Understanding VN_Port to VF_Port FIP Snooping on an FCoE Transit Switch
Fibre Channel over Ethernet (FCoE) Initialization Protocol (FIP) snooping is a security mechanism that is designed to prevent unauthorized access and data transmission to a Fibre Channel (FC) network. It works by filtering traffic to permit only servers that have logged in to an FC network to access that network.
You explicitly enable VN_Port to VF_Port (VN2VF_Port) FIP snooping (FC-BB-5) on FCoE VLANs when the switch is an FCoE transit switch at the access edge that connects FCoE devices on the Ethernet network to FC switches or gateways at the FC storage area network (SAN) edge. The transit switch applies FIP snooping filters at the ports associated with the FCoE VLANs on which you enable VN2VF_Port FIP snooping. An FCoE transit switch is a data center bridging (DCB) switch with FIP snooping capability.
An FCoE device that has a converged network adapter (CNA) uses the FIP process to log in to the FC network as an FCoE Node (ENode). The login process establishes a dedicated virtual link between a virtual N_Port (VN_Port) on the ENode and a virtual F_Port (VF_Port) on the FC switch. This dedicated virtual link emulates a point-to-point connection. The emulated connection is called a virtual link.
Virtual links pass transparently through the transit switch. The ENode VN_Port and the FC switch VF_Port do not detect the transit switch, and virtual links appear to be direct point-to-point links.
The switch applies VN2VF_Port FIP snooping firewall filters at the FCoE-network facing ports associated with the FCoE VLANs on which you enable VN2VF_Port FIP snooping. FIP snooping provides security for virtual links by creating firewall filters based on information gathered (snooped) about FC devices during FIP transactions.
The switch also supports VN_Port to VN_Port (VN2VN_Port) FIP snooping (FC-BB-6) to allow FCoE initiators and targets to communicate directly through the switch without going through an FCoE forwarder (FCF) or an FC switch, as described in Understanding VN_Port to VN_Port FIP Snooping on an FCoE Transit Switch.
An FCoE VLAN can support either VN2VF_Port FIP snooping (FC-BB-5) or VN2VN_Port FIP snooping (FC-BB-6), but not both. The same switch can have multiple FCoE VLANs configured, some for VN2VF_Port FIP snooping traffic and others for VN2VN_Port FIP snooping traffic. On FCoE VLANs that are configured as VN2VN_Port snooping VLANs, VN2VF_Port FIP snooping traffic is dropped.
When you enable VN2VF_Port FIP snooping on an FCoE VLAN, the system snoops VN_Port to VF_Port packets and enforces security only on VN2VF_Port virtual links.
When you enable VN2VN_Port FIP snooping on an FCoE VLAN, the system snoops VN_Port to VN_Port packets and enforces security only on VN2VN_Port virtual links.
This topic describes:
FC Network Security
In traditional FC networks, the FC switch is usually a trusted entity, and server ENodes connect directly to its VF_Ports. After an ENode gains access to the network through the fabric login (FLOGI) process, the FC switch enforces zoning configurations, ensures that the ENode uses valid addresses, monitors the connection, and performs other security functions to prevent unauthorized access.
However, FCoE exposes FC frames to Ethernet networks, which do not have the same level of security as native FC networks. VN2VF_Port FIP snooping firewall filters emulate the native FC network security functions by preventing unauthorized access to the FC switch through the transit switch and by ensuring the security of the virtual link between each ENode and the FC switch, as shown in Figure 1. VN2VF_Port FIP snooping also prevents man-in-the-middle attacks.
