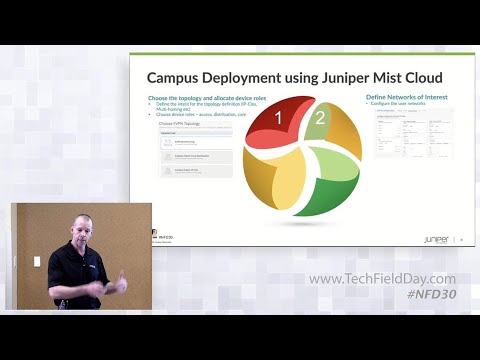
Three step Campus Fabric!

Select your topology, assign devices/roles, and push configurations!
Watch this walk provided by TME Rick Bartosik on how to easily deploy campus fabrics with Juniper’s new campus fabric workflow. Powered through the modern Mist AI cloud, this new switching solution delivers a seamless, standards-based L2 / L3 fabric without the deployment headaches and operational costs that traditionally occur in these environments. You can now deploy common standards-based campus fabrics, such as EVPN multihoming, EVPN core/distribution, and IP Clos with an easy 3 step process.
1:09: Campus Fabric Build
1:19 Organizational Level Build
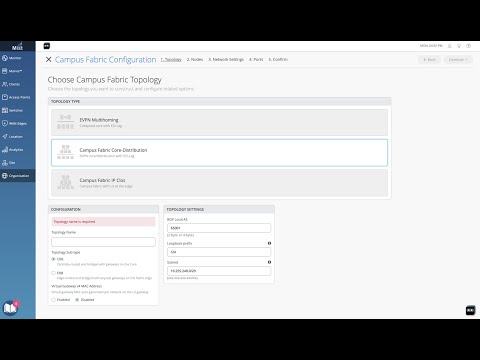
1:46 Choose your Campus Topology and Configurations for the Org Build Note: for a site build, there are three options. EVPN/VXLAN Multihoming, EVPN core/distribution, and IP Clos.
2:53 Select Devices. Select the switches that will be used in each layer of the topology and provide Router IDs as required.
4:34 Configure Networks - Add Pre Configured Template: With the power of Mist, define networks, routing options and port configurations.
6:11 Select switch ports for Fabric connections
8:03 Access device through Remote Shell BGP, Pushing Configurations down to the devices.
10:03 Telemetry of EVPN Insights, Connected Device
10:38 Edit Campus Fabric, Add Secondary device
11:30 BGP convergence. Device is On.
12:00 Access 2 - Remote shell.
12:15: ethernet switching table
12:24 show arp, devices operating.
13:08: Core1 and Core2
13:20: Review of everything we’ve built:
You’ll learn
The easy 3 step process
How to configure Campus Fabric
Who is this for?
Host

Transcript
0:07 at the missed user interface we are
0:11 looking at the various switches that
0:13 will be part of the campus fabric build
0:15 as we mentioned earlier we've got a
0:17 couple access switches couple of course
0:18 switches couple distribution switches uh
0:21 their their current version of code the
0:23 model of switch of course and other
0:25 information that we can add we can
0:27 actually add all kinds of information to
0:30 this particular setup through just a
0:33 real easy drop down menu here
0:36 one thing I want to mention is that
0:38 although these devices are connected
0:39 they don't have to be connected to build
0:40 the fabric so they do have to be part of
0:43 the organizational unit so they have to
0:45 be claimed or or adopted into the org
0:48 unit
0:49 um and that's a that's in this process
0:51 once they are claimed or adopted then we
0:56 can build the fabric irrespective of
0:57 whether whether they're connected or not
Campus Fabric Build
1:00 so let's go look at access points we've
1:02 got an access point connected to access
1:03 one and that is currently disconnected
1:05 which makes a lot of sense because that
1:07 switch is uh in idle mode right now
1:09 waiting for the network to be built so
1:12 let's go jump into the build so we hit
1:14 the organizational option and campus
1:17 fabric
1:18 okay so a couple items here uh we've
1:21 been able to build a campus fabric at a
1:22 site level since the Inception of wire
1:24 insurance but what we're going to do is
1:26 we're going to focus at the
1:27 organizational level because this aligns
1:29 with some of the larger Enterprises
1:30 large universities Healthcare Systems
1:33 where they want to have a multi-pod
1:35 approach and they want to connect those
1:36 pods through a lot through a a core you
1:40 know core layer if you will and then
1:42 that core layer offshoots to the
1:44 internet or maybe you build a Services
1:46 block on top of that core layer for
1:47 external connectivity requirements so
1:50 let's let's start with the campus fabric
1:52 build here so since we talked about and
1:55 we're going to demonstrate group based
1:57 policy
1:57 uh this requires the campus fabric
2:01 ipclos type of architecture which means
2:04 that we're extending vxlan down to the
2:05 axis layer and we talked about that
2:07 vxland header earlier that's where the
2:08 scalable group tag the 16-bit header for
2:11 GBP is associated we're going to push
2:14 the layer 3 Edge all the way down to the
2:16 axis layer we can put it at axis layer
2:19 at distribution it doesn't matter for
2:21 GBP either one works fine and then we've
2:23 got a topology settings here that are
