ON THIS PAGE
IPsec VPN Overview
Read this topic to know about the IKE and IPsec packet processing, and IPsec VPN topologies on SRX Series Firewalls. Learn about the services processing cards, cryptographic acceleration, routing protocols support, and the iked process support.
A VPN is a private network that uses a public network to connect two or more remote sites. Instead of using dedicated connections between networks, VPNs use virtual connections routed (tunneled) through public networks. IPsec VPN is a protocol, consists of set of standards used to establish a VPN connection.
A VPN provides a means by which remote computers communicate securely across a public WAN such as the Internet.
A VPN connection can link two LANs (site-to-site VPN) or a remote dial-up user and a LAN. The traffic that flows between these two points passes through shared resources such as routers, switches, and other network equipment that make up the public WAN. To secure VPN communication while passing through the WAN, the two participants create an IPsec tunnel.
The term tunnel does not denote tunnel mode (see Packet Processing in Tunnel Mode). Instead, it refers to the IPsec connection.
Use Feature Explorer to confirm platform and release support for specific features.
Review the Platform-Specific IPsec VPN Behavior section for notes related to your platform.
See the Additional Platform Information section for more information.
IPsec VPN Topologies on SRX Series Firewalls
The following are some of the IPsec VPN topologies that Junos operating system (OS) supports:
Site-to-site VPNs—Connects two sites in an organization together and allows secure communications between the sites.
Hub-and-spoke VPNs—Connects branch offices to the corporate office in an enterprise network. You can also use this topology to connect spokes together by sending traffic through the hub.
Remote access VPNs—Allows users working at home or traveling to connect to the corporate office and its resources. This topology is sometimes referred to as an end-to-site tunnel.
See Also
Comparing Policy-Based and Route-Based VPNs
Read this topic to understand the differences between policy-based and route-based VPNs.
It is important to understand the differences between policy-based and route-based VPNs and why one might be preferable to the other.
Table 1 lists the differences between route-based VPNs and policy-based VPNs.
|
Route-Based VPNs |
Policy-Based VPNs |
|---|---|
|
With route-based VPNs, a policy does not specifically reference a VPN tunnel. |
With policy-based VPN tunnels, a tunnel is treated as an object that, together with source, destination, application, and action, constitutes a tunnel policy that permits VPN traffic. |
|
The policy references a destination address. |
In a policy-based VPN configuration, a tunnel policy specifically references a VPN tunnel by name. |
|
The number of route-based VPN tunnels that you create is limited by the number of route entries or the number of st0 interfaces that the device supports, whichever number is lower. |
The number of policy-based VPN tunnels that you can create is limited by the number of policies that the device supports. |
|
Route-based VPN tunnel configuration is a good choice when you want to conserve tunnel resources while setting granular restrictions on VPN traffic. |
With a policy-based VPN, although you can create numerous tunnel policies referencing the same VPN tunnel, each tunnel policy pair creates an individual IPsec security association (SA) with the remote peer. Each SA counts as an individual VPN tunnel. |
|
With a route-based approach to VPNs, the regulation of traffic is not coupled to the means of its delivery. You can configure dozens of policies to regulate traffic flowing through a single VPN tunnel between two sites, and only one IPsec SA is at work. Also, a route-based VPN configuration allows you to create policies referencing a destination reached through a VPN tunnel in which the action is deny. |
In a policy-based VPN configuration, the action must be permit and must include a tunnel. |
|
Route-based VPNs support the exchange of dynamic routing information through VPN tunnels. You can enable an instance of a dynamic routing protocol, such as OSPF, on an st0 interface that is bound to a VPN tunnel. |
The exchange of dynamic routing information is not supported in policy-based VPNs. |
|
Route-based configurations are used for hub-and-spoke topologies. |
Policy-based VPNs cannot be used for hub-and-spoke topologies. |
|
With route-based VPNs, a policy does not specifically reference a VPN tunnel. |
When a tunnel does not connect large networks running dynamic routing protocols and you do not need to conserve tunnels or define various policies to filter traffic through the tunnel, a policy-based tunnel is the best choice. |