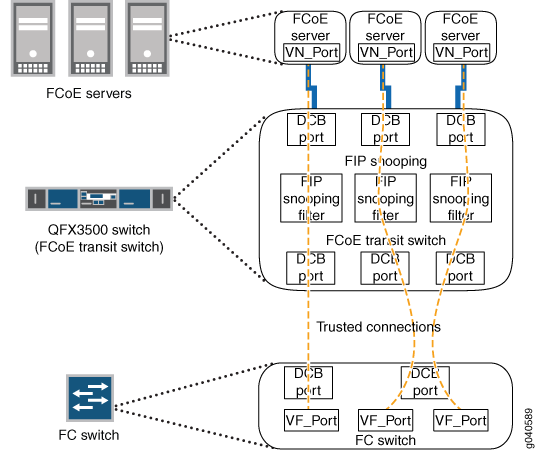
The transit switch performs VN2VF_Port FIP snooping at the ports connected to the FCoE devices. At the SAN edge, the FC switch must be able to convert the FCoE traffic to native FC traffic.
VN2VF_Port FIP Snooping Functions
When VN2VF_Port FIP snooping is enabled, the transit switch sets and applies filters to block all FCoE traffic by default. The transit switch monitors FIP logins, solicitations, and advertisements that pass through it and gathers information about the ENode address and the address of the port on the FC switch. The transit switch uses the information to construct firewall filters that permit access only to logged-in ENodes. All other traffic on the VLAN is denied.
For example, when an ENode on an FCoE VLAN performs a successful login to an FC switch port, the transit switch snoops the FIP information and constructs a firewall filter that provides access for the ENode to that port on the FC switch.
The firewall filters enable FCoE frames to pass through the transit switch only on a virtual link established between an FCoE device ENode VN_Port and the FC switch VF_Port to which it has logged in. The firewall filters ensure that ENodes can only connect to the FC switches they have successfully logged in to and that only valid FCoE traffic along valid paths is transmitted. VN2VF_Port FIP snooping maintains the filters by tracking FCoE sessions (ENode to FCF sessions).
FIP Snooping Firewall Filters
The effect of the firewall filters is to protect the FCoE ports. VN2VF_Port FIP snooping performs the following actions and checks to ensure that FCoE traffic is valid:
Denies ENodes that use the FC switch media access control (MAC) address as the source address.
Enables ENodes to transmit FIP and FCoE frames to the FC switch address.
Ensures that the FCoE source address the FC switch assigns or accepts is only used for FCoE traffic.
Ensures that FCoE frames are only addressed to the accepting FC switch.
FIP Snooping Session Scalability
Enhanced FIP snooping session scaling, which supports up to 2,500 sessions, is enabled by default. On QFabric systems, if you want to disable enhanced FIP snooping scaling (which reduces the number of supported sessions to 376 sessions), you can do so as described in Disabling Enhanced FIP Snooping Scaling.
By default, up to 2500 total FIP snooping sessions are supported on an interface, an FCoE-FC gateway fabric (only supported on QFX3500 switches configured as standalone switches or as QFabric system Node devices), a switch, a QFabric Node device, or a QFabric Node group. For example, you can:
Place all 2500 sessions on one FCoE interface.
Split the 2500 sessions among multiple FCoE interfaces on one FCoE VLAN.
Split the 2500 sessions among multiple FCoE interfaces on multiple FCoE VLANs.
Split the 2500 sessions among the FCoE interfaces on multiple gateway FC fabrics on a switch.
Split the 2500 sessions among the FCoE interfaces on multiple gateway FC fabrics on multiple Node devices in a QFabric Node group.
Regardless of how you allocate the sessions among interfaces and local FC fabrics on a switch or on a QFabric system Node device or Node group, the combined FIP session limit is a maximum of 2500 sessions.
The total number of sessions the system can support is the combined number of VN2VF_Port sessions and VN2VN_Port sessions. If VN2VN_Port sessions are active, the total number of available VN2VF_Port sessions is reduced.
VN2VF_Port FIP Snooping Implementation
You enable VN2VF_Port FIP snooping on a per-VLAN basis on VLANs that carry FCoE traffic. The switch snoops FIP frames at the ports associated with FCoE VLANs enabled for VN2VF_Port FIP snooping. The switch then installs the resulting firewall filters on the ports to ensure that all VN2VF_Port FIP snooping occurs on the switch network edge.
