机箱群集中的逻辑系统
机箱群集可在两个设备作为单个设备运行的 SRX 系列防火墙上提供高可用性。机箱群集包括配置文件同步和 SRX 系列防火墙之间的动态运行时会话状态,这些防火墙是机箱群集设置的一部分。有关更多信息,请参阅以下主题:
了解机箱群集中的逻辑系统
机 箱群集 的行为与其节点由运行逻辑系统的 SRX 系列防火墙组成的群集的行为与群集中的 SRX 系列节点不运行逻辑系统的行为相同。导致节点故障转移的事件之间没有区别。特别是,如果与单个逻辑系统关联的链路发生故障,则设备将故障转移到群集中的另一个节点。
主管理员在创建和配置逻辑系统之前,可先配置机箱群集(包括主节点和辅助节点)。群集中的每个节点都具有相同的配置,就像群集中未运行逻辑系统的节点一样。所有逻辑系统配置都会在群集中的两个节点之间同步和复制。
使用SRX 系列防火墙在机箱群集内运行逻辑系统时,必须为机箱群集中的每个节点购买并安装相同数量的许可证。逻辑系统许可证与机箱群集内的单个机箱或节点相关,而不是群集的全部内容。
从 Junos OS 12.3X48-D50 版开始,在机箱群集内配置逻辑系统时,如果在配置时 commit 备份节点上的逻辑系统许可证不足,则会显示一条警告消息,说明备份节点上所需的许可证数量,就像之前所有版本中的主节点一样。
也可以看看
示例:在主动/被动机箱群集中配置逻辑系统(仅限主管理员)
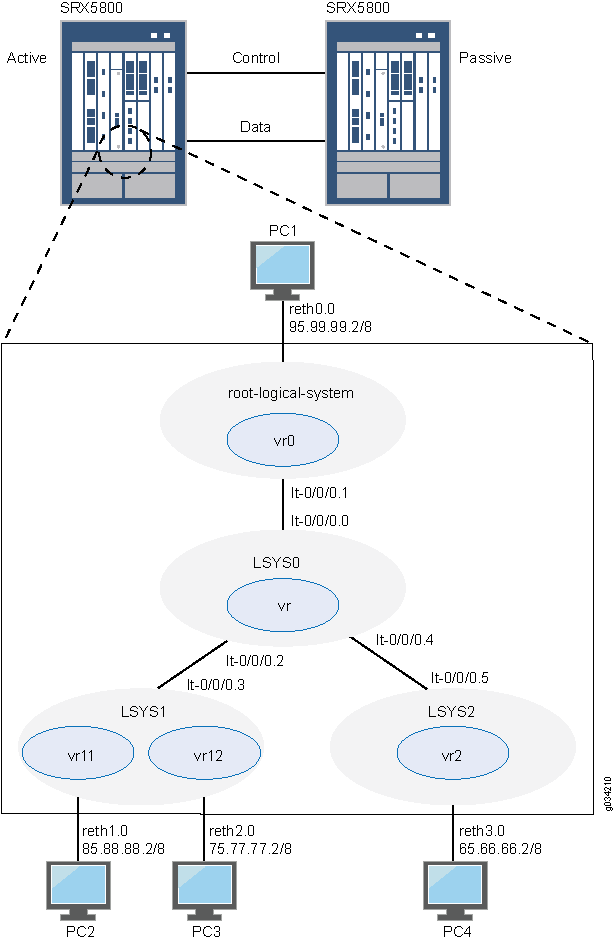
此示例说明如何在基本的主动/被动机箱群集中配置逻辑系统。
主管理员负责配置机箱群集,并创建逻辑系统(包括可选的互连逻辑系统)、管理员和安全配置文件。主管理员或用户逻辑系统管理员可配置用户逻辑系统。配置在群集中的节点之间同步。
要求
开始之前:
-
获取两个硬件配置相同的 SRX 系列防火墙。请参阅 示例:在 SRX5800 设备上配置主动/被动机箱群集。此机箱群集部署方案包括用于连接到 MX240 边缘路由器和 EX8208 以太网交换机的 SRX 系列防火墙配置。
-
物理连接两台设备(背对背连接交换矩阵和控制端口),并确保其型号相同。您可以在 SRX5000 系列上配置交换矩阵端口和控制端口。对于 SRX1400 或 SRX1500 设备或者 SRX3000 系列,只能配置交换矩阵端口。(平台是否支持取决于设备安装的 Junos OS 版本。)请参阅 连接 SRX 系列设备以创建机箱群集。
-
在每台设备上设置机箱群集 ID 和节点 ID,然后重新启动设备以启用群集。请参阅 示例:为机箱群集中的安全性设备设置节点 ID 和群集 ID 。
在此示例中,机箱群集和逻辑系统配置由主管理员在根级别的主(节点 0)设备上执行。以主管理员身份登录设备。请参阅 了解主逻辑系统和主管理员角色。
使用SRX 系列防火墙在机箱群集中运行逻辑系统时,必须为机箱群集中的每个节点购买并安装相同数量的逻辑系统许可证。逻辑系统许可证与机箱群集内的单个机箱或节点相关,而非该群集的全部内容。
概述
在此示例中,基本的主动/被动机箱群集由两台设备组成:
-
一台设备会主动提供逻辑系统,并保持对机箱群集的控制。
-
如果活动设备变为非活动状态,另一台设备会被动维护其群集故障切换功能的状态。
主动/主动机箱群集中的逻辑系统的配置方式与主动/被动机箱群集中的逻辑系统类似。对于主动/主动机箱群集,可以存在多个冗余组,这些组可以在不同节点上作为主节点。
主管理员在主设备(节点 0)上配置以下逻辑系统:
-
主逻辑系统 — 主管理员配置安全配置文件,以便将部分系统安全资源配置到主逻辑系统,并配置主逻辑系统的资源。
-
用户逻辑系统 LSYS1 和 LSYS2 及其管理员 — 主管理员还可配置安全配置文件,以便将部分系统安全资源配置到用户逻辑系统。然后,用户逻辑系统管理员可以配置分配给其逻辑系统的接口、路由和安全资源。
-
连接设备上逻辑系统的互连逻辑系统 LSYS0 — 主管理员在互连逻辑系统和每个逻辑系统之间配置逻辑隧道接口。这些对等接口有效地允许建立隧道。
此示例不介绍如何为逻辑系统配置 NAT、IDP 或 VPN 等功能。有关可为逻辑系统配置的功能的更多信息,请参阅 SRX 系列逻辑系统主管理员配置任务概述 和 用户逻辑系统配置概述 。
如果在机箱群集配置中执行代理 ARP,则必须将代理 ARP 配置应用于 reth 接口,而不是成员接口,因为 reth 接口包含逻辑配置。请参阅为 NAT 配置代理 ARP (CLI 过程)。
配置
机箱群集配置(主管理员)
CLI 快速配置
要快速创建逻辑系统和用户逻辑系统管理员并配置主逻辑系统和互连逻辑系统,请将以下命令复制粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到层次结构级别的 [edit] CLI 中。
在 {primary:node0} 上
set chassis cluster control-ports fpc 0 port 0
set chassis cluster control-ports fpc 6 port 0
set interfaces fab0 fabric-options member-interfaces ge-1/1/0
set interfaces fab1 fabric-options member-interfaces ge-7/1/0
set groups node0 system host-name SRX5800-1
set groups node0 interfaces fxp0 unit 0 family inet address 10.157.90.24/9
set groups node0 system backup-router 10.157.64.1 destination 0.0.0.0/0
set groups node1 system host-name SRX5800-2
set groups node1 interfaces fxp0 unit 0 family inet address 10.157.90.23/19
set groups node1 system backup-router 10.157.64.1 destination 0.0.0.0/0
set apply-groups “${node}”
set chassis cluster reth-count 5
set chassis cluster redundancy-group 0 node 0 priority 200
set chassis cluster redundancy-group 0 node 1 priority 100
set chassis cluster redundancy-group 1 node 0 priority 200
set chassis cluster redundancy-group 1 node 1 priority 100
set interfaces ge-1/0/0 gigether-options redundant-parent reth0
set interfaces ge-1/0/1 gigether-options redundant-parent reth1
set interfaces ge-1/0/2 gigether-options redundant-parent reth2
set interfaces ge-1/0/3 gigether-options redundant-parent reth3
set interfaces ge-7/0/0 gigether-options redundant-parent reth0
set interfaces ge-7/0/1 gigether-options redundant-parent reth1
set interfaces ge-7/0/2 gigether-options redundant-parent reth2
set interfaces ge-7/0/3 gigether-options redundant-parent reth3
set interfaces reth0 redundant-ether-options redundancy-group 1
set interfaces reth0 unit 0 family inet address 95.99.99.1/8
set interfaces reth1 redundant-ether-options redundancy-group 1
set interfaces reth2 redundant-ether-options redundancy-group 1
set interfaces reth3 redundant-ether-options redundancy-group 1
分步程序
下面的示例要求您在各个配置层级中进行导航。有关作说明,请参阅《Junos OS CLI 用户指南》中的在 配置模式下使用CLI编辑器 。
要配置机箱群集,请执行以下作:
在主设备(节点 0)上执行以下步骤。当您执行 commit 命令时,它们会自动复制到辅助设备(节点 1)。
-
为群集配置控制端口。
[edit chass cluster] user@host# set control-ports fpc 0 port 0 user@host# set control-ports fpc 6 port 0
-
配置用于在主动/被动模式下传递 RTO 的群集的交换矩阵(数据)端口。
[edit interfaces] user@host# set fab0 fabric-options member-interfaces ge-1/1/0 user@host# set fab1 fabric-options member-interfaces ge-7/1/0
-
将配置的某些元素分配给特定成员。在 SRX 服务网关的 fxp0 接口上为群集的各个控制平面使用单独的 IP 地址配置带外管理。
[edit] user@host# set groups node0 system host-name SRX5800-1 user@host# set groups node0 interfaces fxp0 unit 0 family inet address 10.157.90.24/9 user@host# set groups node0 system backup-router 10.157.64.1 destination 0.0.0.0/0 user@host# set groups node1 system host-name SRX5800-2 user@host# set groups node1 interfaces fxp0 unit 0 family inet address 10.157.90.23/19 user@host# set groups node1 system backup-router 10.157.64.1 destination 0.0.0.0/0 user@host# set apply-groups “${node}” -
为机箱群集配置冗余组。
[edit chassis cluster] user@host# set reth-count 5 user@host# set redundancy-group 0 node 0 priority 200 user@host# set redundancy-group 0 node 1 priority 100 user@host# set redundancy-group 1 node 0 priority 200 user@host# set redundancy-group 1 node 1 priority 100
-
配置平台上的数据接口,以便在发生数据平面故障切换时,其他机箱群集成员可以无缝接管连接。
[edit interfaces] user@host# set ge-1/0/0 gigether-options redundant-parent reth0 user@host# set ge-1/0/1 gigether-options redundant-parent reth1 user@host# set ge-1/0/2 gigether-options redundant-parent reth2 user@host# set ge-1/0/3 gigether-options redundant-parent reth3 user@host# set ge-7/0/0 gigether-options redundant-parent reth0 user@host# set ge-7/0/1 gigether-options redundant-parent reth1 user@host# set ge-7/0/2 gigether-options redundant-parent reth2 user@host# set ge-7/0/3 gigether-options redundant-parent reth3 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet address 95.99.99.1/8 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth2 redundant-ether-options redundancy-group 1 user@host# set reth3 redundant-ether-options redundancy-group 1
结果
在作模式下,输入 show configuration 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
user@host> show configuration
version ;
groups {
node0 {
system {
host-name SRX58001;
backup-router 10.157.64.1 destination 0.0.0.0/0;
}
interfaces {
fxp0 {
unit 0 {
family inet {
address 10.157.90.24/9;
}
}
}
}
}
node1 {
system {
host-name SRX58002;
backup-router 10.157.64.1 destination 0.0.0.0/0;
}
interfaces {
fxp0 {
unit 0 {
family inet {
address 10.157.90.23/19;
}
}
}
}
}
}
apply-groups "${node}";
chassis {
cluster {
control-link-recovery;
reth-count 5;
control-ports {
fpc 0 port 0;
fpc 6 port 0;
}
redundancy-group 0 {
node 0 priority 200;
node 1 priority 100;
}
redundancy-group 1 {
node 0 priority 200;
node 1 priority 100;
}
}
}
interfaces {
ge-1/0/0 {
gigether–options {
redundant–parent reth0;
}
}
ge-1/0/1 {
gigether–options {
redundant–parent reth1;
}
}
ge-1/0/2 {
gigether–options {
redundant–parent reth2;
}
}
ge-1/0/3 {
gigether–options {
redundant–parent reth3;
}
}
ge-7/0/0 {
gigether–options {
redundant–parent reth0;
}
}
ge-7/0/1 {
gigether–options {
redundant–parent reth1;
}
}
ge-7/0/2 {
gigether–options {
redundant–parent reth2;
}
}
ge-7/0/3 {
gigether–options {
redundant–parent reth3;
}
}
fab0 {
fabric–options {
member–interfaces {
ge-1/1/0;
}
}
}
fab1 {
fabric–options {
member–interfaces {
ge-7/1/0;
}
}
}
reth0 {
redundant–ether–options {
redundancy–group 1;
}
unit 0 {
family inet {
address 95.99.99.1/8;
}
}
}
reth1 {
redundant–ether–options {
redundancy–group 1;
}
}
reth2 {
redundant–ether–options {
redundancy–group 1;
}
}
reth3 {
redundant–ether–options {
redundancy–group 1;
}
}
}
逻辑系统配置(主管理员)
CLI 快速配置
要快速创建逻辑系统和用户逻辑系统管理员并配置主逻辑系统和互连逻辑系统,请将以下命令复制粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到层次结构级别的 [edit] CLI 中。
系统会提示您输入纯文本密码,然后再次输入。
在 {primary:node0} 上
set logical-systems LSYS1
set logical-systems LSYS2
set logical-systems LSYS0
set system login class lsys1 logical-system LSYS1
set system login class lsys1 permissions all
set system login user lsys1admin full-name lsys1-admin
set system login user lsys1admin class lsys1
set user lsys1admin authentication plain-text-password
set system login class lsys2 logical-system LSYS2
set system login class lsys2 permissions all
set system login user lsys2admin full-name lsys2-admin
set system login user lsys2admin class lsys2
set system login user lsys2admin authentication plain-text-password
set system security-profile SP-root policy maximum 200
set system security-profile SP-root policy reserved 100
set system security-profile SP-root zone maximum 200
set system security-profile SP-root zone reserved 100
set system security-profile SP-root flow-session maximum 200
set system security-profile SP-root flow-session reserved 100
set system security-profile SP-root root-logical-system
set system security-profile SP0 logical-system LSYS0
set system security-profile SP1 policy maximum 100
set system security-profile SP1 policy reserved 50
set system security-profile SP1 zone maximum 100
set system security-profile SP1 zone reserved 50
set system security-profile SP1 flow-session maximum 100
set system security-profile SP1 flow-session reserved 50
set system security-profile SP1 logical-system LSYS1
set system security-profile SP2 policy maximum 100
set system security-profile SP2 policy reserved 50
set system security-profile SP2 zone maximum 100
set system security-profile SP2 zone reserved 50
set system security-profile SP2 flow-session maximum 100
set system security-profile SP2 flow-session reserved 50
set system security-profile SP2 logical-system LSYS2
set interfaces lt-0/0/0 unit 1 encapsulation ethernet
set interfaces lt-0/0/0 unit 1 peer-unit 0
set interfaces lt-0/0/0 unit 1 family inet address 2.1.1.1/24
set routing-instances vr0 instance-type virtual-router
set routing-instances vr0 interface lt-0/0/0.1
set routing-instances vr0 interface reth0.0
set routing-instances vr0 routing-options static route 85.0.0.0/8 next-hop 2.1.1.3
set routing-instances vr0 routing-options static route 75.0.0.0/8 next-hop 2.1.1.3
set routing-instances vr0 routing-options static route 65.0.0.0/8 next-hop 2.1.1.5
set security zones security-zone root-trust host-inbound-traffic system-services all
set security zones security-zone root-trust host-inbound-traffic protocols all
set security zones security-zone root-trust interfaces reth0.0
set security zones security-zone root-untrust host-inbound-traffic system-services all
set security zones security-zone root-untrust host-inbound-traffic protocols all
set security zones security-zone root-untrust interfaces lt-0/0/0.1