|
Route-based VPNs do not support remote-access (dial-up) VPN configurations. |
Policy-based VPN tunnels are required for remote-access (dial-up) VPN configurations. |
|
Route-based VPNs might not work correctly with some third-party vendors. |
Policy-based VPNs might be required if the third party requires separate SAs for each remote subnet. |
|
When the security device does a route lookup to find the
interface through which it must send traffic to reach an
address, it finds a route via a secure tunnel interface
( With a route-based VPN tunnel, you can consider a tunnel as a means for delivering traffic, and can consider the policy as a method for either permitting or denying the delivery of that traffic. |
With a policy-based VPN tunnel, you can consider a tunnel as an element in the construction of a policy. |
|
Route-based VPNs support NAT for st0 interfaces. |
Policy-based VPNs cannot be used if NAT is required for tunneled traffic. |
Proxy ID is supported for both route-based and policy-based VPNs. Route-based tunnels also offer the usage of multiple traffic selectors also known as multi-proxy ID. A traffic selector is an agreement between IKE peers to permit traffic through a tunnel, if the traffic matches a specified pair of local and remote IP address prefix, source port range, destination port range, and protocol. You define a traffic selector within a specific route-based VPN, which can result in multiple Phase 2 IPsec SAs. Only traffic that conforms to a traffic selector is permitted through an SA. The traffic selector is commonly required when remote gateway devices are non-Juniper Networks devices.
See Also
Comparison of Policy-Based VPNs and Route-Based VPNs
Table 2 summarizes the differences between policy-based VPNs and route-based VPNs.
Policy-Based VPNs |
Route-Based VPNs |
|---|---|
In policy-based VPNs, a tunnel is treated as an object that, together with source, destination, application, and action, constitutes a tunnel policy that permits VPN traffic. |
In route-based VPNs, a policy does not specifically reference a VPN tunnel. |
A tunnel policy specifically references a VPN tunnel by name. |
A route determines which traffic is sent through the tunnel based on a destination IP address. |
The number of policy-based VPN tunnels that you can create is limited by the number of tunnels that the device supports. |
The number of route-based VPN tunnels that you create is limited by the number of st0 interfaces (for point-to-point VPNs) or the number of tunnels that the device supports, whichever is lower. |
With a policy-based VPN, although you can create numerous tunnel policies referencing the same VPN tunnel, each tunnel policy pair creates an individual IPsec SA with the remote peer. Each SA counts as an individual VPN tunnel. |
Because the route, not the policy, determines which traffic goes through the tunnel, multiple policies can be supported with a single SA or VPN. |
In a policy-based VPN, the action must be permit and must include a tunnel. |
In a route-based VPN, the regulation of traffic is not coupled to the means of its delivery. |
The exchange of dynamic routing information is not supported in policy-based VPNs. |
Route-based VPNs support the exchange of dynamic routing information through VPN tunnels. You can enable an instance of a dynamic routing protocol, such as OSPF, on an st0 interface that is bound to a VPN tunnel. |
If you need more granularity than a route can provide to specify the traffic sent to a tunnel, using a policy-based VPN with security policies is the best choice. |
Route-based VPNs uses routes to specify the traffic sent to a tunnel; a policy does not specifically reference a VPN tunnel. |
With a policy-based VPN tunnel, you can consider a tunnel as an element in the construction of a policy. |
When the security device does a route lookup to find the interface through which it must send traffic to reach an address, it finds a route through a secure tunnel (st0) interface. With a route-based VPN tunnel, you can consider a tunnel as a means for delivering traffic, and can consider the policy as a method for either permitting or denying the delivery of that traffic. |
Understanding IKE and IPsec Packet Processing
An IPsec VPN tunnel consists of tunnel setup and applied security. During tunnel setup, the peers establish security associations (SAs), which define the parameters for securing traffic between themselves. See IPsec Overview. After the tunnel is established, IPsec protects the traffic sent between the two tunnel endpoints by applying the security parameters defined by the SAs during tunnel setup. Within the Junos OS implementation, IPsec is applied in tunnel mode, which supports the Encapsulating Security Payload (ESP) and Authentication Header (AH) protocols.
