SSL Proxy
SSL proxy acts as an intermediary, performing SSL encryption and decryption between the client and the server. Better visibility into application usage can be made available when SSL forward proxy is enabled.
SSL Proxy Overview
For the complete list of supported features and platforms, see SSL Proxy in Feature Explorer.
Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL, also called Transport Layer Security (TLS), ensures the secure transmission of data between a client and a server through a combination of privacy, authentication, confidentiality, and data integrity. SSL relies on certificates and private-public key exchange pairs for this level of security.
SSL proxy is transparent proxy that performs SSL encryption and decryption between the client and the server.
- How Does SSL Proxy Work?
- SSL Proxy with Application Security Services
- Leveraging Dynamic Application Identification
- Types of SSL Proxy
- Supported SSL Protocols
- Benefits of SSL Proxy
- Logical Systems Support
- Limitations
How Does SSL Proxy Work?
SSL proxy provides secure transmission of data between a client and a server through a combination of following:
-
Authentication-Server authentication guards against fraudulent transmissions by enabling a Web browser to validate the identity of a webserver.
-
Confidentiality - SSL enforces confidentiality by encrypting data to prevent unauthorized users from eavesdropping on electronic communications; thus ensures privacy of communications.
-
Integrity- Message integrity ensures that the contents of a communication are not tampered.
SRX Series Firewall acting as SSL proxy manages SSL connections between the client at one end and the server at the other end and performs following actions:
-
SSL session between client and SRX Series- Terminates an SSL connection from a client, when the SSL sessions are initiated from the client to the server. The SRX Series Firewall decrypts the traffic, inspect it for attacks (both directions), and initiates the connection on the clients’ behalf out to the server.
-
SSL session between server and SRX Series - Terminates an SSL connection from a server, when the SSL sessions are initiated from the external server to local server. The SRX Series Firewall receives clear text from the client, and encrypts and transmits the data as ciphertext to the SSL server. On the other side, the SRX Series decrypts the traffic from the SSL server, inspects it for attacks, and sends the data to the client as clear text.
-
Allows inspection of encrypted traffic.
SSL proxy server ensures secure transmission of data with encryption technology. SSL relies on certificates and private-public key exchange pairs to provide the secure communication. For more information, see SSL Certificates.
To establish and maintain an SSL session between the SRX Series Firewall and its client/server, the SRX Series Firewall applies security policy to the traffic that it receives. When the traffic match the security policy criteria, SSL proxy is enabled as an application service within a security policy.
