Bringing EVPN and VXLAN to the Campus with Juniper

Mist AI: How to bring campus networks into the 21st century.
Watch this video from Tech Field Day 2023 to discover how an AI-driven campus fabric from Juniper can address the many challenges arising from legacy technologies. With EVPN and VXLAN combined with Mist AI™, Juniper can provide a networking solution for your campus that boasts a simple, scalable interface that is also easy to use.
You’ll learn
How Juniper Campus Fabric solves many (and we mean MANY) campus problems
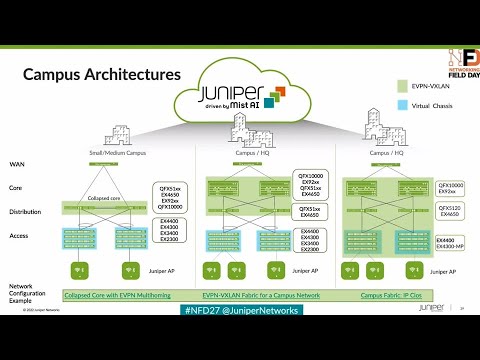
The variations in three types of campus fabric architectures: EVPN multihoming, campus fabric core distribution, and campus fabric IP Clos
Who is this for?
Host

Transcript
0:09 um Rick bartosik technical marketing engineer with juniper a focus on the ex twitching platform and primarily on the
0:16 campus fabric Technologies and so what what Ivy talked about with respect to wired Assurance uh dovetails
0:23 right into a campus fabric architecture so campus fabric to us
0:29 the terminology is EVP and vxlan so it's an EVP and vxlan architecture
0:35 in in different modes we'll talk about we'll dive deep into these modes different different silos but managed
0:42 through the Miss cloud so a customer today we've got hundreds of EVP and vxlan deployments in data
0:48 centers as well as campuses that are not missed managed right they're actually CLI managed maybe ansible playbooks and
0:55 I've built those what I really appreciate about this solution is the
1:01 fact that it extrapolates all the all the complexity so when you're building a multi-protocol
1:06 bgp instantiation you've got route targets and Route distinguishers and all kinds of policy that have to be applied
1:13 what Mist does is it really simplifies that so the goal of today is to educate you
1:19 guys on just what the different architectures are we're going to go through a demo of a build
1:25 with my other partner in crime Rohan and then I hope to see all of your hands when I ask a question can you build a
1:32 fabric through the Miss cloud if you had you know the VLAN information
1:37 if you wanted to isolate traffic into different routing instances and you knew where the pores were connected
1:43 could you build could you build the fabric and the answer hopefully is yes and if the answer is no then we haven't
1:48 done our job right so um just Dive In
1:54 okay so why campus fabric you guys may have seen and by the way we're not the only one who does EVP and VXL what I do
2:00 want to stress is our experience with EVP and vxlan and we'll talk about a
2:06 slide in the next one or two slides that dives into
2:11 um the amount of time you spend building and working with the contributors with an ietf
2:17 with respect to evpn the work we've done in our data center crdc team
2:23 who has been building EVP and vxlan networks for eight years now and so we've taken a lot of their
2:29 expertise and and Blood Sweat and Tears and pull that into our solution
2:35 so these are the four top pillars challenges that when we say Legacy
2:40 sometimes that word is misused let's talk about your standard layer 2 network with spanning tree
2:46 that's a typical instantiation today right so for if we're dealing with that and you've got boundaries and so forth
2:53 we're layered two and layer three exist one of the challenges right now and this
2:58 wasn't the case a couple years ago is micro segmentation so customers are you know there's a
3:03 proliferation of iot devices if you look at retail various Industries where they are bringing devices in
3:10 that are headless lack of security they might can only communicate within the
3:15 same broadcast domain so with these with these Enterprises are struggling with without invoking all kinds of ACLS and
3:21 pushing traffic through firewalls is how do they segment traffic within the actual broadcast domain and the answer
3:27 that typically is private VLAN right you build a private VLAN and you can look inside that broadcast domain
3:34 and say I see these devices and I can I can build a private uh primary VLAN I
3:40 can then build a community VLAN underneath that which absorbs the intelligence of the primary VLAN and
3:45 then I can build isolated vlans that's three separate types of vlans you build with private vlans and although they we have seen them
3:53 interoperate with between vendors they're just difficult and there's there's no scale so at a minimum use
3:59 case what we find is customers just to tackle the iot use case for for intra
4:04 VLAN security they're looking at campus Fabric and the reason for that is for a technology
4:10 called group based policy so group-based policy leverages the vxlan header ABI we're going to show
4:16 we're going to demonstrate that we'll talk about where that is it's a 16-bit header within the vxlan construct itself
4:23 and we are one of the few if only vendor to leverage that true header the actual
4:28 GBP group based policy header to to ascertain how we want to tag traffic
4:35 amongst various criteria and apply that across an entire campus fabric
4:40 whereby we don't now don't have to pass traffic through a firewall we certainly can if you wanted to segment traffic
