VPNs de descoberta automática
Saiba mais sobre a VPN Auto Discovery e como configurá-la em firewalls da Série SRX.
A AUTO Discovery VPN (ADVPN) estabelece dinamicamente túneis VPN entre spokes para evitar o roteamento do tráfego pelo hub.
Use o Feature Explorer para confirmar o suporte de plataforma e versão para recursos específicos.
Analise a Multicast específico da plataforma no comportamento da ADVPN seção para obter notas relacionadas à sua plataforma.
Entendendo a VPN Auto Discovery
Auto Discovery VPN (ADVPN) é uma tecnologia que permite que o Hub central informe dinamicamente os spokes sobre um caminho melhor para o tráfego entre dois spokes. Quando ambos os spokes reconhecem as informações do Hub, eles estabelecem um túnel de atalho e mudam a topologia de roteamento para que o host chegue ao outro lado sem enviar tráfego pelo Hub.
- Protocolo ADVPN
- Estabelecendo um atalho
- Funções de iniciador e respondente de atalhos
- Atributos de atalho
- Terminação de atalho
- Suporte multicast usando PIM
- Limitações de configuração da ADVPN
Protocolo ADVPN
A ADVPN usa uma extensão do protocolo IKEv2 para trocar mensagens entre dois pares, o que permite que os spokes estabeleçam um túnel de atalho entre si. Os dispositivos que oferecem suporte à extensão ADVPN enviam uma ADVPN_SUPPORTED notificação na carga de notificar o IKEv2 , incluindo suas informações de capacidade e o número da versão ADVPN durante a troca inicial de IKE. Um dispositivo que oferece suporte à ADVPN pode agir como um sugestório de atalho ou como um parceiro de atalho, mas não ambos.
Estabelecendo um atalho
Um gateway VPN IPsec pode funcionar como um sugestão de atalho quando percebe que o tráfego está saindo de um túnel com um de seus pares e entrando em um túnel com outro peer. Figura 1 mostra tráfego do Spoke 1 ao Spoke 3 passando pelo Hub.
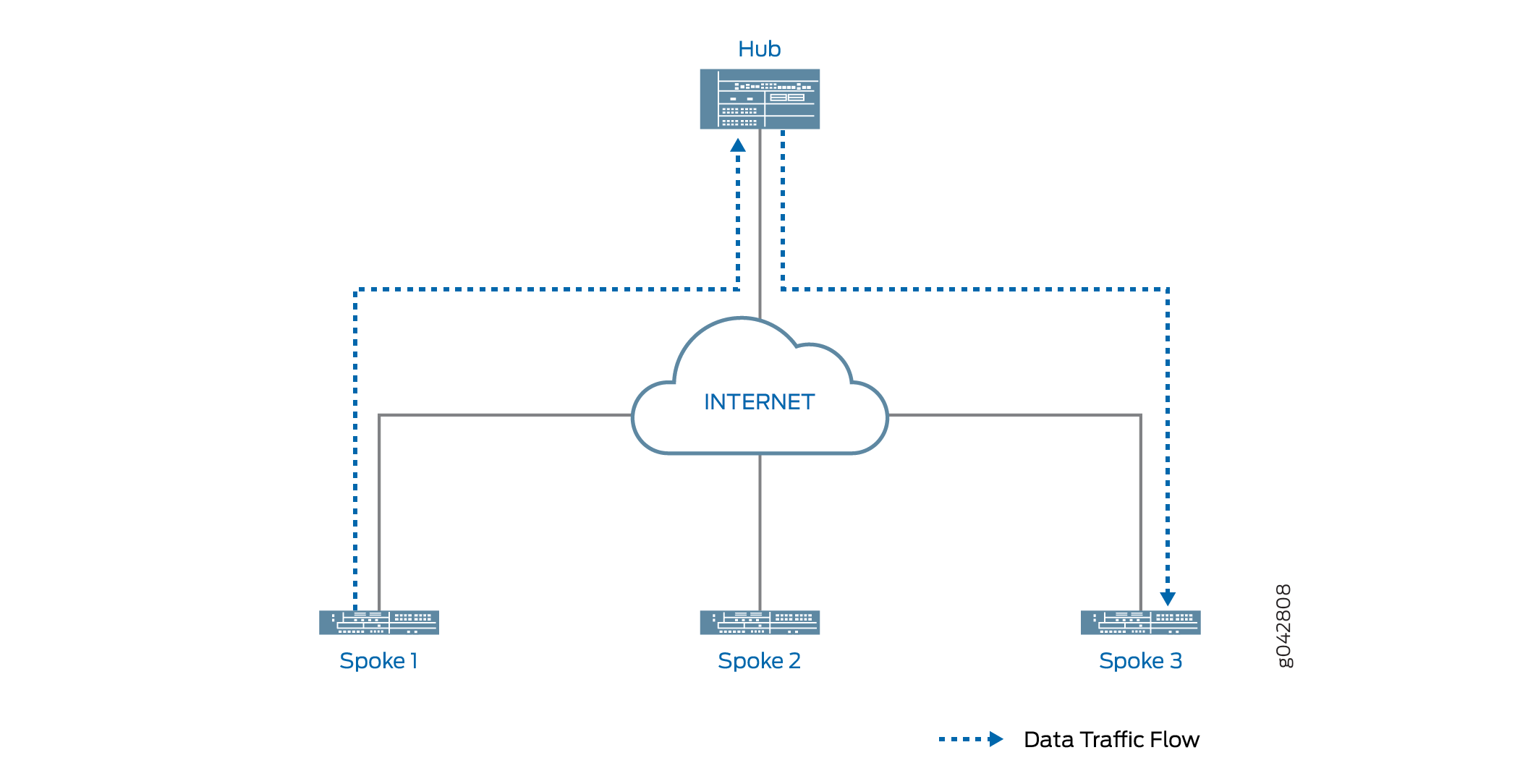
Quando a ADVPN é configurada nos dispositivos, as informações de recursos de atalho da ADVPN são trocadas entre o hub e os spokes. Desde que os Spokes 1 e 3 tenham anunciado anteriormente o recurso de parceiro de atalho da ADVPN para o Hub, o Hub pode sugerir que os Spokes 1 e 3 estabeleçam um atalho entre si.
