静态端点 IPsec 隧道的服务集
服务集
配置 IPSec 隧道时,自适应服务 PIC 支持两种类型的服务集。由于它们用于不同的目的,因此了解这些服务集类型之间的差异非常重要。
下一跃点服务集 — 支持通过 IPSec 的组播和组播样式动态路由协议(如 OSPF)。下一跃点服务集允许您使用自适应服务 PIC 上的 内部 和 外部 逻辑接口与多个路由实例进行连接。它们还允许使用网络地址转换 (NAT) 和有状态防火墙功能。但是,默认情况下,下一跃点服务集不会监控路由引擎流量,需要配置多个服务集来支持来自多个接口的流量。
接口服务集 — 应用于物理接口,类似于无状态 防火墙过滤器。它们易于配置,可以支持来自多个接口的流量,并且默认情况下可以监控路由引擎流量。但是,它们无法支持动态路由协议或通过 IPSec 隧道的组播流量。
通常,我们建议您使用下一跃点服务集,因为它们支持路由协议和 IPSec 隧道组播,它们更易于理解,并且路由表无需管理干预即可做出转发决策。
也可以看看
配置 IPsec 服务集
IPsec 服务集需要您在层次结构级别配置 [edit services service-set service-set-name ipsec-vpn-options] 的其他规范:
[edit services service-set service-set-name ipsec-vpn-options] anti-replay-window-size bits; clear-dont-fragment-bit; copy-dont-fragment-bit set-dont-fragment-bit ike-access-profile profile-name; local-gateway address <gw-interface interface-name.logical-unit-number>; no-anti-replay; no-certificate-chain-in-ike; passive-mode-tunneling; trusted-ca [ ca-profile-names ]; tunnel-mtu bytes;
以下部分介绍了这些语句的配置:
- 为 IPsec 服务集配置本地网关地址
- 为 IPsec 服务集配置 IKE 访问配置文件
- 为 IPsec 服务集配置证书颁发机构
- 配置或禁用防重放服务
- 清除“不分段”位
- 配置被动模式隧道
- 配置隧道 MTU 值
- 使用 UDP 封装配置 IPsec 多路径转发
为 IPsec 服务集配置本地网关地址
如果配置 IPsec 服务集,还必须通过包含 local-gateway 以下语句来配置本地 IPv4 或 IPv6 地址:
如果互联网密钥交换 (IKE) 网关 IP 地址为 inet.0(默认情况),则配置以下语句:
local-gateway address;
如果 IKE 网关 IP 地址位于 VPN 路由和转发 (VRF) 实例中,则可配置以下语句:
local-gateway address routing-instance instance-name;
您可以在单个下一跃点样式服务集中配置共享相同本地网关地址的所有链路类型隧道。您必须在层次结构级别为[edit services service-set service-set-name]语句指定一个与您在层次结构级别配置[edit services ipsec-vpn rule rule-name term term-name from]的值相匹配ipsec-inside-interface的值inside-service-interface。有关 IPsec 配置的详细信息,请参阅配置 IPsec 规则。
从 Junos OS 16.1 版开始,要配置链路类型隧道(即下一跳样式),以实现高可用性目的,可以在层次结构级别使用[edit services ipsec-vpn rule rule-name term term-name from]语句将 AMS 逻辑接口配置为 IPsec 内部接口ipsec-inside-interface interface-name。
从 Junos OS 17.1 版开始,AMS 支持 IPSec 隧道分配。
VRF 实例中的 IKE 地址
您可以配置 VPN 路由和转发 (VRF) 实例中存在的互联网密钥交换 (IKE) 网关 IP 地址,只要可以通过 VRF 实例访问对等方即可。
对于下一跃点服务集,密钥管理进程 (kmd) 会将 IKE 数据包放置在包含您指定值的 outside-service-interface 路由实例中,如下例所示:
routing-instances vrf-nxthop {
instance-type vrf;
interface sp-1/1/0.2;
...
}
services service-set service-set-1 {
next-hop-service {
inside-service-interface sp-1/1/0.1;
outside-service-interface sp-1/1/0.2;
}
...
}
对于接口服务集,语句确定 service-interface VRF,如以下示例所示:
routing-instances vrf-intf {
instance-type vrf;
interface sp-1/1/0.3;
interface ge-1/2/0.1; # interface on which service set is applied
...
}
services service-set service-set-2 {
interface-service {
service-interface sp-1/1/0.3;
}
...
}
当本地网关地址、MS-MPC 或 MS-MIC 出现故障时清除 SA
从 Junos OS 17.2R1 版开始,当 IPsec 隧道 的本地网关 IP 地址出现问题,或者 隧道 服务集中使用的 MS-MIC 或 MS-MPC 出现故障时,tou 可以使用该 gw-interface 语句来清理IKE触发器以及 IKE 和 IPsec SA。
local-gateway address <gw-interface interface-name.logical-unit-number>;
和 interface-name logical-unit-number 必须与配置本地网关 IP 地址的接口和逻辑单元匹配。
如果 IPsec 隧道的服务集的本地网关 IP 地址关闭,或者服务集中使用的 MS-MIC 或 MS-MPC 关闭,则服务集将不再发送 IKE 触发器。此外,当本地网关 IP 地址中断时,下一跃点服务集将清除 IKE 和 IPsec SA,而接口样式服务集将进入“未安装”状态。当本地网关 IP 地址恢复时,具有“未安装”状态的 SA 将被删除。
如果下一跃点服务集关闭的本地网关 IP 地址用于响应方对等方,则需要清除发起方对等方上的 IKE 和 IPsec SA,以便在本地网关 IP 地址恢复后重新启动 IPsec 隧道。您可以手动清除发起方对等方上的 IKE 和 IPsec SA(请参阅 清除服务 ipsec-vpn IKE 安全关联 和 清除服务 ipsec-vpn ipsec 安全关联),或者在发起方对等方上启用失效对等方检测(请参阅 配置有状态防火墙规则)。
为 IPsec 服务集配置 IKE 访问配置文件
仅对于动态端点隧道,您需要引用在层次结构级别配置[edit access]的 IKE 访问配置文件。为此,请在[edit services service-set service-set-name ipsec-vpn-options]层次结构级别包含该ike-access-profile语句:
[edit services service-set service-set-name ipsec-vpn-options] ike-access-profile profile-name;
该ike-access-profile语句引用的名称必须与您在层次结构级别上[edit access]为 IKE 访问配置的profile语句相同的名称。在每个服务集中只能引用一个访问配置文件。此配置文件仅用于与动态对等方协商 IKE 和 IPsec 安全关联。
如果在服务集中配置 IKE 访问配置文件,则其他服务集不能共享同一 local-gateway 地址。
此外,您必须为每个 VRF 配置单独的服务集。该语句在服务集中引用 ipsec-inside-interface 的所有接口都必须属于同一个 VRF。
为 IPsec 服务集配置证书颁发机构
您可以通过包含 trusted-ca 以下语句来指定一个或多个受信任的认证机构:
trusted-ca [ ca-profile-names ];
在 IPsec 配置中配置公钥基础架构 (PKI) 数字证书时,每个服务集都可以拥有自己的一组受信任的认证机构。您为 trusted-ca 语句指定的名称必须与在层次结构级别上 [edit security pki] 配置的配置文件匹配;有关更多信息,请参阅适用于 路由设备的 Junos OS 管理库。有关 IPsec 数字证书配置的详细信息,请参阅 配置 IPsec 规则。
从 Junos OS 18.2R1 版开始,您可以将 MX 系列路由器配置为 MS-MPC 或 MS-MIC,以便仅发送终端实体证书以进行基于证书的 IKE 身份验证,而不是完整的证书链。这样可以避免 IKE 分段。要配置此功能,请包含以下语 no-certificate-chain-in-ike 句:
[edit services service-set service-set-name ipsec-vpn-options] no-certificate-chain-in-ike;
配置或禁用防重放服务
您可以在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该anti-replay-window-size语句,以指定防重放窗口的大小。
anti-replay-window-size bits;
此语句适用于无法在层次结构级别配置[edit services ipsec-vpn rule rule-name term term-name then]该anti-replay-window-size语句的动态端点隧道。
对于静态 IPsec 隧道,此语句会为此服务集中的所有静态隧道设置防重放窗口大小。如果特定隧道需要特定的防重放窗口大小值,请在层次结构级别设置[edit services ipsec-vpn rule rule-name term term-name then]该anti-replay-window-size语句。如果必须为此服务集中的特定隧道禁用防重放检查,请在层次结构级别设置[edit services ipsec-vpn rule rule-name term term-name then]该no-anti-replay语句。
anti-replay-window-size层次结构级别的 [edit services ipsec-vpn rule rule-name term term-name then] 和 no-anti-replay 设置将替代在层次结构级别指定的[edit services service-set service-set-name ipsec-vpn-options]设置。
您还可以在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该no-anti-replay语句以禁用 IPsec 防重放服务。它偶尔会导致安全关联的互作性问题。
no-anti-replay;
此语句适用于无法在层次结构级别配置[edit services ipsec-vpn rule rule-name term term-name then]该no-anti-reply语句的动态端点隧道。
对于静态 IPsec 隧道,此语句将禁用此服务集中所有隧道的防重放检查。如果必须为特定隧道启用防重放检查,则在层次结构级别设置[edit services ipsec-vpn rule rule-name term term-name then]该anti-replay-window-size语句。
在层次结构级别设置 [edit services ipsec-vpn rule rule-name term term-name then] and anti-replay-window-size no-anti-replay 语句将覆盖在层次结构级别指定的[edit services service-set service-set-name ipsec-vpn-options]设置。
清除“不分段”位
您可以在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该clear-dont-fragment-bit语句,以清除进入 IPsec 隧道的所有 IP 版本 4 (IPv4) 数据包上的不分段 (DF) 位。如果封装的数据包大小超过隧道最大传输单元 (MTU),则数据包将在封装前进行分片。
clear-dont-fragment-bit;
此语句适用于无法在层次结构级别配置[edit services ipsec-vpn rule rule-name term term-name then]该clear-dont-fragment-bit语句的动态端点隧道。
对于静态 IPsec 隧道,设置此语句将清除进入此服务集中所有静态隧道的数据包上的 DF 位。如果想要清除进入特定隧道的数据包上的 DF 位,请在层次结构级别设置clear-dont-fragment-bit[edit services ipsec-vpn rule rule-name term term-name then]该语句。
从 Junos OS 14.1 版开始,在通过动态端点 IPSec 隧道传输的数据包中,您可以启用在进入隧道的数据包的 DF 位中设置的值仅复制到 IPsec 数据包的外部标头,并且不会导致对 IPsec 数据包内部标头中的 DF 位进行任何修改。如果数据包大小超过隧道最大传输单元 (MTU) 值,则数据包将在封装前进行分片。对于 IPsec 隧道,无论接口 MTU 设置如何,默认 MTU 值均为 1500。要将 DF 位值仅复制到外部报头,而不修改内部报头,请在层次结构级别使用[edit services service-set service-set-name ipsec-vpn-options]该copy-dont-fragment-bit语句。您还可以将 DF 位配置为仅在 IPsec 数据包的外部 IPv4 报头中设置,而不在内部 IPv4 报头中定义。要仅在 IPsec 数据包的外部报头中配置 DF 位,而不修改内部报头,请在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该set-dont-fragment-bit语句。这些设置适用于动态端点隧道,而不适用于静态隧道,您需要在层次结构级别包含 copy-dont-fragment-bit [edit services ipsec-vpn rule rule-name term term-name then] and set-dont-fragment-bit 语句,以清除进入静态隧道的 IPv4 数据包中的 DF 位。配备 MS-MIC 和 MS-MPC 的 MX 系列路由器支持这些功能。
配置被动模式隧道
您可以在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该passive-mode-tunneling语句,以使服务集能够通过隧道发送格式错误的数据包。
[edit services service-set service-set-name ipsec-vpn-options] passive-mode-tunneling;
此功能绕过主动 IP 检查(如版本、TTL、协议、选项、地址和其他 Land 攻击检查),并按原样对数据包进行隧道传输。如果未配置此语句,则未通过 IP 检查的数据包将在 PIC 中被丢弃。在被动模式下,内部数据包不会受到影响;如果数据包大小超过隧道 MTU 值,则不会生成 ICMP 错误。
IPsec 隧道不会被视为下一跃点,TTL 也不会递减。由于如果数据包大小超过隧道MTU值,则不会生成 ICMP 错误,因此即使数据包超过隧道MTU阈值,也会通过隧道传输数据包。
此功能类似于“跟踪 Junos VPN Site Secure作”中所述的语句提供的功能no-ipsec-tunnel-in-traceroute。从 Junos OS 14.2 版开始,MS-MIC 和 MS-MPC 支持被动模式隧道。
从 Junos OS 14.2 版开始, header-integrity-check MS-MIC 和 MS-MPC 支持的选项用于验证数据包标头是否存在 IP、TCP、UDP 和 ICMP 信息中的异常,并标记此类异常和错误,其功能与被动模式隧道引入的功能相反。如果在 MS-MIC 和 MS-MPC 上同时 header-integrity-check 配置语句和 passive-mode tunneling 语句,并尝试提交此类配置,则在提交期间将显示错误。
被动模式隧道功能(通过在层次结构级别包含passive-mode-tunnelin[edit services service-set service-set-name ipsec-vpn-options]语句)是在 traceroute 输出中禁用 IPsec 隧道端点的功能的超集(通过在no-ipsec-tunnel-in-traceroute层次结构级别包含[edit services ipsec-vpn]语句)。被动模式隧道除了不将隧道视为语句配置no-ipsec-tunnel-in-traceroute的下一跃点外,还会绕过主动 IP 检查和隧道 MTU 检查。
配置隧道 MTU 值
您可以在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该tunnel-mtu语句,以设置 IPsec 隧道的最大传输单元 (MTU) 值。
tunnel-mtu bytes;
此语句适用于无法在层次结构级别配置[edit services ipsec-vpn rule rule-name term term-name then]该tunnel-mtu语句的动态端点隧道。
对于静态 IPsec 隧道,此语句将为此服务集中的所有隧道设置隧道 MTU 值。如果需要特定隧道的特定值,请在层次结构级别设置[edit services ipsec-vpn rule rule-name term term-name then]该tunnel-mtu语句。
tunnel-mtu层次结构级别的[edit services ipsec-vpn rule rule-name term term-name then]设置将覆盖在层次结构级别指定的[edit services service-set service-set-name ipsec-vpn-options]值。
使用 UDP 封装配置 IPsec 多路径转发
从 Junos OS 16.1 版开始,您可以通过在服务集中配置 UDP 封装来启用 IPsec 流量的多路径转发,这会将 UDP 报头添加到数据包的 IPsec 封装中。这会导致 IPsec 流量经过多个路径转发,从而增加 IPsec 流量的吞吐量。如果不启用 UDP 封装,则所有 IPsec 流量都将遵循单一的转发路径。
检测到 NAT-T 时,只会进行 NAT-T UDP 封装,而不对 IPsec 数据包进行 UDP 封装。
要启用 UDP 封装:
启用 UDP 封装。
[edit services service-set service-set-name ipsec-vpn-options] user@host set udp-encapsulation
(选答)指定 UDP 目标端口号。
[edit services service-set service-set-name ipsec-vpn-options udp-encapsulation] user@host set udp-dest-port destination-port
使用 1025 到 65536 之间的目标端口号,但不要使用 4500。如果未指定端口号,则默认目的端口为 4565。
也可以看看
示例:使用数字证书的 IKE 动态 SA 配置
此示例说明如何使用数字证书配置 IKE 动态 SA,其中包含以下部分。
要求
此示例使用以下硬件和软件组件:
四台安装有多服务接口的 M Series、MX 系列 或 T Series 路由器。
Junos OS 9.4 或更高版本。
在配置此示例之前,您必须请求证书颁发机构证书,创建本地证书,并将这些数字证书加载到路由器中。有关详细信息,请参阅注册 证书。
概述
安全关联 (SA) 是一种单工连接,使两台主机能够使用 IPsec 安全地相互通信。此示例说明了使用数字证书进行的 IKE 动态 SA 配置。使用数字证书可为您的 IKE 隧道提供额外的安全性。使用服务 PIC 中的默认值,无需配置 IPsec 提议或 IPsec 策略。但是,您必须配置指定数字证书使用的IKE提议,在IKE策略中引用IKE提议和本地证书,并将证书颁发机构配置文件应用于服务集。
图 1 显示了包含一组四台路由器的 IPsec 拓扑。此配置要求路由器 2 和 3 使用数字证书代替预共享密钥来建立基于 IKE 的 IPsec 隧道。路由器 1 和 4 提供基本连接,用于验证 IPsec 隧道是否正常运行。