set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust match source-address any
set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust match destination-address any
set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust match application any
set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust then permit
set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust match source-address any
set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust match destination-address any
set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust match application any
set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust then permit
set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust match source-address any
set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust match destination-address any
set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust match application any
set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust then permit
set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust match source-address any
set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust match destination-address any
set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust match application any
set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust then permit
set logical-systems LSYS0 interfaces lt-0/0/0 unit 0 encapsulation ethernet-vpls
set logical-systems LSYS0 interfaces lt-0/0/0 unit 0 peer-unit 1
set logical-systems LSYS0 interfaces lt-0/0/0 unit 2 encapsulation ethernet-vpls
set logical-systems LSYS0 interfaces lt-0/0/0 unit 2 peer-unit 3
set logical-systems LSYS0 interfaces lt-0/0/0 unit 4 encapsulation ethernet-vpls
set logical-systems LSYS0 interfaces lt-0/0/0 unit 4 peer-unit 5
set logical-systems LSYS0 routing-instances vr instance-type vpls
set logical-systems LSYS0 routing-instances vr interface lt-0/0/0.0
set logical-systems LSYS0 routing-instances vr interface lt-0/0/0.2
set logical-systems LSYS0 routing-instances vr interface lt-0/0/0.4
set logical-systems LSYS1 interfaces lt-0/0/0 unit 3 encapsulation ethernet
set logical-systems LSYS1 interfaces lt-0/0/0 unit 3 peer-unit 2
set logical-systems LSYS1 interfaces lt-0/0/0 unit 3 family inet address 2.1.1.3/24
set logical-systems LSYS2 interfaces lt-0/0/0 unit 5 encapsulation ethernet
set logical-systems LSYS2 interfaces lt-0/0/0 unit 5 peer-unit 4
set logical-systems LSYS2 interfaces lt-0/0/0 unit 5 family inet address 2.1.1.5/24
分步程序
下面的示例要求您在各个配置层级中进行导航。有关作说明,请参阅在 配置模式下使用 CLI 编辑器。
要创建逻辑系统和用户逻辑系统管理员并配置主逻辑系统和互连逻辑系统,请执行以下作:
-
创建互连和用户逻辑系统。
[edit logical-systems] user@host# set LSYS0 user@host# set LSYS1 user@host# set LSYS2
-
配置用户逻辑系统管理员。
分步程序
-
为 LSYS1 配置用户逻辑系统管理员。
[edit system login] user@host# set class lsys1 logical-system LSYS1 user@host# set class lsys1 permissions all user@host# set user lsys1admin full-name lsys1-admin user@host# set user lsys1admin class lsys1 user@host# set user lsys1admin authentication plain-text-password
-
为 LSYS2 配置用户逻辑系统管理员。
[edit system login] user@host# set class lsys2 logical-system LSYS2 user@host# set class lsys2 permissions all user@host# set user lsys2admin full-name lsys2-admin user@host# set user lsys2admin class lsys2 user@host# set user lsys2admin authentication plain-text-password
-
-
配置安全配置文件并将其分配给逻辑系统。
分步程序
-
配置安全配置文件并将其分配给根逻辑系统。
[edit system security-profile] user@host# set SP-root policy maximum 200 user@host# set SP-root policy reserved 100 user@host# set SP-root zone maximum 200 user@host# set SP-root zone reserved 100 user@host# set SP-root flow-session maximum 200 user@host# set SP-root flow-session reserved 100 user@host# set SP-root root-logical-system
-
将不包含资源的虚拟安全配置文件分配给互连逻辑系统 LSYS0。
[edit system security-profile] user@host# set SP0 logical-system LSYS0
-
配置安全配置文件并将其分配给 LSYS1。
[edit system security-profile] user@host# set SP1 policy maximum 100 user@host# set SP1 policy reserved 50 user@host# set SP1 zone maximum 100 user@host# set SP1 zone reserved 50 user@host# set SP1 flow-session maximum 100 user@host# set SP1 flow-session reserved 50 user@host# set SP1 logical-system LSYS1
-
配置安全配置文件并将其分配给 LSYS2。
[edit system security-profile] user@host# set SP2 policy maximum 100 user@host# set SP2 policy reserved 50 user@host# set SP2 zone maximum 100 user@host# set SP2 zone reserved 50 user@host# set SP2 flow-session maximum 100 user@host# set SP2 flow-session reserved 50 user@host# set SP2 logical-system LSYS2
-
-
配置主逻辑系统。
分步程序
-
配置逻辑隧道接口。
[edit interfaces] user@host# set lt-0/0/0 unit 1 encapsulation ethernet user@host# set lt-0/0/0 unit 1 peer-unit 0 user@host# set lt-0/0/0 unit 1 family inet address 2.1.1.1/24
-
配置路由实例。
[edit routing-instances] user@host# set vr0 instance-type virtual-router user@host# set vr0 interface lt-0/0/0.1 user@host# set vr0 interface reth0.0 user@host# set vr0 routing-options static route 85.0.0.0/8 next-hop 2.1.1.3 user@host# set vr0 routing-options static route 75.0.0.0/8 next-hop 2.1.1.3 user@host# set vr0 routing-options static route 65.0.0.0/8 next-hop 2.1.1.5
-
配置区域。
[edit security zones] user@host# set security-zone root-trust host-inbound-traffic system-services all user@host# set security-zone root-trust host-inbound-traffic protocols all user@host# set security-zone root-trust interfaces reth0.0 user@host# set security-zone root-untrust host-inbound-traffic system-services all user@host# set security-zone root-untrust host-inbound-traffic protocols all user@host# set security-zone root-untrust interfaces lt-0/0/0.1
-
配置安全策略。
[edit security policies from-zone root-trust to-zone root-untrust] user@host# set policy root-Trust_to_root-Untrust match source-address any user@host# set policy root-Trust_to_root-Untrust match destination-address any user@host# set policy root-Trust_to_root-Untrust match application any user@host# set policy root-Trust_to_root-Untrust then permit
[edit security policies from-zone root-untrust to-zone root-trust] user@host# set policy root-Untrust_to_root-Trust match source-address any user@host# set policy root-Untrust_to_root-Trust match destination-address any user@host# set policy root-Untrust_to_root-Trust match application any user@host# set policy root-Untrust_to_root-Trust then permit
[edit security policies from-zone root-untrust to-zone root-untrust] user@host# set policy root-Untrust_to_root-Untrust match source-address any user@host# set policy root-Untrust_to_root-Untrust match destination-address any user@host# set policy root-Untrust_to_root-Untrust match application any user@host# set policy root-Untrust_to_root-Untrust then permit
[edit security policies from-zone root-trust to-zone root-trust] user@host# set policy root-Trust_to_root-Trust match source-address any user@host# set policy root-Trust_to_root-Trust match destination-address any user@host# set policy root-Trust_to_root-Trust match application any user@host# set policy root-Trust_to_root-Trust then permit
-
-
配置互连逻辑系统。
分步程序
-
配置逻辑隧道接口。
[edit logical-systems LSYS0 interfaces] user@host# set lt-0/0/0 unit 0 encapsulation ethernet-vpls user@host# set lt-0/0/0 unit 0 peer-unit 1 user@host# set lt-0/0/0 unit 2 encapsulation ethernet-vpls user@host# set lt-0/0/0 unit 2 peer-unit 3 user@host# set lt-0/0/0 unit 4 encapsulation ethernet-vpls user@host# set lt-0/0/0 unit 4 peer-unit 5
-
配置 VPLS 路由实例。
[edit logical-systems LSYS0 routing-instances] user@host# set vr instance-type vpls user@host# set vr interface lt-0/0/0.0 user@host# set vr interface lt-0/0/0.2 user@host# set vr interface lt-0/0/0.4
-
-
为用户逻辑系统配置逻辑隧道接口。
分步程序
-
为 LSYS1 配置逻辑隧道接口。
[edit logical-systems LSYS1 interfaces ] user@host# set lt-0/0/0 unit 3 encapsulation ethernet user@host# set lt-0/0/0 unit 3 peer-unit 2 user@host# set lt-0/0/0 unit 3 family inet address 2.1.1.3/24
-
为 LSYS2 配置逻辑隧道接口。
[edit logical-systems LSYS2 interfaces ] user@host# set lt-0/0/0 unit 5 encapsulation ethernet user@host# set lt-0/0/0 unit 5 peer-unit 4 user@host# set lt-0/0/0 unit 5 family inet address 2.1.1.5/24
-
结果
在配置模式下,输入 show logical-systems LSYS0 命令以确认 LSYS0 的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
user@host# show logical-systems LSYS0
interfaces {
lt-0/0/0 {
unit 0 {
encapsulation ethernet-vpls;
peer-unit 1;
}
unit 2 {
encapsulation ethernet-vpls;
peer-unit 3;
}
unit 4 {
encapsulation ethernet-vpls;
peer-unit 5;
}
}
}
routing-instances {
vr {
instance-type vpls;
interface lt-0/0/0.0;
interface lt-0/0/0.2;
interface lt-0/0/0.4;
}
}
在配置模式下,输入 show interfaces、 show routing-instances和 show security 命令确认主逻辑系统的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
user@host# show interfaces
lt-0/0/0 {
unit 1 {
encapsulation ethernet;
peer-unit 0;
family inet {
address 2.1.1.1/24;
}
}
}
ge-1/0/0 {
gigether-options {
redundant-parent reth0;
}
}
ge-1/0/1 {
gigether-options {
redundant-parent reth1;
}
}
ge-1/0/2 {
gigether-options {
redundant-parent reth2;
}
}
ge-1/0/3 {
gigether-options {
redundant-parent reth3;
}
}
ge-7/0/0 {
gigether-options {
redundant-parent reth0;
}
}
ge-7/0/1 {
gigether-options {
redundant-parent reth1;
}
}
ge-7/0/2 {
gigether-options {
redundant-parent reth2;
}
}
ge-7/0/3 {
gigether-options {
redundant-parent reth3;
}
}
fab0 {
fabric-options {
member-interfaces {
ge-1/1/0;
}
}
}
fab1 {
fabric-options {
member-interfaces {
ge-7/1/0;
}
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 95.99.99.1/8;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
}
reth2 {
redundant-ether-options {
redundancy-group 1;
}
}
reth3 {
redundant-ether-options {
redundancy-group 1;
}
}
[edit]
user@host# show routing-instances
vr0 {
instance-type virtual-router;
interface lt-0/0/0.1;
interface reth0.0;
routing-options {
static {
route 85.0.0.0/8 next-hop 2.1.1.3;
route 75.0.0.0/8 next-hop 2.1.1.3;
route 65.0.0.0/8 next-hop 2.1.1.5;
}
}
}
[edit]
user@host# show security
policies {
from-zone root-trust to-zone root-untrust {
policy root-Trust_to_root-Untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone root-untrust to-zone root-trust {
policy root-Untrust_to_root-Trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone root-untrust to-zone root-untrust {
policy root-Untrust_to_root-Untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone root-trust to-zone root-trust {
policy root-Trust_to_root-Trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone root-trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth0.0;
}
}
security-zone root-untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lt-0/0/0.1;
