SSL Decryption Mirroring
SSL decryption mirroring feature enables you to monitor SSL decrypted application traffic entering and exiting the SRX Series Firewall. For more information on SSL decryption mirroring, read this topic.
Understanding SSL Decryption Mirroring Functionality
SSL decryption mirroring functionality for SSL forward proxy and for SSL reverse proxy is introduced.
SSL decryption mirroring feature enables you to monitor SSL decrypted application traffic entering and exiting the SRX Series Firewall. When you enable this feature, the SRX Series Firewall uses an Ethernet interface—the configured SSL decryption mirroring interface—to forward a copy of the decrypted SSL traffic to a trusted traffic collection tool or a network analyzer for inspection and analysis. Typically, you connect this external monitoring device to the SSL decryption mirroring interface through a switching device. The external mirror traffic collector port is the port (or interface) that receives the copy of the decrypted traffic from the SSL decryption mirroring interface on the SRX Series Firewall.
To use the SSL decryption mirroring feature, you define an SSL proxy profile, and apply it to the security policy. The security policy rule allows you to define traffic that you want the device to decrypt. When you attach the SSL proxy profile to the security policy rule, the traffic matching the security policy rule is decrypted. The SSL decryption mirroring interface delivers a copy of decrypted HTTPS and STARTTLS (POP3S/SMTPS/IMAPS) traffic to a trusted external device or traffic collection tool for inspection and analysis.
The embedded 5-tuple data of the decrypted IP packet includes the same following values as the encrypted IP packets:
-
Source IP address
-
Destination IP address
-
Source port number
-
Destination port number
-
Protocol number
Retaining the same 5-tuple data without reconfiguration ensures that the decrypted traffic is saved in packet-capturing format (Wireshark) and you can replay the data later.
Only TCP sequence numbers and ACK numbers are constructed based on the actual decrypted payload forwarded on the SSL decryption mirroring port. If the decrypted packet size exceeds the maximum transmission unit (MTU) size of the SSL decryption mirroring port, then the decrypted payload is divided into multiple TCP segments based on the MTU size requirements.
- SSL Decryption Mirroring Before or After Policy Enforcement
- SSL Decryption Mirroring Support
- Benefits of SSL Decryption Mirroring
- Limitations
- SSL Decryption Mirroring Support in Chassis Cluster
SSL Decryption Mirroring Before or After Policy Enforcement
By default, the SRX Series Firewall forwards the SSL decrypted payload to the mirror port before Junos OS enforces Layer 7 security services, including IDP, Juniper ATP Cloud, and Content Security. This option allows you to replay events and analyze traffic that generates a threat or triggers a drop action.
You can also configure mirroring of the decrypted traffic after enforcing the security policy. With this option, only traffic that is forwarded through the security policy is mirrored. However, if the decrypted payload is modified while enforcing the security policy, the modified decrypted payload is forwarded on the mirror port. Similarly, if the decrypted traffic is dropped because of policy enforcement (for example, when a threat is detected in the decrypted traffic), that particular decrypted traffic is not forwarded on the mirror port.
SSL Decryption Mirroring Support
-
Supported for SSL forward proxy and SSL reverse proxy.
-
Supported for both IPv4 and IPv6 traffic.
-
The SSL decrypted traffic available on the mirror port is in cleartext format. All the cipher suites that are supported by SSL proxy support SSL decryption mirroring functionality. For the list of supported cipher suites, see SSL Proxy Overview.
Benefits of SSL Decryption Mirroring
-
Enables comprehensive data capture for auditing, forensic investigations, and historical purposes.
-
Provides data leak prevention.
-
Enables additional security processing done by third-party appliances for IDP, Content Security, and so on.
-
Provides insight about the threats involved.
Limitations
-
SSL decryption mirroring cannot be configured on the st0 tunnel interface.
SSL Decryption Mirroring Support in Chassis Cluster
SSL decryption mirroring feature is supported on redundant Ethernet (reth) interface on SRX Series Firewalls operating in a chassis cluster.
set interfaces reth20 redundant-ether-options redundancy-group 1 set interfaces reth20 unit 0 family inet
Configuring SSL Decryption Mirroring
This example shows how to enable mirroring of SSL decrypted traffic on an SRX Series Firewall.
