MGCP ALG
The Media Gateway Control Protocol (MGCP) is a text-based signaling and call control communications protocol used in VoIP telecommunication systems. MGCP is used to set up, maintain, and terminate calls between multiple endpoints.
Understanding the MGCP ALG
The Media Gateway Control Protocol (MGCP) is a text-based Application Layer protocol used for call setup and call control between the media gateway and the media gateway controller (MGC).
The protocol is based on a primary/client call control architecture: the MGC (call agent) maintains call control intelligence, and media gateways carry out the instructions from the call agent. Both signaling packets and media packets are transmitted over UDP. Junos OS supports MGCP in route mode and Network Address Translation (NAT) mode.
The MGCP Application Layer Gateway (ALG) performs the following procedures:
Conducts voice-over-IP (VoIP) signaling payload inspection. The payload of the incoming VoIP signaling packet is fully inspected based on related RFCs and proprietary standards. Any malformed packet attack is blocked by the ALG.
Conducts MGCP signaling payload inspection. The payload of the incoming MGCP signaling packet is fully inspected in accordance with RFC 3435. Any malformed-packet attack is blocked by the ALG.
Provides stateful processing. The corresponding VoIP-based state machines are invoked to process the parsed information. Any out-of-state or out-of-transaction packet is identified and properly handled.
Performs NAT. Any embedded IP address and port information in the payload is properly translated based on the existing routing information and network topology, and is then replaced with the translated IP address and port number, if necessary.
Manages pinholes for VoIP traffic. To keep the VoIP network secure, the IP address and port information used for media or signaling is identified by the ALG, and any needed pinhole is dynamically created and closed during call setup.
This topic contains the following sections:
MGCP Security
The MGCP ALG includes the following security features:
Denial-of-service (DoS) attack protection. The ALG performs stateful inspection at the UDP packet level, the transaction level, and the call level. MGCP packets matching the RFC 3435 message format, transaction state, and call state, are processed. All other messages are dropped.
Security policy enforcement between gateway and gateway controller (signaling policy).
Security policy enforcement between gateways (media policy).
Per-gateway MGCP message flooding control. Any malfunctioning or hacked gateway will not disrupt the whole VoIP network. Combined with per-gateway flooding control, damage is contained within the impacted gateway.
Per-gateway MGCP connection flooding control.
Seamless switchover/failover if calls, including calls in progress, are switched to the standby firewall in case of system failure.
Entities in MGCP
There are four basic entities in MGCP:
Endpoint
A media gateway is a collection of endpoints. An endpoint can be an analog line, trunk, or any other access point. An endpoint contains the following elements:
local-endpoint-name@domain-name
The following examples are some valid endpoint IDs:
group1/Trk8@example.net group2/Trk1/*@[192.168.10.8] (wild-carding) $@example.net (any endpoint within the media gateway) *@example.net (all endpoints within the media gateway)
Connection
Connections are created on each endpoint by an MG during call setup. A typical VoIP call involves two connections. A complex call, for example a three-party call or conference call, might require more connections. The MGC can instruct media gateways to create, modify, delete, and audit a connection.
A connection is identified by its connection ID, which is created by the MG when it is requested to create a connection. Connection ID is presented as a hexadecimal string, and its maximum length is 32 characters.
Call
A call is identified by its call ID, which is created by the MGC when establishing a new call. Call ID is a hexadecimal string with a maximum length of 32 characters. Call ID is unique within the MGC. Two or more connections can have the same call ID if they belong to the same call.
Call Agent
One or more call agents (also called media gateway controllers) are supported in MGCP to enhance reliability in the VoIP network. The following two examples are of call agent names:
CallAgent@voipCA.example.com voipCA.example.com
Several network addresses can be associated under one domain name in the Domain Name System (DNS). By keeping track of the time to live (TTL) of DNS query/response data and implementing retransmission using other alternative network addresses, switchover and failover is achieved in MGCP.
The concept of a notified entity is essential in MGCP. The notified entity for an endpoint is the call agent currently controlling that endpoint. An endpoint should send any MGCP command to its notified entity. However, different call agents might send MGCP commands to this endpoint.
The notified entity is set to a provisioned value
upon startup, but can be changed by a call agent through the use of
the NotifiedEntity parameter contained in an MGCP message.
If the notified entity for an endpoint is empty or has not been set
explicitly, its value defaults to the source address of the last successful
non-audit MGCP command received for that endpoint.
MGCP Commands
The MGCP protocol defines nine commands for controlling endpoints and connections. All commands are composed of a command header, optionally followed by Session Description Protocol (SDP) information. A command header has the following elements:
A command line: command verb + transaction ID + endpointId + MGCP version.
Zero or more parameter lines, composed of a parameter name followed by a parameter value.
Table 1 lists supported MGCP commands and includes a description of each, the command syntax, and examples. Refer to RFC 2234 for a complete explanation of command syntax.
Command |
Description |
Command Syntax |
Example |
|---|---|---|---|
EPCF |
EndpointConfiguration—Used by a call agent to inform a gateway of coding characteristics (a-law or mu-law) expected by the line side of the endpoint. |
|
|
CRCX |
CreateConnection—Used by a call agent to instruct the gateway to create a connection with, and endpoint inside, the gateway. |
|
|
MDCX |
ModifyConnection—Used by a call agent to instruct a gateway to change the parameters for an existing connection. |
|
|
DLCX |
DeleteConnection—Used by a call agent to instruct a gateway to delete an existing connection. DeleteConnection can also be used by a gateway to release a connection that can no longer be sustained. |
|
Example 1: MGC -> MG
Example 2: MG -> MGC
|
RQNT |
NotificationRequest command—Used by a call agent to instruct an MG to monitor for certain event(s) or signal(s) for a specific endpoint. |
|
|
NTFY |
Notify—Used by a gateway to inform the call agent when requested event(s) or signal(s) occur. |
|
|
AUEP |
AuditEndpoint—Used by a call agent to audit the status of the endpoint. |
|
Example 1:
Example 2:
|
AUCX |
AuditConnection—Used by a call agent to collect the parameters applied to a connection. |
|
|
RSIP |
RestareInProgress—Used by a gateway to notify a call agent that one or more endpoints are being taken out of service or placed back in service. |
|
|
MGCP Response Codes
Every command sent by the calling agent or gateway, whether successful or not, requires a response code. The response code is in the header of the response message, and optionally is followed by session description information.
