
Introducing the Juniper AI-Native Networking Platform
Juniper assures exceptional experiences with its AI-Native Networking Platform – where every connection is reliable, measurable, and secure.
The latest networking ideas from Juniper and the industry
The Feed is a streaming service with videos and podcasts that provides unique access to Juniper executives, experts, and events aimed to inspire and educate today’s business leaders to tomorrow’s network engineers! Start with our top picks!

AI Data Center: Deliver High Performing, Scalable Networks for AI Training and Inference (explainer)

Marvis Minis: Introducing the Only AI-Native Networking Digital Experience Twin (explainer)

Bob Friday Talks: The AI-Native Networking Platform Defined
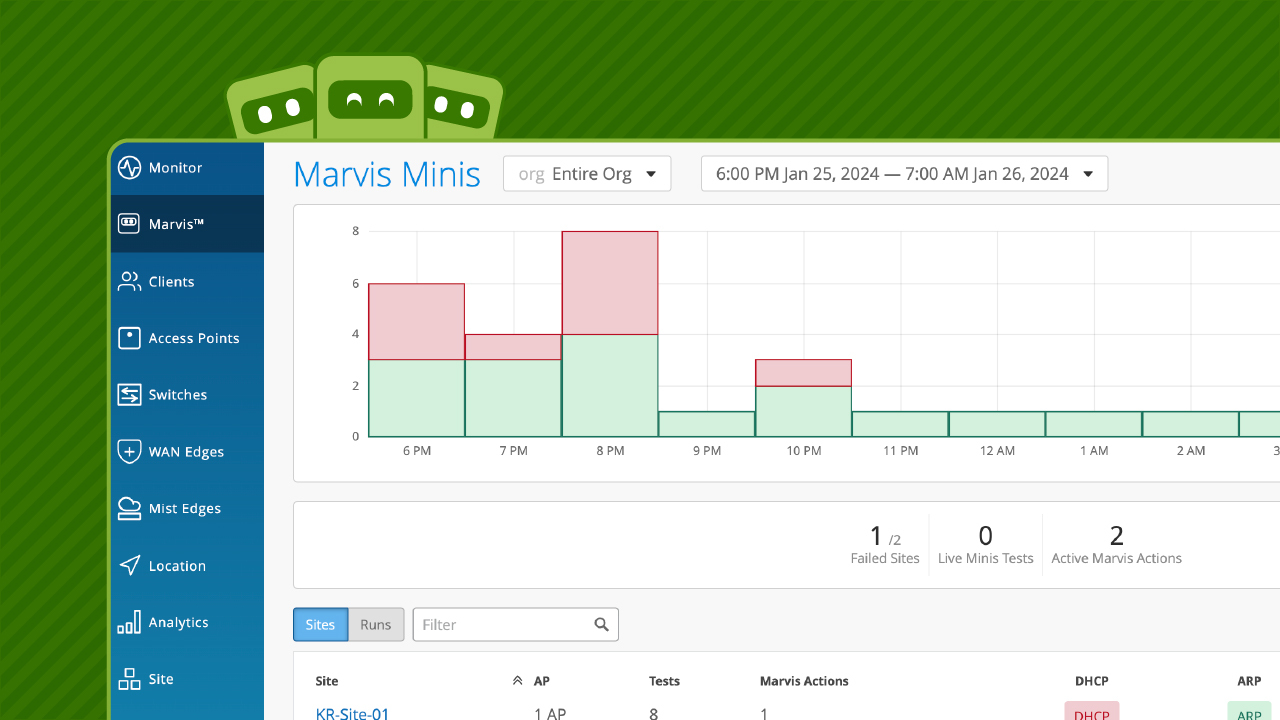
Marvis Minis: Move from Reactive to Proactive Network Management (demo)
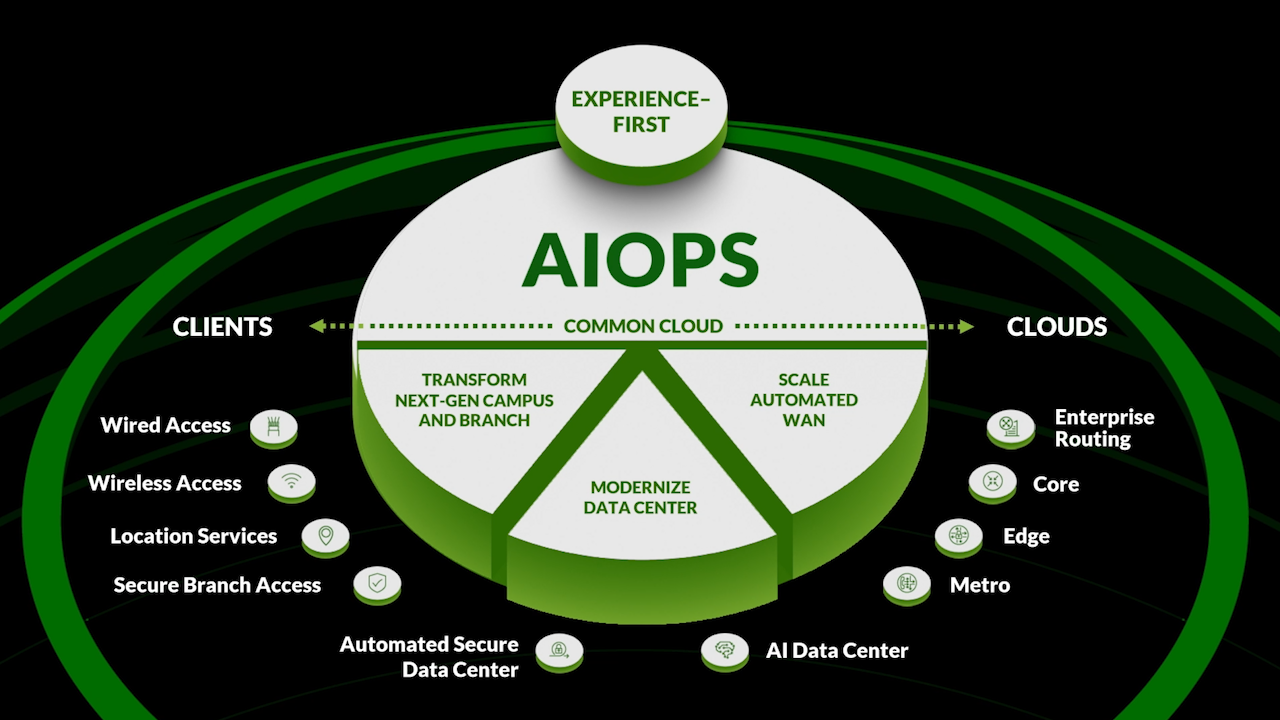
Juniper AI-Native Networking Platform: Deliver Elevated Experiences Across Every Domain (explainer)
Looking for something?
Check out these hand-curated topics and series. Consume the best networking ideas from the industry and Juniper!
Podcasts
Listen to our latest conversations
The AI in the channel episode with Alex Whitford from Partnerships Unraveled

Episode 25: Trust, Verify, Automate: AI’s Role in Modern Managed Services

AI + Authenticity Episode

Episode 24: Agentic AI and the Future of Intelligence with Richard Socher

Episode 23: The Road to Self-Driving Networks with Marvis























