Earlier Versions
In case you missed a release, review a list of features from previous versions of QRadar Use Case Manager.
Version 3.4.0
Tuning active rules enhancements
Added the Offense creation trend by rule chart to the Active rules page. For each rule that meets the conditions of the selected date filter, this trend chart shows the number of offenses that the rule started to contribute to on a specific day. For example, a rule started to contribute to three offenses yesterday, so the chart displays three offenses for that rule and yesterday’s date. Today that same rule started to contribute to four new offenses and continued contributing to two offenses from yesterday. The chart displays four offenses for that rule and today’s date. Because only four offenses are new for the rule, only four are shown on the chart instead of six.
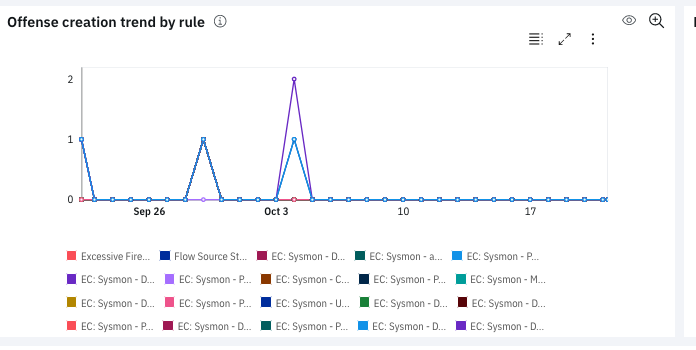
The chart is only supported on QRadar 7.4.1 Fix Pack 2 or later.
On the rule details page for a selected rule, you can change the date range for the trend of the selected rule in the Offense creation by current rule in a certain time chart. In previous versions, the time limit was the last three days only.
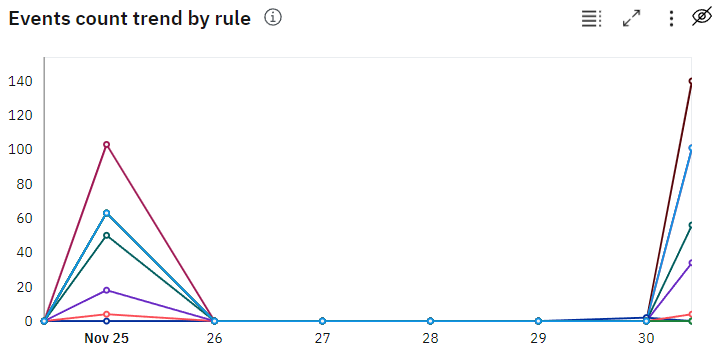
Added the Events count trend by rule chart to the Active rules page. For each rule that meets the conditions of the selected date filter, this trend chart shows the number of events per offense that the rule started to contribute to on a specific day. For example, a rule started to contribute to three offenses with 100 events yesterday, so the chart displays 100 events for that rule and yesterday's date. Today that same rule started to contribute to four new offenses with 200 events, and continued contributing to two offenses with 50 events from yesterday. The chart displays 200 events for that rule and today's date. Because only 200 events are new for the rule, only 200 are shown on the chart instead of 250.
Improved the display of bar charts on the Active rules page by sorting bars with the highest value in descending order. For better visual clarity, limitations were added to the number of bars that are displayed: a maximum of 15 bars on a small chart and a maximum of 30 bars when the chart is expanded to full screen.
Enhanced the visualization capabilities on bar and timeline charts on the Active Rules, CRE Report, MITRE coverage summary and trend, and Rule-log source type coverage summary and trend pages. Now you can view the data in tabular format, expand the charts to full screen, and download the charts in PNG, JPB, or CSV formats.
Export rules as HTML documents to view offline.
Export selected rules to a formatted HTML report that you can view offline. By default, you can export the dependencies, dependents, and visualizations for the selected rules. Share the .zip file with colleagues or management who don't have access to QRadar or QRadar Use Case Manager. For more information, see Exporting rules.
Rule table enhancements
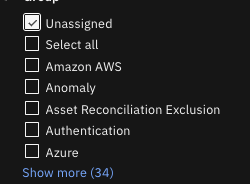
Added an Unassigned filter option to the Group, Action, and Response filters. The Unassigned filter helps you see which rules don't belong to any group.
Added a Test: Log source column in the Use Case Explorer table report that returns specific references to log sources that are used in rule tests.
Create offense rules in rule wizard
Added the ability to create offense rules in the rule wizard. Click the plus sign icon in the report menu bar to access the rule wizard.
MITRE enhancements
Support was added for MITRE v10, which updates Techniques, Groups, and Software for Enterprise, Mobile, and ICS. Version 10 deprecates the Scheduled Task/Job: Launchd sub-technique. As a result, QRadar Use Case Manager redirects that mapping to the parent technique instead. For more information, see Updates - October 2021.
Custom rule attribute enhancements
Export or import custom rule attribute data, including rule mappings, in a JSON file. Sharing the data between colleagues or QRadar deployments helps to streamline your workflow by eliminating work effort. For more information, see Exporting and Importing Custom Rule Attributes and Exporting rules.
Version 3.3.0
Custom rule attributes
A custom rule attribute represents a specific piece of information that you can attach to a rule that doesn't fit into existing rule attributes. For example, the use case the rule belongs to, the team who is responsible for creating or maintaining the rule, or who reviewed the rule. You can now define any custom rule attribute and its values, assign the custom attribute values to a rule, and add the custom attribute as a column in Use Case Explorer. For more information, see Custom Rule Attributes.
Rule management improvements
Added extra checks when rules are enabled or disabled, so that you cannot enable a rule that has disabled dependencies, or disable a rule that has enabled dependents.
You can now delete rules from QRadar by using QRadar Use Case Manager. The same restrictions apply as when you delete rules in QRadar. For more information, see Deleting Rules.
When you export rule data to a file to import into another QRadar deployment, you can now choose to enter details about the export, such as extension name and description. These details are included in the corresponding manifest.txt file, and displayed in the Extensions Management tool upon import. For more information, see Exporting rules.
MITRE improvements
Improved report filtering based on selected MITRE ATT&CK platforms so that no reports contain results that are related to non-selected platforms. To change the selected platforms, modify your user preferences. For more information, see Customizing user preferences.
Support was added for MITRE v9, which updates tactics, techniques, groups, software, and platforms.
Tuning active rules enhancements
A new Event Count column indicates how many events the rule associated to the number of offenses counted in the Offense count column.
The column is supported on QRadar 7.4.1 Fix Pack 2 or later.