4:47 between routing instances right but within a fabric itself within a VLAN micro segmentation strategy is
4:54 one of the top reasons why customers are looking at Fabrics the second is ACL usage so that kind of dovetails off the
4:59 first piece there where if I've if I'm building private vlans or where I'm pushing traffic back through firewalls
5:05 there is a tendency for ACL sprawl and when we look at the demonstration
5:10 hopefully what you'll see is a simplification of how this technology is actually built and presented to the end
5:17 user so the other question would be hopefully can you build a micro segmentation strategy once the fabric is
5:24 built and I hope to see all of your hands right because it there there are this is very complex this technology is
5:31 extremely complex under under the covers when you're building EVP and VX land you
5:36 are you're worried about VLAN to V and I mapping you're worried about scale
5:42 you're worried about okay wait a minute now I so I'm learning a MAC address off a port but now I'm I'm taking that Mac address
5:49 and I'm tunneling across the network how in the world do I troubleshoot that
5:54 and that's where that's where missed and Marvis come complete yes I was actually going to ask about that because one of
6:01 the reasons because vxlank might be pushed away by some people in the Enterprises because yes it is
6:07 technically Deployable and it would bring a plethora of benefits but who's going to manage that right because then
6:13 you would need a bunch of knowledge of all Engineers just do even level one troubleshooting because not everybody's
6:18 going to understand vxline right up the hood or or a vgp or why is this Mac address here and here and why is it
6:25 flopping and this type of stuff but then then it would have to come in a way I assume that's what comes after with
6:31 Marvis that it gets simplified because otherwise then you are setting yourself
6:36 well for failure right because then okay I deployed it and now well while everything is good is wonderful but now
6:43 I have to troubleshooting and well you're getting yourself an up rope to put it around your neck right right yep
6:49 so uh if you're doing this without missed we're giving we're giving you enough rope to hang yourself effectively
6:55 right and I've deployed these Fabrics so I've got quite a bit of experience and
7:01 appreciation for what missed uh so first of all the deployment of the fabric we're gonna we're gonna show that and
7:06 the whole idea is there to extrapolate the the complexity away from the build assuming you've got your basic
7:12 information in front of you day two then becomes critically important because you're only building a fabric one time
7:17 right you might be adding a couple axis switches maybe a couple of core distribution switches but
7:22 um your day two approach we're going to talk about that with with Marvis so in my humble opinion what Mark what Miss does is it not only simplifies the
7:29 deployment it it helps with um so if I if I want to learn where a
7:35 MAC address is in a network in the Juno's operating system I run the same commands whether I'm on a layer 2
7:41 Network or an EVP and vxlan network so that's one thing we've done is we've we've actually tried to take the same
7:47 operational structure approach preview evpmgx Lan into today but now
7:52 we're pulling that into mist so when I build the when I build the fabric I can immediately see my bgp establishments
8:00 I can see the um the updates between the devices I can understand whether or not
8:06 my verb is up or my verb is down all through the missed construct without
8:12 really having to understand what is my route Target what should my route Target
8:17 strategy should be what should my important export policies what should they really be what should my VLAN to V
8:24 and I mapping what should that really be so we we simplify all of that now that's not to say there are some customers out
8:30 there that don't want to dive deeper don't want to die deeper and so we'll we'll talk we'll we'll kind of pull that
8:36 out when we the real Lily is definitely on crunching the information because if you mentioned earlier that you are going
8:42 to get the same output and with this technology or the other then then it's not about this output is how do you
8:49 crunch that information is to provide insights on all day that is just simplified things right that's the focus
8:54 you will see us showcase if you're looking for a MAC address somewhere yes you're no longer going to the ARP table
9:00 somewhere diving deeper to the Shelf before you move on I understand that you want to move on here anytime I see a
9:05 slide like this I want to push back just a little bit and say which Pac-Man um you say that it solves many campus
9:11 problems you say it's great across is there a customer use case where this doesn't make sense uh yes uh I think
9:18 we're customers so that's a great question actually where customers are um where they don't have vlance brawl
9:24 whether where their axis switches are primarily isolated vlans and and they're routing and they don't have Micro
