Juniper Secure Edge Demo: CASB and DLP Use Cases
CASB and DLP demystified in 15 quick minutes.
In this highly informative 15-minute demo, you’ll learn helpful, real-world use cases for Cloud Access Security Broker (CASB) and Data Loss Prevention (DLP). Juniper recently added CASB and DLP into Secure Edge, a cloud-delivered security offering. When combined with Juniper's unique SD-WAN solution driven by Mist AI™, network operators now have a full-stack SASE solution with visibility into both the edge and data center.
Watch this demo to learn how CASB provides insight into SaaS applications to ensure authorized access, threat prevention, and compliance, while DLP classifies and monitors data transactions, so that business-compliance requirements and data-protection rules are followed.
You’ll learn
Use cases for what CASB and DLP provide from a visibility perspective
How you can interface with users by coaching or asking for additional authentication
How to gain insight into trends from a user-behavior analytics perspective
Who is this for?
Transcript
0:07 so let me talk just a little bit about
0:10 casb dlp
0:12 casby is really more focused
0:15 on internet-based services and really
0:18 sas based services where
0:20 policies and compliance type policies
0:22 can be applied from a business
0:24 perspective so there are different types
0:26 of use cases there right
0:28 so for example
0:30 an organization might have sanctioned
0:32 applications where
0:34 their users can
0:36 save content right that would be
0:38 something like we do today with onedrive
0:40 and so forth
0:42 and uh
0:43 casby allows an organization to apply
0:46 policy to those types of interactions
0:48 with assass deployment it also allows
0:51 organizations to drill deeper into
0:54 content so for example they could say
0:56 what types of
0:58 pii information are users allowed to
1:01 deploy into a sas service or let's look
1:04 for pci data you know that type of stuff
1:07 so the policies that are deployed
1:09 can be very granular in nature
1:13 but that's not
1:14 the limit with casbi
1:17 organizations can also delve into any
1:19 other sas
1:21 interactions that their users have so
1:24 ignoring organizationally approved or
1:27 sanctioned applications
1:29 casbi policy can also look into
1:31 unsanctioned applications or what we
1:33 call shadow i.t things that users are
1:36 doing with their own applications and
1:40 organizations can apply policy to that
1:42 data as well
1:47 what you'll see here in this demo is
1:50 quite a few different use cases
1:52 for what
1:54 the casbi dlp capability provides us
1:57 from a visibility perspective
1:59 uh from the ability to block or monitor
2:02 what users are doing
2:04 and
2:05 interface with
2:07 with what users are attempting to do so
2:09 sometimes coaching user asking for
2:11 additional authentication
2:13 before actions are taken
2:15 and then it also gives us the visibility
2:18 into
2:19 trends so like from a user behavior
2:22 analytics perspective
2:24 given us
2:25 visibility into what users are doing and
2:27 potentially investigate and research
2:30 more
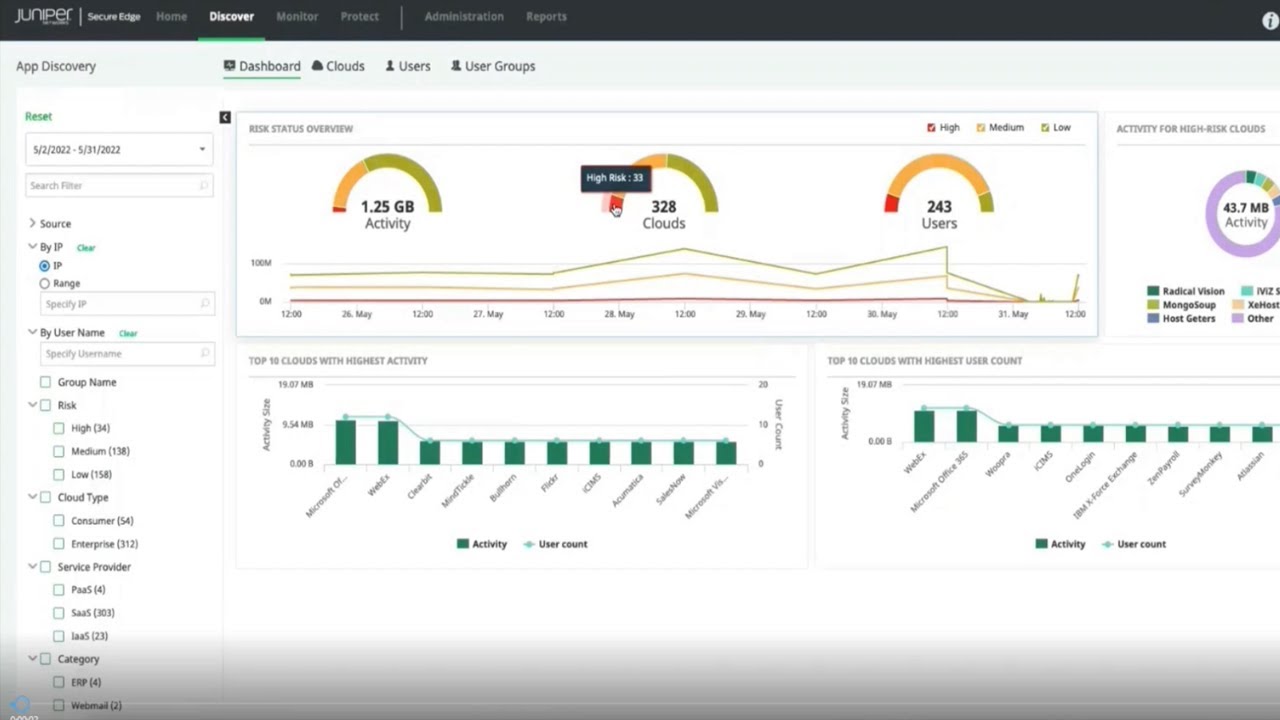
2:32 so the first use case here is just
2:34 simply what
2:35 visibility is provided in the cloud
2:37 applications and so this is just a
2:39 simple dashboard looking at the overall
2:41 risk of a deployment
2:43 um and what's high risk what's low risk
2:46 and
2:47 you know what am i seeing but if i go
2:50 specifically into the cloud workflow i
2:54 can see a
2:56 view of both sanctioned clouds and
2:59 unsanctioned cloud activity
3:01 so from an unsanctioned perspective we
3:03 might drill in and say
