Visualizing Log Source Type Coverage per Rule
Explore current and potential log source type coverage per rule, and see how your rule coverage can expand if new log source types are added to your environment. See the number of rules that provide current coverage for each log source type, based on the rule test definitions.
-
To see the number of rules that provide current coverage for each log source
type based on the rule test definitions, click Rule-log source type
coverage > Summary and offense update
trends.
-
In the Log source type coverage summary table,
check when the log source type last contributed to an offense based on
the last updated date. Then, review the number of events for log sources
of that type. If the last updated date of an offense is old, try tuning
some of the rules for the related log source type. For example, you have
81 rules for a log source type that stopped contributing to an offense
for three weeks and has no events that are associated with it. The 81
rules require investigation to see whether there's something wrong with
them. You can also filter the list in the table chart to fine-tune the
log source types you want to investigate.
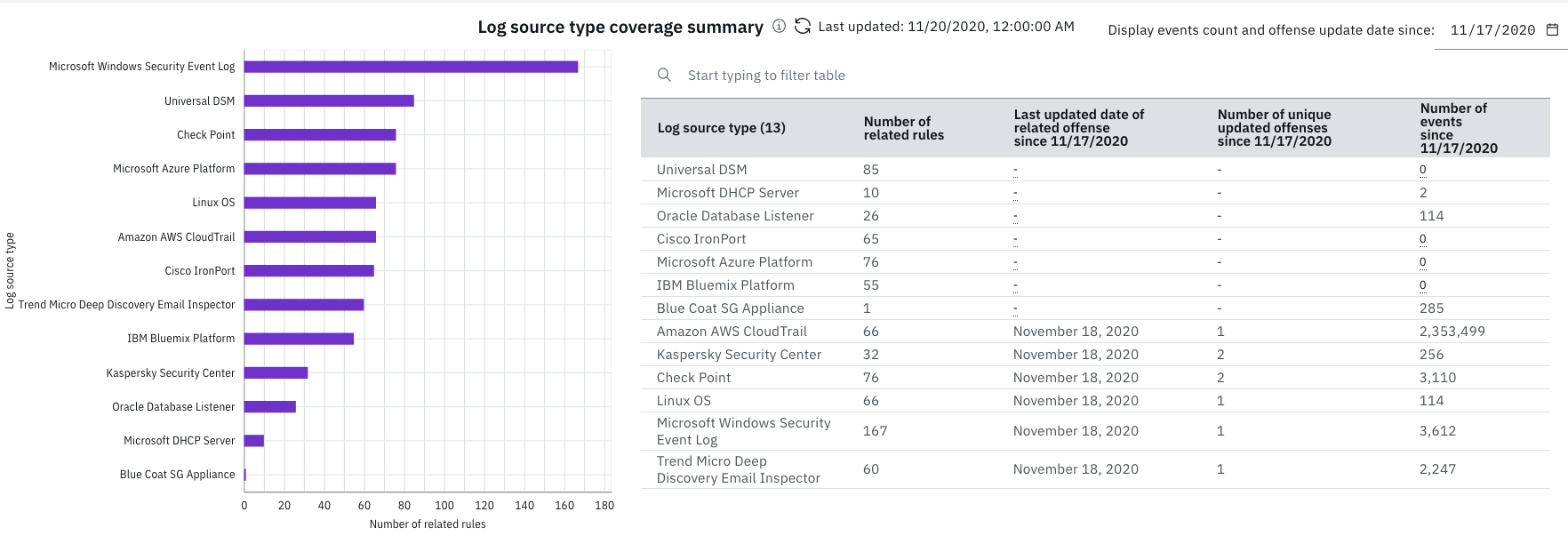
The bar chart is a visualization of the table chart.
-
Change the date for the Log source type coverage
summary chart coverage by clicking the calendar icon for
Display events and offense updated date since:
<date>. QRadar Use Case Manager initially fetches
90 days of data from QRadar, and keeps collecting data daily for 1 year.
Data older than 1 year is then deleted from the database. The default
date is one day before the current day's date.
For more information, see Example log source type coverage summary table.
-
In the Log source type trend chart, review the
number of offenses that are updated on a specific day and related to a
specific log source type. Updated offenses are counted against each
related log source type, regardless of the log source type that caused
the update. Fine-tune the chart by specific log source type by clicking
the checkboxes beneath the chart.