}
}
}
如果完成设备配置,请从配置模式进入。commit
用户逻辑系统配置(用户逻辑系统管理员)
CLI 快速配置
要快速配置用户逻辑系统,请复制以下命令,将其粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到层次结构级别的 [edit] CLI 中。
以 LSYS1 的用户逻辑系统管理员身份登录时,输入以下命令:
set interfaces reth1 unit 0 family inet address 85.88.88.1/8 set interfaces reth2 unit 0 family inet address 75.77.77.1/8 set routing-instances vr11 instance-type virtual-router set routing-instances vr11 interface lt-0/0/0.3 set routing-instances vr11 interface reth1.0 set routing-instances vr11 routing-options static route 65.0.0.0/8 next-hop 2.1.1.5 set routing-instances vr11 routing-options static route 95.0.0.0/8 next-hop 2.1.1.1 set routing-instances vr12 instance-type virtual-router set routing-instances vr12 interface reth2.0 set routing-instances vr12 routing-options interface-routes rib-group inet vr11vr12v4 set routing-instances vr12 routing-options static route 85.0.0.0/8 next-table vr11.inet.0 set routing-instances vr12 routing-options static route 95.0.0.0/8 next-table vr11.inet.0 set routing-instances vr12 routing-options static route 65.0.0.0/8 next-table vr11.inet.0 set routing-instances vr12 routing-options static route 2.1.1.0/24 next-table vr11.inet.0 set routing-options rib-groups vr11vr12v4 import-rib vr11.inet.0 set routing-options rib-groups vr11vr12v4 import-rib vr12.inet.0 set security zones security-zone lsys1-trust host-inbound-traffic system-services all set security zones security-zone lsys1-trust host-inbound-traffic protocols all set security zones security-zone lsys1-trust interfaces reth1.0 set security zones security-zone lsys1-trust interfaces lt-0/0/0.3 set security zones security-zone lsys1-untrust host-inbound-traffic system-services all set security zones security-zone lsys1-untrust host-inbound-traffic protocols all set security zones security-zone lsys1-untrust interfaces reth2.0 set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust match source-address any set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust match destination-address any set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust match application any set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust then permit set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust match source-address any set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust match destination-address any set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust match application any set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust then permit set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust match source-address any set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust match destination-address any set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust match application any set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust then permit set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust match source-address any set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust match destination-address any set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust match application any set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust then permit
以 LSYS2 的用户逻辑系统管理员身份登录时,输入以下命令:
set interfaces reth3 unit 0 family inet address 65.66.66.1/8 set routing-instances vr2 instance-type virtual-router set routing-instances vr2 interface lt-0/0/0.5 set routing-instances vr2 interface reth3.0 set routing-instances vr2 routing-options static route 75.0.0.0/8 next-hop 2.1.1.3 set routing-instances vr2 routing-options static route 85.0.0.0/8 next-hop 2.1.1.3 set routing-instances vr2 routing-options static route 95.0.0.0/8 next-hop 2.1.1.1 set security zones security-zone lsys2-trust host-inbound-traffic system-services all set security zones security-zone lsys2-trust host-inbound-traffic protocols all set security zones security-zone lsys2-trust interfaces reth3.0 set security zones security-zone lsys2-untrust host-inbound-traffic system-services all set security zones security-zone lsys2-untrust host-inbound-traffic protocols all set security zones security-zone lsys2-untrust interfaces lt-0/0/0.5 set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust match source-address any set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust match destination-address any set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust match application any set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust then permit set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust match source-address any set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust match destination-address any set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust match application any set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust then permit set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust match source-address any set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust match destination-address any set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust match application any set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust then permit set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust match source-address any set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust match destination-address any set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust match application any set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust then permit
分步程序
用户逻辑系统管理员在登录到其用户逻辑系统时执行以下配置。主管理员还可以在 [edit logical-systems logical-system] 层级配置用户逻辑系统。
下面的示例要求您在各个配置层级中进行导航。有关作说明,请参阅在 配置模式下使用 CLI 编辑器。
要配置 LSYS1 用户逻辑系统,请执行以下作:
-
配置接口。
[edit interfaces] lsys1-admin@host:LSYS1# set reth1 unit 0 family inet address 85.88.88.1/8 lsys1-admin@host:LSYS1# set reth2 unit 0 family inet address 75.77.77.1/8
-
配置路由。
[edit routing-instances] lsys1-admin@host:LSYS1# set vr11 instance-type virtual-router lsys1-admin@host:LSYS1# set vr11 interface lt-0/0/0.3 lsys1-admin@host:LSYS1# set vr11 interface reth1.0 lsys1-admin@host:LSYS1# set vr11 routing-options static route 65.0.0.0/8 next-hop 2.1.1.5 lsys1-admin@host:LSYS1# set vr11 routing-options static route 95.0.0.0/8 next-hop 2.1.1.1 lsys1-admin@host:LSYS1# set vr12 instance-type virtual-router lsys1-admin@host:LSYS1# set vr12 interface reth2.0 lsys1-admin@host:LSYS1# set vr12 routing-options interface-routes rib-group inet vr11vr12v4 lsys1-admin@host:LSYS1# set vr12 routing-options static route 85.0.0.0/8 next-table vr11.inet.0 lsys1-admin@host:LSYS1# set vr12 routing-options static route 95.0.0.0/8 next-table vr11.inet.0 lsys1-admin@host:LSYS1# set vr12 routing-options static route 65.0.0.0/8 next-table vr11.inet.0 lsys1-admin@host:LSYS1# set vr12 routing-options static route 2.1.1.0/24 next-table vr11.inet.0
[edit routing-options] lsys1-admin@host:LSYS1# set rib-groups vr11vr12v4 import-rib vr11.inet.0 lsys1-admin@host:LSYS1# set rib-groups vr11vr12v4 import-rib vr12.inet.0
-
配置区域和安全策略。
[edit security zones] lsys1-admin@host:LSYS1# set security-zone lsys1-trust host-inbound-traffic system-services all lsys1-admin@host:LSYS1# set security-zone lsys1-trust host-inbound-traffic protocols all lsys1-admin@host:LSYS1# set security-zone lsys1-trust interfaces reth1.0 lsys1-admin@host:LSYS1# set security-zone lsys1-trust interfaces lt-0/0/0.3 lsys1-admin@host:LSYS1# set security-zone lsys1-untrust host-inbound-traffic system-services all lsys1-admin@host:LSYS1# set security-zone lsys1-untrust host-inbound-traffic protocols all lsys1-admin@host:LSYS1# set security-zone lsys1-untrust interfaces reth2.0
[edit security policies from-zone lsys1-trust to-zone lsys1-untrust] lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust match source-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust match application any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust then permit
[edit security policies from-zone lsys1-untrust to-zone lsys1-trust] lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust match source-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust match application any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust then permit
[edit security policies from-zone lsys1-untrust to-zone lsys1-untrust] lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust match source-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust match application any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust then permit
[edit security policies from-zone lsys1-trust to-zone lsys1-trust] lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust match source-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust match application any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust then permit
分步程序
要配置 LSYS2 用户逻辑系统,请执行以下作:
-
配置接口。
[edit interfaces] lsys2-admin@host:LSYS2# set reth3 unit 0 family inet address 65.66.66.1/8
-
配置路由。
[edit routing-instances] lsys2-admin@host:LSYS2# set vr2 instance-type virtual-router lsys2-admin@host:LSYS2# set vr2 interface lt-0/0/0.5 lsys2-admin@host:LSYS2# set vr2 interface reth3.0 lsys2-admin@host:LSYS2# set vr2 routing-options static route 75.0.0.0/8 next-hop 2.1.1.3 lsys2-admin@host:LSYS2# set vr2 routing-options static route 85.0.0.0/8 next-hop 2.1.1.3 lsys2-admin@host:LSYS2# set vr2 routing-options static route 95.0.0.0/8 next-hop 2.1.1.1
-
配置区域和安全策略。
[edit security zones] lsys2-admin@host:LSYS2# set security-zone lsys2-trust host-inbound-traffic system-services all lsys2-admin@host:LSYS2# set security-zone lsys2-trust host-inbound-traffic protocols all lsys2-admin@host:LSYS2# set security-zone lsys2-trust interfaces reth3.0 lsys2-admin@host:LSYS2# set security zones security-zone lsys2-untrust host-inbound-traffic system-services all lsys2-admin@host:LSYS2# set security-zone lsys2-untrust host-inbound-traffic protocols all lsys2-admin@host:LSYS2# set security-zone lsys2-untrust interfaces lt-0/0/0.5
[edit security policies from-zone lsys2-trust to-zone lsys2-untrust] lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust match source-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust match application any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust then permit
[edit security policies from-zone from-zone lsys2-untrust to-zone lsys2-trust] lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust match source-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust match application any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust then permit