拓扑结构
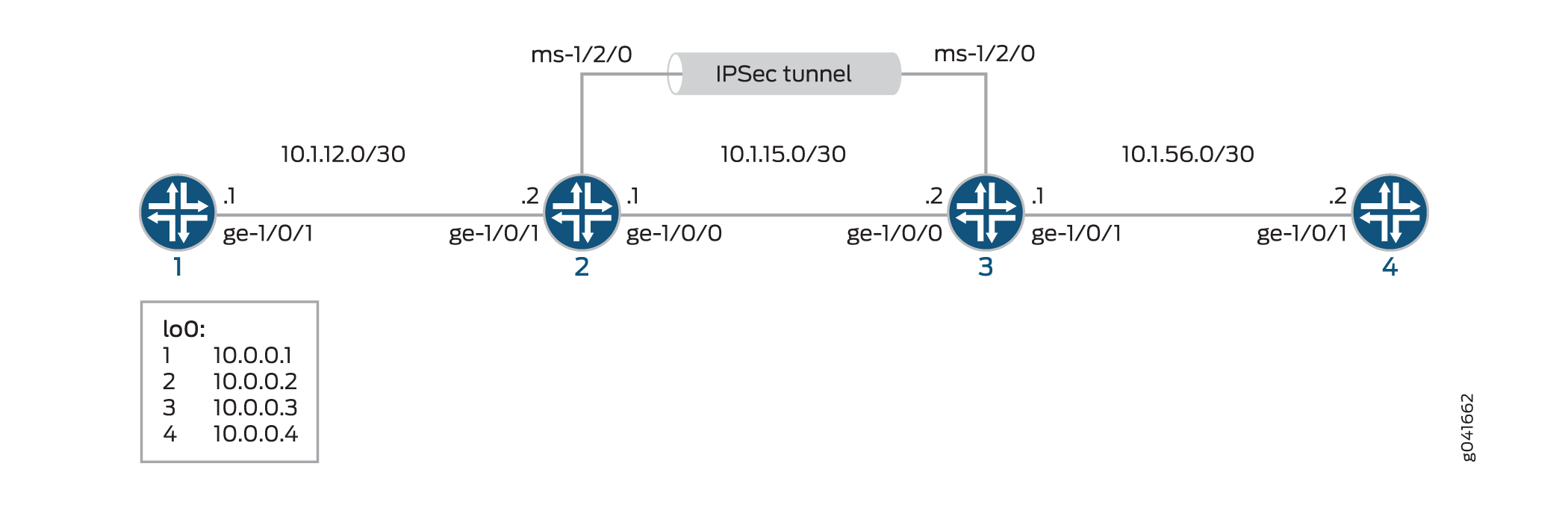
配置
要使用数字证书配置 IKE 动态 SA,请执行以下任务:
此示例中显示的接口类型仅供参考。例如,您可以使用 so- 接口代替 ge- sp- ms-和 。
配置路由器 1
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 1 的 [edit] 层级的 CLI 中。
set interfaces ge-0/0/0 description "to R2 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.12.2/30 set interfaces lo0 unit 0 family inet address 10.0.0.1/32 set routing-options router-id 10.0.0.1 set protocols ospf area 0.0.0.0 interface ge-0/0/0 set protocols ospf area 0.0.0.0 interface lo0.0
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要配置路由器 1 以便与路由器 2 建立 OSPF 连接:
配置以太网接口和环路接口。
[edit interfaces] user@router1# set ge-0/0/0 description "to R2 ge-0/0/0" user@router1# set ge-0/0/0 unit 0 family inet address 10.1.12.2/30 user@router1# set lo0 unit 0 family inet address 10.0.0.1/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
[edit protocols] user@router1# set ospf area 0.0.0.0 interface ge-0/0/0.0 user@router1# set ospf area 0.0.0.0 interface lo0.0
配置路由器 ID。
[edit routing-options] user@router1# set router-id 10.0.0.1
提交配置。
[edit] user@router1# commit
结果
在配置模式下,输入 show interfaces、 show protocols ospf和 show routing-options 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置。
user@router1# show interfaces
interfaces {
ge-0/0/0 {
description "To R2 ge-0/0/0";
unit 0 {
family inet {
address 10.1.12.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.1/32;
}
}
}
}
user@router1# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
}
}
}
user@router1# show routing-options
routing-options {
router-id 10.0.0.1;
}
配置路由器 2
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 2 层次结构级别的 CLI 中。
set interfaces ge-0/0/0 description "to R1 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.12.1/30 set interfaces ge-0/0/1 description "to R3 ge-0/0/1" set interfaces ge-0/0/1 unit 0 family inet address 10.1.15.1/30 set interfaces ms-1/2/0 services-options syslog host local services info set interfaces ms-1/2/0 unit 0 family inet set interfaces ms-1/2/0 unit 1 family inet set interfaces ms-1/2/0 unit 1 service-domain inside set interfaces ms-1/2/0 unit 2 family inet set interfaces ms-1/2/0 unit 2 service-domain outside set interfaces lo0 unit 0 family inet address 10.0.0.2/32 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 set protocols ospf area 0.0.0.0 interface ms-1/2/0.1 set routing-options router-id 10.0.0.2 set services ipsec-vpn rule rule-ike term term-ike then remote-gateway 10.1.15.2 set services ipsec-vpn rule rule-ike term term-ike then dynamic ike-policy ike-digital-certificates set services ipsec-vpn rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy set services ipsec-vpn rule match-direction input set services ipsec-vpn ike proposal ike-demo-proposal authentication-method rsa-signatures set services ipsec-vpn ike policy ike-digital-certificates proposals ike-demo-proposal set services ipsec-vpn ike policy ike-digital-certificates local-id fqdn router2.example.com set services ipsec-vpn ike policy ike-digital-certificates local-certificate local-entrust2 set services ipsec-vpn ike policy ike-digital-certificates remote-id fqdn router3.example.com set services ipsec-vpn ipsec proposal ipsec-demo-proposal protocol esp set services ipsec-vpn ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec proposals ipsec-demo-proposal set services ipsec-vpn establish-tunnels immediately set services service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 set services service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 set services service-set demo-service-set ipsec-vpn-options trusted-ca entrust set services service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.1 set services service-set demo-service-set ipsec-vpn-rules rule-ike
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要在路由器 2 上配置 OSPF 连接和 IPsec 隧道参数:
配置接口属性。在此步骤中,您将配置两个以太网接口(ge-1/0/0 和 ge-1/0/1)、环路接口和一个多服务接口 (ms-1/2/0)。
[edit interfaces] user@router2# set ge-0/0/0 description "to R1 ge-0/0/0" user@router2# set ge-0/0/0 unit 0 family inet address 10.1.12.1/30 user@router2# set ge-0/0/1 description "to R3 ge-0/0/1" user@router2# set ge-0/0/1 unit 0 family inet address 10.1.15.1/30 user@router2# set ms-1/2/0 services-options syslog host local services info user@router2# set ms-1/2/0 unit 0 family inet user@router2# set ms-1/2/0 unit 1 family inet user@router2# set ms-1/2/0 unit 1 service-domain inside user@router2# set ms-1/2/0 unit 2 family inet user@router2# set ms-1/2/0 unit 2 service-domain outside user@router2# set lo0 unit 0 family inet address 10.0.0.2/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
[edit protocols] user@router2# set ospf area 0.0.0.0 interface ge-0/0/0.0 user@router2# set ospf area 0.0.0.0 interface lo0.0 user@router2# set ospf area 0.0.0.0 interface ms-1/2/0.1
配置路由器 ID。
[edit routing-options] user@router2# set router-ID 10.0.0.2
配置 IKE 提议和策略。要为数字证书启用 IKE 提议,请在层次结构级别包含
[edit services ipsec-vpn ike proposal proposal-name authentication-method]该rsa-signatures语句。要在 IKE 策略中引用本地证书,请在层次结构级别包含[edit services ipsec-vpn ike policy policy-name]该local-certificate语句。要在服务集中标识证书颁发机构或注册机关,请在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该trusted-ca语句。注意:有关创建和安装数字证书的信息,请参阅注册 证书。
[edit services ipsec-vpn] user@router2# set ike proposal ike-demo-proposal authentication-method rsa-signatures user@router2# set ike policy ike-digital-certificates proposals ike-demo-proposal user@router2# set ike policy ike-digital-certificates local-id fqdn router2.example.com user@router2# set ike policy ike-digital-certificates local-certificate local-entrust2 user@router2# set ike policy ike-digital-certificates remote-id fqdn router3.example.com
配置 IPsec 提议和策略。另外,将旋钮
immediately设置为established-tunnels。[edit services ipsec-vpn] user@router2# set ipsec proposal ipsec-demo-proposal protocol esp user@router2# set ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 user@router2# set ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc user@router2# set ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 user@router2# set ipsec proposals ipsec-demo-proposal user@router2# set establish-tunnels immediately
配置 IPsec 规则。
[edit services ipsec-vpn] user@router2# set rule rule-ike term term-ike then remote-gateway 10.1.15.2 user@router2# set rule rule-ike term term-ike then dynamic ike-policy ike-digital-certificates user@router2# set rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy user@router2# set rule match-direction input
配置下一跃点样式的服务集,指定本地网关地址,并将 IPsec VPN 规则与服务集相关联。
[edit services] user@router2# set service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 user@router2# set service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 user@router2# set service-set demo-service-set ipsec-vpn-options trusted-ca entrust user@router2# set service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.1 user@router2# set service-set demo-service-set ipsec-vpn-rules rule-ike
提交配置。
[edit] user@router2# commit
结果
在配置模式下,输入 show interfaces、 show protocols ospf、 show routing-options和 show services 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router2# show interfaces
interfaces {
ge-0/0/0 {
description "To R1 ge-0/0/0";
unit 0 {
family inet {
address 10.1.12.1/30;
}
}
}
ge-0/0/1 {
description "To R3 ge-0/0/1";
unit 0 {
family inet {
address 10.1.15.1/30;
}
}
}
ms-1/2/0 {
services-options {
syslog {
host local {
services info;
}
}
}
unit 0 {
family inet;
}
unit 1 {
family inet;
service-domain inside;
}
unit 2 {
family inet;
service-domain outside;
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.2/32;
}
}
}
}
user@router2# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
interface ms-1/2/0.1;
}
}
}
user@router2# show routing-options
routing-options {
router-id 10.0.0.2;
}
user@router2# show services
services {
ipsec-vpn {
rule rule-ike {
term term-ike {
then {
remote-gateway 10.1.15.2;
dynamic {
ike-policy ike-digital-certificates;
ipsec-policy ipsec-demo-policy
}
}
}
match-direction input;
}
ike {
proposal ike-demo-proposal {
authentication-method rsa-signatures;
}
policy ike-digital-certificates {
proposals ike-demo-proposal;
local-id fqdn router2.example.com;
local-certificate local-entrust2;
remote-id fqdn router3.example.com;
}
}
ipsec {
proposal ipsec-demo-proposal {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy demo-policy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec-demo-proposal;
}
establish-tunnels immediately;
}
service-set service-set-dynamic-demo-service-set {
next-hop-service {
inside-service-interface ms-1/2/0.1;
outside-service-interface ms-1/2/0.2;
}
ipsec-vpn-options {
trusted-ca entrust;
local-gateway 10.1.15.1;
}
ipsec-vpn-rules rule-ike;
}
}
}
配置路由器 3
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 3 的 [edit] 层级的 CLI 中。
