Understanding VN_Port to VN_Port FIP Snooping on an FCoE Transit Switch
VN_Port to VN_Port (VN2VN_Port) Fibre Channel over Ethernet (FCoE) Initialization Protocol (FIP) snooping (FC-BB-6) on an FCoE transit switch is conceptually similar to VN_Port to VF_Port (VN2VF_Port) FIP snooping (FC-BB-5) on an FCoE transit switch. An FCoE transit switch is a data center bridging (DCB) switch with FIP snooping capability. VN2VN_Port FIP snooping provides security in the form of filters. The filters help prevent unauthorized access and data transmission on a bridge that connects ENodes on the Ethernet network.
The main difference between VN2VN_Port FIP snooping and VN2VF_Port FIP snooping is that you use VN2VN_Port FIP snooping when the FCoE devices reside on the Ethernet network, so there is no need to forward traffic between FCoE devices to the Fibre Channel (FC) network, and you use VN2VF_Port FIP snooping when FCoE devices on the Ethernet network need to access targets on the FC network, so FCoE traffic must be forwarded to the FC network. See Understanding VN_Port to VF_Port FIP Snooping on an FCoE Transit Switch for information about VN2VF_Port FIP snooping.
You enable VN2VN_Port FIP snooping on the FCoE VLAN that transports the VN2VN traffic. The transit switch applies VN2VN_Port FIP snooping filters at the ports associated with the FCoE VLANs on which you enable VN2VN FIP snooping.
A key benefit of VN2VN_Port FIP snooping is that it enables FCoE initiators and targets to communicate directly through the switch without going through an FCoE forwarder (FCF) or an FC switch. The transit switch does not differentiate between initiators and targets because the transit switch sees both VN_Ports as FIP virtual link end points. Direct VN2VN_Port communication requires secure access (FIP snooping filters) because ENodes are not trusted entities.
This topic describes:
VN2VN_Port FIP Snooping and FIP Snooping Virtual Links
FIP snooping under the T11 FC-BB-5 specification requires that an FC switch or an FCF be in the path between two VN_Ports when they communicate. Introduced in the T11 FC-BB-6 specification (see http://www.t11.org/ftp/t11/pub/fc/bb-6/10-019v3.pdf), VN2VN_Port FIP snooping allows the FCoE transit switch to connect two VN_Ports to each other directly, without going through an FC switch or an FCF, provided that the ENodes have logged in to the FC network.
In VN2VF_Port FIP snooping, when an ENode logs in to the FC network, the FCoE transit switch snoops the FIP communication between the ENode and the FC switch. In VN2VN_Port FIP snooping mode, the transit switch creates filters on the switch access ports to control VN_Port access to other VN_Ports on the Ethernet network. The VN2VN_Port FIP snooping filters allow the switch to establish a dedicated virtual link that emulates a point-to-point connection between two VN_Ports, through the switch.
Virtual links pass transparently through the transit switch. The VN_Ports do not detect the transit switch, and virtual links appear to be direct point-to-point links.
You explicitly enable VN2VN_Port FIP snooping on FCoE VLANs when the switch or QFabric system Node device is an FCoE transit switch connecting FCoE devices on the Ethernet network to each other and to FC switches or gateways at the FC storage area network (SAN) edge.
An FCoE VLAN can support either VN2VF_Port FIP snooping or VN2VN_Port FIP snooping, but not both. Configure separate FCoE VLANs for VN2VF_Port FIP snooping traffic and for VN2VN_Port FIP snooping traffic. On FCoE VLANs that are configured as VN2VN_Port FIP snooping VLANs, VN_Port to VF_Port traffic is dropped.
When you enable FIP snooping, the system snoops VN2VF_Port packets and enforces security only on VN_Port to VF_Port virtual links. When you enable VN2VN_Port FIP snooping, the system snoops VN_Port to VN_Port FIP packets and enforces security only on VN_Port to VN_Port virtual links.
The transit switch applies VN2VN_Port FIP snooping filters at the ports associated with the FCoE VLANs on which you enable VN2VN_Port FIP snooping. VN2VN_Port FIP snooping provides security for virtual links by creating filters based on information gathered (snooped) about FCoE devices during FIP transactions.
