L2TP LAC Tunneling for Subscribers
LAC Tunnel Selection Overview
When a user logs in to a domain, the PPP client contacts the LAC establish a connection. The LAC has to find a destination in the domain and a tunnel that can reach it. The association between destinations, tunnels, and domains is provided by a tunnel profile either in a domain map in the subscriber’s access profile or in the Tunnel-Group attribute (VSA 26-64) received from a RADIUS server. The RADIUS attribute takes precedence over a profile specified in a domain map. The tunnel profile includes a list of tunnels; each tunnel is associated with a destination IP address and with a tunnel preference level.
L2TP enables you to specify:
-
Up to 31 destinations for a domain.
-
Up to eight levels of tunnel preference. The preference level determines the order in which the LAC attempts to use an existing tunnel (or establish a new one) to a destination in the user’s requested domain.
Note:Zero (0) is the highest level of preference; this is the most-preferred level.
If two tunnels both reach valid destinations within a domain, the LAC first selects the tunnel with the highest preference level. For example, when Tunnel A has a preference level of 1 and Tunnel B has a preference level of 4, the LAC attempts to use Tunnel A first.
-
Up to 31 destinations for a single preference level.
When the LAC determines that a PPP session should be tunneled, it selects a tunnel from the set of tunnels associated with either the PPP user or the PPP user’s domain by a tunnel profile.
Tunnel selection is affected by the following configurations:
-
Failover between preference levels—By default, when a tunnel to a valid destination is not selected within a preference level, the selection process fails over to the next level; that is, the LAC drops down to the next lower level to continue the search for a suitable tunnel. See Selection When Failover Between Preference Levels Is Configured for more information.
-
Failover within a preference level—In this case, the LAC does not limit its attempts to establish a session to only a single tunnel at a preference level. If the attempt fails through the selected tunnel, the selection process fails over within that same level by selecting another suitable tunnel to a valid destination. The LAC continues its connection attempts within the level until no more tunnels to a valid destination are available at that level. Then the LAC drops down to the next lower level to continue the search. See Selection When Failover Within a Preference Level Is Configured for more information.
-
Maximum sessions per tunnel—When the maximum number of sessions allowed per tunnel is configured, the LAC takes that setting into account during the tunnel selection process. The maximum number of sessions per tunnel can be configured by means of the RADIUS Tunnel-Max-Sessions VSA [26-33] or by including the
max-sessionsstatement in a tunnel profile.When a randomly selected tunnel has a current session count equal to its maximum session count, the LAC does not attempt to connect to a destination with that tunnel. Instead, it selects an alternate tunnel from the set of tunnels at that preference level that have valid destinations in the domain. If no such tunnels exist at the current preference level, the LAC drops to the next preference level to make the selection. This process is consistent, regardless of which failover scheme is currently running on the LAC.
When the maximum number of sessions is not configured for a tunnel, then that tunnel has no upper limit on the number of sessions it can support. By default, the maximum sessions value is 0 (zero), which allows unlimited sessions in the tunnel.
-
Weighted load balancing—This balancing method uses a probability-based evaluation of tunnel weight to distribute sessions across tunnels. The LAC still selects tunnels randomly within a preference level, but on average the sessions are distributed across tunnels in relationship to the weight of the tunnels. The weight of a tunnel is determined by the tunnel’s maximum session limit and the maximum session limits of the other tunnels at the same preference level. See Weighted Load Balancing for more information.
-
Destination-equal load balancing—This session-balancing method evaluates tunnels according to the number of sessions to the destination and the number of sessions carried by the tunnel in order to spread the session load equally among all tunnels. The tunnel with a destination that has the lowest session count is determined to have the lightest load. This process operates on tunnels at the highest available preference level. See Destination-Equal Load Balancing for more information.
Take the following information into consideration to understand the tunnel and destination selection process and failover:
-
More than one tunnel may be able to reach a destination, and those tunnels can have the same preference level or different preference levels.
-
The tunnel selected to establish the subscriber session may itself already be established. meaning that it has currently active sessions. Alternatively, the LAC might have to establish a new tunnel to the destination if no tunnel capable of reaching the destination is already established.
-
A valid destination meets the following criteria:
-
It is reachable by a tunnel that has not met its maximum session limit.
-
It has not yet been contacted for the current subscriber login request.
-
It can be either locked or unlocked.
-
-
A locked destination is one for which the destination lockout timer is running. Locked destinations are placed on a lockout list until the timer expires or is cleared (reset to zero). Destinations on the list cannot be contacted to establish a session.
-
An unlocked destination is one for which the destination lockout timer is zero.
-
When the LAC discovers valid destinations that are locked, it places them on the DestinationsLockedNotContacted list, which is different than the lockout list that includes all locked-out destinations. The DestinationsLockedNotContacted list includes only locked destinations that the LAC has not yet attempted to contact for the current, in-progress subscriber login. The DestinationsLockedNotContacted list does not include destinations that the LAC locks out after it has attempted and failed to establish a connection.
-
You can use the
clear services l2tp destination lockoutcommand to manually clear all locked destinations or only locked destinations that match the specified local or remote gateway address. You might use the command if, for example, you want to clear a specific destination so that it gets priority within a preference level. -
The failover behavior that is part of the tunnel selection process applies only when the destination is unreachable for one of the following reasons:
-
The LNS fails to return an SCCRP message in response to the SCCRQ message from the LAC after the maximum number of retransmission attempts.
-
The tunnel is established, but the LNS does not return an ICRP message in response to the ICRQ from the LAC after the maximum number of retransmission attempts.
-
-
This failover behavior does not apply in the following circumstances:
-
The client terminates the connection.
-
The tunnel is established, but the LNS sends a CDN message while the LAC is attempting to establish the session with the LNS, resulting in the failure of the subscriber login attempt.
