ICAP Service Redirect
You can prevent data loss from your network by employing Internet Content Adaptation Protocol (ICAP) redirect services. SRX Series Firewalls support ICAP redirect functionality to redirect HTTP or HTTPS traffic to any third-party server. For more information, read this topic.
Data Loss Prevention (DLP) Using ICAP Service Redirect
You can prevent data loss from your network by employing Internet Content Adaptation Protocol (ICAP) redirect services. ICAP is a lightweight HTTP-based remote procedure call protocol. ICAP allows its clients to pass HTTP-based content (HTML) to the ICAP servers for performing services such as virus scanning, content translation, or content filtering and so on for the associated client requests.
- Junos OS ICAP Support for SRX Series Device
- ICAP Profile
- Service Redirect for Layer 7 Dynamic Applications with Unified Policies
- Benefits of ICAP Redirect Service Support
Junos OS ICAP Support for SRX Series Device
SRX Series Firewalls support ICAP redirect functionality to redirect HTTP or HTTPS traffic to any third-party server. The SRX Series Firewall acts as an SSL proxy server and decrypts the pass-through traffic with the proper SSL profile under a security policy. SRX Series Firewall decrypts HTTPS traffic and redirects HTTP message to a third-party, on-premise server using an ICAP channel. After DLP processing, the traffic is redirected back to the SRX Series Firewall and action is taken according to the results from the ICAP server. If any sensitive data is detected per the policies, the SRX Series Firewall logs, redirects, or blocks the data traffic as configured in the profile.
The following sequences are involved in a typical ICAP redirect scenario:
The user opens a connection to a Website on the internet.
-
The request goes through the SRX Series Firewall that is acting as a proxy server.
-
The SRX Series Firewall receives information from the end-host, encapsulates the message and forwards the encapsulated ICAP message to the third-party on-premise ICAP server.
The ICAP server receives the ICAP request and analyzes it.
If the request does not contain any confidential information, the ICAP server sends it back to the proxy server, and directs the proxy server to send the HTTP to the internet.
If the request contains confidential information, you can choose to take action (block, permit, log) as per your requirement.
The HTTP throughput depends on the connections between the SRX Series Firewall and the ICAP channel.
ICAP redirect adds X-Client-IP, X-Server-IP,
X-Authenticated-User, and
X-Authenticated-Groups header extensions in an ICAP message to
provide information about the source of the encapsulated HTTP message.
ICAP Profile
When you configure ICAP redirect service on SRX Series Firewalls, you must configure the ICAP server information. This profile is applied to a security policy as application services for the permitted traffic. The ICAP profile defines the settings that allow the ICAP server to process request messages, response messages, fallback options (in case of a timeout), connectivity issues, too many requests, or any other conditions.
Service Redirect for Layer 7 Dynamic Applications with Unified Policies
SRX Series Firewalls support ICAP service redirect feature when the device is configured with unified policies.
Unified policies are the security policies that enable you to use dynamic applications as match conditions as part of the existing 5-tuple or 6-tuple (5-tuple with user firewall) match conditions to detect application changes over time.
In a unified policy with dynamic applications as a match condition, you configure an ICAP redirect profile and SSL proxy profile and apply these profiles as application services in the security policy for the permitted traffic. When the traffic matches the policy, the ICAP redirect service profile that is configured as application services is applied. The ICAP server profile defines the behavior of redirection and server specifications. The ICAP server performs the policy scan and the traffic is redirected to the SRX Series Firewall, and the specified action is taken as per the ICAP redirect profile.
Note the following behavior while using ICAP redirect service with unified policy:
When ICAP redirect is configured in a unified policy and the data that needs to be redirected has arrived and the final policy is not determined, the request is ignored by the ICAP redirect service.
Because ICAP redirect is one of services located in the service chain, the data received by the ICAP redirect service might be different from the original data. The data sent by the ICAP redirect might affect downstream services.