The response header is composed of a response line, followed by zero or more parameter lines, each containing a parameter name letter followed by its value. The response header is composed of a three-digit response code, transaction ID, and optionally followed by commentary. The response header in the following response message shows response code 200 (successful completion), followed by ID 1204 and the comment:OK.
200 1204 OK I: FDE234C8 v=0 o=- 25678 753849 IN IP4 128.96.41.1 s=- c=IN IP4 128.96.41.1 t=0 0 m=audio 3456 RTP/AVP 96 a=rtpmap:96 G726-32/8000
The ranges of response codes are defined as follows:
000 — 099 indicate a response acknowledgement.
100 — 199—indicate a provisional response.
200 — 299 indicate a successful completion (final response).
400 — 499 indicate a transient error (final response).
500 — 599 indicate a permanent error (final response).
Refer to RFC 3661 for detailed information about response codes.
A response to a command is sent to the source address of the command, not to the current notified entity. A media gateway can receive MGCP commands from various network addresses simultaneously, and send back responses to corresponding network addresses. However, it sends all MGCP commands to its current notified entity.
MGCP ALG Configuration Overview
The Media Gateway Control Protocol (MGCP ALG) is enabled by default on the device—no action is required to enable it. However, you might choose to fine-tune MGCP ALG operations by using the following instructions:
Free up bandwidth when calls fail to properly terminate. See Example: Setting MGCP ALG Call Duration.
Control how long a call can remain active without any media traffic. See Example: Setting MGCP ALG Inactive Media Timeout.
Track and clear signaling traffic when it times out. See Example: Setting MGCP ALG Transaction Timeout.
Protect the media gateway from denial-of-service (DoS) flood attacks. See Example: Configuring MGCP ALG DoS Attack Protection.
Enable unknown messages to pass when the session is in Network Address Translation (NAT) mode and route mode. See Example: Allowing Unknown MGCP ALG Message Types.
Example: Configuring Media Gateways in Subscriber Homes Using MGCP ALGs
This example shows how to configure media gateways in subscriber homes using MGCP ALGs.
Requirements
Before you begin:
-
Configure zones. See Example: Creating Security Zones.
-
Configure addresses and interfaces. See Example: Configuring Address Books and Address Sets.
-
Configure security policies. See Security Policies Configuration Overview.
Overview
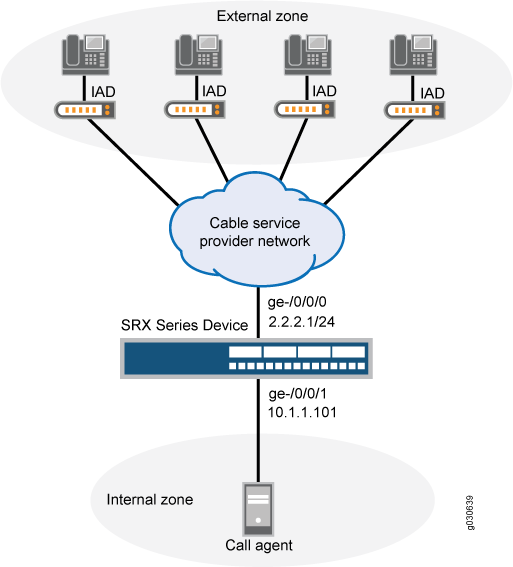
When a cable service provider offers MGCP services to residential subscribers, they locate the Juniper Networks device and call agent on their premises and install a set-top box, in each subscriber's home. The set-top boxes act as gateways for the residences.
After creating zones—external_subscriber for the customer and internal_ca for the service provider—you configure addresses, then interfaces, and finally policies to allow signaling between endpoints. Note that although gateways frequently reside in different zones, requiring policies for media traffic, in this example both gateways are in the same subnet. Note also that because RTP traffic between the gateways never passes through the device, no policy is needed for the media. See Figure 1.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this section of the example,
copy the following commands, paste them into a text file, remove any
line breaks, change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security zones security-zone external-subscriber host-inbound-traffic system-services all set security zones security-zone external-subscriber host-inbound-traffic protocols all set security zones security-zone internal-ca host-inbound-traffic system-services all set security zones security-zone internal-ca host-inbound-traffic protocols all set interfaces ge-0/0/1 unit 0 family inet address 2.2.2.1/24 set interfaces ge-0/0/0 unit 0 family inet set security zones security-zone external-subscriber interfaces ge-0/0/0 set security zones security-zone internal-ca interfaces ge-0/0/1 set security address-book book1 address ca-agent 110.1.1.101/32 set security address-book book1 attach zone internal-ca set security address-book book2 address subscriber-subnet 2.2.2.1/24 set security address-book book2 attach zone external-subscriber set security policies from-zone internal-ca to-zone external-subscriber policy ca-to-subscribers match source-address ca-agent-1 set security policies from-zone internal-ca to-zone external-subscriber policy ca-to-subscribers match destination-address subscriber-subnet set security policies from-zone internal-ca to-zone external-subscriber policy ca-to-subscribers match application junos-mgcp set security policies from-zone internal-ca to-zone external-subscriber policy ca-to-subscribers then permit set security policies from-zone external-subscriber to-zone internal-ca policy subscriber-to-ca match source-address subscriber-subnet set security policies from-zone external-subscriber to-zone internal-ca policy subscriber-to-ca match destination-address ca-agent-1 set security policies from-zone external-subscriber to-zone internal-ca policy subscriber-to-ca match application junos-mgcp set security policies from-zone external-subscriber to-zone internal-ca policy subscriber-to-ca then permit set security policies from-zone internal-ca to-zone internal-ca policy intra-ca then permit set security policies from-zone external-subscriber to-zone external-subscriber policy intra-subscriber match destination-address any
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure media gateways in subscriber homes using MGCP ALGs:
-
Create security zones for the customer and the service provider.