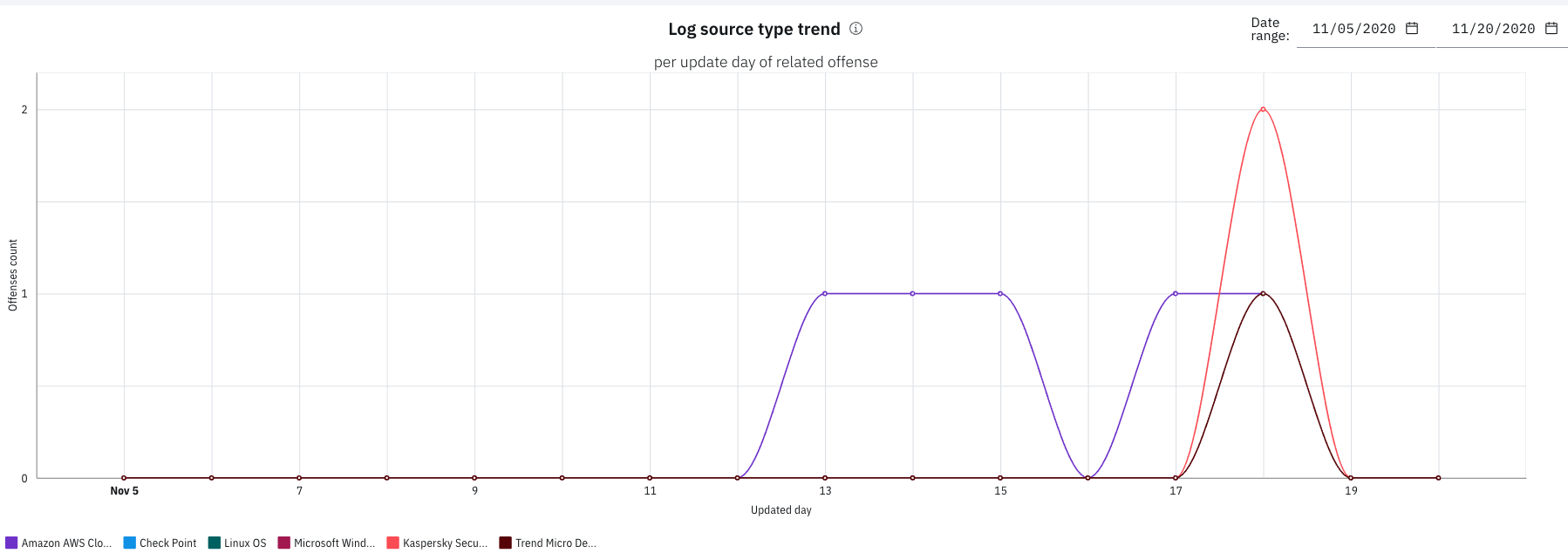
- Change the date for the Log source type trend chart coverage by clicking the calendar icons for Date range. Trend data is only available from the date of app installation.
-
In the Log source type coverage summary table,
check when the log source type last contributed to an offense based on
the last updated date. Then, review the number of events for log sources
of that type. If the last updated date of an offense is old, try tuning
some of the rules for the related log source type. For example, you have
81 rules for a log source type that stopped contributing to an offense
for three weeks and has no events that are associated with it. The 81
rules require investigation to see whether there's something wrong with
them. You can also filter the list in the table chart to fine-tune the
log source types you want to investigate.
-
To see current and potential log source type coverage, click
Rule-log source type coverage > Current and
potential.
 Note:
Note:QRadar Use Case Manager excludes log source types that QRadar considers 'internal' from these charts; for example, Health Metrics, SIM Audits, Custom Rule Engine, System Notifications, and Asset Profiler.