3:05 this certain service has a high risk
3:07 score and we might want to
3:09 block our users from
3:12 utilizing that service or simply log our
3:15 users uh
3:17 or you log that traffic if our users
3:19 utilize that service
3:21 so it's full visibility on on both
3:23 sanctioned and unsanctioned sides
3:25 and there's also the ability to drill
3:28 into the the cloud knowledge database so
3:31 we might
3:35 [Music]
3:44 are there are thousands of cloud-based
3:46 applications that are identified there
3:49 so let's drill into our first use case
3:51 this is a
3:53 user who has a document that has
3:56 uh
3:57 uh that has credit card numbers
3:58 associated with it
4:00 and this user is going to attempt to
4:03 share this sensitive information in the
4:06 cloud
4:07 to
4:08 other
4:09 users the first user they attempt to
4:11 share it with
4:13 is a partner
4:14 that uh that is a sanctioned partner so
4:17 so it's something that that would
4:18 normally be allowed it's okay to share
4:20 this information but the second user
4:22 is a
4:24 is a user in a domain that we don't
4:26 identify and we don't know about an
4:29 individual user so consider the first
4:31 user to be a sanctioned user should get
4:33 the info the second user
4:36 is not a sanction user for this at least
4:38 for this info
4:40 so the first thing we'll do here is now
4:42 that we've shared this document um
4:44 we're going to to take a look at uh the
4:48 sharing the sharing details of this
4:51 initially if you just look at it you'll
4:52 notice that both of those users are
4:55 listed as
4:57 users that we've shared this document
4:59 with
5:00 but because we've deployed a policy that
5:03 says
5:04 for certain domains we allow this
5:06 information to be shared and for others
5:08 please prohibit it
5:11 you'll see that when we take a another
5:13 quick look at it that one of the users
5:16 has been prohibited from sharing so now
5:18 only the sanctioned user is allowed to
5:20 access this document and that was
5:22 because we're deploying a cloud-based
5:25 policy
5:26 that prohibits this information from
5:28 being shared to certain users so what
5:30 does that this policy look like
5:32 if we look in details at this policy
5:34 it's created as
5:36 a dlp scan
5:38 in the cloud-based policy and it's
5:41 applied to
5:43 our
5:44 application
5:46 to our to our office application
5:49 and it's based on pci data
5:52 and we have to create a context for this
5:55 policy that we're applying we're going
5:57 to call this
5:58 um a sharing policy right
6:00 it's all based on
6:02 how we're going to share data
6:04 in the cloud and then the other thing
6:07 that we are able to do here is create a
6:09 white list of domains that we're going
6:12 to allow this information to be shared
6:14 to
6:15 and so we've created two domains um
6:18 actionable cosby and finance book both
6:21 of those are
6:23 sanctioned domains
6:25 then what's the action that we take
6:27 if it is an unsanctioned user we remove
6:30 that collaboration and that was what we
6:32 did in this example where we removed
6:35 that the collaboration automatically you
6:37 saw that originally
6:40 all right
6:41 let's move on to a second use case here
6:43 where a user is attempting to
6:46 upload information to their personal
6:49 onedrive so what you'll see here is
6:51 first the activity of the user the user
6:54 is going into their personal onedrive
6:57 account
6:59 and once they get into onedrive
7:02 they're going to select a document
7:06 that they're going to upload to that
7:09 account
7:10 or at least attempt to upload to that
7:12 account
7:16 and again we've created this policy
7:18 based on sensitive information but when
