使用 OCSP 配置 IPsec VPN 以实现证书吊销状态
此示例说明如何使用联机证书状态协议 (OCSP) 配置两个对等方,以检查 IPsec VPN 隧道第 1 阶段协商中使用的证书的吊销状态,从而提高安全性。
要求
在每台设备上:
获取并注册本地证书。这可以手动完成,也可以使用简单证书注册协议 (SCEP) 完成。
(可选)启用本地证书的自动续订。
配置安全策略以允许进出对等设备的流量。
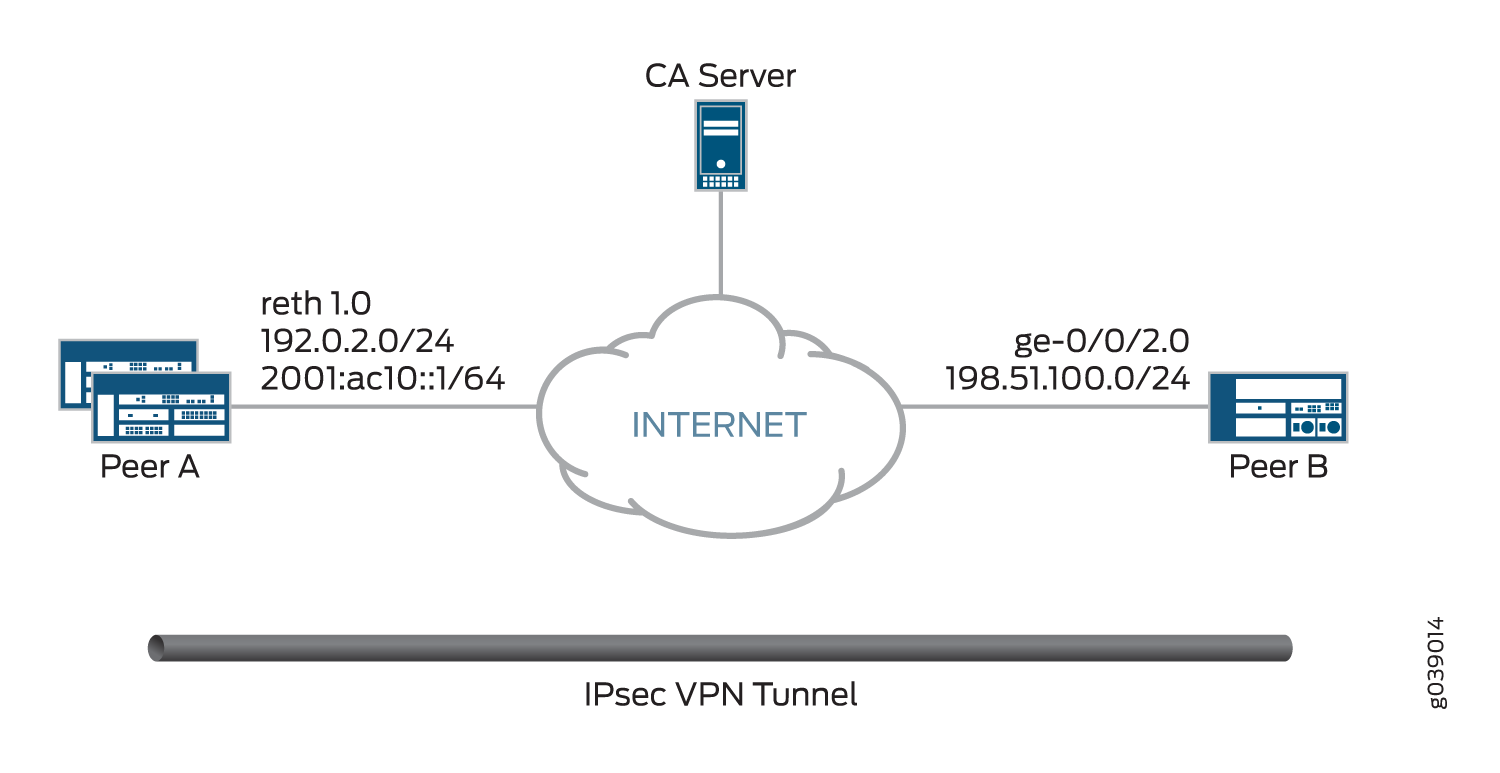
概述
在两个对等方上,证书颁发机构 (CA) 配置文件 OCSP-ROOT 配置了以下选项:
CA 名称为 OCSP-ROOT。
注册 URL 已 http://10.1.1.1:8080/scep/OCSP-ROOT/。这是向 CA 发送 SCEP 请求的 URL。
OCSP 服务器的 URL 已 http://10.157.88.56:8210/OCSP-ROOT/。
首先使用 OCSP 检查证书吊销状态。如果 OCSP 服务器没有响应,则使用证书吊销列表 (CRL) 检查状态。CRL 网址 http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45。
不会检查在 OCSP 响应中收到的 CA 证书是否有证书吊销。在 OCSP 响应中收到的证书通常具有较短的生存期,并且不需要吊销检查。
表 1 显示了此示例中使用的第 1 阶段选项。
选项 |
对等方 A |
对等方 B |
|---|---|---|
IKE 提案 |
ike_prop |
ike_prop |
身份验证方法 |
RSA 签名 |
RSA 签名 |
DH集团 |
group2 |
group2 |
身份验证算法 |
SHA 1 |
SHA 1 |
加密算法 |
3DES 全血细胞计数 |
3DES 全血细胞计数 |
IKE 策略 |
ike_policy |
ike_policy |
模式 |
积极 |
积极 |
提议 |
ike_prop |
ike_prop |
证书 |
local-certificate localcert1 |
local-certificate localcert1 |
IKE 网关 |
jsr_gateway |
jsr_gateway |
策略 |
ike_policy |
ike_policy |
网关地址 |
198.51.100.50 |
192.0.2.50 |
远程身份 |
localcert11.example.net |
- |
本地标识 |
- |
localcert11.example.net |
外部接口 |
RETH1 |
ge-0/0/2.0 |
版本 |
v2 |
v2 |
表 2 显示了此示例中使用的第 2 阶段选项。
选项 |
对等方 A |
对等方 B |
|---|---|---|
IPsec 提议 |
ipsec_prop |
ipsec_prop |
协议 |
ESP |
ESP |
身份验证算法 |
HMAC SHA1-96 |
HMAC SHA1-96 |
加密算法 |
3DES 全血细胞计数 |
3DES 全血细胞计数 |
生命周期秒数 |
1200 |
1200 |
生命周期千字节 |
150,000 |
150,000 |
IPsec 策略 |
ipsec_policy |
ipsec_policy |
PFC 按键 |
group2 |
group2 |
提议 |
ipsec_prop |
ipsec_prop |
VPN |
test_vpn |
test_vpn |
绑定接口 |
st0.1 |
st0.1 |
IKE 网关 |
jsr_gateway |
jsr_gateway |
策略 |
ipsec_policy |
ipsec_policy |
建立隧道 |
- |
马上 |
配置
配置对等方 A
CLI 快速配置
要快速配置 VPN 对等方 A 以使用 OCSP,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改任何必要的详细信息以匹配您的网络配置,将命令复制并粘贴到 [edit] 层次结构级别的 CLI 中,然后从配置模式进入 commit 。
set interfaces ge-0/0/3 gigether-options redundant-parent reth1 set interfaces ge-9/0/3 gigether-options redundant-parent reth1 set interfaces lo0 unit 0 family inet address 172.16.1.100/24 set interfaces lo0 redundant-pseudo-interface-options redundancy-group 1 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet address 192.0.2.50/24 set interfaces st0 unit 1 family inet address 172.18.1.100/24 set security pki ca-profile OCSP-ROOT ca-identity OCSP-ROOT set security pki ca-profile OCSP-ROOT enrollment url http://10.1.1.1:8080/scep/OCSP-ROOT/ set security pki ca-profile OCSP-ROOT revocation-check ocsp url http://10.157.88.56:8210/OCSP-ROOT/ set security pki ca-profile OCSP-ROOT revocation-check use-ocsp set security pki ca-profile OCSP-ROOT revocation-check ocsp disable-responder-revocation-check set security pki ca-profile OCSP-ROOT revocation-check ocsp connection-failure fallback-crl set security pki ca-profile OCSP-ROOT revocation-check crl url http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45 