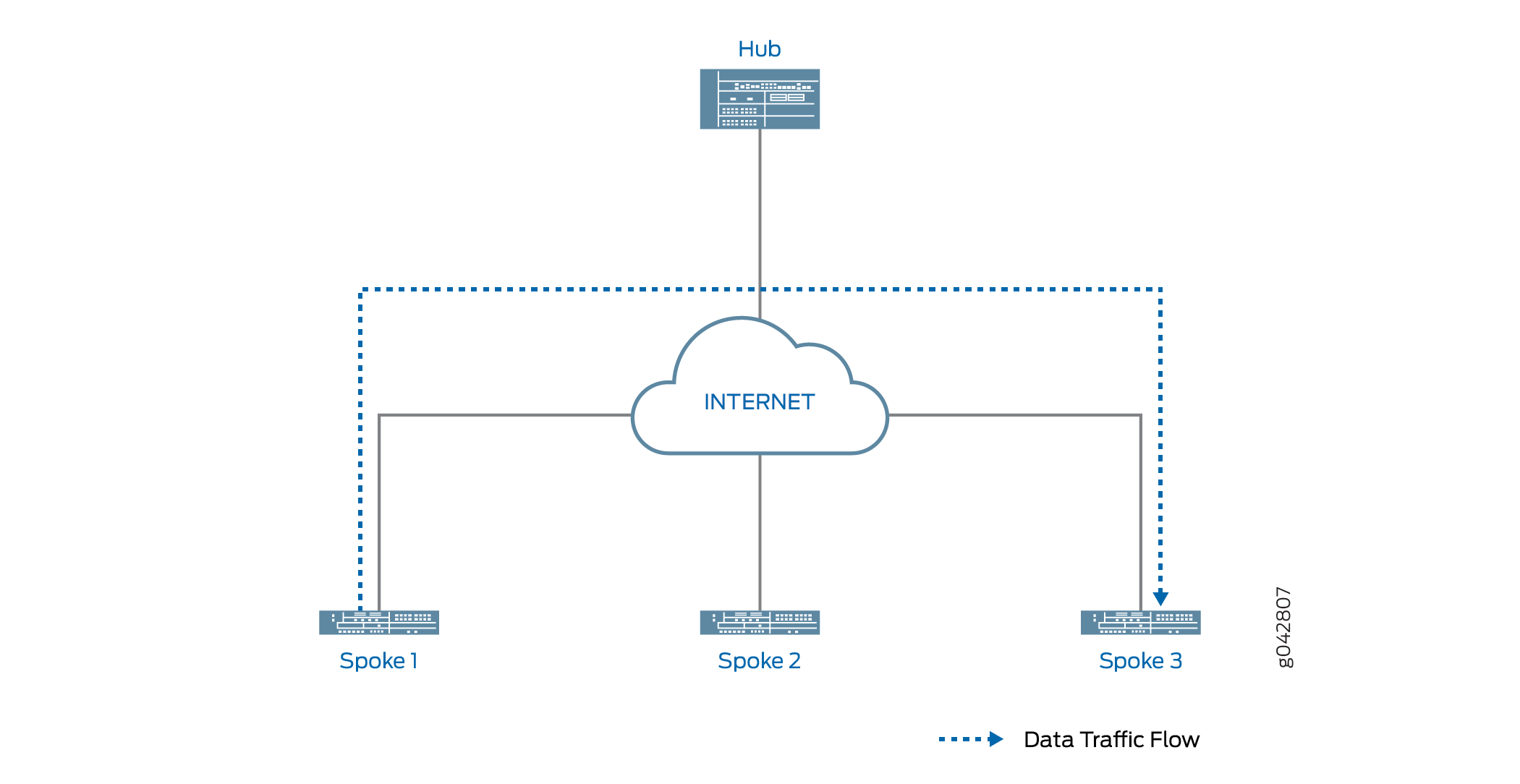
O sugestor de atalho usa seus SAs IKEv2 já estabelecidos com os pares para iniciar uma troca de atalhos com um dos dois pares. Se o peer aceitar a troca de atalhos, o sugestão de atalho inicia uma troca de atalhos com o outro peer. A troca de atalhos inclui informações que permitem que os pares ( conhecidos como parceiros de atalho) estabeleçam SAs IKE e IPsec entre si. A criação do atalho entre os parceiros de atalho só começa após ambos os pares aceitarem a troca de atalhos.
Figura 2 mostra o tráfego passando por um atalho entre spokes 1 e 3. O tráfego do Spoke 1 ao Spoke 3 não precisa atravessar o Hub.
Funções de iniciador e respondente de atalhos
O sugestor de atalho escolhe um dos parceiros de atalho para agir como o iniciador do atalho; o outro parceiro atua como o respondente. Se um dos parceiros estiver por trás de um dispositivo NAT, o parceiro por trás do dispositivo NAT será escolhido como o iniciador. Se nenhum dos parceiros estiver por trás de um dispositivo NAT, o sugestor escolhe aleatoriamente um dos parceiros como iniciador; o outro parceiro atua como o respondente. Se ambos os parceiros estiverem por trás de dispositivos NAT, um atalho não poderá ser criado entre eles; o sugestão não envia uma troca de atalhos a nenhum dos pares.
O sugestão de atalho inicia a troca de atalhos com o respondente em primeiro lugar. Se o respondente aceitar a sugestão de atalho, o sugestor notifica o iniciador.
Usando informações contidas na notificação do sugestor de atalho, o iniciador de atalho estabelece uma troca IKEv2 com o respondente, e uma nova SA IPsec é estabelecida entre os dois parceiros. Em cada parceiro, a rota para a rede por trás de seu parceiro agora aponta para o atalho em vez de para o túnel entre o parceiro e o sugestão. O tráfego originado atrás de um dos parceiros destinados a uma rede por trás do outro atalho flui pelo atalho.
Se os parceiros recusarem a sugestão de atalho, os parceiros notificarão o sugestionador com o motivo da rejeição. Neste caso, o tráfego entre os parceiros continua a fluir pelo sugestador de atalho.
Atributos de atalho
O atalho recebe alguns de seus atributos do sugestão de atalho, enquanto outros atributos são herdados da configuração do túnel de VPN do parceiro sugestão. Tabela 1 mostra os parâmetros do atalho.
|
Atributos |
Recebido/herdado |
|---|---|
|
ADVPN |
Configuração |
|
Antireplay |
Configuração |
|
Algoritmo de autenticação |
Configuração |
|
Detecção de peer inativo |
Configuração |
|
Bit DF |
Configuração |
|
Algoritmo de criptografia |
Configuração |
|
Estabelecer túneis |
Sugestão |
|
Interface externa |
Configuração |
|
Política de gateway |
Configuração |
|
ID geral de IKE |
Configuração |
|
Versão IKE |
Configuração |
|
Intervalo de instalação |
Configuração |
|
Endereço local |
Configuração |
|
Identidade local |
Sugestão |
|
Travessia de NAT |
Configuração |
|
Sigilo perfeito de envio |
Configuração |
|
Protocolo |
Configuração |
|
Proxy ID |
Não aplicável |
|
Endereço remoto |
Sugestão |
|
Identidade remota |
Sugestão |
|
Responda a um SPI ruim |
Configuração |
|
Seletor de tráfego |
Não aplicável |
Terminação de atalho
Por padrão, o atalho dura indefinidamente. Os parceiros de atalho encerram o atalho se o tráfego estiver abaixo de uma taxa especificada por um tempo especificado. Por padrão, o atalho é encerrado se o tráfego cair abaixo de 5 pacotes por segundo por 300 segundos; o tempo ocioso e os valores de limite ociosos são configuráveis para os parceiros. Você pode excluir manualmente o atalho em um parceiro de atalho com o clear security ike security-association ou clear security ipsec security-association comandos para limpar o IKE ou o IPsec SA correspondentes. Qualquer um dos parceiros de atalho pode encerrar o atalho a qualquer momento, enviando uma carga de exclusão IKEv2 para o outro parceiro de atalho.