9:30 segmentation requirements in that case I wouldn't position this technology now I'd position Miss to manage assess to
9:36 manage the network absolutely because mist is so campus fabric is the EVP and vxlan build and the management of a EVP
9:44 and Vaseline network but but miss wired Assurance will do that as well as your
9:49 standard Layer Two or your standard grounded Network so if I've got access switches whether they're you know virtual chassis and
9:56 I've got layer 3 Boundaries at the access and I I all my security requirements are maintained pushing
10:02 traffic through a firewall Northbound I wouldn't position this at all I don't so so I don't have any Loop free issues
10:08 right because I'm routing I I have um I've got equal cost multipass so I'm
10:14 using allpass anyways right and I don't have the the issues with VLAN sprawl
10:21 so that's that's and and we see those customers we see them are there any technical use limitations around things
10:26 like multicast or other types of things that yeah say like maybe how much to go how much time do you have yeah
10:32 so so I'm I'm going to answer your question as I'm changing that's fine yeah please no
10:38 no no no that's a great question so multicast would be a that is something we are solving right now as we speak so
10:45 there are so evpn introduces eight new route types that's exciting right eight
10:51 new ways instead of having one Mac address you now have eight route types one through eight and six two six
10:58 through eight are multicast specific okay and they're built for an evpn Network we have a technology called
11:04 optimize internet oism what that means is that if you're building multicast push it close to the axis layer as
11:11 possible so that's where you want to build an ipclos with the x-lan and then those those axis switches actually have
11:18 incredible intelligence and can participate in the multicast leaves joins prunes Etc
11:23 and they know exactly where to send these packets across the network because they're using selective multicast so
11:28 it's very daunting though because then you have scale so um and I don't mean to minimize that
11:34 that that's that's very important I just want to ask us I've heard the vxline pad pitch yeah for years now right but
11:40 there's always been those like use cases that have been challenging so you're no no we'll take cash no questions absolutely no question and IPv6 I'll
11:47 throw that in there as well right um I so we uh we are leading contributor in ietf uh many standards we've deployed
11:54 you see this here and we've once again I can't stress how important it is that we've taken what we've done in in the
12:01 data center world there's a lot of a lot of pull in from data center into the campus piece anycast addressing
12:09 MTU sizes you wouldn't believe the different MTU sizes you can have in a network with jumbo frames right so he's
12:16 taking all that stuff and minimize it we don't ask the question we just do it in the background for the for the consumer
12:21 okay um great discussions by the way I love the questions so let's let's look at the different
12:27 architectures and we will then bring up a couple of examples per architecture then we'll get into the fun which is a
12:34 demo and I've got my toes crossed I don't know if you can see that so anyways the
12:40 first three three architectures evpn multi-homing is our first think of that as a collapsed core replacement you guys
12:48 have seen I'm sure you've seen architectures where the the axis layer the routers the
12:55 firewalls are coming into a collapse core typically two bigger devices interconnected right they might be
13:02 running MC lag maybe they're running vrrp of some sort maybe they're running spanning tree and they're just doing multiple span tree instances and doing
13:09 what they can to load balance even an odd vlans well that's what this use case does is it targets that approach
13:17 um and what it what it what it really focuses on is the ability to keep your axis layer where it is so if it's
13:23 running standard lag lacp that doesn't change that's going to be consistent we
13:29 we uh we target the main core operating devices we introduce EVP and vxlan
13:35 between those two devices this can also scale up to four devices horizontally so
13:41 if you think about MC lag and these other Technologies typically it's two if you have to build another pod that's
13:46 another pod managed separately another two so Mist will manage up to four in a collapsed core and that could be larger
13:54 switch it could be a mid-tier switch for us it just depends on what the scale is quite honestly it depends what the fiber plant is as well right so that's the use
14:01 case for Ev pan multi-homing is really targeting the collapsed core campus core distribution is where the
14:08 customer still wants to keep the access layer the same typically these are those are both Layer Two instantiations by the way Layer Two
14:14 to the left on evpn multi-homing Layer Two at core core distribution they
14:20 hopefully their Juniper switches as long as the lacp lag that's all we care about right so the replacement technology once
