-elapsed: 0 hrs 19 mins 24 secs
Url: https://kme.juniper.net:8080
Local-sae-id: SAE_HUB
Local-certificate-id: SAE_HUB_CERT
Trusted-cas: [ ROOT_CA_CERT ]
Peer-sae-ids: N/A
Default-key-size: N/A
Request stats:
Received: 2
In-progress: 0
Success: 2
Failed: 0
意义
示例输出确认量子密钥管理器配置文件。
从主机 1 到主机 3 的 Ping
目的
验证从主机 1 到主机 3 的连接。
操作
在操作模式下,输入 ping 192.168.90.20 source 192.168.80.20 count 5 命令以查看从主机 1 到主机 3 的连接。
user@host1# ping 192.168.90.20 source 192.168.80.20 count 5 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms 64 bytes from 192.168.90.20: icmp_seq=4 ttl=64 time=1.515 ms --- 192.168.90.20 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
意义
示例输出确认从主机 1 到主机 3 的连接。
从主机 2 到主机 3 的 Ping
目的
验证从主机 2 到主机 3 的连接。
操作
在操作模式下,输入 ping 192.168.90.20 source 192.168.80.20 count 5 命令,以查看从主机 2 到主机 3 的连接。
user@host2# ping 192.168.90.20 source 192.168.70.20 count 5 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms 64 bytes from 192.168.90.20: icmp_seq=4 ttl=64 time=1.759 ms --- 192.168.90.20 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
意义
示例输出确认从主机 2 到主机 3 的连接。
附录1:在所有设备上设置命令
在所有设备上设置命令输出。
在集线器上设置命令
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id HUB_CRT challenge-password <password> domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_HUB filename SAE_HUB.cert key SAE_HUB.key set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager url https://www.kme_hub-qkd-server.net set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_HUB set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_HUB_CERT set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal HUB_IKE_PROP authentication-method rsa-signatures set security ike proposal HUB_IKE_PROP dh-group group14 set security ike proposal HUB_IKE_PROP authentication-algorithm sha-256 set security ike proposal HUB_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal HUB_IKE_PROP lifetime-seconds 3600 set security ike policy HUB_IKE_POL proposals HUB_IKE_PROP set security ike policy HUB_IKE_POL certificate local-certificate HUB_CRT set security ike gateway HUB_IKE_GW local-address 172.18.10.1 set security ike gateway HUB_IKE_GW ike-policy HUB_IKE_POL set security ike gateway HUB_IKE_GW external-interface ge-0/0/2.0 set security ike gateway HUB_IKE_GW local-identity distinguished-name set security ike gateway HUB_IKE_GW dynamic ike-user-type group-ike-id set security ike gateway HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper set security ike gateway HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 set security ike gateway HUB_IKE_GW version v2-only set security ipsec proposal HUB_IPSEC_PROP protocol esp set security ipsec proposal HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal HUB_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP set security ipsec vpn HUB_IPSEC_VPN bind-interface st0.1 set security ipsec vpn HUB_IPSEC_VPN ike gateway HUB_IKE_GW set security ipsec vpn HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.1/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
在分支 1 上设置命令
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <password> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_SPOKE_1 filename SAE_SPOKE_1.cert key SAE_SPOKE_1.key set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_1-qkd-server.net set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_1 set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_1_CERT set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_1_IKE_PROP dh-group group14 set security ike proposal SPOKE_1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_1_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP set security ike policy SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT set security ike gateway SPOKE_1_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_1_IKE_GW local-address 172.18.10.2 set security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL set security ike gateway SPOKE_1_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_1_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 set security ike gateway SPOKE_1_IKE_GW version v2-only set security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP set security ipsec vpn SPOKE_1_IPSEC_VPN bind-interface st0.1 set security ipsec vpn SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW set security ipsec vpn SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.2/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
在分支 2 上设置命令
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_2_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_2_CRT challenge-password <password> domain-name spoke_2.juniper.net email spoke_2@juniper.net subject DC=juniper,CN=spoke_2.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_SPOKE_2 filename SAE_SPOKE_2.cert key SAE_SPOKE_2.key set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_2-qkd-server.net set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_2 set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_2_CERT set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_2_IKE_PROP dh-group group14 set security ike proposal SPOKE_2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_2_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_2_IKE_POL proposals SPOKE_IKE_PROP set security ike policy SPOKE_2_IKE_POL certificate local-certificate SPOKE_2_CRT set security ike gateway SPOKE_2_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_2_IKE_GW local-address 172.18.10.3 set security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL set security ike gateway SPOKE_2_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_2_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW ppk-profile SPOKE_2_KM_PROFILE_1 set security ike gateway SPOKE_2_IKE_GW version v2-only set security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_2_IPSEC_POL proposals SPOKE_2_IPSEC_PROP set security ipsec vpn SPOKE_2_IPSEC_VPN bind-interface st0.2 set security ipsec vpn SPOKE_2_IPSEC_VPN ike gateway SPOKE_2_IKE_GW set security ipsec vpn SPOKE_2_IPSEC_VPN ike ipsec-policy SPOKE_2_IPSEC_POL set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 local-ip 192.168.70.0/24 set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.3/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.70.1/24 set interfaces st0 unit 2 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.2 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