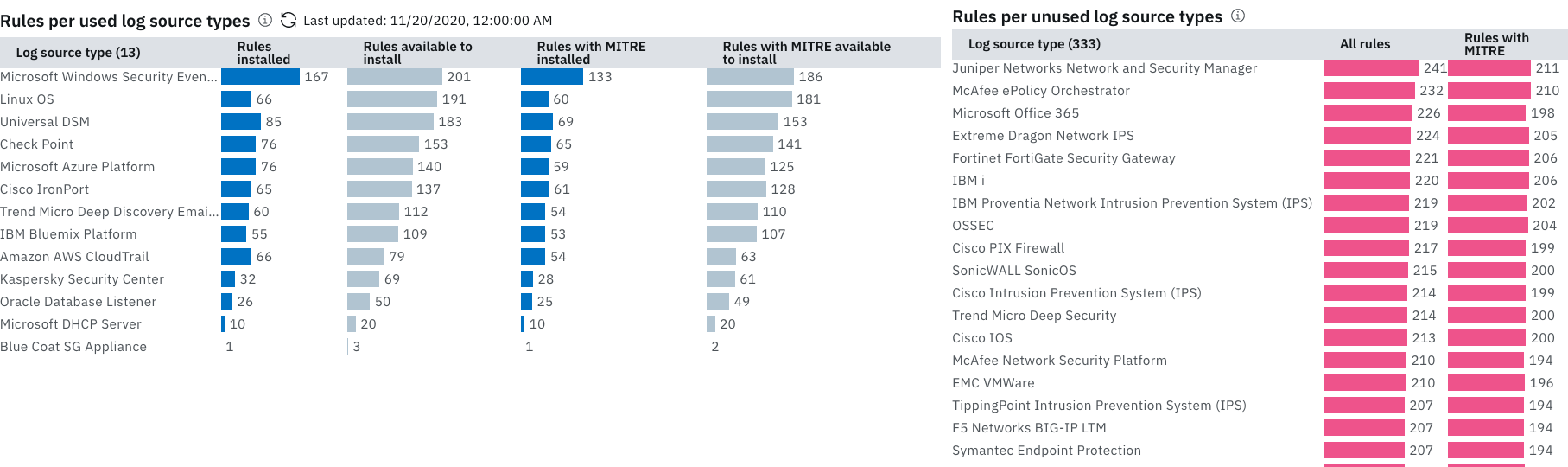
- Explore current and potential coverage in the Rules per used log source types chart. The Rules available to install and the Rules with MITRE available to install columns indicate the number of rules from content extensions that are available on the IBM Security App Exchange. To generate a report of content extensions for a selected log source type, select the corresponding bar and click Apply Filters in the filter pane. Then, click the content extension name link in the table report to view or install the content extension.
- Explore how coverage can expand if new log source types are added in the Rules per unused log source types chart. Rules that are represented in the bars are either already installed or available to install from content extensions on the IBM Security App Exchange. To generate a report of the rules and their origin for a selected log source type, select the corresponding bar and then click Apply Filters in the filter pane. Then, click the content extension name link in the table report to view or install the content extension.
Example Log Source Type Coverage Summary Table
The Log source type coverage summary table shows some coverage results since November 16, 2020. Learn how to use these examples to interpret your own results.
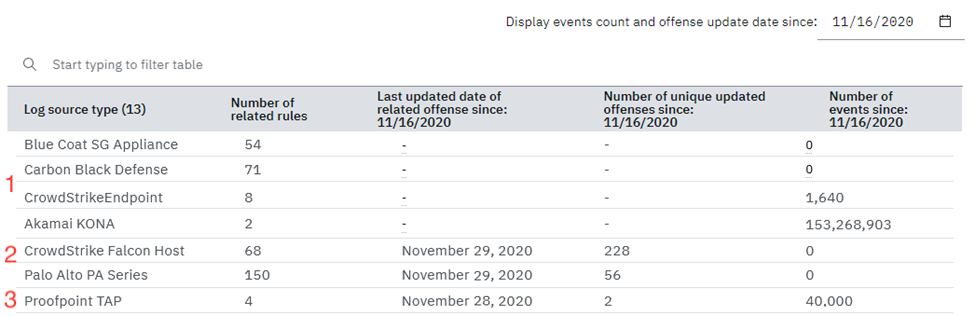
The report was run on 30 November 2020 to track coverage that began on 16 November 2020.
-
The first 4 log source types did not contribute events to any offense since
16 November 2020. Events coming from these log source types didn't affect
any offense in two weeks. The CrowdStrikeEndpoint and Akamai KONA log source
types received events, and although Akamai KONA had almost 154,000,000
events, none of them contributed to any offense. Follow these steps to
resolve these types of cases:
-
Investigate the rules that are related to these log source types for any tuning actions. Run one of the log source coverage templates and add the filter for any needed log source types.
-
Check whether more rules are available to install from the IBM Security App Exchange that can provide better coverage for these log source types. Select Rule-log source type coverage > Current and potential coverage, find the log source type in the chart, and click the bar next to it in the Rules available to install column. Then, apply the filters and check the resulting report.
-
- The CrowdStrike Falcon Host and Palo Alto PA Series log source types show that several offenses were updated, but neither received any events. Because these log source types don't have any events, this means that these log source types are related to some offenses that were updated by events from other log source types.
- The Proofpoint TAP log source type had many events that contributed to two offenses. This is a common example.