Configuration
Step-by-Step Procedure
Use the following steps to configure the SSL decryption mirroring.
-
Define the SSL decryption mirroring interface with logical unit number 0.
user@host#set interfaces ge-0/0/2 unit 0 -
Specify the SSL decryption mirroring interface in the SSL proxy profile.
user@host#set services ssl proxy profile profile-1 mirror-decrypt-traffic interface ge-0/0/2.0Ge-0/0/2.0 is configured as designated SSL decryption mirroring interface.
-
Specify the MAC address of the of the external mirror traffic collector port.
user@host#set services ssl proxy profile profile-1 mirror-decrypt-traffic destination-mac-address 00:50:56:a6:5f:1f -
Create a security policy by specifying the match criteria for the traffic.
user@host#set security policies from-zone trust to-zone untrust policy policy-1 match source-address anyuser@host#set security policies from-zone trust to-zone untrust policy policy-1 match destination-address anyuser@host#set security policies from-zone trust to-zone untrust policy policy-1 match application any -
Attach the SSL proxy profile to the security policy rule.
user@host#set security policies from-zone trust to-zone untrust policy policy-1 then permit application-services ssl-proxy profile-name profile-1This configuration enables the external mirror traffic collector port (or interface) to receive the copy of the decrypted traffic from the SSL decryption mirroring interface on the SRX Series Firewall.
Results
From configuration mode, confirm your configuration by entering
the show services ssl proxy profile and show security
policies from-zone trust to-zone untrust policy commands. If
the output does not display the intended configuration, repeat the
configuration instructions in this example to correct it.
[edit]
user@host# show services ssl proxy profile profile-1
server-certificate Email_server_cert;
mirror-decrypt-traffic {
interface ge-0/0/2.0;
destination-mac-address 00:50:56:a6:5f:1f;
}
[edit]
user@host# show security policies from-zone trust to-zone untrust policy policy-1
match {
source-address any;
destination-address any;
application any;
}
then {
permit {
application-services {
ssl-proxy {
profile-name profile-1;
}
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Requirements
This example uses the following hardware and software components:
-
Any SRX Series Firewall with Junos OS Release 18.4R1 or later. This configuration example is tested for Junos OS Release 18.4R1.
No special configuration beyond device initialization is required before configuring this feature.
Before you begin:
-
Configure SSL proxy. See SSL Proxy Overview.
-
The SSL decryption mirroring interface that you configure doesn’t need to be part of any security zones.
-
Ensure that SSL decryption mirroring interface and the actual client-server SSL traffic processing interfaces are part of the same routing instance.
-
Ensure that the SSL decryption mirroring interface on the SRX Series Firewall and the external mirror traffic collector port must be part of the same broadcast domain.
You don’t need to configure a separate security policy to allow traffic from SRX Series Firewall to the SSL decryption mirroring interface..
Overview
In this example, configure an SSL forward proxy profile by specifying the name of the SSL decryption mirroring interface and the MAC address of the external mirror traffic collector port. Next, create a security policy and invoke the SSL proxy as application service on the permitted traffic. The traffic matching the security policy rule is decrypted. A copy of the decrypted SSL payload is then encapsulated into an IP packet and forwarded to the on the external mirror traffic collector port through SSL decryption mirroring interface.
Figure 1 illustrates the topology used in this example.