This topic includes the following sections:
Packet Processing in Tunnel Mode
IPsec operates in one of two modes—transport or tunnel. When both ends of the tunnel are hosts, you can use either mode. When at least one of the endpoints of a tunnel is a security gateway, such as a Junos OS router or firewall, you must use tunnel mode. Juniper Networks devices always operate in tunnel mode for IPsec tunnels.
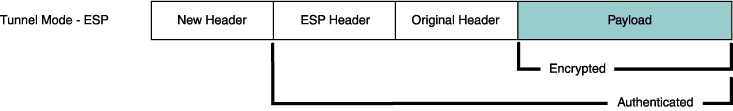
In tunnel mode, the entire original IP packet—payload and header—is encapsulated within another IP payload, and a new header is appended to it, as shown in Figure 1. The entire original packet can be encrypted, authenticated, or both. With the Authentication Header (AH) protocol, the AH and new headers are also authenticated. With the Encapsulating Security Payload (ESP) protocol, the ESP header can also be authenticated.
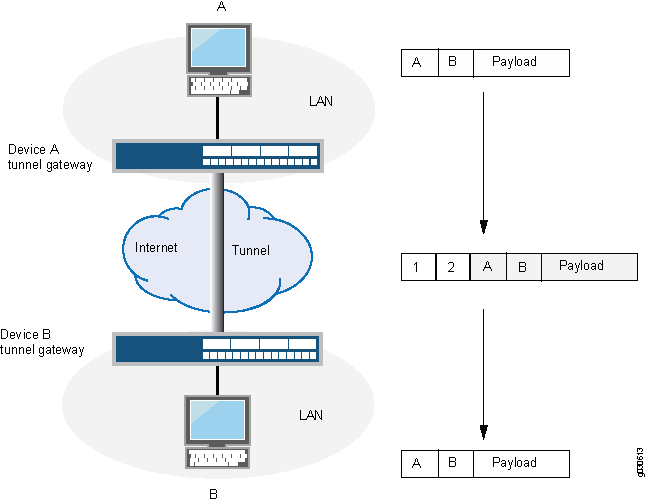
In a site-to-site VPN, the source and destination addresses used in the new header are the IP addresses of the outgoing interface. See Figure 2.
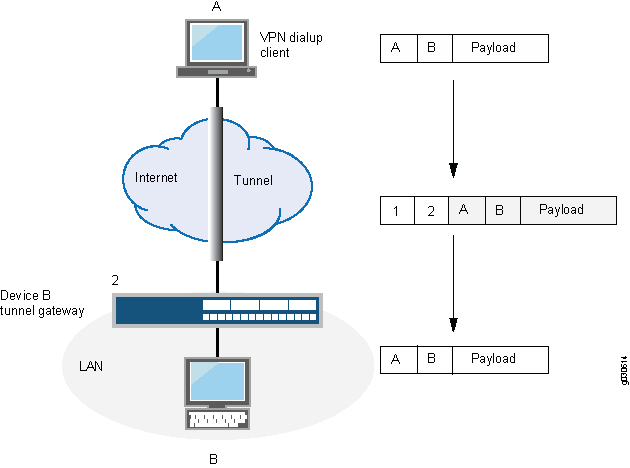
In a dial-up VPN, there is no tunnel gateway on the VPN dial-up client end of the tunnel; the tunnel extends directly to the client itself (see Figure 3). In this case, on packets sent from the dial-up client, both the new header and the encapsulated original header have the same IP address: that of the client’s computer.
Some VPN clients, such as the Netscreen-Remote, use a virtual inner IP address (also called a “sticky address”). Netscreen-Remote enables you to define the virtual IP address. In such cases, the virtual inner IP address is the source IP address in the original packet header of traffic originating from the client, and the IP address that the ISP dynamically assigns the dial-up client is the source IP address in the outer header.
See Also
Distribution of IKE and IPsec Sessions Across SPUs
Review the Platform-Specific SPUs VPN Processing Behavior section for notes related to your platform.
In SRX Series Firewalls, IKE provides tunnel management for IPsec and authenticates end entities. IKE performs a Diffie-Hellman (DH) key exchange to generate an IPsec tunnel between network devices. The IPsec tunnels generated by IKE are used to encrypt, decrypt, and authenticate user traffic between the network devices at the IP layer.