Benefits of ICAP Redirect Service Support
Keeps the sensitive data from leaving the network.
Supports common on-premise server pool for redirection thereby improving management, security, and control of the content.
The HTTP throughput depends on the connections between the SRX Series Firewall and SRX ICAP .
Example: Configuring ICAP Redirect Service on SRX Series Firewalls
This example shows how to define an ICAP redirect profile for an SRX Series Firewall.
Requirements
This example uses the following hardware and software components:
-
SRX Series Firewall with Junos OS Release 18.1R1 or later. This configuration example is tested for Junos OS Release 18.1R1.
ICAP redirect profile for an SRX Series Firewall with unified policies example is tested for Junos OS Release 18.2R1.
No special configuration beyond device initialization is required before configuring this feature.
Overview
In this example, you configure an ICAP redirect profile and an SSL proxy profile and apply these profiles as application services in the security policy for the permitted traffic.
Figure 1 shows the topology used in this example.
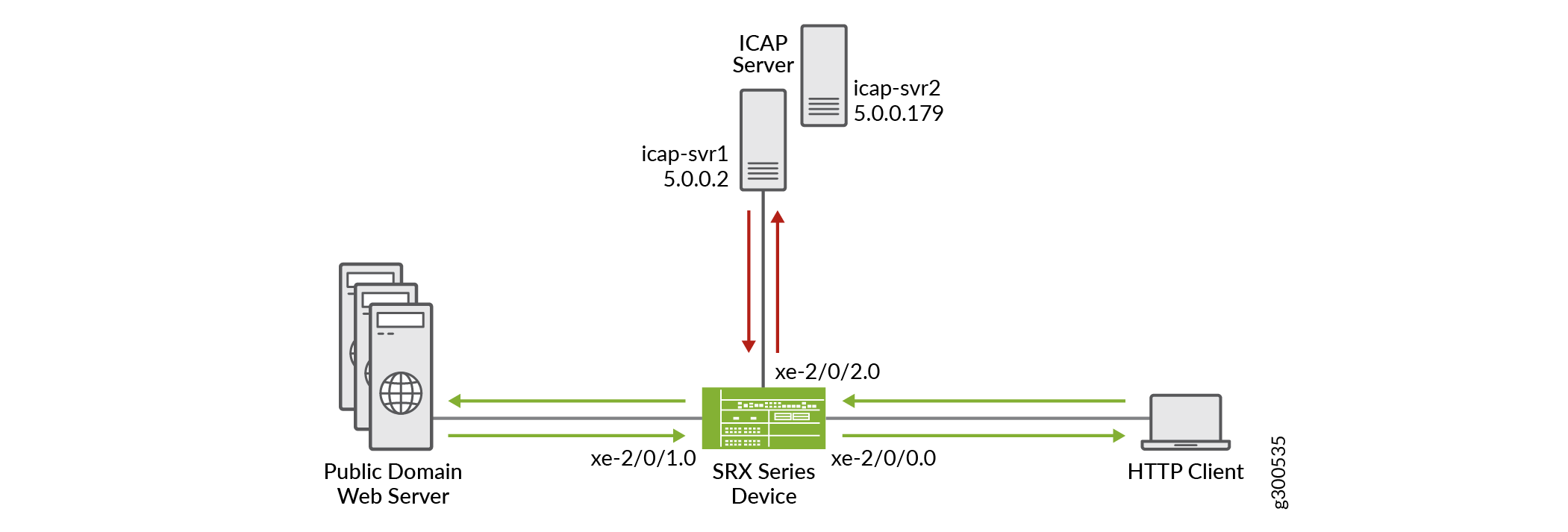
To enable the service redirect using ICAP, you must configure an SSL profile to secure the connection to the ICAP server. Next, you configure a security policy to process the traffic, and specify the action for the permitted traffic.
