SSL Certificates Support on SRX Series Firewalls
Firewall acting as SSL proxy manages SSL connections between the client at one end and the server at the other end. SSL proxy server ensures secure transmission of data with encryption technology. SSL relies on certificates and private-public key exchange pairs to provide the secure communication. In this topic, you learn about how to generate and install SSL certificate on your security device for SSL connections.
Configuring and Loading SSL Certificates
Figure 1 displays an overview of how SSL proxy is configured. Configuring SSL proxy includes:
-
Configuring the root CA certificate
-
Loading a CA profile group
-
Configure SSL proxy profile and associate root CA certificate and CA profile group
-
Applying an SSL proxy profile to a security policy
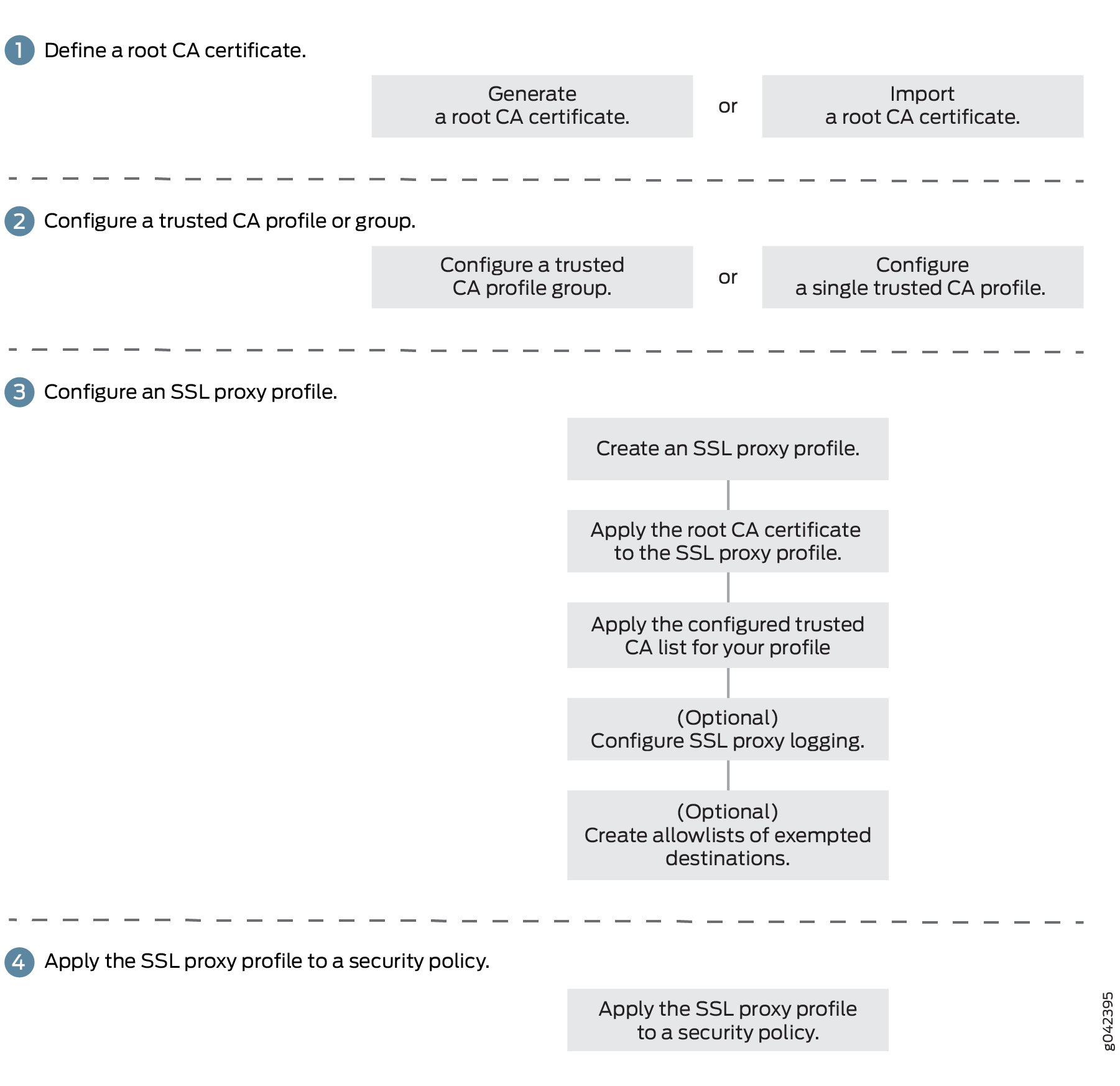
To configure the root CA certificate, see Enroll a Certificate.
Lets discuss these procedures in detail in the following sections:
Ignore Server Authentication Failure
Server Authentication
Implicit trust between the client and the device (because the client accepts the certificate generated by the device) is an important aspect of SSL proxy. It is extremely important that server authentication is not compromised; however, in reality, self-signed certificates and certificates with anomalies are in abundance. Anomalies can include expired certificates, instances of common name not matching a domain name, and so forth.
Server authentication is governed by setting the ignore-server-auth-failure option in the SSL proxy profile. The results of setting this option is available in Table 1.
[edit]user@host#set services ssl proxy profile profile-name actions ignore-server-auth-failure
|
SSL Proxy Profile Action |
Results |
|---|---|
|
The ignore-server-auth-failure option is not set (Default option) |
|
|
The ignore-server-auth-failure option is set |
|
Client Authentication
Currently, client authentication is not supported in SSL proxy. If a server requests client authentication, a warning is issued that a certificate is not available. The warning lets the server determine whether to continue or to exit.
Working with the Certificate Revocation Lists for SSL Proxy
Certificate authority (CA) periodically publishes a list of revoked certificate using a certificate revocation list (CRL). The security device downloads and caches the most recently issued CRL. The CRL contains the list of digital certificates with serial numbers that have been canceled before their expiration date. See also Revoke a Certificate and Online Certificate Status Protocol and Certificate Revocation Lists.
CA revokes the issued certificate if there is any chance that the certificate is compromised. Some other reasons for revoking a certificate are:
-
Unspecified (no particular reason is given).
-
Private key associated with the certificate or CA that issued the certificate was compromised.
-
The owner of the certificate is no longer affiliated with the issuer of the certificate
-
Another certificate replaces the original certificate.
-
The CA that issued the certificate has ceased to operate.
-
The certificate is on hold pending further action. It is treated as revoked but might be accepted in the future.
When a participating device uses a digital certificate, it checks the certificate signature and validity. By default, CRL verification is enabled on SSL proxy profile.
Security devices support certificate revocation list (CRL) validation, which involves checking for revoked certificates from designated servers. By default, CRL validation is enabled for SSL proxy profiles. This feature can be enabled or disabled based on specific security requirements.
You can allow or drop the sessions when a CRL information is not available for reasons such as failed CRL download or unavailability of the CRL path in the root or intermediate certificate.
-
Allow the sessions when CRL information is not available.
[edit] user@host# set services ssl proxy profile profile-name actions crl if-not-present allow
-
Drop the sessions when CRL information is not available.
[edit] user@host# set services ssl proxy profile profile-name actions crl if-not-present drop
-
Configure your security device to accept a certificate without a reliable confirmation available on the revocation status and allow the sessions when a certificate is revoked and the revocation reason is on hold.
[edit] user@host# set services ssl proxy profile profile-name actions crl ignore-hold-instruction-code
See Revoke a Certificate for details.
SSL Performance Enhancements
SSL performance enhancement includes following features:
- Optimizing the SSL Performance
- Session Resumption
- Session Renegotiation
- Negotiating StartTLS for SMTP Sessions
- Dynamic Resolution of Domain Names
Optimizing the SSL Performance
The SSL/TLS handshake is a CPU-intensive process. Since SSL/TLS is the most widely used security protocol on the web, it’s performance results in significant impact on the web performance.
You can use the following options for optimizing the performance:
-
Use optimized RSA key exchanges
-
Use Authenticated Encryption with Associated Data (AEAD)—AES128-CBC-SHA, AES256-CBC-SHA
-
Maintaining certificate cache—Certificate cache stores the interdicted server certificate along with the server certificate details. During SSL/TLS handshake, SSL proxy can present the cached interdicted certificate to client instead of generating the new interdicted certificate.
Improving the SSL performance results in improved website performance without compromising security and maximized user experience.
You can optionally configure the following settings for your certificate cache. However, we recommend retaining the default values.
Example:
-
(Optional) Set the certificate cache timeout value (example- 300 seconds) .
[edit]user@host# set services ssl proxy global-config certificate-cache-timeout 300In this example, the certificate cache stores the certificate details for 300 seconds. The default timeout value is 600 seconds.
-
(Optional) Disable the certificate cache.
[edit]user@host# set services ssl proxy global-config disable-cert-cacheWhen you disable certificate cache, the device allows the SSL full handshake for a new connection. By default certificate cache is enabled.
-
(Optional) Invalidate the existing certificate cache.
[edit]user@host# set services ssl proxy global-config invalidate-cache-on-crl-updateIn this example, the device invalidates the existing certificate cache when certificate revocation list (CRL) is updated. By default, invalidate certificate cache on CRL update is disabled.
Session Resumption
SSL session resumption provides a mechanism to resume a previous session using already negotiated session IDs. Session resumption saves the client and server the computational overhead of a complete SSL handshake and generation of new primary keys. Session resumption shortens the handshake process and accelerates SSL transactions resulting in improved performance while maintaining appropriate level of security.
TLS 1.2 supports session resumption with session identifiers and session tickets mechanisms. An SSL session resumption includes the following steps:
-
A session caching mechanism caches session information, such as the pre-master secret key and agreed-upon ciphers for both the client and server.
-
Session ID identifies the cached information.
-
In subsequent connections both parties agree to use the session ID to retrieve the information rather than create a pre-master secret key.
Starting in Junos OS Release 22.1R1, TLS 1.3 supports session resumption using a pre-shared key (PSK) in SSL proxy. Session resumption using PSK allows resuming a session with a previously established shared secret key to reduce SSL handshake overhead.
PSK is a unique encryption key derived from the initial TLS handshake. After a successful TLS handshake, the server sends a PSK identity to the client. The client uses that PSK identity in the future handshakes to negotiate the use of associated PSK to resume the session.
An SSL session resumption with TLS1.3 includes the following steps:
-
After an initial TLS handshake, the server sends a new Session Ticket message to the client, which contains the PSK identity (encrypted copy of the PSK).
- Next time, when the client attempts to resume the session, it sends the same Session Ticket to the server in the Hello message.
- The server decrypts the message, identifies the PSK, and retrieves the session information from its cache to resume the session.
An SSL-I (SSL initiation) uses PSK with ECDHE key exchange mode, and SSL-T (SSL termination) uses PSK and PSK with ECDHE exchange modes.
SSL proxy session supports interoperability between TLS1.3 and TLS1.2 and earlier versions on two ends of a connection for session resumption.
By default, session resumption is enabled for SSL proxy. You can clear the session resumption or re-enable as per your requirements.
- To clear the session resumption:
[edit] user@host# set services ssl proxy profile ssl actions disable-session-resumption
- To re-enable session resumption:
[edit] user@host# delete services ssl proxy profile ssl actions disable-session-resumption
Use the following command to configure the session timeout value.
[edit] user@host# set services ssl proxy global-config session-cache-timeout session-cache-timeout
Session Renegotiation
Firewalls support session renegotiation. After a session is created and SSL tunnel transport is established, a change in SSL parameters requires renegotiation. SSL proxy supports both secure (RFC 5746) and nonsecure (TLS v1.0, TLS v1.1, and TLS v1.2) renegotiation. When session resumption is enabled, session renegotiation is useful in the following situations:
-
Cipher keys need to be refreshed after a prolonged SSL session.
-
Stronger ciphers need to be applied for a more secure connection.
If you modify the SSL proxy profile by changing a certificate, or cipher strength, or trusted CA list, then the system flushes the cache entries when you commit the modified policy. In this case, a full handshake is required to establish the new SSL parameters. (There is no impact to non-SSL sessions.)
If the SSL proxy profile is not altered, cache entries corresponding to that profile are not flushed and the session continues.
Negotiating StartTLS for SMTP Sessions
The StartTLS enables an SMTP session from an initial plain TCP connection to a more secure TLS connection. StartTLS allows SMTP session between the server and client over the TLS layer after successful negotiation between the peers. StartTLS upgrades an existing insecure plain SMTP connection to a secure SSL/TLS connection.
You can set a threshold that allows you to decide how long to wait before ignoring the session if StartTLS is not received from the client.
You can configure the following options:
- byte-threshold—Minimum bytes of unencrypted session allowed before ignoring the session if StartTLS is not received from the client. Range 100 to 300.
- packet-threshold—Number of unencrypted packets allowed in client-to-server direction before ignoring the session if StartTLS is not received from the client. Range 1 to 15.
Example:
[edit] user@host# set services ssl proxy global-config mail-threshold byte-threshold 100
In this exaple, SSL proxy allows 100 bytes of plain (unencrypted) SMTP traffic. After reaching 100 bytes, it ignores the session if StartTLS is not received from the client.
[edit] user@host# set services ssl proxy global-config mail-threshold packet-threshold 2
In this example, SSL proxy allows 2 packets of plain (unencrypted) SMTP traffic. After reaching 2 packets, it ignores the session if StartTLS is not received from the client.
Dynamic Resolution of Domain Names
The IP addresses associated with domain names are dynamic and can change at any time. Whenever a domain IP address changes, it is propagated to the SSL proxy configuration (similar to what is done in the firewall policy configuration).
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