14:26 again doesn't touch the most expensive part of the network which is the axis layer core distribution introduces EVP and
14:32 vxlan at different layers for scale so if they wanted to scale this horizontally they could begin to do that
14:38 place layer 3 at the distribution layer or at the core layer give them the chance whatever makes most sense in
14:44 their discovery that happens in all of this and then the final campus fabric IB Clause is where we pull EVP and vxlan
14:51 all the way down to the axis layer that would be mostly a green field opportunity right so a new building new new
14:59 deployment we would we would be looking at that and EVP and vxlan comes down to the axis layer and that's really where
15:06 you begin to look at micro segmentation so when customers if they're if they've got a DOT 1X strategy they're plugging
15:11 devices into their axis layer maybe they're using forscow Aruba clear pass Cisco ice free radius what have you to
15:18 authenticate those devices we can take that authentication we'll show this and apply a tactile authentication and now
15:25 that tag moves with the device no matter where it is within the fabric and now we can actually micro segment and we leverage that vxlan transport and we
15:32 leverage it leverage that open standard-based way of actually exchanging tags these these what we call
15:38 scalable group tags across an EVP and vxi Network I do want to dig into the
15:43 micro segmentation a little bit because more and more the the network is being relied upon to be that sensory
15:49 enforcement Point uh for security so you had mentioned how you group those
15:55 devices so you're when a device gets plugged into the network how is that
16:01 um how is that tagging happening so you're relying on a radius solution we we don't
16:06 have to rely on a radius solution but we certainly can so let's say you've got let's say you've got forescout somewhere
16:13 in the core of your network right and and so the the Juniper switching architecture which would be either our 4100s or 4400s would have a handshake
16:20 already with that four Scout device so when a user um plugs in right that
16:26 radius authentication method would get past forescout forescout would would authenticate that message within their
16:33 database they'll actually have a group based tag applied to that group or to
16:38 that supplicant okay and that's a standard AVP a standard radius attribute value pair that information gets pushed
16:45 back to the switch now the switch says Ah for this Mac address or this IP address or this VLAN
16:52 I'm going to apply this tag and now that tag is commensurate with
16:57 that user no matter where it's located within the fabric so traffic within the fabric within the
17:03 vxlan construct we use that tag to pop to police traffic so if I've got VLAN
17:09 over here 100 and VLAN 100 over here and I'm extending that VLAN and these devices are shouldn't really be talking
17:15 at all their iot devices put them in different tags and also and just you know through
17:21 their authentication and block that at Ingress and so so to take that a step further
17:27 from what I'm hearing we have uh options of either ACL or tag based
17:33 yes um as far as and I'm assuming the the ACL enforcement is at packet Ingress
17:39 into this it isn't it is ingress it could be Ingress or egress most people are going to choose Ingress okay in in
17:44 tag enforcement is that at can you do tag enforcement at Ingress yes the packet have to travel no no tag
17:50 enforcement and Ingress yes sir okay thank you yep and and that's important because
17:56 the fabric is a bgp fabric it's a it's a multi-protocol bgp fabric right and so
18:02 we use things like bgp communities to instruct the far end device hey
18:07 here's a tag right we're using things like type 5 prefix routes so we're using the standards already there we're just
18:12 leveraging them to to share information across the devices so when you when you think about interoperability and eantc
18:20 you guys are familiar with the entc they're a third-party Consortium that does all kinds of evpn mpls they they
18:27 pit the vendors against each other right not in steel cages at all but um you know can your stuff talk to this vendor and we're always
18:34 pulling back the curtain exposing what we're able to do through a standards-based Consortium so I'd go
18:40 there to validate what I'm saying here so you look confused though I mean are you you're good no I'm just I'm I'm
18:46 comparing with other platforms and and where to handle that that enforcement point because to me
18:53 traditional network security you want to drop that packet as soon as possible absolutely why let it travel no no no
18:58 question no question that travel through the network if it's just going to end up no question yeah I mean if for egress enforcement so the reason why you do
19:05 egoist enforcement just since we're all friends here is scale right it's it's it scales much higher Ingress enforcement
19:13 requires more typically tcam instantiation but it's absolutely preferred because you need to pull down