set interfaces ge-0/0/0 description "to R4 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.56.1/30 set interfaces ge-0/0/1 description "to R2 ge-0/0/1" set interfaces ge-0/0/1 unit 0 family inet address 10.1.15.2/30 set interfaces ms-1/2/0 services-options syslog host local services info set interfaces ms-1/2/0 unit 0 family inet set interfaces ms-1/2/0 unit 1 family inet set interfaces ms-1/2/0 unit 1 service-domain inside set interfaces ms-1/2/0 unit 2 family inet set interfaces ms-1/2/0 unit 2 service-domain outside set interfaces lo0 unit 0 family inet address 10.0.0.3/32 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 set protocols ospf area 0.0.0.0 interface ms-1/2/0.1 set routing-options router-id 10.0.0.3 set services ipsec-vpn rule rule-ike term term-ike then remote-gateway 10.1.15.1 set services ipsec-vpn rule rule-ike term term-ike then dynamic ike-policy ike-digital-certificates set services ipsec-vpn rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy set services ipsec-vpn rule match-direction input set services ipsec-vpn ike proposal ike-demo-proposal authentication-method rsa-signatures set services ipsec-vpn ike policy ike-digital-certificates proposals ike-demo-proposal set services ipsec-vpn ike policy ike-digital-certificates local-id fqdn router3.example.com set services ipsec-vpn ike policy ike-digital-certificates local-certificate local-entrust3 set services ipsec-vpn ike policy ike-digital-certificates remote-id fqdn router2.example.com set services ipsec-vpn ipsec proposal ipsec-demo-proposal protocol esp set services ipsec-vpn ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec proposals ipsec-demo-proposal set services ipsec-vpn establish-tunnels immediately set services service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 set services service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 set services service-set demo-service-set ipsec-vpn-options trusted-ca entrust set services service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.2 set services service-set demo-service-set ipsec-vpn-rules rule-ike
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
如果 IPsec 对等方没有包含所有必要组件的对称配置,则无法建立对等关系。您需要申请 证书颁发机构证书,创建本地证书,将这些数字证书加载到路由器中,并在 IPsec 配置中引用这些证书。有关数字认证的信息,请参阅注册 证书。
要在路由器 3 上配置 OSPF 连接和 IPsec 隧道参数:
配置接口属性。在此步骤中,您将配置两个以太网接口(ge-1/0/0 和 ge-1/0/1)、环路接口和一个多服务接口 (ms-1/2/0)。
[edit interfaces] user@router3# set ge-0/0/0 description "to R4 ge-0/0/0" user@router3# set ge-0/0/0 unit 0 family inet address 10.1.56.1/30 user@router3# set ge-0/0/1 description "to R2 ge-0/0/1" user@router3# set ge-0/0/1 unit 0 family inet address 10.1.15.2/30 user@router3# set ms-1/2/0 services-options syslog host local services info user@router3# set ms-1/2/0 unit 0 family inet user@router3# set ms-1/2/0 unit 1 family inet user@router3# set ms-1/2/0 unit 1 service-domain inside user@router3# set ms-1/2/0 unit 2 family inet user@router3# set ms-1/2/0 unit 2 service-domain outside user@router3# set lo0 unit 0 family inet address 10.0.0.3/32
指定 OSPF 区域,将接口与 OSPF 区域相关联。
[edit protocols] user@router3# set ospf area 0.0.0.0 interface ge-0/0/0.0 user@router3# set ospf area 0.0.0.0 interface lo0.0 user@router3# set ospf area 0.0.0.0 interface ms-1/2/0.1
配置路由器 ID。
[edit routing-options] user@router3# set router-id 10.0.0.3
配置 IKE 提议和策略。要为数字证书启用 IKE 提议,请在层次结构级别包含
[edit services ipsec-vpn ike proposal proposal-name authentication-method]该rsa-signatures语句。要在 IKE 策略中引用本地证书,请在层次结构级别包含[edit services ipsec-vpn ike policy policy-name]该local-certificate语句。要在服务集中标识证书颁发机构或注册机关,请在层次结构级别包含[edit services service-set service-set-name ipsec-vpn-options]该trusted-ca语句。注意:有关创建和安装数字证书的信息,请参阅注册 证书。
[edit services ipsec-vpn] user@router3# set ike proposal ike-demo-proposal authentication-method rsa-signatures user@router3# set ike policy ike-digital-certificates proposals ike-demo-proposal user@router3# set ike policy ike-digital-certificates local-id fqdn router2.example.com user@router3# set ike policy ike-digital-certificates local-certificate local-entrust2 user@router3# set ike policy ike-digital-certificates remote-id fqdn router3.example.com
配置 IPsec 提议。另外,将旋钮
immediately设置为established-tunnels。[edit services ipsec-vpn] user@router3# set ipsec proposal ipsec-demo-proposal protocol esp user@router3# set ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 user@router3# set ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc user@router3# set ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 user@router3# set ipsec proposals ipsec-demo-proposal user@router3# set establish-tunnels immediately
配置 IPsec 规则。
[edit services ipsec-vpn] user@router3# set rule rule-ike term term-ike then remote-gateway 10.1.15.2 user@router3# set rule rule-ike term term-ike then dynamic ike-policy ike-digital-certificates user@router3# set rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy user@router3# set rule match-direction input
配置下一跃点样式的服务集,指定本地网关地址,并将 IPsec VPN 规则与服务集相关联。
[edit services] user@router3# set service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 user@router3# set service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 user@router3# set service-set demo-service-set ipsec-vpn-options trusted-ca entrust user@router3# set service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.2 user@router3# set service-set demo-service-set ipsec-vpn-rules rule-ike
提交配置。
[edit] user@router3# commit
结果
在配置模式下,输入 show interfaces、 show protocols ospf、 show routing-options和 show services 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router3# show interfaces
interfaces {
ge-0/0/0 {
description "To R4 ge-0/0/0";
unit 0 {
family inet {
address 10.1.56.1/30;
}
}
}
ge-0/0/1 {
description "To R2 ge-0/0/1";
unit 0 {
family inet {
address 10.1.15.2/30;
}
}
}
ms-1/2/0 {
services-options {
syslog {
host local {
services info;
}
}
}
unit 0 {
family inet {
}
unit 1 {
family inet;
service-domain inside;
}
unit 2 {
family inet;
service-domain outside;
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.3/32;
}
}
}
}
}
user@router3# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
interface ms-1/2/0.1;
}
}
}
user@router3# show routing-options
routing-options {
router-id 10.0.0.3;
}
user@router3# show services
services {
ipsec-vpn {
rule rule-ike {
term term-ike {
then {
remote-gateway 10.1.15.1;
dynamic {
ike-policy ike-digital-certificates;
ipsec-policy ipsec-demo-policy
}
}
}
match-direction input;
}
ike {
proposal ike-demo-proposal {
authentication-method rsa-signatures;
}
policy ike-digital-certificates {
proposals ike-demo-proposal;
local-id fqdn router3.example.com;
local-certificate local-entrust3;
remote-id fqdn router2.example.com;
}
}
ipsec {
proposal ipsec-demo-proposal {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy demo-policy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec-demo-proposal;
}
establish-tunnels immediately;
}
service-set service-set-dynamic-demo-service-set {
next-hop-service {
inside-service-interface ms-1/2/0.1;
outside-service-interface ms-1/2/0.2;
}
ipsec-vpn-options {
trusted-ca entrust;
local-gateway 10.1.15.2;
}
ipsec-vpn-rules rule-ike;
}
}
}
配置路由器 4
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 4 层次结构级别的 CLI 中。
set interfaces ge-0/0/0 description "to R3 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.56.2/30 set interfaces lo0 unit 0 family inet address 10.0.0.4/32 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 set routing-options router-id 10.0.0.4
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要设置与路由器 4 的 OSPF 连接,请执行以下作
配置接口。在此步骤中,您将配置以太网接口 (ge-1/0/1) 和环路接口。
[edit interfaces] user@router4# set ge-0/0/0 description "to R3 ge-0/0/0" user@router4# set ge-0/0/0 unit 0 family inet address 10.1.56.2/30 user@router4# set lo0 unit 0 family inet address 10.0.0.4/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
[edit protocols] user@router4# set ospf area 0.0.0.0 interface ge-0/0/0 user@router4# set ospf area 0.0.0.0 interface lo0.0
配置路由器 ID。
[edit routing-options] user@router4# set router-id 10.0.0.4
结果
在配置模式下,输入 show interfaces、 show protocols ospf和 show routing-options 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router4# show interfaces
interfaces {
ge-0/0/0 {
description "To R3 ge-0/0/0";
unit 0 {
family inet {
address 10.1.56.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.4/32;
}
}
}
}
user@router4# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
}
}
}
user@router4# show routing-options
routing-options {
router-id 10.0.0.4;
}
验证
验证您在路由器 1 上的工作
目的
在路由器 1 上,验证对路由器 4 上的 so-0/0/0 接口的 ping 命令,以便通过 IPsec 隧道发送流量。
行动
在作模式下,输入 ping 10.1.56.2。
user@router1>ping 10.1.56.2 PING 10.1.56.2 (10.1.56.2): 56 data bytes 64 bytes from 10.1.56.2: icmp_seq=0 ttl=254 time=1.351 ms 64 bytes from 10.1.56.2: icmp_seq=1 ttl=254 time=1.187 ms 64 bytes from 10.1.56.2: icmp_seq=2 ttl=254 time=1.172 ms 64 bytes from 10.1.56.2: icmp_seq=3 ttl=254 time=1.154 ms 64 bytes from 10.1.56.2: icmp_seq=4 ttl=254 time=1.156 ms ^C --- 10.1.56.2 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.154/1.204/1.351/0.074 ms
如果对路由器 4 的环路地址使用 Ping 命令,则作会成功,因为该地址是路由器 4 上配置的 OSPF 网络的一部分。
user@router1>ping 10.0.0.4 PING 10.0.0.4 (10.0.0.4): 56 data bytes 64 bytes from 10.0.0.4: icmp_seq=0 ttl=62 time=1.318 ms 64 bytes from 10.0.0.4: icmp_seq=1 ttl=62 time=1.084 ms 64 bytes from 10.0.0.4: icmp_seq=2 ttl=62 time=3.260 ms ^C --- 10.0.0.4 ping statistics --- 3 packets transmitted, 3 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.084/1.887/3.260/0.975 ms
验证您在路由器 2 上的工作
目的
要验证匹配的流量是否正在转移到双向 IPsec 隧道,请查看 IPsec 统计信息:
行动
在作模式下,输入 show services ipsec-vpn ipsec statistics。
user@router2>show services ipsec-vpn ipsec statistics PIC: sp-1/2/0, Service set: service-set-dynamic-demo-service-set ESP Statistics: Encrypted bytes: 162056 Decrypted bytes: 161896 Encrypted packets: 2215 Decrypted packets: 2216 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0
要验证 IKE SA 协商是否成功,请发出以下 show services ipsec-vpn ike security-associations 命令:
在作模式下,进入 show services ipsec-vpn ike security-associations
