Hierarchical Class of Service for Network Slicing
Understanding Network Slicing
Network slicing is the partitioning of a physical network into multiple logical networks. Each logical network is called a slice. On virtue of being a logical network, a slice is a designated set of network resources, such as interfaces, firewall filters, policers, virtual output queues, schedulers, shapers, traffic control profiles etc. to carry traffic.
Slice Domain
A set of connected physical nodes such as routers and switches (along with their links) that participate in network slicing is called a slice domain. The slice domain has ingress nodes, transit nodes, and egress nodes. Ingress and egress nodes are located at the borders of the slice domain. The ingress nodes receive traffic into the domain and may classify them before forwarding them to the transit nodes. The egress nodes forward traffic out of the slice domain, and before doing so, may classify the packets.
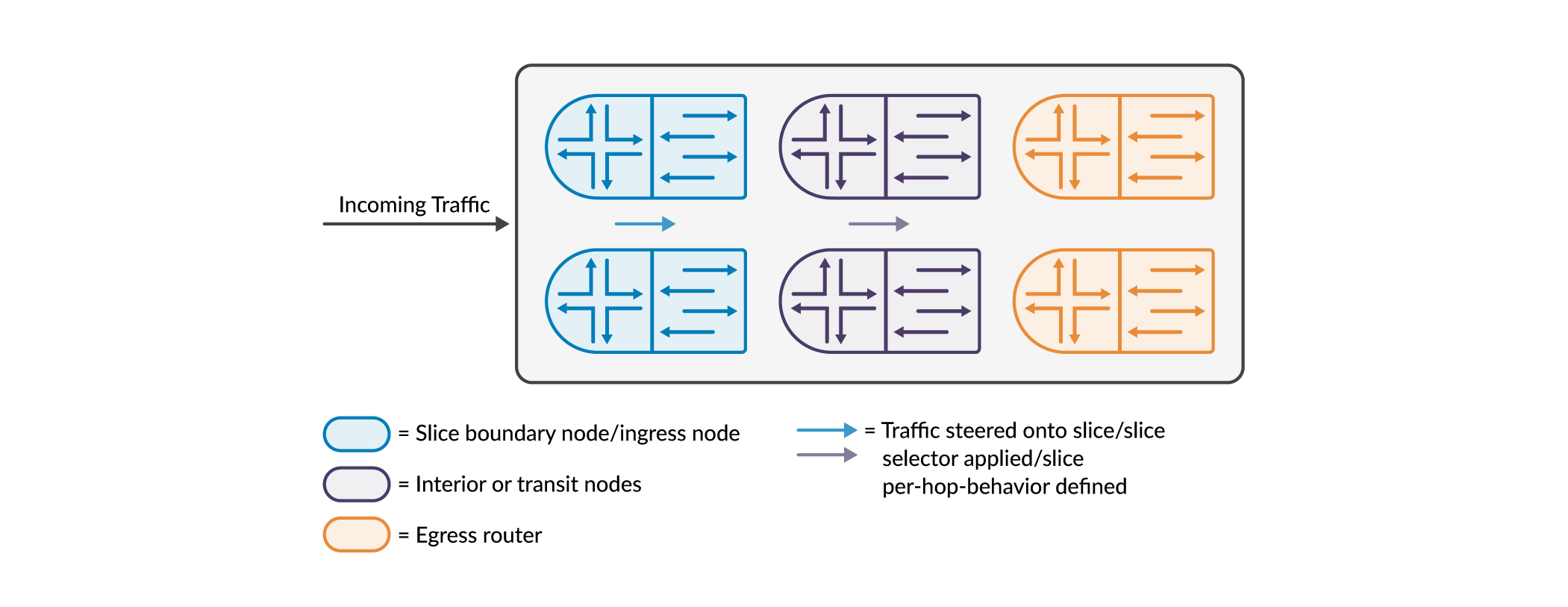
Slice Selector
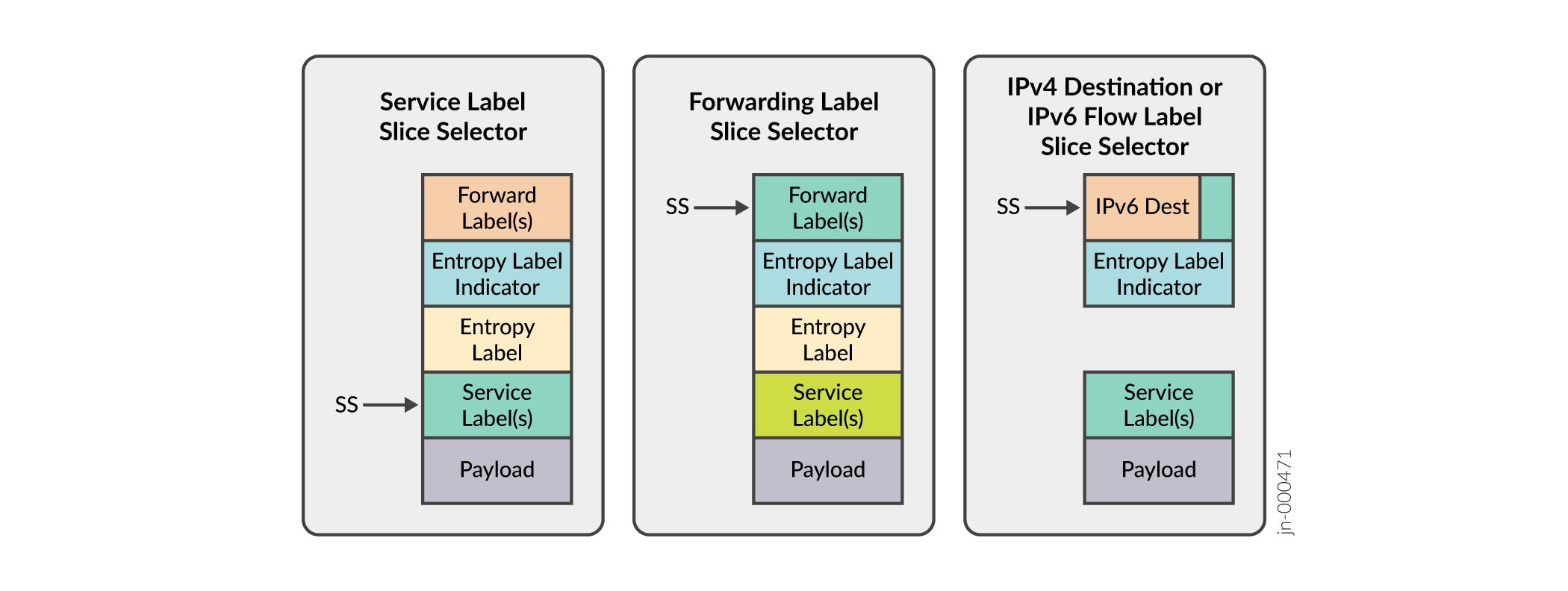
By definition, a slice selector is information in the packet header. The information is used by the boundary nodes and/or transit nodes of a slice domain to classify and/or process packets. There are various options to encapsulate/identify/designate a slice selector in the packet. As an example, a Service Label in the packet header can be used as a slice selector. If defined, this label is allotted a position in the packet header and is checked at this position by firewall filters to determine/designate slices. Similarly, there are several other options as depicted in the following figure.
Workflow for Creating Slices
Slices as entities are created by specifying them under network slicing hierarchy under services. Then these slices are used to steer packets and to manage traffic destined to slices.
Hierarchical class of service for slices
You define a traffic control profile for a slice under a physical or aggregated Ethernet interface. Note that you can define traffic control profiles for multiple slices under a physical or aggregated Ethernet interface. See slice (CoS Interfaces).
See Hierarchical Class of Service (CoS) Queuing for Slice Per-hop-behavior to understand how slices (as part of a hierarchy) are used to control traffic.
Packet steering