19:19 that full picture to know you need to pull down what devices you need to know all your devices source and Destiny
19:24 that's right or your tags sorry that's right but I think that would be better than letting then the traffic go to the
19:29 other side of the fabric waste of the bandwidth so you can drop it on the other Leaf so like I said there's always there's somewhere else nothing's
19:36 nothing's for free all right right so if I want to tag Ingress and I want enforce Ingress which is what I prefer to do
19:42 then there's a scale you know we just and this these are all standards right we're all using for the for the most
19:47 part the same broadcom chipsets right for the most part we are and they all have the same scale limitations so
19:55 Discovery is important when we talk to customers about micro segmentation it's very important to understand the
20:00 differences between Ingress and egress just from that perspective but yes you want to drop it at Ingress that that's
20:07 our that's our problem how do you help your or how do you guide your customers understand those scale limits so so the
20:13 beauty is we work with our partners a lot to do that right we have we are a huge partner-based Consortium so we
20:19 trust those folks but at the end of the day myself Abby the other folks in this room we constantly show the technology so
20:27 they're comfortable with it and then we are constantly doing QA and scale scale testing so we work with we understand
20:33 are using radius if you're not um what kind of uh what kind of tagging and classification do you prefer would
20:40 you prefer IP sub subnet IP Source would you prefer VLAN so there's all different
20:46 types of ways of actually classifying a tag against various criteria but it the Simplicity of it is
20:53 what's what's your scale right so so what is your scale today how many how many devices because if you're doing
20:59 things like IPv6 which is it's supported across V4 and V6 it's analogous you're
21:04 then dealing with higher scale right uh a a V6 endpoint will have multiple
21:09 addresses and so forth you have to be concerned about so it it is a it is this
21:14 is the year where group based policy will really begin to take off in my humble opinion
21:20 um because of the the work that we've done and I think last year was almost a proof of concept kind of kicking the
21:26 tires hey I wanna I wanna test VLAN to VLAN segmentation can I do that across
21:31 the fabric I can't okay well that's that's kind of cool but the use cases weren't as prevalent as they are right
21:36 now and and our solution is much more mature so bring us involved in those cases and
21:43 and we'll we'll make sure that the the right questions are being being asked this these this slide kind of
21:49 um redescribes the the previous slide of the different architectures um what about you know evpn multi-homing
21:56 core distribution campus fabric IP cloths uh they are all EVP and VX land
22:01 constructs just depending on where they are in the network what's nice about the first two is the the use case around the
22:08 axis layer switches doesn't change and if it's Layer Two and these are just standard lag devices those devices don't
22:15 get tested all so now you build a method or procedure around how you replace the core effectively and then campus fabric
22:21 ipclos mandatory for for group based policy so if you're extending vxlan down
22:27 to your access layer that's where your GBP tagging really begins at that point so if a customer is interested in micro
22:33 segmentation campus fabric ipclos right does that make sense I mean do these
22:39 architectures okay I just well Services block is something we've taken
22:46 from our data center folks in crdc where customers are interested in and these
22:52 would this would be applicable to a larger customer who wants to keep the the core very lean
22:57 what does that mean that means that they've got a core layer that they want to to be used to Route packets as fast
23:03 as they can they don't want to place the burden of encapsulation and decapsulation of vxlan on that layer of
23:10 the network itself and so they can offload that the services block as a way to extend and talk to outside of the
23:18 fabric so if I've got critical infrastructure devices like DHCP servers or radio servers obviously Wan routers
23:24 firewalls you plug them into the services block treat that as just another Leaf pair or axis pair and now
23:32 the core can do what it does really well which is Route traffic so when we build the fabric we'll show both options we'll
23:37 actually show hey we'll combine this on our core so the core is going to connect directly to a firewall cluster or I can
23:44 deselect the option and we could build a separate Services block that's where the Gateway exists essentially
23:53 okay so let's talk about um Bobby did a great job of talking about water Assurance I'm going to spend a couple of steps to go through the
24:00 build and then we'll um we'll we'll describe what you're going to see in the demonstration then we'll we'll jump into
24:05 it before we jump there there's one question online that I wanted to get answered no problem um and that is uh someone's been looking
