What is VXLAN?
What is VXLAN?
Virtual eXtensible Local-Area Network, or VXLAN, is an Internet Engineering Task Force (IETF) network virtualization technology standard. It allows a single physical network to be shared by multiple different organizations, or “tenants,” without any one tenant being able to see the network traffic of any other.
In this way, VXLANs are analogous to individual units in an apartment building: each apartment is a separate, private dwelling within a common structure, just as each VXLAN is a discrete, private network segment within a shared physical network.
Technically speaking, a VXLAN allows a physical network to be segmented into as many as 16 million virtual, or logical, networks. It works by encapsulating Layer 2 Ethernet frames into a Layer 4 User Datagram Protocol (UDP) packet alongside a VXLAN header. When combined with an Ethernet virtual private network (EVPN)—which transports Ethernet traffic in virtualized networks using WAN protocols—VXLAN allows Layer 2 networks to be extended across a Layer 3 IP or MPLS network.
Key advantages
Because VXLANs are encapsulated inside a UDP packet, they can run on any network able to transmit UDP packets. The physical layout and geographic distance between nodes of the underlying network don’t matter, as long as the UDP datagrams are forwarded from the encapsulating VXLAN Tunnel Endpoint (VTEP) to the decapsulating VTEP.
When VXLAN combines with EVPN, operators can create virtual networks out of physical network ports on any physical network switches that support the standard and are part of the same Layer 3 network. For example, you could take a port from switch A, two ports from switch B, and another port from switch C and construct a virtual network that appears to all the connected devices as a single physical network. Devices participating in this virtual network would be unable to see traffic in any other VXLANs or the underlying network fabric.
Problems that VXLAN solves
Just as the rapid adoption of server virtualization has driven dramatic increases in agility and flexibility, virtual networks decoupled from physical infrastructure are easier, faster, and more affordable to operate. For example, they allow multiple tenants to share a single physical network securely, enabling network operators to quickly and economically scale their infrastructures to meet growing demand. The primary reasons to segment networks are privacy and security; to prevent one tenant from seeing or accessing traffic belonging to another tenant.
Operators logically segment their networks in ways similar to how they’ve long deployed traditional virtual LANs (VLANs); however, VXLANs overcome VLAN scaling limitations in the following ways.
- You can theoretically create as many as 16 million VXLANs in an administrative domain, compared to a maximum of 4094 traditional VLANs. In this way, VXLANs provide network segmentation at the scale required by cloud and service providers to support very large numbers of tenants.
- VXLANs enable you to create network segments that stretch between data centers. Traditional VLAN-based network segmentation creates broadcast domains, but as soon as a packet containing VLAN tags hits a router, all of that VLAN information is removed. This means VLANs only travel as far as your underlying Layer 2 network can reach. This is a problem for some use cases, such as virtual machine (VM) migration, which typically prefers not to cross Layer 3 boundaries. By contrast, VXLAN network segmentation encapsulates the original packet inside a UDP packet. This allows a VXLAN network segment to extend as far as the physical Layer 3 routed network can reach, provided that all switches and routers in the path support VXLAN, without the applications running on the virtual overlay network being required to cross any Layer 3 boundaries. As far as the servers connected to the network are concerned, they are part of the same Layer 2 network, even though the underlying UDP packets may have transited one or more routers.
- The ability to provide Layer 2 segmentation over the top of an underlying Layer 3 network, combined with the high number of supported network segments, allows servers to be part of the same VXLAN even if they are remote from one another while enabling network administrators to keep Layer 2 networks small. Having smaller Layer 2 networks helps avoid MAC table overflow on switches.
Primary VXLAN applications
Service provider and cloud provider VXLAN use cases are straightforward: these operators have large numbers of tenants, or customers, and there are multiple legal, privacy, and ethical reasons why providers must partition one customer’s network traffic from another’s.
In enterprise environments, a tenant might be a user group, department, or other set of network-segmented users or devices created for internal security reasons. For example, Internet of Things (IoT) devices such as data center environmental sensors are prone to compromise, so it’s a sound security practice to isolate IoT network traffic from production network application traffic.
