Example: Configuring Multicast Snooping
Understanding Multicast Snooping
Network devices such as routers operate mainly at the packet level, or Layer 3. Other network devices such as bridges or LAN switches operate mainly at the frame level, or Layer 2. Multicasting functions mainly at the packet level, Layer 3, but there is a way to map Layer 3 IP multicast group addresses to Layer 2 MAC multicast group addresses at the frame level.
Routers can handle both Layer 2 and Layer 3 addressing information because the frame and its addresses must be processed to access the encapsulated packet inside. Routers can run Layer 3 multicast protocols such as PIM or IGMP and determine where to forward multicast content or when a host on an interface joins or leaves a group. However, bridges and LAN switches, as Layer 2 devices, are not supposed to have access to the multicast information inside the packets that their frames carry.
How then are bridges and other Layer 2 devices to determine when a device on an interface joins or leaves a multicast tree, or whether a host on an attached LAN wants to receive the content of a particular multicast group?
The answer is for the Layer 2 device to implement multicast snooping. Multicast snooping is a general term and applies to the process of a Layer 2 device “snooping” at the Layer 3 packet content to determine which actions are taken to process or forward a frame. There are more specific forms of snooping, such as IGMP snooping or PIM snooping. In all cases, snooping involves a device configured to function at Layer 2 having access to normally “forbidden” Layer 3 (packet) information. Snooping makes multicasting more efficient in these devices.
See Also
Understanding Multicast Snooping and VPLS Root Protection
Snooping occurs when a Layer 2 protocol such as a spanning-tree protocol is aware of the operational details of a Layer 3 protocol such as the Internet Group Management Protocol (IGMP) or other multicast protocol. Snooping is necessary when Layer 2 devices such as VLAN switches must be aware of Layer 3 information such as the media access control (MAC) addresses of members of a multicast group.
VPLS root protection is a spanning-tree protocol process in which only one interface in a multihomed environment is actively forwarding spanning-tree protocol frames. This protects the root of the spanning tree against bridging loops, but also prevents both devices in the multihomed topology from snooped information, such as IGMP membership reports.
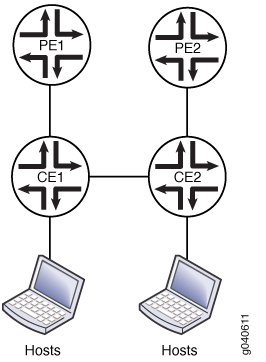
For example, consider a collection of multicast-capable hosts connected to two customer edge (CE) routers (CE1 and CE2) which are connected to each other (a CE1–CE2 link is configured) and multihomed to two provider edge (PE) routers (PE1 and PE2, respectively). The active PE only receives forwarded spanning-tree protocol information on the active PE-CE link, due to root protection operation. As long as the CE1–CE2 link is operational, this is not a problem. However, if the link between CE1 and CE2 fails, and the other PE becomes the active spanning-tree protocol link, no multicast snooping information is available on the new active PE. The new active PE will not forward multicast traffic to the CE and the hosts serviced by this CE router.
The service outage is corrected once the hosts send new group membership IGMP reports to the CE routers. However, the service outage can be avoided if multicast snooping information is available to both PEs in spite of normal spanning-tree protocol root protection operation.
You can configure multicast snooping to ignore messages about spanning tree topology
changes on bridge domains on virtual switches and bridge domains default routing switches.
You can use the ignore-stp-topology-change command to ignore messages about spanning
tree topology changes
See Also
Configuring Multicast Snooping
To configure the general multicast snooping parameters for MX
Series routers, include the multicast-snooping-options statement:
multicast-snooping-options { flood-groups [ ip-addresses ]; forwarding-cache { threshold suppress value <reuse value>; } graceful-restart <restart-duration seconds>; ignore-stp-topology-change; multichassis-lag-replicate-state; nexthop-hold-time milliseconds; traceoptions { file filename <files number> <size size> <world-readable | no-world-readable>; flag flag <flag-modifier> <disable>; } }
You can include this statement at the following hierarchy levels:
[edit routing-instances routing-instance-name][edit logical-systems logical-system-name routing-instances routing-instance-name]
By default, multicast snooping is disabled. You can enable multicast snooping in VPLS or virtual switch instance types in the instance hierarchy.
If there are multiple bridge domains configured under a VPLS or virtual switch instance, the multicast snooping options configured at the instance level apply to all the bridge domains.
The ignore-stp-topology-change statement is
supported for the virtual-switch routing instance type
only and is not supported under the [edit logical-systems] hierarchy.