24:11 at your product it's like this is all great but there's one missing piece around a campus Network and that's dot
24:17 1X authentication you you partner with multiple Solutions does Juniper have
24:23 anything in the in the works to kind of bring dot 1X into Miss so so um so we've been talking about uh this
24:32 for a while in the last Mobility field day I suppose we did speak about right what we are footing into so you will see
24:39 a solution that's baked in again one in the missed Cloud a cloud-based Radio
24:45 Service that's going to hit you and it's not it's not it's public knowledge we've discussed about this in in a Mobility
24:50 field day we're absolutely doing it excellent thank you very good great question I think that's a really good
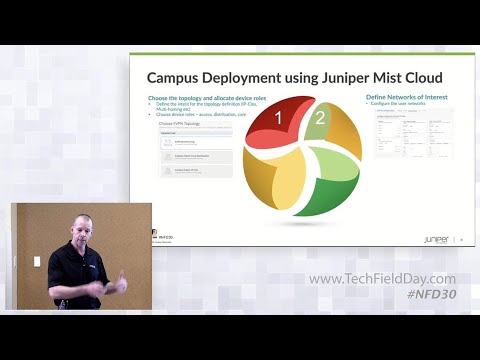
24:55 question oh that's a great question yeah okay so the first uh the first option when we when we build out a campus
25:01 fabric would be to choose the topology and allocate to the device role so one
25:07 of three topologies right EVP and multi-homing addressing collab score core fabric
25:12 distribution or campus fabric IP claw so when we go through the build we'll talk about the different settings and options
25:18 what we've done is we've we're using ebgp as a protocol for our underlaying overlay and so we've really simplified
25:25 the as a numbering and how we build point-to-point subnets using a slash 31
25:30 all this stuff is there most customers keep the defaults because they just work but they can be changed just depending
25:36 on what the customer feels like right what they're comfortable with and then we select the devices and where they is
25:41 where they're positioned within the build in a five-stage clause which is what we're going to build we've got two
25:47 core devices we've got two distribution devices and we're going to originally build one axis layer get that Opera
25:53 operational and then we'll add a second axis layer and make sure we got full routing right all that's done really
25:59 within the first step the second step is the Second Step could actually be predefined you can build through missed
26:05 wired Assurance templates so my vlans and my subnets are here I can build that template and ingest that
26:11 import that into the build and select that as an option and we'll show that we use things like anycast IP addressing
26:17 when we push the boundary down to the axis layer which gives me a single IP address across all my devices and a
26:23 single Mac address right very very simplistic and then we um and then when the
26:29 customer sees how simple it is to build a verf you know outside of guest Wi-Fi
26:34 right they begin to they begin to go down that path they realize that they're here are users
26:41 that are typically part of this the single autonomous system not From bgp perspective but they all communicate
26:46 we'll put them in one verf and then the guess Wi-Fi verb is completely segmented from everybody else for obvious reasons
26:52 and then maybe there's an iot version so the the verf concept that typically is
26:58 very difficult when you provision it through CLI is really simplistic when we look at the missed piece you select the
27:04 the vlans and that's that's really it and then the next phase is you you interconnect the
27:11 ports you you connect the adjacent layers together and the Telemetry through lodp will tell
27:17 you whether those ports are the correct ports or not so when we build the system EVP and insights will will pull all that
27:23 Telemetry in we'll we'll see that the the fabric is built green is good if there's red involved the bgp peer is
27:30 down and it could be down because we actually chose the wrong Port or Port one is connected to distribution one
27:35 when it when actually lldp is telling us this distribution two so that's part of
27:40 the third step and the fourth step is just applying the intent apply the configuration so that the build is
27:46 relatively straightforward if you had basic information vlans subnets whether
27:51 you want to introduce routing instances and then the port interconnects that's really all you need
27:57 to build the fabric uh one thing we wanted to emphasize as part of that build out honestly is those questions
28:04 that were asked there are all things that campus administrators do today we did not want to introduce anything that
28:11 is not new or you know con all the constructs I spoke about we wanted to keep it to a point where how can we
28:18 migrate an existing campus in traditional based routing into vpnbxlan easy without uh with with the
28:24 simplification so the questions are all things that that you do today with your ex yeah we're not we're not trying to
28:29 stop you right they're relatively straightforward questions so um spend just a couple seconds on this
28:35 slide and then we'll jump in to the demonstration um it just greatly simplifies if EVP and
28:41 vxlan build that's really the one of the great benefits of Campus fabric it reduces the complexity in how the
28:46 technology is built um MTU optimizations you wouldn't believe so if you look at an underlay