VN2VN_Port Communication Modes
The transit switch supports two VN2VN_Port communication modes:
-
Point-to-point mode
-
Multipoint mode
In point-to-point mode, two ENodes are connected to the network and form a single VN_Port to VN_Port virtual link. This is analogous to the point-to-point FC link between an FC initiator and an FC target.
In multipoint mode, multiple ENodes are connected to the network and form multiple virtual links. Each virtual link is created between one pair of VN_Ports. This is analogous to loop mode in traditional FC networks.
The VN2VN_Port communication mode is not configured; it is determined by the number of ENodes connected to the network.
Network Security
In traditional FC networks, the FC switch is usually a trusted entity and the server ENodes are untrusted entities. The ENodes connect directly to the FC switch VF_Ports. After an ENode gains access to the network through the fabric login (FLOGI) process, the FC switch enforces zoning configurations, ensures that the ENode uses valid addresses, monitors the connection, and performs other security functions to prevent unauthorized access.
However, FCoE exposes FC frames to Ethernet networks, which do not have the same level of security as native FC networks. VN2VN_Port FIP snooping filters emulate the native FC network security functions by preventing unauthorized access and by ensuring the security of the virtual link between ENode VN_Ports. The transit switch performs VN2VN_Port FIP snooping at the ports connected to the FCoE VN_Port devices.
VN2VN_Port FIP Snooping Functions
When you enable VN2VN_Port FIP snooping, the transit switch sets and applies filters to block all FCoE traffic on the VLAN by default. The transit switch monitors FIP logins, solicitations, and advertisements that pass through it and gathers information about the ENode address. The transit switch uses the information to construct filters that permit access only to logged-in ENodes. All other traffic on the VLAN is denied.
The filters enable FCoE frames to pass through the transit switch only on a virtual link established between two VN_Ports. The filters ensure that ENodes can only connect to other ENodes if they have successfully logged in to each other, and that only valid FCoE traffic along valid paths is transmitted. VN2VN_Port FIP snooping maintains the filters by tracking VN_Port to VN_Port sessions.
Scalability
Because ENodes are untrusted and the system needs to apply filters to untrusted FIP snooping interfaces, the total number of combined VN2VN_Port FIP snooping sessions per switch is 376 sessions (ENode to ENode sessions) on untrusted interfaces. On interfaces that are configured as trusted interfaces, no FIP snooping filters are applied.
The total number of sessions the system can support is the combined number of VN2VF_Port sessions and VN2VN_Port sessions. If VN2VF_Port sessions are active, the total number of available VN2VN_Port sessions is reduced.
VN2VN_Port FIP Snooping Implementation
You enable VN2VN_Port FIP snooping on a per-VLAN basis on VLANs that carry FCoE traffic. The switch snoops FIP frames at the ports associated with FCoE VLANs enabled for VN2VN_Port FIP snooping. The switch then installs the resulting filters on the ENode-facing ports to ensure that all FIP snooping occurs on the switch network edge.
VN2VN_Port FIP snooping FCoE VLANs must meet the following criteria:
-
An FCoE VLAN should be dedicated to FCoE traffic only.
-
An FCoE VLAN cannot support both VN2VF_Port FIP snooping (FC-BB-5) and VN2VN_Port FIP snooping (FC-BB-6) simultaneously. You must configure separate FCoE VLANs for FIP snooping traffic and for VN2VN_Port FIP snooping traffic.
Note:Changing an FCoE VLAN from VN2VF_Port FIP snooping mode to VN2VN_Port FIP snooping mode terminates the existing virtual links on the VLAN. The transit switch removes the existing FIP snooping filters, creates the new FIP snooping filters, and applies them to the FIP snooping ports. If you downgrade the software to Junos OS Release 12.1 or earlier, VLANs configured for VN2VN_Port FIP snooping revert to VN2VF_Port FIP snooping VLANs.