[edit security zones security-zone external-subscriber] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all [edit security zones security-zone internal-ca] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all
-
Configure interfaces for the zones.
[edit] user@host# edit security zones security-zone external-subscriber interfaces ge-0/0/0 user@host# set interfaces ge-0/0/0 unit 0 family inet user@host# set security zones security-zone internal-ca interfaces ge-0/0/1 user@host# set interfaces ge-0/0/1 unit 0 family inet address 2.2.2.1/24
-
Configure address books and attach zones to them.
[edit security address-book book1] user@host# set address ca-agent 110.1.1.101/32 user@host# set attach zone internal-ca
[edit security address-book book2] user@host# set address subscriber-subnet 2.2.2.1/24 user@host# set attach zone external-subscriber
-
Configure policies for traffic from the internal to the external zone.
[edit security policies from-zone internal-ca to-zone external-subscriber policy ca-to-subscribers] user@host# edit match source-address ca-agent-1 user@host# set match destination-address subscriber-subnet user@host# set match application junos-mgcp user@host# set then permit
-
Configure policies for traffic from the external to the internal zone.
[edit security policies from-zone external-subscriber to-zone internal-ca policy subscriber-to-ca] user@host# edit match source-address subscriber-subnet user@host# set match destination-address ca-agent-1 user@host# set match application junos-mgcp user@host# set then permit
-
Configure policies for traffic between two internal zones.
[edit security policies from-zone internal-ca to-zone internal-ca policy intra-ca] user@host# edit match source-address any user@host# set match destination-address any user@host# set match application any user@host# set then permit
-
Configure policies for traffic between two external zones.
[edit security policies from-zone external-subscriber to-zone external-subscriber policy intra-subscriber] user@host# edit match source-address any user@host# set match destination-address any user@host# set match application any user@host# set then permit
Results
From configuration mode, confirm your configuration
by entering the show security policies command. If the
output does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
from-zone internal-ca to-zone external-subscriber {
policy ca-to-subscribers {
match {
source-address ca-agent-1;
destination-address subscriber-subnet;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone external-subscriber to-zone internal-ca {
policy subscriber-to-ca {
match {
source-address subscriber-subnet;
destination-address ca-agent-1;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone internal-ca to-zone internal-ca {
policy intra-ca {
match {
ssource-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone external-subscriber to-zone external-subscriber {
policy intra-subscriber {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}If you are done configuring the device, enter commit from configuration mode.
Verification
To confirm that the configuration is working properly, perform this task:
- Verifying MGCP ALGs
- Verifying MGCP ALG Calls
- Verifying MGCP ALG Endpoints
- Verifying MGCP ALG Counters
Verifying MGCP ALGs
Purpose
Verify the MGCP ALG verification options.
Action
From operational mode, enter the show security
alg mgcp ? command.
user@host> show security alg mgcp ? Possible completions: calls Show MGCP calls counters Show MGCP counters endpoints Show MGCP endpoints
Meaning
The output shows a list of all MGCP verification parameters. Verify the following information:
-
All MGCP calls
-
Counters for all MGCP calls
-
Information about all MGCP endpoints
Verifying MGCP ALG Calls
Purpose
Verify information about active MGCP calls.
Action
From operational mode, enter the show security
alg mgcp calls command.
user@host> show security alg mgcp calls
Endpoint@GW Zone Call ID RM Group
d001@101.50.10.1 Trust 10d55b81140e0f76 512
Connection Id> 0
Local SDP> o: 101.50.10.1 x_o: 101.50.10.1
c: 101.50.10.1/32206 x_c: 101.50.10.1/32206
Remote SDP> c: 3.3.3.5/16928 x_c: 3.3.3.5/16928
Endpoint@GW Zone Call ID RM Group
d001@3.3.3.5 Untrust 3a104e9b41a7c4c9 511
Connection Id> 0
Local SDP> o: 3.3.3.5 x_o: 3.3.3.5
c: 3.3.3.5/16928 x_c: 3.3.3.5/16928
Remote SDP> c: 101.50.10.1/32206 x_c: 101.50.10.1/32206Meaning
The output displays information about all MGCP calls. Verify the following information:
-
Endpoint
-
Zone
-
Call identifier
-
Resource Manager group
Verifying MGCP ALG Endpoints
Purpose
Verify information about MGCP endpoints.
Action
From operational mode, enter the show security
alg mgcp endpoints command.
user@host> show security alg mgcp endpoints Gateway: 101.50.10.1 Zone: Trust IP: 101.50.10.1 -> 101.50.10.1 Endpoint Trans # Call # Notified Entity d001 1 1 0.0.0.0/0->0.0.0.0/0 Gateway: 3.3.3.5 Zone: Untrust IP: 3.3.3.5 -> 3.3.3.5 Endpoint Trans # Call # Notified Entity d001 1 1 0.0.0.0/0->0.0.0.0/0
Meaning
The output displays information about all MGCP endpoints. Verify the following information:
-
Gateway IP address and zone of both endpoints
-
Endpoint identifier, transaction number, call number, and notified entity for each gateway
Verifying MGCP ALG Counters
Purpose
Verify information about MGCP counters.