The Total offenses by closure reason and rule chart is renamed to Closed offenses by reason and rule to more accurately describe the contents.
Rule investigation details page enhancements
Added a Refresh icon to update edits to the page.
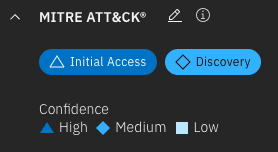
Enhanced the display of the MITRE tags in the MITRE ATT&CK section of the page. Previously, the confidence level was expressed only through the color shading, but a shape was added for accessibility reasons, and a legend was added for further explanation.
Content Extensions
After you install new content extensions, the Use Case Explorer page is refreshed with data within 15 minutes. In previous versions, the refresh only occurred overnight or by clearing the QRadar Use Case Manager cache on the Configuration page from the Admin tab.
Version 3.2.0
Rule enhancements
Now you can report on rules that assign events to offenses that are not active in a specific time period, or since installation. Rules that don’t trigger in a certain timeframe might be misconfigured, and you might not be getting the most value out of your QRadar deployment. Review your inactive rules for possible tuning options. Filtering for inactive rules is supported on QRadar 7.4.1 Fix Pack 2 or later. For more information, see Filtering rules and building blocks by their properties.
APIs are available so that you can download rule report data to CSV or JSON formats in any configuration that is possible on the Use Case Explorer page. For more information, see Accessing report data by using QRadar Use Case Manager APIs.
Rule integration with IBM QRadar User Behavior Analytics 4.1.0
If you use QRadar User Behavior Analytics 4.1.0 in your environment, you now manage user analytics rules in QRadar Use Case Manager 3.2.0 instead of on the Rules and Tuning page in QRadar User Behavior Analytics.
During the upgrade for both apps, they communicate with each other and the rules are automatically integrated. After you tune the rules in the QRadar Use Case Manager app, the modifications are sent back to IBM QRadar User Behavior Analytics to use in the dashboards, which visualize user risks to your network.
For more information, see Investigating user behavior analytics rules.
Enhanced tuning active rules
A new chart was added to the Active Rules page to filter offenses by the closure reason and related rule. For example, you can filter to see which rules generated the offenses that were closed as false positives. For more information, see Tuning the active rules that generate offenses.
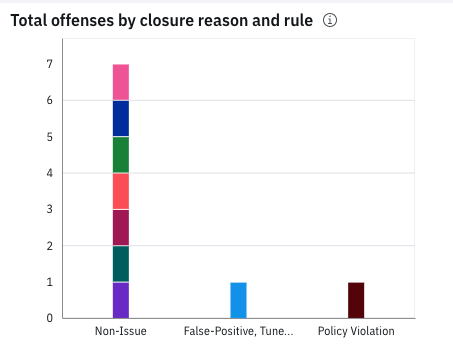
You can now export rule data from the Active rules that generate offenses page and the Active rules that generate CRE events page to CSV format.
MITRE enhancements
You can now exclude offenses from the Detected in timeframe chart based on their closure reasons. For example, you can exclude the rules that generated offenses that were closed as false positives. Rules with many false positives likely need tuning. Offenses that are closed as a non-issue are usually considered not critical to your organization. You might not want to include these offenses when you review the detected MITRE tactics and techniques.
Support was added for MITRE v8.2, which updates Techniques, Groups, and Software for Enterprise.
Support was also added for all MITRE platforms to filter the Detected in timeframe and the Coverage map MITRE reports. By default, the Linux, macOS, and Windows platforms are supported. Changing the platform selection affects the heat maps, the tactic and technique selection in the filters, and the MITRE ATT&CK Mappings edit page. For more information, see Customizing user preferences.
Export MITRE coverage maps and MITRE coverage summary and trend charts as PNG images. Then, you can share the image with colleagues or executives who don't have access to the QRadar Use Case Manager app.
Workflow improvements
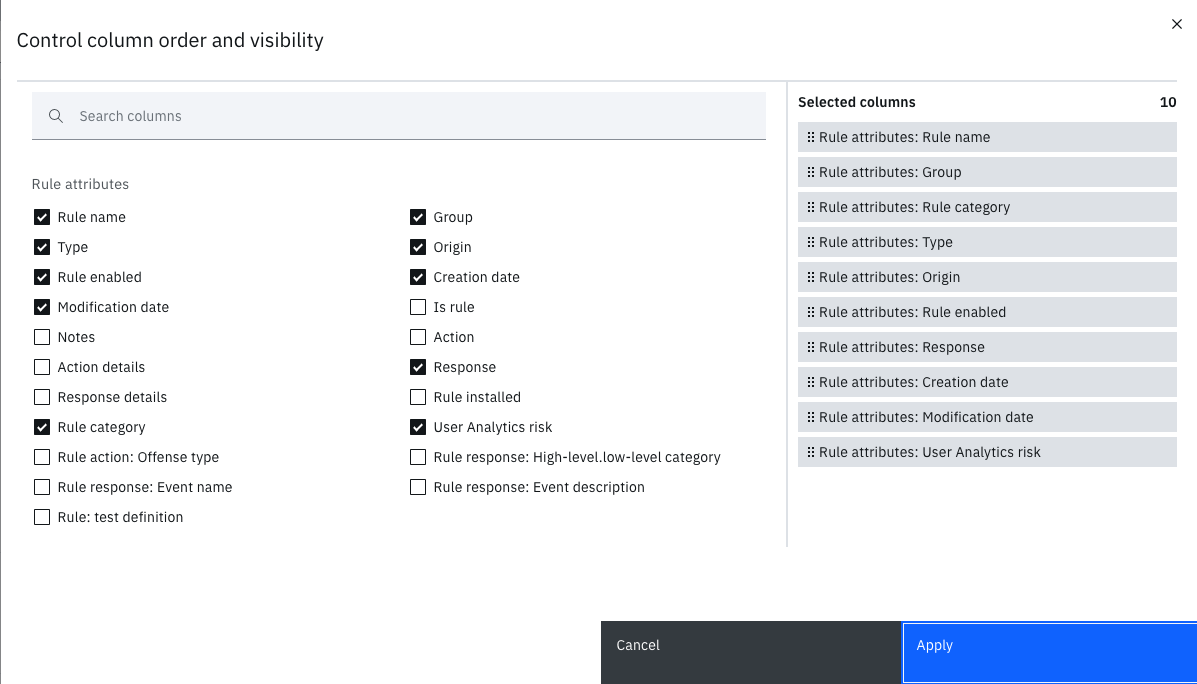
The window to add columns to the table reports was redesigned to make it easier to add columns and arrange the order that they are displayed in the report. Now you can search the columns or scroll through the window to find the column that you want to add.
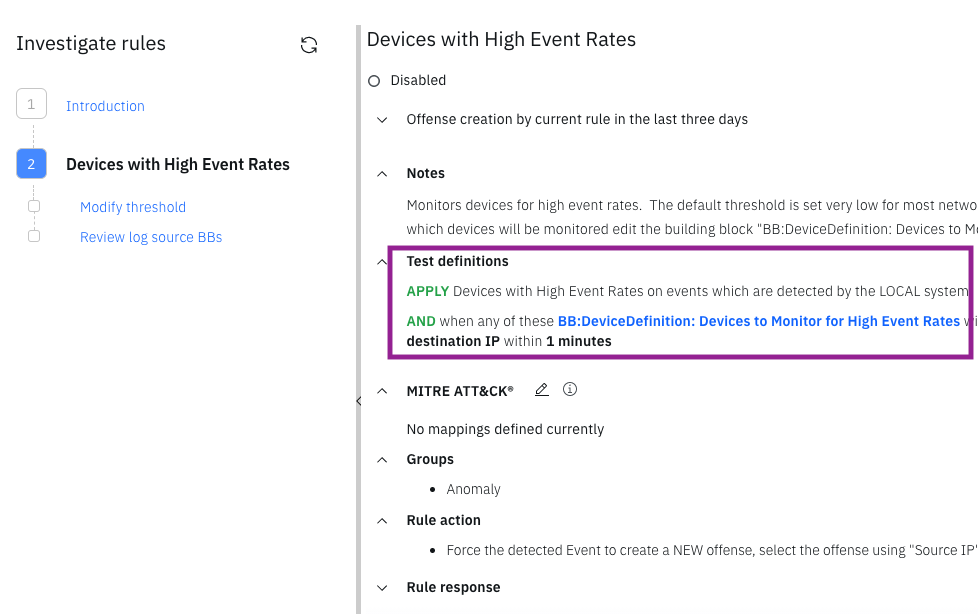
On the rule details page, the name of the building block in the rule test now links and displays the test information for further investigation.
Version 3.1.0
Improved rule export capabilities
Added the ability to export rules and their dependencies as XML that can then be imported into another QRadar deployment using the Extension Management function on the Admin tab. This capability is supported on QRadar 7.4.0 or later. For more information, see Exporting Rules.
MITRE coverage enhancements
Support was added for MITRE v8.1. All custom mappings that were created in previous versions of the app are automatically migrated to the new version. Mappings to techniques that are now deprecated or don't exist under a given tactic will be deleted and included in the migration report. You can review a migration report to see the affected mappings so that you can consider creating new mappings to these rules. For more information about technique deprecation, see https://attack.mitre.org/resources/updates/.
Added support for MITRE sub-techniques in reports, filters, and templates. Sub-techniques provide a more specific description of the behavior an adversary uses to achieve their goal, such as dumping credentials by accessing the Local Security Authority (LSA) Secrets. Sub-techniques are added to the MITRE heat maps for the Detected in timeframe and Coverage map and report charts.
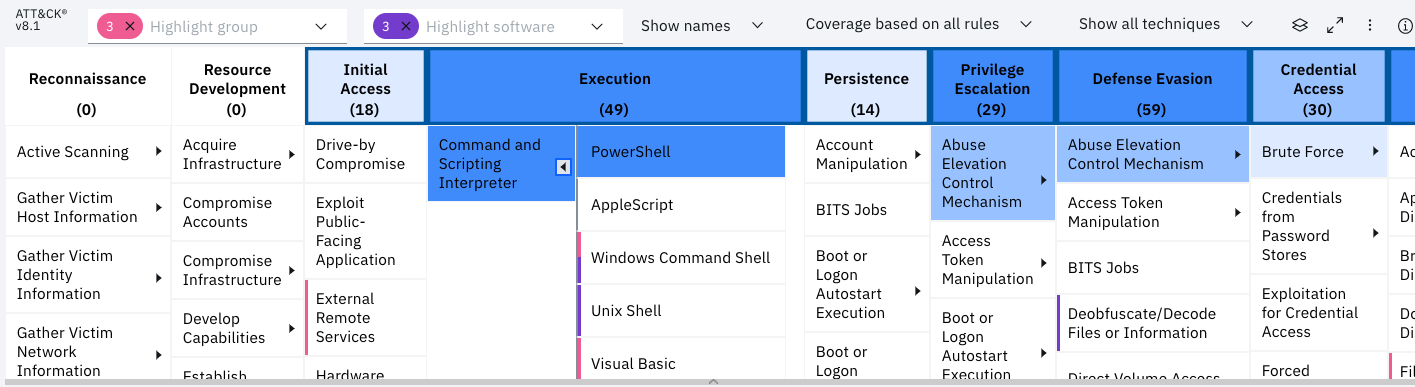
Enhanced the MITRE heat map chart displays by adding tooltips that list the software or group selections when you hover over vertical lines in the chart. The heat map calculations were adjusted for each technique; all mappings to its sub-techniques are counted as if they are mappings to that technique. Numbers in the chart header and cells indicate the number of enabled rules that are mapped to each tactic, technique, and sub-technique. Tooltips were added to explain how the color correlates with the heat map calculation. You can also choose how you see tactics and techniques that are displayed in the chart by showing their name, ID, or a combination of both. For more information, see Visualizing MITRE tactics and techniques that are detected in a specific timeframe and Visualizing MITRE tactic and technique coverage in your environment.
When you edit MITRE mappings in multiple rules or building blocks, you can now add or remove sub-techniques for each technique. For more information, see .Editing MITRE Mappings in Multiple Rules or Building Blocks
Now you can export MITRE mappings to a JSON file that can be imported as a layer into the MITRE ATT&CK Navigator. For more information, see Sharing MITRE-mapping Files.
Log source coverage enhancements
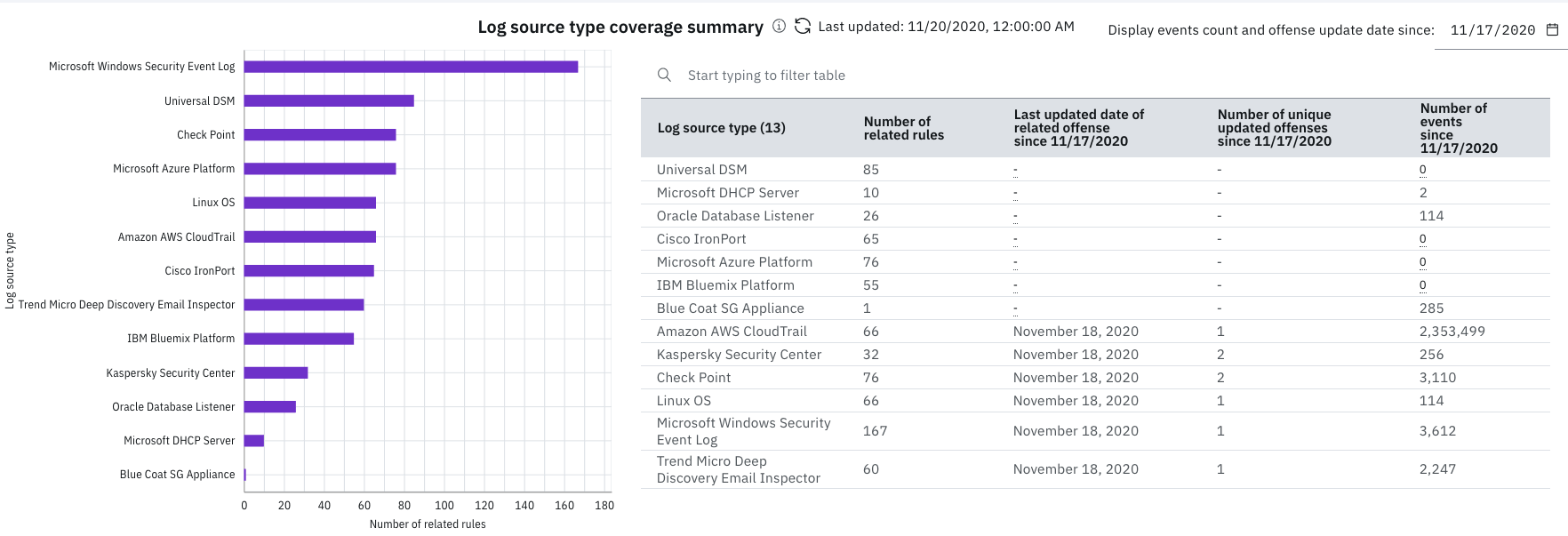
The Log source type coverage summary chart displays the number of rules that provide coverage for each log source type, and when the log source type last contributed to an offense, based on the last updated date. Use the table to review the number of events for log sources of that type. If the last updated date of an offense is old, try tuning some of the rules for the related log source type. For more information, see Visualizing log source type coverage per rule.
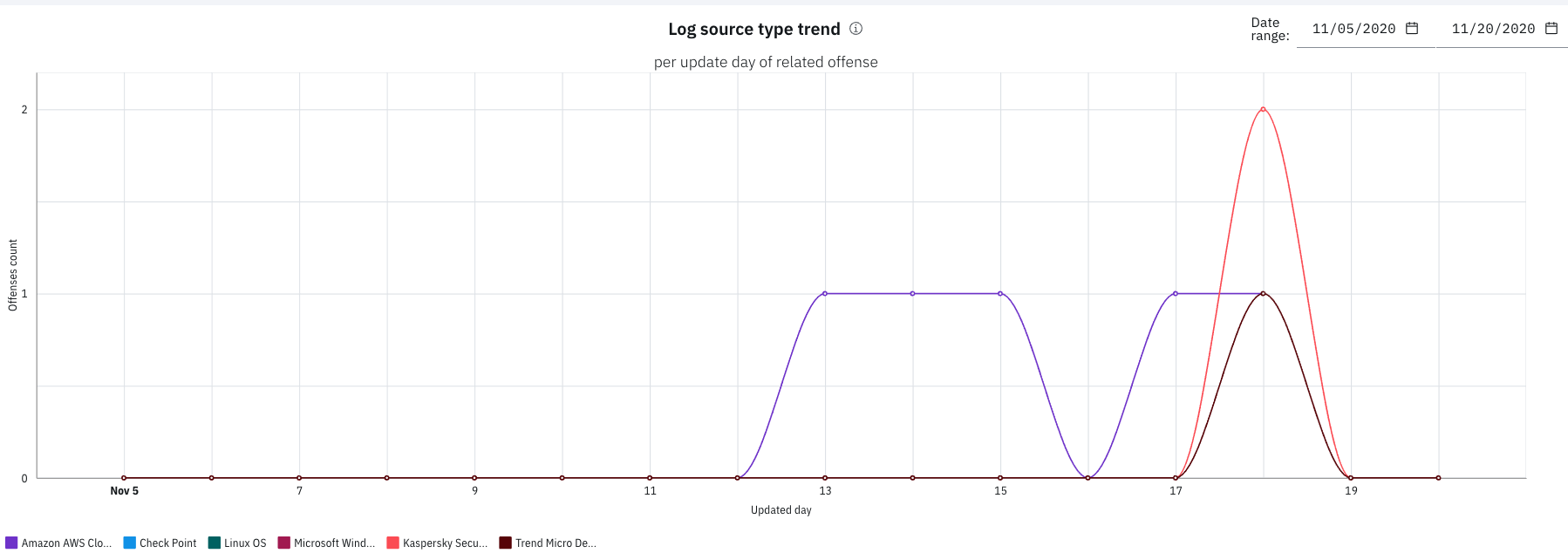
The Log source type trend chart displays the number of offenses that log source types contributed to over time since the app was first installed. You can fine-tune the chart by specific log source type by clicking the checkboxes beneath the chart.
Added the last updated date to the Rules per used log source types chart. The date can help you decide whether to refresh the rule data or wait for the automated refresh to occur.
For more information, see Visualizing Log Source Type Coverage per Rule.
Integrations
Packaged a QRadar Pulse dashboard template. QRadar Pulse users can import this template as a dashboard into their Pulse workspace to view the following charts:
-
MITRE rule mappings per tactic
-
MITRE rule mappings trend per tactic
-
Current and potential rules per used log source type
-
Log source type coverage and activity
For more information, see Synchronizing dashboard templates from content extensions.
Any links to offenses now link to the offenses page in the QRadar Analyst Workflow, if it is installed in your environment. When QRadar Use Case Manager opens from the QRadar Analyst Workflow, it appears in the theme that is selected in Analyst workflow.
Any links to reference sets now link to the reference sets in QRadar Reference Data Management app, if the app is installed in your environment.
Enhanced templates and report column data
You can edit the name and description of custom templates. For more information, see Customizing Report Content Templates.
Change the default template at any time. The default template now runs when the use case explorer page is first loaded.
Use the new column Test: Reference set (number of elements) for a quick reference to rules that depend on reference sets that are empty or have many elements. For example, select the Rules per reference set template, and then use the column customization option to replace the Reference set column with the Reference set (number of elements) column.
Version 3.0.0
Work more efficiently
Customizable user preferences include the option to use a light or dark theme and an option to reduce or increase table row height of the rule report. The default row height is now smaller than before to save space. For more information, see Customizing User Preferences.
Support for multiple languages was added based on QRadar user preferences. Supported languages include English, Simplified Chinese, Traditional Chinese, French, German, Korean, Portuguese, Russian, Spanish, Italian, and Japanese.
You can expand the relationship graph and MITRE coverage heat maps to fit the whole window, and zoom in or out to focus on details. Any filtering that you apply in the expanded pane is kept when you return to the Use Case Explorer page.
You can also further customize the table groupings in the rule report by choosing to show child rows or only the count of child rows in the grouped mode of the report. Click the arrow in the tree structure icon. Then, select from the groupable columns that are currently displayed or show only the number of child rows in the report instead of the actual rows. After you have the number of items in the report column, click the number to see the list of actual child items. For more information, see Rule Report Presentation.
Save time and effort from creating new rules by duplicating existing rules. Then, you can customize the duplicated rules to meet the needs of your environment. For more information, see Duplicating Rules for Further Customization.
Visualize MITRE coverage in new ways
The MITRE Coverage Summary and MITRE Coverage Trend reports provide new ways of visualizing MITRE ATT&CK coverage. In the coverage summary report, you can check the current number and percentage to see where you're lacking in rule coverage, and plan to increase coverage for some tactics. The trend report shows the total rule coverage trend over time. For more information, see Visualizing MITRE Tactic and Technique Coverage in Your Environment.
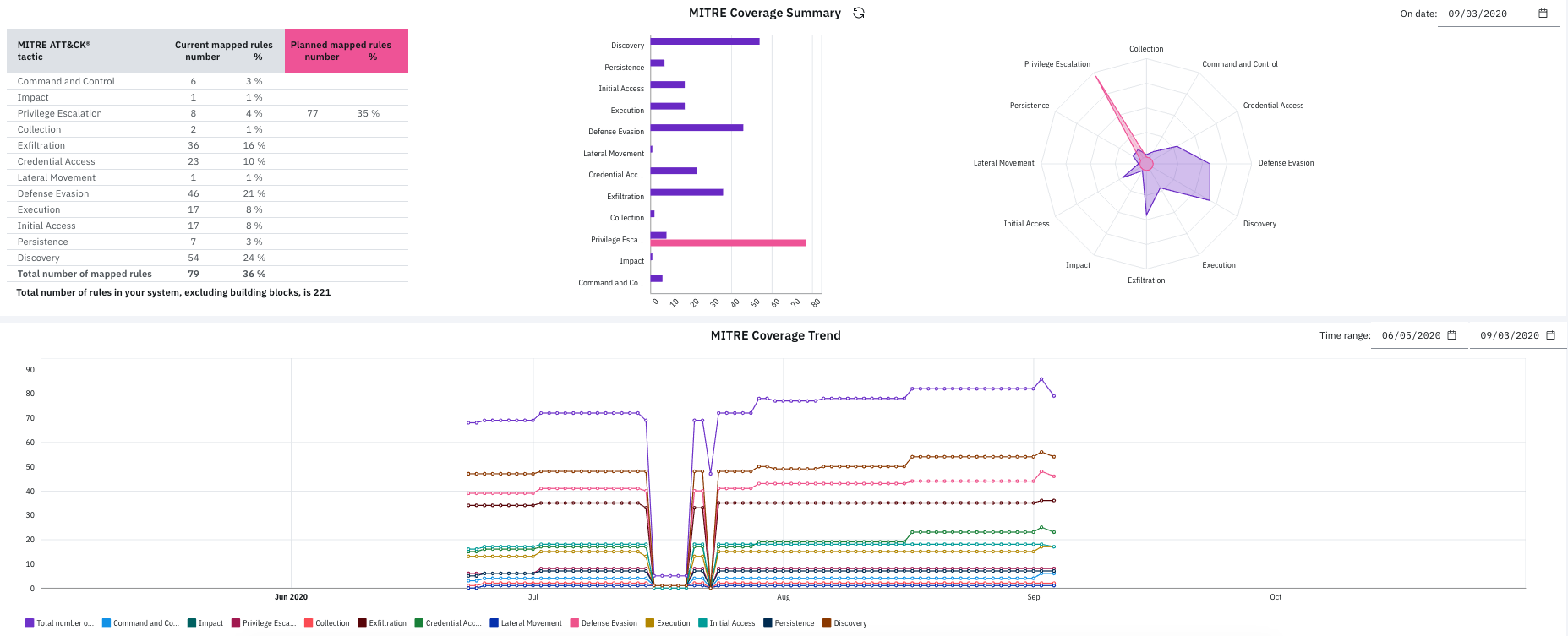
On MITRE coverage heat maps, you can identify techniques that are used by groups or software that is identified by MITRE. You can also filter out (hide) techniques in the chart that are not related to the techniques currently selected in filter for report. For more information, see Visualizing MITRE Tactic and Technique Coverage in Your Environment.
Improve your rule coverage by adding content extensions from the IBM Security App Exchange
Content awareness capabilities help you see from which content extension the rules originate. Filter by content extensions for installed rules and uninstalled rules available in content extensions on IBM Security App Exchange. Link from content extension names in the report to the corresponding dialog in QRadar Assistant app for easier installation or updating. New predefined templates recommend content extensions from IBM Security App Exchange based on increased log source and MITRE coverage.