-
- Selection When Failover Between Preference Levels Is Configured
- Selection When Failover Within a Preference Level Is Configured
- Selection When Distributing the Session Load Across Multiple LNSs
Selection When Failover Between Preference Levels Is Configured
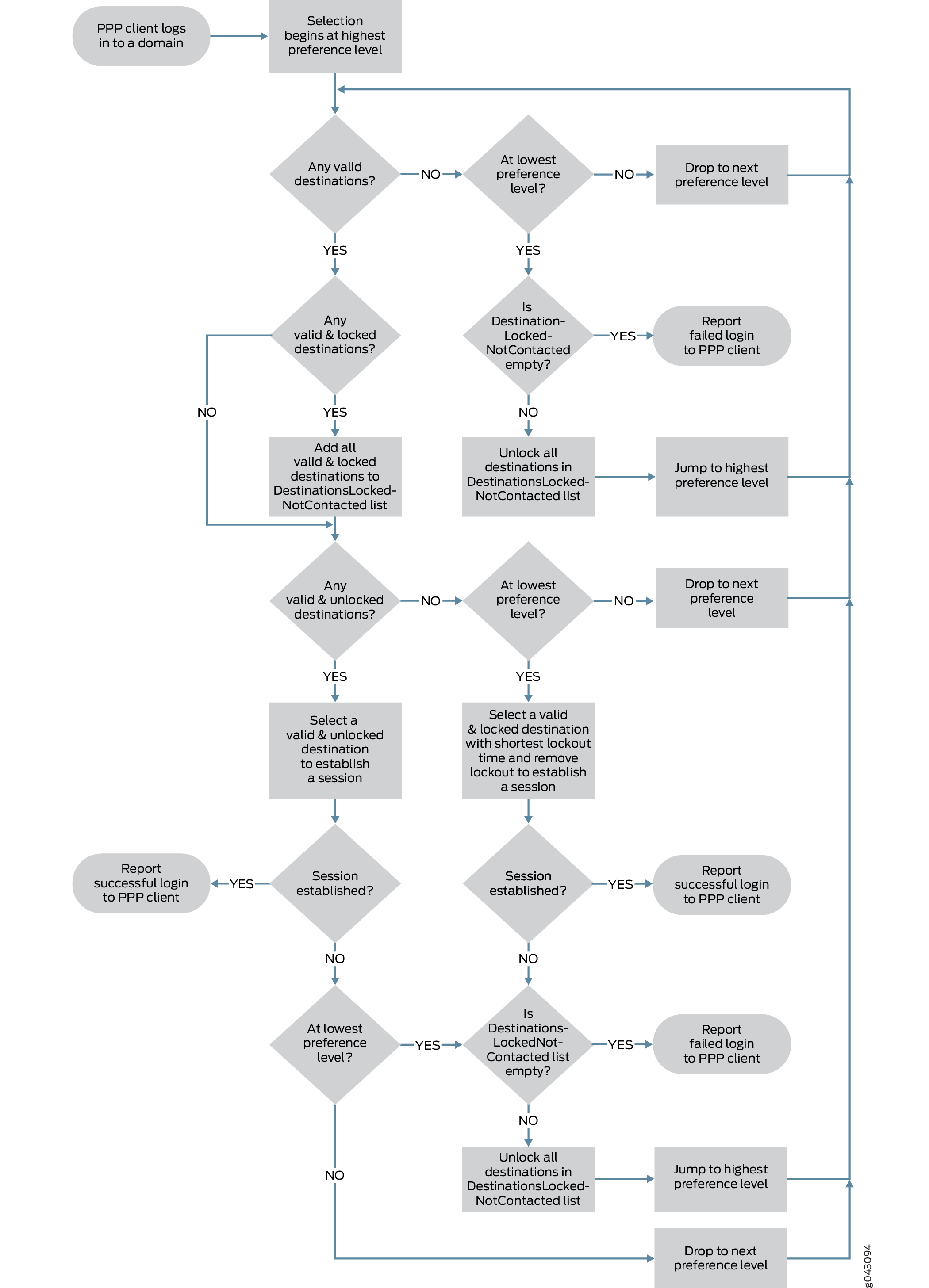
When a user tries to log in to a domain in a default configuration—that is, when failover within a preference level and load balancing are not configured—the LAC searches for valid destinations to the requested domain, starting at the highest tunnel preference level. If no valid destination is found, or the attempt to connect to a destination fails, the LAC drops down to the next lower level to continue searching. The search process is the same for all levels except for the lowest:
-
The search begins by identifying tunnels with valid destinations at the preference level from among all the tunnels specified in the domain’s tunnel profile.
-
All locked, valid destinations are placed on the DestinationsLockedNotContacted list. No attempt is made to contact any of these destinations.
-
From among the unlocked, valid destinations, the LAC selects one at random and attempts to connect through the associated tunnel; if the tunnel has no current sessions, then the LAC must establish the tunnel.
Note:Random selection is the default behavior. The behavior is different when weighted load balancing or destination-equal load balancing is configured. See Selection When Distributing the Session Load Across Multiple LNSs for information about load balancing.
-
If the attempt is successful, the LAC reports the successful login to the PPP client. The LAC also clears all destinations on the DestinationsLockedNotContacted list.
-
If the LAC receives no response, it retries the attempt up to the maximum retry number. If the LAC exhausts the retries without receiving a reply, the attempt is considered unsuccessful and the LAC marks the destination as unreachable by locking out the destination. It places the destination on the lockout list and starts the destination lockout timer.
-
-
What the LAC does next depends on the current preference level.
-
If it is not the lowest preference level, then the LAC drops to the next lower preference level and continues the search process.
-
If it is the lowest preference level and the DestinationsLockedNotContacted list is not empty, then the LAC unlocks all destinations in the DestinationsLockedNotContacted list and jumps back up to the highest preference level and restarts the search process.
-
If it is the lowest preference level and the DestinationsLockedNotContacted list is empty—meaning that all valid destinations have been attempted—then the LAC reports a failed login to the PPP client.
-
-
When the valid destinations at one level are all locked, what the LAC does next depends on the current preference level.
-
If it is not the lowest preference level, then the LAC drops to the next lower preference level and continues the search process.
-
If it is the lowest preference level, the LAC selects the locked, valid destination with the shortest remaining lockout time. It clears the lockout timer and attempts to connect to the destination and establish a session.
-
If the attempt is successful, the LAC reports the successful login to the PPP client.
-
If the attempt fails and the DestinationsLockedNotContacted list is empty—meaning that all valid destinations have been attempted—then the LAC reports a failed login to the PPP client.
-
If the attempt fails and the DestinationsLockedNotContacted list is not empty, then the LAC unlocks all destinations in the DestinationsLockedNotContacted list, jumps back up to the highest preference level, and restarts the search process.
-
-
-
When no valid destinations are present, what the LAC does next depends on the current preference level.
-
If it is not the lowest preference level, then the LAC drops to the next lower preference level and continues the search process.
-
If it is the lowest preference level and the DestinationsLockedNotContacted list is empty—meaning that all valid destinations have been attempted—then the LAC reports a failed login to the PPP client.
-
If it is the lowest preference level and the DestinationsLockedNotContacted list is not empty, then the LAC unlocks all destinations in the DestinationsLockedNotContacted list, jumps back up to the highest preference level, and restarts the process.
-
-
The search and failover process cycles through the levels until either a session is established or all valid destinations have been attempted—no destinations remain on the DestinationsLockedNotContacted list—and the login fails.
Figure 1 illustrates the possible conditions and decision points that determine the selection of a destination and corresponding tunnel for the default case, where failover occurs between tunnel preference levels.
For example, suppose that the tunnel profile includes the following tunnels, each with a valid destination:
-
Preference 0, Tunnel 1, 192.168.10.10
-
Preference 1, Tunnel 2, 192.168.22.22
-
Preference 1, Tunnel 3, 192.168.33.33
-
Preference 2, Tunnel 4, 192.168.44.44
Failover within preference and load balancing are not configured.
When a PPP user tries to connect to the domain, the LAC acts as follows:
-
At the highest preference level, 0, the LAC selects Tunnel 1 because it is the only tunnel in the level with a valid destination. The LAC attempts to reach 192.168.10.10.
-
This connection attempt fails, so the LAC locks out 192.168.10.10. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
The LAC drops (fails over) to the next level, preference level 1, to reach a destination for the domain. The LAC randomly selects between 192.168.22.22 through Tunnel 2 and 192.168.33.33 through Tunnel 3. It selects 192.168.22.22 and attempts to connect through Tunnel 2.
-
The connection attempt to 192.168.22.22 fails, so the LAC locks out 192.168.22.22. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
Note:Even though Tunnel 3 has an unlocked, valid destination, the LAC cannot now select that tunnel to reach 192.168.33.33, because the LAC can make only one attempt to reach a valid destination each time it searches in a level when the failover method is between preference levels.
-
The LAC drops to the final (lowest) level in this example, preference level 2. The LAC selects Tunnel 4 because it is the only tunnel in the level with a valid destination. The LAC attempts to reach 192.168.44.44.
-
The connection attempt to 192.168.44.44 also fails, so the LAC locks out 192.168.44.44. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
Because this is the lowest level, and the DestinationsLockedNotContacted list is empty, the LAC rejects the login request from the PPP client.