How VXLAN works
The VXLAN tunneling protocol encapsulates Layer 2 Ethernet frames in Layer 4 UDP packets, enabling you to create virtualized Layer 2 subnets that span physical Layer 3 networks. Each segmented subnet is uniquely identified by a VXLAN Network Identifier (VNI).
The entity that performs the encapsulation and decapsulation of packets is called the VXLAN Tunnel Endpoint (VTEP). A VTEP can be an independent network device, such as a physical router or switch, or a virtual switch deployed on a server. VTEPs encapsulate Ethernet frames into VXLAN packets, which are then sent to the destination VTEP over an IP or other Layer 3 network, where they’re decapsulated and forwarded to the destination server.
To support devices that can’t operate as a VTEP on their own, such as bare-metal servers, hardware VTEPs such as select Juniper switches and routers can encapsulate and decapsulate data packets. In addition, VTEPs can reside in hypervisor hosts, such as kernel-based virtual machines (KVMs), to directly support virtualized workloads. This type of VTEP is known as a software VTEP.
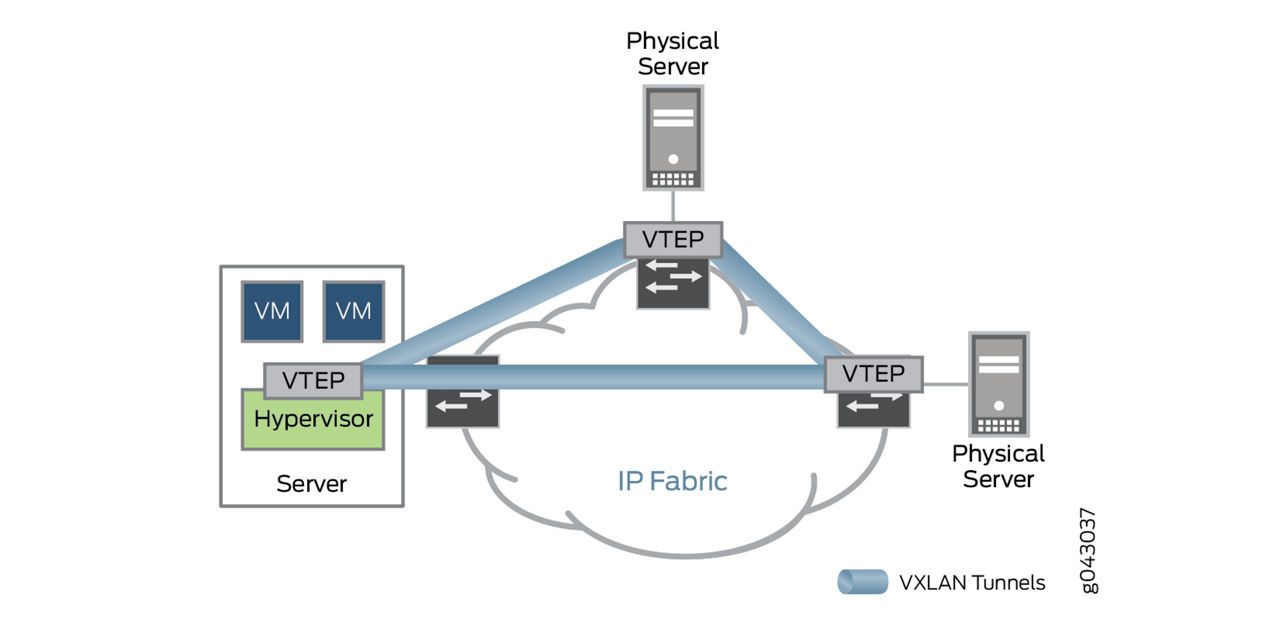
Hardware and software VTEPs are shown above.