Quando o atalho é encerrado, o SA IKE correspondente e todos os SAs IPsec para crianças são excluídos. Após o término do atalho, a rota correspondente é excluída em parceiros de atalho e o tráfego entre os dois pares novamente flui pelo sugestão. As informações de rescisão de atalho são enviadas de um parceiro para o sugestão.
A vida útil de um atalho é independente do túnel entre o sugestor de atalho e o parceiro de atalho. O atalho não é encerrado simplesmente porque o túnel entre o sugestão e o parceiro é encerrado.
Suporte multicast usando PIM
Os firewalls da Série SRX oferecem suporte a Protocolo Independente Multicast (PIM) no modo ponto a multiponto (P2MP) em infraestrutura ADVPN. Você pode habilitar o PIM na interface segura de túnel do firewall, st0, com modo P2MP. O suporte para tráfego multicast usando PIM na ADVPN é semelhante ao suporte fornecido na AutoVPN. A ADVPN segue as mesmas considerações que o AutoVPN ao configurar o suporte multicast. Para obter mais detalhes sobre como entender o suporte multicast usando o PIM na infraestrutura P2MP, consulte Understand AutoVPN. Para habilitar o PIM na interface st0 P2MP:
-
Em ambiente multinodo de alta disponibilidade, o multicast P2MP é alcançado usando túneis locais de nós. O protocolo de roteamento na interface st0 não oferece suporte a túnel de estado sincronizado. Veja o suporte para VPN IPsec em alta disponibilidade multinodo.
Um dos firewalls da Série SRX é um sugestão de atalho e outros firewalls são parceiros de atalho. Normalmente, o remetente multicast reside atrás do sugestor de atalho, enquanto os receptores multicast estão por trás dos parceiros de atalho. Para suporte multicast, a interface de túnel segura, st0, no sugestor e os dispositivos parceiros estão configurados com o modo PIM P2MP. Em cada um desses dispositivos, a interface st0 P2MP rastreia todas as junções de PIM por vizinho para garantir que o encaminhamento ou replicação multicast ocorra apenas para os vizinhos que estão em estado de adesão.
Os firewalls da Série SRX oferecem suporte a tráfego IP multicast no modo PIM esparso por meio da interface st0 P2MP. O sugestório atua como o roteador de primeiro salto (FHR) ou o ponto de encontro (RP). Os parceiros podem atuar como roteadores de último salto (LHR) na rede P2MP. Os dispositivos da rede replicam os pacotes de dados multicast para vizinhos que se juntam ao grupo multicast.
Para obter mais informações sobre como configurar o PIM na infraestrutura P2MP, veja Configurar o suporte multicast na infraestrutura P2MP.
Limitações de configuração da ADVPN
Observe as seguintes limitações ao configurar a ADVPN:
-
A ADVPN só tem suporte para comunicações de site para local. A configuração de um sugestão de ADVPN só é permitida em hubs AutoVPN.
-
Você não pode configurar as funções de sugestão e parceiro. Quando a ADVPN é habilitada em um gateway, você não pode desabilitar funções de sugestão e de parceiro no gateway.
-
Você não pode criar um atalho entre parceiros que estejam ambos por trás de dispositivos NAT. O sugestório só pode iniciar uma troca de atalhos se um dos parceiros estiver por trás de um dispositivo NAT ou se nenhum parceiro estiver por trás de dispositivos NAT.
- Para usar um endereço IPv6 para ADVPN:
-
Você deve configurar a interface st0 com suporte para P2MP em todos os dispositivos hub e spoke.
-
Você deve executar protocolos de roteamento dinâmicos (DRPs), como o OSPFv3, para atualizar a preferência de roteamento ao túnel de atalho em túnel estático.
-
Observe que você não pode configurar o recurso de monitor VPN com ADVPN baseada em interface IPv6 P2MP st0.
-
-
Você pode executar o serviço ADVPN com um DRP que oferece suporte ao endereço IPv6 ou ao endereço IPv4, mas não ambos ao mesmo tempo.
-
Para mudanças de configuração no parceiro, como ativar, desabilitar ou mudar de função, o iked:
Derruba e desfaz o IKE SA estático e o IPsec SA para trocar a nova capacidade.
Limpa o IKE SA de atalho e o IPsec SA, e as informações de sugestão que existem.
-
Para alterações de configuração não ADVPN, como:
A mudança de configuração de túnel estático que leva à limpeza tanto do IKE SA estático quanto do IPsec SA, o iked derruba o atalho IKE SA e o IPsec SA. O iked limpa as informações da sugestão. O túnel de atalho não se desassociou novamente, até que receba sugestão de atalho do sugestionador.
A mudança de configuração de túnel estático que leva à limpeza apenas do túnel estático IPsec SA, o iked derruba o atalho IKE SA e o IPsec SA. O iked limpa as informações da sugestão. O túnel de atalho não se desassociou novamente, até que receba sugestão de atalho do sugestionador.
Não oferecemos suporte às seguintes configurações com a ADVPN com os processos kmd e iked:
-
IKEv1
-
VPN baseada em políticas
-
Carga útil da configuração IKEv2
-
Seletores de tráfego
-
Interfaces de túnel seguros ponto a ponto
-
Chave pré-compartilhada semeada
-
Chave pré-compartilhada — sem suporte com processo de kmd
Entender o roteamento de tráfego com túneis de atalho
Flaps de túnel ou mudanças catastróficos podem fazer com que túneis estáticos e túneis de atalho caiam. Quando isso acontece, o tráfego para um destino específico pode ser roteado por um túnel de atalho inesperado em vez de através de um túnel estático esperado.
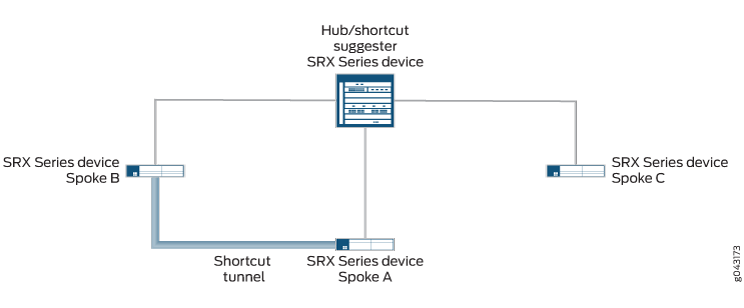
Em Figura 3, túneis estáticos existem entre o hub e cada um dos spokes. As adjacências osPF estão estabelecidas entre o hub e os spokes. O Spoke A também tem um túnel de atalho com as adjacências Spoke B e OSPF estabelecidas entre os spokes. O hub (o sugestão de atalho) reconhece que, se a conectividade entre o hub e o Spoke A diminuir, a rede spoke A pode ser alcançada através do túnel de atalho entre Spoke B e Spoke A.
Em Figura 4, o túnel estático entre o hub e o Spoke A está desativado. Se houver um novo tráfego do Spoke C ao Spoke A, o Spoke C encaminha o tráfego para o hub porque ele não tem um túnel de atalho com Spoke A. O hub não tem um túnel estático ativo com Spoke A, mas reconhece que há um túnel de atalho entre Spoke A e Spoke B, para que ele encaminhe o tráfego do Spoke C para o Spoke B.