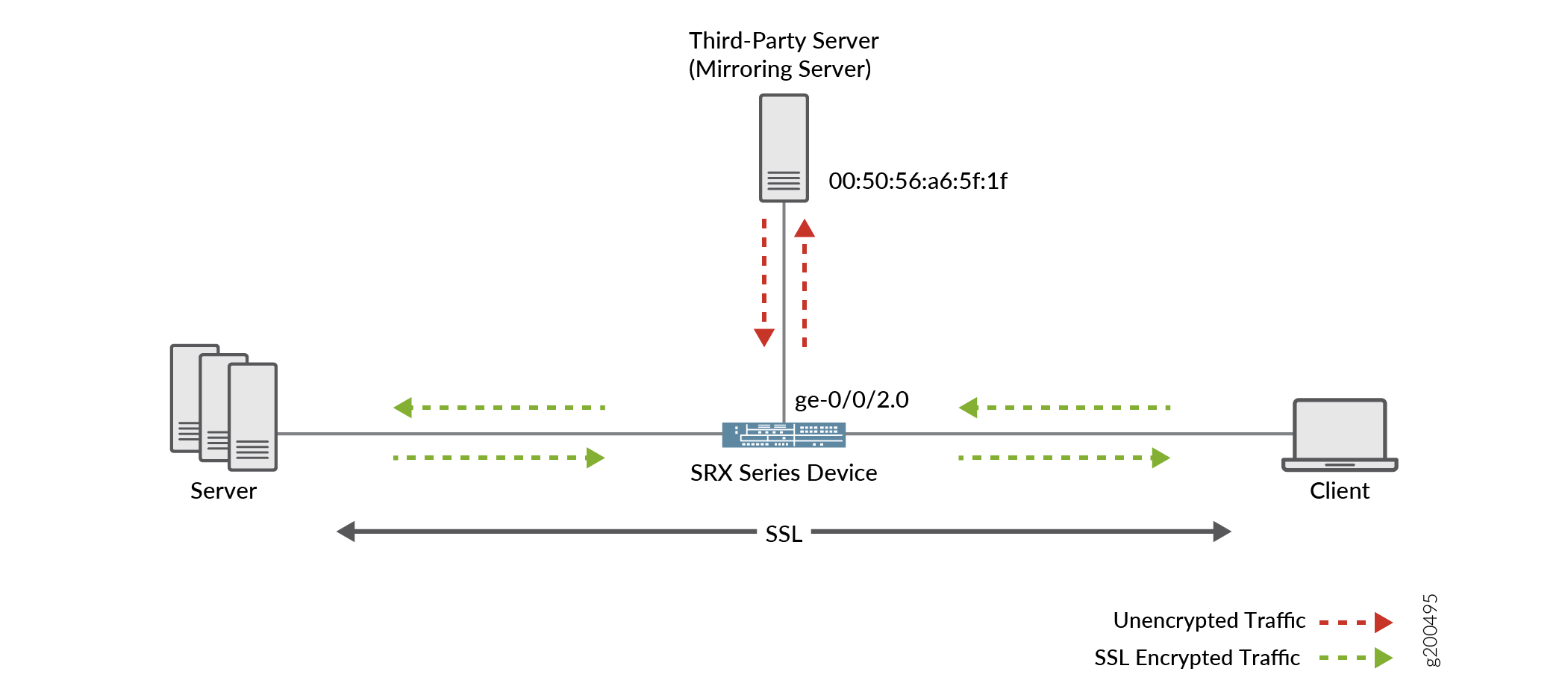
Table 1 provides the details of the parameters used in this example.
|
Parameter |
Name |
|---|---|
|
SSL decryption mirroring interface on SRX Series Firewall |
ge-0/0/2.0 |
|
MAC address of the external mirror traffic collector port |
00:50:56:a6:5f:1f |
|
SSL proxy profile |
profile-1 |
|
Security policy |
policy 1 |
Verification
Verify SSL Proxy Configuration
Purpose
Confirm that the configuration is working properly by displaying the SSL proxy statistics.
Action
From operational mode, enter the show services
ssl proxy statistics command.
user@host> show services ssl proxy statistics
PIC:fwdd0 fpc[0] pic[0]
sessions matched 30647
sessions bypassed:non-ssl 0
sessions bypassed:mem overflow 0
sessions bypassed:low memory 0
sessions created 25665
sessions ignored 0
sessions active 0
sessions dropped 0
sessions whitelisted 0
whitelisted url category match 0
default profile hit 0
session dropped no default profile 0
policy hit no profile configured 0 Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