Action
From operational mode, enter the show security
alg mgcp counters command.
user@host> show security alg mgcp counters MGCP counters summary: Packets received :284 Packets dropped :0 Message received :284 Number of connections :4 Number of active connections :3 Number of calls :4 Number of active calls :3 Number of transactions :121 Number of active transactions:52 Number of re-transmission :68 MGCP Error Counters: Unknown-method :0 Decoding error :0 Transaction error :0 Call error :0 Connection error :0 Connection flood drop :0 Message flood drop :0 IP resolve error :0 NAT error :0 Resource manager error :0 MGCP Packet Counters: CRCX :4 MDCX :9 DLCX :2 AUEP :1 AUCX :0 NTFY :43 RSIP :79 EPCF :0 RQNT :51 000-199 :0 200-299 :95 300-999 :0
Meaning
The output displays information about all MGCP counters. Verify the following information:
-
Summary of MGCP counters
-
MGCP error counters
-
MGCP packet counters
Example: Configuring Three-Zone ISP-Hosted Service Using MGCP ALG and NAT
This example shows how to configure a three-zone configuration using MGCP ALG and NAT.
Requirements
Before you begin, understand NAT support with MGCP ALG. See Understanding the MGCP ALG.
Overview
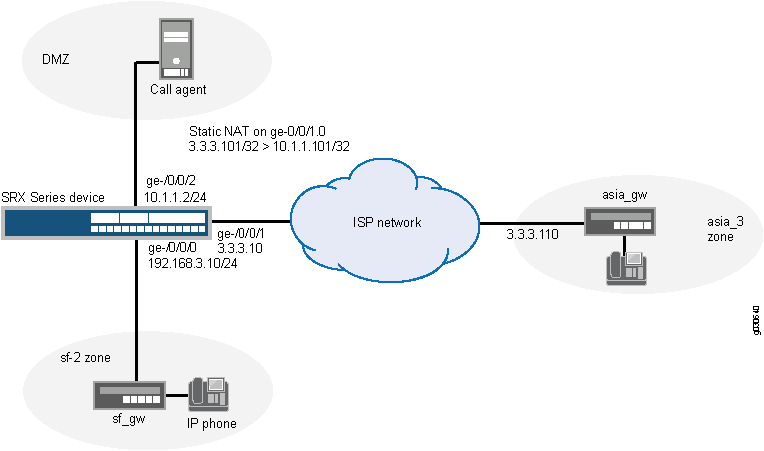
Typically, a three-zone configuration is used when an ISP in one geographical location provides service to two networks in different geographical locations.
In this example (see Figure 2), an ISP located on the USA West Coast provides MGCP service to customers in separate networks in Asia and San Francisco. Asia customers are in the asia-3 zone and are supported by the asia-gw gateway; San Francisco customers are in the sf-2 zone and are supported by the sf-gw gateway. A call agent, west-ca, is in the DMZ. The gateways and the call agent are listed in Table 2, showing the corresponding IP address, interface, and zone.
In this example, after creating zones and setting addresses for the gateways and the call agent, you associate the zones to interfaces, and then configure static NAT to the call agent and source NAT for communication from an IP phone in the sf-2 zone to phones in the asia-3 zone. You also configure a policy between the zones to allow the communication.
Topology
Figure 2 shows a three-zone ISP-hosted service.
|
Gateway |
IP Address |
Interface |
Zone |
|---|---|---|---|
|
sf-gw |
192.168.3.201 |
ge-0/0/0 |
sf-2 |
|
asia-gw |
3.3.3.101 |
ge-0/0/1 |
asia-3 |
|
west-ca |
10.1.1.101 |
ge-0/0/2 |
DMZ |
Configuration
Procedure
CLI Quick Configuration
To quickly configure this section of the example,
copy the following commands, paste them into a text file, remove any
line breaks, change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set interfaces ge-0/0/0 unit 0 family inet address 192.168.3.10/24 >set interfaces ge-0/0/1 unit 0 family inet address 3.3.3.10/24 >set interfaces ge-0/0/2 unit 0 family inet address 10.1.1.2/24 >set security zones security-zone sf-2 interfaces ge-0/0/0.0 >set security zones security-zone asia-3 interfaces ge-0/0/1.0 >set security zones security-zone dmz interfaces ge-0/0/2.0 >set security address-book book1 address sf-gw 192.168.3.201/32 >set security address-book book1 attach zone sf-2 >set security address-book book2 address asia-gw 3.3.3.101/32 >set security address-book book2 attach zone asia-3 >set security address-book book3 address west-ca 10.1.1.101/32 >set security address-book book3 attach zone dmz >set security nat source pool ip-phone-pool address 3.3.3.20/32 >set security nat source rule-set phones from zone sf-2 >set security nat source rule-set phones to zone asia-3 >set security nat source rule-set phones rule phone1 match source-address 192.168.3.10/32 >set security nat source rule-set phones rule phone1 match destination 3.3.3.101/32 >set security nat source rule-set phones rule phone1 then source-nat pool ip-phone-pool >set security nat static rule-set to-callagent from zone asia-3 >set security nat static rule-set to-callagent rule phone1 match destination-address 3.3.3.101/32 >set security nat static rule-set to-callagent rule phone1 then static-nat prefix 10.1.1.101/32 >set security nat proxy-arp interface ge-0/0/1.0 address 3.3.3.101/32 >set security nat proxy-arp interface ge-0/0/1.0 address 3.3.3.20/32 >set security policies from-zone dmz to-zone asia-3 policy pol-dmz-to-asia-3 match source-address west-ca >set security policies from-zone dmz to-zone asia-3 policy pol-dmz-to-asia-3 match destination-address asia-gw >set security policies from-zone dmz to-zone asia-3 policy pol-dmz-to-asia-3 match application junos-mgcp >set security policies from-zone dmz to-zone asia-3 policy pol-dmz-to-asia-3 then permit >set security policies from-zone asia-3 to-zone dmz policy pol-asia-3-to-dmz match source-address asia-gw >set security policies from-zone asia-3 to-zone dmz policy pol-asia-3-to-dmz match destination-address west-ca >set security policies from-zone asia-3 to-zone dmz