VN2VF_Port FIP snooping FCoE VLANs must meet the following criteria:
An FCoE VLAN should be dedicated to FCoE traffic only.
An FCoE VLAN cannot support both VN2VF_Port FIP snooping and VN2VN_Port FIP snooping simultaneously. You must configure separate FCoE VLANs for VN2VF_Port FIP snooping traffic and for VN2VN_Port FIP snooping traffic.
Note:Changing an FCoE VLAN from VN2VF_Port FIP snooping mode to VN2VN_Port snooping mode terminates the existing virtual links on the VLAN. The transit switch removes the existing FIP snooping filters, creates the new FIP snooping filters, and applies them to the FIP snooping ports. If you downgrade the software to Junos OS Release 12.1 or earlier, VLANs configured for VN2VN_Port FIP snooping revert to VN2VF_Port FIP snooping VLANs.
For systems that use software that does not support Enhanced Layer 2 Software (ELS) CLI, configure all access ports that belong to an FCoE VLAN (ports connected to a converged network adapter [CNA] in an FCoE device) in
tagged-accessport mode. Access ports associated with an FCoE VLAN should not be configured as access ports or trunk ports on these platforms, although trunk port configuration is supported.However, on switches that use the ELS CLI, configure access ports that belong to an FCoE VLAN in
trunkinterface mode.All ports connected to an FC switch (or FCoE forwarder) must be configured in
trunkport mode. Ports connected to an FC switch must be configured as trusted ports.FIP traffic uses the native VLAN (FIP VLAN discovery and notification frames are exchanged as untagged packets).
All FCoE VLAN traffic must be tagged and cannot belong to the native VLAN.
FCoE VLAN traffic cannot be untagged or priority-tagged.
When you enable VN2VF_Port FIP snooping, the switch inspects FIP frames.
The VN2VF_Port FIP snooping implementation includes the following considerations, which are described in the next sections:
ENode-facing interfaces
Network-facing interfaces
FCoE Mapped Address Prefix (FC-MAP) value
ENode-Facing Interfaces
When the interfaces that belong to an FCoE VLAN connect directly to FCoE devices (there is no other transit switch between the FCoE devices and the switch), we recommend that you enable VN2VF_Port FIP snooping on all FCoE VLANs that connect VN_Ports to VF_Ports. Enabling FIP snooping ensures secure connections between server ENodes and FC switches. (Enabling VN2VN_Port FIP snooping ensures secure connections on FCoE VLANs that connect VN_Ports to other VN_Ports). FIP snooping should always be enabled at the access edge.
Systems that run Enhanced Layer 2 Software (ELS) support a slightly different configuration on ENode-facing interfaces than systems that do not run ELS. This section describes:
- Non-ELS Port Mode for FCoE Interfaces
- ELS Interface Mode for FCoE Interfaces
- Trusted and Untrusted FCoE Interfaces
Non-ELS Port Mode for FCoE Interfaces
The interfaces that belong to FCoE VLANs (interfaces that connect
to CNAs in FCoE devices) on systems that do not support ELS should
be configured in tagged-access port mode. After you enable
VN2VF_Port FIP snooping on an FCoE VLAN, the transit switch denies
FCoE traffic from any ENode on that VLAN until the ENode performs
a valid fabric login with an FC switch.
The tagged-access port mode was not available in
Junos OS Release 11.3 and prior releases. In Release 11.3 and earlier, trunk port mode was used for Ethernet interfaces that connected
to FCoE access devices. Because tagged-access mode is now
available, using trunk mode for interfaces connected to
FCoE CNAs is not recommended.
If an existing configuration uses trunk mode for
ports connected to FCoE CNAs, you can change the port mode to tagged-access without disrupting traffic. Although we recommend
changing the port mode of these ports from trunk to tagged-access as a best practice, it is not mandatory. New
configurations should use tagged-access mode for interfaces
that connect to FCoE devices.