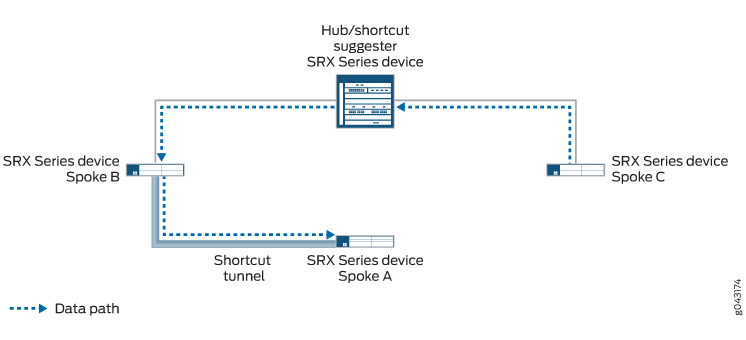
Enquanto o Spoke B e o Spoke C oferecem suporte a recursos de parceiros Auto Discovery VPN (ADVPN), o hub pode sugerir que os spokes estabeleçam um atalho direto entre si. Isso ocorre, embora não haja tráfego direto entre os dois spokes. O tráfego de Spoke C para Spoke A passa pelo túnel de atalho entre Spoke C e Spoke B, e depois pelo túnel de atalho entre Spoke B e Spoke A (ver Figura 5).
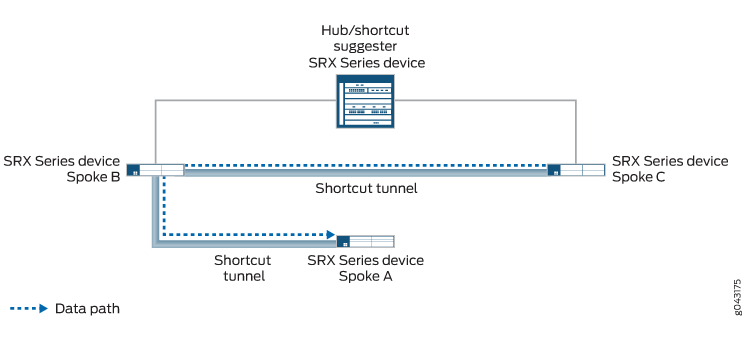
Quando o túnel estático entre o hub e o Spoke A é restabelecido, o túnel é anunciado para todos os spokes. Spoke C descobre que existe um caminho melhor para chegar ao Spoke A; em vez de passar o tráfego pelo Spoke B, ele encaminha o tráfego para o Spoke A para o hub. O hub sugere que um túnel de atalho seja estabelecido entre Spoke C e Spoke A. Quando o túnel de atalho é estabelecido entre Spoke C e Spoke A, o tráfego flui pelo túnel de atalho (ver Figura 6). O tráfego entre Spoke C e Spoke A não passa mais pelo Spoke B, e o túnel de atalho entre Spoke B e Spoke C acaba desaparecendo.
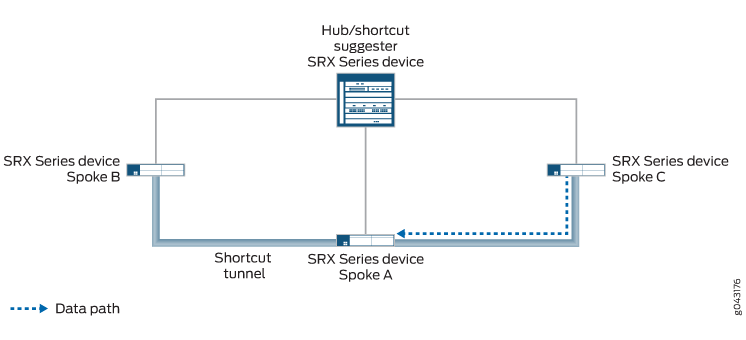
Você pode usar a opção connection-limit no nível [edit security ike gateway gateway-name advpn partner] de hierarquia para definir o número máximo de túneis de atalho que podem ser criados com diferentes parceiros de atalho usando um gateway específico. O número máximo, que também é o padrão, é dependente da plataforma.
Consulte também
Exemplo: Melhorando a utilização de recursos de rede com túneis dinâmicos de VPN de descoberta automática
Se você estiver implantando uma rede AutoVPN, você pode ser capaz de aumentar a utilização de seus recursos de rede configurando a VPN Auto Discovery (ADVPN). Nas redes AutoVPN, o tráfego de VPN flui pelo hub mesmo quando o tráfego está viajando de um para o outro. A ADVPN permite que os túneis vpn sejam estabelecidos dinamicamente entre spokes, o que pode resultar em uma melhor utilização de recursos de rede. Use este exemplo para configurar a ADVPN para permitir túneis VPN dinâmicos de spoke-to-spoke em sua rede AutoVPN.
Requisitos
Este exemplo usa os seguintes componentes de hardware e software:
Três firewalls da Série SRX suportados como hub autoVPN e spokes.
Versão Junos OS 12.3X48-D10 ou posteriores que oferecem suporte a ADVPN.
Certificados digitais inscritos no hub e spokes que permitem que os dispositivos se autenticam.
Antes de começar:
Obtenha o endereço da autoridade de certificado (CA) e as informações que eles exigem (como a senha do desafio) quando você enviar solicitações de certificados locais.
Inscreva os certificados digitais em cada dispositivo.
Consulte o certificado de inscrição.
Este exemplo usa o protocolo de roteamento dinâmico OSPF, bem como configurações de rotas estáticas para encaminhar pacotes por túneis VPN. Você deve estar familiarizado com o protocolo de roteamento dinâmico OSPF usado para encaminhar pacotes pelos túneis vpn.
Visão geral
Este exemplo mostra as configurações de um hub AutoVPN e dois spokes para ADVPN. Os spokes estabelecem conexões de VPN IPsec para o hub, o que permite que eles se comuniquem entre si, bem como acessem recursos no hub. Embora o tráfego seja inicialmente passado de um spoke para o outro através do hub, a ADVPN permite que os spokes estabeleçam uma associação de segurança direta entre si. O hub funciona como o sugestão de atalho. No hub, a configuração da ADVPN desativa a partner função. Nos spokes, a configuração da ADVPN desativa a suggester função.
Certas opções de túnel de IKE da Fase 1 e Fase 2 configuradas no hub AutoVPN e spokes devem ter os mesmos valores. Tabela 2 mostra os valores usados neste exemplo.
Opção |
Value |
|---|---|
Proposta de IKE: |
|
Método de autenticação |
rsa-assinaturas |
Grupo Diffie-Hellman (DH) |
group5 |
Algoritmo de autenticação |
sha1 |
Algoritmo de criptografia |
aes-256-cbc |
Política de IKE: |
|
Certificado |
certificado local |
Gateway IKE: |
|
Versão |
somente v2 |
Proposta de IPsec: |
|
Protocolo |
Esp |
Algoritmo de autenticação |
hmac-sha1-96 |
Algoritmo de criptografia |
aes-256-cbc |
Política de IPsec: |
|
Grupo Perfect Forward Secrecy (PFS) |
group5 |
A configuração de gateway IKE no hub e spokes inclui valores remotos e locais que identificam os pares de VPN. Tabela 3 mostra a configuração de gateway IKE para o hub e os spokes neste exemplo.