-
For switches that do not run Enhanced Layer 2 Software (ELS), as a best practice, you should configure all access ports that belong to an FCoE VLAN (ports connected to a converged network adapter [CNA] in an FCoE device) in
tagged-accessport mode. However, access and trunk port modes are also supported. For switches that use ELS, configure access ports that belong to an FCoE VLAN intrunkinterface mode. -
Access ports should be configured as untrusted ports.
-
All ports connected to another transit switch must be configured in
trunkport mode. -
FIP traffic uses the native VLAN.
-
You can enable VN2VN_Port FIP snooping on a native VLAN.
ENode-Facing Interfaces
When the interfaces that belong to an FCoE VLAN connect directly to FCoE devices (there is no other transit switch between the FCoE devices and the switch), we recommend that you either enable VN2VN_Port FIP snooping on all FCoE VLANs to ensure secure connections between VN_Ports, or enable VN2VF_Port FIP snooping on FCoE VLANs that connect ENodes to an FC switch. FIP snooping should always be enabled at the access edge.
Systems that run Enhanced Layer 2 Software (ELS) support a slightly different configuration on ENode-facing interfaces than systems that do not run ELS. This section describes:
- Non-ELS Port Mode for FCoE Interfaces
- ELS Interface Mode for FCoE Interfaces
- Trusted and Untrusted FCoE Interfaces
Non-ELS Port Mode for FCoE Interfaces
The interfaces that belong to FCoE VLANs (interfaces that connect
to CNAs in FCoE devices) should be configured in tagged-access port mode, unless your CNA does not support tagged VN2VN traffic.
After you enable VN2VN_Port FIP snooping on an FCoE VLAN, the transit
switch denies FCoE traffic from any ENode on that VLAN until the ENode
performs a valid fabric login (FIP FLOGI) with another ENode.
The tagged-access port mode was not available in
Junos OS Release 11.3 and prior releases. In Release 11.3 and earlier, trunk port mode was used for Ethernet interfaces that connected
to FCoE access devices. Because tagged-access mode is now
available, using trunk mode for interfaces connected to
FCoE CNAs is not recommended.
If an existing configuration uses trunk mode for
ports connected to FCoE CNAs, you can change the port mode to tagged-access without disrupting traffic. Although we recommend
changing the port mode of these ports from trunk to tagged-access as a best practice, it is not mandatory. New
configurations should use tagged-access mode for interfaces
that connect to FCoE devices.
ELS Interface Mode for FCoE Interfaces
The interfaces that belong to FCoE VLANs (interfaces that connect
to CNAs in FCoE devices) on systems that support ELS should be configured
in trunk interface mode. After you enable VN2VF_Port FIP
snooping on an FCoE VLAN, the transit switch denies FCoE traffic from
any ENode on that VLAN until the ENode performs a valid fabric login
with an FC switch.
Trusted and Untrusted FCoE Interfaces
Do not configure ENode-facing interfaces as FCoE trusted interfaces
when VN2VF_Port FIP snooping is enabled on those interfaces. If you
enable VN2VF_Port FIP snooping on an FCoE VLAN and you configure ENode-facing
interfaces that are members of the FIP snooping VLAN as fcoe-trusted, then FCoE devices might not be able to log in to the FC network.
Changing ports from untrusted to trusted removes any existing VN2VF_Port FIP snooping filters from the ports and terminates the existing sessions. Changing the fabric ports from trusted to untrusted forces all of the FCoE sessions on those ports to log out so that when the ENodes and VN_Ports log in again, the switch can build the appropriate VN2VF_Port FIP snooping filters.
Network-Facing Interfaces (Connecting to Another Transit Switch)
Configure any interface that is connected to another transit
switch (not to an ENode) as an FCoE trusted interface, in trunk port mode, and as a 10-Gigabit Ethernet interface.
Network-facing Ethernet interfaces have the following requirements and behaviors:
-
You must explicitly configure network-facing trunk ports on an FCoE transit switch as FCoE trusted interfaces.
-
After you configure a network-facing trunk port as a trusted interface, the FCoE transit switch always processes frames from the connected switch because they come from a source on a trusted interface.
-
As a best practice, configure ports in an FCoE VLAN as tagged access ports, but access and trunk port modes are also supported to accommodate whatever types of VN2VN traffic your CNA supports.