Packet steering is the process of marking/matching packets to/from slices. Packets can be steered using firewall filters (firewall steering) and/or routing policy (route steering).
Firewall steering
-
A firewall filter can be used at the ingress node to mark matched packets as belonging to slices using the “slice” action. See slice (firewall filter action).
-
A firewall filter can also be used at the transit node to match slice packets using the “slice” match condition. See slice (firewall filter match condition). The packet can then be marked to another slice if required by the firewall filter or a policer applied to this packet etc.
-
Packets that are not marked/matched to to/from slices are processed as non-slice traffic.
Route steering
-
An export policy can be used at the ingress and/or transit node to mark matched routes as belonging to slices. See slice (export routing policy action).
-
The export policy can also attach a firewall filter to the route. The firewall filter is used to typically apply a policer to the packets matching the route on the ingress side. This firewall filter is not attached to any interface. Rather, it is part of the forwarding information of the route. See filter (export routing policy action).
-
The slice and/or firewall filter will be part of the route’s next-hop forwarding information. See show route extensive expanded-nh to view slices and/or firewall filters attached to routes.
-
Packets that do not match routes with slice information, are classified as non-slice traffic. Packets that match routes with no slice information, are also classified as non-slice traffic.
To summarize, the following are the configurations that are to be enabled before creating slices, can be used to create slices, or manage packets belonging to slices.
-
Specify the slices under network slicing hierarchy under services- – Refer to network-slicing.
-
Enable enhanced-ip mode – Refer network-services.
-
Perform class of service configuration to enable a slice under an interface and also apply an output traffic control profile for the slice – See slice (CoS Interfaces). See Hierarchical Class of Service (CoS) Queuing for Slice Per-hop-behavior to understand how slices (as part of a hierarchy) are used to control traffic.
-
Configure firewall filters to steer routes to slices and/or match routes from slices – See slice (firewall filter match condition) and slice (firewall filter action).