user@router2> show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 10.1.15.2 Matured d82610c59114fd37 ec4391f76783ef28 Main
要验证 IPsec 安全关联是否处于活动状态,请发出命令 show services ipsec-vpn ipsec security-associations detail 。请注意,SA 包含服务 PIC 固有的默认设置,例如,用于协议的 ESP 和用于身份验证算法的 HMAC-SHA1-96。
在作模式下,进入 show services ipsec-vpn ipsec security-associations detail
user@router2> show services ipsec-vpn ipsec security-associations detail Service set: service-set-dynamic-demo-service-set Rule: rule-ike, Term: term-ike, Tunnel index: 1 Local gateway: 10.1.15.1, Remote gateway: 10.1.15.2 IPsec inside interface: sp-1/2/0.1 Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Remote identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Direction: inbound, SPI: 857451461, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 9052 seconds Hard lifetime: Expires in 9187 seconds Anti-replay service: Enabled, Replay window size: 64 Direction: outbound, SPI: 1272330309, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 9052 seconds Hard lifetime: Expires in 9187 seconds Anti-replay service: Enabled, Replay window size: 64
要显示用于建立 IPsec 隧道的数字证书,请发出 show services ipsec-vpn certificates 命令:
在作模式下,进入 show services ipsec-vpn certificates
user@router2> show services ipsec-vpn certificates Service set: service-set-dynamic-demo-service-set, Total entries: 3 Certificate cache entry: 3 Flags: Non-root Trusted Issued to: router3.example.com, Issued by: juniper Alternate subject: router3.example.com Validity: Not before: 2005 Nov 21st, 23:33:58 GMT Not after: 2008 Nov 22nd, 00:03:58 GMT Certificate cache entry: 2 Flags: Non-root Trusted Issued to: router2.example.com, Issued by: juniper Alternate subject: router2.example.com Validity: Not before: 2005 Nov 21st, 23:28:22 GMT Not after: 2008 Nov 21st, 23:58:22 GMT Certificate cache entry: 1 Flags: Root Trusted Issued to: juniper, Issued by: juniper Validity: Not before: 2005 Oct 18th, 23:54:22 GMT Not after: 2025 Oct 19th, 00:24:22 GMT
要显示证书颁发机构证书,请发出 show security pki ca-certificate detail 命令。请注意,有三个单独的证书:一个用于证书签名,一个用于密钥加密,一个用于 证书颁发机构的数字签名。
在作模式下,进入 show security pki ca-certificate detail
user@router2> show security pki ca-certificate detail Certificate identifier: entrust Certificate version: 3 Serial number: 4355 9235 Issuer: Organization: juniper, Country: us Subject: Organization: juniper, Country: us Validity: Not before: 2005 Oct 18th, 23:54:22 GMT Not after: 2025 Oct 19th, 00:24:22 GMT Public key algorithm: rsaEncryption(1024 bits) cb:9e:2d:c0:70:f8:ea:3c:f2:b5:f0:02:48:87:dc:68:99:a3:57:4f 0e:b9:98:0b:95:47:0d:1f:97:7c:53:17:dd:1a:f8:da:e5:08:d1:1c 78:68:1f:2f:72:9f:a2:cf:81:e3:ce:c5:56:89:ce:f0:97:93:fa:36 19:3e:18:7d:8c:9d:21:fe:1f:c3:87:8d:b3:5d:f3:03:66:9d:16:a7 bf:18:3f:f0:7a:80:f0:62:50:43:83:4f:0e:d7:c6:42:48:c0:8a:b2 c7:46:30:38:df:9b:dc:bc:b5:08:7a:f3:cd:64:db:2b:71:67:fe:d8 04:47:08:07:de:17:23:13 Signature algorithm: sha1WithRSAEncryption Fingerprint: 00:8e:6f:58:dd:68:bf:25:0a:e3:f9:17:70:d6:61:f3:53:a7:79:10 (sha1) 71:6f:6a:76:17:9b:d6:2a:e7:5a:72:97:82:6d:26:86 (md5) Distribution CRL: C=us, O=juniper, CN=CRL1 http://CA-1/CRL/juniper_us_crlfile.crl Use for key: CRL signing, Certificate signing Certificate identifier: entrust Certificate version: 3 Serial number: 4355 925c Issuer: Organization: juniper, Country: us Subject: Organization: juniper, Country: us, Common name: First Officer Validity: Not before: 2005 Oct 18th, 23:55:59 GMT Not after: 2008 Oct 19th, 00:25:59 GMT Public key algorithm: rsaEncryption(1024 bits) c0:a4:21:32:95:0a:cd:ec:12:03:d1:a2:89:71:8e:ce:4e:a6:f9:2f 1a:9a:13:8c:f6:a0:3d:c9:bd:9d:c2:a0:41:77:99:1b:1e:ed:5b:80 34:46:f8:5b:28:34:38:2e:91:7d:4e:ad:14:86:78:67:e7:02:1d:2e 19:11:b7:fa:0d:ba:64:20:e1:28:4e:3e:bb:6e:64:dc:cd:b1:b4:7a ca:8f:47:dd:40:69:c2:35:95:ce:b8:85:56:d7:0f:2d:04:4d:5d:d8 42:e1:4f:6b:bf:38:c0:45:1e:9e:f0:b4:7f:74:6f:e9:70:fd:4a:78 da:eb:10:27:bd:46:34:33 Signature algorithm: sha1WithRSAEncryption Fingerprint: bc:78:87:9b:a7:91:13:20:71:db:ac:b5:56:71:42:ad:1a:b6:46:17 (sha1) 23:79:40:c9:6d:a6:f0:ca:e0:13:30:d4:29:6f:86:79 (md5) Distribution CRL: C=us, O=juniper, CN=CRL1 http://CA-1/CRL/juniper_us_crlfile.crl Use for key: Key encipherment Certificate identifier: entrust Certificate version: 3 Serial number: 4355 925b Issuer: Organization: juniper, Country: us Subject: Organization: juniper, Country: us, Common name: First Officer Validity: Not before: 2005 Oct 18th, 23:55:59 GMT Not after: 2008 Oct 19th, 00:25:59 GMT Public key algorithm: rsaEncryption(1024 bits) ea:75:c4:f3:58:08:ea:65:5c:7e:b3:de:63:0a:cf:cf:ec:9a:82:e2 d7:e8:b9:2f:bd:4b:cd:86:2f:f1:dd:d8:a2:95:af:ab:51:a5:49:4e 00:10:c6:25:ff:b5:49:6a:99:64:74:69:e5:8c:23:5b:b4:70:62:8e e4:f9:a2:28:d4:54:e2:0b:1f:50:a2:92:cf:6c:8f:ae:10:d4:69:3c 90:e2:1f:04:ea:ac:05:9b:3a:93:74:d0:59:24:e9:d2:9d:c2:ef:22 b9:32:c7:2c:29:4f:91:cb:5a:26:fe:1d:c0:36:dc:f4:9c:8b:f5:26 af:44:bf:53:aa:d4:5f:67 Signature algorithm: sha1WithRSAEncryption Fingerprint: 46:71:15:34:f0:a6:41:76:65:81:33:4f:68:47:c4:df:78:b8:e3:3f (sha1) ee:cc:c7:f4:5d:ac:65:33:0a:55:db:59:72:2c:dd:16 (md5) Distribution CRL: C=us, O=juniper, CN=CRL1 http://CA-1/CRL/juniper_us_crlfile.crl Use for key: Digital signature
要显示本地证书请求,请发出 show security pki certificate-request 命令:
在作模式下,进入 show security pki certificate-request
user@router2> show security pki certificate-request Certificate identifier: local-entrust2 Issued to: router2.example.com Public key algorithm: rsaEncryption(1024 bits) Public key verification status: Passed
要显示本地证书,请发出 show security pki local-certificate 命令:
在作模式下,进入 show security pki local-certificate
user@router2> show security pki local-certificate Certificate identifier: local-entrust2 Issued to: router2.example.com, Issued by: juniper Validity: Not before: 2005 Nov 21st, 23:28:22 GMT Not after: 2008 Nov 21st, 23:58:22 GMT Public key algorithm: rsaEncryption(1024 bits) Public key verification status: Passed
验证您在路由器 3 上的工作
目的
要验证匹配的流量是否正在转移到双向 IPsec 隧道,请查看 IPsec 统计信息:
行动
在作模式下,输入 show services ipsec-vpn ipsec statistics。
user@router3>show services ipsec-vpn ipsec statistics PIC: sp-1/2/0, Service set: service-set-dynamic-demo-service-set ESP Statistics: Encrypted bytes: 161896 Decrypted bytes: 162056 Encrypted packets: 2216 Decrypted packets: 2215 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0
要验证 IKE SA 协商是否成功,请发出 show services ipsec-vpn ike security-associations 命令。要成功,路由器 3 上的 SA 必须包含在您在路由器 2 上指定的相同设置。
在作模式下,输入 show services ipsec-vpn ike security-associations。
user@router3>show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 10.1.15.1 Matured d82610c59114fd37 ec4391f76783ef28 Main
要验证 IPsec SA 是否处于活动状态,请发出 show services ipsec-vpn ipsec security-associations detail 命令。要成功,路由器 3 上的 SA 必须包含在您在路由器 2 上指定的相同设置。
在作模式下,输入 show services ipsec-vpn ipsec security-associations detail。
user@router3>show services ipsec-vpn ipsec security-associations detail Service set: service-set-dynamic-demo-service-set Rule: rule-ike, Term: term-ike, Tunnel index: 1 Local gateway: 10.1.15.2, Remote gateway: 10.1.15.1 IPsec inside interface: sp-1/2/0.1 Local identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Remote identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0) Direction: inbound, SPI: 1272330309, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 7219 seconds Hard lifetime: Expires in 7309 seconds Anti-replay service: Enabled, Replay window size: 64 Direction: outbound, SPI: 857451461, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 7219 seconds Hard lifetime: Expires in 7309 seconds Anti-replay service: Enabled, Replay window size: 64
要显示用于建立 IPsec 隧道的数字证书,请发出 show services ipsec-vpn certificates 命令:
在作模式下,输入 show services ipsec-vpn certificates。
user@router3>show services ipsec-vpn certificates Service set: service-set-dynamic-demo-service-set, Total entries: 3 Certificate cache entry: 3 Flags: Non-root Trusted Issued to: router3.example.com, Issued by: juniper Alternate subject: router3.example.com Validity: Not before: 2005 Nov 21st, 23:33:58 GMT Not after: 2008 Nov 22nd, 00:03:58 GMT Certificate cache entry: 2 Flags: Non-root Trusted Issued to: router2.example.com, Issued by: juniper Alternate subject: router2.example.com Validity: Not before: 2005 Nov 21st, 23:28:22 GMT Not after: 2008 Nov 21st, 23:58:22 GMT Certificate cache entry: 1 Flags: Root Trusted Issued to: juniper, Issued by: juniper Validity: Not before: 2005 Oct 18th, 23:54:22 GMT Not after: 2025 Oct 19th, 00:24:22 GMT
要显示证书颁发机构证书,请发出 show security pki ca-certificate detail 命令。请注意,有三个单独的证书:一个用于证书签名,一个用于密钥加密,一个用于 证书颁发机构的数字签名。
在作模式下,输入 show security pki ca-certificate detail。