policy pol-asia-3-to-dmz match application junos-mgcp >set security policies from-zone asia-3 to-zone dmz policy pol-asia-3-to-dmz then permit >set security policies from-zone sf-2 to-zone dmz policy pol-sf-2-to-dmz match source-address sf-gw >set security policies from-zone sf-2 to-zone dmz policy pol-sf-2-to-dmz match destination-address west-ca >set security policies from-zone sf-2 to-zone dmz policy pol-sf-2-to-dmz match application junos-mgcp >set security policies from-zone sf-2 to-zone dmz policy pol-sf-2-to-dmz then permit >set security policies from-zone dmz to-zone sf-2 policy pol-dmz-to-sf-2 match source-address west-ca >set security policies from-zone dmz to-zone sf-2 policy pol-dmz-to-sf-2 match destination-address sf-gw >set security policies from-zone dmz to-zone sf-2 policy pol-dmz-to-sf-2 match application junos-mgcp >set security policies from-zone dmz to-zone sf-2 policy pol-dmz-to-sf-2 then permit >set security policies from-zone sf-2 to-zone asia-3 policy pol-sf-2-to-asia-3 match source-address sf-gw >set security policies from-zone sf-2 to-zone asia-3 policy pol-sf-2-to-asia-3 match destination-address asia-gw >set security policies from-zone sf-2 to-zone asia-3 policy pol-sf-2-to-asia-3 match application junos-mgcp >set security policies from-zone sf-2 to-zone asia-3 policy pol-sf-2-to-asia-3 then permit >set security policies from-zone asia-3 to-zone sf-2 policy pol-asia-3-to-sf-2 match source-address asia-gw >set security policies from-zone asia-3 to-zone sf-2 policy pol-asia-3-to-sf-2 match destination sf-gw >set security policies from-zone asia-3 to-zone sf-2 policy pol-asia-3-to-sf-2 match application junos-mgcp >set security policies from-zone asia-3 to-zone sf-2 policy pol-asia-3-to-sf-2 then permit >set security policies from-zone sf-2 to-zone sf-2 policy pol-intra-sf-2 match source-address any >set security policies from-zone sf-2 to-zone sf-2 policy pol-intra-sf-2 match destination-address any >set security policies from-zone sf-2 to-zone sf-2 policy pol-intra-sf-2 match application any > set security policies from-zone sf-2 to-zone sf-2 policy pol-intra-sf-2 then permit >set security policies from-zone asia-3 to-zone asia-3 policy pol-intra-asia-3 match source-address any >set security policies from-zone asia-3 to-zone asia-3 policy pol-intra-asia-3 match destination-address any >set security policies from-zone asia-3 to-zone asia-3 policy pol-intra-asia-3 match application any >set security policies from-zone asia-3 to-zone asia-3 policy pol-intra-asia-3 then permit
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a three-zone configuration using MGCP ALG and NAT:
-
Configure interfaces.
[edit] user@host# set interfaces ge-0/0/0 unit 0 family inet address 192.168.3.10/24 user@host# set interfaces ge-0/0/1 unit 0 family inet address 3.3.3.10/24 user@host# set interfaces ge-0/0/2 unit 0 family inet address 10.1.1.2/24
-
Create security zones.
[edit security zones] user@host# set security-zone sf-2 interfaces ge-0/0/0 user@host# set security-zone asia-3 interfaces ge-0/0/1 user@host# set security-zone dmz interfaces ge-0/0/2
-
Create address books and assign zones to them.
[edit security address-book book1] user@host# set address sf-gw 192.168.3.201/32 user@host# set attach zone sf-2
[edit security address-book book2] user@host# set address asia-gw 3.3.3.101/32 user@host# set attach zone asia-3
[edit security address-book book3] user@host# set address west-ca 10.1.1.101/32 user@host# set attach zone dmz
-
Create a static NAT rule set and set the match conditions and actions for it.
[edit security nat static rule-set to-callagent] user@host# set from zone asia-3 user@host# set rule phone1 match destination-address 3.3.3.101/32 user@host# set rule phone1 then static-nat prefix 10.1.1.101/32
-
Configure proxy ARP for address
3.3.3.101/32on interfacege-0/0/1.0.[edit security nat ] user@host# set proxy-arp interface ge-0/0/1.0 address 3.3.3.101/32 -
Create a source NAT pool.
[edit security nat] user@host# set source pool ip-phone-pool address 3.3.3.20/32
-
Create a source NAT rule set and set the match conditions and actions for it.
[edit security nat source rule-set phones] user@host# set from zone sf-2 user@host# set to zone asia-3 user@host# set rule phone1 match source-address 192.168.3.10/32 user@host# set rule phone1 match destination-address 3.3.3.101/32 user@host# set rule phone1 then source-nat pool ip-phone-pool
-
Configure proxy ARP for address
3.3.3.20/32on interfacege-0/0/1.0.[edit security nat ] user@host# set proxy-arp interface ge-0/0/1.0 address 3.3.3.20/32
-
Configure a policy to allow traffic from DMZ to Asia.
[edit security policies from-zone dmz to-zone asia-3 policy pol-dmz-to-asia-3] user@host# set match source-address west-ca user@host# set match destination-address asia-gw user@host# set match application junos-mgcp user@host# set then permit
-
Configure a policy to allow traffic from Asia to DMZ.