7:20 the user tries to do that not only are
7:22 they blocked but they're also coached
7:23 and there's they're they're basically
7:26 steered towards their corporate onedrive
7:28 rather than their personal onedrive to
7:31 utilize
7:32 and upload information
7:35 now this is because we've applied a
7:36 policy that says do not allow pci
7:38 uploads to personal accounts
7:41 but we would allow upload of information
7:43 to an organizational
7:45 account
7:47 so what does this policy look like then
7:50 when we
7:51 deploy it in the interface
7:53 we defined this as
7:56 as a pci upload policy right so we've
7:59 we've called it uh prevent a pci upload
8:02 to a personal account and it's again
8:04 a dlp
8:06 type policy
8:08 and then the first thing that we have to
8:10 do is define the context for that so
8:13 this is the upload of information to an
8:15 unsanctioned application the
8:16 unsanctioned application in this cr in
8:18 this case is a personal onedrive account
8:22 and the activity that the policy is
8:25 based on
8:26 is the upload of information
8:29 and we could also apply to a download of
8:31 information just for reference but in
8:33 this case we applied it to an upload
8:37 and then the content that we're scanning
8:38 for is pci data if there's pci data in
8:41 it prevent it from being uploaded right
8:44 there of course other types of data that
8:46 we can uh identify the context for
8:50 again also for
8:52 the who who or how does this apply we're
8:55 we're defining this based on users but
8:57 it could be defined for example based on
8:58 ip address or device and so forth
9:02 so once we've identified the context
9:04 then we need to determine the action in
9:06 this case we're going to deny
9:09 the attempt to upload pci information to
9:11 a personal account
9:13 and not only that we're going to
9:15 provide a notification to the user
9:19 the next use case is using salesforce so
9:23 in this case a user is attempting to
9:26 export
9:28 information from salesforce
9:30 now the rule that we're going to apply
9:32 here is going to request or require the
9:36 user
9:37 to
9:37 [Music]
9:39 essentially provide another
9:41 set of authentication information in
9:44 order to proceed so we're going to
9:45 require that they provide additional
9:47 credentials
9:49 in order to proceed with the sales force
9:51 export
9:53 so once they're notified then they're
9:55 provided access
9:57 to the
9:59 mfa integration
10:00 and once that is successfully
10:02 authenticated then they're allowed to
10:04 proceed
10:06 so what does this policy look like in
10:08 our casbi interface
10:11 this is a little bit unique
10:13 it's identified with the activity of
10:16 doing a salesforce export
10:18 so there's no content inspection type
10:20 defined here
10:22 but you'll see this defined as
10:23 salesforce export here in a second so we
10:25 identified this or associated with the
10:28 salesforce
10:29 application
10:31 and the activity that we're associating
10:34 it with is is an export and you'll see
10:36 that with with salesforce there are a
10:37 lot of other capabilities that could be
10:39 integrated here
10:41 but we're we're triggering on just a
10:43 sales force export based on user
10:46 we're going to allow this
10:48 and log it but then also as a secondary
10:50 action we're going to request continuous
10:53 authentication from
10:55 an mfa profile that we've defined
11:01 and then
11:02 one more use case here is our ability to
11:05 coach users on
11:07 downloading information
11:09 so we have an application here that has
11:11 personal information
11:13 deployed in it social security numbers