set security ike proposal ike_prop authentication-method rsa-signatures set security ike proposal ike_prop dh-group group2 set security ike proposal ike_prop authentication-algorithm sha1 set security ike proposal ike_prop encryption-algorithm 3des-cbc set security ike policy ike_policy mode aggressive set security ike policy ike_policy proposals ike_prop set security ike policy ike_policy certificate local-certificate localcert1 set security ike gateway jsr_gateway ike-policy ike_policy set security ike gateway jsr_gateway address 198.51.100.50 set security ike gateway jsr_gateway remote-identity hostname localcert11.example.net set security ike gateway jsr_gateway external-interface reth1 set security ike gateway jsr_gateway version v2-only set security ipsec proposal ipsec_prop protocol esp set security ipsec proposal ipsec_prop authentication-algorithm hmac-sha1-96 set security ipsec proposal ipsec_prop encryption-algorithm 3des-cbc set security ipsec proposal ipsec_prop lifetime-seconds 1200 set security ipsec proposal ipsec_prop lifetime-kilobytes 150000 set security ipsec policy ipsec_policy perfect-forward-secrecy keys group2 set security ipsec policy ipsec_policy proposals ipsec_prop set security ipsec vpn test_vpn bind-interface st0.1 set security ipsec vpn test_vpn ike gateway jsr_gateway set security ipsec vpn test_vpn ike ipsec-policy ipsec_policy
分步过程
下面的示例要求您在各个配置层级中进行导航。有关如何执行此操作的说明,请参阅 Junos OS CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要将 VPN 对等方 A 配置为使用 OCSP,请执行以下操作:
配置接口。
[edit interfaces] set ge-0/0/3 gigether-options redundant-parent reth1 set ge-9/0/3 gigether-options redundant-parent reth1 set lo0 unit 0 family inet address 172.16.1.100/24 set lo0 redundant-pseudo-interface-options redundancy-group 1 set reth1 redundant-ether-options redundancy-group 1 set reth1 unit 0 family inet address 192.0.2.0/24 set st0 unit 1 family inet address 172.18.1.100/24
配置 CA 配置文件。
[edit security pki ca-profile OCSP-ROOT] set ca-identity OCSP-ROOT set enrollment url http://10.1.1.1:8080/scep/OCSP-ROOT/ set revocation-check ocsp url http://10.157.88.56:8210/OCSP-ROOT/ set revocation-check use-ocsp set revocation-check ocsp disable-responder-revocation-check set revocation-check ocsp connection-failure fallback-crl set revocation-check crl url http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45
配置第 1 阶段选项。
[edit security ike proposal ike_prop] set authentication-method rsa-signatures set dh-group group2 set authentication-algorithm sha1 set encryption-algorithm 3des-cbc [edit security ike policy ike_policy] set mode aggressive set proposals ike_prop set certificate local-certificate localcert1 [edit security ike gateway jsr_gateway] set ike-policy ike_policy set address 198.51.100.50 set remote-identity hostname localcert11.example.net set external-interface reth1 set version v2-only
配置第 2 阶段选项。
[edit security ipsec proposal ipsec_prop] set protocol esp set authentication-algorithm hmac-sha1-96 set encryption-algorithm 3des-cbc set lifetime-seconds 1200 set lifetime-kilobytes 150000 [edit security ipsec policy ipsec_policy] set perfect-forward-secrecy keys group2 set proposals ipsec_prop [edit security ipsec vpn test_vpn] set bind-interface st0.1 set ike gateway jsr_gateway set ike ipsec-policy ipsec_policy
结果
在配置模式下,输入 show interfaces 、show security pki ca-profile OCSP-ROOT、show security ike 和 show security ipsec 命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/3 {
gigether-options {
redundant-parent reth1;
}
}
ge-9/0/3 {
gigether-options {
redundant-parent reth1;
}
}
lo0 {
unit 0 {
family inet {
address 172.16.1.100/24;
}
}
redundant-pseudo-interface-options {
redundancy-group 1;
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 192.0.2.0/24;
}
}
}
st0 {
unit 1 {
family inet {
address 172.18.1.100/24;
}
}
}
[edit]
user@host# show security pki ca-profile OCSP-ROOT
ca-identity OCSP-ROOT;
enrollment {
url http://10.1.1.1:8080/scep/OCSP-ROOT/;
}
revocation-check {
crl {
url http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45;
}
ocsp {
disable-responder-revocation-check;
url http://10.157.88.56:8210/OCSP-ROOT/;
}
use-ocsp;
}
[edit]
user@host# show security ike
proposal ike_prop {
authentication-method rsa-signatures;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
}
policy ike_policy {
mode aggressive;
proposals ike_prop;
certificate {
local-certificate localcert1;
}
}
gateway jsr_gateway {
ike-policy ike_policy;
address 10.10.2.50;
remote-identity hostname localcert11.example.net;
external-interface reth1;
version v2-only;
}
[edit]
user@host# show security ipsec
proposal ipsec_prop {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 1200;
lifetime-kilobytes 150000;
}
policy ipsec_policy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec_prop;
}
vpn test_vpn {
bind-interface st0.1;
ike {
gateway jsr_gateway;
ipsec-policy ipsec_policy;
}
}
如果完成设备配置,请从配置模式输入 commit。
配置对等方 B
CLI 快速配置
要快速配置 VPN 对等方 B 以使用 OCSP,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改任何必要的详细信息以匹配您的网络配置,将命令复制并粘贴到 [edit] 层次结构级别的 CLI 中,然后从配置模式进入 commit 。
set interfaces ge-0/0/2 unit 0 family inet address 198.51.100.0/24 set interfaces lo0 unit 0 family inet address 172.17.1.100/24 set interfaces st0 unit 1 family inet address 172.18.1.1/24 set security pki ca-profile OCSP-ROOT ca-identity OCSP-ROOT set security pki ca-profile OCSP-ROOT enrollment url http://10.1.1.1:8080/scep/OCSP-ROOT/ set security pki ca-profile OCSP-ROOT revocation-check ocsp url http://10.157.88.56:8210/OCSP-ROOT/ set security pki ca-profile OCSP-ROOT revocation-check use-ocsp set security pki ca-profile OCSP-ROOT revocation-check ocsp disable-responder-revocation-check set security pki ca-profile OCSP-ROOT revocation-check ocsp connection-failure fallback-crl set security pki ca-profile OCSP-ROOT revocation-check crl url http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45 set security ike proposal ike_prop authentication-method rsa-signatures set security ike proposal ike_prop dh-group group2 set security ike proposal ike_prop authentication-algorithm sha1 set security ike proposal ike_prop encryption-algorithm 3des-cbc set security ike policy ike_policy mode aggressive set security ike policy ike_policy proposals ike_prop set security ike policy ike_policy certificate local-certificate localcert11 set security ike gateway jsr_gateway ike-policy ike_policy set security ike gateway jsr_gateway address 192.0.2.50 set security ike gateway jsr_gateway local-identity hostname localcert11.example.net set security ike gateway jsr_gateway external-interface ge-0/0/2.0 set security ike gateway jsr_gateway version v2-only set security ipsec proposal ipsec_prop protocol esp set security ipsec proposal ipsec_prop authentication-algorithm hmac-sha1-96 set security ipsec proposal ipsec_prop encryption-algorithm 3des-cbc set security ipsec proposal ipsec_prop lifetime-seconds 1200 set security ipsec proposal ipsec_prop lifetime-kilobytes 150000 set security ipsec policy ipsec_policy perfect-forward-secrecy keys group2 set security ipsec policy ipsec_policy proposals ipsec_prop set security ipsec vpn test_vpn bind-interface st0.1 set security ipsec vpn test_vpn ike gateway jsr_gateway set security ipsec vpn test_vpn ike ipsec-policy ipsec_policy set security ipsec vpn test_vpn establish-tunnels immediately
分步过程
下面的示例要求您在各个配置层级中进行导航。有关如何执行此操作的说明,请参阅 Junos OS CLI 用户指南中的在配置模式下使用 CLI 编辑器。
要将 VPN 对等方 B 配置为使用 OCSP,请执行以下操作:
配置接口。
[edit interfaces] set ge-0/0/2 unit 0 family inet address 198.51.100.0/24 set lo0 unit 0 family inet address 172.17.1.100/24 set st0 unit 1 family inet address 172.18.1.1/24
配置 CA 配置文件。
[edit security pki ca-profile OCSP-ROOT] set ca-identity OCSP-ROOT set enrollment url http://10.1.1.1:8080/scep/OCSP-ROOT/ set revocation-check ocsp url http://10.157.88.56:8210/OCSP-ROOT/ set revocation-check use-ocsp set revocation-check ocsp disable-responder-revocation-check set revocation-check ocsp connection-failure fallback-crl set revocation-check crl url http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45
配置第 1 阶段选项。
[edit security ike proposal ike_prop] set authentication-method rsa-signatures set dh-group group2 set authentication-algorithm sha1 set encryption-algorithm 3des-cbc [edit security ike policy ike_policy] set mode aggressive set proposals ike_prop set certificate local-certificate localcert1 [edit security ike gateway jsr_gateway] set ike-policy ike_policy set address 192.0.2.50 set local-identity hostname localcert11.example.net set external-interface ge-0/0/2.0 set version v2-only
配置第 2 阶段选项。
[edit security ipsec proposal ipsec_prop] set protocol esp set authentication-algorithm hmac-sha1-96 set encryption-algorithm 3des-cbc set lifetime-seconds 1200 set lifetime-kilobytes 150000 [edit security ipsec policy ipsec_policy] set perfect-forward-secrecy keys group2 set proposals ipsec_prop [edit security ipsec vpn test_vpn] set bind-interface st0.1 set ike gateway jsr_gateway set ike ipsec-policy ipsec_policy set establish-tunnels immediately
结果
在配置模式下,输入 show interfaces 、show security pki ca-profile OCSP-ROOT、show security ike 和 show security ipsec 命令,以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明,以便进行更正。
[edit]
user@host# show interfaces
ge-0/0/2 {
unit 0 {
family inet {
address 198.51.100.0/24;
}
}
}
lo0 {
unit 0 {
family inet {
address 172.17.1.100/24;
}
}
}
st0 {
unit 1 {
family inet {
address 172.18.1.1/24;
}
}
}
[edit]
user@host# show security pki ca-profile OCSP-ROOT
ca-identity OCSP-ROOT;
enrollment {
url http://10.1.1.1:8080/scep/OCSP-ROOT/;
}
revocation-check {
crl {
url http://10.1.1.1:8080/crl-as-der/currentcrl-45.crlid=45;
}
ocsp {
disable-responder-revocation-check;
url http://10.157.88.56:8210/OCSP-ROOT/;
}
use-ocsp;
}
[edit]
user@host# show security ike
proposal ike_prop {
authentication-method rsa-signatures;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm 3des-cbc;
}
policy ike_policy {
mode aggressive;
proposals ike_prop;
certificate {
local-certificate localcert11;
}
}
gateway jsr_gateway {
ike-policy ike_policy;
address 192.0.2.50;
local-identity hostname localcert11.example.net;
external-interface ge-0/0/2.0;
version v2-only;
}
[edit]
user@host# show security ipsec
proposal ipsec_prop {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 1200;
lifetime-kilobytes 150000;
}
policy ipsec_policy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec_prop;
}
vpn test_vpn {
bind-interface st0.1;
ike {
gateway jsr_gateway;
ipsec-policy ipsec_policy;
}
establish-tunnels immediately;
}
如果完成设备配置,请从配置模式输入 commit。
验证
确认配置工作正常。
验证 CA 证书
目的
验证每个对等设备上 CA 证书的有效性。
操作
在操作模式下,输入 show security pki ca-certificate ca-profile OCSP-ROOT 或 show security pki ca-certificate ca-profile OCSP-ROOT detail 命令。
user@host> show security pki ca-certificate ca-profile OCSP-ROOT
Certificate identifier: OCSP-ROOT
Issued to: OCSP-ROOT, Issued by: C = US, O = example, CN = OCSP-ROOT
Validity:
Not before: 11-15-2013 22:26 UTC
Not after: 11-14-2016 22:26 UTC
Public key algorithm: rsaEncryption(2048 bits)
user@host> show security pki ca-certificate ca-profile OCSP-ROOT detail
Certificate identifier: OCSP-ROOT
Certificate version: 3
Serial number: 0000a17f
Issuer:
Organization: example, Country: US, Common name: OCSP-ROOT
Subject:
Organization: example, Country: US, Common name: OCSP-ROOT
Subject string:
C=US, O=example, CN=OCSP-ROOT
Validity:
Not before: 11-15-2013 22:26 UTC
Not after: 11-14-2016 22:26 UTC
Public key algorithm: rsaEncryption(2048 bits)
30:82:01:0a:02:82:01:01:00:c6:38:e9:03:69:5e:45:d8:a3:ea:3d
2e:e3:b8:3f:f0:5b:39:f0:b7:35:64:ed:60:a0:ba:89:28:63:29:e7
27:82:47:c4:f6:41:53:c8:97:d7:1e:3c:ca:f0:a0:b9:09:0e:3d:f8
76:5b:10:6f:b5:f8:ef:c5:e8:48:b9:fe:46:a3:c6:ba:b5:05:de:2d
91:ce:20:12:8f:55:3c:a6:a4:99:bb:91:cf:05:5c:89:d3:a7:dc:a4
d1:46:f2:dc:36:f3:f0:b5:fd:1d:18:f2:e6:33:d3:38:bb:44:8a:19
ad:e0:b1:1a:15:c3:56:07:f9:2d:f6:19:f7:cd:80:cf:61:de:58:b8
a3:f5:e0:d1:a3:3a:19:99:80:b0:63:03:1f:25:05:cc:b2:0c:cd:18
ef:37:37:46:91:20:04:bc:a3:4a:44:a9:85:3b:50:33:76:45:d9:ba
26:3a:3b:0d:ff:82:40:36:64:4e:ea:6a:d8:9b:06:ff:3f:e2:c4:a6
76:ee:8b:58:56:a6:09:d3:4e:08:b0:64:60:75:f3:e2:06:91:64:73
d2:78:e9:7a:cb:8c:57:0e:d1:9a:6d:3a:4a:9e:5b:d9:e4:a2:ef:31
5d:2b:2b:53:ab:a1:ad:45:49:fd:a5:e0:8b:4e:0b:71:52:ca:6b:fa
8b:0e:2c:7c:7b:02:03:01:00:01
Signature algorithm: sha1WithRSAEncryption
Distribution CRL:
http://10.1.1.1:8080/crl-as-der/currentcrl-45.crl?id=45
Authority Information Access OCSP:
http://10.1.1.1:8090/OCSP-ROOT/
Use for key: CRL signing, Certificate signing, Key encipherment, Digital signature
Fingerprint:
ed:ce:ec:13:1a:d2:ab:0a:76:e5:26:6d:2c:29:5d:49:90:57:f9:41 (sha1)
af:87:07:69:f0:3e:f7:c6:b8:2c:f8:df:0b:ae:b0:28 (md5)
在此示例中,IP 地址用于 CA 配置文件配置中的 URL。如果 IP 地址未与 CA 颁发的证书或 CA 证书一起使用,则必须在设备的配置中配置 DNS。DNS 必须能够在分发 CRL 和 CA 配置文件配置中的 CA URL 中解析主机。此外,您必须具有对同一主机的网络可访问性才能接收吊销检查。
意义
输出显示每个对等方上 CA 证书的详细信息和有效性,如下所示:
C—国家。O——组织。CN- 通用名。Not before- 生效的开始日期。Not after- 有效期结束日期。
验证本地证书
目的
验证每个对等设备上本地证书的有效性。
操作
在操作模式下,输入 show security pki local-certificate certificate-id localcert1 detail 命令。
user@host> show security pki local-certificate certificate-id localcert1 detail
Certificate identifier: localcert1
Certificate version: 3
Serial number: 013e3f1d
Issuer:
Organization: example, Country: US, Common name: OCSP-ROOT
Subject:
Organization: example, Organizational unit: example, State: california1, Locality: sunnyvale1, Common name: localcert1, Domain component: domain_component1
Subject string:
DC=domain_component1, CN=localcert1, OU=example, O=example, L=sunnyvale1, ST=california1, C=us1
Alternate subject: "localcert1@example.net", localcert1.example.net, 10.10.1.50
Validity:
Not before: 01-28-2014 22:23 UTC
Not after: 03-29-2014 22:53 UTC
Public key algorithm: rsaEncryption(1024 bits)
30:81:89:02:81:81:00:a6:df:c1:57:59:f8:4d:0f:c4:a8:96:25:97
03:c4:a0:fb:df:d5:f3:d5:56:b6:5a:26:65:b8:1a:ec:be:f6:c6:5f
b3:d7:d3:59:39:48:52:4a:e3:1b:e4:e0:6d:24:c3:c1:50:8c:55:3b
c0:c1:29:a0:45:29:8e:ec:3e:52:2f:84:b3:e8:89:9a:0f:8b:7d:e8
90:4b:c1:28:48:95:b3:aa:11:ab:b4:8c:a8:80:ce:90:07:2a:13:a2
2f:84:44:92:3b:be:7d:39:5b:2f:9a:4c:7a:2f:2d:31:8b:12:6d:52
34:7d:6b:e4:69:7e:f3:86:55:e2:89:31:98:c9:15:02:03:01:00:01
Signature algorithm: sha1WithRSAEncryption
Distribution CRL:
http://10.1.1.1:8080/crl-as-der/currentcrl-45.crl?id=45
Authority Information Access OCSP:
http://10.1.1.1/:8090/OCSP-ROOT/
Fingerprint:
00:c6:56:64:ad:e3:ce:8e:26:6b:df:17:1e:de:fc:14:a4:bb:8c:e4 (sha1)
7f:43:c6:ed:e4:b3:7a:4f:9a:8c:0b:61:95:01:c9:52 (md5)
Auto-re-enrollment:
Status: Disabled
Next trigger time: Timer not started
意义
输出显示每个对等方上本地证书的详细信息和有效性,如下所示:
DC- 域组件。CN- 通用名。OU- 组织单位。O——组织。L- 产地ST—状态。C—国家。Not before- 生效的开始日期。Not after- 有效期结束日期。
验证 IKE 第 1 阶段状态
目的
验证每个对等设备上的 IKE 第 1 阶段状态。
操作
在操作模式下,输入 show security ike security-associations 命令。
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 6534660 UP 3e62e05abd6a703f c552b238e8a26668 IKEv2 198.51.100.50
在操作模式下,输入 show security ike security-associations detail 命令。
user@host> show security ike security-associations detail
IKE peer 198.51.100.50, Index 6534660, Gateway Name: jsr_gateway
Role: Responder, State: UP
Initiator cookie: 3e62e05abd6a703f, Responder cookie: c552b238e8a26668
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 192.0.2.50:500, Remote: 198.51.100.50:500
Lifetime: Expires in 26906 seconds
Peer ike-id: localcert11.example.net
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : 3des-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-2
Traffic statistics:
Input bytes : 2152
Output bytes : 2097
Input packets: 4
Output packets: 4
Flags: IKE SA is created
IPSec security associations: 4 created, 0 deleted
Phase 2 negotiations in progress: 0
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 192.0.2.50:500, Remote: 198.51.100.50:500
Local identity: 192.0.2.50
Remote identity: localcert11.example.net
Flags: IKE SA is created
意义
flags输出中的字段显示已创建 IKE 安全关联。
验证 IPsec 第 2 阶段状态
目的
验证每个对等设备上的 IPsec 第 2 阶段状态。
操作
在操作模式下,输入 show security ipsec security-associations 命令。
user@host> show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <131073 ESP:3des/sha1 9d1066e2 252/ 150000 - root 500 198.51.100.50 >131073 ESP:3des/sha1 82079c2c 252/ 150000 - root 500 198.51.100.50
在操作模式下,输入 show security ipsec security-associations detail 命令。
user@host> show security ipsec security-associations detail
ID: 131073 Virtual-system: root, VPN Name: test_vpn
Local Gateway: 192.0.2.50, Remote Gateway: 198.51.100.50
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear
Bind-interface: st0.1
Port: 500, Nego#: 2, Fail#: 0, Def-Del#: 0 Flag: 0x600a29
Last Tunnel Down Reason: Delete payload received
Direction: inbound, SPI: 9d1066e2, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 249 seconds
Lifesize Remaining: 150000 kilobytes
Soft lifetime: Expires in 10 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 82079c2c, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 249 seconds
Lifesize Remaining: 150000 kilobytes
Soft lifetime: Expires in 10 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Anti-replay service: counter-based enabled, Replay window size: 64意义
输出显示 ipsec 安全关联详细信息。