[edit security policies from-zone lsys2-untrust to-zone lsys2-untrust] lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust match source-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust match application any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust then permit
[edit security policies from-zone lsys2-trust to-zone lsys2-trust] lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust match source-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust match application any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust then permit
结果
在配置模式下,输入 show interfaces、 show routing-instances、 show routing-options和 show security 命令以确认 LSYS1 的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
lsys1-admin@host:LSYS1# show interfaces
interfaces {
lt-0/0/0 {
unit 3 {
encapsulation ethernet;
peer-unit 2;
family inet {
address 2.1.1.3/24;
}
}
}
reth1 {
unit 0 {
family inet {
address 85.88.88.1/8;
}
}
}
reth2 {
unit 0 {
family inet {
address 75.77.77.1/8;
}
}
}
}
[edit]
lsys1-admin@host:LSYS1# show routing-instances
routing-instances {
vr11 {
instance-type virtual-router;
interface lt-0/0/0.3;
interface reth1.0;
routing-options {
static {
route 65.0.0.0/8 next-hop 2.1.1.5;
route 95.0.0.0/8 next-hop 2.1.1.1;
}
}
}
vr12 {
instance-type virtual-router;
interface reth2.0;
routing-options {
interface-routes {
rib-group inet vr11vr12v4;
}
static {
route 85.0.0.0/8 next-table vr11.inet.0;
route 95.0.0.0/8 next-table vr11.inet.0;
route 65.0.0.0/8 next-table vr11.inet.0;
route 2.1.1.0/24 next-table vr11.inet.0;
}
}
}
}
[edit]
lsys1-admin@host:LSYS1# show routing-options
rib-groups {
vr11vr12v4 {
import-rib [ vr11.inet.0 vr12.inet.0 ];
}
}
[edit]
lsys1-admin@host:LSYS1# show security
security {
policies {
from-zone lsys1-trust to-zone lsys1-untrust {
policy lsys1trust-to-lsys1untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys1-untrust to-zone lsys1-trust {
policy lsys1untrust-to-lsys1trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys1-untrust to-zone lsys1-untrust {
policy lsys1untrust-to-lsys1untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys1-trust to-zone lsys1-trust {
policy lsys1trust-to-lsys1trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone lsys1-trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.0;
lt-0/0/0.3;
}
}
security-zone lsys1-untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth2.0;
}
}
}
}
在配置模式下,输入 show interfaces、 show routing-instances和 show security 命令以确认 LSYS2 的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
lsys2-admin@host:LSYS2# show interfaces
[edit]
interfaces {
lt-0/0/0 {
unit 5 {
encapsulation ethernet;
peer-unit 4;
family inet {
address 2.1.1.5/24;
}
}
}
reth3 {
unit 0 {
family inet {
address 65.66.66.1/8;
}
}
}
}
[edit]
lsys2-admin@host:LSYS2# show routing-instances
routing-instances {
vr2 {
instance-type virtual-router;
interface lt-0/0/0.5;
interface reth3.0;
routing-options {
static {
route 75.0.0.0/8 next-hop 2.1.1.3;
route 85.0.0.0/8 next-hop 2.1.1.3;
route 95.0.0.0/8 next-hop 2.1.1.1;
}
}
}
}
[edit]
lsys2-admin@host:LSYS2# show security
security {
policies {
from-zone lsys2-trust to-zone lsys2-untrust {
policy lsys2trust-to-lsys2untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys2-untrust to-zone lsys2-trust {
policy lsys2untrust-to-lsys2trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys2-untrust to-zone lsys2-untrust {
policy lsys2untrust-to-lsys2untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys2-trust to-zone lsys2-trust {
policy lsys2trust-to-lsys2trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone lsys2-trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth3.0;
}
}
security-zone lsys2-untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lt-0/0/0.5;
}
}
}
}
如果完成设备配置,请从配置模式进入。commit
验证
确认配置工作正常。
验证机箱群集状态
目的
验证机箱群集状态、故障切换状态和冗余组信息。
行动
在作模式下,输入命令 show chassis cluster status 。
{primary:node0}
show chassis cluster status
Cluster ID: 1
Node Priority Status Preempt Manual failover
Redundancy group: 0 , Failover count: 1
node0 200 primary no no
node1 100 secondary no no
Redundancy group: 1 , Failover count: 1
node0 200 primary no no
node1 100 secondary no no
使用日志对机箱群集进行故障排除
目的
通过查看两个节点上的日志来确定任何机箱群集问题。
行动
在作模式下,输入以下 show log 命令。
user@host> show log jsrpd user@host> show log chassisd user@host> show log messages user@host> show log dcd user@host> show traceoptions
验证逻辑系统许可证
目的
验证有关逻辑系统许可证的信息。
行动
在作模式下,输入命令 show system license status logical-system all 。
{primary:node0}
user@host> show system license status logical-system all
node0:
--------------------------------------------------------------------------
Logical system license status:
logical system name license status
root-logical-system enabled
LSYS0 enabled
LSYS1 enabled
LSYS2 enabled
验证逻辑系统许可证使用情况
目的
验证有关逻辑系统许可证使用情况的信息。
实际使用的许可证数仅显示在主节点上。
行动
在作模式下,输入命令 show system license 。
{primary:node0}
user@host> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
logical-system 4 25 0 permanent
Licenses installed:
License identifier: JUNOS305013
License version: 2
Valid for device: JN110B54BAGB
Features:
logical-system-25 - Logical System Capacity
permanent
验证逻辑系统上的逻辑系统内流量
目的
验证有关逻辑系统中当前活动安全会话的信息。
行动
在作模式下,输入命令 show security flow session logical-system LSYS1 。
{primary:node0}
user@host> show security flow session logical-system LSYS1
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Session ID: 90000114, Policy name: lsys1trust-to-lsys1untrust/8, State: Active, Timeout: 1782, Valid
In: 85.88.88.2/34538 --> 75.77.77.2/23;tcp, If: reth1.0, Pkts: 33, Bytes: 1881
Out: 75.77.77.2/23 --> 85.88.88.2/34538;tcp, If: reth2.0, Pkts: 28, Bytes: 2329
Total sessions: 1
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Session ID: 90000001, Policy name: lsys1trust-to-lsys1untrust/8, State: Backup, Timeout: 14388, Valid
In: 85.88.88.2/34538 --> 75.77.77.2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 75.77.77.2/23 --> 85.88.88.2/34538;tcp, If: reth2.0, Pkts: 0, Bytes: 0
Total sessions: 1
验证所有逻辑系统内的逻辑系统内流量
目的
验证有关所有逻辑系统上当前活动安全会话的信息。
行动
在作模式下,输入命令 show security flow session logical-system all 。
{primary:node0}
user@host> show security flow session logical-system all
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Session ID: 90000114, Policy name: lsys1trust-to-lsys1untrust/8, State: Active, Timeout: 1776, Valid
Logical system: LSYS1
In: 85.88.88.2/34538 --> 75.77.77.2/23;tcp, If: reth1.0, Pkts: 33, Bytes: 1881
Out: 75.77.77.2/23 --> 85.88.88.2/34538;tcp, If: reth2.0, Pkts: 28, Bytes: 2329
Total sessions: 1
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Session ID: 90000001, Policy name: lsys1trust-to-lsys1untrust/8, State: Backup, Timeout: 14382, Valid
Logical system: LSYS1
In: 85.88.88.2/34538 --> 75.77.77.2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 75.77.77.2/23 --> 85.88.88.2/34538;tcp, If: reth2.0, Pkts: 0, Bytes: 0
Total sessions: 1
验证用户逻辑系统之间的流量
目的
验证有关逻辑系统之间当前活动安全会话的信息。
行动
在作模式下,输入命令 show security flow session logical-system logical-system-name 。
{primary:node0}
user@host> show security flow session logical-system LSYS1
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Session ID: 10000094, Policy name: root-Untrust_to_root-Trust/5, State: Active, Timeout: 1768, Valid
In: 75.77.77.2/34590 --> 95.99.99.2/23;tcp, If: lt-0/0/0.1, Pkts: 23, Bytes: 1351
Out: 95.99.99.2/23 --> 75.77.77.2/34590;tcp, If: reth0.0, Pkts: 22, Bytes: 1880
Total sessions: 1
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Session ID: 10000002, Policy name: root-Untrust_to_root-Trust/5, State: Backup, Timeout: 14384, Valid
In: 75.77.77.2/34590 --> 95.99.99.2/23;tcp, If: lt-0/0/0.1, Pkts: 0, Bytes: 0
Out: 95.99.99.2/23 --> 75.77.77.2/34590;tcp, If: reth0.0, Pkts: 0, Bytes: 0
Total sessions: 1
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Total sessions: 0
{primary:node0}
user@host> show security flow session logical-system LSYS2
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000089, Policy name: lsys2untrust-to-lsys2trust/13, State: Active, Timeout: 1790, Valid
In: 85.88.88.2/34539 --> 65.66.66.2/23;tcp, If: lt-0/0/0.5, Pkts: 40, Bytes: 2252
Out: 65.66.66.2/23 --> 85.88.88.2/34539;tcp, If: reth3.0, Pkts: 32, Bytes: 2114
Total sessions: 1
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000002, Policy name: lsys2untrust-to-lsys2trust/13, State: Backup, Timeout: 14398, Valid
In: 85.88.88.2/34539 --> 65.66.66.2/23;tcp, If: lt-0/0/0.5, Pkts: 0, Bytes: 0
Out: 65.66.66.2/23 --> 85.88.88.2/34539;tcp, If: reth3.0, Pkts: 0, Bytes: 0
Total sessions: 1
Flow Sessions on FPC2 PIC1:
Total sessions: 0
{primary:node0}
user@host> show security flow session logical-system all
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000088, Policy name: lsys1trust-to-lsys1trust/11, State: Active, Timeout: 1782, Valid
Logical system: LSYS1
In: 85.88.88.2/34539 --> 65.66.66.2/23;tcp, If: reth1.0, Pkts: 40, Bytes: 2252
Out: 65.66.66.2/23 --> 85.88.88.2/34539;tcp, If: lt-0/0/0.3, Pkts: 32, Bytes: 2114
Session ID: 80000089, Policy name: lsys2untrust-to-lsys2trust/13, State: Active, Timeout: 1782, Valid
Logical system: LSYS2
In: 85.88.88.2/34539 --> 65.66.66.2/23;tcp, If: lt-0/0/0.5, Pkts: 40, Bytes: 2252
Out: 65.66.66.2/23 --> 85.88.88.2/34539;tcp, If: reth3.0, Pkts: 32, Bytes: 2114
Total sessions: 2
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000001, Policy name: lsys1trust-to-lsys1trust/11, State: Backup, Timeout: 14382, Valid
Logical system: LSYS1
In: 85.88.88.2/34539 --> 65.66.66.2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 65.66.66.2/23 --> 85.88.88.2/34539;tcp, If: lt-0/0/0.3, Pkts: 0, Bytes: 0
Session ID: 80000002, Policy name: lsys2untrust-to-lsys2trust/13, State: Backup, Timeout: 14390, Valid
Logical system: LSYS2
In: 85.88.88.2/34539 --> 65.66.66.2/23;tcp, If: lt-0/0/0.5, Pkts: 0, Bytes: 0
Out: 65.66.66.2/23 --> 85.88.88.2/34539;tcp, If: reth3.0, Pkts: 0, Bytes: 0
Total sessions: 2
Flow Sessions on FPC2 PIC1:
Total sessions: 0
示例:在主动/被动机箱群集中配置逻辑系统 (IPv6)(仅限主管理员)
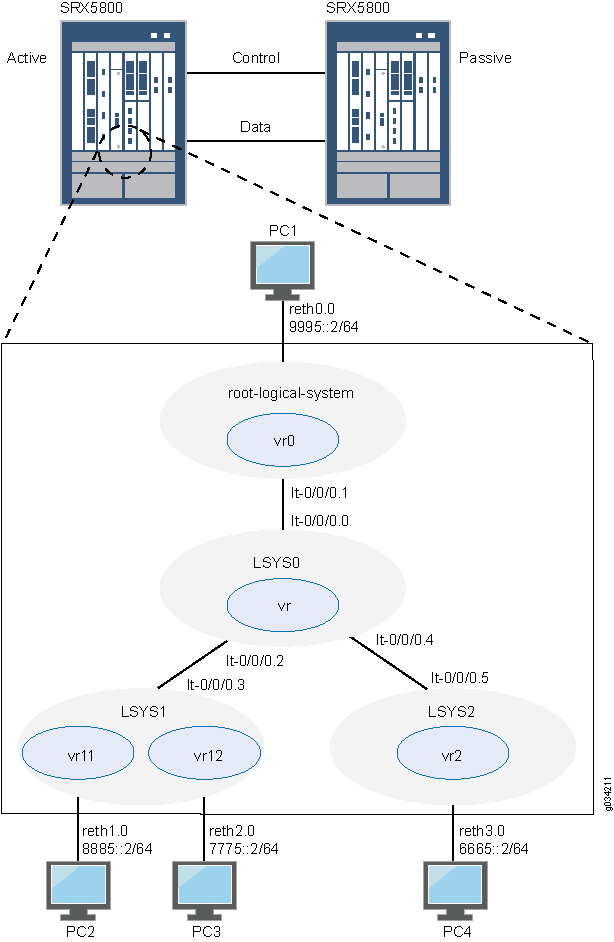
此示例说明如何在具有 IPv6 地址的基本主动/被动机箱群集中配置逻辑系统。
主管理员负责配置机箱群集,并创建逻辑系统(包括可选的互连逻辑系统)、管理员和安全配置文件。主管理员或用户逻辑系统管理员可配置用户逻辑系统。配置在群集中的节点之间同步。
要求
开始之前:
-
获取两个硬件配置相同的 SRX 系列防火墙。请参阅 示例:在 SRX5800 设备上配置主动/被动机箱群集。此机箱群集部署方案包括用于连接到 MX240 边缘路由器和 EX8208 以太网交换机的 SRX 系列防火墙配置。
-
物理连接两台设备(背对背连接交换矩阵和控制端口),并确保其型号相同。您可以在 SRX5000 系列上配置交换矩阵端口和控制端口。对于 SRX1400 或 SRX1500 设备或者 SRX3000 系列,只能配置交换矩阵端口。(平台是否支持取决于设备安装的 Junos OS 版本。)
-
在每台设备上设置机箱群集 ID 和节点 ID,然后重新启动设备以启用群集。请参阅 示例:为机箱群集中的安全性设备设置节点 ID 和群集 ID 。