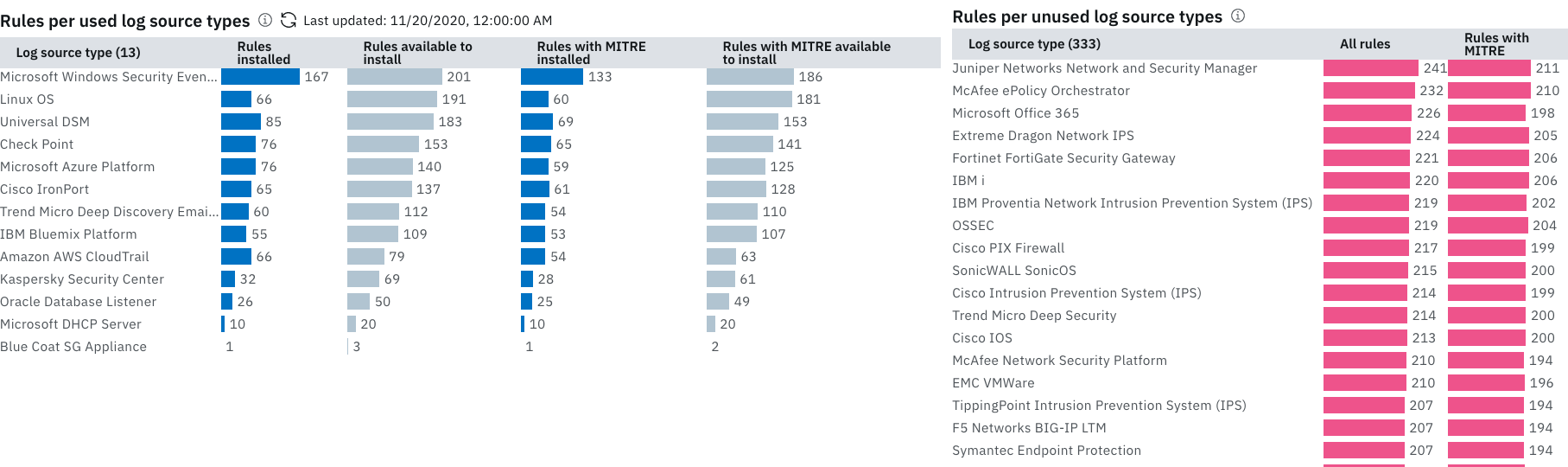
New charts show an overview of log source coverage and MITRE coverage by currently installed rules and uninstalled rules that can be installed from IBM Security App Exchange. For more information, see Identifying Gaps in QRadar Rule Coverage from Content Extensions.
Apply rule and building block filters more easily
Previously, the Apply button was visible at the bottom of the pane, but it was often difficult to realize that you had to click it to apply the filters. Now, it appears only when you select at least one filter in the pane. As you select filters, they appear in a different color in the filter row, but they change color after you click Apply Filters.
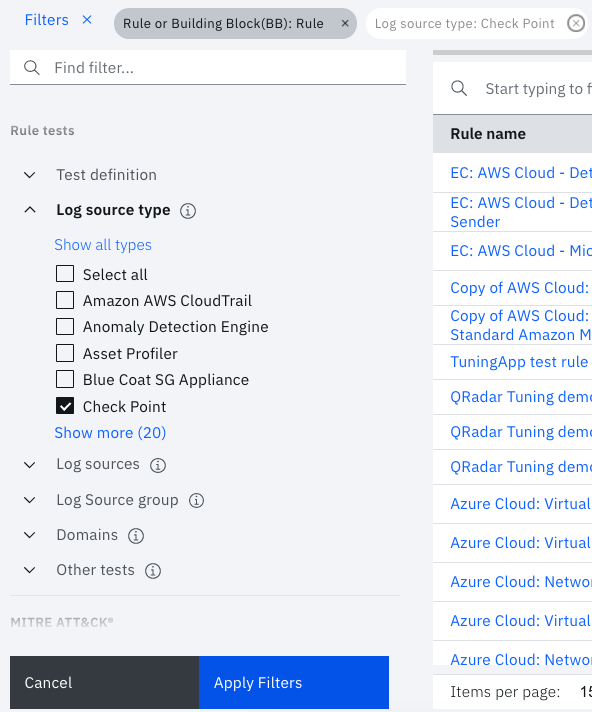
A new search filter in the log source rule test facilitates filtering when the list contains many log sources. You can also filter rules that are related to only used log sources types or unused log source types.
Rule wizard contains more data and is easier to read
The following enhancements were made to improve tuning in the rule wizard:
-
Added all parts of rule action and rule response to rule details page. Also added two new columns: Rule attribute: Rule action details and Rule attribute: Rule response details that contain complete rule action and rule response information.
-
Added the rule scope information before the test definition section to indicate whether the rule is global or local.
-
The log source type section is now sorted and includes the number of log source types.
-
Rule details are now refreshed automatically after you edit MITRE mappings for the rule.
-
Improved layout of rule details page by rearranging sections and expanding some sections by default.
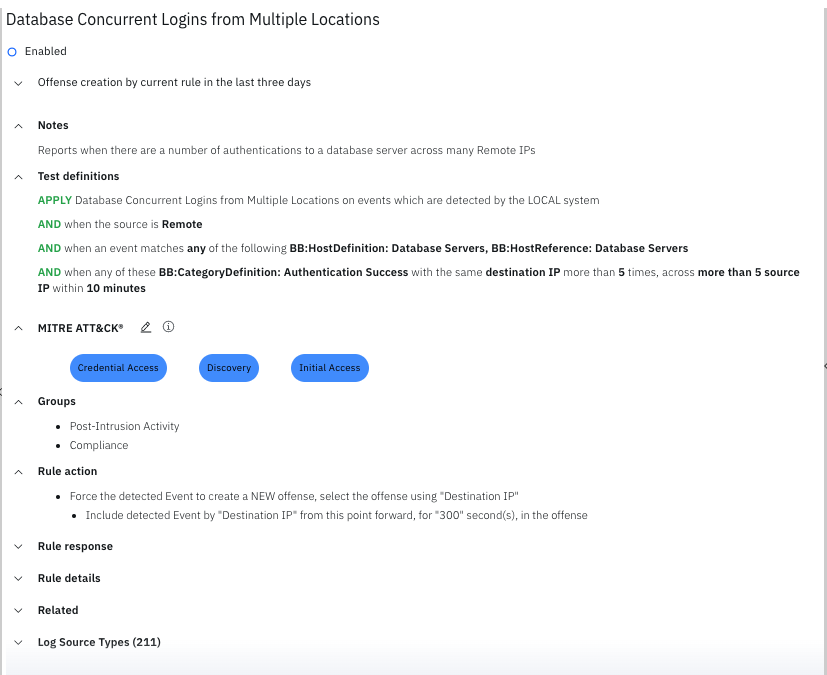
Configure a proxy
You can now configure a proxy so that QRadar Use Case Manager can access the IBM Security App Exchange to get up-to-date information about non-installed content extensions and MITRE mappings for all content extensions. If you don't configure the proxy, you can still see the information in the app, but be aware that it can become out of date.
Version 2.3.1
Performance improvements
Improved performance for generating MITRE-related reports and heat map coverage visualization, as well as overall report generation.