The nexthop-hold-time statement is supported
only at the [edit routing-instances routing-instance-name] hierarchy, and only for an instance type of virtual-switch or vpls.
See Also
Example: Configuring Multicast Snooping
This example shows how to configure multicast snooping in a bridge or VPLS routing-instance scenario.
Requirements
This example uses the following hardware components:
One MX Series router
One Layer 3 device functioning as a multicast router
Before you begin:
Configure the interfaces.
Configure an interior gateway protocol. See the Junos OS Routing Protocols Library for Routing Devices.
Configure a multicast protocol. This feature works with the following multicast protocols:
DVMRP
PIM-DM
PIM-SM
PIM-SSM
Overview and Topology
IGMP snooping prevents Layer 2 devices from indiscriminately flooding multicast traffic out all interfaces. The settings that you configure for multicast snooping help manage the behavior of IGMP snooping.
You can configure multicast snooping options on the default master instance and on individual bridge or VPLS instances. The default master instance configuration is global and applies to all individual bridge or VPLS instances in the logical router. The configuration for the individual instances overrides the global configuration.
This example includes the following statements:
flood-groups—Enables you to list multicast group addresses for which traffic must be flooded. This setting if useful for making sure that IGMP snooping does not prevent necessary multicast flooding. The block of multicast addresses from 224.0.0.1 through 224.0.0.255 is reserved for local wire use. Groups in this range are assigned for various uses, including routing protocols and local discovery mechanisms. For example, OSPF uses 224.0.0.5 for all OSPF routers.
forwarding-cache—Specifies how forwarding entries are aged out and how the number of entries is controlled.
You can configure threshold values on the forwarding cache to suppress (suspend) snooping when the cache entries reach a certain maximum and reuse the cache when the number falls to another threshold value. By default, no threshold values are enabled on the router.
The suppress threshold suppresses new multicast forwarding cache entries. An optional reuse threshold specifies the point at which the router begins to create new multicast forwarding cache entries. The range for both thresholds is from 1 through 200,000. If configured, the reuse value must be less than the suppression value. The suppression value is mandatory. If you do not specify the optional reuse value, then the number of multicast forwarding cache entries is limited to the suppression value. A new entry is created as soon as the number of multicast forwarding cache entries falls below the suppression value.
graceful-restart—Configures the time after which routes learned before a restart are replaced with routes relearned. If graceful restart for multicast snooping is disabled, snooping information is lost after a Routing Engine restart.
By default, the graceful restart duration is 180 seconds (3 minutes). You can set this value between 0 and 300 seconds. If you set the duration to 0, graceful restart is effectively disabled. Set this value slightly larger than the IGMP query response interval.
ignore-stp-topology-change—Configures the MX Series router to ignore messages about the spanning-tree topology state change.
By default the IGMP snooping process on an MX Series router detects interface state changes made by any of the spanning tree protocols (STPs).
In a VPLS multihoming environment where two PE routers are connected to two interconnected CE routers and STP root protection is enabled on the PE routers, one of the PE router interfaces is in forwarding state and the other is in blocking state.
If the link interconnecting the two CE routers fails, the PE router interface in blocking state transitions to the forwarding state.
The PE router interface does not wait to receive membership reports in response to the next general or group-specific query. Instead, the IGMP snooping process sends a general query message toward the CE router. The hosts connected to the CE router reply with reports for all groups they are interested in.
When the link interconnecting the two CE routers is restored, the original spanning-tree state on both PE routers is restored. The forwarding PE receives a spanning-tree topology change message and sends a general query message toward the CE router to immediately reconstruct the group membership state.
Note:The
ignore-stp-topology-changestatement is supported for the virtual-switch routing instance type only.
Topology
Figure 1 shows a VPLS multihoming topology in which a customer network has two CE devices with a link between them. Each CE is connected to one PE.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste
them into a text file, remove any line breaks, change any details necessary to match your
network configuration, copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set bridge-domains domain1 multicast-snooping-options forwarding-cache threshold suppress 100 set bridge-domains domain1 multicast-snooping-options forwarding-cache threshold reuse 50 set bridge-domains domain1 multicast-snooping-options graceful-restart restart-duration 120 set routing-instances ce1 instance-type virtual-switch set routing-instances ce1 bridge-domains domain1 domain-type bridge set routing-instances ce1 bridge-domains domain1 vlan-id 100 set routing-instances ce1 bridge-domains domain1 interface ge-0/3/9.0 set routing-instances ce1 bridge-domains domain1 interface ge-0/0/6.0 set routing-instances ce1 bridge-domains domain1 multicast-snooping-options flood-groups 224.0.0.5 set routing-instances ce1 bridge-domains domain1 multicast-snooping-options ignore-stp-topology-change
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For information about navigating the CLI, see the Junos OS CLI User Guide.