user@router3>show security pki ca-certificate detail Certificate identifier: entrust Certificate version: 3 Serial number: 4355 9235 Issuer: Organization: juniper, Country: us Subject: Organization: juniper, Country: us Validity: Not before: 2005 Oct 18th, 23:54:22 GMT Not after: 2025 Oct 19th, 00:24:22 GMT Public key algorithm: rsaEncryption(1024 bits) cb:9e:2d:c0:70:f8:ea:3c:f2:b5:f0:02:48:87:dc:68:99:a3:57:4f 0e:b9:98:0b:95:47:0d:1f:97:7c:53:17:dd:1a:f8:da:e5:08:d1:1c 78:68:1f:2f:72:9f:a2:cf:81:e3:ce:c5:56:89:ce:f0:97:93:fa:36 19:3e:18:7d:8c:9d:21:fe:1f:c3:87:8d:b3:5d:f3:03:66:9d:16:a7 bf:18:3f:f0:7a:80:f0:62:50:43:83:4f:0e:d7:c6:42:48:c0:8a:b2 c7:46:30:38:df:9b:dc:bc:b5:08:7a:f3:cd:64:db:2b:71:67:fe:d8 04:47:08:07:de:17:23:13 Signature algorithm: sha1WithRSAEncryption Fingerprint: 00:8e:6f:58:dd:68:bf:25:0a:e3:f9:17:70:d6:61:f3:53:a7:79:10 (sha1) 71:6f:6a:76:17:9b:d6:2a:e7:5a:72:97:82:6d:26:86 (md5) Distribution CRL: C=us, O=juniper, CN=CRL1 http://CA-1/CRL/juniper_us_crlfile.crl Use for key: CRL signing, Certificate signing Certificate identifier: entrust Certificate version: 3 Serial number: 4355 925c Issuer: Organization: juniper, Country: us Subject: Organization: juniper, Country: us, Common name: First Officer Validity: Not before: 2005 Oct 18th, 23:55:59 GMT Not after: 2008 Oct 19th, 00:25:59 GMT Public key algorithm: rsaEncryption(1024 bits) c0:a4:21:32:95:0a:cd:ec:12:03:d1:a2:89:71:8e:ce:4e:a6:f9:2f 1a:9a:13:8c:f6:a0:3d:c9:bd:9d:c2:a0:41:77:99:1b:1e:ed:5b:80 34:46:f8:5b:28:34:38:2e:91:7d:4e:ad:14:86:78:67:e7:02:1d:2e 19:11:b7:fa:0d:ba:64:20:e1:28:4e:3e:bb:6e:64:dc:cd:b1:b4:7a ca:8f:47:dd:40:69:c2:35:95:ce:b8:85:56:d7:0f:2d:04:4d:5d:d8 42:e1:4f:6b:bf:38:c0:45:1e:9e:f0:b4:7f:74:6f:e9:70:fd:4a:78 da:eb:10:27:bd:46:34:33 Signature algorithm: sha1WithRSAEncryption Fingerprint: bc:78:87:9b:a7:91:13:20:71:db:ac:b5:56:71:42:ad:1a:b6:46:17 (sha1) 23:79:40:c9:6d:a6:f0:ca:e0:13:30:d4:29:6f:86:79 (md5) Distribution CRL: C=us, O=juniper, CN=CRL1 http://CA-1/CRL/juniper_us_crlfile.crl Use for key: Key encipherment Certificate identifier: entrust Certificate version: 3 Serial number: 4355 925b Issuer: Organization: juniper, Country: us Subject: Organization: juniper, Country: us, Common name: First Officer Validity: Not before: 2005 Oct 18th, 23:55:59 GMT Not after: 2008 Oct 19th, 00:25:59 GMT Public key algorithm: rsaEncryption(1024 bits) ea:75:c4:f3:58:08:ea:65:5c:7e:b3:de:63:0a:cf:cf:ec:9a:82:e2 d7:e8:b9:2f:bd:4b:cd:86:2f:f1:dd:d8:a2:95:af:ab:51:a5:49:4e 00:10:c6:25:ff:b5:49:6a:99:64:74:69:e5:8c:23:5b:b4:70:62:8e e4:f9:a2:28:d4:54:e2:0b:1f:50:a2:92:cf:6c:8f:ae:10:d4:69:3c 90:e2:1f:04:ea:ac:05:9b:3a:93:74:d0:59:24:e9:d2:9d:c2:ef:22 b9:32:c7:2c:29:4f:91:cb:5a:26:fe:1d:c0:36:dc:f4:9c:8b:f5:26 af:44:bf:53:aa:d4:5f:67 Signature algorithm: sha1WithRSAEncryption Fingerprint: 46:71:15:34:f0:a6:41:76:65:81:33:4f:68:47:c4:df:78:b8:e3:3f (sha1) ee:cc:c7:f4:5d:ac:65:33:0a:55:db:59:72:2c:dd:16 (md5) Distribution CRL: C=us, O=juniper, CN=CRL1 http://CA-1/CRL/juniper_us_crlfile.crl Use for key: Digital signature
要显示本地证书请求,请发出 show security pki certificate-request 命令:
在作模式下,输入 show security pki certificate-request。
user@router3>show security pki certificate-request Certificate identifier: local-entrust3 Issued to: router3.example.com Public key algorithm: rsaEncryption(1024 bits) Public key verification status: Passed
要显示本地证书,请发出 show security pki local-certificate 命令:
在作模式下,输入 show security pki local-certificate。
user@router3>show security pki local-certificate Certificate identifier: local-entrust3 Issued to: router3.example.com, Issued by: juniper Validity: Not before: 2005 Nov 21st, 23:33:58 GMT Not after: 2008 Nov 22nd, 00:03:58 GMT Public key algorithm: rsaEncryption(1024 bits) Public key verification status: Passed
验证您在路由器 4 上的工作
目的
在路由器 4 上,向路由器 1 上的 so-0/0/0 接口发出 ping 命令,以通过 IPsec 隧道发送流量。
行动
在作模式下,输入 ping 10.1.12.2。
user@router4>ping 10.1.12.2 PING 10.1.12.2 (10.1.12.2): 56 data bytes 64 bytes from 10.1.12.2: icmp_seq=0 ttl=254 time=1.350 ms 64 bytes from 10.1.12.2: icmp_seq=1 ttl=254 time=1.161 ms 64 bytes from 10.1.12.2: icmp_seq=2 ttl=254 time=1.124 ms 64 bytes from 10.1.12.2: icmp_seq=5 ttl=254 time=1.116 ms ^C --- 10.1.12.2 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.116/1.172/1.350/0.081 ms
确认流量是否通过 IPsec 隧道传输的最后一种方法是向路由器 1 上的 so-0/0/0 接口发出 traceroute 命令。请注意,路径中未引用路由器 2 和 3 之间的物理接口;流量通过路由器 3 上的自适应服务 IPsec 内部接口进入 IPsec 隧道,通过路由器 2 上的环路接口,最后在路由器 1 上的 so-0/0/0 接口结束。
在作模式下,输入 traceroute 10.1.12.2。
user@router4>traceroute 10.1.12.2 traceroute to 10.1.12.2 (10.1.12.2), 30 hops max, 40 byte packets 1 10.1.15.2 (10.1.15.2) 0.987 ms 0.630 ms 0.563 ms 2 10.0.0.2 (10.0.0.2) 1.194 ms 1.058 ms 1.033 ms 3 10.1.12.2 (10.1.12.2) 1.073 ms 0.949 ms 0.932 ms
配置 Junos VPN Site Secure 或 IPSec VPN
所有带有 MS-MIC、MS-MPC 或 MS-DPC 的 MX 系列路由器均支持 IPsec VPN。
在 M Series 和 T Series 路由器上,多服务 100 PIC、多服务 400 PIC 和多服务 500 PIC 支持 IPsec VPN。
从 Junos OS 13.2 及更高版本开始支持 MS-MIC 和 MS-MPC。MS-MIC 和 MS-MPC 支持 MS-DPC 和 MS-PIC 支持的所有功能,但用于动态或手册安全关联和无流 IPsec 服务的身份验证头协议 (AH)、封装安全有效负载协议 (ESP) 和捆绑包(AH 和 ESP 协议)协议除外。
从 Junos OS 17.4R1 版及更高版本开始,IKEv1 和 IKEv2 支持 NAT 遍历 (NAT-T)。默认情况下启用 NAT-T。您可以使用层次结构级别的[edit services ipsec-vpn]配置disable-natt为 IKE 和 ESP 数据包指定 UDP 封装和解封装。
也可以看看
示例:在 MS-MIC 和 MS-MPC 上配置 Junos VPN Site Secure
您可以按照相同的过程并使用此示例中给出的相同配置,在 MS-MPC 上配置 Junos VPN Site Secure(以前称为 IPsec 功能)。
此示例包含以下部分:
要求
此示例使用以下硬件和软件组件:
两台配备 MS-MIC 的 MX 系列路由器
Junos OS 13.2 或更高版本
概述
Junos OS 13.2 版将对 Junos VPN Site Secure(以前称为 IPsec 功能)的支持扩展到 MX 系列路由器上新推出的多服务 MIC 和 MPC(MS-MIC 和 MS-MPC)。Junos OS 扩展提供程序包已预安装并预配置在 MS-MIC 和 MS-MPC 上。
13.2 版中的 MS-MIC 和 MS-MPC 支持以下 Junos VPN Site Secure 功能:
动态端点 (DEP)
封装安全性有效负载 (ESP) 协议
失效对等方检测 (DPD) 触发消息
序列号展期通知
具有下一跳和接口样式服务集的静态 IPsec 隧道
但是,在 Junos OS 13.2 版中,MS-MIC 和 MS-MPC 上的 Junos VPN Site Secure 支持仅限于 IPv4 流量。MS-MIC 和 MS-MPC 不支持无源模块隧道。
图 2 显示了 IPsec VPN 隧道拓扑。
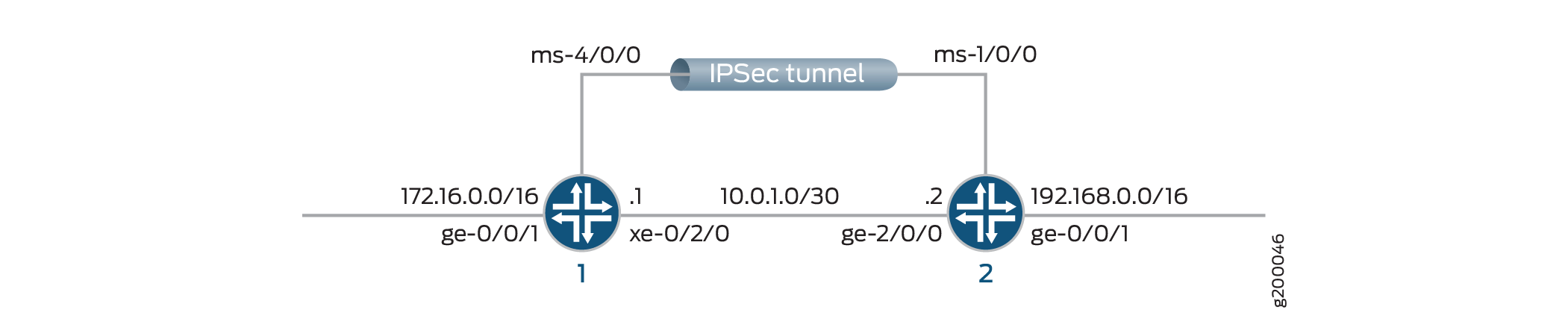
此示例显示了两台路由器(路由器 1 和路由器 2)的配置,这两台路由器之间配置了 IPsec VPN 隧道。
配置路由器时,请注意以下几点:
您在路由器 1 上的层次结构级别下
[edit services ipsec-vpn rule name term term from]配置source-address的 IP 地址必须与您在路由器 2 上的相同层级下配置的destination-addressIP 地址相同,反之亦然。您在层次结构级别下
[edit services ipsec-vpn rule name term term then]配置的 IP 地址remote-gateway应与您在路由器 2 层级下[edit services service-set name ipsec-vpn-options]配置的 IP 地址local-gateway匹配,反之亦然。
配置
本节包含:
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到 [edit] 层级的 CLI 中。
在路由器 1 上配置接口
set interfaces ms-4/0/0 unit 0 family inet set interfaces ms-4/0/0 unit 1 family inet set interfaces ms-4/0/0 unit 1 family inet6 set interfaces ms-4/0/0 unit 1 service-domain inside set interfaces ms-4/0/0 unit 2 family inet set interfaces ms-4/0/0 unit 2 family inet6 set interfaces ms-4/0/0 unit 2 service-domain outside set interfaces xe-0/2/0 unit 0 family inet address 10.0.1.1/30
在路由器 1 上配置 IPsec VPN 服务
set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 from source-address 172.16.0.0/16 set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 from destination-address 192.168.0.0/16 set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then remote-gateway 10.0.1.2 set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then dynamic ike-policy ike_policy_ms_4_0_0 set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then dynamic ipsec-policy ipsec_policy_ms_4_0_0 set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then anti-replay-window-size 4096 set services ipsec-vpn rule vpn_rule_ms_4_0_01 match-direction input set services ipsec-vpn ipsec proposal ipsec_proposal_ms_4_0_0 protocol esp set services ipsec-vpn ipsec proposal ipsec_proposal_ms_4_0_0 authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec_proposal_ms_4_0_0 encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy ipsec_policy_ms_4_0_0 perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec policy ipsec_policy_ms_4_0_0 proposals ipsec_proposal_ms_4_0_0 set services ipsec-vpn ike proposal ike_proposal_ms_4_0_0 authentication-method pre-shared-keys set services ipsec-vpn ike proposal ike_proposal_ms_4_0_0 dh-group group2 set services ipsec-vpn ike policy ike_policy_ms_4_0_0 version 2 set services ipsec-vpn ike policy ike_policy_ms_4_0_0 proposals ike_proposal_ms_4_0_0 set services ipsec-vpn ike policy ike_policy_ms_4_0_0 pre-shared-key ascii-text secret-data
在路由器 1 上配置服务集
set services service-set ipsec_ss_ms_4_0_01 next-hop-service inside-service-interface ms-4/0/0.1 set services service-set ipsec_ss_ms_4_0_01 next-hop-service outside-service-interface ms-4/0/0.2 set services service-set ipsec_ss_ms_4_0_01 ipsec-vpn-options local-gateway 10.0.1.1 set services service-set ipsec_ss_ms_4_0_01 ipsec-vpn-rules vpn_rule_ms_4_0_01
在路由器 1 上配置路由选项
set routing-options static route 192.168.0.0/16 next-hop ms-4/0/0.1
在路由器 2 上配置接口
set interfaces ms-1/0/0 unit 0 family inet set interfaces ms-1/0/0 unit 1 family inet set interfaces ms-1/0/0 unit 1 family inet6 set interfaces ms-1/0/0 unit 1 service-domain inside set interfaces ms-1/0/0 unit 2 family inet set interfaces ms-1/0/0 unit 2 family inet6 set interfaces ms-1/0/0 unit 2 service-domain outside set interfaces ge-2/0/0 unit 0 family inet address 10.0.1.2/30
在路由器 2 上配置 IPsec VPN 服务
set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 from source-address 192.168.0.0/16 set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 from destination-address 172.16.0.0/16 set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then remote-gateway 10.0.1.1 set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then dynamic ike-policy ike_policy_ms_5_2_0 set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then dynamic ipsec-policy ipsec_policy_ms_5_2_0 set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then anti-replay-window-size 4096 set services ipsec-vpn rule vpn_rule_ms_5_2_01 match-direction input set services ipsec-vpn ipsec proposal ipsec_proposal_ms_5_2_0 protocol esp set services ipsec-vpn ipsec proposal ipsec_proposal_ms_5_2_0 authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec_proposal_ms_5_2_0 encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy ipsec_policy_ms_5_2_0 perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec policy ipsec_policy_ms_5_2_0 proposals ipsec_proposal_ms_5_2_0 set services ipsec-vpn ike proposal ike_proposal_ms_5_2_0 authentication-method pre-shared-keys set services ipsec-vpn ike proposal ike_proposal_ms_5_2_0 dh-group group2 set services ipsec-vpn ike policy ike_policy_ms_5_2_0 version 2 set services ipsec-vpn ike policy ike_policy_ms_5_2_0 proposals ike_proposal_ms_5_2_0 set services ipsec-vpn ike policy ike_policy_ms_5_2_0 pre-shared-key ascii-text secret-data set services ipsec-vpn establish-tunnels immediately
