99.7% security effectiveness
Juniper received a 99.7% exploit block rate with zero false positives in the CyberRatings.org 2024 Cloud Network Firewall Report.
Juniper.net is transitioning to HPE.com — One home for all networking innovation. Read more >>
Solutions
Featured solutions AI Campus and branch Data center WAN Security Service provider Cloud operator Industries
Welcome to the NOW Way to Wi-Fi
Take your networking performance to new heights with a modern, cloud-native, AI-Native architecture. Only Juniper can help you unleash the full potential of Wi-Fi 7 with our AI-Native platform for innovation.

AI Data Center Networking
Juniper’s AI data center solution is a quick way to deploy high performing AI training and inference networks that are the most flexible to design and easiest to manage with limited IT resources.

Enterprise AI‑Native Routing
Juniper's Ai-Native routing solution delivers robust 400GbE and 800GbE capabilities for unmatched performance, reliability, and sustainability at scale.

Gartner® Magic Quadrant™ Leader
Gartner® has named Juniper a Leader in the 2025 Magic Quadrant™ for Enterprise Wired and Wireless LAN Infrastructure.

Ops4AI Lab
Visit our lab in Sunnyvale, CA and see our AI data center solution for yourself. You can try out your own model’s functionality and performance, too.

Enterprise AI‑Native Routing
Juniper's Ai-Native routing solution delivers robust 400GbE and 800GbE capabilities for unmatched performance, reliability, and sustainability at scale.

Shaping Student Experiences: The NOW Way to Build Higher Education Networks
Juniper Networks CIO Sharon Mandell and a virtual summit of C-level IT leaders from prestigious institutions discuss ongoing efforts to support digital transformation on campus.

AI-Native Healthcare Networking
Sudheer Matta, SVP Product Management at Juniper Networks, Philip Bradley, Digital Health Strategist at HIMSS Analytics, and other healthcare IT leaders discuss the challenges to deliver quality patient care and the role of AI-native networking.

AI-Native Networks for Scalable Retail Success
Sanjoy Dey, VP of Product Marketing at Juniper, and global retail leaders share how Juniper is redefining IT infrastructure for the industry’s future.
Products
Wireless access Wired access SD-WAN / SASE Routing and switching Security Marvis AI Management software Network operating system Blueprint for AI-Native Acceleration Optics
Next-gen AI-Native EX4000 line of switches
Lack of AI innovation from your current networking vendor slowing you down? Embrace Juniper’s cloud-native, AI-Native access switches that support every level and layer, across nearly every deployment.

The Q&AI Podcast
Delivering practical solutions and enriching discussions, this podcast series is a vital resource for those seeking an in-depth exploration of AI's transformative potential.
Services
Services
Juniper AI Care Services Revolutionize Your Service Experience
Our industry-first AI-Native services couple AIOps with our deep expertise across the full network life cycle. You can move from reactive response to proactive insight and action.

Juniper AI Data Center Deployment Services Optimize Your AI Model Runs
We use our expertise and validated designs to help design, deploy, validate and tune networks, including GPUs and storage, to get the most from your AI infrastructure operation.
Partners
PartnersSupport and Documentation
Support and Documentation
The Juniper Support Portal (JSP) mobile app is now available!
Get Juniper support anytime, anywhere with the JSP mobile application, now available for Android and iOS!
Learn
About Juniper Training Events The Feed Resources Technology learning topics Thought leadership and insights
Trust Center
The trust center is the source of truth for our customers, partners, and the industry.

Gartner® Magic Quadrant™ Leader
Gartner® has named Juniper a Leader in the 2025 Magic Quadrant™ for Enterprise Wired and Wireless LAN Infrastructure.

Executive insights
Dive deep with leading experts and thought leaders on all the topics that matter most to your business, from AI to network security to driving rapid, relevant transformation for your business.

Leadership voices
Juniper Networks’ leaders operate on the front lines of creating the network of the future. Take a look around to see what’s on their minds.