11:15 phone numbers address information and so
11:18 forth
11:19 and a user is going to attempt to
11:22 download this information or this this
11:25 document
11:26 because of a policy that we've defined
11:28 here
11:30 we're going to request additional
11:32 justification from the user before
11:33 they're allowed to proceed so we will
11:36 allow this activity to occur
11:38 but
11:39 the customer or the user is going to
11:41 have to
11:43 add additional justification before they
11:46 proceed and so once they justify their
11:48 activity
11:49 then the download
11:51 of the document is allowed
11:54 so just one more quick reference as to
11:56 how that policy is created this looks
12:00 very familiar very similar to the other
12:01 policies it's based on a dlp scan again
12:06 and
12:07 then we have to define the context
12:08 around that so the context here
12:11 is going to be a file sharing context
12:14 the ability to download content from
12:17 office 365.
12:19 so we selected the the download activity
12:24 and you'll also notice that
12:27 the rule template in this case is
12:29 associated with
12:31 uh pii information right we have pci i
12:35 think in the past in this case it's a
12:37 pii
12:39 and we're also going to deploy this
12:41 for all users
12:44 and then the activity that we take again
12:46 is to allow it but in this case our
12:48 secondary action is coaching the user to
12:51 identify
12:52 a justification
12:53 before they proceed
12:57 a couple more demos here within casbi so
13:00 we have the ability to do cloud data
13:02 discovery so think about
13:05 deployments in the cloud where we might
13:07 not have had historical visibility into
13:10 what's going on but
13:12 maybe we need to for example
13:14 sweep
13:16 box and determine
13:19 what information
13:20 is currently resident in in box that may
13:24 not comply with
13:26 our sensitive information policy
13:29 so we've already created
13:31 a report based on that we've swept a box
13:35 based on certain policies of sensitive
13:38 information we've classified as
13:39 sensitive information
13:41 and this report then shows us what is
13:44 currently residing in the organizational
13:46 box
13:47 and associated with that
13:50 the details of that content so credit
13:53 card numbers uh social security numbers
13:56 and so forth all within that report
14:00 and then the final use case here is
14:02 looking at behavior analytics so we have
14:04 different ways to look at anomalous
14:06 activity
14:07 one of the things we might do here is
14:10 look at
14:12 download activity by various users so if
14:15 we drill into one of these we're going
14:17 to click into this one i believe thomas
14:20 is the user here
14:22 there's been a lot of download activity
14:24 by thomas and so we see a lot of spikes
14:27 in activity maybe some of it is normal
14:30 maybe some of it isn't but within our
14:32 user
14:33 behavior analytics capability we can
14:36 look at trends and so you see
14:38 the application has already identified a
14:40 lot of green dots those green dots are
14:43 what we might consider to be usual
14:45 activity
14:46 the red dot is an outlier
14:48 the nice thing about this is it's a
14:50 three-dimensional chart here and so we
14:52 can look at times of the day
14:54 and see how
14:56 the download activity
14:58 is
14:59 uh trending through different times of
15:01 the day
15:02 but then also we can look at it through
15:04 days of the week so based on weekends or
15:08 weekdays
15:09 how has that activity trended and we can
15:12 definitely see why that one
15:14 significant amount of download was was
15:16 an outlier
15:18 based on our reporting