Opção |
Hub |
Raios |
|---|---|---|
Endereço IP remoto |
Dinâmico |
Falei 1: 11.1.1.1 Falei 2: 11.1.1.1 |
Endereço IP local |
11.1.1.1 |
Falei 1: 21.1.1.2 Falei 2: 31.1.1.2 |
ID remoto de IKE |
Nome distinto (DN) com a corda "XYZ" no campo da organização (O) e "Vendas" no campo da unidade de organização (OU) nos certificados dos spokes |
DN com o string "Vendas" no campo de OU no certificado do hub |
Local IKE ID |
DN no certificado do hub |
DN no certificado dos spokes |
O hub autentica o ID IKE dos spokes se os campos de assunto dos certificados dos spokes conterem a string "XYZ" no campo O e "Vendas" no campo de OU.
Neste exemplo, a política de segurança padrão que permite todo o tráfego é usada para todos os dispositivos. Políticas de segurança mais restritivas devem ser configuradas para ambientes de produção. Veja a visão geral das políticas de segurança.
Topologia
Figura 7 mostra que os firewalls da Série SRX serão configurados para este exemplo.
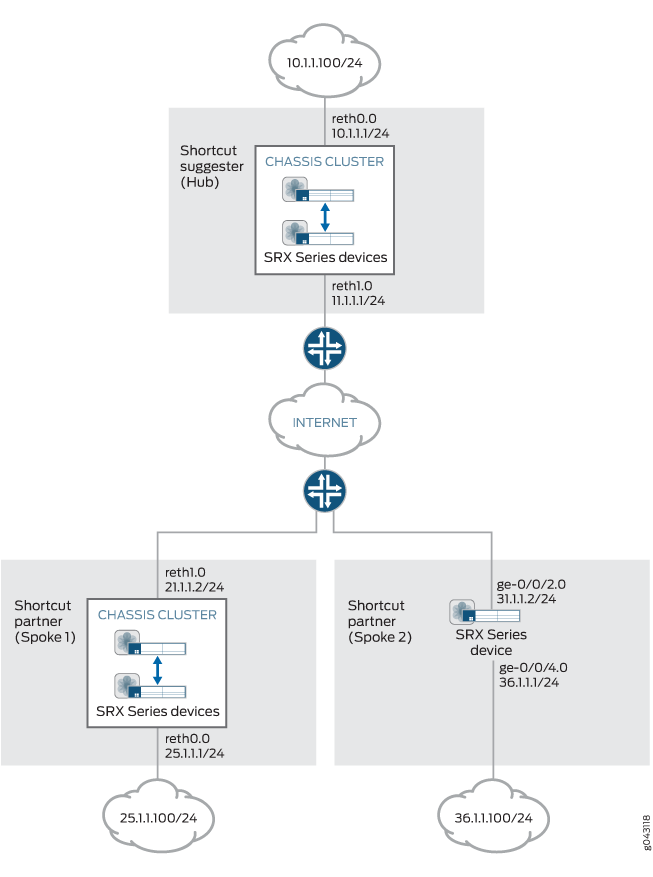
Configuração
Configurando o Sugestão (Hub)
Configuração rápida da CLI
Para configurar rapidamente este exemplo, copie os seguintes comandos, cole-os em um arquivo de texto, remova quaisquer quebras de linha, altere todos os detalhes necessários para combinar com a configuração da sua rede, copiar e colar os comandos na CLI no nível de [edit] hierarquia e, em seguida, entrar no commit modo de configuração.
set interfaces ge-0/0/3 gigether-options redundant-parent reth0 set interfaces ge-0/0/4 gigether-options redundant-parent reth1 set interfaces ge-7/0/3 gigether-options redundant-parent reth0 set interfaces ge-7/0/4 gigether-options redundant-parent reth1 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth0 unit 0 family inet address 10.1.1.1/24 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet address 11.1.1.1/24 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet address 172.16.1.1/24 set protocols ospf graceful-restart restart-duration 300 set protocols ospf graceful-restart notify-duration 300 set protocols ospf graceful-restart no-strict-lsa-checking set protocols ospf area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf area 0.0.0.0 interface st0.1 metric 10 set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40 set protocols ospf area 0.0.0.0 interface st0.1 demand-circuit set protocols ospf area 0.0.0.0 interface st0.1 dynamic-neighbors set protocols ospf area 0.0.0.0 interface reth0.0 set routing-options graceful-restart set routing-options static route 21.1.1.0/24 next-hop 11.1.1.2 set routing-options static route 31.1.1.0/24 next-hop 11.1.1.2 set routing-options router-id 172.16.1.1 set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group5 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate Suggester_Certificate_ID set security ike gateway SUGGESTER_GW ike-policy IKE_POL set security ike gateway SUGGESTER_GW dynamic distinguished-name wildcard O=XYZ, OU=Sales set security ike gateway SUGGESTER_GW dynamic ike-user-type group-ike-id set security ike gateway SUGGESTER_GW dead-peer-detection set security ike gateway SUGGESTER_GW local-identity distinguished-name set security ike gateway SUGGESTER_GW external-interface reth1.0 set security ike gateway SUGGESTER_GW local-address 11.1.1.1 set security ike gateway SUGGESTER_GW advpn partner disable set security ike gateway SUGGESTER_GW advpn suggester set security ike gateway SUGGESTER_GW version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha1-96 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group5 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn SUGGESTER_VPN bind-interface st0.1 set security ipsec vpn SUGGESTER_VPN ike gateway SUGGESTER_GW set security ipsec vpn SUGGESTER_VPN ike ipsec-policy IPSEC_POL set security pki ca-profile advpn ca-identity advpn set security pki ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/ set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces st0.1 set security zones security-zone trust interfaces reth0.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces reth1.0 set security policies default-policy permit-all
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter instruções sobre como fazer isso, veja Usando o Editor de CLI no modo de configuração no Guia do usuário da CLI.
Para configurar o sugestão:
Configure interfaces.
[edit interfaces] user@host# set ge-0/0/3 gigether-options redundant-parent reth0 user@host# set ge-0/0/4 gigether-options redundant-parent reth1 user@host# set ge-7/0/3 gigether-options redundant-parent reth0 user@host# set ge-7/0/4 gigether-options redundant-parent reth1 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet address 10.1.1.1/24 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth1 unit 0 family inet address 11.1.1.1/24 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet address 172.16.1.1/24
Configure o protocolo de roteamento e as rotas estáticas.