在路由器 2 上配置服务集
set services service-set ipsec_ss_ms_5_2_01 next-hop-service inside-service-interface ms-1/0/0.1 set services service-set ipsec_ss_ms_5_2_01 next-hop-service outside-service-interface ms-1/0/0.2 set services service-set ipsec_ss_ms_5_2_01 ipsec-vpn-options local-gateway 10.0.1.2 set services service-set ipsec_ss_ms_5_2_01 ipsec-vpn-rules vpn_rule_ms_5_2_01
在路由器 2 上配置路由选项
set routing-options static route 172.16.0.0/16 next-hop ms-1/0/0.1
配置路由器 1
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
从 13.2 版开始,Junos OS 扩展提供程序包预安装在多服务 MIC 和 MPC(MS-MIC 和 MS-MPC)上。 adaptive-services 层次结构级别的 [edit chassis fpc number pic number] 配置在这些卡上预先配置。
配置接口属性,例如家族、服务域和单元。
user@router1# set interfaces ms-4/0/0 unit 0 family inet user@router1# set interfaces ms-4/0/0 unit 1 family inet user@router1# set interfaces ms-4/0/0 unit 1 family inet6 user@router1# set interfaces ms-4/0/0 unit 1 service-domain inside user@router1# set interfaces ms-4/0/0 unit 2 family inet user@router1# set interfaces ms-4/0/0 unit 2 family inet6 user@router1# set interfaces ms-4/0/0 unit 2 service-domain outside user@router1# set interfaces xe-0/2/0 unit 0 family inet address 10.0.1.1/30
配置 IPsec 属性,例如地址、远程网关、策略、匹配方向、协议、重放窗口大小、算法详细信息、保密密钥、提议、身份验证方法、组和版本。
user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 from source-address 172.16.0.0/16 user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 from destination-address 192.168.0.0/16 user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then remote-gateway 10.0.1.2 user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then dynamic ike-policy ike_policy_ms_4_0_0 user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then dynamic ipsec-policy ipsec_policy_ms_4_0_0 user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 term term11 then anti-replay-window-size 4096 user@router1# set services ipsec-vpn rule vpn_rule_ms_4_0_01 match-direction input user@router1# set services ipsec-vpn ipsec proposal ipsec_proposal_ms_4_0_0 protocol esp user@router1# set services ipsec-vpn ipsec proposal ipsec_proposal_ms_4_0_0 authentication-algorithm hmac-sha1-96 user@router1# set services ipsec-vpn ipsec proposal ipsec_proposal_ms_4_0_0 encryption-algorithm 3des-cbc user@router1# set services ipsec-vpn ipsec policy ipsec_policy_ms_4_0_0 perfect-forward-secrecy keys group2 user@router1# set services ipsec-vpn ipsec policy ipsec_policy_ms_4_0_0 proposals ipsec_proposal_ms_4_0_0 user@router1# set services ipsec-vpn ike proposal ike_proposal_ms_4_0_0 authentication-method pre-shared-keys user@router1# set services ipsec-vpn ike proposal ike_proposal_ms_4_0_0 dh-group group2 user@router1# set services ipsec-vpn ike policy ike_policy_ms_4_0_0 version 2 user@router1# set services ipsec-vpn ike policy ike_policy_ms_4_0_0 proposals ike_proposal_ms_4_0_0 user@router1# set services ipsec-vpn ike policy ike_policy_ms_4_0_0 pre-shared-key ascii-text secret-key
配置服务集、ipsec-vpn 选项和规则。
user@router1# set services service-set ipsec_ss_ms_4_0_01 next-hop-service inside-service-interface ms-4/0/0.1 user@router1# set services service-set ipsec_ss_ms_4_0_01 next-hop-service outside-service-interface ms-4/0/0.2 user@router1# set services service-set ipsec_ss_ms_4_0_01 ipsec-vpn-options local-gateway 10.0.1.1 user@router1# set services service-set ipsec_ss_ms_4_0_01 ipsec-vpn-rules vpn_rule_ms_4_0_01
配置路由选项、静态路由和下一跳。
user@router1# set routing-options static route 192.168.0.0/16 next-hop ms-4/0/0.1
结果
在路由器 1 的配置模式下,输入 show interfaces、 show services ipsec-vpn和 show services service-set 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置。
user@router1# show interfaces
ms-4/0/0{
unit 0 {
family inet;
}
unit 1 {
family inet;
family inet6;
service-domain inside;
}
unit 2 {
family inet;
family inet6;
service-domain outside;
}
}
xe-0/2/0 {
unit 0 {
family inet {
address 10.0.1.1/30;
}
}
}
user@router1# show services ipsec-vpn
rule vpn_rule_ms_4_0_01 {
term term11 {
from {
source-address {
172.16.0.0/16;
}
destination-address {
192.168.0.0/16;
}
}
then {
remote-gateway 10.0.1.2;
dynamic {
ike-policy ike_policy_ms_4_0_0;
ipsec-policy ipsec_policy_ms_4_0_0;
}
anti-replay-window-size 4096;
}
}
match-direction input;
}
ipsec {
proposal ipsec_proposal_ms_4_0_0 {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy ipsec_policy_ms_4_0_0 {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec_proposal_ms_4_0_0;
}
}
ike {
proposal ike_proposal_ms_4_0_0 {
authentication-method pre-shared-keys;
dh-group group2;
}
policy ike_policy_ms_4_0_0 {
version 2;
proposals ike_proposal_ms_4_0_0;
pre-shared-key ascii-text "$9ABC123"; ## SECRET-DATA
}
}
user@router1# show services service-set
ipsec_ss_ms_4_0_01 {
next-hop-service {
inside-service-interface ms-4/0/0.1;
outside-service-interface ms-4/0/0.2;
}
ipsec-vpn-options {
local-gateway 10.0.1.1;
}
ipsec-vpn-rules vpn_rule_ms_4_0_01;
}
配置路由器 2
分步程序
配置接口属性,例如家族、服务域和单元。
user@router2# set interfaces ms-1/0/0 services-options inactivity-non-tcp-timeout 600 user@router2# set interfaces ms-1/0/0 unit 0 family inet user@router2# set interfaces ms-1/0/0 unit 1 family inet user@router2# set interfaces ms-1/0/0 unit 1 family inet6 user@router2# set interfaces ms-1/0/0 unit 1 service-domain inside user@router2# set interfaces ms-1/0/0 unit 2 family inet user@router2# set interfaces ms-1/0/0 unit 2 family inet6 user@router2# set interfaces ms-1/0/0 unit 2 service-domain outside user@router2# set interfaces ge-2/0/0 unit 0 family inet adddress 10.0.1.2/30
配置 IPsec 属性,例如地址、远程网关、策略、匹配方向、协议、重放窗口大小、算法详细信息、保密密钥、提议、身份验证方法、组和版本。
user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 from source-address 192.168.0.0/16 user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 from destination-address 172.16.0.0/16 user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then remote-gateway 10.0.1.1 user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then dynamic ike-policy ike_policy_ms_5_2_0 user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then dynamic ipsec-policy ipsec_policy_ms_5_2_0 user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 term term11 then anti-replay-window-size 4096 user@router2# set services ipsec-vpn rule vpn_rule_ms_5_2_01 match-direction input user@router2# set services ipsec-vpn ipsec proposal ipsec_proposal_ms_5_2_0 protocol esp user@router2# set services ipsec-vpn ipsec proposal ipsec_proposal_ms_5_2_0 authentication-algorithm hmac-sha1-96 user@router2# set services ipsec-vpn ipsec proposal ipsec_proposal_ms_5_2_0 encryption-algorithm 3des-cbc user@router2# set services ipsec-vpn ipsec policy ipsec_policy_ms_5_2_0 perfect-forward-secrecy keys group2 user@router2# set services ipsec-vpn ipsec policy ipsec_policy_ms_5_2_0 proposals ipsec_proposal_ms_5_2_0 user@router2# set services ipsec-vpn ike proposal ike_proposal_ms_5_2_0 authentication-method pre-shared-keys user@router2# set services ipsec-vpn ike proposal ike_proposal_ms_5_2_0 dh-group group2 user@router2# set services ipsec-vpn ike policy ike_policy_ms_5_2_0 version 2 user@router2# set services ipsec-vpn ike policy ike_policy_ms_5_2_0 proposals ike_proposal_ms_5_2_0 user@router2# set services ipsec-vpn ike policy ike_policy_ms_5_2_0 pre-shared-key ascii-text "$ABC123" user@router2# set services ipsec-vpn establish-tunnels immediately
配置服务集,例如 next-hop-service 和 ipsec-vpn-options。
user@router2# set services service-set ipsec_ss_ms_5_2_01 next-hop-service inside-service-interface ms-1/0/0.1 user@router2# set services service-set ipsec_ss_ms_5_2_01 next-hop-service outside-service-interface ms-1/0/0.2 user@router2# set services service-set ipsec_ss_ms_5_2_01 ipsec-vpn-options local-gateway 10.0.1.2 user@router2# set services service-set ipsec_ss_ms_5_2_01 ipsec-vpn-rules vpn_rule_ms_5_2_01
配置路由选项、静态路由和下一跳。
user@router2# set routing-options static route 172.16.0.0/16 next-hop ms-1/0/0.1
结果
在路由器 2 的配置模式下,输入 show interfaces、 show services ipsec-vpn和 show services service-set 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置。
user@router2# show interfaces
ms-1/0/0 {
unit 0 {
family inet;
}
unit 1 {
family inet;
family inet6;
service-domain inside;
}
unit 2 {
family inet;
family inet6;
service-domain outside;
}
}
ge-2/0/0 {
unit 0 {
family inet {
address 10.0.1.2/30;
}
}
}
user@router2# show services ipsec-vpn
rule vpn_rule_ms_5_2_01 {
term term11 {
from {
source-address {
192.168.0.0/16;
}
destination-address {
172.16.0.0/16;
}
}
then {
remote-gateway 10.0.1.1;
dynamic {
ike-policy ike_policy_ms_5_2_0;
ipsec-policy ipsec_policy_ms_5_2_0;
}
anti-replay-window-size 4096;
}
}
match-direction input;
}
ipsec {
proposal ipsec_proposal_ms_5_2_0 {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy ipsec_policy_ms_5_2_0 {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec_proposal_ms_5_2_0;
}
}
ike {
proposal ike_proposal_ms_5_2_0 {
authentication-method pre-shared-keys;
dh-group group2;
}
policy ike_policy_ms_5_2_0 {
version 2;
proposals ike_proposal_ms_5_2_0;