28:51 that's an MTU setting if you look at a bundled ether interface that's a different MTU setting if you look at the
28:58 layer 3 boundary that's a different mpu setting and these are all settings that we've taken from our our experience with data center builds so all of that
29:05 information anycast is another one all the information is pulled under the covers when we build it through the through the through the fabric
29:12 so multi-homing address the collapse core piece micro segmentation through ipclos
29:17 when multicast is introduced we recommend an ipclos as well to push the
29:23 layer 3 boundary close to the axis layer right so we can participate and spare the fabric you know multicast traffic
29:29 layer 3 boundary a distribution layer is another option where if you if we're dealing with scale
29:35 uh where Next Top addresses are very high maybe we push the layer 3 boundary
29:41 from the axis typically a smaller platform to the distribution model
29:46 right so that that device Which is higher performing is going to have higher scale and so those are those are
29:51 kind of questions that we kind of ascertain through discovery right give us a sense of of where we are
29:57 today where you want to go in three years five years um you know use cases around security
30:03 use cases around scale those are very important to to kind of peel back the onion on and then when we talk about our
30:09 build there are two ways you could build a fabric one is on a site by site basis right I might I might say Santa Clara
30:16 Hilton I'm going to build a fabric think good or I can build an organizational level approach where uh that that works
30:24 well for larger campuses universities where they've got a core layer and then they build multi-pods
30:31 so those pods are all connected through the core layer and then the core layer jumps off to a firewall it would have you we're gonna we're gonna show that
30:38 in our build the organizational level do you need that organizational level fabric to be able to pass those uh group
30:46 based tags it could be any it could be any one of the bills we do so it's got to be a campus fabric copy Clause okay
30:52 right so vxlan down to the axis but it could be a site build or an org build irrespective
30:59 okay and then reply I have to talk about our platforms right
31:05 the the I'm part of the ex switching platform I've talked so much about Miss today because I love Mist but these are
31:11 the platforms that we manufacture um industry-leading last Mobility field day we introduced the 4100 so that's a
31:19 really really solid axis layer switch fixed form factor Poe the 4100 400 which
31:26 is the other axis layer switch is a incredible amounts of telemetry so
31:32 flow-based Telemetry through the broadcom chipset is something that we feel we differentiate ourselves on the
31:39 types of telemetry dos mitigation actually at the axis layer through the broadcom chipset we support both that
31:45 type of technology in the 4100 4400 and then we've got obviously distribution
31:50 core the 9200 very very popular enterprise-based chassis modular switch
31:56 and here's the breakdown of the different layers and where the different products sit within each layer
32:03 foreign so now we're bringing
32:09 evpn vxlan to the camp to the campus yes I'm very familiar with it in the data
32:15 center yes so do things need to be built consistently between the data center and
32:20 the campus and then also those group tags um can they flow yes campus to Data
32:27 Center yes and so and and I'll speak to our data center and our campus deployments so our data center
32:34 deployment and campus both support group-based policy today the beauty of group-based policy is that it's just
32:39 it's just a tag within the vxline header so there's no reason why our GBP policy
32:44 couldn't work with any other vendor that adheres to the standard no reason whatsoever it's just a 16-bit header
32:51 within the vxland construct um the the the data center approached how it's built and the campus approach
32:57 house built is different um most of most of the time it's because you've got higher scale and more
33:02 microscape more uh more if you will multi-tenancy in the data center piece
33:08 but the constructs of how the fabric is built are almost the same the empty settings anycast equal cost
33:16 multipath the policies that we use for multi-protocol bgp those almost those are almost on net you can't even look at
33:22 the you can't see the difference between the two so where um and so miss is really focused on Enterprise and and how that's
33:28 built so and we're always tying data centers and our campus Fabrics together uh sometimes you do it through CLI if
33:35 there's no approach but through Mist we can build that border Gateway and exchange information with any other type of data center
33:42 so really the difference would be the multi-tenancy piece and and the scale and you'll hear terms like you know
33:48 leave spine core distribution access I mean they're the same thing just different
33:54 terminology to separate data center from from access our data center from Enterprise