ELS Interface Mode for FCoE Interfaces
The interfaces that belong to FCoE VLANs (interfaces that connect
to CNAs in FCoE devices) on systems that support ELS should be configured
in trunk interface mode. After you enable VN2VF_Port FIP
snooping on an FCoE VLAN, the transit switch denies FCoE traffic from
any ENode on that VLAN until the ENode performs a valid fabric login
with an FC switch.
Trusted and Untrusted FCoE Interfaces
Do not configure ENode-facing interfaces as FCoE trusted interfaces
when VN2VF_Port FIP snooping is enabled on those interfaces. If you
enable VN2VF_Port FIP snooping on an FCoE VLAN and you configure ENode-facing
interfaces that are members of the FIP snooping VLAN as fcoe-trusted, then FCoE devices might not be able to log in to the FC network.
Changing ports from untrusted to trusted removes any existing VN2VF_Port FIP snooping filters from the ports and terminates the existing sessions. Changing the fabric ports from trusted to untrusted forces all of the FCoE sessions on those ports to log out so that when the ENodes and VN_Ports log in again, the switch can build the appropriate VN2VF_Port FIP snooping filters.
Network-Facing Interfaces
When the switch acts an FCoE transit switch, you must configure
any interface that is connected to a switch as an FCoE trusted interface
in trunk port mode and as a 10-Gigabit Ethernet interface.
Switch-facing Ethernet interfaces have the following requirements and behaviors:
You must explicitly configure switch-facing trunk ports on an FCoE transit switch as FCoE trusted interfaces.
After you configure an FC switch-facing trunk port as a trusted interface, the FCoE transit switch always processes FC switch frames because they come from a source on a trusted interface.
All ports in an FCoE VLAN must be configured as tagged access or trunk ports.
FCoE Mapped Address Prefix Value (FC-MAP)
When the switch acts as an FCoE transit switch and you enable VN2VF_Port FIP snooping on an FCoE VLAN, you can optionally specify a 24-bit FCoE mapped address prefix (FC-MAP) value. On a given VLAN, the transit switch learns only those FC switches that have a matching FC-MAP value. If the transit switch FCoE VLAN FC-MAP value does not match the FC switch FC-MAP value, the transit switch does not discover the FC switch on that VLAN, and the ENodes on that VLAN cannot access the FC switch. An FCoE VLAN can have one and only one FC-MAP value.
The FC-MAP value is a MAC address prefix unique to an FC switch in the FC SAN fabric that the FC switch uses to identify FCoE traffic for a given FC fabric (traffic on a particular FCoE VLAN). The FC switch combines the FC-MAP value with a unique 24-bit FCID value for the ENode VN_Port during the login process. This creates a 48-bit identifier that is unique to the fabric. The FC switch assigns this 48-bit value to the ENode VN_Port as its MAC address and unique identifier for the session. Each VN_Port session the ENode establishes with the FC switch receives a unique FCID from the FC switch, so an FCoE device can host multiple virtual links (one for each VN_Port) to an FC switch, each with a 48-bit MAC address that is unique to the fabric.
The VN2VF_Port FIP snooping filter compares the configured FC-MAP value with the FC-MAP value in the header of frames coming from the ENode VN_Port. If the values do not match, the transit switch denies access.
Changing the FC-MAP value causes all logins to be dropped and forces ENodes to log in again.
Do not configure static MAC addresses with the FC-MAP value as a prefix (the first 24 bits of the MAC address). If you configure a static MAC address that uses the FC-MAP value as a prefix, the system deletes the static MAC address automatically after you enable FIP snooping. The static MAC address configuration is not restored even if you disable FIP snooping later. (The system considers a static MAC address with the FC-MAP value as the prefix to be a misconfiguration.) Do not use a MAC address with the FC-MAP value as the prefix for any traffic other than the FIP snooping traffic when the switch is acting as a transit switch.
T11 VN2VF_Port FIP Snooping Specification
For more details about VN2VF_Port FIP snooping, see http://www.t11.org/ftp/t11/pub/fc/bb-5/08-264v3.pdf for the Technical Committee T11 organization document Increasing FCoE Robustness using FIP Snooping.