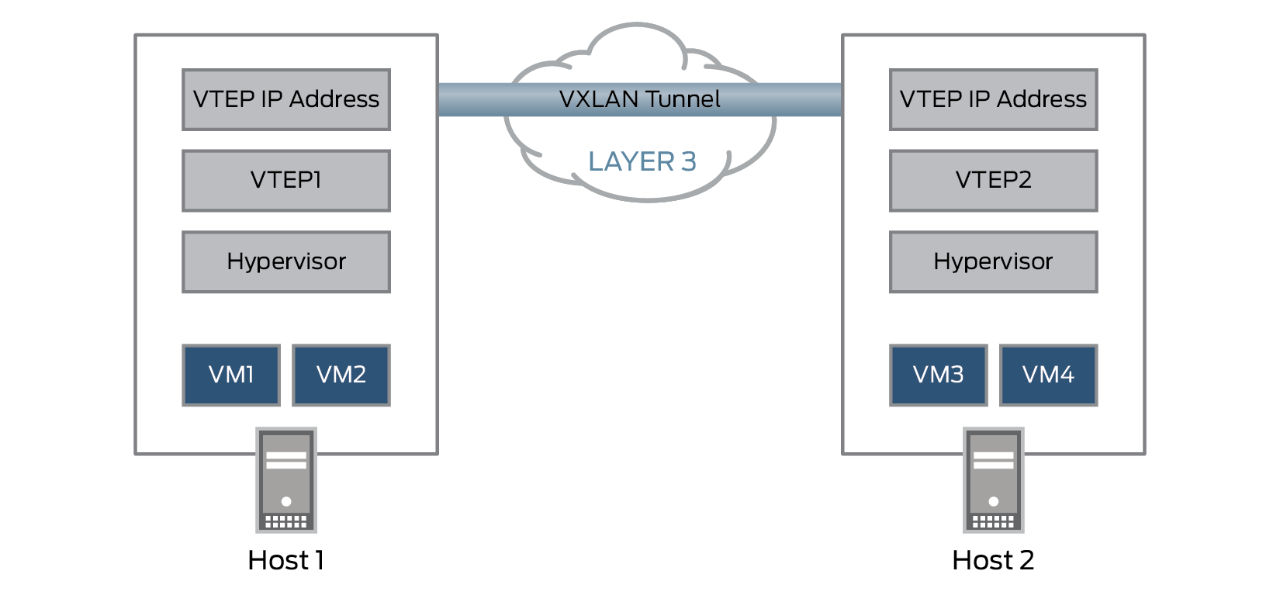
In the figure above, when VTEP1 receives an Ethernet frame from Virtual Machine 1 (VM1) addressed to Virtual Machine 3 (VM3), it uses the VNI and the destination MAC to look up in its forwarding table for the VTEP to send the packet to. VTEP1 adds a VXLAN header that contains the VNI to the Ethernet frame, encapsulates the frame in a Layer 3 UDP packet, and routes the packet to VTEP2 over the Layer 3 network. VTEP2 decapsulates the original Ethernet frame and forwards it to VM3. VM1 and VM3 are completely unaware of the VXLAN tunnel and the Layer 3 network between them.
Juniper Networks VXLAN Solutions
Juniper Networks MX Series routers, QFX Series switches, and EX Series switches support EVPN-VXLAN and can act as VTEP gateways, encapsulating/decapsulating VXLAN packets, and also route between different VXLANs.
VXLAN FAQs
What is VXLAN used for?
VXLANs are used to accomplish network segmentation beyond what classic VLANs can deliver. Classic VLANs offer only 4094 virtual networks, while VXLANs offer up to 16 million. Network segmentation has two primary uses: allowing multiple tenants to share a single physical network without seeing one another’s traffic and allowing for the reuse of IP address space. It’s also possible to configure network segments with differentiated quality-of-service (QoS) policies and service-level agreements (SLAs).
VXLAN is primarily used within large data centers, service provider networks, and cloud operator networks where the 4094 virtual network limit of classic VLANs is too constraining. That said, as VXLAN becomes supported by more—and less expensive—switch processors, it’s beginning to move out of the data center and into campus networks.
Is VXLAN a standard?
Yes, the VXLAN standard was created in 2014 by the IETF and is specified in RFC 7348.
Is VXLAN a Layer 3 standard?
VXLAN is sometimes considered a Layer 3 protocol because it relies on an IP (Layer 3) transport network. It’s sometimes also considered a Layer 4 standard, because it encapsulates Ethernet frames in UDP, affecting Layer 4 UDP by operation.
Does VXLAN replace VLAN?
VXLANs do not entirely replace VLANs; in some circumstances, such as large service provider data centers, both standards may be used. VXLANs may be used to segment the service provider’s global network, isolating each customer on its own VXLAN while enabling each customer to create private VLANs within their VXLAN.
What’s the basic difference between VXLAN, VLAN, and QinQ technologies?
VLAN, QinQ, and VXLAN are all standards used for logically segmenting physical networks into multiple virtual networks. Each standard respectively provides greater scalability than the last. Networks are usually segmented for security reasons and to support differentiated QoS requirements, which are usually part of SLAs.
VLANs were the first to be standardized in 1998; QinQ built on VLANs to expand the number of logical networks that can be created. QinQ also enables enterprise/business VLANs to be supported across public WAN services. VXLAN offers the greatest extensibility and flexibility of the three technologies.
Technically, the differences among these technologies lie in how they tag and encapsulate Ethernet frames before transmission over communications networks.
What are the more technical distinctions between VXLAN, VLAN, and QinQ?
Understanding these different virtualization technologies requires a basic grasp of how Ethernet networks operate. An Ethernet frame consists of a header with data-forwarding information, such as the source and destination MAC and IP addresses, and a payload containing the actual data to be transmitted. For these frames to be successfully forwarded from one location to another, every network element involved in the communications chain, such as network interface cards, switches, and routers, must understand the Ethernet and virtualization standards involved.
VLAN and QinQ both extend the length of the basic Ethernet frame header, requiring that all network devices (both endpoints, as well as all intermediate devices) support the standards. By contrast, VXLAN does not extend the Ethernet frame header, thus only requiring support for the standard on the devices serving as the VTEPs.
The VLAN standard created in 1998 extends Ethernet frame headers by 4 bytes, allowing Ethernet frames to be “tagged” as belonging to one of up to 4094 virtual networks. QinQ extends the VLAN standard to allow 4094 “private” VLANs to be created on each of 4094 “public” VLANs, or 16 million VLANs in total. To get the job done, it also extends the Ethernet frame header by 4 bytes.
Like QinQ, the VXLAN standard, created in 2014, supports up to 16 million virtual networks. While it doesn’t extend the Ethernet frame header, it does require an increased maximum IP packet size, extending IPv4 packets from 1518 bytes to 1554 bytes. VXLAN packets encapsulate the original Ethernet frame inside a UDP packet. The new UDP packet contains both the VXLAN header and the complete original Ethernet frame inside its payload. UDP, often used for delay-sensitive traffic, is the connectionless Layer 4 communications protocol in the core Internet protocol suite that’s a lower-latency alternative to connection-oriented TCP.
Are VXLAN, VLAN, and QinQ typically used together?
Hypothetically, you can use traditional VLANs, QinQ VLANs, and VXLANs all at the same time. This is because of where the network identifiers exist within the data packet. VXLANs don’t change or extend the format of the UDP packet in which they are encapsulated, nor do they change or extend the outer Ethernet frame in which that UDP packet is carried. That’s because VXLAN packets are contained within the payload of a UDP packet (not the header). They include a VXLAN header and the complete original Ethernet frame that ultimately was to be transmitted. VXLAN-in-UDP packets, then, can have outer Ethernet frames that also contain VLAN and QinQ identifiers.
In other words, in a VXLAN packet, there are three places where virtual networks can be defined: the outer Ethernet frame, the VXLAN header, and the inner Ethernet frame, and each of these sets of virtual networks can be completely distinct from one another. This can result in a packet where the outer Ethernet frame can support 16 million virtual networks, the VLXAN header can support an additional 16 million virtual networks, and then the inner Ethernet frame can support another 16 million virtual networks.
In enterprise networking practice, however, networks tend to be either VLAN or VXLAN-based. When technologies are combined, it is typically by network and cloud service providers who offer business customers the ability to use VLANs within their own VXLAN. This scenario makes use of VLANs on the inner Ethernet frame, as well as the virtual network capabilities of the VXLAN header, but does not make use of VLANs on the outer Ethernet frame.
Is VXLAN better than VLAN?
VXLANs and VLANs, while superficially similar, solve the same problem in different ways. This means that they get used in different circumstances and that they are not mutually exclusive.
Today nearly every switch sold can support at least basic VLANs, and most – including many consumer switches – can support QinQ. EVPN-VXLAN support is typically limited to more capable enterprise or carrier-grade switches.
VXLANs are considered the more efficient technology. The reason is that only the switches that contain VTEPs carry an additional look-up table (LUT) burden in a VXLAN-based network, and they only need to do so for the virtual networks for which they have VTEPs, not for the entire network. This contrasts with VLAN-based networks, such as QinQ, which supports the same 16 million potential virtual networks as VXLAN but requires that all switches assume the extra burden.
What are the technical details of VXLAN efficiency, compared to QinQ VLANs?
QinQ VLANs require that every device that may interact with a QinQ packet support the extended Ethernet header. VXLAN requires that every device that may interact with a VXLAN packet support the longer Ethernet frame, but requires only those devices with VTEPs to support decapsulation and reading of the VXLAN header.
Because both classic VLAN and its QinQ extension simply add a tag to the Ethernet frame header, every switch that sees a VLAN or QinQ packet will store metadata about every packet. This results in rapidly expanding LUTs, as each switch needs to know where every single device on the entire network is.
Because VXLANs encapsulate the original Ethernet frame, they separate the network into an “underlay” and an “overlay.” The underlay is the physical network that transmits the UDP packets in which the VXLAN header and the original Ethernet frame reside. The majority of the physical switches transmitting these UDP packets do not need to store information about either the VXLAN header or the original Ethernet frame: all they need to know is where to deliver the UDP packet.
When the UDP packet arrives at a switch with a relevant VTEP, the UDP packet is decapsulated, and the switch with the VTEP then reads the VXLAN header and encapsulated Ethernet frame’s header information, adding that data to its LUT. As a result, only the switches containing VTEPs carry the additional LUT burden of virtual networks in a VXLAN-based network, and they only need to carry that burden for the virtual networks for which they have VTEPs, not for the entire network. This contrasts with VLAN-based networks, where all switches would have to do so.
A large VXLAN-based network is thus far more efficient from a LUT resource usage standpoint than a VLAN/QinQ-based network. However, the VXLAN-based network requires switches that support VTEPs, something currently restricted to higher-end switches.
What is the difference between VXLAN and EVPN?
All types of virtual LANs are a means of segmenting physical networks into multiple, private, virtual networks. Ethernet VPN (EPVN) and VXLAN are frequently used together but they are technically independent with different objectives.
VXLANs expand Layer 2 address space from about 4000 to about 16 million to extend Ethernet networks across broader IP networks, slicing up the physical network so that multiple tenants can share its resources without seeing one another’s traffic. EVPN enables the creation of virtual networks that comprise switch ports and other resources from different equipment and network domains. EVPN is basically a way to enable computers that aren’t connected to the same physical network and might be geographically remote from one another to behave as though they were plugged into the same physical switch, with all nodes part of that EVPN receiving data broadcasts as though connected to a traditional Layer 2 local network.
Why would I use VXLAN and EVPN together?
When you combine these technologies into an EVPN-VXLAN, you gain ultimate network configuration flexibility; the physical location of a computer has no bearing on the network to which it’s connected. A single 32-port switch could have each port exposing a different VXLAN, meaning that a computer plugged into any port would be unable to talk to any other computer plugged into another port on that same switch without a router to provide connectivity. EVPN, however, allows you to build virtual Ethernet networks such that, with the right configuration, computers in two different cities can be part of the same subnet.
What VXLAN solutions does Juniper offer?
Juniper offers VXLAN VTEP support in several of our switches and routers along with options for configuring and managing VXLAN and EVPN-VXLAN data center fabrics:
- Select Juniper networking devices, including QFX Series Switches, EX Series Switches, and MX Series Universal Routers, can serve as VTEPs, forwarding UDP packets containing VXLAN headers and the encapsulated Ethernet frame, because they do not need to be aware of the VXLAN contents.
- EVPN-VXLAN data center fabrics can be managed manually through the Junos operating system CLI, the Junos OS API, or the Juniper Apstra data center fabric manager.
- Juniper’s AI-driven campus fabrics, based on a VXLAN overlay with an EVPN control plane, deliver an efficient and scalable way to build and interconnect enterprise networks with consistency.
- Select Juniper SRX Series Firewalls support security inspection of VXLAN tunnels.