The VPN is created by distributing the IKE and IPsec workload among the multiple Services Processing Units (SPUs) of the platform. For site-to-site tunnels, the least-loaded SPU is chosen as the anchor SPU. If multiple SPUs have the same smallest load, any of them can be chosen as an anchor SPU. Here, load corresponds to the number of site-to-site gateways or manual VPN tunnels anchored on an SPU. For dynamic tunnels, the newly established dynamic tunnels employ a round-robin algorithm to select the SPU.
In IPsec, the workload is distributed by the same algorithm that distributes the IKE. The Phase 2 SA for a given VPN tunnel termination points pair is exclusively owned by a particular SPU, and all IPsec packets belonging to this Phase 2 SA are forwarded to the anchoring SPU of that SA for IPsec processing.
Multiple IPsec sessions (Phase 2 SA) can operate over one or more IKE sessions. The SPU that is selected for anchoring the IPsec session is based on the SPU that is anchoring the underlying IKE session. Therefore, all IPsec sessions that run over a single IKE gateway are serviced by the same SPU and are not load-balanced across several SPUs.
Table 3 shows an example of the firewall with three SPUs running seven IPsec tunnels over three IKE gateways.
|
SPU |
IKE Gateway |
IPsec Tunnel |
|---|---|---|
|
SPU0 |
IKE-1 |
IPsec-1 |
|
IPsec-2 |
||
|
IPsec-3 |
||
|
SPU1 |
IKE-2 |
IPsec-4 |
|
IPsec-5 |
||
|
IPsec-6 |
||
|
SPU2 |
IKE-3 |
IPsec-7 |
The three SPUs have an equal load of one IKE gateway each. If a new IKE gateway is created, SPU0, SPU1, or SPU2 could be selected to anchor the IKE gateway and its IPsec sessions.
Setting up and tearing down existing IPsec tunnels does not affect the underlying IKE session or existing IPsec tunnels.
Use the following show command to view the current tunnel count per SPU:
show security ike tunnel-map.
Use the summary option of the command to view the anchor points of each
gateway: show security ike tunnel-map summary.
VPN Support for Inserting Services Processing Cards
High-end SRX Series Firewalls have a chassis-based distributed processor architecture. The flow processing power is shared and is based on the number of Services Processing Cards (SPCs). You can scale the processing power of the device by installing new SPCs.
Review the Platform-Specific SRX5000 Line SPC Behavior section for notes related to your platform.
See the Additional Platform Information for kmd and iked Process in SRX5000 Line section for more information.
In high-end SRX Series chassis cluster, you can insert SPCs on the devices without affecting or disrupting the traffic on the existing IKE or IPsec VPN tunnels.
You can insert SPC3 or SPC2 card to an existing chassis containing SPC3 card. You can only insert the cards in a higher slot than the existing SPC3 card on the chassis.
However, existing tunnels cannot use the processing power of the Service Processing Units (SPUs) in the new SPCs. A new SPU can anchor newly established site-to-site and dynamic tunnels. Newly configured tunnels are not, however, guaranteed to be anchored on a new SPU.
Site-to-site tunnels are anchored on different SPUs based on a load-balancing algorithm. The load-balancing algorithm is dependent on number flow threads each SPU is using. Tunnels belonging to the same local and remote gateway IP addresses are anchored on the same SPU on different flow RT threads used by the SPU. The SPU with the smallest load is chosen as the anchor SPU. Each SPU maintains number of flow RT threads that are hosted in that particular SPU. The number of flow RT threads hosted on each SPU vary based on the type of SPU.
Tunnel load factor = Number of tunnels anchored on the SPU / Total number of flow RT threads used by the SPU.
Dynamic tunnels are anchored on different SPUs based on a round-robin algorithm. Newly configured dynamic tunnels are not guaranteed to be anchored on the new SPC.
When both SPC2 and SPC3 cards are installed, you can verify the tunnel mapping on
different SPUs using the show security ipsec tunnel-distribution
command.
Use the command show security ike tunnel-map to view the tunnel mapping
on different SPUs with only SPC2 card inserted. The command show security ike
tunnel-map is not valid in an environment where SPC2 and SPC3 cards are
installed.