[edit protocols ospf] user@host# set graceful-restart restart-duration 300 user@host# set graceful-restart notify-duration 300 user@host# set graceful-restart no-strict-lsa-checking user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 metric 10 user@host# set area 0.0.0.0 interface st0.1 retransmit-interval 1 user@host# set area 0.0.0.0 interface st0.1 dead-interval 40 user@host# set area 0.0.0.0 interface st0.1 demand-circuit user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set area 0.0.0.0 interface reth0.0 [edit routing-options] user@host# set graceful-restart user@host# set static route 21.1.1.0/24 next-hop 11.1.1.2 user@host# set static route 31.1.1.0/24 next-hop 11.1.1.2 user@host# set router-id 172.16.1.1
Configure as opções de Fase 1.
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit security ike policy IKE_POL] user@host# set proposals IKE_PROP user@host# set certificate local-certificate Suggester_Certificate_ID [edit security ike gateway SUGGESTER_GW] user@host# set ike-policy IKE_POL user@host# set dynamic distinguished-name wildcard O=XYZ, OU=Sales user@host# set dynamic ike-user-type group-ike-id user@host# set dead-peer-detection user@host# set local-identity distinguished-name user@host# set external-interface reth1.0 user@host# set local-address 11.1.1.1 user@host# set advpn partner disable user@host# set advpn suggester user@host# set version v2-only
Configure as opções de Fase 2.
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm aes-256-cbc [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group5 user@host# set proposals IPSEC_PROP [edit security isec vpn SUGGESTER_VPN] user@host# set bind-interface st0.1 user@host# set ike gateway SUGGESTER_GW user@host# set ike ipsec-policy IPSEC_POL
Configure as informações do certificado.
[edit security pki] user@host# set ca-profile advpn ca-identity advpn user@host# set ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/
Configure zonas.
[edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces st0.1 user@host# set interfaces reth0.0 [edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces reth1.0
Configure a política de segurança padrão.
[edit security policies] user@host# set default-policy permit-all
Resultados
A partir do modo de configuração, confirme sua configuração inserindo os show interfacesshow security ipsecshow protocolsshow security ikeshow security pkishow routing-optionsshow security zonescomandos e show security policies comandos. Se a saída não exibir a configuração pretendida, repita as instruções neste exemplo para corrigir a configuração.
[edit]
user@host# show interfaces
ge-0/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-0/0/4 {
gigether-options {
redundant-parent reth1;
}
}
ge-7/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-7/0/4 {
gigether-options {
redundant-parent reth1;
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 10.1.1.1/24;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 11.1.1.1/24;
}
}
}
st0 {
unit 1 {
multipoint;
family inet {
address 172.16.1.1/24;
}
}
}
[edit]
user@host# show protocols
ospf {
graceful-restart {
restart-duration 300;
notify-duration 300;
no-strict-lsa-checking;
}
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
metric 10;
retransmit-interval 1;
dead-interval 40;
demand-circuit;
dynamic-neighbors;
}
interface reth0.0;
}
}
[edit]
user@host# show routing-options
graceful-restart;
static {
route 21.1.1.0/24 next-hop 11.1.1.2;
route 31.1.1.0/24 next-hop 11.1.1.2;
}
router-id 172.16.1.1;
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy IKE_POL {
proposals IKE_PROP;
certificate {
local-certificate Suggester_Certificate_ID;
}
}
gateway SUGGESTER_GW {
ike-policy IKE_POL;
dynamic {
distinguished-name {
wildcard O=XYZ, OU=Sales;
}
ike-user-type group-ike-id;
}
dead-peer-detection {
}
local-identity distinguished-name;
external-interface reth1.0
local-address 11.1.1.1;
advpn {
partner {
disable;
}
suggester {
]
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group5;
}
proposals IPSEC_PROP;
}
vpn SUGGESTER_VPN {
bind-interface st0.1;
ike {
gateway SUGGESTER_GW;
ipsec-policy IPSEC_POL;
}
}
[edit]
user@host# show security pki
ca-profile advpn {
ca-identity advpn;
enrollment {
url http://10.157.92.176:8080/scep/advpn/;
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.1;
reth0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Configuração do parceiro (Spoke 1)
Configuração rápida da CLI
Para configurar rapidamente este exemplo, copie os seguintes comandos, cole-os em um arquivo de texto, remova quaisquer quebras de linha, altere todos os detalhes necessários para combinar com a configuração da sua rede, copiar e colar os comandos na CLI no nível de [edit] hierarquia e, em seguida, entrar no commit modo de configuração.
set interfaces ge-0/0/3 gigether-options redundant-parent reth0 set interfaces ge-0/0/4 gigether-options redundant-parent reth1 set interfaces ge-7/0/3 gigether-options redundant-parent reth0 set interfaces ge-7/0/4 gigether-options redundant-parent reth1 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth0 unit 0 family inet address 25.1.1.1/24 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet address 21.1.1.2/24 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet address 172.16.1.2/24 set protocols ospf graceful-restart restart-duration 300 set protocols ospf graceful-restart notify-duration 300 set protocols ospf graceful-restart no-strict-lsa-checking set protocols ospf area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf area 0.0.0.0 interface st0.1 metric 15 set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40 set protocols ospf area 0.0.0.0 interface st0.1 demand-circuit set protocols ospf area 0.0.0.0 interface st0.1 dynamic-neighbors set protocols ospf area 0.0.0.0 interface reth0.0 set routing-options graceful-restart set routing-options static route 11.1.1.0/24 next-hop 21.1.1.1 set routing-options static route 31.1.1.0/24 next-hop 21.1.1.1 set routing-options router-id 172.16.1.2 set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group5 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate Partner1_Certificate_ID set security ike gateway PARTNER_GW ike-policy IKE_POL set security ike gateway PARTNER_GW address 11.1.1.1 set security ike gateway PARTNER_GW local-identity distinguished-name set security ike gateway PARTNER_GW remote-identity distinguished-name container OU=Sales set security ike gateway PARTNER_GW external-interface reth1 set security ike gateway PARTNER_GW local-address 21.1.1.2 set security ike gateway PARTNER_GW advpn suggester disable set security ike gateway PARTNER_GW advpn partner set security ike gateway PARTNER_GW version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha1-96 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group5 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn PARTNER_VPN bind-interface st0.1 set security ipsec vpn PARTNER_VPN ike gateway PARTNER_GW set security ipsec vpn PARTNER_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn PARTNER_VPN establish-tunnels immediately set security pki ca-profile advpn ca-identity advpn set security pki ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/ set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces st0.1 set security zones security-zone trust interfaces reth0.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces reth1.0 set security policies default-policy permit-all
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter instruções sobre como fazer isso, veja Usando o Editor de CLI no modo de configuração no Guia do usuário da CLI.
Para configurar o spoke 1:
Configure interfaces.
[edit interfaces] user@host# set ge-0/0/3 gigether-options redundant-parent reth0 user@host# set ge-0/0/4 gigether-options redundant-parent reth1 user@host# set ge-7/0/3 gigether-options redundant-parent reth0 user@host# set ge-7/0/4 gigether-options redundant-parent reth1 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet address 25.1.1.1/24 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth1 unit 0 family inet address 21.1.1.2/24 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet address 172.16.1.2/24
Configure o protocolo de roteamento e as rotas estáticas.