[edit security policies from-zone asia-3 to-zone dmz policy pol-asia-3-to-dmz] user@host# set match source-address asia-gw user@host# set match destination-address west-ca user@host# set match application junos-mgcp user@host# set then permit
-
Configure a policy to allow traffic from San Francisco to DMZ.
[edit security policies from-zone sf-2 to-zone dmz policy pol-sf-2-to-dmz] user@host# set match source-address sf-gw user@host# set match destination-address west-ca user@host# set match application junos-mgcp user@host# set then permit
-
Configure a policy to allow traffic from DMZ to San Francisco.
[edit security policies from-zone dmz to-zone sf-2 policy pol-dmz-to-sf-2] user@host# set match source-address west-ca user@host# set match destination-address sf-gw user@host# set match application junos-mgcp user@host# set then permit
-
Configure a policy to allow traffic from San Francisco to Asia.
[edit security policies from-zone sf-2 to-zone asia-3 policy pol-sf-2-to-asia-3] user@host# set match source-address sf-gw user@host# set match destination-address asia-gw user@host# set match application junos-mgcp user@host# set then permit
-
Configure a policy to allow traffic from Asia to San Francisco.
[edit security policies from-zone asia-3 to-zone sf-2 policy pol-asia-3-to-sf-2] user@host# set match source-address asia-gw user@host# set match destination-address sf-gw user@host# set match application junos-mgcp user@host# set then permit
-
Configure a policy to allow traffic on devices within San Francisco.
[edit security policies from-zone sf-2 to-zone sf-2 policy pol-intra-sf-2] user@host# set match source-address any user@host# set match destination-address any user@host# set match application any user@host# set then permit
-
Configure a policy to allow traffic on devices within Asia.
[edit security policies from-zone asia-3 to-zone asia-3 policy pol-intra-asia-3] user@host# set match source-address any user@host# set match destination-address any user@host# set match application any user@host# set then permit
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show security zones, show security address-book, show security nat, and show security policies commands. If the output does
not display the intended configuration, repeat the configuration instructions
in this example to correct it.
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 192.168.3.10/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 3.3.3.10/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 10.1.1.2/24;
}
}
}
[edit]
user@host# show security zones
security-zone sf-2 {
interfaces {
ge-0/0/0.0;
}
}
security-zone asia-3 {
interfaces {
ge-0/0/1.0;
}
}
security-zone dmz {
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show security address-book
book1 {
address sf-gw 192.168.3.201/32;
attach {
zone sf-2;
}
}
book2 {
address asia-gw 3.3.3.101/32;
attach {
zone asia-3;
}
}
book3 {
address west-ca 10.1.1.101/32;
attach {
zone dmz;
}
}
[edit]
user@host# show security nat
source {
pool ip-phone-pool {
address {
3.3.3.20/32;
}
}
rule-set phones {
from zone sf-2;
to zone asia-3;
rule phone1 {
match {
source-address 192.168.3.10/32;
destination-address 3.3.3.101/32;
}
then {
source-nat {
pool {
ip-phone-pool;
}
}
}
}
}
}
static {
rule-set to-callagent {
from zone asia-3;
rule phone1 {
match {
destination-address 3.3.3.101/32;
}
then {
static-nat prefix 10.1.1.101/32;
}
}
}
}
proxy-arp {
interface ge-0/0/1.0 {
address {
3.3.3.101/32;
3.3.3.20/32;
}
}
}
[edit]
user@host# show security policies
from-zone dmz to-zone asia-3 {
policy pol-dmz-to-asia-3 {
match {
source-address west-ca;
destination-address asia-gw;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone asia-3 to-zone dmz {
policy pol-asia-3-to-dmz {
match {
source-address asia-gw;
destination-address west-ca;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone sf-2 to-zone dmz {
policy pol-sf-2-to-dmz {
match {
source-address sf-gw;
destination-address west-ca;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone dmz to-zone sf-2 {
policy pol-dmz-to-sf-2 {
match {
source-address west-ca;
destination-address sf-gw;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone sf-2 to-zone asia-3 {
policy pol-sf-2-to-asia-3 {
match {
source-address sf-gw;
destination-address asia-gw;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone asia-3 to-zone sf-2 {
policy pol-asia-3-to-sf-2 {
match {
source-address asia-gw;
destination-address sf-gw;
application junos-mgcp;
}
then {
permit;
}
}
}
from-zone sf-2 to-zone sf-2 {
policy pol-intra-sf-2 {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone asia-3 to-zone asia-3 {
policy pol-intra-asia-3 {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}If you are done configuring the device, enter commit from configuration mode.
Verification
To confirm that the configuration is working properly, perform these tasks:
Verifying MGCP ALG
Purpose
Verify if the MGCP ALG is enabled.
Action
From operational mode, enter the show security
alg status | match mgcp command.
user@host> show security alg status | match mgcp
MGCP : Enabled
Meaning
The output shows the MGCPALG status as follows:
-
Enabled—Shows the MGCP ALG is enabled.
-
Disabled—Shows the MGCP ALG is disabled.
Verifying MGCP Calls
Purpose
Verify the MGCP calls that are currently active.
Action
From operational mode, enter the show security
alg mgcp calls command.
user@host> show security alg mgcp calls
Endpoint@GW Zone Call ID RM Group
d001@101.50.10.1 Trust 10d55b81140e0f76 512
Connection Id> 0
Local SDP> o: 101.50.10.1 x_o: 101.50.10.1
c: 101.50.10.1/32206 x_c: 101.50.10.1/32206
Remote SDP> c: 3.3.3.5/16928 x_c: 3.3.3.5/16928
Endpoint@GW Zone Call ID RM Group
d001@3.3.3.5 Untrust 3a104e9b41a7c4c9 511
Connection Id> 0
Local SDP> o: 3.3.3.5 x_o: 3.3.3.5
c: 3.3.3.5/16928 x_c: 3.3.3.5/16928
Remote SDP> c: 101.50.10.1/32206 x_c: 101.50.10.1/32206Meaning
The output displays information about all MGCP calls. Verify the following information:
-
Endpoint
-
Zone
-
Call identifier
-
Resource Manager group
Verifying MGCP ALG Statistics
Purpose
Verify the MGCP ALG statistics.