Version 2.3.0
Moved the MITRE-mapping capabilities into the app
The MITRE-mapping capabilities were moved to QRadar Use Case Manager. This streamlines the process of editing rule MITRE mappings. The Cyber Adversary Framework Mapping app is no longer included in the QRadar Use Case Manager installation package. If the Cyber Adversary Framework Mapping app is already installed, QRadar Use Case Manager gathers any existing mappings during installation. Afterward, you can delete the Cyber Adversary Framework Mapping app and use QRadar Use Case Manager instead to help ensure that all your rule mappings are up to date in the app.
Reduced memory requirement
Reduced the memory requirement of the app to 500 MB.
Edit rule MITRE mappings
Save time and effort by selecting several rules and editing the MITRE mappings for all of them at once. If needed, you can also export the selected mappings that you edited.
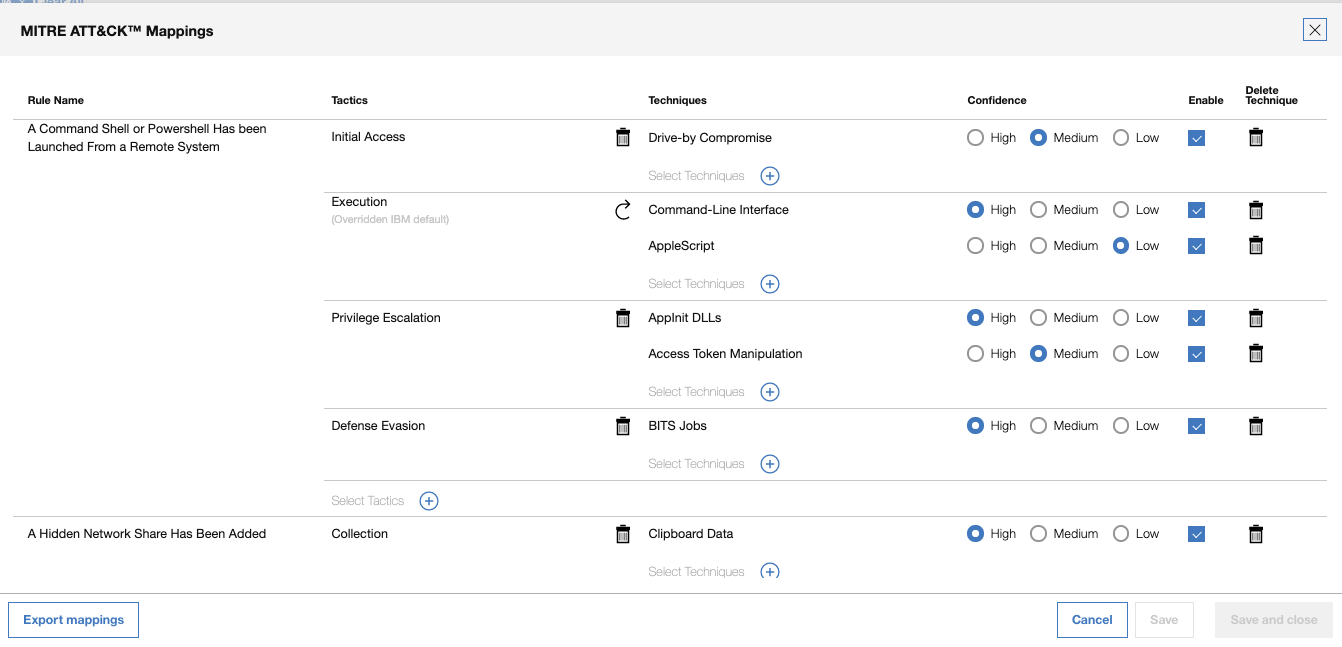
Enhanced exporting capabilities
Added options to export only the MITRE mappings for the rules in the current report view or export all the rule mappings in the app. Share the JSON file with your other instances of QRadar Use Case Manager.
Rules Explorer enhancements
New MITRE Tactic ID and MITRE Technique ID columns are now available as options in the rule report to provide more context.
Select multiple rules and open them in the Rule Wizard for simultaneous investigation.
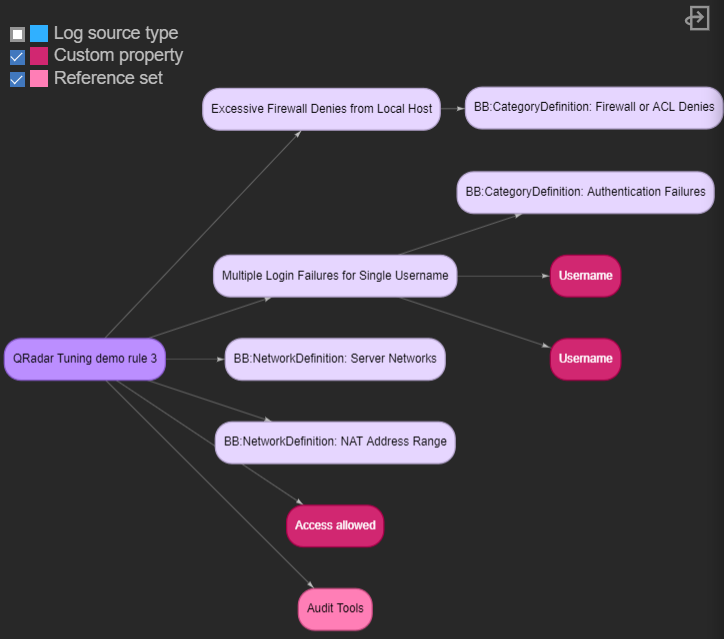
Rule visualization enhancement
Added options to show related reference sets, custom properties, and log source types.
Fixed issue
Fixed an issue where the SNMP Trap was not visible in the rule details page when SNMP Trap was selected as a rule response attribute on the rule details page.
Version 2.2.0
MITRE improvements
You can now see which MITRE ATT&CK tactics and techniques were detected in your environment in a specific time period. A heat map and flexible reports show the detected tactics and techniques and related rules and offenses. For more information, see Visualizing MITRE Tactics and Techniques that are Detected in a Specific Timeframe.
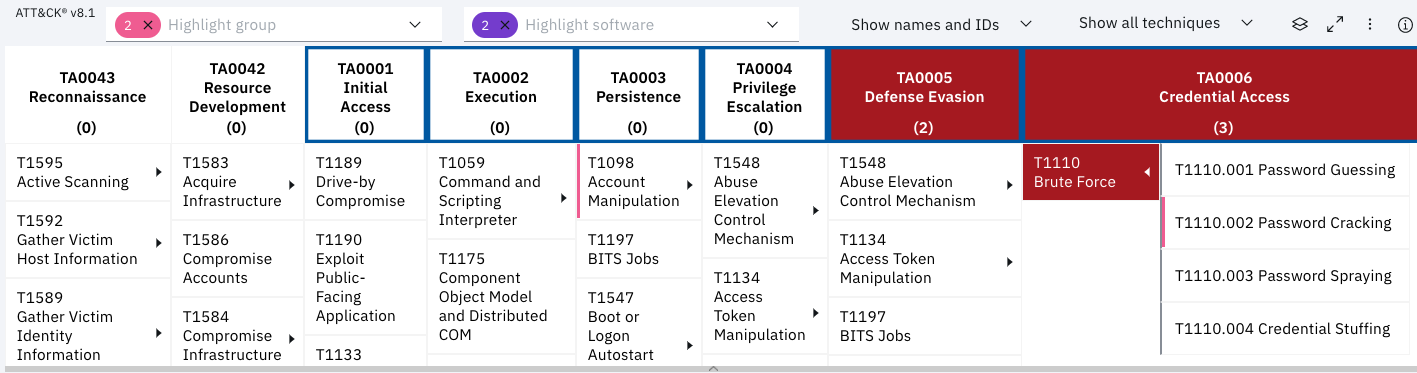
ATT&CK options are now more visible in the Rule Explorer
An ATT&CK Actions menu makes it easier to access the heat maps to see rule coverage and detected tactics and techniques. A switch for the coverage heat map filters the table coloring based on only the rule mappings in the current report or by all the rules in your environment.
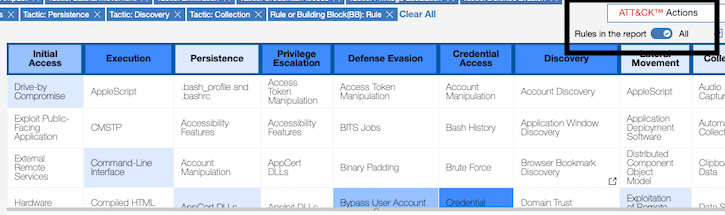
MITRE tactics table header stays fixed for easier scrolling
The tactics header in the heat map is now in a fixed state while you scroll down the table, making it easier to track the tactics and techniques that you're reviewing.
Rule Explorer enhancements
Domains are now represented by the rule test filters. The domain filter group lists all the domains in a multi-domain environment. For more information, see Filtering Rules and Building Blocks by their Properties.
A new Rule Response: Event Description column is available as an option in the rule report to provide more context.
Rule wizard enhancement
A MITRE tag in the rule details screen of the rule wizard now shows the source BB or rule from where the mapping originates. This information also displays as a column in the rule report.
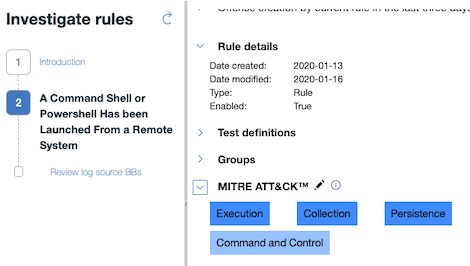
Fixed issues
-
Problems related to renaming system rules when either old name or duplicate name shows up in Rule Explorer
-
Problems in early patches of QRadar 7.3.1 where QRadar Use Case Manager 2.1.0 didn't work.
Version 2.1.0
-
Added an option to group related data properties in the report table. For more information, see Rule Report Presentation.
-
Create custom templates in the Rules Explorer from existing templates or create new ones. For more information, see Customizing Report Content Templates.
-
Added a "Select all" option to the rules attribute filter to make it easier to select all the groups in the list.
-
Added a Notes filter to the Rule Attributes page to search for specific rules with notes.
-
The app now detects when newer versions are available to download on the IBM Security App Exchange.
-
Implemented the following usability improvements that are related to MITRE ATT&CK:
-
Added an exploratory icon link to the MITRE documentation for each tactic and technique in the technique coverage heat map.
-
Added a Mapping enabled column to the filters and the report, which indicates that the mapping between Cyber Adversary Framework Mapping app and QRadar is turned on. Mappings that are disabled are not added to the technique coverage heat map.
-
Added capabilities to the rule wizard to open the rule directly in the Cyber Adversary Framework Mapping app for editing.
-
Re-calibrated the heat map formula to use only enabled rules to calculate the heat map colors.
-
Added a tooltip to the MITRE ATT&CK filter page to remind users to set an authentication token for the Cyber Adversary Framework Mapping app.
-
Added a column selection option for Tactic (at rule level) and Technique (at rule level) to show only values that are mapped directly to the rule.
-
-
Fixed an issue where the way QRadar handles incomplete rules causes some APIs in some product versions to fail, and causes data inconsistencies in QRadar Use Case Manager.
-
Fixed an issue where the log source type filter doesn't have any values in cases where there are more than 50,000 log sources.
Version 2.0.0
-
Added a rule explorer to filter rules by different properties, such as attributes, rule tests, and MITRE ATT&CK tactics and techniques. Use filters to ensure that the rules are defined and working as intended, including log source coverage. Determine which rules you might need to edit in QRadar or investigate further in QRadar Use Case Manager.
-
Added the Cyber Adversary Framework Mapping app. With the Cyber Adversary Framework Mapping app, you can map your custom rules and building blocks to MITRE ATT&CK tactics and techniques and override the QRadar default rule mappings.
-
Added MITRE ATT&CK tactics visualization and the ability to customize your mappings with the Cyber Adversary Framework Mapping app.
-
Made the following minor UI improvements:
-
Added a wrench icon to any links and buttons that lead to the investigation wizard.
-
Added links for reference sets to open in QRadar.
-
Version 1.1.0
-
Automatically download rules in IBM QRadar 7.3.2 or later.
-
Added the ability to edit IP addresses of reference sets in the IPs & Ports tab of the Host definitions page. Supported in IBM QRadar 7.3.1 or later.
-
Added the ability to edit ports of building blocks and rules in the IPs & Ports tab of the Host definitions page. Supported in IBM QRadar 7.3.2 or later.
Version 1.0.1
Increased the rules.xml file upload limit to 50 MB.
Version 1.0.0
-
Tune most active rules
-
Tune most active rules based on the CRE event report
-
Review network hierarchy
-
Review building blocks
In this early access version, you need to run a script on the QRadar Console to generate a rules data file and then upload it to the app. This temporary step might not be required in later releases.