Bob Friday Talks
Join Bob as he ventures into all the knowns -- and -- unknowns -- of AI.
Product
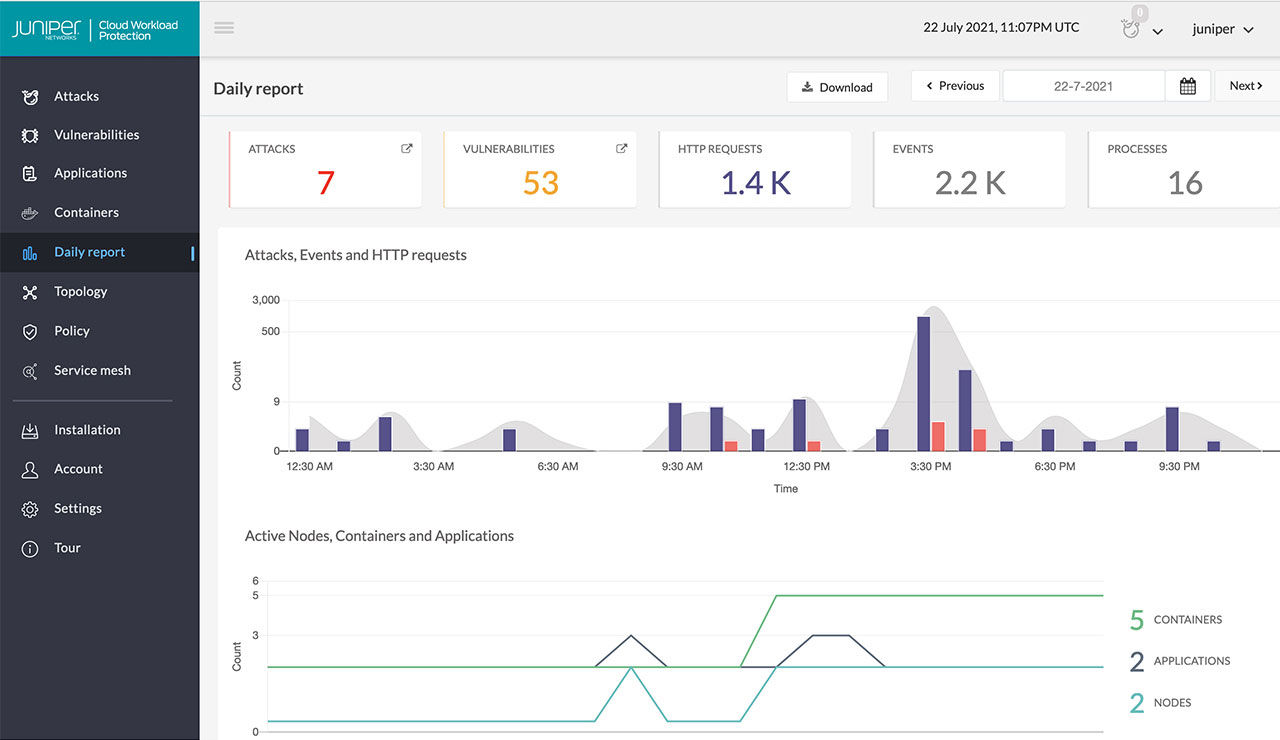
Juniper Cloud Workload Protection defends application workloads in any cloud or on-premises environment in and against advanced and zero-day exploits, automatically as they happen. It ensures that production applications always have a safety net against vulnerability exploits, keeping business-critical services connected and resilient.
Key Features
Provides real-time protection against attacks and safeguards the application from malicious actions without manual intervention, catching sophisticated attacks that endpoint detection (EDR) and web application firewall (WAF) solutions cannot.
Safeguards against sophisticated attacks like zero-day exploits, the OWASP Top 10, and memory-based attacks aimed at application vulnerabilities and workloads.
Continuously assesses vulnerabilities in applications and containers, detecting serious and critical exploit attempts as they happen.
Provides rich, application-level security event generation and reporting, including application connectivity, topology, and detailed information about the attempted attack.
Validates the execution of applications and detects attacks without using behavior or signatures, resulting in virtually no false alerts.
Shields application resources from lateral threat propagation and integrates with Juniper vSRX Virtualized Firewalls to restrict access based on risk, even as workloads and virtual environments change. Automated threat response with built-in, real-time telemetry helps security teams detect once, and block across the entire network.
Juniper received a 99.7% exploit block rate with zero false positives in the CyberRatings.org 2024 Cloud Network Firewall Report.
Make your network threat-aware. Juniper’s security portfolio safeguards users, data, and infrastructure by extending security to every point of connection—from client to cloud—across the entire network.
Learn moreAccelerate public cloud adoption securely with simplified deployment, consistent security, and a unified management experience at every level—within workloads, between applications and instances, and across environments.
Get the detailsJuniper Connected Security safeguards users, data, and infrastructure by extending threat intelligence to all connection points across your network.
Learn more