Table 1 lists the details of the parameters used in this example.
|
Parameters |
Names |
Description |
|---|---|---|
|
Profile |
icap-pf1 |
The ICAP server profile allows the ICAP server to process request messages, response messages, fallback options and so on, for the permitted traffic. This profile is applied as an application service in the security policy. |
|
Server name |
icap-svr1 icap-svr2 |
The machine name of the remote ICAP host. Client’s request is redirected to this ICAP server. |
|
Server IP address |
5.0.0.2 5.0.0.179 |
The IP address of the remote ICAP host. Client’s request is redirected to this ICAP server. |
|
SSL proxy profile |
ssl-inspect-profile |
An SSL proxy profile defines SSL behavior for the SRX Series Firewall. The SSL proxy profile is applied to the security policy as an application service. |
|
SSL profile |
dlp_ssl |
The SRX Series Firewall that is acting as an SSL proxy client, initiates and maintains SSL sessions with an SSL server. This configuration enables you to secure the connection to the ICAP server. |
|
Security policy |
sp1 |
In a security policy, apply the SSL proxy profile and ICAP redirect profile. to the permitted traffic. |
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set services ssl initiation profile dlp_ssl trusted-ca all set services ssl initiation profile dlp_ssl actions ignore-server-auth-failure set services ssl initiation profile dlp_ssl actions crl disable set services icap-redirect profile icap-pf1 server icap-svr1 host 5.0.0.2 set services icap-redirect profile icap-pf1 server icap-svr1 reqmod-uri echo set services icap-redirect profile icap-pf1 server icap-svr1 respmod-uri echo set services icap-redirect profile icap-pf1 server icap-svr1 sockets 64 set services icap-redirect profile icap-pf1 server icap-svr2 host 5.0.0.179 set services icap-redirect profile icap-pf1 server icap-svr2 reqmod-uri echo set services icap-redirect profile icap-pf1 server icap-svr2 respmod-uri echo set services icap-redirect profile icap-pf1 server icap-svr2 sockets 64 set services icap-redirect profile icap-pf1 server icap-svr2 tls-profile dlp_ssl set services icap-redirect profile icap-pf1 http redirect-request set services icap-redirect profile icap-pf1 http redirect-response set security policies from-zone trust to-zone untrust policy sec_policy match source-address any set security policies from-zone trust to-zone untrust policy sec_policy match destination-address any set security policies from-zone trust to-zone untrust policy sec_policy match application any set security policies from-zone trust to-zone untrust policy sec_policy then permit application-services ssl-proxy profile-name ssl-inspect-profile set security policies from-zone trust to-zone untrust policy sec_policy then permit application-services icap-redirect icap-pf1 set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces xe-2/0/0.0 set security zones security-zone trust interfaces xe-2/0/2.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces xe-2/0/1.0 set interfaces xe-2/0/0 unit 0 family inet address 192.0.2.1/24 set interfaces xe-2/0/0 unit 0 family inet6 address 2001:db8::1/64 set interfaces xe-2/0/1 unit 0 family inet address 198.51.100.1/24 set interfaces xe-2/0/1 unit 0 family inet6 address 2001:db8::2/64 set interfaces xe-2/0/2 unit 0 family inet address 198.51.100.2/24 set interfaces xe-2/0/2 unit 0 family inet6 address 2001:db8::3/64
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure the ICAP redirect service:
-
Configure the SSL profile for a secured connection with the ICAP server.
[edit services] user@host# set ssl initiation profile dlp_ssl trusted-ca all user@host# set ssl initiation profile dlp_ssl actions ignore-server-auth-failure user@host# set ssl initiation profile dlp_ssl actions crl disable
-
Configure the ICAP redirect profile for the first server (icap-svr1).
[edit services] user@host# set icap-redirect profile icap-pf1 server icap-svr1 host 5.0.0.2 user@host# set icap-redirect profile icap-pf1 server icap-svr1 reqmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr1 respmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr1 sockets 64
-
Configure the ICAP redirect profile for the second server (icap-svr2).