pre-shared-key ascii-text "$9ABC123"; ## SECRET-DATA
}
}
establish-tunnels immediately;
user@router2# show services service-set
ipsec_ss_ms_5_2_01 {
next-hop-service {
inside-service-interface ms-1/0/0.1;
outside-service-interface ms-1/0/0.2;
}
ipsec-vpn-options {
local-gateway 10.0.1.2;
}
ipsec-vpn-rules vpn_rule_ms_5_2_01;
}
user@router2 #show routing-options
static {
route 172.16.0.0/16 next-hop ms-1/0/0.1;
}
验证
验证隧道创建
目的
验证是否已创建动态端点。
行动
在路由器 1 上运行以下命令:
user@router1 >show services ipsec-vpn ipsec security-associations detail
Service set: ipsec_ss_ms_4_0_01, IKE Routing-instance: default
Rule: vpn_rule_ms_4_0_01, Term: term11, Tunnel index: 1
Local gateway: 10.0.1.1, Remote gateway: 10.0.1.2
IPSec inside interface: ms-4/0/0.1, Tunnel MTU: 1500
Local identity: ipv4_subnet(any:0,[0..7]=172.16.0.0/16)
Remote identity: ipv4_subnet(any:0,[0..7]=192.168.0.0/16)
Direction: inbound, SPI: 112014862, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 24556 seconds
Hard lifetime: Expires in 25130 seconds
Anti-replay service: Enabled, Replay window size: 4096
Direction: outbound, SPI: 1469281276, AUX-SPI: 0
Mode: tunnel, Type: dynamic, State: Installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc
Soft lifetime: Expires in 24556 seconds
Hard lifetime: Expires in 25130 seconds
Anti-replay service: Enabled, Replay window size: 4096
意义
输出显示路由器上的 IPSec SA 已启动,状态为已安装。IPSec 隧道已启动,可通过隧道发送流量。
验证通过 DEP 隧道的流量
目的
验证通过新创建的 DEP 隧道的流量。
行动
在路由器 2 上运行以下命令:
user@router2> show services ipsec-vpn ipsec statistics PIC: ms-1/0/0, Service set: ipsec_ss_ms_5_2_01 ESP Statistics: Encrypted bytes: 153328 Decrypted bytes: 131424 Encrypted packets: 2738 Decrypted packets: 2738 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0 ESP authentication failures: 0 ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Replay before window drops: 0, Replayed pkts: 0 IP integrity errors: 0, Exceeds tunnel MTU: 0 Rule lookup failures: 0, No SA errors: 0 Flow errors: 0, Misc errors: 0
验证服务集的 IPsec 安全性关联
目的
验证为服务集配置的安全关联是否正常运行。
行动
在路由器 2 上运行以下命令:
user@router2> show services ipsec-vpn ipsec security-associations ipsec_ss_ms_5_2_01
Service set: ipsec_ss_ms_5_2_01, IKE Routing-instance: default
Rule: vpn_rule_ms_5_2_01, Term: term11, Tunnel index: 1
Local gateway: 10.0.1.2., Remote gateway: 10.0.1.1
IPSec inside interface: ms-1/0/0.1, Tunnel MTU: 1500
Direction SPI AUX-SPI Mode Type Protocol
inbound 1612447024 0 tunnel dynamic ESP
outbound 1824720964 0 tunnel dynamic ESP
示例:通过 VRF 实例配置静态分配的 IPsec 隧道
此示例说明了如何通过 VRF 实例配置静态分配的 IPsec 隧道,包含以下部分:
要求
此示例使用以下硬件和软件组件:
M Series、MX 系列或配置为提供商边缘路由器的T Series路由器。
Junos OS 9.4 及更高版本。
在配置此功能之前,不需要除设备初始化之外的特殊配置。
概述
您可以通过 Junos OS 在虚拟路由和转发 (VRF) 实例上配置静态分配的 IPsec 隧道。能够在 VRF 实例上配置 IPsec 隧道,从而增强网络分段和安全性。您可以通过 VRF 实例在同一 PE 路由器上配置多个客户隧道。每个 VRF 实例都可用作具有专用路由表的逻辑路由器。
配置
此示例显示了通过提供商边缘路由器上的 VRF 实例配置 IPsec 隧道,并提供了完成所需配置的分步说明。
本节包含:
配置提供商边缘路由器
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到 [edit] 层级的 CLI 中。
set interfaces ge-0/3/0 unit 0 family inet address 10.6.6.6/32 set interfaces ge-1/1/0 description "teller ge-0/1/0" set interfaces ge-1/1/0 unit 0 family inet address 10.21.1.1/16 set interfaces ms-1/2/0 unit 0 family inet address 10.7.7.7/32 set interfaces ms-1/2/0 unit 1 family inet set interfaces ms-1/2/0 unit 1 service-domain inside set interfaces ms-1/2/0 unit 2 family inet set interfaces ms-1/2/0 unit 2 service-domain outside set policy-options policy-statement vpn-export then community add vpn-community set policy-options policy-statement vpn-export then accept set policy-options policy-statement vpn-import term a from community vpn-community set policy-options policy-statement vpn-import term a then accept set policy-options community vpn-community members target:100:20 set routing-instances vrf instance-type vrf set routing-instances vrf interface ge-0/3/0.0 set routing-instances vrf interface ms-1/2/0.1 set routing-instances vrf route-distinguisher 192.168.0.1:1 set routing-instances vrf vrf-import vpn-import set routing-instances vrf vrf-export vpn-export set routing-instances vrf routing-options static route 10.0.0.0/0 next-hop ge-0/3/0.0 set routing-instances vrf routing-options static route 10.11.11.1/32 next-hop ge-0/3/0.0 set routing-instances vrf routing-options static route 10.8.8.1/32 next-hop ms-1/2/0.1 set services ipsec-vpn ipsec proposal demo_ipsec_proposal protocol esp set services ipsec-vpn ipsec proposal demo_ipsec_proposal authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal demo_ipsec_proposal encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy demo_ipsec_policy perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec policy demo_ipsec_policy proposals demo_ipsec_proposal set services ipsec-vpn ike proposal demo_ike_proposal authentication-method pre-shared-keys set services ipsec-vpn ike proposal demo_ike_proposal dh-group group2 set services ipsec-vpn ike policy demo_ike_policy proposals demo_ike_proposal set services ipsec-vpn ike policy demo_ike_policy pre-shared-key ascii-text juniperkey set services ipsec-vpn rule demo-rule term demo-term then remote-gateway 10.21.2.1 set services ipsec-vpn rule demo-rule term demo-term then dynamic ike-policy demo_ike_policy set services ipsec-vpn rule demo-rule match-direction input set services service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 set services service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 set services service-set demo-service-set ipsec-vpn-options local-gateway 10.21.1.1 set services service-set demo-service-set ipsec-vpn-rules demo-rule
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要在 VRF 实例上配置静态分配的 IPsec 隧道:
配置接口。在此步骤中,您将为服务接口的逻辑接口配置两个以太网 (
ge) 接口、一个服务接口 (ms-) 以及服务域属性。请注意,标记为内部接口的逻辑接口对流量应用配置的服务,而标记为外部接口的逻辑接口则充当内部接口应用服务的流量的出口点。[edit interfaces] user@PE1# set ge-0/3/0 unit 0 family inet address 10.6.6.6/32 user@PE1# set ge-1/1/0 description "teller ge-0/1/0" user@PE1# set ge-1/1/0 unit 0 family inet address 10.21.1.1/16 user@PE1# set ms-1/2/0 unit 0 family inet address 10.7.7.7/32 user@PE1# set ms-1/2/0 unit 1 family inet user@PE1# set ms-1/2/0 unit 1 service-domain inside user@PE1# set ms-1/2/0 unit 2 family inet user@PE1# set ms-1/2/0 unit 2 service-domain outside
配置路由策略以指定 VRF 实例的路由导入和导出标准。此步骤中定义的导入和导出策略将从下一步的路由实例配置中引用。
[edit policy-options] user@PE1# set policy-statement vpn-export then community add vpn-community user@PE1# set policy-statement vpn-export then accept user@PE1# set policy-statement vpn-import term a from community vpn-community user@PE1# set policy-statement vpn-import term a then accept user@PE1# set community vpn-community members target:100:20
配置路由实例并将路由实例类型指定为
vrf。将上一步中定义的导入和导出策略应用于路由实例,并指定静态路由以将 IPsec 流量发送到第一步中配置的内部接口 (ms-1/2/0.1)。[edit routing-instance] user@PE1# set vrf instance-type vrf user@PE1# set vrf interface ge-0/3/0.0 user@PE1# set vrf interface ms-1/2/0.1 user@PE1# set vrf route-distinguisher 192.168.0.1:1 user@PE1# set vrf vrf-import vpn-import user@PE1# set vrf vrf-export vpn-export user@PE1# set vrf routing-options static route 10.0.0.0/0 next-hop ge-0/3/0.0 user@PE1# set vrf routing-options static route 10.11.11.1/32 next-hop ge-0/3/0.0 user@PE1# set vrf routing-options static route 10.8.8.1/32 next-hop ms-1/2/0.1
配置 IKE 和 IPsec 提议和策略,以及用于对传入流量应用 IKE 策略的规则。
注意:默认情况下,Junos OS 使用 IKE 策略版本 1.0。Junos OS 11.4 及更高版本还支持 IKE 策略 2.0 版,您必须在 上
[edit services ipsec-vpn ike policy policy-name pre-shared]进行配置。[edit services] user@PE1# set ipsec-vpn ipsec proposal demo_ipsec_proposal protocol esp user@PE1# set ipsec-vpn ipsec proposal demo_ipsec_proposal authentication-algorithm hmac-sha1-96 user@PE1# set ipsec-vpn ipsec proposal demo_ipsec_proposal encryption-algorithm 3des-cbc user@PE1# set ipsec-vpn ipsec policy demo_ipsec_policy perfect-forward-secrecy keys group2 user@PE1# set ipsec-vpn ipsec policy demo_ipsec_policy proposals demo_ipsec_proposal user@PE1# set ipsec-vpn ike proposal demo_ike_proposal authentication-method pre-shared-keys user@PE1# set ipsec-vpn ike proposal demo_ike_proposal dh-group group2 user@PE1# set ipsec-vpn ike policy demo_ike_policy proposals demo_ike_proposal user@PE1# set ipsec-vpn ike policy demo_ike_policy pre-shared-key ascii-text juniperkey user@PE1# set ipsec-vpn rule demo-rule term demo-term then remote-gateway 10.21.2.1 user@PE1# set ipsec-vpn rule demo-rule term demo-term then dynamic ike-policy demo_ike_policy user@PE1# set ipsec-vpn rule demo-rule match-direction input
配置下一跳样式服务集。请注意,您必须将第一步中配置的内部和外部接口分别配置为 和
inside-service-interfaceoutside-service-interface。[edit services] user@PE1# set service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 user@PE1# set service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 user@PE1# set service-set demo-service-set ipsec-vpn-options local-gateway 10.21.1.1 user@PE1# set service-set demo-service-set ipsec-vpn-rules demo-rule
提交配置。
[edit] user@PE1# commit
结果
在路由器 1 的配置模式下,输入 show interfaces、 show policy-options、 show routing-instancesshow services ipsec-vpn、 和show services service-set 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置。
user@PE1# show interfaces
...
ms-1/2/0 {
unit 0 {
family inet {
address 10.7.7.7/32;
}
}
unit 1 {
family inet;
service-domain inside;
}
unit 2 {
family inet;
service-domain outside;
}
}
ge-0/3/0 {
unit 0 {
family inet {
address 10.6.6.6/32;
}
}
}
ge-1/1/0 {
description "teller ge-0/1/0";
unit 0 {
family inet {
address 10.21.1.1/16;
}
}
}
...