在此示例中,机箱群集和逻辑系统配置由主管理员在根级别的主(节点 0)设备上执行。以主管理员身份登录设备。请参阅 了解主逻辑系统和主管理员角色。
使用SRX 系列防火墙在机箱群集中运行逻辑系统时,必须为机箱群集中的每个节点购买并安装相同数量的逻辑系统许可证。逻辑系统许可证与机箱群集内的单个机箱或节点相关,而非该群集的全部内容。
概述
在此示例中,基本的主动/被动机箱群集由两台设备组成:
-
一台设备会主动提供逻辑系统,并保持对机箱群集的控制。
-
如果活动设备变为非活动状态,另一台设备会被动维护其群集故障切换功能的状态。
主动/主动机箱群集中的逻辑系统的配置方式与主动/被动机箱群集中的逻辑系统类似。对于主动/主动机箱群集,可以存在多个冗余组,这些组可以在不同节点上作为主节点。
主管理员在主设备(节点 0)上配置以下逻辑系统:
-
主逻辑系统 — 主管理员配置安全配置文件,以便将部分系统安全资源配置到主逻辑系统,并配置主逻辑系统的资源。
-
用户逻辑系统 LSYS1 和 LSYS2 及其管理员 — 主管理员还可配置安全配置文件,以便将部分系统安全资源配置到用户逻辑系统。然后,用户逻辑系统管理员可以配置分配给其逻辑系统的接口、路由和安全资源。
-
连接设备上逻辑系统的互连逻辑系统 LSYS0 — 主管理员在互连逻辑系统和每个逻辑系统之间配置逻辑隧道接口。这些对等接口有效地允许建立隧道。
此示例不介绍如何为逻辑系统配置 NAT、IDP 或 VPN 等功能。有关可为逻辑系统配置的功能的更多信息,请参阅 SRX 系列逻辑系统主管理员配置任务概述 和 用户逻辑系统配置概述 。
如果在机箱群集配置中执行代理 ARP,则必须将代理 ARP 配置应用于 reth 接口,而不是成员接口,因为 reth 接口包含逻辑配置。请参阅为 NAT 配置代理 ARP (CLI 过程)。
配置
使用 IPv6 地址的机箱群集配置(主管理员)
CLI 快速配置
要快速创建逻辑系统和用户逻辑系统管理员并配置主逻辑系统和互连逻辑系统,请将以下命令复制粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到层次结构级别的 [edit] CLI 中。
在 {primary:node0} 上
set chassis cluster control-ports fpc 0 port 0
set chassis cluster control-ports fpc 6 port 0
set interfaces fab0 fabric-options member-interfaces ge-1/1/0
set interfaces fab1 fabric-options member-interfaces ge-7/1/0
set groups node0 system host-name SRX5800-1
set groups node0 interfaces fxp0 unit 0 family inet address 10.157.90.24/9
set groups node0 system backup-router 10.157.64.1 destination 0.0.0.0/0
set groups node1 system host-name SRX5800-2
set groups node1 interfaces fxp0 unit 0 family inet address 10.157.90.23/19
set groups node1 system backup-router 10.157.64.1 destination 0.0.0.0/0
set apply-groups “${node}”
set chassis cluster reth-count 5
set chassis cluster redundancy-group 0 node 0 priority 200
set chassis cluster redundancy-group 0 node 1 priority 100
set chassis cluster redundancy-group 1 node 0 priority 200
set chassis cluster redundancy-group 1 node 1 priority 100
set interfaces ge-1/0/0 gigether-options redundant-parent reth0
set interfaces ge-1/0/1 gigether-options redundant-parent reth1
set interfaces ge-1/0/2 gigether-options redundant-parent reth2
set interfaces ge-1/0/3 gigether-options redundant-parent reth3
set interfaces ge-7/0/0 gigether-options redundant-parent reth0
set interfaces ge-7/0/1 gigether-options redundant-parent reth1
set interfaces ge-7/0/2 gigether-options redundant-parent reth2
set interfaces ge-7/0/3 gigether-options redundant-parent reth3
set interfaces reth0 redundant-ether-options redundancy-group 1
set interfaces reth0 unit 0 family inet6 address 9995::1/64
set interfaces reth1 redundant-ether-options redundancy-group 1
set interfaces reth2 redundant-ether-options redundancy-group 1
set interfaces reth3 redundant-ether-options redundancy-group 1
分步程序
下面的示例要求您在各个配置层级中进行导航。有关作说明,请参阅《Junos OS CLI 用户指南》中的在 配置模式下使用CLI编辑器 。
要配置机箱群集,请执行以下作:
在主设备(节点 0)上执行以下步骤。当您执行 commit 命令时,它们会自动复制到辅助设备(节点 1)。
-
为群集配置控制端口。
[edit chassis cluster] user@host# set control-ports fpc 0 port 0 user@host# set control-ports fpc 6 port 0
-
配置用于在主动/被动模式下传递 RTO 的群集的交换矩阵(数据)端口。
[edit interfaces] user@host# set fab0 fabric-options member-interfaces ge-1/1/0 user@host# set fab1 fabric-options member-interfaces ge-7/1/0
-
将配置的某些元素分配给特定成员。在 SRX 服务网关的 fxp0 接口上为群集的各个控制平面使用单独的 IP 地址配置带外管理。
[edit] user@host# set groups node0 system host-name SRX5800-1 user@host# set groups node0 interfaces fxp0 unit 0 family inet address 10.157.90.24/9 user@host# set groups node0 system backup-router 10.157.64.1 destination 0.0.0.0/0 user@host# set groups node1 system host-name SRX5800-2 user@host# set groups node1 interfaces fxp0 unit 0 family inet address 10.157.90.23/19 user@host# set groups node1 system backup-router 10.157.64.1 destination 0.0.0.0/0 user@host# set apply-groups “${node}” -
为机箱群集配置冗余组。
[edit chassis cluster] user@host# set reth-count 5 user@host# set redundancy-group 0 node 0 priority 200 user@host# set redundancy-group 0 node 1 priority 100 user@host# set redundancy-group 1 node 0 priority 200 user@host# set redundancy-group 1 node 1 priority 100
-
配置平台上的数据接口,以便在发生数据平面故障切换时,其他机箱群集成员可以无缝接管连接。
[edit interfaces] user@host# set ge-1/0/0 gigether-options redundant-parent reth0 user@host# set ge-1/0/1 gigether-options redundant-parent reth1 user@host# set ge-1/0/2 gigether-options redundant-parent reth2 user@host# set ge-1/0/3 gigether-options redundant-parent reth3 user@host# set ge-7/0/0 gigether-options redundant-parent reth0 user@host# set ge-7/0/1 gigether-options redundant-parent reth1 user@host# set ge-7/0/2 gigether-options redundant-parent reth2 user@host# set ge-7/0/3 gigether-options redundant-parent reth3 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet6 address 9995::1/64 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth2 redundant-ether-options redundancy-group 1 user@host# set reth3 redundant-ether-options redundancy-group 1
结果
在作模式下,输入 show configuration 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
user@host> show configuration
version ;
groups {
node0 {
system {
host-name SRX58001;
backup-router 10.157.64.1 destination 0.0.0.0/0;
}
interfaces {
fxp0 {
unit 0 {
family inet {
address 10.157.90.24/9;
}
}
}
}
}
node1 {
system {
host-name SRX58002;
backup-router 10.157.64.1 destination 0.0.0.0/0;
}
interfaces {
fxp0 {
unit 0 {
family inet {
address 10.157.90.23/19;
}
}
}
}
}
}
apply-groups "${node}";
chassis {
cluster {
control-link-recovery;
reth-count 5;
control-ports {
fpc 0 port 0;
fpc 6 port 0;
}
redundancy-group 0 {
node 0 priority 200;
node 1 priority 100;
}
redundancy-group 1 {
node 0 priority 200;
node 1 priority 100;
}
}
}
interfaces {
ge-1/0/0 {
gigether–options {
redundant–parent reth0;
}
}
ge-1/0/1 {
gigether–options {
redundant–parent reth1;
}
}
ge-1/0/2 {
gigether–options {
redundant–parent reth2;
}
}
ge-1/0/3 {
gigether–options {
redundant–parent reth3;
}
}
ge-7/0/0 {
gigether–options {
redundant–parent reth0;
}
}
ge-7/0/1 {
gigether–options {
redundant–parent reth1;
}
}
ge-7/0/2 {
gigether–options {
redundant–parent reth2;
}
}
ge-7/0/3 {
gigether–options {
redundant–parent reth3;
}
}
fab0 {
fabric–options {
member–interfaces {
ge-1/1/0;
}
}
}
fab1 {
fabric–options {
member–interfaces {
ge-7/1/0;
}
}
}
reth0 {
redundant–ether–options {
redundancy–group 1;
}
unit 0 {
family inet6 {
address 9995::1/64;
}
}
}
reth1 {
redundant–ether–options {
redundancy–group 1;
}
}
reth2 {
redundant–ether–options {
redundancy–group 1;
}
}
reth3 {
redundant–ether–options {
redundancy–group 1;
}
}
}
使用 IPv6 地址的逻辑系统配置(主管理员)
CLI 快速配置
要快速创建逻辑系统和用户逻辑系统管理员并配置主逻辑系统和互连逻辑系统,请将以下命令复制粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到层次结构级别的 [edit] CLI 中。
系统会提示您输入纯文本密码,然后再次输入。
在 {primary:node0} 上
set logical-systems LSYS1 set logical-systems LSYS2 set logical-systems LSYS0 set system login class lsys1 logical-system LSYS1 set system login class lsys1 permissions all set system login user lsys1admin full-name lsys1-admin set system login user lsys1admin class lsys1 set user lsys1admin authentication plain-text-password set system login class lsys2 logical-system LSYS2 set system login class lsys2 permissions all set system login user lsys2admin full-name lsys2-admin set system login user lsys2admin class lsys2 set system login user lsys2admin authentication plain-text-password set system security-profile SP-root policy maximum 200 set system security-profile SP-root policy reserved 100 set system security-profile SP-root zone maximum 200 set system security-profile SP-root zone reserved 100 set system security-profile SP-root flow-session maximum 200 set system security-profile SP-root flow-session reserved 100 set system security-profile SP-root root-logical-system set system security-profile SP0 logical-system LSYS0 set system security-profile SP1 policy maximum 100 set system security-profile SP1 policy reserved 50 set system security-profile SP1 zone maximum 100 set system security-profile SP1 zone reserved 50 set system security-profile SP1 flow-session maximum 100 set system security-profile SP1 flow-session reserved 50 set system security-profile SP1 logical-system LSYS1 set system security-profile SP2 policy maximum 100 set system security-profile SP2 policy reserved 50 set system security-profile SP2 zone maximum 100 set system security-profile SP2 zone reserved 50 set system security-profile SP2 flow-session maximum 100 set system security-profile SP2 flow-session reserved 50 set system security-profile SP2 logical-system LSYS2 set interfaces lt-0/0/0 unit 1 encapsulation ethernet set interfaces lt-0/0/0 unit 1 peer-unit 0 set interfaces lt-0/0/0 unit 1 family inet6 address 2111::1/64 set routing-instances vr0 instance-type virtual-router set routing-instances vr0 interface lt-0/0/0.1 set routing-instances vr0 interface reth0.0 set routing-instances vr0 routing-options rib vr0.inet6.0 static route 8885::/64 next-hop 2111::3 set routing-instances vr0 routing-options rib vr0.inet6.0 static route 7775::/64 next-hop 2111::3 set routing-instances vr0 routing-options rib vr0.inet6.0 static route 6665::/64 next-hop 2111::5 set security zones security-zone root-trust host-inbound-traffic system-services all set security zones security-zone root-trust host-inbound-traffic protocols all set security zones security-zone root-trust interfaces reth0.0 set security zones security-zone root-untrust host-inbound-traffic system-services all set security zones security-zone root-untrust host-inbound-traffic protocols all set security zones security-zone root-untrust interfaces lt-0/0/0.1 set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust match source-address any set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust match destination-address any set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust match application any set security policies from-zone root-trust to-zone root-untrust policy root-Trust_to_root-Untrust then permit set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust match source-address any set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust match destination-address any set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust match application any set security policies from-zone root-untrust to-zone root-trust policy root-Untrust_to_root-Trust then permit set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust match source-address any set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust match destination-address any set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust match application any set security policies from-zone root-untrust