[edit services] user@host# set icap-redirect profile icap-pf1 server icap-svr2 host 5.0.0.179 user@host# set icap-redirect profile icap-pf1 server icap-svr2 reqmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr2 respmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr2 sockets 64 user@host# set icap-redirect profile icap-pf1 server icap-svr2 tls-profile dlp_ssl
-
Configure the redirect request and the redirect response for the HTTP traffic.
[edit services] user@host# set icap-redirect profile icap-pf1 http redirect-request user@host# set icap-redirect profile icap-pf1 http redirect-response
-
Configure a security policy to apply application services for the ICAP redirect to the permitted traffic.
[edit security] user@host# set policies from-zone trust to-zone untrust policy sec_policy match source-address any user@host# set policies from-zone trust to-zone untrust policy sec_policy match destination-address any user@host# set policies from-zone trust to-zone untrust policy sec_policy match application any user@host# set policies from-zone trust to-zone untrust policy sec_policy then permit application-services ssl-proxy profile-name ssl-inspect-profile user@host# set policies from-zone trust to-zone untrust policy sec_policy then permit application-services icap-redirect icap-pf1 user@host# set policies default-policy permit-all
-
Configure interfaces and zones.
[edit] user@host# set interfaces xe-2/0/0 unit 0 family inet address 192.0.2.1/24 user@host# set interfaces xe-2/0/0 unit 0 family inet6 address 2001:db8::1/64 user@host# set interfaces xe-2/0/1 unit 0 family inet address 198.51.100.1/24 user@host# set interfaces xe-2/0/1 unit 0 family inet6 address 2001:db8::2/64 user@host# set interfaces xe-2/0/2 unit 0 family inet address 198.51.100.2/24 user@host# set interfaces xe-2/0/2 unit 0 family inet6 address 2001:db8::3/64 user@host# set zones security-zone trust host-inbound-traffic system-services all user@host# set zones security-zone trust host-inbound-traffic protocols all user@host# set zones security-zone trust interfaces xe-2/0/0.0 user@host# set zones security-zone trust interfaces xe-2/0/2.0 user@host# set zones security-zone untrust host-inbound-traffic system-services all user@host# set zones security-zone untrust host-inbound-traffic protocols all user@host# set zones security-zone untrust interfaces xe-2/0/1.0
Results
From configuration mode, confirm your configuration
by entering the show services ssl, show services icap-redirect, show security policies, show security zones, and show interfaces commands. If the output does not
display the intended configuration, repeat the configuration instructions
in this example to correct it.
user@host# show services ssl
initiation {
profile dlp_ssl {
trusted-ca all;
actions {
ignore-server-auth-failure;
crl {
disable;
}
}
}
}
user@host# show services icap-redirect
profile icap-pf1 {
server icap-svr1 {
host 5.0.0.2;
reqmod-uri echo;
respmod-uri echo;
sockets 64;
}
server icap-svr2 {
host 5.0.0.179;
reqmod-uri echo;
respmod-uri echo;
sockets 10;
tls-profile dlp_ssl;
}
http {
redirect-request;
redirect-response;
}
}
user@host# show security policies
from-zone trust to-zone untrust {
policy sec_policy {
match {
source-address any;
destination-address any;
application any;
}
then {
permit {
application-services {
ssl-proxy {
profile-name ssl-inspect-profile;
}
icap-redirect icap-pf1;
}
}
}
}
}
default-policy {
permit-all;
}
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
xe-2/0/0.0;
xe-2/0/2.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
xe-2/0/1.0;
}
}
user@host# show interfaces
xe-2/0/0 {
unit 0 {
family inet {
address 192.0.2.1/24;
}
family inet6 {
address 2001:db8::1/64;
}
}
}
xe-2/0/1 {
unit 0 {
family inet {
address 198.51.100.1/24;
}
family inet6 {
address 2001:db8::2/64;
}
}
}
xe-2/0/2 {
unit 0 {
family inet {
address 198.51.100.2/24;
}
family inet6 {
address 2001:db8::3/64;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Configuring ICAP Service Redirect for Unified Policy
Step-by-Step Procedure
You can follow the procedure below if you have configured a unified policy.