Action
From operational mode, enter the show security
alg mgcp counters command.
user@host> show security alg mgcp counters
MGCP counters summary: Packets received :284 Packets dropped :0 Message received :284 Number of connections :4 Number of active connections :3 Number of calls :4 Number of active calls :3 Number of transactions :121 Number of active transactions:52 Number of re-transmission :68 MGCP Error Counters: Unknown-method :0 Decoding error :0 Transaction error :0 Call error :0 Connection error :0 Connection flood drop :0 Message flood drop :0 IP resolve error :0 NAT error :0 Resource manager error :0 MGCP Packet Counters: CRCX :4 MDCX :9 DLCX :2 AUEP :1 AUCX :0 NTFY :43 RSIP :79 EPCF :0 RQNT :51 000-199 :0 200-299 :95 300-999 :0
Meaning
The output displays information about all MGCP counters. Verify the following information:
-
Summary of MGCP counters
-
MGCP error counters
-
MGCP packet counters
Verifying MGCP Endpoints
Purpose
Verify the MGCP endpoints.
Action
From operational mode, enter the show security
alg mgcp endpoints command.
user@host> show security alg mgcp endpoints
Gateway: 101.50.10.1 Zone: Trust IP: 101.50.10.1 -> 101.50.10.1 Endpoint Trans # Call # Notified Entity d001 1 1 0.0.0.0/0->0.0.0.0/0 Gateway: 3.3.3.5 Zone: Untrust IP: 3.3.3.5 -> 3.3.3.5 Endpoint Trans # Call # Notified Entity d001 1 1 0.0.0.0/0->0.0.0.0/0
Meaning
The output displays information about all MGCP endpoints. Verify the following information:
-
Gateway IP address and zone of both endpoints
-
Endpoint identifier, transaction number, call number, and notified entity for each gateway
Understanding MGCP ALG Call Duration and Timeouts
The call duration feature gives you control over Media Gateway Control Protocol (MGCP) call activity and helps you to manage network resources.
Typically a Delete Connection (DLCX) message will be sent out to delete a connection. The MCGP Application Layer Gateway (ALG) intercepts it and removes all media sessions for that connection.
A call can have one or more voice channels. Each voice channel has two sessions (or two media streams), one for Real-Time Transport Protocol (RTP) traffic and one for Real-Time Control Protocol (RTCP) signaling. When managing the sessions, the device considers the sessions in each voice channel as one group. Timeouts and call duration settings apply to a group as opposed to each session.
The following parameters govern MGCP call activity:
maximum-call-duration—This parameter sets the absolute maximum length of a call. When a call exceeds this parameter setting, the MGCP ALG tears down the call and releases the media sessions. The default setting is 720 minutes, and the range is 3 through 720 minutes. This setting also frees up bandwidth in cases where calls fail to properly terminate.inactive-media-timeout—This parameter indicates the maximum length of time (in seconds) a call can remain active without any media (RTP or RTCP) traffic within a group. Each time an RTP or RTCP packet occurs within a call, this timeout resets. When the period of inactivity exceeds this setting, the MGCP ALG gates opened for media are closed. The default setting is 120 seconds, and the range is 10 through 2550 seconds. Note that upon timeout, while resources for media (sessions and pinholes) are removed, the call is not terminated.Note:The
inactive-media-timeoutvalue should be less than themaximum-call-durationvalue.transaction-timeout—A transaction is a command and its mandatory response. For example, an NTFY from the gateway to the call agent or a 200 OK from the call agent to the gateway. The Juniper Networks device tracks these transactions and clears them when they time out. The timeout range for MGCP transactions is 3 through 50 seconds and the default is 30 seconds.
Example: Setting MGCP ALG Call Duration
This example shows how to set call duration for the MGCP ALG.
Requirements
Before you begin, determine the type of parameter used to control the MGCP call activity and manage its network resources. See Understanding MGCP ALG Call Duration and Timeouts.
Overview
The maximum-call-duration parameter governs MGCP
call activity and sets the absolute maximum length of a call. When
a call exceeds this parameter setting, the MGCP ALG tears down the
call and releases the media sessions. The default setting is 720 minutes,
and the range is 3 through 720 minutes. This setting also frees up
bandwidth in cases where calls fail to properly terminate. In this
example, the call duration is set to 600 minutes.
Configuration
Procedure
GUI Quick Configuration
Step-by-Step Procedure
To set call duration for the MGCP ALG:
Select
Configure>Security>ALG.Select the
MGCPtab.In the Maximum call duration box, enter
600.Click
OKto check your configuration and save it as a candidate configuration.If you are done configuring the device, click
Commit Options>Commit.
Step-by-Step Procedure
To set call duration for the MGCP ALG:
Configure the MGCP ALG call duration.
[edit] user@host# set security alg mgcp maximum-call-duration 600
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security alg mgcp command.
Example: Setting MGCP ALG Inactive Media Timeout
This example shows how to set the inactive media timeout value for the MGCP ALG.
Requirements
Before you begin, determine the type of parameter used to control the MGCP call activity and manage its network resources. See Understanding MGCP ALG Call Duration and Timeouts.