To configure IGMP snooping:
Configure multicast snooping settings in the master routing instance.
[edit bridge-domains domain1] user@host# set multicast-snooping-options forwarding-cache threshold suppress 100 reuse 50 user@host# set multicast-snooping-options graceful-restart 120
Configure the routing instance.
[edit routing-instances ce1] user@host# set instance-type virtual-switch
Configure the bridge domain in the routing instance.
[edit routing-instances ce1 bridge-domains domain1] user@host# set domain-type bridge user@host# set interface ge-0/0/6.0 user@host# set interface ge-0/3/9.0 user@host# set vlan-id 100
Configure flood groups.
[edit routing-instances ce1 bridge-domains domain1] user@host# set multicast-snooping-options flood-groups 224.0.0.5
Configure the router to ignore messages about spanning-tree topology state changes.
[edit routing-instances ce1 bridge-domains domain1] user@host# set multicast-snooping-options ignore-stp-topology-change
If you are done configuring the device, commit the configuration.
user@host# commit
Results
Confirm your configuration by entering the show bridge-domains and show routing-instances commands.
user@host# show bridge-domains
domain1 {
multicast-snooping-options {
forwarding-cache {
threshold {
suppress 100;
reuse 50;
}
}
}
}
user@host# show routing-instances
ce1 {
instance-type virtual-switch;
bridge-domains {
domain1 {
domain-type bridge;
vlan-id 100;
interface ge-0/3/9.0; ## 'ge-0/3/9.0' is not defined
interface ge-0/0/6.0; ## 'ge-0/0/6.0' is not defined
multicast-snooping-options {
flood-groups 224.0.0.5;
ignore-stp-topology-change;
}
}
}
}
Verification
To verify the configuration, run the following commands:
show igmp snooping interface
show igmp snooping membership
show igmp snooping statistics
show multicast snooping route
show route table
Enabling Bulk Updates for Multicast Snooping
Whenever an individual interface joins or leaves a multicast
group, a new next hop entry is installed in the routing table and
the forwarding table. You can use the nexthop-hold-time statement to specify a time, from 1 through 1000 milliseconds (ms),
during which outgoing interface changes are accumulated and then updated
in bulk to the routing table and forwarding table. Bulk updating reduces
the processing time and memory overhead required to process join and
leave messages. This is useful for applications such as Internet Potocol
television (IPTV), in which users changing channels can create thousands
of interfaces joining or leaving a group in a short period. In IPTV
scenarios, typically there is a relatively small and controlled number
of streams and a high number of outgoing interfaces. Using bulk updates
can reduce the join delay.
In this example, you configure a hold-time of 20 milliseconds
for instance-type virtual-switch, using the nexthop-hold-time statement:
You can include the nexthop-hold-time statement only
for routing-instance types of virtual-switch or vpls at the following hierarchy level.
[edit routing-instances routing-instance-name multicast-snooping-options]
If the nexthop-hold-time statement is deleted from
the router configuration, bulk updates are disabled.
See Also
Enabling Multicast Snooping for Multichassis Link Aggregation Group Interfaces
Include the multichassis-lag-replicate-state statement
at the [edit multicast-snooping-options] hierarchy level
to enable IGMP snooping and state replication for multichassis link
aggregation group (MC-LAG) interfaces.
[edit]
multicast-snooping-options {
multichassis-lag-replicate-state;
}
Replicating join and leave messages between links of a dual-link MC-LAG interface enables faster recovery of membership information for MC-LAG interfaces that experience service interruption.
Without state replication, if a dual-link MC-LAG interface experiences a service interruption (for example, if an active link switches to standby), the membership information for the interface is recovered by generating an IGMP query to the network. This method can take from 1 through 10 seconds to complete, which might be too long for some applications.
When state replication is provided for MC-LAG interfaces, IGMP join or leave messages received on an MC-LAG device are replicated from the active MC-LAG link to the standby link through an Interchassis Communication Protocol (ICCP) connection. The standby link processes the messages as if they were received from the corresponding active MC-LAG link, except it does not add itself as a next hop and it does not flood the message to the network. After a failover, the multicast membership status of the link can be recovered within a few seconds or less by retrieving the replicated messages.
This example enables state replication for MC-LAG interfaces:
