vSRX Virtual Firewall Datasheet
Download DatasheetProduct Overview
The vSRX Virtual Firewall delivers a complete virtual firewall solution, including advanced security, robust networking, and automated virtual machine life cycle management capabilities for service providers and enterprises. The vSRX empowers security professionals to deploy and scale firewall protection in highly dynamic environments.

Product Description
Data centers increasingly rely on server virtualization to deliver services faster and more efficiently than ever before. The virtualized data center, however, introduces new challenges that require additional security considerations beyond those needed to secure physical assets.
Virtual machines (VM) can be highly dynamic and elastic in a virtualized data center, with frequent additions, moves, and changes. These frequent changes complicate the ability to attach security policies to a VM instantiation and track security policies with VM movement to ensure continued regulatory compliance. In short, the dynamic and flexible nature of virtualization can easily lead to a loss of visibility and control.
Network and security professionals must perform a delicate balancing act, delivering the benefits of virtualization and cloud technologies without undermining the organization's security. This challenge can only be met by a security solution that can keep pace with evolving threats while matching the agility and scalability of virtualized and cloud environments—without sacrificing reliability, visibility, and control.
Juniper addresses these challenges head‑on by extending the capabilities of the award‑winning Juniper Networks® SRX Series Firewalls to the virtual world with the vSRX Virtual Firewall. They make security easy by securing the cloud at every level—between applications, instances, and across environments.
Powered by Juniper’s industry‑leading Junos® operating system, the vSRX delivers a complete and integrated virtual security solution, including L4‑L7 advanced security services, robust networking, and automated life cycle management capabilities for service providers and enterprises alike.
The vSRX’s automated provisioning capabilities allow network and security administrators to quickly and efficiently provision and scale firewall protection to meet the dynamic needs of virtualized and cloud environments. By combining the vSRX with the power of Junos Space® Security Director, administrators can significantly improve policy configuration, management, and visibility into both physical and virtual assets from a standard, centralized platform.
For service providers and organizations deploying service-oriented applications in software, the vSRX’s portfolio of virtualized network and security services supports a variety of Network Functions Virtualization (NFV) use cases. The vSRX also supports Juniper Networks Contrail, OpenContrail, and other third‑party solutions. It can also be integrated with other next‑generation cloud orchestration tools, such as OpenStack, either directly or through rich APIs.
| Feature | Feature Description | Benefits |
| Antivirus |
|
|
| Web filtering |
|
|
| Content filtering |
|
|
| Antispam |
|
|
Architecture and Key Components
Advanced Security Services
Implementing nonintegrated, legacy systems built around traditional firewalls and individual standalone appliances and software is no longer adequate to protect against today’s sophisticated attacks. Juniper’s advanced security suite enables users to deploy multiple technologies to meet the unique and evolving needs of modern organizations and the continually changing threat landscape. Real‑time updates ensure that the technologies, policies, and other security measures are always current.
Through Juniper Networks AppSecure, the vSRX delivers a versatile and powerful set of advanced security services, including content security, intrusion detection and prevention (IDP/IPS), and application control and visibility services.
Content Security
The vSRX includes comprehensive content security against malware, viruses, phishing attacks, intrusions, spam, and other threats with best-in-class antivirus, antispam, web filtering, and content filtering features (see Table 1).
Intrusion Prevention System (IPS)
IPS for vSRX controls access to IT networks to protect systems from attack by inspecting data and taking actions such as blocking attacks as they are developing—and before they succeed—or creating a series of rules in the firewall. IPS tightly integrates Juniper’s applications security features with the network infrastructure to further mitigate threats and protect against a wide range of attacks and vulnerabilities (see Table 2).
EVPN-VXLAN
All Juniper SRX Series Firewalls support EVPN‑VXLAN Type 5 configuration so that security is embedded automatically across the entire EVPN‑VXLAN fabric. As a result, customers can extend their workloads and securely connect from on‑premises to public clouds and on‑premises to on‑premises (Date Center Interconnectivity).
When policy enforcement points are embedded into the data center fabric, the network becomes truly threat aware and security controls are composable like the rest of the network. Natively speaking EVPN/VXLAN enables the vSRX to be fully fabric aware, which means the technical contexts defined by the network engineering team such as tenant, virtual routing and forwarding, VNIs, and others are shared with vSRX, so security teams understand how the network is set up and segmented. Changes made to the network are automatically propagated via standard protocols, eliminating manual intervention. Complete fabric awareness enables security operators to respond to threats faster and minimize the blast radius.
By offering both routing and security in a single virtualized network function, businesses can leverage the simplified and extended EVPN‑VXLAN fabric design to rollout security services faster and logically separate customers.
| Feature | Feature Description | Benefits |
| Stateful signature inspection | Signatures are applied only to relevant portions of the network traffic determined by the appropriate protocol context. | Minimizes false positives and offers flexible signature development. |
| Protocol decodes | More than 65 protocol decodes are supported, along with more than 500 contexts to ensure proper protocol usage. | Improves signature accuracy through the precise context of protocols. |
| Signatures | There are more than 15,000 signatures for identifying anomalies, attacks, spyware, and applications. | Attacks are accurately identified and attempts to exploit known vulnerabilities are detected. |
| Traffic normalization | Reassembly, normalization, and protocol decoding are provided. | System overcomes attempts to bypass other IPS detections by using obfuscation methods. |
| Fast signature creation | Protocol anomaly detection and same day coverage for newly found vulnerabilities is provided. | Protects networks against any new exploits. |
| Recommended policy | The Juniper Security Team identifies attack signatures as critical for the typical enterprise. | Installation and maintenance are simplified while ensuring the highest network security. |
| Active/active traffic monitoring | IPS monitoring includes active/active vSRX chassis clusters. | Support included for active/active IPS monitoring. |
| Packet capture | IPS policy supports packet capture logging per rule. | Users can conduct further analysis of surrounding traffic and determine additional steps to protect the target. |
| Feature | Description | Benefit |
| AppTrack | Analyzes application data and classifies it based on risk level, zones, source, and destination addresses. | Tracks application usage to identify high-risk applications and analyze traffic patterns, improving network management and control. |
| AppFW | Creates application control policies to allow or deny traffic based on dynamic application or group names. | Enhances security policy creation and enforcement based on applications rather than traditional port and protocol analysis. |
| AppQoS | Meters and marks traffic based on the application security policies set by the administrator. | Prioritizes traffic and limits and shapes bandwidth based on application information and context to improve overall performance. |
Application Visibility and Control with AppSecure
AppSecure is a next-generation application security suite for vSRX and SRX Series Firewalls that delivers threat visibility, protection, enforcement, and control.
Whether needing to understand how many users are accessing cloud-based applications like Facebook every day or needing to know what applications are using the most bandwidth, AppSecure delivers powerful visibility and ongoing application tracking. With open signatures, unique application sets can be monitored, measured, and controlled to tie closely to the organization’s business priorities.
Juniper Advanced Threat Prevention
Juniper Advanced Threat Prevention integrates with the vSRX to provide dynamic, automated protection against known malware and advanced zero-day threats, resulting in instantaneous responses (see Table 4).
Security policies determine if a session can originate in one zone and be forwarded to another zone. The vSRX receives packets and keeps track of every session, every application, and every user. As a VM moves within a virtualized or cloud environment, it will still send packets to the vSRX for processing—continuously communicating in a secure mode.
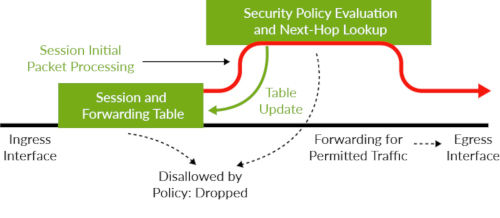
Figure 1: vSRX session-based forwarding algorithm
High Availability (HA)
The vSRX provides mission‑critical reliability, supporting chassis clustering for active/active and active/passive modes. The HA functionality provides full stateful failover for any connections processed and for cluster members to span hypervisors. When configured in a cluster, vSRX VMs synchronize the connection/session state and flow information with IPsec security associations, Network Address Translation (NAT) traffic, address book information, configuration changes, and more. As a result, not only is the session preserved during failover, but security is also kept intact. In an unstable network, vSRX also mitigates link flapping.
Juniper Secure Connect
Juniper Secure Connect is a highly flexible SSL VPN application that provides secure access to corporate and cloud resources for employees working away from protected resources. Juniper Secure Connect is available for desktop and mobile devices including Windows, Mac OS, Android, and iOS. When combined with the SRX Series Firewalls, Secure Connect helps organizations achieve dynamic, flexible, and adaptable connectivity to any device anywhere, reducing risk by extending visibility and enforcement from users to cloud.
| Features | Benefits |
| Deep inspection and analysis | Extracts compromised files and sends them to the cloud to rapidly identify known threats or deep-level file analysis that looks for particularly evasive malware. |
| Instant identification to block attacks | Instantly identifies and communicates detected malware to SRX Series Firewalls to block attacks. |
| Web-based portal with rich reporting and analytics tools | Provides a web-based interface for performing management tasks such as configuration and product updates. It also offers a rich set of reporting and analytics tools that provide visibility into threats and compromised hosts. |
| Quarantine of systems and hosts | Allows administrators and security staff to analyze and correlate data, identifying compromised systems and feeding the information to SRX Series Firewalls to quarantine those systems. |
| SecIntel | Provides dynamic threat intelligence feeds that cascade threat information to SRX Series Firewalls for immediate action. |
| AI-Predictive Threat Prevention | Keeps known and zero-day threats off the network at line rate for the entire attack lifecycle—not just for 24 hours—helping keep your network safe from initial and subsequent attacks. |
| Command and control (C&C) data | Provides C&C data to the SRX Series Firewalls, preventing compromised internal systems from communicating with these devices. |
| Email analysis and remediation | Isolates and quarantines malicious malware, preventing email from being used as an attack vector. Machine learning algorithms analyze email traffic, detect malicious attachments, and block files at the firewall. |
| Threat intelligence | Uses powerful open APIs for seamless integration with third-party vendors, providing multiple threat intelligence feeds and reducing the attack surface. |
| Encrypted Traffic Insights | Restores visibility into traffic lost due to encryption without the heavy burden of full TLS/SSL decryption. |
| Adaptive Threat Profiling | Enables a quicker response time to combat the continuous onslaught of new threats. Organizations can use ATP Cloud’s Adaptive Threat Profiling to automatically create security intelligence threat feeds based on who and what is currently attacking the network. |
| 1 All performance numbers are “up to” and depend on the underlying hardware configuration (some server configurations may perform better). Performance, capacity and features listed are based on vSRX running Junos OS 23.1R1 release and are measured under ideal testing conditions. Actual results may vary based on Junos OS releases and by deployments | ||||||||
| 2 Throughput numbers measured based on HTTP traffic with 64KB transaction size and Connections per second methodology | ||||||||
| 3 Maximum concurrent sessions can be increased based on the memory allocation for the vSRX. For more information, visit https://www.juniper.net/documentation/product/us/en/vsrx/ | ||||||||
| Performance and Capacity1 | VMware | KVM | ||||||
| vCPUs | 2 | 5 | 9 | 17 | 2 | 5 | 9 | 17 |
| Memory | 4 GB | 8 GB | 16 GB | 32/64 GB | 4 GB | 8 GB | 16 GB | 32/64 GB |
| Firewall throughput, large packet (1514B) | 16.6 Gbps | 51.6 Gbps | 121.8 Gbps | 200 Gbps | 17.8 Gbps | 51.5 Gbps | 128.8 Gbps | 200 Gbps |
| Firewall throughput, IMIX | 4 Gbps | 12.8 Gbps | 31.1 Gbps | 56 Gbps | 4.1 Gbps | 13 Gbps | 33.6 Gbps | 55.3 Gbps |
| AES+GCM IPSec VPN throughput (1420B) | 7.9 Gbps | 30.1 Gbps | 53.5 Gbps | 91 Gbps | 6.2 Gbps | 17 Gbps | 51.1 Gbps | 82.3 Gbps |
| Application visibility and control2 | 5.1 Gbps | 10.8 Gbps | 27.5 Gbps | 50.2 Gbps | 6.9 Gbps | 21.8 Gbps | 52.9 Gbps | 88 Gbps |
| IPS recommended signatures | 1.9 Gbps | 5.5 Gbps | 15.5 Gbps | 28.8 Gbps | 2.9 Gbps | 6.6 Gbps | 19.8 Gbps | 36.2 Gbps |
| TCP connections per second | 30,000 | 100,000 | 315,000 | 585,000 | 41,000 | 135,000 | 336,000 | 580,000 |
| Maximum concurrent sessions3 | 512,000 | 2M | 4M | 12/28M | 512,000 | 2M | 4M | 12/28M |
| Number of remote access/SSL VPN (concurrent) users | 500 | 500 | 500 | 500 | 500 | 500 | 500 | 500 |
Performance
Traditionally, customers have had to choose between scalability and performance. Juniper’s vSRX solution is optimized to leverage multiple virtual CPUs to maximize packet processing and overall throughput in the virtual environment. Each vSRX VM also has multiple virtual network interface cards (vNICs) that can be connected to various virtual networks to simultaneously protect multiple network segments. The vSRX operates from within the virtual fabric, providing the best of both worlds—strong security with the performance needed to support a virtualized or cloud‑based environment.
Leveraging the Software Receive Side Scaling implementation, the vSRX provides additional cores* beyond the minimum two vCPU, up to a maximum of 32 vCPUs, to the same instance without having to certify a new instance image. By using 17 vCPUs from a single socket, the vSRX can achieve up to 98 Gbps performance.
| Virtual CPU Cores | Memory (GB) | Supported NIC Types |
| 2 | 4, 8, 16, 20, 32 | VMXNET3, VIRTIO, 82599 SR-IOV, ICE / I40E SR-IOV |
| 5 | 8, 16, 20, 32 | VMXNET3, VIRTIO, 82599 SR-IOV, ICE / I40E SR-IOV |
| 9 | 16, 32, 50, 64 | ICE / I40E SR-IOV |
| 17 | 32, 50, 64 | ICE / I40E SR-IOV |
| 32 | 64 | ICE / I40E SR-IOV |
Junos Space Security Director
Junos Space Security Director provides security policy management through an intuitive and centralized web-based interface that offers enforcement across emerging and traditional risk vectors. As an application on the Junos Space platform, Security Director provides extensive security scale, granular policy control, and policy breadth across the network. It helps administrators quickly manage all phases of security policy life cycle for stateful firewall, content security, IPS, AppFW, VPN, and NAT.
Unified Management
Leveraging the power of Junos Space Security Director, administrators can significantly improve policy configuration, management, and visibility into both physical and virtual assets from one common, centralized platform.
Key Features and Benefits
- Secures multitenant private and public cloud environments by delivering a complete firewall with stateful packet processing and application-layer gateway features in a virtual machine format
- Leverages the same, consistent, advanced security and networking features (IPsec VPN, NAT, QoS, and full routing capabilities) of the SRX Series Firewalls
- Defends against an increasingly sophisticated threat landscape by integrating robust content security, IPS, and application visibility and control capabilities for a comprehensive threat management framework
- Improves management flexibility with open RESTful APIs to support integration with third-party management and cloud orchestration tools
- Expands visibility into and control over firewall security policy configuration and management across virtual and non-virtual environments with Junos Space Security Director
- Supports SDN and NFV via integration with Contrail, OpenContrail, and other third-party solutions
Juniper Mist WAN Assurance and AI-Native Operations
Alternatively, vSRX can be operated and orchestrated through the Juniper Mist Cloud. Mist AI delivers unprecedented automation using a combination of artificial intelligence, machine learning algorithms, and data science techniques to save time, maximize IT productivity, and deliver the best experience to digital users.
Juniper Mist WAN Assurance is built on the Juniper Mist Cloud and delivers full life cycle management and operations, including AI‑Native insights, automated speed tests, dynamic packet capture (dPCAP), anomaly detection, and root cause identification that focuses on end users’ experience. For Day 0 and Day 1 operations, WAN Assurance also provides orchestration, administration, and ZTP for vSRX. See the WAN Assurance datasheet for more information.
Available for Nutanix
The vSRX is available for deployment on Nutanix enterprise cloud to provide advanced network and application security and secure IPsec VPN connectivity between Nutanix AVH on‑premises resources. Using Junos Space Security Director, customers can maintain and manage consistent security policies on SRX Series Firewalls spread across campus, data center, and cloud. The vSRX has been certified Nutanix Ready. For more information, visit https://www.nutanix.com/partners/technology‑alliances/juniper‑networks.
Available on Amazon Web Services Marketplace
The vSRX is available on the Amazon Web Services (AWS) Marketplace to provide advanced network and application security and secure IPsec VPN connectivity to AWS VPCs, private clouds, and on‑premises resources. With vSRX 3.0, you can take advantage of AWS auto scaling to dynamically increase capacity while maintaining steady, predictable performance at the lowest possible cost. Using Junos Space Security Director, customers can maintain and manage consistent security policies on SRX Series Firewalls spread across on‑premises and AWS VPCs. Customers using the vSRX on AWS can either bring their vSRX license or pay via usage‑based pricing (pay‑as‑you‑go, hourly or annually).
Available on Microsoft Azure Marketplace
The vSRX is available on the Microsoft Azure Marketplace and on Microsoft Azure Government to provide secure IPsec VPN connectivity and advanced next‑generation security to Azure virtual networks. Using Junos Space Security Director, customers can maintain and manage consistent security policies on SRX Series next‑generation firewalls deployed on‑premises, as well as in Azure virtual networks. The vSRX is available in Bring‑Your‑Own‑License (BYOL) mode on the Microsoft Azure Marketplace and Microsoft Azure Government.
Available on Google Cloud Platform Marketplace
The vSRX is available on the Google Cloud Platform Marketplace and Google Cloud Government, providing secure IPsec VPN connectivity and advanced next‑generation and content security features to Google virtual networks. Juniper offers Bring‑Your‑Own‑License (BYOL), as well as Pay‑as‑You‑Go (PAYG) licensing options on the Google Cloud Platform and Google Cloud Government.
Juniper Networks Services and Support
Juniper Networks is the leader in performance‑enabling services designed to accelerate, extend, and optimize your high‑ performance network. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing the network to maintain required levels of performance, reliability, and availability. For more details, please visit https://www.juniper.net/us/en/products.html.
Specifications
The following table highlights high‑level specifications. Please see the product documentation for a complete list.
| *Hypervisor support is regularly updated. To find the complete list of all hypervisor versions supported, please view the vSRX on KVM page. | ||||
| Protocols | IP Address Management | Security | SLA, Measurement, and Monitoring | Hypervisors |
|
|
|
|
|
ICSA Labs Firewall Certification
Juniper Networks vSRX Virtual Firewall has satisfied the complete set of ICSA Labs Firewall security testing requirements in both the baseline and corporate criteria documents and has been awarded the ICSA Labs Firewall Certification.

Ordering Information
For more information about Juniper Networks vSRX Virtual Firewall, please visit https://www.juniper.net/us/en/products/security/srx-series/vsrx-virtual-firewall.html or contact the nearest Juniper Networks sales representative. For a free vSRX trial, visit https://www.juniper.net/us/en/dm/download-next-gen-vsrx-firewall-trial.html.
About Juniper Networks
Juniper Networks believes that connectivity is not the same as experiencing a great connection. Juniper's AI‑Native Networking Platform is built from the ground up to leverage AI to deliver exceptional, highly secure, and sustainable user experiences from the edge to the data center and cloud. Additional information can be found at juniper.net or connect with Juniper on X (formerly Twitter), LinkedIn, and Facebook.
1000489 - 025 - EN OCTOBER 2024






