Overview
The inactive-media-timeout parameter governs MGCP
call activity and indicates the maximum length of time (in seconds)
a call can remain active without any media (RTP or RTCP) traffic within
a group. Each time an RTP or RTCP packet occurs within a call, this
timeout resets. When the period of inactivity exceeds this setting,
the MGCP ALG gates opened for media are closed. The default setting
is 120 seconds, and the range is from 10 to 2550 seconds. Note that
upon timeout, while resources for media (sessions and pinholes) are
removed, the call is not terminated. In this example, the inactive
media timeout is set to 90 seconds.
Configuration
Procedure
GUI Quick Configuration
Step-by-Step Procedure
To set the inactive media timeout for the MGCP ALG:
Select
Configure>Security>ALG.Select the
MGCPtab.In the Inactive Media Timeout box, enter
90.Click
OKto check your configuration and save it as a candidate configuration.If you are done configuring the device, click
Commit Options>Commit.
Step-by-Step Procedure
To set the inactive media timeout for the MGCP ALG:
Configure the MGCP ALG inactive media timeout value.
[edit] user@host# set security alg mgcp inactive-media-timeout 90
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security alg mgcp command.
Example: Setting MGCP ALG Transaction Timeout
This example shows how to set the transaction timeout for the MGCP ALG.
Requirements
Before you begin, determine the type of parameter used to control the MGCP call activity and manage its network resources. See Understanding MGCP ALG Call Duration and Timeouts.
Overview
The transaction-timeout parameter governs MGCP call
activity and is a signaling message; for example, a NTFY from the
gateway to the call agent or a 200 OK from the call agent to the gateway.
The Juniper Networks device tracks these transactions, and clears
them when they time out. The timeout range for MGCP transactions is
from 3 to 50 seconds, and the default is 30 seconds. In this example,
the transaction timeout is set to 20 seconds.
Configuration
Procedure
GUI Quick Configuration
Step-by-Step Procedure
To set the transaction timeout for the MGCP ALG:
Select
Configure>Security>ALG.Select the
MGCPtab.In the Transaction Timeout box, enter
20.Click
OKto check your configuration and save it as a candidate configuration.If you are done configuring the device, click
Commit Options>Commit.
Step-by-Step Procedure
To set the transaction timeout for the MGCP ALG:
Configure the MGCP ALG transaction timeout value.
[edit] user@host# set security alg mgcp transaction-timeout 20
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security alg mgcp command.
Example: Configuring MGCP ALG DoS Attack Protection
This example shows how to configure connection flood protection for the MGCP ALG.
Requirements
Before you begin, determine whether to protect the MGCP media gateway from DoS flood attacks.
Overview
You can protect the Media Gateway Control Protocol (MGCP) media gateway from denial-of-service (DoS) flood attacks by limiting the number of remote access service (RAS) messages and connections per second it will attempt to process.
When you configure MGCP message flood protection, the MGCP Application Layer Gateway (ALG) drops any messages exceeding the threshold you set. The range is 2 to 50,000 messages per second per media gateway, and the default is 1000 messages per second per media gateway.
When you configure MGCP connection flood protection,
the MGCP ALG drops any connection request exceeding the threshold
you set. This limits the rate of processing of CreateConnection (CRCX) commands, thereby indirectly limiting pinhole
creation. The range is 2 to 10,000 connection requests per second
per media gateway, the default is 200.
In this example, you configure the MGCP ALG to drop any message requests exceeding 10,000 requests per second and to drop any connection requests exceeding 4000 per second.
Configuration
Procedure
GUI Quick Configuration
Step-by-Step Procedure
To configure connection flood protection for the MGCP ALG:
Select
Configure>Security>ALG.Select the
MGCPtab.In the Message flood gatekeeper threshold box, type
10000.In the Connection flood threshold box, type
4000.Click
OKto check your configuration and save it as a candidate configuration.If you are done configuring the device, click
Commit Options>Commit.
Step-by-Step Procedure
To configure connection flood protection for the MGCP ALG:
Configure the connection flood threshold value.
[edit] user@host# set security alg mgcp application-screen message-flood threshold 10000 user@host# set security alg mgcp application-screen connection-flood threshold 4000
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security alg mgcp command.
Example: Allowing Unknown MGCP ALG Message Types
This example shows how to configure the MGCP ALG to allow unknown MGCP message types in both NAT mode and route mode.
Requirements
Before you begin, determine whether to accommodate new and unknown MGCP message types for the device.
Overview
To accommodate on-going development of the Media Gateway Control Protocol (MGCP), you might want to allow traffic containing new MGCP message types. The unknown MGCP message type feature enables you to configure the Juniper Networks device to accept MGCP traffic containing unknown message types in both Network Address Translation (NAT) mode and route mode.
This feature enables you to specify how unidentified MGCP messages are handled by the Juniper Networks device. The default is to drop unknown (unsupported) messages. Unknown messages can compromise security. However, in a secure test or production environment, this command can be useful for resolving interoperability issues with disparate vendor equipment. Permitting unknown MGCP messages can help you get your network operational so that you can later analyze your voice-over-IP (VoIP) traffic to determine why some messages were being dropped.
Note that this command applies only to received packets identified as supported VoIP packets. If a packet cannot be identified, it is always dropped. If a packet is identified as a supported protocol and you have configured the device to permit unknown message types, the message is forwarded without processing.
Configuration
Procedure
GUI Quick Configuration
Step-by-Step Procedure
To configure the MGCP ALG to allow unknown message types:
Select
Configure>Security>ALG.Select the
MGCPtab.Select the
Enable Permit NAT appliedcheck box.Select the
Enable Permit routedcheck box.Click
OKto check your configuration and save it as a candidate configuration.If you are done configuring the device, click
Commit Options>Commit.
Step-by-Step Procedure
To configure the MGCP ALG to allow unknown message types:
Allow unknown message types to pass if the session is in either NAT mode or in route mode.
[edit] user@host# set security alg mgcp application-screen unknown-message permit-nat-applied permit-routed
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security alg mgcp command.