to-zone root-untrust policy root-Untrust_to_root-Untrust then permit set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust match source-address any set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust match destination-address any set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust match application any set security policies from-zone root-trust to-zone root-trust policy root-Trust_to_root-Trust then permit set logical-systems LSYS0 interfaces lt-0/0/0 unit 0 encapsulation ethernet-vpls set logical-systems LSYS0 interfaces lt-0/0/0 unit 0 peer-unit 1 set logical-systems LSYS0 interfaces lt-0/0/0 unit 2 encapsulation ethernet-vpls set logical-systems LSYS0 interfaces lt-0/0/0 unit 2 peer-unit 3 set logical-systems LSYS0 interfaces lt-0/0/0 unit 4 encapsulation ethernet-vpls set logical-systems LSYS0 interfaces lt-0/0/0 unit 4 peer-unit 5 set logical-systems LSYS0 routing-instances vr instance-type vpls set logical-systems LSYS0 routing-instances vr interface lt-0/0/0.0 set logical-systems LSYS0 routing-instances vr interface lt-0/0/0.2 set logical-systems LSYS0 routing-instances vr interface lt-0/0/0.4 set logical-systems LSYS1 interfaces lt-0/0/0 unit 3 encapsulation ethernet set logical-systems LSYS1 interfaces lt-0/0/0 unit 3 peer-unit 2 set logical-systems LSYS1 interfaces lt-0/0/0 unit 3 family inet6 address 2111::3/64 set logical-systems LSYS2 interfaces lt-0/0/0 unit 5 encapsulation ethernet set logical-systems LSYS2 interfaces lt-0/0/0 unit 5 peer-unit 4 set logical-systems LSYS2 interfaces lt-0/0/0 unit 5 family inet6 address 2111::5/64
分步程序
下面的示例要求您在各个配置层级中进行导航。有关作说明,请参阅在 配置模式下使用 CLI 编辑器。
要创建逻辑系统和用户逻辑系统管理员并配置主逻辑系统和互连逻辑系统,请执行以下作:
-
创建互连和用户逻辑系统。
[edit logical-systems] user@host# set LSYS0 user@host# set LSYS1 user@host# set LSYS2
-
配置用户逻辑系统管理员。
分步程序
-
为 LSYS1 配置用户逻辑系统管理员。
[edit system login] user@host# set class lsys1 logical-system LSYS1 user@host# set class lsys1 permissions all user@host# set user lsys1admin full-name lsys1-admin user@host# set user lsys1admin class lsys1 user@host# set user lsys1admin authentication plain-text-password
-
为 LSYS2 配置用户逻辑系统管理员。
[edit system login] user@host# set class lsys2 logical-system LSYS2 user@host# set class lsys2 permissions all user@host# set user lsys2admin full-name lsys2-admin user@host# set user lsys2admin class lsys2 user@host# set user lsys2admin authentication plain-text-password
-
-
配置安全配置文件并将其分配给逻辑系统。
分步程序
-
配置安全配置文件并将其分配给根逻辑系统。
[edit system security-profile] user@host# set SP-root policy maximum 200 user@host# set SP-root policy reserved 100 user@host# set SP-root zone maximum 200 user@host# set SP-root zone reserved 100 user@host# set SP-root flow-session maximum 200 user@host# set SP-root flow-session reserved 100 user@host# set SP-root root-logical-system
-
将不包含资源的虚拟安全配置文件分配给互连逻辑系统 LSYS0。
[edit system security-profile] user@host# set SP0 logical-system LSYS0 -
配置安全配置文件并将其分配给 LSYS1。
[edit system security-profile] user@host# set SP1 policy maximum 100 user@host# set SP1 policy reserved 50 user@host# set SP1 zone maximum 100 user@host# set SP1 zone reserved 50 user@host# set SP1 flow-session maximum 100 user@host# set SP1 flow-session reserved 50 user@host# set SP1 logical-system LSYS1
-
配置安全配置文件并将其分配给 LSYS2。
[edit system security-profile] user@host# set SP2 policy maximum 100 user@host# set SP2 policy reserved 50 user@host# set SP2 zone maximum 100 user@host# set SP2 zone reserved 50 user@host# set SP2 flow-session maximum 100 user@host# set SP2 flow-session reserved 50 user@host# set SP2 logical-system LSYS2
-
-
配置主逻辑系统。
分步程序
-
配置逻辑隧道接口。
[edit interfaces] user@host# set lt-0/0/0 unit 1 encapsulation ethernet user@host# set lt-0/0/0 unit 1 peer-unit 0 user@host# set lt-0/0/0 unit 1 family inet6 address 2111::1/64
-
配置路由实例。
[edit routing-instances] user@host# set vr0 instance-type virtual-router user@host# set vr0 interface lt-0/0/0.1 user@host# set vr0 interface reth0.0 user@host# set vr0 routing-options rib vr0.inet6.0 static route 8885::/64 next-hop 2111::3 user@host# set vr0 routing-options rib vr0.inet6.0 static route 7775::/64 next-hop 2111::3 user@host# set vr0 routing-options rib vr0.inet6.0 static route 6665::/64 next-hop 2111::5
-
配置区域。
[edit security zones] user@host# set security-zone root-trust host-inbound-traffic system-services all user@host# set security-zone root-trust host-inbound-traffic protocols all user@host# set security-zone root-trust interfaces reth0.0 user@host# set security-zone root-untrust host-inbound-traffic system-services all user@host# set security-zone root-untrust host-inbound-traffic protocols all user@host# set security-zone root-untrust interfaces lt-0/0/0.1
-
配置安全策略。
[edit security policies from-zone root-trust to-zone root-untrust] user@host# set policy root-Trust_to_root-Untrust match source-address any user@host# set policy root-Trust_to_root-Untrust match destination-address any user@host# set policy root-Trust_to_root-Untrust match application any user@host# set policy root-Trust_to_root-Untrust then permit
[edit security policies from-zone root-untrust to-zone root-trust] user@host# set policy root-Untrust_to_root-Trust match source-address any user@host# set policy root-Untrust_to_root-Trust match destination-address any user@host# set policy root-Untrust_to_root-Trust match application any user@host# set policy root-Untrust_to_root-Trust then permit
[edit security policies from-zone root-untrust to-zone root-untrust] user@host# set policy root-Untrust_to_root-Untrust match source-address any user@host# set policy root-Untrust_to_root-Untrust match destination-address any user@host# set policy root-Untrust_to_root-Untrust match application any user@host# set policy root-Untrust_to_root-Untrust then permit
[edit security policies from-zone root-trust to-zone root-trust] user@host# set policy root-Trust_to_root-Trust match source-address any user@host# set policy root-Trust_to_root-Trust match destination-address any user@host# set policy root-Trust_to_root-Trust match application any user@host# set policy root-Trust_to_root-Trust then permit
-
-
配置互连逻辑系统。
分步程序
-
配置逻辑隧道接口。
[edit logical-systems LSYS0 interfaces] user@host# set lt-0/0/0 unit 0 encapsulation ethernet-vpls user@host# set lt-0/0/0 unit 0 peer-unit 1 user@host# set lt-0/0/0 unit 2 encapsulation ethernet-vpls user@host# set lt-0/0/0 unit 2 peer-unit 3 user@host# set lt-0/0/0 unit 4 encapsulation ethernet-vpls user@host# set lt-0/0/0 unit 4 peer-unit 5
-
配置 VPLS 路由实例。
[edit logical-systems LSYS0 routing-instances] user@host# set vr instance-type vpls user@host# set vr interface lt-0/0/0.0 user@host# set vr interface lt-0/0/0.2 user@host# set vr interface lt-0/0/0.4
-
-
为用户逻辑系统配置逻辑隧道接口。
分步程序
-
为 LSYS1 配置逻辑隧道接口。
[edit logical-systems LSYS1 interfaces ] user@host# set lt-0/0/0 unit 3 encapsulation ethernet user@host# set lt-0/0/0 unit 3 peer-unit 2 user@host# set lt-0/0/0 unit 3 family inet6 address 2111::3/64
-
为 LSYS2 配置逻辑隧道接口。
[edit logical-systems LSYS2 interfaces ] user@host# set lt-0/0/0 unit 5 encapsulation ethernet user@host# set lt-0/0/0 unit 5 peer-unit 4 user@host# set lt-0/0/0 unit 5 family inet6 address 2111::5/64
-
结果
在配置模式下,输入 show logical-systems LSYS0 命令以确认 LSYS0 的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
user@host# show logical-systems LSYS0
interfaces {
lt-0/0/0 {
unit 0 {
encapsulation ethernet-vpls;
peer-unit 1;
}
unit 2 {
encapsulation ethernet-vpls;
peer-unit 3;
}
unit 4 {
encapsulation ethernet-vpls;
peer-unit 5;
}
}
}
routing-instances {
vr {
instance-type vpls;
interface lt-0/0/0.0;
interface lt-0/0/0.2;
interface lt-0/0/0.4;
}
}
在配置模式下,输入 show interfaces、 show routing-instances和 show security 命令确认主逻辑系统的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
user@host# show interfaces
lt-0/0/0 {
unit 1 {
encapsulation ethernet;
peer-unit 0;
family inet6 {
address 2111::1/64;
}
}
}
ge-1/0/0 {
gigether-options {
redundant-parent reth0;
}
}
ge-1/0/1 {
gigether-options {
redundant-parent reth1;
}
}
ge-1/0/2 {
gigether-options {
redundant-parent reth2;
}
}
ge-1/0/3 {
gigether-options {
redundant-parent reth3;
}
}
ge-7/0/0 {
gigether-options {
redundant-parent reth0;
}
}
ge-7/0/1 {
gigether-options {
redundant-parent reth1;
}
}
ge-7/0/2 {
gigether-options {
redundant-parent reth2;
}
}
ge-7/0/3 {
gigether-options {
redundant-parent reth3;
}
}
fab0 {
fabric-options {
member-interfaces {
ge-1/1/0;
}
}
}
fab1 {
fabric-options {
member-interfaces {
ge-7/1/0;
}
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet6 {
address 9995::1/64;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
}
reth2 {
redundant-ether-options {
redundancy-group 1;
}
}
reth3 {
redundant-ether-options {
redundancy-group 1;
}
}
[edit]
user@host# show routing-instances
vr0 {
instance-type virtual-router;
interface lt-0/0/0.1;
interface reth0.0;
routing-options {
rib vr0.inet6.0 {
static {
route 8885::/64 next-hop 2111::3;
route 7775::/64 next-hop 2111::3;
route 6665::/64 next-hop 2111::5;
}
}
}
}
[edit]
user@host# show security
policies {
from-zone root-trust to-zone root-untrust {
policy root-Trust_to_root-Untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone root-untrust to-zone root-trust {
policy root-Untrust_to_root-Trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone root-untrust to-zone root-untrust {
policy root-Untrust_to_root-Untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone root-trust to-zone root-trust {
policy root-Trust_to_root-Trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone root-trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth0.0;
}
}
security-zone root-untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lt-0/0/0.1;
}
}
}
如果完成设备配置,请从配置模式进入。commit
使用 IPv6 进行用户逻辑系统配置(用户逻辑系统管理员)
CLI 快速配置
要快速配置用户逻辑系统,请复制以下命令,将其粘贴到文本文件中,移除所有换行符,更改任何必要的详细信息以匹配您的网络配置,然后将命令复制粘贴到层次结构级别的 [edit] CLI 中。
以 LSYS1 的用户逻辑系统管理员身份登录时,输入以下命令:
set interfaces reth1 unit 0 family inet6 address 8885::1/64 set interfaces reth2 unit 0 family inet6 address 7775::1/64 set routing-instances vr11 instance-type virtual-router set routing-instances vr11 interface lt-0/0/0.3 set routing-instances vr11 interface reth1.0 set routing-instances vr11 routing-options rib vr11.inet6.0 static route 6665::/64 next-hop 2111::5 set routing-instances vr11 routing-options rib vr11.inet6.0 static route 9995::/64 next-hop 2111::1 set routing-instances vr12 instance-type virtual-router set routing-instances vr12 interface reth2.0 set routing-instances vr12 routing-options interface-routes rib-group inet6 vr11vr12v6 set routing-instances vr12 rrouting-options rib vr12.inet6.0 static route 8885::/64 next-table vr11.inet6.0 set routing-instances vr12 routing-options rib vr12.inet6.0 static route 9995::/64 next-table vr11.inet6.0 set routing-instances vr12 routing-options rib vr12.inet6.0 static route 6665::/64 next-table vr11.inet6.0 set routing-instances vr12 routing-options rib vr12.inet6.0 static route 2111::/64 next-table vr11.inet6.0 set routing-options rib-groups vr11vr12v6 import-rib vr11.inet6.0 set routing-options rib-groups vr11vr12v6 import-rib vr12.inet6.0 set security zones security-zone lsys1-trust host-inbound-traffic system-services all set security zones security-zone lsys1-trust host-inbound-traffic protocols all set security zones security-zone lsys1-trust interfaces reth1.0 set security zones security-zone lsys1-trust interfaces lt-0/0/0.3 set security zones security-zone lsys1-untrust host-inbound-traffic system-services all set security zones security-zone lsys1-untrust host-inbound-traffic protocols all set security zones security-zone lsys1-untrust interfaces reth2.0 set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust match source-address any set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust match destination-address any set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust match application any set security policies from-zone lsys1-trust to-zone lsys1-untrust policy lsys1trust-to-lsys1untrust then permit set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust match source-address any set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust match destination-address any set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust match application any set security policies from-zone lsys1-untrust to-zone lsys1-trust policy lsys1untrust-to-lsys1trust then permit set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust match source-address any set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust match destination-address any set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust match application any set security policies from-zone lsys1-untrust to-zone lsys1-untrust policy lsys1untrust-to-lsys1untrust then permit set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust match source-address any set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust match destination-address any set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust match application any set security policies from-zone lsys1-trust to-zone lsys1-trust policy lsys1trust-to-lsys1trust then permit
以 LSYS2 的用户逻辑系统管理员身份登录时,输入以下命令:
set interfaces reth3 unit 0 family inet6 address 6665::1/64 set routing-instances vr2 instance-type virtual-router set routing-instances vr2 interface lt-0/0/0.5 set routing-instances vr2 interface reth3.0 set routing-instances vr2 routing-options rib vr2.inet6.0 static route 7775::/64 next-hop 2111::3 set routing-instances vr2 routing-options rib vr2.inet6.0 static route 8885::/64 next-hop 2111::3 set routing-instances vr2 routing-options rib vr2.inet6.0 static route 9995::/64 next-hop 2111::1 set security zones security-zone lsys2-trust host-inbound-traffic system-services all set security zones security-zone lsys2-trust host-inbound-traffic protocols all set security zones security-zone lsys2-trust interfaces reth3.0 set security zones security-zone lsys2-untrust host-inbound-traffic system-services all set security zones security-zone lsys2-untrust host-inbound-traffic protocols all set security zones security-zone lsys2-untrust interfaces lt-0/0/0.5 set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust match source-address any set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust match destination-address any set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust match application any set security policies from-zone lsys2-trust to-zone lsys2-untrust policy lsys2trust-to-lsys2untrust then permit set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust match source-address any set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust match destination-address any set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust match application any set security policies from-zone lsys2-untrust to-zone lsys2-trust policy lsys2untrust-to-lsys2trust then permit set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust match source-address any set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust match destination-address any set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust match application any set security policies from-zone lsys2-untrust to-zone lsys2-untrust policy lsys2untrust-to-lsys2untrust then permit set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust match source-address any set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust match destination-address any set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust match application any set security policies from-zone lsys2-trust to-zone lsys2-trust policy lsys2trust-to-lsys2trust then permit
分步程序
用户逻辑系统管理员在登录到其用户逻辑系统时执行以下配置。主管理员还可以在 [edit logical-systems logical-system] 层级配置用户逻辑系统。
下面的示例要求您在各个配置层级中进行导航。有关作说明,请参阅在 配置模式下使用 CLI 编辑器。
要配置 LSYS1 用户逻辑系统,请执行以下作:
-
配置接口。
[edit interfaces] lsys1-admin@host:LSYS1# set reth1 unit 0 family inet6 address 8885::1/64 lsys1-admin@host:LSYS1# set reth2 unit 0 family inet6 address 7775::1/64
-
配置路由。
[edit routing-instances] lsys1-admin@host:LSYS1# set vr11 instance-type virtual-router lsys1-admin@host:LSYS1# set vr11 interface lt-0/0/0.3 lsys1-admin@host:LSYS1# set vr11 interface reth1.0 lsys1-admin@host:LSYS1# set vr11 routing-options rib vr11.inet6.0 static route 6665::/64 next-hop 2111::5 lsys1-admin@host:LSYS1# set vr11 routing-options rib vr11.inet6.0 static route 9995::/64 next-hop 2111::1 lsys1-admin@host:LSYS1# set vr12 instance-type virtual-router lsys1-admin@host:LSYS1# set vr12 interface reth2.0 lsys1-admin@host:LSYS1# set vr12 routing-options interface-routes rib-group inet6 vr11vr12v6 lsys1-admin@host:LSYS1# set vr12 routing-options rib vr12.inet6.0 static route 8885::/64 next-table vr11.inet6.0 lsys1-admin@host:LSYS1# set vr12 routing-options rib vr12.inet6.0 static route 9995::/64 next-table vr11.inet6.0 lsys1-admin@host:LSYS1# set vr12 routing-options rib vr12.inet6.0 static route 6665::/64 next-table vr11.inet6.0 lsys1-admin@host:LSYS1# set vr12 routing-options rib vr12.inet6.0 static route 2111::/64 next-table vr11.inet6.0
[edit routing-options] lsys1-admin@host:LSYS1# set rib-groups vr11vr12v6 import-rib vr11.inet6.0 lsys1-admin@host:LSYS1# set rib-groups vr11vr12v6 import-rib vr12.inet6.0
-
配置区域和安全策略。
[edit security zones] lsys1-admin@host:LSYS1# set security-zone lsys1-trust host-inbound-traffic system-services all lsys1-admin@host:LSYS1# set security-zone lsys1-trust host-inbound-traffic protocols all lsys1-admin@host:LSYS1# set security-zone lsys1-trust interfaces reth1.0 lsys1-admin@host:LSYS1# set security-zone lsys1-trust interfaces lt-0/0/0.3 lsys1-admin@host:LSYS1# set security-zone lsys1-untrust host-inbound-traffic system-services all lsys1-admin@host:LSYS1# set security-zone lsys1-untrust host-inbound-traffic protocols all lsys1-admin@host:LSYS1# set security-zone lsys1-untrust interfaces reth2.0
[edit security policies from-zone lsys1-trust to-zone lsys1-untrust] lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust match source-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust match application any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1untrust then permit
[edit security policies from-zone lsys1-untrust to-zone lsys1-trust] lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust match source-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust match application any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1trust then permit
[edit security policies from-zone lsys1-untrust to-zone lsys1-untrust] lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust match source-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust match application any lsys1-admin@host:LSYS1# set policy lsys1untrust-to-lsys1untrust then permit
[edit security policies from-zone lsys1-trust to-zone lsys1-trust] lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust match source-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust match destination-address any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust match application any lsys1-admin@host:LSYS1# set policy lsys1trust-to-lsys1trust then permit
分步程序
要配置 LSYS2 用户逻辑系统,请执行以下作:
-
配置接口。
[edit interfaces] lsys2-admin@host:LSYS2# set reth3 unit 0 family inet6 address 6665::1/64
-
配置路由。
[edit routing-instances] lsys2-admin@host:LSYS2# set vr2 instance-type virtual-router lsys2-admin@host:LSYS2# set vr2 interface lt-0/0/0.5 lsys2-admin@host:LSYS2# set vr2 interface reth3.0 lsys2-admin@host:LSYS2# set vr2 routing-options rib vr2.inet6.0 static route 7775::/64 next-hop 2111::3 lsys2-admin@host:LSYS2# set vr2 routing-options rib vr2.inet6.0 static route 8885::/64 next-hop 2111::3 lsys2-admin@host:LSYS2# set vr2 routing-options rib vr2.inet6.0 static route 9995::/64 next-hop 2111::1
-
配置区域和安全策略。
[edit security zones] lsys2-admin@host:LSYS2# set security-zone lsys2-trust host-inbound-traffic system-services all lsys2-admin@host:LSYS2# set security-zone lsys2-trust host-inbound-traffic protocols all lsys2-admin@host:LSYS2# set security-zone lsys2-trust interfaces reth3.0 lsys2-admin@host:LSYS2# set security zones security-zone lsys2-untrust host-inbound-traffic system-services all lsys2-admin@host:LSYS2# set security-zone lsys2-untrust host-inbound-traffic protocols all lsys2-admin@host:LSYS2# set security-zone lsys2-untrust interfaces lt-0/0/0.5
[edit security policies from-zone lsys2-trust to-zone lsys2-untrust] lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust match source-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust match application any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2untrust then permit
[edit security policies from-zone from-zone lsys2-untrust to-zone lsys2-trust] lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust match source-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust match application any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2trust then permit
