
Help us improve your experience.
Let us know what you think.
Do you have time for a two-minute survey?

Help us improve your experience.
Let us know what you think.
Do you have time for a two-minute survey?
Access the Email Attachments page from the Monitor > Files > Email Attachments menu.
Benefits of Viewing Scanned Email Attachments
Allows you to view a compiled list of suspicious email attachments all in one place, including the file hash, threat level, filename, and malware type.
Allows you to filter the list of email attachments by individual categories.
Export Data—Click the Export button to download file scanning data to a CSV file. You are prompted to narrow the data download to a selected time-frame.
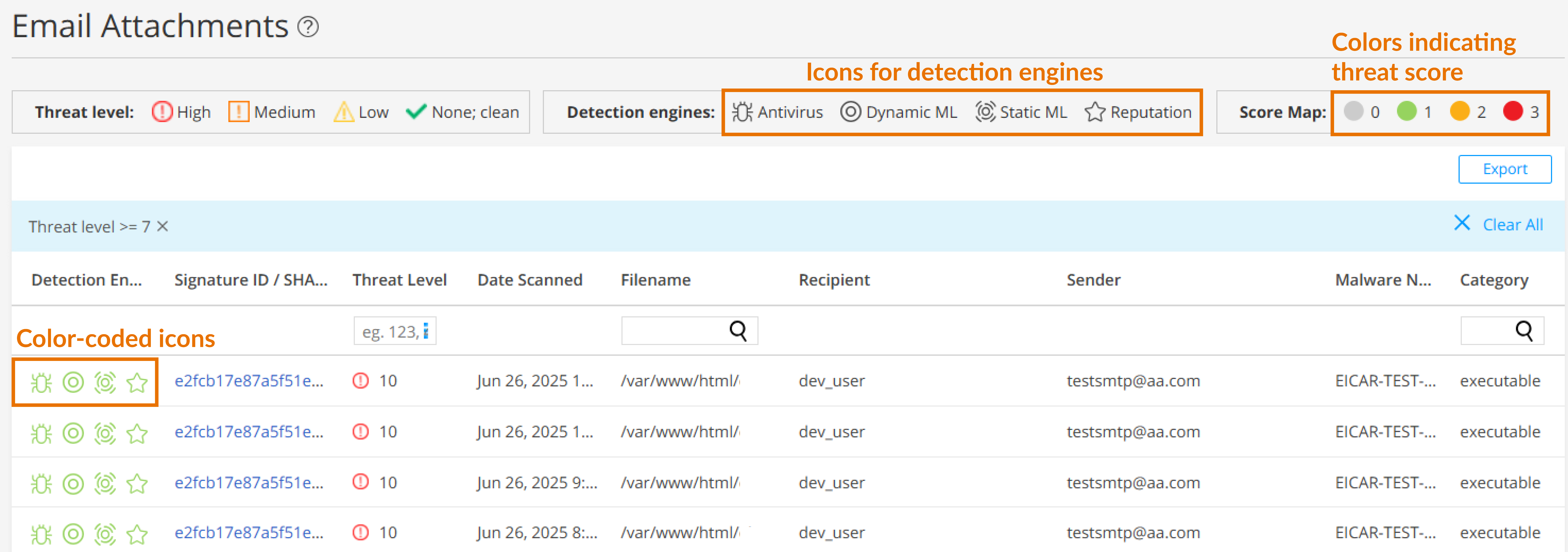
The following information is available on this page.
|
Field |
Definition |
|---|---|
|
Detection Engine |
Displays color-coded icons representing the confidence levels of various detection engines in identifying threats. For more information about detection engines, see Table 2. The color codes signify the following threat severities:
To view the threat severity score assigned by each detection engine, hover over the icons. |
|
Signature ID / SHA-256 / ML Hit |
If applicable, the Signature ID uniquely identifies the signature that is triggered for this detection; otherwise, the SHA-256 file hash is displayed.
|
|
Threat Level |
The threat score. Click the three vertical dots at the top of the column to filter the information in the page by threat level. |
|
Date Scanned |
The date and time the file was scanned. |
|
Filename |
The name of the file, including the extension |
|
Recipient |
The email address of the intended recipient |
|
Sender |
The email address of the sender |
|
Malware Name |
The type of malware found |
|
Status |
Indicates whether the file was blocked or permitted. |
|
Category |
The type of file Examples: PDF, executable, document |