Inserting SPC3 Card: Guidelines and Limitations:
-
In a chassis cluster, if one of the nodes has 1 SPC3 card and the other node has 2 SPC3 cards, the failover to the node that has 1 SPC3 card is not supported.
-
You must insert the SPC3 or SPC2 in an existing chassis in a higher slot than a current SPC3 present in a lower slot.
-
For SPC3 ISHU to work, you must insert the new SPC3 card into the higher slot number.
-
We do not support SPC3 hot removal.
See Also
IPsec VPN with iked Process
The two processes, iked and ikemd support IPsec VPN features on SRX Series Firewalls. A single instance of iked and ikemd run on the Routing Engine at a time.
With junos-ike package, the firewall runs IPsec VPN service using the
iked process. SRX Series Firewalls support junos-ike package is
multiple releases.
See the Additional Platform Information for junos-ike Package
Support section for more information.
Both
the
iked
and
ikemd
processes running on the Routing Engine are available with
the
junos-ike
package.
To install the junos-ike package on SRX Series Firewall, use the
following command:
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
To restart the
ikemd
process in the Routine Engine use the restart ike-config-management
command.
To restart the
iked
process in the Routing Engine use the restart ike-key-management
command.
Disregarding the specified Junos OS release versions when installing the
junos-ike package may result in unsupported features not
functioning as expected.
To operate IPsec VPN features using the legacy
kmd
process on
SRX
Series
Firewalls,
run the request system software delete junos-ike command and reboot the
device.
To check the installed junos-ike package, use the following command:
user@host> show version | grep ike
JUNOS ike [20190617.180318_builder_junos_182_x41]
JUNOS ike [20190617.180318_builder_junos_182_x41]
{primary:node0}
IPsec VPN Features Not Supported with iked Process
This section provides a summary of IPsec VPN features that are not supported on the SRX Series Firewalls.
Table 4 summarizes the non-supported IPsec VPN features on SRX Series Firewalls and vSRX Virtual Firewall running iked process.
|
Features |
Support Availability |
|---|---|
|
AutoVPN Protocol Independent Multicast (PIM) point-to-multipoint mode. |
No. But support is available on vSRX 3.0 |
|
Configuring forwarding class on IPsec VPNs. |
No |
|
Group VPN. |
No |
|
Packet size configuration for IPsec datapath verification. |
No |
|
Policy-based IPsec VPN. |
No |
Cryptographic Acceleration Support
Review the Platform-Specific Cryptographic Acceleration Behavior section for notes related to your platform.
See the Additional Platform Information for Cryptographic Acceleration Support section for more information.
Junos OS supports acceleration of cryptographic operations to the hardware cryptographic engine. SRX Series Firewall can offload DH, RSA, and ECDSA cryptographic operations to the hardware cryptographic engine.
With junos-ike package, the firewall runs IPsec VPN service using the iked process. The firewall requires the iked process as the control plane software to install and enable advanced IPsec VPN features. As a result of junos-ike package the firewall runs the iked and ikemd process on the routing engine by default instead of IPsec key management daemon (kmd).
The firewalls support hardware acceleration for various ciphers.
See Also
Routing Protocols Support on IPsec VPN Tunnels
See the Table 12, Table 13, Table 14, Table 15, Table 16, and Table 17 in Additional Platform Information section for more information.
Junos OS supports routing protocols on IPsec VPN tunnels with SRX Series Firewalls and MX Series routers with SPC3. Supported protocols include OSPF, BGP, PIM, RIP, and BFD when running the kmd or iked process. The protocol support varies based on the following:
-
IP addressing scheme: IPv4 or IPv6 addresses
-
Type of st0 interface: point-to-point (P2P) or point-to-multipoint (P2MP)
Anti-Replay Window
Review the Platform-Specific Antireplay Window Behavior section for notes related to your platform.
On SRX Series Firewalls, anti-replay-window is enabled by default with a
window size value of 64.
To
configure the window size, use the new anti-replay-window-size option.
An incoming packet is validated for replay attack based on the
anti-replay-window-size that is configured.