Destinations 192.168.10.10, 192.168.22.22, and 192.168.44.44 were locked out, but not added to the DestinationsLockedNotContacted list because the LAC locked them out after attempting to connect. Destination 192.168.33.33 was not contacted, but not added to the DestinationsLockedNotContacted list because it is not locked out.
-
The client tries to log in again and the LAC repeats the tunnel selection process, starting over at preference level 0 to check for an unlocked, valid destination, and cycling through the levels as needed.
-
At preference level 0, 192.168.10.10 is the only valid destination and is still locked out, so the LAC cannot attempt to connect to the destination. The LAC adds 192.168.10.10 to the DestinationsLockedNotContacted list and then drops to preference level 1.
Note:Remember that the destination lockout timer applies globally, so it persists across multiple subscriber logins. The DestinationsLockedNotContacted list applies only to a given subscriber login and does not persist. Even though the LAC contacted 192.168.10.10 for this subscriber, it was during a previous login attempt. In this login attempt, it cannot contact the destination because of the lockout, and consequently places the destination on the DestinationsLockedNotContacted list.
-
At preference level 1, 192.168.22.22 is still locked out, so the LAC adds 192.168.22.22 to the DestinationsLockedNotContacted list. 192.168.33.33 is still available. The LAC attempts to connect to 192.168.33.33 through Tunnel 3.
-
This connection attempt fails, so the LAC locks out 192.168.33.33. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires. The LAC drops to preference level 2.
-
192.168.44.44 is still locked out, so the LAC adds 192.168.44.44 to the DestinationsLockedNotContacted list.
-
This is the lowest preference level, but this time the DestinationsLockedNotContacted list is not empty; it contains 192.168.10.10, 192.168.22.22, and 192.168.44.44. The LAC unlocks all destinations on the DestinationsLockedNotContacted list and then jumps back to the highest preference level.
-
At preference level 0, the LAC attempts to connect to 192.168.10.10 because it was unlocked. The LAC establishes the session and reports the successful login to the PPP client.
Although the LAC does not attempt to contact a destination that is locked out, there is a special case when the LAC has reached the lowest preference level. The level must have more than one valid destination and all of them must be locked out. For example, suppose that the tunnel profile includes the following tunnels, each with a valid destination:
-
Preference 0, Tunnel 1, 192.168.10.10
-
Preference 1, Tunnel 2, 192.168.22.22. The destination is locked out with the lockout timer currently at 245 seconds.
-
Preference 1, Tunnel 3, 192.168.33.33. The destination is locked out with the lockout timer currently at 180 seconds.
Failover within preference and load balancing are not configured.
When a PPP user tries to connect to the domain, the LAC acts as follows:
-
At the highest preference level, 0, the LAC selects Tunnel 1 because it is the only tunnel in the level with a valid destination. The LAC attempts to reach 192.168.10.10.
-
This connection attempt fails, so the LAC locks out 192.168.10.10. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
The LAC drops to the next level, preference level 1, to reach a destination for the domain. Both valid destinations at this level, 192.168.22.22 and 192.168.33.33, are locked out.
-
The LAC adds both destinations to the DestinationsLockedNotContacted list.
-
Because this is the lowest preference level, the LAC determines which destination has a shorter remaining lockout time. It selects 192.168.33.33 because it has a shorter remaining lockout time (180 seconds) than 192.168.22.22 (245 seconds). The LAC unlocks 192.168.33.33 and attempts to connect through Tunnel 3. As a consequence, the LAC also removes 192.168.33.33 from the DestinationsLockedNotContacted list.
-
The connection attempt is successful and a session is established to 192.168.33.33. The LAC reports a successful login to the PPP client.
Selection When Failover Within a Preference Level Is Configured
When you configure failover within a preference level, the destination and tunnel selection process is the same as for the default configuration, with one exception: the LAC is not limited to only one connection attempt at a preference level.
When the LAC tries to connect to an unlocked, valid destination and is unsuccessful, it locks out that destination but does not immediately drop down to the next lower level. Instead, if another unlocked, valid destination is available at the same preference level, the LAC attempts to connect to that destination.
If the LAC does not connect, then it continues to try to reach a destination within that preference level until no more unlocked, valid destinations remain to be attempted. At that point the LAC drops down to search at the next lower preference level. At each level, the LAC searches for and attempts to connect to a valid destination until no unlocked, valid destinations are available.
If the LAC drops down to the lowest preference level and finds no unlocked, valid destinations, the behavior depends on the DestinationsLockedNotContacted list:
-
If the DestinationsLockedNotContacted list is not empty, then the LAC unlocks all destinations in the DestinationsLockedNotContacted list and jumps back up to the highest preference level and restarts the search process.
-
If the DestinationsLockedNotContacted is empty—meaning that all valid destinations have been attempted—then the LAC reports a failed login to the PPP client.
For example, suppose that the tunnel profile specifies the following tunnels and destinations. Load balancing is not configured. All destinations are valid; all are unlocked except 192.168.3.3. The preference levels for the tunnels are assigned as follows:
-
Preference 0, Tunnel 1, 192.168.1.1, unlocked
-
Preference 0, Tunnel 2, 192.168.2.2, unlocked
-
Preference 0, Tunnel 3, 192.168.3.3, lockout timer 100 seconds
-
Preference 1, Tunnel 4, 192.168.4.4, unlocked
-
Preference 1, Tunnel 5, 192.168.5.5, unlocked
In this example, when a PPP user tries to connect to the domain, the LAC acts as follows:
-
The LAC randomly selects between the two unlocked, valid destinations at preference level 0, 192.168.1.1 through Tunnel 1 and 192.168.2.2 through Tunnel 2. It chooses 192.168.2.2 and attempts to connect through Tunnel 2.
-
The connection attempt to 192.168.2.2 fails, so the LAC locks out 192.168.2.2. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
The LAC then attempts to connect to 192.168.1.1 through Tunnel 1 at preference level 0.
-
The connection attempt to 192.168.1.1 fails, so the LAC locks out 192.168.1.1. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
192.168.3.3 through Tunnel 3 is the only remaining valid destination at preference level 0, but it is locked. The LAC adds 192.168.3.3 to the DestinationsLockedNotContacted list. The LAC did not add 192.168.1.1 and 192.168.2.2 to the DestinationsLockedNotContacted list, because it locked them out after attempting to contact them.
-
Because level 0 has no more unlocked, valid destinations, the LAC drops to the next level, preference level 1, to reach a destination for the domain.
-
At preference level 1, the LAC randomly selects 192.168.4.4 and attempts to connect through Tunnel 4.
-
The connection attempt to 192.168.4.4 fails, so the LAC locks out 192.168.4.4. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
The LAC then attempts to connect to 192.168.5.5 through Tunnel 5 at preference level 1.
-
The connection attempt to 192.168.5.5 fails, so the LAC locks out 192.168.5.5. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires. Level 1 has no more unlocked, valid destinations. Because the DestinationsLockedNotContacted list is not empty, the LAC unlocks all the destinations on the list—in this case, 192.168.3.3—and jumps back up to the highest preference level, 0.
-
192.168.3.3 is now the only unlocked destination at preference level 0, so the LAC attempts to connect to it through Tunnel 3.
-
The connection attempt to 192.168.3.3 fails, so the LAC locks out 192.168.3.3. It is not considered again during this login attempt, and cannot be considered for any login attempt until the destination lockout timer expires.
-
Because level 0 has no more unlocked, valid destinations, the LAC drops to the next level, preference level 1.