SSL Proxy with Application Security Services
Figure 1 shows how SSL proxy works on an encrypted payload.
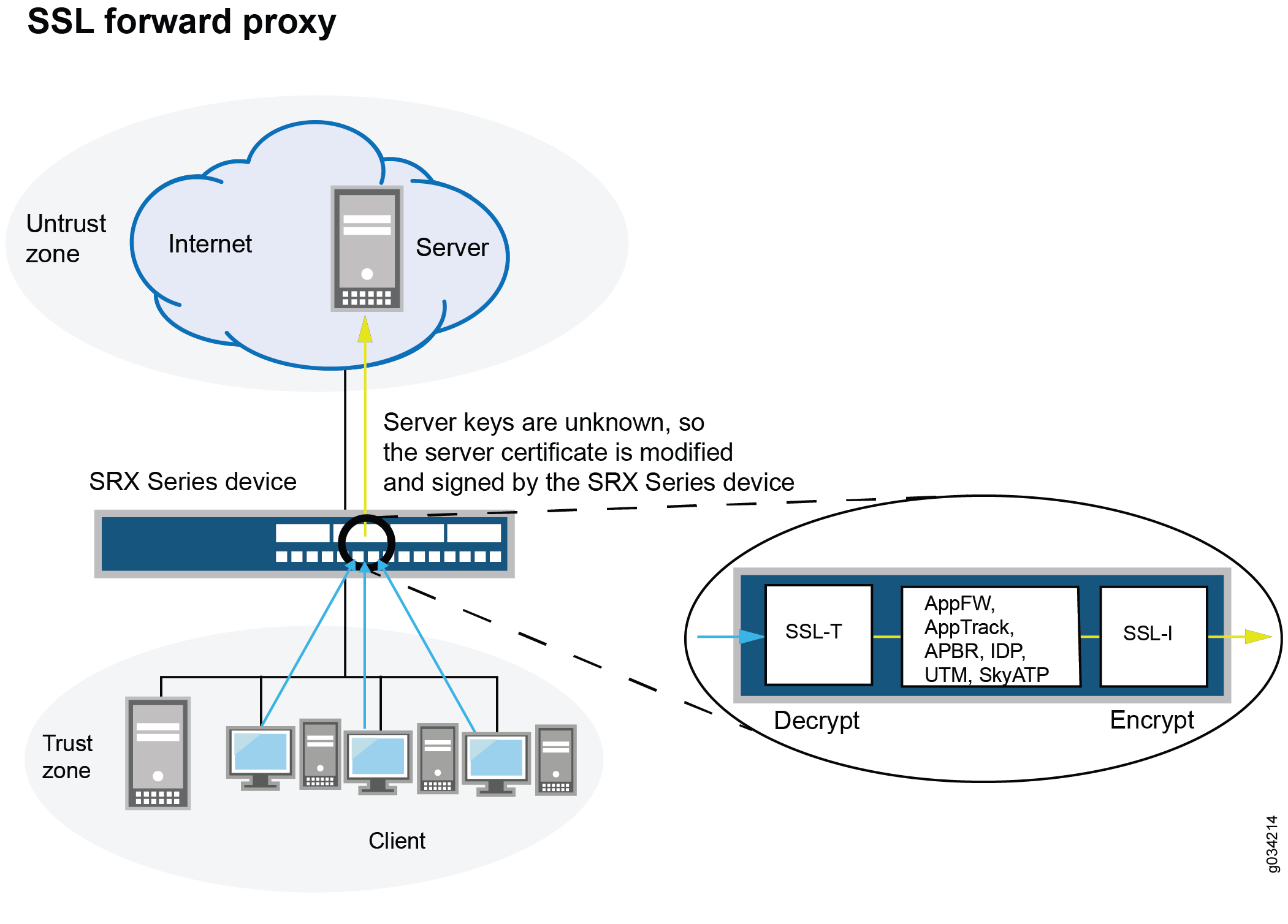
When Advanced Security services such as application firewall (AppFW), Intrusion Detection and Prevention (IDP), application tracking (AppTrack), Content Security, and ATP Cloud is configured, the SSL proxy acts as an SSL server by terminating the SSL session from the client and establishing a new SSL session to the server. The SRX Series Firewall decrypts and then reencrypts all SSL proxy traffic.
IDP, AppFW, AppTracking, advanced policy-based routing (APBR), Content Security, ATP Cloud, and ICAP service redirect can use the decrypted content from SSL proxy. If none of these services are configured, then SSL proxy services are bypassed even if an SSL proxy profile is attached to a firewall policy.
With the implementation of SSL proxy, AppID can identify applications encrypted in SSL. SSL proxy can be enabled as an application service in a regular firewall policy rule. Intrusion Detection and Prevention (IDP), application firewall (AppFW), application tracking (AppTrack), advanced policy-based routing (APBR) services, Content Security, ATP Cloud, and Security Intelligence (SecIntel) can use the decrypted content from SSL proxy.
To determine if a feature is supported by a specific platform or Junos OS release, refer Feature Explorer
On the SSL payload, IDP can inspect attacks and anomalies; for example, HTTP chunk length overflow on HTTPS. On encrypted applications, such as Facebook, AppFW can enforce policies and AppTrack (when configured in the from and to zones) can report logging issues based on dynamic applications.
If none of the services (AppFW, IDP, or AppTrack) are configured, then SSL proxy services are bypassed even if an SSL proxy is attached to a firewall policy.
The IDP module will not perform an SSL inspection on a session if an SSL proxy is enabled for that session. That is, if both SSL inspection and SSL proxy are enabled on a session, SSL proxy will always take precedence.
Leveraging Dynamic Application Identification
SSL proxy uses application identification services to dynamically detect if a particular session is SSL encrypted. SSL proxies are allowed only if a session is SSL encrypted. The following rules apply for a session:
-
Session is marked Encrypted=Yes in the application system cache. If the session is marked Encrypted=Yes, it indicates that the final match from application identification for that session is SSL encrypted, and SSL proxy transitions to a state where proxy functionality can be initiated.
-
Session is marked Encrypted=No in the application system cache. If a non-SSL entry is found in the application system cache, it indicates that the final match from application identification for that session is non-SSL and SSL proxy ignores the session.