You can configure replay-window-size at two different levels:
-
Global level—Configured at the [
edit security ipsec] hierarchy level.For example:
[edit security ipsec] user@host# set anti-replay-window-size <64..8192>;
-
VPN object—Configured at the [
edit security ipsec vpn vpn-name ike] hierarchy level.For example:
[edit security ipsec vpn vpn-name ike] user@host# set anti-replay-window-size <64..8192>;
If anti-replay is configured at both levels, the window size configured for a VPN object level takes precedence over the window size configured at the global level. If anti-replay is not configured, the window size is 64 by default.
To disable the anti-replay window option on a VPN object, use the set
no-anti-replay command at the [edit security ipsec vpn vpn-name
ike] hierarchy level. You cannot disable anti-replay at the global
level.
You cannot configure both anti-replay-window-size and
no-anti-replay on a VPN object.
See Also
Understanding Hub-and-Spoke VPNs
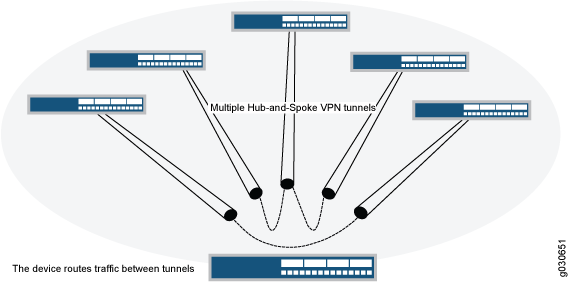
If you create two VPN tunnels that terminate at a device, you can set up a pair of routes so that the device directs traffic exiting one tunnel to the other tunnel. You also need to create a policy to permit the traffic to pass from one tunnel to the other. Such an arrangement is known as hub-and-spoke VPN. (See Figure 4.)
You can also configure multiple VPNs and route traffic between any two tunnels.
SRX Series Firewalls support only the route-based hub-and-spoke feature.
See Also
Platform-Specific IPsec VPN Behavior
Use Feature Explorer to confirm platform and release support for specific features.
See the Additional Platform Information section for more information.
Use the following tables to review platform-specific behaviors for your platforms.
- Platform-Specific SPUs VPN Processing Behavior
- Platform-Specific SRX5000 Line SPC Behavior
- Platform-Specific Cryptographic Acceleration Behavior
- Platform-Specific Antireplay Window Behavior
Platform-Specific SPUs VPN Processing Behavior
| Platform | Difference |
|---|---|
| SRX Series |
|
Platform-Specific SRX5000 Line SPC Behavior
| Platform | Difference |
|---|---|
| SRX Series |
|
Platform-Specific Cryptographic Acceleration Behavior
| Platform | Difference |
|---|---|
| SRX Series |
|
Platform-Specific Antireplay Window Behavior
| Platform | Difference |
|---|---|
| SRX Series |
|
Additional Platform Information
Use Feature Explorer to confirm platform and release support for specific features. Additional Platforms may be supported.
| Supported Process | SRX5000 Line |
|---|---|
| iked process |
Supports two options:
|
| kmd process |
|
junos-ike Package |
SRX1500 | SRX1600SRX2300 | SRX4100SRX4200SRX4600 | SRX4300 | SRX4700 | SRX5000 Line with SPC3 | vSRX 3.0 |
|---|---|---|---|---|---|---|---|
| Default | 25.2R1 and later | 23.4R1 and later | 25.2R1 and later | 24.2R1 and later |
24.4R1 and later |
19.4R1 and later (for RE3) | 25.2R1 and later |
| Optional | 22.3R1 and later | NA | 22.3R1 and later | NA | NA | 18.2R1 and later (for RE2) | 20.3R1 and later |
| Ciphers | SRX1500 (kmd) | SRX1500 (iked) | SRX4100SRX4200(kmd) | SRX4100SRX4200(iked) | SRX4600(kmd) | SRX4600(iked) | SRX5000 Line with SPC3(iked) | vSRX 3.0(kmd) | vSRX 3.0(iked) |
|---|---|---|---|---|---|---|---|---|---|
| DH (Groups 1, 2, 5, 14) | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| DH (Groups 19, 20) | No | Yes | No | Yes | No | Yes | Yes | Yes | Yes |