The following example requires you to navigate to various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure the ICAP redirect service:
-
Configure the SSL profile for secured connection with the ICAP server.
[edit services] user@host# set ssl initiation profile dlp_ssl trusted-ca all user@host# set ssl initiation profile dlp_ssl actions ignore-server-auth-failure user@host# set ssl initiation profile dlp_ssl actions crl disable
-
Configure the ICAP redirect profile for the first server (icap-svr1).
[edit services] user@host# set icap-redirect profile icap-pf1 server icap-svr1 host 5.0.0.2 user@host# set icap-redirect profile icap-pf1 server icap-svr1 reqmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr1 respmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr1 sockets 64
-
Configure the ICAP redirect profile for the second server (icap-svr2).
[edit services] user@host# set icap-redirect profile icap-pf1 server icap-svr2 host 5.0.0.179 user@host# set icap-redirect profile icap-pf1 server icap-svr2 reqmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr2 respmod-uri echo user@host# set icap-redirect profile icap-pf1 server icap-svr2 sockets 64 user@host# set icap-redirect profile icap-pf1 server icap-svr2 tls-profile dlp_ssl
-
Configure the redirect request for HTTP traffic.
[edit services] user@host# set icap-redirect profile icap-pf1 http redirect-request user@host# set icap-redirect profile icap-pf1 http redirect-response
-
Configure a security policy to apply application services for the ICAP redirect to the permitted traffic.
[edit security] user@host# set policies from-zone trust to-zone untrust policy sec_policy match source-address any user@host# set policies from-zone trust to-zone untrust policy sec_policy match destination-address any user@host# set policies from-zone trust to-zone untrust policy sec_policy match application any user@host# set policies from-zone trust to-zone untrust policy sec_policy match dynamic-application junos:HTTP user@host# set policies from-zone trust to-zone untrust policy sec_policy then permit application-services ssl-proxy profile-name ssl-inspect-profile user@host# set policies from-zone trust to-zone untrust policy sec_policy then permit application-services icap-redirect icap-pf1 user@host# set policies default-policy permit-all
Verification
Verifying ICAP Redirect Configuration
Purpose
Verify that the ICAP redirect service is configured on the device.
Action
From operational mode, enter the show services
icap-redirect status and show services icap-redirect statistic commands.
user@host> show services icap-redirect status
ICAP Status :
Spu-1 Profile: icap-pf1 Server: icap-svr1 : UP
ICAP Status :
Spu-1 Profile: icap-pf1 Server: icap-svr2 : UP
ICAP Status :
Spu-2 Profile: icap-pf1 Server: icap-svr1 : UP
ICAP Status :
Spu-2 Profile: icap-pf1 Server: icap-svr2 : UP
ICAP Status :
Spu-3 Profile: icap-pf1 Server: icap-svr1 : UP
ICAP Status :
Spu-3 Profile: icap-pf1 Server: icap-svr2 : UP
user@host> show services icap-redirect statistic
ICAP Redirect statistic:
Message Redirected : 2
Message REQMOD Redirected : 1
Message RESPMOD Redirected : 1
Message Received : 2
Message REQMOD Received : 1
Message RESPMOD Received : 1
Fallback: permit log-permit reject
Timeout 0 0 0
Connectivity 0 0 0
Default 0 0 0
Meaning
The status Up indicates that the ICAP redirect
service is enabled. The Message Redirected and the Message Received fields show the number of HTTP requests that
have passed through the ICAP channel.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
X-Client-IP,
X-Server-IP,
X-Authenticated-User, and
X-Authenticated-Groups header
extensions in an ICAP message to provide
information about the source of the encapsulated
HTTP message.