-
Preference level 1 has no unlocked, valid destinations. The DestinationsLockedNotContacted is empty because the LAC has contacted all valid destinations at both preference levels. The LAC rejects the login request from the PPP client.
Selection When Distributing the Session Load Across Multiple LNSs
Multiple tunnel profiles can be configured on the LAC; some tunnels may share destinations. When the LAC tunnels the session for a PPP subscriber to the LNS, a tunnel has to be selected for the subscriber session. The tunnel selection process chooses a tunnel with the highest preference that has a reachable destination. By default, the LAC selects a tunnel at random from among multiple tunnels that meet the same criteria. Alternatively, you can configure load balancing to enable different selection choices. Both load-balancing methods affect which tunnels and destinations the LAC selects, but the selection and failover process otherwise remains the same.
Weighted load balancing and destination-equal load balancing are mutually exclusive. You can enable only one or the other.
Weighted Load Balancing
Weighted load balancing evaluates tunnels according to their weight. The weight of a tunnel is determined by the tunnel’s maximum session limit and the maximum session limits of the other tunnels at the same preference level. The tunnel with the highest maximum session limit has the highest weight in that preference level. The tunnel with the next-highest maximum session limit has the next-highest weight, and so on. The tunnel with the lowest maximum session limit has the lowest weight.
Tunnel selection and session distribution are probability based; the load is not strictly distributed according to weight.
When you configure weighted load balancing, the LAC still selects tunnels randomly within a preference level, but on average the sessions are distributed across tunnels in relationship to the weight of the tunnels.
With weighted load balancing, the LAC generates a random number within a range equal to the aggregate total of all session limits for all tunnels in the preference level. It associates part of the range—a pool of numbers—with each tunnel proportional to the tunnel weight. A tunnel with a higher weight is associated with a greater portion of the range—a larger pool—than a tunnel with a lower weight. A tunnel is selected when the random number is in its associated pool of numbers. The random number is more likely, on average, to be in a larger pool, so a tunnel with a higher weight (larger pool) is more likely to be selected than a tunnel with a lower weight (smaller pool).
For example, consider a preference level that has only two tunnels, 1 and 2. Tunnel 1 has a maximum limit of 1000 sessions and Tunnel 2 has a limit of 2000 sessions, resulting in an aggregate total of 3000 sessions. The LAC generates a random number from a pool of 3000 in the range from 0 through 2999. A pool of 1000 numbers, the portion of the range from 0 through 999, is associated with Tunnel 1. A pool of 2000 numbers, the portion of the range from 1000 through 2999, is associated with Tunnel 2.
-
When the generated number is less than 1000, then Tunnel 1 is selected, even though it has a lower weight (1000) than Tunnel 2 (2000).
-
When the generated number is 1000 or larger, then Tunnel 2 is selected.
Because the pool of possible generated numbers for Tunnel 2 (2000) is twice that for Tunnel 1 (1000), Tunnel 2, on average, is selected twice as often as Tunnel 1.
Destination-Equal Load Balancing
Destination-equal load balancing evaluates tunnels according to the number of sessions to the destination and the number of sessions carried by the tunnel in order to spread the session load equally among all tunnels. The tunnel with a destination that has the lowest session count is considered to have the lightest load. This process operates on tunnels at the highest available preference level and uses the following guidelines:
-
When each tunnel goes to a separate destination and only one destination has the lowest session count among all destinations, the LAC selects the tunnel to that destination.
-
When each tunnel goes to a separate destination and more than one destination has the same lowest session count, the LAC selects a tunnel at random from among the tunnels to these destinations.
-
When more than one tunnel goes to the same destination and that destination has the lowest destination session count, the LAC selects from among these tunnels the one that has the lowest total number of tunnel sessions. If the tunnel session count is the same for all these tunnels, then the LAC selects one of them at random.
Consider the following scenarios to better understand tunnel selection behavior when destination-equal load balancing is enabled.
In Scenario 1, every tunnel has a different valid destination and only the destination session count is evaluated:
-
Tunnel 1, preference level 1, 192.168.1.1, destination session count = 200
-
Tunnel 2, preference level 1, 192.168.2.2, destination session count = 50
-
Tunnel 3, preference level 1, 192.168.3.3, destination session count = 300
-
Tunnel 4, preference level 1, 192.168.4.4, destination session count = 100
When the first PPP user tries to connect to the domain, the LAC selects Tunnel 2, because it is at the highest preference level, 1, and has the valid destination, B, with the lowest session count, 50.
When additional PPP users try to connect to the domain, the LAC acts as follows:
-
Tunnel 2 continues to be selected until the session count for 192.168.2.2 equals 100, matching the next lowest session count, 192.168.4.4’s in Tunnel 4.
-
When the next subscriber logs in, the LAC randomly selects between Tunnel 2 and Tunnel 4, because their destinations have the same session count, and it is lower than that for the other destinations.
-
Whichever tunnel is selected from this pair, the session count for its destination is now 101. The other tunnel is selected when the next subscriber logs in, because it has the lower destination session count of 100. This raises its destination session count to 101, matching the other tunnel.
-
As subscribers continue to log in, the LAC repeats this process, randomly selecting between Tunnel 2 and Tunnel 4 when their session counts match and then selecting the other tunnel with the next subscriber, until their destination session counts both reach 200, matching Tunnel 1.
-
When the next subscriber logs in, the LAC now randomly selects among Tunnel 1, Tunnel 2, and Tunnel 4, because 192.168.1.1, 192.168.2.2, 192.168.3.3 all have the same session count of 200. The destination session count is raised for the selected tunnel to 201, so for the next subscriber, the LAC randomly selects between the other two tunnels. Now two tunnels have a destination session count of 201, so the LAC selects the remaining tunnel for the next subscriber.
-
As subscribers continue to log in, the LAC repeats this process, randomly selecting among Tunnel 1, Tunnel 2, and Tunnel 4 when their session counts match, randomly selecting between the remaining pair for the next subscriber, and then selecting the remaining tunnel, so the destination session counts for these three tunnels match again. This pattern continues until the destination session count for all three tunnels reaches 300, matching Tunnel 3.
-
Now the destinations for all four tunnels have the same session count. Because there are only four tunnels, the final pattern is established. The LAC first randomly selects among all four tunnels, then the remaining three, then the remaining pair, and finally selects the last tunnel. When the destination session counts are all the same, the LAC starts this pattern again.
In Scenario 2, two tunnels share the same valid destination. The tunnel session count and the destination session count are both evaluated:
-
Tunnel 1, preference level 1, tunnel session count = 120, 192.168.1.1, destination session count = 200
-
Tunnel 2, preference level 1, tunnel session count = 80, 192.168.1.1, destination session count = 200
-
Tunnel 3, preference level 1, 192.168.2.2, destination session count = 300
-
Tunnel 4, preference level 2, 192.168.3.3, destination session count = 100
When the first PPP user tries to connect to the domain, the LAC first selects between destinations. The tunnels for both 192.168.1.1 and 192.168.2.2 are at preference level 1. The LAC selects 192.168.1.1, because it has a lower session count (200) than 192.168.2.2 (300). The LAC then has to choose between Tunnel 1 and Tunnel 2 because both go to 192.168.1.1. The LAC evaluates the tunnel session count. Tunnel 2 has a lower count (80) than Tunnel 1 (120), so the LAC selects Tunnel 2 for the first subscriber.
When additional PPP users try to connect to the domain, the LAC acts as follows:
-
Tunnel 2 continues to be selected until its tunnel session count increases to 120, matching Tunnel 1.
-
When the next subscriber logs in, the LAC randomly selects between Tunnel 1 and Tunnel 2, because they have the same tunnel session count. The tunnel session count of the selected tunnel is raised to 121.
-
When the next subscriber logs in, the LAC selects the other tunnel to 192.168.1.1, because it has a lower tunnel session count. From this point, the LAC continues to alternate, first making a random selection between Tunnels 1 and 2 and then selecting the other tunnel, until the destination session count rises to 300, matching the session count for 192.168.2.2 in Tunnel 3. (At this point, the tunnel session count is 150 for both Tunnel 1 and Tunnel 2.)
-
For the next subscriber, the LAC randomly selects among Tunnels 1, 2, and 3.
-
If the LAC selects either Tunnel 1 or Tunnel 2, the 192.168.1.1 session count rises to 301. Consequently the LAC selects Tunnel 3 for the next subscriber because the 192.168.2.2 session count is still 300. At this point, both destinations have the same session count again.
-
If the LAC selects Tunnel 3, the 192.168.2.2 session count rises to 301. For the next subscriber, the LAC randomly selects between Tunnel 1 and Tunnel 2 because they both go to 192.168.1.1. Whichever one the LAC selects, the 192.168.1.1 session count rises to 301. At this point, both destinations have the same session count again.
Note:The tunnel session count for Tunnels 1 and 2 is no longer evaluated; the LAC only considers the destination session count for 192.168.1.1 and 192.168.2.2.
This pattern continues for all subsequent subscribers.
-
In Scenario 3, each tunnel has a different valid destination and only the destination session count is evaluated:
-
Tunnel 1, preference level 1, 192.168.1.1, destination session count = 100
-
Tunnel 2, preference level 1, 192.168.2.2, destination session count = 100
-
Tunnel 3, preference level 1, 192.168.3.3, destination session count = 100
-
Tunnel 4, preference level 1, 192.168.4.4, destination session count = 100
When the first PPP user tries to connect to the domain, the LAC determines that the destination session count is the same for all destinations for all four tunnels at the preference level. Consequently, the LAC selects randomly among the four tunnels.
Suppose the LAC selects Tunnel 1 for the first subscriber.
When additional PPP users try to connect to the domain, the LAC acts as follows:
-
The LAC selects randomly among Tunnels 2, 3, and 4, because Destinations 192.168.2.2, 192.168.3.3, and 192.168.4.4 all have the same session count, 100, which is lower than the current session count for 192.168.1.1, 101.
-
Suppose the LAC selects Tunnel 2. For the next subscriber, the LAC randomly selects between Tunnels 3 and 4, because 192.168.3.3 and 192.168.4.4 all have the same session count, 100, which is lower than the current session count of 101 for 192.168.1.1 and 192.168.2.2.
-
Suppose the LAC selects Tunnel 3. For the next subscriber, the LAC selects Tunnel 4, because 192.168.4.4 has a session count of 100, and all the other destinations have a count of 101.
-
Now the destinations for all four tunnels have the same session count. Because there are only four tunnels, the final pattern is established. As subscribers continue to log in, the LAC first randomly selects among all four tunnels, then the remaining three, then the remaining pair, and finally selects the last tunnel. When the destination session counts are all the same, the LAC starts this pattern again.
In Scenario 4, the LAC evaluates both destination session limits and tunnel maximum session limits:
-
Tunnel 1, preference level 1, 192.168.1.1, destination session count = 30, tunnel maximum session limit = 200
-
Tunnel 2, preference level 1, 192.168.2.2, destination session count = 40, tunnel maximum session limit = 200
-
Tunnel 3, preference level 1, 192.168.3.3, destination session count = 300, tunnel maximum session limit = 1000
-
Tunnel 4, preference level 2, 192.168.4.4, destination session count = 100
When the first PPP user tries to connect to the domain, the LAC selects Tunnel 1, because 192.168.1.1 has the lowest session count in the preference level.
When additional PPP users try to connect to the domain, the LAC acts as follows:
-
The LAC continues to select Tunnel 1 until the destination session count for 192.168.1.1 equals 40, matching the count for 192.168.2.2 in Tunnel 2.
-
When the next subscriber logs in, the LAC randomly selects between Tunnel 1 and Tunnel 2, because their destinations have the same session count, and it is lower than that for Tunnel 3 (300).
-
Whichever tunnel is selected from this pair, the session count for its destination is now 41. The other tunnel is selected when the next subscriber logs in, because it has the lower destination session count of 40. This raises its destination session count to 41, matching the other tunnel.
-
As subscribers continue to log in, the LAC repeats this process, randomly selecting between Tunnel 1 and Tunnel 2 when their session counts match and then selecting the other tunnel with the next subscriber, until their destination session counts both reach 200, matching their tunnel maximum session limit of 200. Because both tunnels have reached their maximum session limit, they are not available for selection.
-
As subscribers continue to log in, the LAC selects the remaining tunnel in the preference level, Tunnel 3, until the session count for its destination reaches the maximum session limit for the tunnel, 1000.
-
When the next subscriber logs in, the LAC drops to the next preference level and selects Tunnel 4, because it is the only tunnel at this level.
-
As subscribers continue to log in, the LAC continues to select Tunnel 4, because no maximum session limit is configured for this tunnel. The LAC can subsequently select a tunnel in the higher preference level only when a session is terminated for one of the tunnels at that level, dropping it’s session count below the maximum limit.
In Scenario 5, one of the destinations is locked:
-
Tunnel 1, preference level 1, 192.168.1.1, destination session count = 100, destination locked out
-
Tunnel 2, preference level 1, 192.168.2.2, destination session count = 200
-
Tunnel 3, preference level 1, 192.168.3.3, destination session count = 250
When the first PPP user tries to connect to the domain, the LAC cannot select Tunnel 1, even though its destination has the lowest session count, because the tunnel is in the destination lockout state. Tunnel 1 cannot be considered until it is out of the locked state. The LAC selects Tunnel 2 because the session count for 192.168.2.2 is lower than for 192.168.3.3.
When additional PPP users try to connect to the domain, what happens next depends on when 192.168.1.1 emerges from the lockout state. For as long as 192.168.1.1 is locked out, the LAC makes the selections as follows:
-
The LAC continues to select Tunnel 2 until the session count for 192.168.2.2 equals 250, matching the count for 192.168.3.3 in Tunnel 3.
-
When the next subscriber logs in, the LAC randomly selects between Tunnel 2 and Tunnel 3, because their destinations have the same session count, 250.
-
Whichever tunnel is selected from this pair, the session count for its destination is now 251. The other tunnel is selected when the next subscriber logs in, because it has the lower destination session count of 250. This raises its destination session count to 251, matching the other tunnel.
-
As subscribers continue to log in, the LAC repeats this process, randomly selecting between Tunnel 2 and Tunnel 3 when their session counts match and then selecting the other tunnel with the next subscriber.
Whenever 192.168.1.1 emerges from the lockout state, the LAC selects Tunnel 1 for the next subscriber because 192.168.1.1 has the lowest session count. The LAC continues to do so until the session count for 192.168.1.1 matches the current session count for either of the other destinations. From that point forward, the LAC alternates making a random selection between tunnels with matching destination session counts and then subsequently selecting the tunnel with the lowest count.
Whenever 192.168.1.1 emerges from the lockout state,
-
The LAC selects Tunnel 1 for the next subscriber because 192.168.1.1 has the lowest session count.
-
The LAC continues to select Tunnel 1 until the session count for 192.168.1.1 matches the current session count for either of the other destinations.
-
From that point forward, the LAC alternates making a random selection between tunnels with matching destination session counts and then subsequently selecting the tunnel with the lowest count.
L2TP Session Limits Overview
When an L2TP session request is initiated, the LNS or LAC checks the number of current active sessions against the maximum number of sessions allowed for the chassis, tunnels, a tunnel group, a client (requesting host device), or a group of clients. New session requests are rejected when the configured session limit is reached.
When a session is requested, the LNS checks for session limits in the following order:
chassis > tunnel > tunnel group > session-limit group > client
At each level, the LNS determines whether the current session count is less than the configured limit. When that is true or when no limit is configured, the check passes and the LNS proceeds to check the next level. If at any level the current session count is equal to the configured limit, then the LNS rejects the session request and does not check any other level. Otherwise, the session can be established.
When a session request is rejected for an existing tunnel, a Call-Disconnect-Notify (CDN) message with a result code and error code both set to 4 is returned in response to the incoming-call request (ICRQ). When the rejected request is for a new tunnel, the tunnel is established but the session fails to come up, causing the tunnel to come down because it has no sessions.
The LAC performs the same check, but only for the chassis and tunnel levels. The LAC rejects requests by returning a PPP terminate message to the client.
You can configure session limits for the chassis, all tunnels, a tunnel group, a group of clients, or an individual client. The scenarios that follow describe what happens for different configurations of session limits.
- Scenario 1: Chassis Limit
- Scenario 2: Tunnel Limit
- Scenario 3: Tunnel Group Limit
- Scenario 4: Session-Limit Group Limit
- Scenario 5: Individual Client Limit
Scenario 1: Chassis Limit
In Table 1, the current L2TP session count is 10,000 and the session limit is configured as 10,000 at every level. When a new session is requested, the first check at the chassis level fails, because the current session count matches the configured limit. No further checks are performed at the other levels and the session request is rejected. No new sessions are allowed at any level until the current session count drops below 10,000.
Level |
Configured Session Limit |
Current Session Count Displayed by |
Session Limit Check Result |
|---|---|---|---|
Chassis |
10,000 |
10,000 |
Fail |
Tunnel A |
10,000 |
10,000 |
– |
Tunnel group B |
10,000 |
10,000 |
– |
Session-limit group |
10,000 |
10,000 |
– |
Client |
10,000 |
10,000 |
– |
Scenario 2: Tunnel Limit
In Table 2, the current L2TP session count is 2000. When a new session is requested, the first check at the chassis level passes because the configured limit allows up to 10,000 sessions on the chassis, but only 2000 sessions are currently active. The next check, at the tunnel level, fails, because the current session count matches the configured limit tunnel limit of 2000 for tunnel A.
No further checks are performed at the other levels and the session request is rejected.
Level |
Configured Session Limit |
Current Session Count Displayed by |
Session Limit Check Result |
|---|---|---|---|
Chassis |
10,000 |
2000 |
Pass |
Tunnel A |
2000 |
2000 |
Fail |
Tunnel group B |
10,000 |
2000 |
– |
Session-limit group |
6000 |
2000 |
– |
Client |
6000 |
2000 |
– |
No new sessions are allowed on tunnel A until its current session count drops below 2000 and the session check can pass. If that happens, then the other level checks pass in this scenario because their configured limits are greater than their current counts.
The session limit of 2000 applies to all tunnels; that is, each active tunnel has an independent limit of 2000 sessions. The failure of one tunnel has no effect on other tunnels. A session request on any other tunnel passes, as long as the current session count for that tunnel is less than 2000.
Scenario 3: Tunnel Group Limit
In Table 3, the current L2TP session count is 2000. When a new session is requested, the first check at the chassis level passes because the configured limit allows up to 10,000 sessions on the chassis, but only 2000 sessions are currently active. The second check, at the tunnel level, also passes for the same reason. The next check, at the tunnel group level for tunnel group B, fails, because the current session count for tunnel group B matches the configured limit tunnel group limit of 2000.
No further checks are performed at the other levels and the session request is rejected.
Level |
Configured Session Limit |
Current Session Count Displayed by |
Session Limit Check Result |
|---|---|---|---|
Chassis |
10,000 |
2000 |
Pass |
Tunnel A |
10,000 |
2000 |
Pass |
Tunnel group B |
2000 |
2000 |
Fail |
Session-limit group |
6000 |
2000 |
– |
Client |
6000 |
2000 |
– |
No new sessions are allowed on tunnel group B until its current session count drops below 2000 and the session check can pass. If that happens, then the other level checks can pass because their configured limits are greater than their current counts.
For tunnel groups, the session limit is configured on a per-group basis; that is, you cannot specify a single limit that applies to all tunnel groups. The failure of any tunnel group has no effect on other tunnel groups. In this scenario, a session request on any other tunnel group passes, if the current session count for that group is less than its configured session limit.
Scenario 4: Session-Limit Group Limit
In Table 4, the current L2TP session count is 6000. When a new session is requested, the check passes for the chassis, tunnel, and tunnel group because the configured limit for each allows up to 10,000 sessions, but only 6000 sessions are currently active. The check at the session-limit group fails, because the current session count for session-limit group slg1 matches the configured limit of 6000.
No further checks are performed at the remaining level and the session request is rejected.
Level |
Configured Session Limit |
Current Session Count Displayed by |
Session Limit Check Result |
|---|---|---|---|
Chassis |
10,000 |
6000 |
Pass |
Tunnel A |
10,000 |
6000 |
Pass |
Tunnel group B |
10,000 |
6000 |
Pass |
Session-Limit group slg1 |
6000 |
6000 |
Fail |
Client |
8000 |
2000 |
– |
No new sessions are allowed for any clients in session-limit group slg1 until the group’s current session count drops below 6000 and the session check can pass. If that happens, then the remaining level check can pass because its configured limit is greater than its current count.
You can reconfigure a session-limit group by removing or adding clients without affecting any current sessions. The reconfiguration does affect the number of sessions available to be established for the client group.
If you remove a client, then the number of new sessions that can be established increases by the number of that client’s current sessions.
If you add a client, then the number of new sessions that can be established is reduced by the number of that client’s current sessions. The new total of current sessions for existing clients plus the new client can exceed the configured limit for the session-limit group. In this case, no sessions are dropped, but no new sessions can be established until the session count drops below the configured group limit.
To explore this further, consider the following sequence of events:
The session-limit group slg1 has two clients, ent1-serviceA with a current session count of 3500 and ent1-serviceB with a current session count of 0. Because group slg1 has a limit of 6000, no more than 2500 sessions can be added for these clients:
6000 - 3500 = 2500
Then 1000 sessions are logged in for client ent1-service B. Now no more than 1500 sessions can be added for these clients:
6000 - (3500 + 1000) = 1500
Next, suppose you remove client ent1-serviceA from the session-limit group. The group session capacity increases to 5000 sessions:
6000 - 1000 = 5000
Finally, you add a new client, ent1-serviceC, to the session-limit group. This new client currently has 8000 active sessions. In this case, the session-limit group now has 9000 sessions:
1000 + 8000 = 9000
No sessions are dropped even though the maximum session limit for the group, 6000, is exceeded. No new sessions can be added until the session count drops from 9000 to below 6000.
Scenario 5: Individual Client Limit
In Table 5, the session check passes for the chassis, tunnel, and tunnel group because their configured limits are greater than their current session counts. The client, ent1-serviceA, does not belong to a session-limit-group. The limit check fails for the client because its current session count matches the configured limit of 6000.
Level |
Configured Session Limit |
Current Session Count Displayed by |
Session Limit Check Result |
|---|---|---|---|
Chassis |
10,000 |
6000 |
Pass |
Tunnel A |
10,000 |
6000 |
Pass |
Tunnel group B |
8000 |
6000 |
Pass |
Client ent1-serviceA |
6000 |
6000 |
Fail |
No new sessions are allowed for this client until its current session count drops below 6000 and the session check can pass. The failure of any independent client has no effect on other clients. In this scenario, a session request for any other independent client passes, if the current session count for that client is less than its configured session limit.
The session limit that you set for an individual client—one that is not part of a session-limit group—applies on a per-tunnel-group basis. Multiple LACs with the same source hostname but different source IP addresses are treated as the same client.
Suppose you have three LACs, A, B, and C. All three have the same source hostname, ce-lac. LAC A and LAC B establish sessions with an LNS through the gateway address associated with tunnel group 1. LAC C establishes sessions through a different gateway associated with tunnel group 2. Because the LACs have the same hostname, the client configuration is the same for all three. However, the client session limit applies differently to the LACs because of the tunnel groups.
Suppose the client session limit is 100. Because LAC A and LAC B both create sessions in tunnel group 1, they must share the client limit. That means that the total number of sessions allowed for LAC A and LAC B combined is 100.
LAC C creates sessions in a different tunnel group, 2. Because the client session limit applies per tunnel group, then LAC C is allowed 100 sessions, regardless of how many sessions LAC A and LAC B have already established.
Limiting the Number of L2TP Sessions Allowed by the LAC or LNS
You can place a limit on the maximum number of L2TP sessions allowed for the chassis, all tunnels, a tunnel group, a group of clients, an individual client, or an individual service interface or aggregated service interface. New session requests are rejected by the LNS or LAC when the configured session limit is reached. Session requests are also rejected when the maximum chassis limit has been reached, even when a configured limit is not exceeded. Configurable session limits provide fine-grained control of the number of sessions that a customer can have while connected over LACs in multiple locations.
You cannot set the limit to be more than the default maximum limit for the chassis.
To limit the number of sessions allowed on a chassis (LAC or LNS):
Configure the maximum number of sessions.
[edit services l2tp] user@host# set maximum-sessions number
To limit the number of sessions per tunnel for all tunnels (LAC or LNS):
Configure the maximum number of sessions.
[edit services l2tp tunnel ] user@host# set maximum-sessions number
You cannot set the limit to be more than 65,535 sessions.
To limit the number of sessions for all tunnels in a specific tunnel group (LNS):
Configure the maximum number of sessions.
[edit services l2tp tunnel-group tunnel-group-name] user@host# set maximum-sessions number
To limit the number of sessions that are allowed on an individual service interface:
Configure the maximum number of sessions.
[edit interfaces si-slot/pic/port] user@host# set l2tp-maximum-session number
To limit the number of sessions that are allowed on an individual aggregated service interface:
Configure the maximum number of sessions.
[edit interfaces asinumber] user@host# set l2tp-maximum-session number
Note:The configuration applies to all member interfaces; the limit cannot be configured for individual member interfaces of the aggregated service interface.
To limit the number of sessions for a group of clients (LNS):
To limit the number of sessions for a client that is not a member of a session-limit group (LNS):
Configure the maximum number of sessions.
[edit access profile profile-name client client-name] user@host# set maximum-sessions number
Configuring the session limit at any level to be less than the number of sessions that currently exist at that level has no effect on existing sessions. The new limit applies only if the number of sessions drops below the new limit.
You can use the show services l2tp summary extensive command to display the configured sessions limit for a tunnel:
user@host> show services l2tp tunnel extensive
...
Max sessions: 32000, Window size: 4, Hello interval: 60
...The displayed limit for configured sessions is set to the lowest of the following configured session values:
Global (chassis)—(LAC and LNS)
set services l2tp tunnel maximum-sessionsnumberTunnel profile (individual tunnel)—(LAC and LNS)
set access tunnel-profile profile-name tunnel tunnel-idmax-sessionsnumber]RADIUS—(LAC and LNS) Value of VSA 26–33, Tunnel-Max-Sessions
Host profile—(LNS only)
set access profile profile-name client client-name l2tp maximum-sessions-per-tunnel
The configured values determine the field value starting in the following Junos OS releases: 19.2R3, 19.3R3, 19.4R3, 20.1R2, 20.2R2, and 20.3R1. In earlier releases, the field displays the host profile value for the LNS, but it displays a fixed value of 512,000 for the LAC.
After a GRES, a unified ISSU, or a restart of the jl2tpd process, the value of this field is accurate only after a new session comes up on the tunnel. Until that happens, the field shows a value of 65,535 instead of the configured value.
Suppose you have two tunnels, tunnel A and tunnel B. A GRES takes place, and the field for each tunnel shows 65,535. When a new session comes up on tunnel B, the value for that tunnel updates to the configured value. For tunnel A, the field continues to show 65,535 until that tunnel gets a new session.
Setting the Format for the Tunnel Name
By default, the name of a tunnel corresponds to the Tunnel-Assignment-Id
[82] returned by the AAA server. You can optionally configure the
LAC to use more elements in the construction of a tunnel name by including
the assignment-id-format client-server-id statement at
the [edit services l2tp tunnel] hierarchy level. This format
uses three attributes: Tunnel-Client-Auth-Id [90], Tunnel-Server-Endpoint
[67], and Tunnel-Assignment-Id [82]. These attributes correspond,
respectively, to the values configured in the tunnel profile for the
LAC (source gateway) name, the tunnel endpoint (remote gateway) address
on the LNS, and the tunnel ID.
A consequence of the client-server-id format is that
the LAC automatically creates a new tunnel when the AAA server returns
a different Tunnel-Client-Auth-Id than previously returned.
Before you downgrade to a Junos OS Release that does not
support this statement, we recommend that you explicitly unconfigure
the feature by including the no assignment-id-format assignment-id statement at the [edit services l2tp tunnel] hierarchy
level.
To change how the tunnel name is formatted:
Configure the format.
[edit services l2tp tunnel] user@host# set assignment-id-format client-server-id
Configuring a Tunnel Profile for Subscriber Access
The tunnel profile specifies a set of attributes to characterize the tunnel. The profile can be applied by a domain map or automatically when the tunnel is created.
RADIUS attributes and VSAs can override the values you configured by a tunnel profile in a domain map. In the absence of a domain map, RADIUS can supply all the characteristics of a tunnel. The steps in the following procedure list the corresponding standard RADIUS attribute or VSA that you can configure on your RADIUS server to modify or configure the tunnel profile.
RADIUS-supplied attributes are associated with a tunnel by a tag carried in the attribute, which matches the tunnel identifier. A tag of 0 indicates the tag is not used. If L2TP receives a RADIUS attribute with a tag of 0, the attribute cannot be merged with the tunnel profile configuration corresponding to the subscriber domain because a tunnel profile cannot provide a tunnel tag (tunnel identifier) of 0. Only tags in the range of 1 through 31 are supported.
To configure a tunnel definition for a tunnel profile:
The following example shows a complete configuration for a tunnel profile:
tunnel-profile marketing {
tunnel 1 {
preference 5;
remote-gateway {
address 198.51.100.4;
gateway-name work;
}
source-gateway {
address 192.0.2.10;
gateway-name local;
}
secret $ABC123;
logical-system bos-metro-5;
routing-instance rox-12-32;
medium ipv4;
type l2tp;
identification tunnel_to_work;
max-sessions 32;
nas-port-method cisco avp;
}
}
Configuring the L2TP LAC Tunnel Selection Parameters
When the LAC determines that a PPP session should be tunneled, it selects a tunnel from the set of tunnels associated with either the PPP user or the PPP user’s domain. You can configure how a tunnel is selected and whether certain information is sent by the LAC to the LNS.
To configure tunnel selection parameters:
Configuring LAC Tunnel Selection Failover Within a Preference Level
You can configure how LAC tunnel selection continues in the event of a failure to connect. By default, when the router is unable to connect to a destination at a given preference level, it attempts to connect at the next lower level. You can specify that the router instead attempt to connect to another destination at the same level as the failed attempt.
If all destinations at a preference level are marked as unreachable, the router does not attempt to connect to a destination at that level. It drops to the next lower preference level to select a destination.
If all destinations at all preference levels are marked as unreachable, the router chooses the destination that failed first and tries to make a connection. If the connection fails, the router rejects the PPP user session without attempting to contact the remote router.
For example, suppose there are four tunnels for a domain: A, B, C, and D. All tunnels are considered reachable, and the preference levels are assigned as follows:
A and B at preference 0
C and D at preference 1
When the router attempts to connect to the domain, suppose it randomly selects tunnel B from preference 0. If it fails to connect to tunnel B, the router excludes tunnel B for five minutes and attempts to connect to tunnel A. If this attempt also fails, the router drops to preference 1. Then suppose the router selects tunnel C. If it also fails to connect to tunnel C, the router excludes tunnel C for five minutes and attempts to connect to tunnel D.
You configure the preference level used for this tunnel selection method in the tunnel profile or the RADIUS Tunnel-Preference [83] attribute.
To enable tunnel selection failover within a preference level:
Specify failover within preference.
[edit services l2tp] user@host# set failover-within-preference
Configuring Weighted Load Balancing for LAC Tunnel Sessions
By default, the L2TP LAC selects tunnels for new sessions at random from within the highest available preference level. You can configure the LAC to distribute sessions across tunnels at the highest available preference level by evaluating the weight of each tunnel. This method is known as weighted load balancing. The weight of a tunnel is proportional to its maximum session limit and the maximum session limits of the other tunnels at the same preference level. When you configure weighted load balancing, the LAC still selects tunnels randomly within a preference level, but on average the sessions are distributed across tunnels in relationship to the tunnel weights.
To configure weighted load balancing:
Specify load balancing.
[edit services l2tp] user@host# set weighted-load-balancing
Configuring Destination-Equal Load Balancing for LAC Tunnel Sessions
By default, the L2TP LAC selects tunnels for new sessions at random from within the highest available preference level. Starting in Junos OS Release 15.1, you can configure the LAC to distribute sessions equally across all tunnels at the highest available preference level by evaluating the number of sessions to the destinations and the number of sessions carried by the tunnels. This distribution method is known as destination-equal load balancing. The LAC selects the tunnel with the lightest load, according to the following guidelines:
When each tunnel goes to a separate destination and only one destination has the lowest session count among all destinations, the LAC selects the tunnel to that destination.
When each tunnel goes to a separate destination and more than one destination has the same lowest session count, the LAC selects a tunnel at random from among the tunnels to these destinations.
When more than one tunnel goes to the same destination and that destination has the lowest destination session count, the LAC selects from among these tunnels the one that has the lowest total number of tunnel sessions. If the tunnel session count is the same for all these tunnels, then the LAC selects one of them at random.
To configure destination-equal load balancing:
Specify destination-equal load balancing.
[edit services l2tp] user@host# set destination-equal-load-balancing
Enabling the LAC for IPv6 Services
You can configure the LAC to create the IPv6 address family (inet6) when tunneling the subscribers to the LNS. IPv6 firewall filters can then be applied by services on the LAC to subscriber traffic. By default, the LAC requires only family inet to enable forwarding into an IP tunnel. The LAC can apply IPv4 firewall filters to the session. Even when family inet6 is included in the dynamic profile, by default it is not created in order to conserve resources, because it is not needed. Consequently IPv6 firewall filters cannot be applied.
To enable IPv6 address family creation and the application of IPv6 firewall filters:
Configure enabling.
[edit services l2tp] user@host# set enable-ipv6-services-for-lac
You can use the show services l2tp summary command to display whether the statement
is enabled or disabled.
Testing L2TP Tunnel Configurations from the LAC
You can test L2TP tunnel configurations on the LAC and successful subscriber authentication and tunneling without bringing up a PPP user and an associated tunnel.
Issue the test services l2tp tunnel command from CLI operational mode to map a subscriber to an L2TP tunnel, verify the L2TP tunnel configuration (both locally on the LAC and on a back-end server such as a RADIUS server), and verify that L2TP tunnels from the LAC can be established with the remote LNS.
The Junos OS LAC implementation enables you to configure multiple tunnels from which one tunnel is chosen for tunneling a PPP subscriber. You can use the test services l2tp tunnel command to test all possible tunnel configurations to verify that each can be established. Alternatively, you can test only a specific tunnel for the subscriber.
You must specify a configured subscriber username when you issue the command. The test generates a dummy password—testpass—for the subscriber, or you can optionally specify the password. The test verifies whether the subscriber identified by that username can be tunneled according to the tunnel configuration. If the subscriber can be tunneled, then the test verifies whether the L2TP tunnel can be established with the LNS according to the L2TP configuration.
You can optionally specify a tunnel ID, in which case only that tunnel is tested; the tunnel must be already configured for that username. If you omit this option, the test is applied to the full set of tunnel configurations that are returned for the username. The tunnel ID you specify is the same as that used by Tunnel-Assignment-Id (RADIUS attribute 82) and specified by the identification statement in the tunnel profile.
To test subscriber authentication and tunnel configuration:
Specify only the username.
Example 1:
user@host> test services l2tp tunnel user test-user1@example.com Subscriber: test-user1@example.com, authentication failed
The user failed authentication with the generated password and consequently was not tunneled.
Example 2:
user@host> test services l2tp tunnel user user23@example.com Subscriber: user23@example.com, authentication success, l2tp tunneled Tunnel-name Tunnel-peer Logical-System Routing-Instance Status test1tunnel 192.168.2.3 default default Up test2tunnel 192.168.30.3 default default Peer unresponsive test3tunnel 192.168.50.1 default test Up
This user was authenticated with the generated password and successfully tunneled. A set of tunnels was found to be associated with that username and the entire set was tested.
Specify the username and the user’s configured password.
user@host> test services l2tp tunnel user test-user1@example.com password grZ98#jW Subscriber: test-user1@example.com, authentication success, locally terminated
The subscriber was authenticated. However, the user was terminated locally rather than tunneled; this means that no tunnel was found to be associated with the user.
Specify the username and a particular tunnel for the subscriber.
user@host> test services l2tp tunnel user rx37w@example.com tunnel-name ce-lac Subscriber: rx37w@example.com, authentication success, l2tp tunneled Tunnel-name Tunnel-peer Logical-System Routing-Instance Status ce-lac 192.168.5.10 default default Up
The subscriber was authenticated and tunneled. The specified tunnel was found for the subscriber and the tunnel was established, confirming the tunnel configuration.
Specify the username, the user’s configured password, and a tunnel.
user@host> test services l2tp tunnel user fanta4-mfg-fan@example.com password dieda499 tunnel-name tunnel5 Subscriber: fanta4-mfg-fan@example.com, authentication success, l2tp tunneled
The subscriber was authenticated and tunneled. The absence of tunnel information in the output indicates that the specified tunnel configuration does not exist.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