Beacon Period (VN2VN_Port FIP Snooping Link Maintenance)
The transit switch needs to maintain the virtual links between VN_Ports, and needs to know when sessions begin and end, and when to install and remove the FIP snooping filters. FIP snooping uses a FIP keepalive advertisement to accomplish this task. VN2VN_Port FIP snooping does not exchange FIP keepalive timer information. Instead, you configure a beacon period, which performs the same function as a keepalive timer.
The beacon period is the time interval between messages which verify that the connection is still valid and that the device at the other end of the virtual link is still reachable. You set the beacon period value for each FCoE VLAN that you configure to do VN2VN_Port FIP snooping.
Explicitly set the beacon period when you configure VN2VN_Port FIP snooping. VN_Ports do not automatically send beacons.
ENodes transmit periodic multicast N_Port_ID beacons to the ALL-VN2VN-ENode-MACs address. The transmission period varies by a random delay of between 0 ms and 100 ms to avoid synchronized bursts of multicast traffic on the network.
If the transit switch does not receive a beacon message from an ENode within 2.5 times the configured beacon period, the transit switch considers the virtual link to be down and terminates the virtual link to that ENode.
QFabric System Differences in VN2VN_Port FIP Snooping Traffic Handling
Configuring VN2VN_Port FIP snooping on a QFabric system is the same as configuring VN2VN_Port FIP snooping on a standalone switch. However, there are internal differences in the way a QFabric system handles VN2VN_Port FIP snooping traffic compared to the way a standalone switch handles VN2VN_Port FIP snooping traffic. The internal differences are transparent. Whether you configure VN2VN_Port FIP snooping on a QFabric system or on a standalone switch, the proper FIP snooping filters and forwarding information are installed on each device.
On standalone switches, the VN2VN_Port FIP snooping traffic does not cross a fabric (Interconnect device). VN2VN_Port traffic enters and exits ports on a single switch, so the ingress port and the egress port have access to the same local forwarding and FIP snooping databases.
However, on a QFabric system, VN2VN_Port FIP snooping traffic might enter on the ingress port of one Node device, traverse the Interconnect device fabric, and exit on the egress port of a different Node device. In this case, the QFabric system must ensure that the FIP snooping database and forwarding information for the VN2VN_Port traffic is installed correctly on both of the Node devices so that traffic is correctly filtered and forwarded.
For example, Figure 1 shows that VN2VN_Port traffic from FCoE host ENode E1 enters the QFabric system at Node device ND1, traverses the Interconnect device fabric, and then exits from Node device ND2 before arriving at FCoE host ENode E2. Similarly, VN2VN_Port traffic from FCoE host ENode E2 enters the QFabric system at Node device ND2, traverses the Interconnect device fabric, and then exits from Node device ND1 before arriving at FCoE host ENode E1.
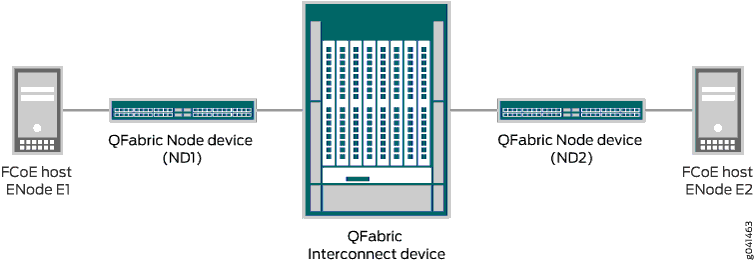
When the QFabric system receives a FLOGI ACC from either ENode E1 or ENode E2, the QFabric system creates and installs the correct VN2VN_Port FIP snooping filters on both Node devices, and updates the forwarding tables accordingly.
In addition, the QFabric system must also ensure that the VN2VN_Port FIP snooping session statistics are correctly counted. Even though a session is running on each of the two Node devices, the QFabric system counts the complete VN2VN_Port connection as one session because the two Node devices belong to the same session. This ensures that VN2VN_Port sessions that traverse the Interconnect device fabric are counted as one unique session, not as two separate sessions.