附录2:显示 DUT 上的配置输出
在 DUT 上显示命令输出。
枢纽
在配置模式下,输入show security pki ca-profile Root-CA、、show security key-manager、 show security ike policy HUB_IKE_POLshow security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security policies from-zone vpn to-zone trustshow security ike proposal HUB_IKE_PROPshow security ipsec proposal HUB_IPSEC_PROPshow interfacesshow security ike gateway HUB_IKE_GWshow security ipsec policy HUB_IPSEC_POLshow security ipsec vpn HUB_IPSEC_VPNshow security zones security-zone untrust和命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@hub# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@hub# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$7VNs4UDkPT3Hq9A01yrWLxNYoPfTz3924"; ## SECRET-DATA
key ascii-text "$9$RraElM7NbwgJ-VkPTFAtxNdws4GUHqmTaZ36AtOBwY24UHfTz9A0JGu1IhrlGDjHmTFn/9p0fT39p0hc-VwgGiPfzn9pJGqfQnpurev8xds2aDjqX7"; ## SECRET-DATA
}
}
HUB_KM_PROFILE_1 {
quantum-key-manager {
url https://www.kme_hub-qkd-server.net;
local-sae-id SAE_HUB;
local-certificate-id SAE_HUB_CERT;
trusted-cas Root-CA;
}
}
}
user@hub# show security ike proposal HUB_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@hub# show security ike policy HUB_IKE_POL
proposals HUB_IKE_PROP;
certificate {
local-certificate HUB_CRT;
}user@hub# show security ike gateway HUB_IKE_GW
ike-policy HUB_IKE_POL;
dynamic {
distinguished-name {
wildcard C=us,DC=juniper;
}
ike-user-type group-ike-id;
}
local-identity distinguished-name;
external-interface ge-0/0/2.0;
local-address 172.18.10.1;
version v2-only;
ppk-profile HUB_KM_PROFILE_1;
user@hub# show security ipsec proposal HUB_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@hub# show security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP;
user@hub# show security ipsec vpn HUB_IPSEC_VPN
bind-interface st0.1;
ike {
gateway HUB_IKE_GW;
ipsec-policy HUB_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 0.0.0.0/0;
}user@hub# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@hub# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@hub# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@hub# show security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@hub# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
st0 {
unit 1 {
family inet;
}
}辐条 1
在配置模式下,输入show security pki ca-profile Root-CA、、show security key-manager profiles SPOKE_1_KM_PROFILE_1、 show security ike policy SPOKE_1_IKE_POLshow security zones security-zone untrustshow security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security ike proposal SPOKE_1_IKE_PROPshow security ipsec proposal SPOKE_1_IPSEC_PROPshow security policies from-zone vpn to-zone trustshow security ike gateway SPOKE_1_IKE_GWshow security ipsec policy SPOKE_1_IPSEC_POLshow security ipsec vpn SPOKE_1_IPSEC_VPNshow interfaces和命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@spoke1# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@spoke1# show security key-manager profiles SPOKE_1_KM_PROFILE_1
quantum-key-manager {
url https://www.kme_spoke_1-qkd-server.net;
local-sae-id SAE_SPOKE_1;
local-certificate-id SAE_SPOKE_1_CERT;
trusted-cas Root-CA;
}user@spoke1# show security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke1# show security ike policy SPOKE_1_IKE_POL
proposals SPOKE_1_IKE_PROP;
certificate {
local-certificate SPOKE_1_CRT;
}user@spoke1# show security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.2; version v2-only; ppk-profile SPOKE_1_KM_PROFILE_1;
user@spoke1# show security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke1# show security ipsec vpn SPOKE_1_IPSEC_VPN
bind-interface st0.1;
ike {
gateway SPOKE_1_IKE_GW;
ipsec-policy SPOKE_1_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}user@spoke1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
st0 {
unit 1 {
family inet;
}
} user@spoke1# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@spoke1# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@spoke1# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@spoke1# security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}辐条 2
在配置模式下,输入show security pki ca-profile Root-CA、、show security key-manager profiles SPOKE_1_KM_PROFILE_1、 show security ike policy SPOKE_1_IKE_POLshow security zones security-zone untrustshow security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security ike proposal SPOKE_1_IKE_PROPshow security ipsec proposal SPOKE_1_IPSEC_PROPshow security policies from-zone vpn to-zone trustshow security ike gateway SPOKE_1_IKE_GWshow security ipsec policy SPOKE_1_IPSEC_POLshow security ipsec vpn SPOKE_1_IPSEC_VPNshow interfaces和命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
user@spoke2# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@spoke2# show security key-manager profiles SPOKE_2_KM_PROFILE_1
quantum-key-manager {
url https://www.kme_spoke_2-qkd-server.net;
local-sae-id SAE_SPOKE_2;
local-certificate-id SAE_SPOKE_2_CERT;
trusted-cas Root-CA;
}user@spoke2# show security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke2# show security ike policy SPOKE_2_IKE_POL
##
## Warning: Referenced proposal is not defined
##
proposals SPOKE_IKE_PROP;
certificate {
local-certificate SPOKE_2_CRT;
}
user@spoke2# show security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.3; version v2-only; ppk-profile SPOKE_2_KM_PROFILE_1;
user@spoke2# show security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke2# show security ipsec policy SPOKE_2_IPSEC_POL
proposals SPOKE_2_IPSEC_PROP;
[edit]
user@spoke2# show security ipsec vpn SPOKE_2_IPSEC_VPN
bind-interface st0.2;
ike {
gateway SPOKE_2_IKE_GW;
ipsec-policy SPOKE_2_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.70.0/24;
remote-ip 192.168.90.0/24;
}user@spoke2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}
user@spoke2# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@spoke2# show security zones security-zone vpn
interfaces {
st0.1;
st0.2;
}
user@spoke2# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@spoke2# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
user@spoke2# show security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}