-
Use routing policy to steer routes to slices and/or attach firewall – See slice (export routing policy action) and filter (export routing policy action).
-
View slices and/or firewall filters attached to routes. See show route extensive <route> expanded-nh.
-
View slices attached to the forwarding table. See show class-of-service forwarding-table slice.
-
Show mapping of traffic control profiles to slices. See show class-of-service forwarding-table slice mapping.
-
View traffic control profile(s) attached to a slice under an interface. See show class-of-service slice <slice_name> interface <interface_name>.
-
View statistics for a slice. See show cos halp flow queue-stats.
Hierarchical Class of Service (CoS) Queuing for Slice Per-hop-behavior
In hierarchical CoS, packets are classified at various levels. It could be at the port level, followed by the logical unit level, and then at the queue level. This means that packets are passing through a hierarchy. At every stage of the hierarchy, packets are being classified, shaped, scheduled etc.
In the context of network slicing, a slice also becomes part of the hierarchy. Shapers, schedulers, and traffic control profiles can be applied to the slice. Just as queues are made available to logical units, queues are made available to slices as well.
As the following figure shows, the queues (labeled BA1, BA2, BA3, BA4) are made available to the slice. The queues map to forwarding classes (FCs). Based on behavioral aggregate classifiers, packets are classified into FCs, and subsequently into a corresponding queue (BA1 or BA2 or BA3 etc.).
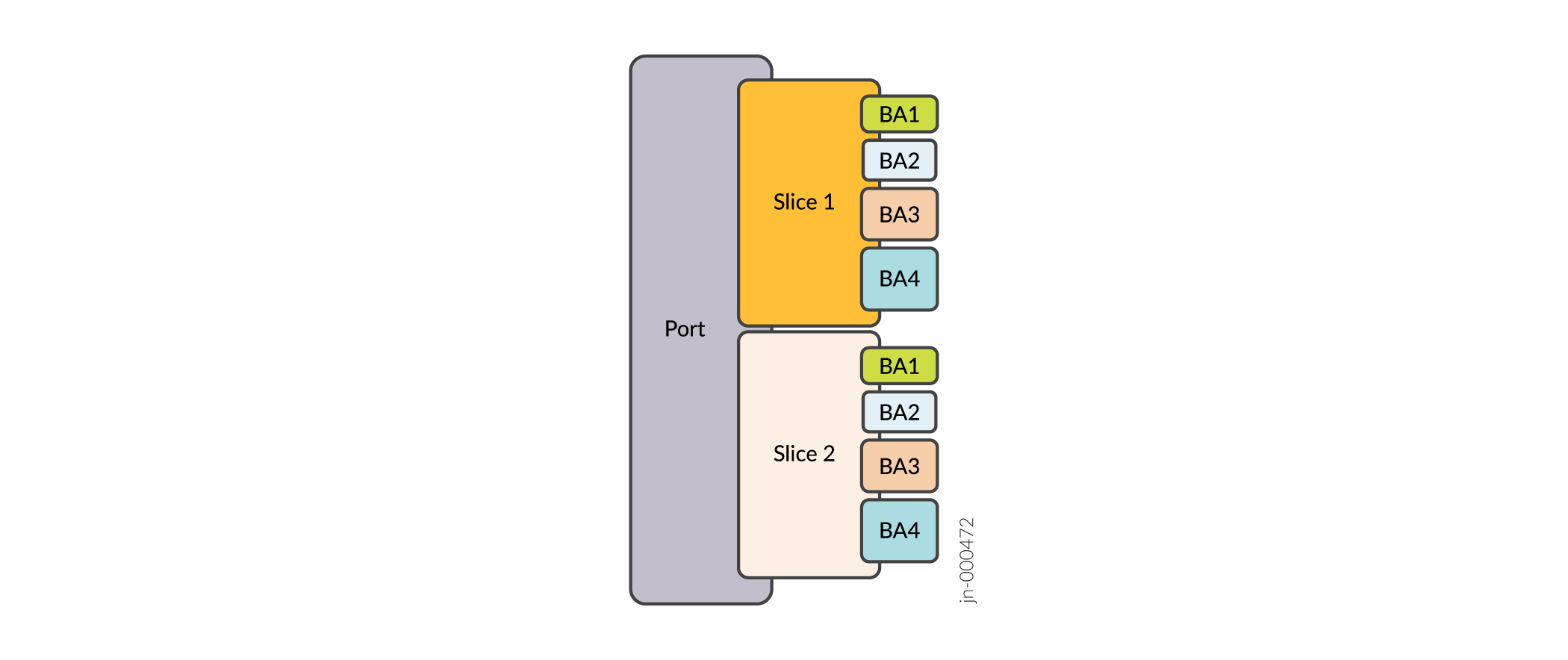
As Workflow for Creating Slices describes, you configure network slicing using a combination of firewall filters and Class of Service (CoS) configuration. See slice (CoS Interfaces) to read on how to enable slice(s) under any interface using CoS configuration.