-
An entry is not found in the application system cache. This can happen on the first session, or when the application system cache has been cleaned or has expired. In such a scenario, SSL proxy cannot wait for the final match (requires traffic in both directions). In SSL proxy, traffic in reverse direction happens only if SSL proxy has initiated an SSL handshake. Initially, for such a scenario SSL proxy tries to leverage prematch or aggressive match results from application identification , and if the results indicate SSL, SSL proxy will go ahead with the handshake.
-
Application identification fails due to resource constraints and other errors. Whenever the result from application identification is not available, SSL proxy will assume static port binding and will try to initiate SSL handshake on the session. This will succeed for actual SSL sessions, but it will result in dropped sessions for non SSL sessions.
Types of SSL Proxy
SSL proxy is a transparent proxy that performs SSL encryption and decryption between the client and the server. SRX acts as the server from the client’s perspective and it acts as the client from the server’s perspective. On SRX Series Firewalls, client protection (forward proxy) and server protection (reverse proxy) are supported using same echo system SSL-T-SSL [terminator on the client side] and SSL-I-SSL [initiator on the server side]).
SRX Series Firewall support following types of SSL proxy:
-
Client-protection SSL proxy also known as forward proxy—The SRX Series Firewall resides between the internal client and outside server. Proxying outbound session, that is, locally initiated SSL session to the Internet. It decrypts and inspects traffic from internal users to the web.
-
Server-protection SSL proxy also known as reverse proxy—The SRX Series Firewall resides between the internal server and outside client. Proxying inbound session, that is, externally initiated SSL sessions from the Internet to the local server.
For more information on SSL forward proxy and reverse proxy, see Configuring SSL Proxy.
Supported SSL Protocols
The following SSL protocols are supported on SRX Series Firewalls for SSL initiation and termination service:
-
TLS version 1.0—Provides authentication and secure communications between communicating applications.
-
TLS version 1.1—This enhanced version of TLS provides protection against cipher block chaining (CBC) attacks.
-
TLS version 1.2 — This enhanced version of TLS provides improved flexibility for negotiation of cryptographic algorithms.
-
TLS version 1.3 — This enhanced version of TLS provides improved security and better performance.
When you use TLS 1.3, the SRX Series Firewall supports the secp256r1 group for key-exchange for establishing connection with the server. If the server supports only secp384r1, then the connection will be terminated.
SRX Series Firewalls support SNI for SSL initiation (SSL-I) process. Server Name Indication (SNI) is an extension of the SSL/TLS header, which carries the destination server's hostname during the HTTPS "Client Hello" exchange in clear text before the SSL handshake is complete.
Benefits of SSL Proxy
-
Decrypts SSL traffic to obtain granular application information and enable you to apply advanced security services protection and detect threats.
-
Enforces the use of strong protocols and ciphers by the client and the server.
-
Provides visibility and protection against threats embedded in SSL encrypted traffic.
-
Controls what needs to be decrypted by using Selective SSL Proxy.
Logical Systems Support
It is possible to enable SSL proxy on firewall policies that are configured using logical systems; however, note the following limitations:
-
The “services” category is currently not supported in logical systems configuration. Because SSL proxy is under “services,” you cannot configure SSL proxy profiles on a per-logical-system basis.
-
Because proxy profiles configured at a global level (within “services ssl proxy”) are visible across logical system configurations, it is possible to configure proxy profiles at a global level and then attach them to the firewall policies of one or more logical systems.
Limitations
On all SRX Series Firewalls, the current SSL proxy implementation has the following connectivity limitations:
-
The SSLv3.0 protocol support is deprecated.
-
The SSLv2 protocol is not supported. SSL sessions using SSLv2 are dropped.
-
Only X.509v3 certificate is supported.
-
Client authentication of SSL handshake is not supported.
-
SSL sessions where client certificate authentication is mandatory are dropped.
-
SSL sessions where renegotiation is requested are dropped.
- On SRX Series Firewalls, for a particular session, the SSL proxy is only enabled if a relevant feature related to SSL traffic is also enabled. Features that are related to SSL traffic are IDP, application identification, application firewall, application tracking, advanced policy-based routing, Content Security, ATP Cloud, and ICAP redirect service. If none of these features are active on a session, the SSL proxy bypasses the session and logs are not generated in this scenario.
- SRX Series Firewalls operating in Multinode High Availability setup do not support the SSL proxy functionality.
See Also
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