user@PE1# show policy-options
policy-statement vpn-export {
then {
community add vpn-community;
accept;
}
}
policy-statement vpn-import {
term a {
from community vpn-community;
then accept;
}
}
community vpn-community members target:100:20;
user@PE1# show routing-instances
vrf {
instance-type vrf;
interface ge-0/3/0.0;
interface ms-1/2/0.1;
route-distinguisher 192.168.0.1:1;
vrf-import vpn-import;
vrf-export vpn-export;
routing-options {
static {
route 10.0.0.0/0 next-hop ge-0/3/0.0;
route 10.11.11.1/32 next-hop ge-0/3/0.0;
route 10.8.8.1/32 next-hop ms-1/2/0.1;
}
}
}
user@PE1# show services ipsec-vpn
ipsec-vpn {
rule demo-rule {
term demo-term {
then {
remote-gateway 10.21.2.1;
dynamic {
ike-policy demo_ike_policy;
}
}
}
match-direction input;
}
ipsec {
proposal demo_ipsec_proposal {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy demo_ipsec_policy {
perfect-forward-secrecy {
keys group2;
}
proposals demo_ipsec_proposal;
}
}
ike {
proposal demo_ike_proposal {
authentication-method pre-shared-keys;
dh-group group2;
}
policy demo_ike_policy {
proposals demo_ike_proposal;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
}
}
user@PE1# show services service-set demo-service-set
next-hop-service {
inside-service-interface ms-1/2/0.1;
outside-service-interface ms-1/2/0.2;
}
ipsec-vpn-options {
local-gateway 10.21.1.1;
}
ipsec-vpn-rules demo-rule;
多任务 示例:配置 IPsec 服务
以下基于示例的说明说明了如何配置 IPsec 服务。配置涉及定义 IKE 策略、IPsec 策略、IPsec 规则、追踪选项和服务集。
本主题包含以下任务:
- 配置 IKE 提议
- 配置 IKE 策略(并引用 IKE 提议)
- 配置 IPsec 提议
- 配置 IPsec 策略(并引用 IPsec 提议)
- 配置 IPsec 规则(并引用 IKE 和 IPsec 策略)
- 配置 IPsec 追踪选项
- 配置访问配置文件(并引用 IKE 和 IPsec 策略)
- 配置服务集(并引用 IKE 配置文件和 IPsec 规则)
配置 IKE 提议
IKE 提议配置定义用于与对等安全网关建立安全 IKE 连接的算法和密钥。有关 IKE 提议的详细信息,请参阅 配置 IKE 提议。
要定义 IKE 提议I:
以下示例输出显示了 IKE 提议的配置:
[edit services ipsec-vpn]
user@host# show ike
proposal test-IKE-proposal {
authentication-method pre-shared-keys;
dh-group group1;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
也可以看看
配置 IKE 策略(并引用 IKE 提议)
IKE 策略配置定义 IKE 协商期间使用的提议、模式、地址和其他安全参数。有关 IKE 策略的详细信息,请参阅 配置 IKE 策略。
要定义 IKE 策略并引用 IKE 提议,请执行以下作:
以下示例输出显示了 IKE 策略的配置:
[edit services ipsec-vpn]
user@host# show ike
policy test-IKE-policy {
mode main;
proposals test-IKE-proposal;
local-id ipv4_addr 192.168.255.2;
pre-shared-key ascii-text TEST;
}
配置 IPsec 提议
IPsec 提议配置定义与远程 IPsec 对等方协商所需的协议和算法(安全服务)。有关 IPsec 提议的详细信息,请参阅 配置 IPsec 提议。
要定义 IPsec 提议,请执行以下作:
以下示例输出显示了 IPsec 提议的配置:
[edit services ipsec-vpn]
user@host# show ike
proposal test-IPsec-proposal {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
也可以看看
配置 IPsec 策略(并引用 IPsec 提议)
IPsec 策略配置定义了 IPsec 协商期间使用的安全参数(IPsec 提议)的组合。它定义了 PFS 和连接所需的提议。有关 IPsec 策略的详细信息,请参阅 配置 IPsec 策略。
要定义 IPsec 策略并引用 IPsec 提议,请执行以下作:
以下示例输出显示了 IPsec 策略的配置:
[edit services ipsec-vpn]
user@host# show ipsec policy test-IPsec-policy
perfect-forward-secrecy {
keys group1;
}
proposals test-IPsec-proposal;
也可以看看
配置 IPsec 规则(并引用 IKE 和 IPsec 策略)
IPsec 规则配置定义的方向指定是在接口的输入侧还是输出侧应用匹配。该配置还包含一组术语,这些术语指定包含和排除的匹配条件和应用程序,还指定要由路由器软件执行的作和作修改器。有关 IPsec 规则的详细信息,请参阅 配置 IPsec 规则。
要定义 IPsec 规则并引用 IKE 和 IPsec 策略,请执行以下作:
以下示例输出显示了 IPsec 规则的配置:
[edit services ipsec-vpn]
user@host# show rule test-IPsec-rule
term 10 {
from {
destination-address {
192.168.255.2/32;
}
}
then {
remote-gateway 0.0.0.0;
dynamic {
ike-policy test-IKE-policy;
ipsec-policy test-IPsec-policy;
}
}
}
match-direction input;
配置 IPsec 追踪选项
IPsec 追踪选项配置跟踪 IPsec 事件,并将其记录在 /var/log 目录中的日志文件中。默认情况下,此文件名为 /var/log/kmd。有关 IPsec 规则的详细信息,请参阅跟踪 Junos VPN Site Secure作。
要定义 IPsec 追踪选项:
以下示例输出显示了 IPsec 追踪选项的配置:
[edit services ipsec-vpn] user@host# show traceoptions file ipsec.log; flag all;
配置访问配置文件(并引用 IKE 和 IPsec 策略)
访问配置文件配置定义访问配置文件并引用 IKE 和 IPsec 策略。有关访问配置文件的详细信息,请参阅 配置 IKE 访问配置文件。
要定义访问配置文件并引用 IKE 和 IPsec 策略,请执行以下作:
以下示例输出显示了访问配置文件的配置:
[edit access]
user@host# show
profile IKE-profile-TEST {
client * {
ike {
allowed-proxy-pair local 10.0.0.0/24 remote 10.0.1.0/24;
ike-policy test-IKE-policy;
ipsec-policy test-IPsec-policy; # new statement
interface-id TEST-intf;
}
}
}
也可以看看
配置服务集(并引用 IKE 配置文件和 IPsec 规则)
服务集配置定义需要其他规范并引用 IKE 配置文件和 IPsec 规则的 IPsec 服务集。有关 IPsec 服务集的详细信息,请参阅 配置 IPsec 服务集。
要使用下一跃点服务集和 IPsec VPN 选项定义服务集配置:
以下示例输出显示了引用 IKE 配置文件和 IPsec 规则的服务集配置的配置:
[edit services]user@host# show service-set TEST
next-hop-service {
inside-service-interface sp-1/2/0.1;
outside-service-interface sp-1/2/0.2;
}
ipsec-vpn-options {
local-gateway 192.168.255.2;
ike-access-profile IKE-profile-TEST;
}
ipsec-vpn-rules test-IPsec-rule;
也可以看看
禁用 MX 系列路由器上的 NAT-T,以处理受 IPsec 保护的数据包的 NAT
在 Junos OS 17.4R1 之前,MX 系列路由器上的 Junos VPN Site Secure IPsec 功能套件不支持网络地址转换遍历 (NAT-T)。默认情况下,Junos OS 会检测任一 IPsec 隧道是否位于 NAT 设备后面,并自动切换为对受保护的流量使用 NAT-T。为避免在 17.4R1 之前的 Junos OS 版本中运行不受支持的 NAT-T,您必须通过在 disable-natt 层次结构级别包含 [edit services ipsec-vpn] 该语句来禁用 NAT-T。禁用 NAT-T 后,NAT-T 功能将全局关闭。禁用 NAT-T 且两个 IPsec 网关之间存在 NAT 设备时,将使用 UDP 端口 500 协商 ISAKMP 消息,并使用封装安全性有效负载 (ESP) 封装数据包。
网络地址转换遍历 (NAT-T) 是一种绕过受 IPsec 保护的数据通过 NAT 设备进行地址转换时遇到的 NAT 地址转换问题的方法。对 IP 寻址(NAT 的功能)进行的任何更改都会导致 IKE 丢弃数据包。在第 1 阶段交换期间检测到数据路径上的一个或多个 NAT 设备后,NAT-T 会为 IPsec 数据包添加一层用户数据报协议 (UDP) 封装,以便在地址转换后不会将其丢弃。NAT-T 将 IKE 和 ESP 流量封装到 UDP 中,并将端口 4500 用作源端口和目标端口。由于 NAT 设备会使过时的 UDP 转换,因此对等方之间需要激活消息。
NAT 设备的位置可以是:
只有 IKEv1 或 IKEv2 发起方位于 NAT 设备后面。多个发起方可以位于单独的 NAT 设备后面。发起方还可通过多个 NAT 设备连接到响应方。
只有 IKEv1 或 IKEv2 响应方位于 NAT 设备后面。
IKEv1 或 IKEv2 发起方和响应方均位于 NAT 设备后面。
动态端点 VPN 涵盖发起方的 IKE 外部地址不是固定的,因此响应方不知道的情况。当发起方的地址由 ISP 动态分配时,或者当发起方的连接通过从动态地址池分配地址的动态 NAT 设备时,可能会发生这种情况。
对于只有响应方位于 NAT 设备后面的拓扑,以及发起方和响应方都位于 NAT 设备后面的拓扑,提供了 NAT-T 的配置示例。发起方和响应方都支持用于 NAT-T 的站点到站点 IKE 网关配置。远程IKE ID 用于在IKE隧道协商的第 1 阶段验证对等方的本地 IKE ID。发起方和响应方都需要本地标识和远程标识字符串。
也可以看看
跟踪 Junos VPN Site Secure作
Junos VPN Site Secure 是多服务线卡(MS-DPC、MS-MPC 和 MS-MIC)支持的一套 IPsec 功能,之前称为 IPsec 服务。
追踪作会跟踪 IPsec 事件,并将其记录在目录中的 /var/log 日志文件中。默认情况下,此文件名为 /var/log/kmd。
要跟踪 IPsec作,请在层次结构级别包含[edit services ipsec-vpn]以下traceoptions语句:
[edit services ipsec-vpn] traceoptions { file <filename> <files number> <match regular-expression> <size bytes> <world-readable | no-world-readable>; flag flag; level level; no-remote-trace; }
您可以指定以下 IPsec 跟踪标志:
all——追踪一切。certificates- 跟踪证书事件。database- 跟踪安全关联数据库事件。general—跟踪一般事件。ike— 跟踪 IKE 模块处理。parse—跟踪配置处理。policy-manager—跟踪策略管理器处理。routing-socket- 跟踪路由套接字消息。snmp— 跟踪 SNMP作。timer—跟踪内部计时器事件。
该 level 语句设置密钥管理进程 (kmd) 跟踪级别。支持以下值:
all- 匹配所有级别。error- 匹配错误条件。info–匹配信息性消息。notice- 应特殊处理的匹配条件。verbose- 匹配详细消息。warning- 匹配警告消息。
本部分包含以下主题:
在 traceroute 中禁用 IPsec 隧道端点
如果在层次结构级别包含[edit services ipsec-vpn]该no-ipsec-tunnel-in-traceroute语句,则 IPsec 隧道不会被视为下一跃点,生存时间 (TTL) 也不会递减。此外,如果 TTL 达到零,则不会生成 ICMP 超时消息。
[edit services ipsec-vpn] no-ipsec-tunnel-in-traceroute;
语句也提供了 passive-mode-tunneling 此功能。在特定场景中,您可以使用该 no-ipsec-tunnel-in-traceroute 语句,在这些场景中,IPsec 隧道不应被视为下一跃点,并且不需要使用被动模式。
追踪 IPsec PKI作
追踪作会跟踪 IPsec PKI 事件,并将其记录在目录中的 /var/log 日志文件中。默认情况下,此文件名为 /var/log/pkid。
要跟踪 IPsec PKI作,请在层次结构级别包含[edit security pki]该traceoptions语句:
[edit security pki] traceoptions { file filename <files number> <match regular-expression> <size maximum-file-size> <world-readable | no-world-readable>; flag flag (all | certificate-verification | enrollment | online-crl-check); }
您可以指定以下 PKI 跟踪标志:
all——追踪一切。certificates- 跟踪证书事件。database- 跟踪安全关联数据库事件。general—跟踪一般事件。ike— 跟踪 IKE 模块处理。parse—跟踪配置处理。policy-manager—跟踪策略管理器处理。routing-socket- 跟踪路由套接字消息。snmp— 跟踪 SNMP作。timer—跟踪内部计时器事件。
变更历史表
是否支持某项功能取决于您使用的平台和版本。使用 功能资源管理器 确定您的平台是否支持某个功能。
gw-interface 语句来清理IKE触发器以及 IKE 和 IPsec SA。
[edit services ipsec-vpn rule rule-name term term-name from]语句将 AMS 逻辑接口配置为 IPsec 内部接口
ipsec-inside-interface interface-name。
header-integrity-check MS-MIC 和 MS-MPC 支持的选项用于验证数据包标头是否存在 IP、TCP、UDP 和 ICMP 信息中的异常,并标记此类异常和错误,其功能与被动模式隧道引入的功能相反。