[edit security policies from-zone lsys2-untrust to-zone lsys2-untrust] lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust match source-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust match application any lsys2-admin@host:LSYS2# set policy lsys2untrust-to-lsys2untrust then permit
[edit security policies from-zone lsys2-trust to-zone lsys2-trust] lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust match source-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust match destination-address any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust match application any lsys2-admin@host:LSYS2# set policy lsys2trust-to-lsys2trust then permit
结果
在配置模式下,输入 show interfaces、 show routing-instances、 show routing-options和 show security 命令以确认 LSYS1 的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
lsys1-admin@host:LSYS1# show interfaces
interfaces {
lt-0/0/0 {
unit 3 {
encapsulation ethernet;
peer-unit 2;
family inet6 {
address 2111::3/64;
}
}
}
reth1 {
unit 0 {
family inet6 {
address 8885::1/64;
}
}
}
reth2 {
unit 0 {
family inet6 {
address 7775::1/64;
}
}
}
}
[edit]
lsys1-admin@host:LSYS1# show routing-instances
routing-instances {
vr11 {
instance-type virtual-router;
interface lt-0/0/0.3;
interface reth1.0;
routing-options {
rib vr11.inet6.0 {
static {
route 6665::/64 next-hop 2111::5;
route 9995::/64 next-hop 2111::1;
}
}
}
}
vr12 {
instance-type virtual-router;
interface reth2.0;
routing-options {
interface-routes {
rib-group inet6 vr11vr12v6;
}
rib vr12.inet6.0 {
static {
route 8885::/64 next-table vr11.inet6.0;
route 9995::/64 next-table vr11.inet6.0;
route 6665::/64 next-table vr11.inet6.0;
route 2111::/64 next-table vr11.inet6.0;
}
}
}
}
}
[edit]
lsys1-admin@host:LSYS1# show routing-options
rib-groups {
vr11vr12v6 {
import-rib [ vr11.inet6.0 vr12.inet6.0 ];
}
}
[edit]
lsys1-admin@host:LSYS1# show security
security {
policies {
from-zone lsys1-trust to-zone lsys1-untrust {
policy lsys1trust-to-lsys1untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys1-untrust to-zone lsys1-trust {
policy lsys1untrust-to-lsys1trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys1-untrust to-zone lsys1-untrust {
policy lsys1untrust-to-lsys1untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys1-trust to-zone lsys1-trust {
policy lsys1trust-to-lsys1trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone lsys1-trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.0;
lt-0/0/0.3;
}
}
security-zone lsys1-untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth2.0;
}
}
}
}
在配置模式下,输入 show interfaces、 show routing-instances和 show security 命令以确认 LSYS2 的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
lsys2-admin@host:LSYS2# show interfaces
interfaces {
lt-0/0/0 {
unit 5 {
encapsulation ethernet;
peer-unit 4;
family inet6 {
address 2111::5/64;
}
}
}
reth3 {
unit 0 {
family inet6 {
address 6665::1/64;
}
}
}
}
[edit]
lsys2-admin@host:LSYS2# show routing-instances
routing-instances {
vr2 {
instance-type virtual-router;
interface lt-0/0/0.5;
interface reth3.0;
routing-options {
rib vr2.inet6.0 {
static {
route 7775::/64 next-hop 2111::3;
route 8885::/64 next-hop 2111::3;
route 9995::/64 next-hop 2111::1;
}
}
}
}
}
[edit]
lsys2-admin@host:LSYS2# show security
security {
policies {
from-zone lsys2-trust to-zone lsys2-untrust {
policy lsys2trust-to-lsys2untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys2-untrust to-zone lsys2-trust {
policy lsys2untrust-to-lsys2trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys2-untrust to-zone lsys2-untrust {
policy lsys2untrust-to-lsys2untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone lsys2-trust to-zone lsys2-trust {
policy lsys2trust-to-lsys2trust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone lsys2-trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth3.0;
}
}
security-zone lsys2-untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lt-0/0/0.5;
}
}
}
}
如果完成设备配置,请从配置模式进入。commit
验证
确认配置工作正常。
- 验证机箱群集状态 (IPv6)
- 使用日志对机箱群集进行故障排除 (IPv6)
- 验证逻辑系统许可证 (IPv6)
- 验证逻辑系统许可证使用情况 (IPv6)
- 验证逻辑系统 (IPv6) 上的逻辑系统内流量
- 验证所有逻辑系统内的逻辑系统内流量 (IPv6)
- 验证用户逻辑系统之间的流量 (IPv6)
验证机箱群集状态 (IPv6)
目的
验证机箱群集状态、故障切换状态和冗余组信息。
行动
在作模式下,输入命令 show chassis cluster status 。
{primary:node0}
show chassis cluster status
Cluster ID: 1
Node Priority Status Preempt Manual failover
Redundancy group: 0 , Failover count: 1
node0 200 primary no no
node1 100 secondary no no
Redundancy group: 1 , Failover count: 1
node0 200 primary no no
node1 100 secondary no no
使用日志对机箱群集进行故障排除 (IPv6)
目的
使用这些日志来确定任何机箱群集问题。您应该在两个节点上都运行这些日志。
行动
在作模式下,输入以下 show log 命令。
user@host> show log jsrpd user@host> show log chassisd user@host> show log messages user@host> show log dcd user@host> show traceoptions
验证逻辑系统许可证 (IPv6)
目的
验证有关逻辑系统许可证的信息。
行动
在作模式下,输入命令 show system license status logical-system all 。
{primary:node0}
user@host> show system license status logical-system all
node0:
--------------------------------------------------------------------------
Logical system license status:
logical system name license status
root-logical-system enabled
LSYS0 enabled
LSYS1 enabled
LSYS2 enabled
验证逻辑系统许可证使用情况 (IPv6)
目的
验证有关逻辑系统许可证使用情况的信息。
实际使用的许可证数仅显示在主节点上。
行动
在作模式下,输入命令 show system license 。
{primary:node0}
user@host> show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
logical-system 4 25 0 permanent
Licenses installed:
License identifier: JUNOS305013
License version: 2
Valid for device: JN110B54BAGB
Features:
logical-system-25 - Logical System Capacity
permanent
验证逻辑系统 (IPv6) 上的逻辑系统内流量
目的
验证有关逻辑系统中当前活动安全会话的信息。
行动
在作模式下,输入命令 show security flow session logical-system LSYS1 。
{primary:node0}
user@host> show security flow session logical-system LSYS1
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Session ID: 10000115, Policy name: lsys1trust-to-lsys1untrust/8, State: Active, Timeout: 1784, Valid
In: 8885::2/34564 --> 7775::2/23;tcp, If: reth1.0, Pkts: 22, Bytes: 1745
Out: 7775::2/23 --> 8885::2/34564;tcp, If: reth2.0, Pkts: 19, Bytes: 2108
Total sessions: 1
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Session ID: 10000006, Policy name: lsys1trust-to-lsys1untrust/8, State: Backup, Timeout: 14392, Valid
In: 8885::2/34564 --> 7775::2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 7775::2/23 --> 8885::2/34564;tcp, If: reth2.0, Pkts: 0, Bytes: 0
Total sessions: 1
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Total sessions: 0
验证所有逻辑系统内的逻辑系统内流量 (IPv6)
目的
验证有关所有逻辑系统上当前活动安全会话的信息。
行动
在作模式下,输入命令 show security flow session logical-system all 。
{primary:node0}
user@host> show security flow session logical-system all
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Session ID: 10000115, Policy name: lsys1trust-to-lsys1untrust/8, State: Active, Timeout: 1776, Valid
Logical system: LSYS1
In: 8885::2/34564 --> 7775::2/23;tcp, If: reth1.0, Pkts: 22, Bytes: 1745
Out: 7775::2/23 --> 8885::2/34564;tcp, If: reth2.0, Pkts: 19, Bytes: 2108
Total sessions: 1
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Session ID: 10000006, Policy name: lsys1trust-to-lsys1untrust/8, State: Backup, Timeout: 14384, Valid
Logical system: LSYS1
In: 8885::2/34564 --> 7775::2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 7775::2/23 --> 8885::2/34564;tcp, If: reth2.0, Pkts: 0, Bytes: 0
Total sessions: 1
Flow Sessions on FPC2 PIC0:
Total sessions: 0
Flow Sessions on FPC2 PIC1:
Total sessions: 0
验证用户逻辑系统之间的流量 (IPv6)
目的
验证有关逻辑系统之间当前活动安全会话的信息。
行动
在作模式下,输入命令 show security flow session logical-system logical-system-name 。
{primary:node0}
user@host> show security flow session logical-system LSYS1
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000118, Policy name: lsys1trust-to-lsys1trust/11, State: Active, Timeout: 1792, Valid
In: 8885::2/34565 --> 6665::2/23;tcp, If: reth1.0, Pkts: 91, Bytes: 6802
Out: 6665::2/23 --> 8885::2/34565;tcp, If: lt-0/0/0.3, Pkts: 65, Bytes: 6701
Total sessions: 1
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000010, Policy name: lsys1trust-to-lsys1trust/11, State: Backup, Timeout: 14388, Valid
In: 8885::2/34565 --> 6665::2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 6665::2/23 --> 8885::2/34565;tcp, If: lt-0/0/0.3, Pkts: 0, Bytes: 0
Total sessions: 1
Flow Sessions on FPC2 PIC1:
Total sessions: 0
{primary:node0}
user@host> show security flow session logical-system LSYS2
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000119, Policy name: lsys2untrust-to-lsys2trust/13, State: Active, Timeout: 1788, Valid
In: 8885::2/34565 --> 6665::2/23;tcp, If: lt-0/0/0.5, Pkts: 91, Bytes: 6802
Out: 6665::2/23 --> 8885::2/34565;tcp, If: reth3.0, Pkts: 65, Bytes: 6701
Total sessions: 1
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000011, Policy name: lsys2untrust-to-lsys2trust/13, State: Backup, Timeout: 14380, Valid
In: 8885::2/34565 --> 6665::2/23;tcp, If: lt-0/0/0.5, Pkts: 0, Bytes: 0
Out: 6665::2/23 --> 8885::2/34565;tcp, If: reth3.0, Pkts: 0, Bytes: 0
Total sessions: 1
Flow Sessions on FPC2 PIC1:
Total sessions: 0
{primary:node0}
user@host> show security flow session logical-system all
node0:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000118, Policy name: lsys1trust-to-lsys1trust/11, State: Active, Timeout: 1784, Valid
Logical system: LSYS1
In: 8885::2/34565 --> 6665::2/23;tcp, If: reth1.0, Pkts: 91, Bytes: 6802
Out: 6665::2/23 --> 8885::2/34565;tcp, If: lt-0/0/0.3, Pkts: 65, Bytes: 6701
Session ID: 80000119, Policy name: lsys2untrust-to-lsys2trust/13, State: Active, Timeout: 1784, Valid
Logical system: LSYS2
In: 8885::2/34565 --> 6665::2/23;tcp, If: lt-0/0/0.5, Pkts: 91, Bytes: 6802
Out: 6665::2/23 --> 8885::2/34565;tcp, If: reth3.0, Pkts: 65, Bytes: 6701
Total sessions: 2
Flow Sessions on FPC2 PIC1:
Total sessions: 0
node1:
--------------------------------------------------------------------------
Flow Sessions on FPC0 PIC1:
Total sessions: 0
Flow Sessions on FPC2 PIC0:
Session ID: 80000010, Policy name: lsys1trust-to-lsys1trust/11, State: Backup, Timeout: 14378, Valid
Logical system: LSYS1
In: 8885::2/34565 --> 6665::2/23;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 6665::2/23 --> 8885::2/34565;tcp, If: lt-0/0/0.3, Pkts: 0, Bytes: 0
Session ID: 80000011, Policy name: lsys2untrust-to-lsys2trust/13, State: Backup, Timeout: 14376, Valid
Logical system: LSYS2
In: 8885::2/34565 --> 6665::2/23;tcp, If: lt-0/0/0.5, Pkts: 0, Bytes: 0
Out: 6665::2/23 --> 8885::2/34565;tcp, If: reth3.0, Pkts: 0, Bytes: 0
Total sessions: 2
Flow Sessions on FPC2 PIC1:
Total sessions: 0
变更历史表
是否支持某项功能取决于您使用的平台和版本。使用 功能资源管理器 确定您的平台是否支持某个功能。
commit 备份节点上的逻辑系统许可证不足,则会显示一条警告消息,说明备份节点上所需的许可证数量,就像之前所有版本中的主节点一样。