[edit protocols ospf] user@host# set graceful-restart restart-duration 300 user@host# set graceful-restart notify-duration 300 user@host# set graceful-restart no-strict-lsa-checking user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 metric 15 user@host# set area 0.0.0.0 interface st0.1 retransmit-interval 1 user@host# set area 0.0.0.0 interface st0.1 dead-interval 40 user@host# set area 0.0.0.0 interface st0.1 demand-circuit user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set protocols ospf area 0.0.0.0 interface reth0.0 [edit routing-options] user@host# set graceful-restart user@host# set static route 11.1.1.0/24 next-hop 21.1.1.1 user@host# set static route 31.1.1.0/24 next-hop 21.1.1.1 user@host# set router-id 172.16.1.2
Configure as opções de Fase 1.
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit security ike policy IKE_POL] user@host# set proposals IKE_PROP user@host# set certificate local-certificate Partner1_Certificate_ID [edit security ike gateway PARTNER_GW] user@host# set ike-policy IKE_POL user@host# set address 11.1.1.1 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=Sales user@host# set external-interface reth1 user@host# set local-address 21.1.1.2 user@host# set advpn suggester disable user@host# set advpn partner user@host# set version v2-only
Configure as opções de Fase 2.
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm aes-256-cbc [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group5 user@host# set proposals IPSEC_PROP [edit security isec vpn PARTNER_VPN] user@host# set bind-interface st0.1 user@host# set ike gateway PARTNER_GW user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
Configure as informações do certificado.
[edit security pki] user@host# set ca-profile advpn ca-identity advpn user@host# set ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/
Configure zonas.
[edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces st0.1 user@host# set interfaces reth0.0 [edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces reth1.0
Configure a política de segurança padrão.
[edit security policies] user@host# set default-policy permit-all
Resultados
A partir do modo de configuração, confirme sua configuração inserindo os show interfacesshow security ipsecshow protocolsshow security ikeshow security pkishow routing-optionsshow security zonescomandos e show security policies comandos. Se a saída não exibir a configuração pretendida, repita as instruções neste exemplo para corrigir a configuração.
[edit]
user@host# show interfaces
ge-0/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-0/0/4 {
gigether-options {
redundant-parent reth1;
}
}
ge-7/0/3 {
gigether-options {
redundant-parent reth0;
}
}
ge-7/0/4 {
gigether-options {
redundant-parent reth1;
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 25.1.1.1/24;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet {
address 21.1.1.2/24;
}
}
}
st0 {
unit 1 {
multipoint;
family inet {
address 172.16.1.2/24;
}
}
}
[edit]
user@host# show protocols
ospf {
graceful-restart {
restart-duration 300;
notify-duration 300;
no-strict-lsa-checking;
}
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
metric 15;
retransmit-interval 1;
dead-interval 40;
demand-circuit;
dynamic-neighbors;
}
interface reth0.0;
}
}
[edit]
user@host# show routing-options
graceful-restart;
static {
route 11.1.1.0/24 next-hop 21.1.1.1;
route 31.1.1.0/24 next-hop 21.1.1.1;
}
router-id 172.16.1.2;
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy IKE_POL {
proposals IKE_PROP;
certificate {
local-certificate Partner1_Certificate_ID;
}
}
gateway PARTNER_GW {
ike-policy IKE_POL;
address 11.1.1.1;
local-identity distinguished-name;
remote-identity distinguished-name container OU=Sales;
external-interface reth1;
local-address 21.1.1.2;
advpn {
suggester {
disable;
}
partner {
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group5;
}
proposals IPSEC_PROP;
}
vpn PARTNER_VPN {
bind-interface st0.1;
ike {
gateway PARTNER_GW;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security pki
ca-profile advpn {
ca-identity advpn;
enrollment {
url http://10.157.92.176:8080/scep/advpn/;
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.1;
reth0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
reth1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Configuração do parceiro (Spoke 2)
Configuração rápida da CLI
Para configurar rapidamente este exemplo, copie os seguintes comandos, cole-os em um arquivo de texto, remova quaisquer quebras de linha, altere todos os detalhes necessários para combinar com a configuração da sua rede, copiar e colar os comandos na CLI no nível de [edit] hierarquia e, em seguida, entrar no commit modo de configuração.
set interfaces ge-0/0/2 unit 0 family inet address 31.1.1.2/24 set interfaces ge-0/0/4 unit 0 family inet address 36.1.1.1/24 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet address 172.16.1.3/24 set protocols ospf graceful-restart restart-duration 300 set protocols ospf graceful-restart notify-duration 300 set protocols ospf graceful-restart no-strict-lsa-checking set protocols ospf area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf area 0.0.0.0 interface st0.1 metric 15 set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40 set protocols ospf area 0.0.0.0 interface st0.1 demand-circuit set protocols ospf area 0.0.0.0 interface st0.1 dynamic-neighbors set protocols ospf area 0.0.0.0 interface ge-0/0/4.0 set routing-options graceful-restart set routing-options static route 11.1.1.0/24 next-hop 31.1.1.1 set routing-options static route 21.1.1.0/24 next-hop 31.1.1.1 set routing-options router-id 172.16.1.3 set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group5 set security ike proposal IKE_PROP authentication-algorithm sha1 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate Partner2_Certificate_ID set security ike gateway PARTNER_GW ike-policy IKE_POL set security ike gateway PARTNER_GW address 11.1.1.1 set security ike gateway PARTNER_GW dead-peer-detection set security ike gateway PARTNER_GW local-identity distinguished-name set security ike gateway PARTNER_GW remote-identity distinguished-name container OU=Sales set security ike gateway PARTNER_GW external-interface ge-0/0/2.0 set security ike gateway PARTNER_GW local-address 31.1.1.2 set security ike gateway PARTNER_GW advpn suggester disable set security ike gateway PARTNER_GW advpn partner set security ike gateway PARTNER_GW version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha1-96 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group5 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn PARTNER_VPN bind-interface st0.1 set security ipsec vpn PARTNER_VPN ike gateway PARTNER_GW set security ipsec vpn PARTNER_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn PARTNER_VPN establish-tunnels immediately set security pki ca-profile advpn ca-identity advpn set security pki ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/ set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone trust interfaces st0.1 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces ge-0/0/2.0 set security policies default-policy permit-all
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter instruções sobre como fazer isso, veja Usando o Editor de CLI no modo de configuração no Guia do usuário da CLI.
Para configurar o spoke 2:
Configure interfaces.
[edit interfaces] user@host# set ge-0/0/2 unit 0 family inet address 31.1.1.2/24 user@host# set ge-0/0/4 unit 0 family inet address 36.1.1.1/24 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet address 172.16.1.3/24
Configure o protocolo de roteamento e as rotas estáticas.