2:25 relatively straightforward we use ebgp
2:28 for underlaying overlay we support equal
2:30 cost multi-path for underlay and overlay
2:32 and so these this setting right here is
2:35 is relatively straightforward customers
2:38 don't really change it to policy
2:40 settings at all we don't recommend they
2:43 change them but if they want to they can
2:44 so it's certainly customizable and then
2:46 the subnet clarification here is these
2:49 are the point-to-point subnets between
2:50 the adjacent layers so access layer to
2:53 distribution distribution to core uh and
2:55 that those are the the particular subnet
2:57 addresses
2:59 all right next option is to select the
Device Selection
3:02 devices that we are going to add to our
3:05 complete campus fabric build so we're
3:07 going to start start with the core
3:08 you'll notice a core is a bore option so
3:11 for a mid-tier smaller deployments I
3:15 would expect this would be used and this
3:17 would be where the customer is okay with
3:20 terminating the outside world directly
3:23 to the core so they might have a
3:24 firewall cluster maybe a couple of
3:26 routers that they pull directly into the
3:28 core
3:30 um and and that's a that's a clean
3:31 approach for them the cores of order
3:33 option just provides the the vxlan
3:36 awareness the encapsulation
3:38 de-encapsulation of vxlan to VLAN and so
3:40 forth at the core
3:42 however customers that it might be a
3:45 little bit larger or that want to keep a
3:47 lean core where the core is just a very
3:49 high speed router pack it in pack it out
3:51 as fast as possible they can deselect
3:53 this option and actually build a single
3:55 or a pair which is recommended of
3:57 switches to handle that border node
3:59 peace that border Gateway peace and and
4:02 that would be where a customer would
4:04 once again connect the internet uh their
4:07 Wan Edge devices their firewalls maybe
4:09 critical infrastructure DHCP radio
4:11 servers you know those those devices
4:13 that really they want to offshoot into
4:14 their own uh own pod if you will but
4:18 we're gonna we're gonna go ahead and
4:19 keep this selected here for the sake of
4:21 our demo
4:22 we're going to name the pod
4:23 Santa Clara Hilton because that's where
4:26 we are located and then we'll add both
4:28 5120 distribution switches and we were
4:31 going to add one axis switch which is
4:33 Axis one we'll come back later and add
4:35 access to real simple stuff here right
4:38 so we click on connect continue and then
4:40 this is really where Miss begins to
4:43 provide quite a bit of value so we have
4:46 a pre-configured template that we add or
4:49 import into the fabric so our vlans are
4:51 created with our IP addresses this this
4:54 would be the address default gateway
4:56 push down to the axis layer when I add
4:58 access to it's actually going to use the
5:00 same addressing scheme so same VLAN same
5:02 IP addressing we're using anycast in
5:05 this particular deployment model real
5:07 easy to configure single IP address
5:09 single Mac entry once again all hidden
5:11 using the Mist UI customers once they
5:15 see the Simplicity of how they build
5:16 verse they go ahead and just knock
5:18 themselves out with that so we're going
5:19 to build a guest and a Corp wife or a
5:22 guest Wi-Fi and a Corp ID verf uh both
5:25 desktops are going to be placed into
5:26 court by T as as they were part of kind
5:30 of if you want to consider that the same
5:33 routing is the same for same
5:35 administrative domain these are devices
5:36 that can communicate amongst themselves
5:38 without having to Traverse through a
5:40 third-party device like a router or a
5:42 firewall so we'll build that there and
5:44 then we're going to build guest Wi-Fi
5:47 and we're going to add that particular
5:49 VLAN which is where that AP remember
5:51 that AP is just disconnected the one we
5:52 showed that showed earlier that's off
5:55 that particular particular broadcast
5:57 domain so real simple I mean we we added
6:01 our we imported a template which had
6:03 pre-configured layer two layer three
6:04 that was automatically assigned to the
6:07 axis layer at because that's where we're
6:08 doing our layer 3 boundary for default
6:11 gateway capabilities and then we added a
6:13 couple verse with the proper networks
6:15 last bit of information is where we
6:19 actually interconnect the uh the layers
6:21 so the core is going to communicate with
6:23 both distribution switches only and we
6:26 do that here
6:27 and so coral one and core two uh connect
6:30 to distribution one and two and we see
6:33 here that we've got uh five and six uh
6:36 ports for
6:37 um both this one and this two now as we
6:40 build this out uh the the fabric itself
6:43 is using lldp from a Telemetry
6:46 perspective to validate that the
6:49 endpoint devices that we are
6:50 communicating with once these ports go
6:52 live that the name matches what we
6:54 expected to see on the other end right
6:56 on the on the config so if I happen to
6:57 misconfigure and select the wrong ports
7:00 then this system will absolutely tell me
7:02 and I can easily go back in and make
7:04 that change so let's go here and let's
7:06 just select the proper ports we that we
7:09 expect that will be the case here six
7:11 and five of this two and then we've got
7:15 we want to connect to our Downstream
7:18 access switch and that will be done here
7:19 on Port 37. and then we go to dist1 we
7:22 do the same thing so we're going to
7:24 connect to five and four for core one
7:27 and chord two
7:29 and what's really cool about this is
7:31 once we're done with the build we then
7:34 will be able to download a connection
7:35 table and the connection table could be
7:37 handed to the folks that are actually
7:39 plugging the devices in if there is a
7:41 separate group of Engineers or maybe
7:43 other resources that uh you know maybe
7:46 maybe this is being shipped to another
7:48 site remember we can build this without
7:50 the devices being online they just have
7:52 to be onboarded to the org
7:54 so we've got this built now I can click
7:57 on connect continue apply my changes
Demo
8:00 and we should see this get pushed down
8:03 relatively quickly so I'm going to jump
8:04 really quickly into this and I want to
8:07 go down to my
8:09 my Axis layer first device and what I
8:12 want to do is poke around a little bit
8:13 you notice I can access the device
8:15 through a remote show which is pretty
8:16 cool
8:17 so I like that I'm just I'm just the guy
8:19 who who likes to be able to
8:22 you know poke around and make sure CLI
8:25 is is because that's my what I believe
8:28 is is truly the case CLI is always going
8:30 to tell the truth uh so we've got our
8:32 bgp session set up right here that looks
8:34 good so I've got bgp underlay and
8:36 overlay let's go and take a look at my
8:39 ethernet switching table
8:41 and what we have here is we've got our
8:43 our AP device right there you see that
8:45 local so I'm going to come up here to my
8:47 desktops
8:49 and what I'm going to do is I'm going to
8:50 start to ping my local device for
8:53 desktop one which is 1099 or my local
8:56 Gateway
8:57 109999.1 so I'm able to Ping that it's
9:00 pretty cool come over here and hit this
9:02 again I see the local desktop show up
9:04 now I I shouldn't see anything across
9:06 the network and I really don't I see the
9:08 other devices I've got the excellent
9:10 tunnels to but remember we have not yet
9:12 onboarded access switch 2. so here 1088
9:18 1.1 is my local Gateway off desktop 2
9:20 and let's take a look at my
9:22 configuration of desktop 2 and that is
9:25 here so I'm not able to Ping that device
9:27 and it shouldn't be but I'm going to
9:28 keep that pane going because we're going
9:30 to add this switch in just a second here
9:31 all right so I'm able to Ping there
9:34 and I've got internet connectivity from
9:36 the desktop through the cloud and the
9:37 reason I know it's through the cloud is
9:40 because I could do a trace route and I
9:42 could see that my next hop is
9:45 10999.1 which is access one that's a
9:48 good thing so I'm actually going all the
9:49 way through
9:50 the firewall at the top end part of my
9:54 network to access the internet so that
9:57 that was a relatively quick turnaround
10:00 with respect to bgp and signaling and
10:03 actually pushing the configuration down
10:05 to the devices that happens within
10:08 seconds now what takes a little bit
10:11 longer is just a Telemetry piece of the
10:14 uh what you see here the actual campus
10:16 fabric EVP and insights option which is
10:19 going to turn green once everything gets
10:21 collaborated and corresponded back to
10:23 the cloud
10:24 all right let's look at the access point
Access Point
10:26 that might not yet be oh there it is
10:27 it's connected cool so the access point
10:29 has connectivity out to the internet
10:31 through the local axis one switch that's
10:34 a good thing so we've got users that can
10:35 take an onboard we're in pretty good
10:37 shape there uh let's go back to campus
10:40 fabric click on this guy and look around
10:43 and what we're going to do is we're
10:44 going to edit campus Fabric and we're
10:47 going to build and we're just going to
10:48 add the secondary switch
10:51 to this particular configuration which
10:53 is access to right all we need to do
10:56 here is we've already built the layer
10:58 three we've already imported that so all
11:00 I need is to go down to my my port
11:02 values and make sure I click I click on
11:04 once again the right Port connecting to
11:07 access to relatively straightforward
11:09 lodp is going to help me with this
11:12 which is awesome because I make quite a
11:14 few mistakes
11:15 so anyways we'll go over here and we'll
11:17 connect to what we expect to be the
11:20 proper ports
11:23 all right and let's go ahead and click
11:25 on continue apply changes and confirm
11:28 that
11:29 all right so now we've confirmed that
11:32 I'm going to go back to my secure CRT
11:35 and I'm going to set up a ping
11:37 to
11:38 1088-88.88
11:39 and that'll hopefully resolve soon okay
11:42 we're already paying our local Gateway
11:43 from the desktop perspective
11:45 and that should that should that ping
11:48 across the network should happen pretty
11:50 quickly as bgp converges wow that's
11:52 pretty good timing man I couldn't have
11:54 chosen any better timing there so we're
11:56 good there that device is is operational
11:59 and uh let's go ahead and take a look at
12:01 access 2 here just to take once again we
12:05 can remote shell into the device I
12:07 actually like to use secure CRT as well
12:09 and so you can have an off board or you
12:11 know third-party secure CRT or
12:14 third-party SSH access application
12:16 doesn't matter whatever you're most
12:18 comfortable with but there is a remote
12:19 shell capability built into this
12:21 uh once again we're going to look at the
12:23 ethernet switching table we see our
12:25 local AP we see dot 12 which is the the
12:29 workstation and if I look at ARP which
12:31 helps me a little bit easier I can see
12:34 um 10888 and that's a good thing right
12:38 so I'm able to see my local APS and
12:41 things looked like they're operating as
12:43 as I would expect them to operate let's
12:45 go back to desktop one here and ping
12:47 back through to 1088 and we're good
12:49 there we're hitting that 1099
12:53 9999 good shape there okay so I want to
12:57 go back to let's go ahead and minimize
12:59 this
13:00 we'll go back to our AP yet we're good
13:04 there I'm going to go ahead and refresh
13:05 my screen up top here
13:08 and I would expect that our our fabric
13:10 should be just about built with all
13:12 devices operational okay we're in pretty
13:15 good shape there
13:16 core One Core two
13:18 and I'm happy with that so what we've
13:21 demonstrated is the campus fabric EVP
13:25 and vxlan build through the Miss Cloud
13:28 we built the five stage Clause that we
13:33 saw earlier which is access layer
13:35 distribution layer core layer attached
13:38 to a SRX firewall that was pre-built so
13:42 far was already built we had a port
13:44 profile configured for bgp all we need
13:46 to do is just build the fabric through
13:48 the template access so we used we
13:50 imported a template for layer two layer
13:52 three we applied that against the port
13:55 values that we selected at the very end
13:57 and then here we've got our our device
14:01 our our Network which is operational and
14:03 you can see that what what's what's of
14:05 interest is that these EVP and insights
14:08 will give us a sense of which of these
14:10 links are being used heavier than others
14:12 here we're doing pretty good job of load
14:13 balancing here we're using one link more
14:16 than the other it's just the way that
14:17 ecmp works on occasion we've got some
14:20 information over here that is applicable
14:22 as well
14:23 so this has been uh once again the
14:26 demonstration of Campus fabric build
14:28 hopefully this has been good for you
14:30 guys and I hope you have a great day
14:32 thank you