| DH (Groups 15, 16) | No | Yes | No | Yes | No | Yes | Yes | Yes | Yes |
| DH Group 21 | No | Yes | No | Yes | No | Yes | Yes | Yes | Yes |
| DH Group 24 | Yes | Yes | Yes | Yes | Yes | Yes | No | No | No |
| RSA | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| ECDSA (256, 384, 521) | No | Yes | No | Yes | No | Yes | Yes | Yes | Yes |
|
OSPF on IPsec VPN |
SRX300SRX320 SRX340SRX345SRX380 |
SRX550 HM |
SRX1500 |
SRX4100SRX4200SRX4600 |
SRX5000 Line with SPC3SRX5000 Line with SPC2 |
SRX5000 Line with Mixed-Mode (SPC3+SPC2) |
vSRX 3.0 |
MX-SPC3 |
|
|---|---|---|---|---|---|---|---|---|---|
|
st0 in P2P |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
With IPv6 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
|
st0 in P2MP |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
With IPv6 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
|
OSPFv3 on IPsec VPN |
SRX300SRX320 SRX340SRX345SRX380 |
SRX550 HM |
SRX1500 |
SRX4100SRX4200SRX4600 |
SRX5000 Line with SPC3SRX5000 Line with SPC2 |
SRX5000 Line with Mixed-Mode (SPC3+SPC2) |
vSRX 3.0 |
MX-SPC3 |
|
|---|---|---|---|---|---|---|---|---|---|
|
st0 in P2P |
With IPv4 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
st0 in P2MP |
With IPv4 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
BGP on IPsec VPN |
SRX300SRX320 SRX340SRX345SRX380 |
SRX550 HM |
SRX1500 |
SRX4100SRX4200SRX4600 |
SRX5000 Line with SPC3SRX5000 Line with SPC2 |
SRX5000 Line with Mixed-Mode (SPC3+SPC2) |
vSRX 3.0 |
MX-SPC3 |
|
|---|---|---|---|---|---|---|---|---|---|
|
st0 in P2P |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
st0 in P2MP |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
|
|
PIM on IPsec VPN |
SRX300SRX320 SRX340SRX345SRX380 |
SRX550 HM |
SRX1500 |
SRX4100SRX4200SRX4600 |
SRX5000 Line with SPC3SRX5000 Line with SPC2 |
SRX5000 Line with Mixed-Mode (SPC3+SPC2) |
vSRX 3.0 |
MX-SPC3 |
|
|---|---|---|---|---|---|---|---|---|---|
|
st0 in P2P |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
With IPv6 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
|
st0 in P2MP |
With IPv4 address |
Yes |
No |
Yes |
No |
No |
No |
Yes. Multithread is not supported. |
No |
|
With IPv6 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
|
RIP Protocol on IPsec VPN |
SRX300SRX320 SRX340SRX345SRX380 |
SRX550 HM |
SRX1500 |
SRX4100SRX4200SRX4600 |
SRX5000 Line with SPC3SRX5000 Line with SPC2 |
SRX5000 Line with Mixed-Mode (SPC3+SPC2) |
vSRX 3.0 |
MX-SPC3 |
|
|---|---|---|---|---|---|---|---|---|---|
|
st0 in P2P |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
st0 in P2MP |
With IPv4 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
With IPv6 address |
No |
No |
No |
No |
No |
No |
No |
No |
|
|
BFD on IPsec VPN |
SRX300SRX320 SRX340SRX345SRX380 |
SRX550 HM |
SRX1500 |
SRX4100SRX4200SRX4600 |
SRX5000 Line with SPC3SRX5000 Line with SPC2 |
SRX5000 Line with Mixed-Mode (SPC3+SPC2) |
vSRX 3.0 |
MX-SPC3 |
|
|---|---|---|---|---|---|---|---|---|---|
|
st0 in P2P |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
|
st0 in P2MP |
With IPv4 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
|
With IPv6 address |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
|
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
junos-ike package is installed in Junos
OS Releases 20.1R2, 20.2R2, 20.3R2, 20.4R1, and later for SRX5000 line with RE3.
As a result iked and ikemd process
runs on the routing engine by default instead of IPsec key management daemon
(kmd).