[edit protocols ospf user@host# set graceful-restart restart-duration 300 user@host# set graceful-restart notify-duration 300 user@host# set graceful-restart no-strict-lsa-checking user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 metric 15 user@host# set area 0.0.0.0 interface st0.1 retransmit-interval 1 user@host# set area 0.0.0.0 interface st0.1 dead-interval 40 user@host# set area 0.0.0.0 interface st0.1 demand-circuit user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set area 0.0.0.0 interface ge-0/0/4.0 [edit routing-options] user@host# set graceful-restart user@host# set static route 11.1.1.0/24 next-hop 31.1.1.1 user@host# set static route 21.1.1.0/24 next-hop 31.1.1.1 user@host# set router-id 172.16.1.3
Configure as opções de Fase 1.
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit security ike policy IKE_POL] user@host# set proposals IKE_PROP user@host# set certificate local-certificate Partner2_Certificate_ID [edit security ike gateway PARTNER_GW] user@host# set ike-policy IKE_POL user@host# set address 11.1.1.1 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=Sales user@host# set external-interface ge-0/0/2.0 user@host# set local-address 31.1.1.2 user@host# set advpn suggester disable user@host# set advpn partner user@host# set version v2-only
Configure as opções de Fase 2.
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm aes-256-cbc [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group5 user@host# set proposals IPSEC_PROP [edit security isec vpn PARTNER_VPN] user@host# set bind-interface st0.1 user@host# set ike gateway PARTNER_GW user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
Configure as informações do certificado.
[edit security pki] user@host# set ca-profile advpn ca-identity advpn user@host# set ca-profile advpn enrollment url http://10.157.92.176:8080/scep/advpn/
Configure zonas.
[edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces ge-0/0/4.0 user@host# set interfaces st0.1 [edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols all user@host# set interfaces ge-0/0/2.0
Configure a política de segurança padrão.
[edit security policies] user@host# set default-policy permit-all
Resultados
A partir do modo de configuração, confirme sua configuração inserindo os show interfacesshow security ipsecshow protocolsshow security ikeshow security pkishow routing-optionsshow security zonescomandos e show security policies comandos. Se a saída não exibir a configuração pretendida, repita as instruções neste exemplo para corrigir a configuração.
[edit]
user@host# show interfaces
ge-0/0/2 {
unit 0 {
family inet {
address 31.1.1.2/24;
}
}
}
ge-0/0/4{
unit 0 {
family inet {
address 36.1.1.1/24;
}
}
}
st0 {
unit 1 {
multipoint;
family inet {
address 172.16.1.3/24;
}
}
}
[edit]
user@host# show protocols
ospf {
graceful-restart {
restart-duration 300;
notify-duration 300;
no-strict-lsa-checking;
}
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
metric 15;
retransmit-interval 1;
dead-interval 40;
demand-circuit;
dynamic-neighbors;
}
interface ge-0/0/4.0;
}
}
[edit]
user@host# show routing-options
graceful-restart;
static {
route 11.1.1.0/24 next-hop 31.1.1.1;
route 21.1.1.0/24 next-hop 31.1.1.1;
}
router-id 172.16.1.3;
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy IKE_POL {
proposals IKE_PROP;
certificate {
local-certificate Partner2_Certificate_ID
}
}
gateway PARTNER_GW {
ike-policy IKE_POL;
address 11.1.1.1;
local-identity distinguished-name;
remote-identity distinguished-name container OU=Sales;
external-interface ge-0/0/2.0;
local-address 31.1.1.2;
advpn {
suggester{
disable;
}
partner {
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-256-cbc;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group5;
}
proposals IPSEC_PROP;
}
vpn PARTNER_VPN {
bind-interface st0.1;
ike {
gateway PARTNER_GW;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security pki
ca-profile advpn {
ca-identity advpn;
enrollment {
url http://10.157.92.176:8080/scep/advpn/;
}
}
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Verificação
Confirme se a configuração está funcionando corretamente. Primeiro, verifique se os túneis estão estabelecidos entre o hub AutoVPN e os spokes. Quando o tráfego é passado de um falou para outro através do hub, um atalho pode ser estabelecido entre os spokes. Verifique se os parceiros de atalho estabeleceram um túnel entre eles e se uma rota para o peer está instalada nos parceiros.
Verificação de túneis entre o hub e os spokes
Propósito
Verifique se os túneis estão estabelecidos entre o hub AutoVPN e os spokes. O tráfego inicial de um falou com o outro deve percorrer o hub.
Ação
A partir do modo operacional, entre no show security ike security-associations e show security ipsec security-associations comanda no hub e spokes.
Os seguintes comandos são inseridos no hub:
user@host> show security ike security-associations node1: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 10957048 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 31.1.1.2 10957049 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 21.1.1.2
user@host> show security ike security-associations detail
node1:
--------------------------------------------------------------------------
IKE peer 31.1.1.2, Index 10957048, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Lifetime: Expires in 28196 seconds
Peer ike-id: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2030
Output bytes : 2023
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
IKE peer 21.1.1.2, Index 10957049, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Lifetime: Expires in 28219 seconds
Peer ike-id: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2030
Output bytes : 2023
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node1: -------------------------------------------------------------------------- Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <201326593 ESP:aes-cbc-256/sha1 44ccf265 2999/ unlim - root 500 31.1.1.2 >201326593 ESP:aes-cbc-256/sha1 a9d301b0 2999/ unlim - root 500 31.1.1.2 <201326594 ESP:aes-cbc-256/sha1 98a2b155 3022/ unlim - root 500 21.1.1.2 >201326594 ESP:aes-cbc-256/sha1 de912bcd 3022/ unlim - root 500 21.1.1.2
user@host> show security ipsec security-associations detail
node1:
--------------------------------------------------------------------------
ID: 201326593 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 31.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 2, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 12:57:48 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:57:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:57:48 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2991 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2414 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2991 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2414 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 201326594 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 21.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 3, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 12:58:11 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:58:11 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:58:11 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 3014 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2436 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 3014 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2436 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 28 destinations, 28 routes (27 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
25.1.1.0/24 *[OSPF/10] 00:00:27, metric 11
> to 172.16.1.2 via st0.1
36.1.1.0/24 *[OSPF/10] 00:00:27, metric 11
> to 172.16.1.3 via st0.1
172.16.1.2/32 *[OSPF/10] 00:00:27, metric 10
> to 172.16.1.2 via st0.1
172.16.1.3/32 *[OSPF/10] 00:00:27, metric 10
> to 172.16.1.3 via st0.1
224.0.0.5/32 *[OSPF/10] 00:00:48, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.3 st0.1 Full 172.16.1.3 128 - 172.16.1.2 st0.1 Full 172.16.1.2 128 -
Os seguintes comandos são inseridos no spoke 1:
user@host> show security ike security-associations node0: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 578872 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 11.1.1.1
user@host> show security ike security-associations detail
node0:
--------------------------------------------------------------------------
IKE peer 11.1.1.1, Index 578872, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 28183 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2023
Output bytes : 2030
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node0: -------------------------------------------------------------------------- Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 de912bcd 2985/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 98a2b155 2985/ unlim - root 500 11.1.1.1
user@host> show security ipsec security-associations detail
node0:
--------------------------------------------------------------------------
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 21.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:58:11 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:58:11 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:58:11 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 2980 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2358 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 2980 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2358 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:11:46, metric 16
> to 172.16.1.1 via st0.1
36.1.1.0/24 *[OSPF/10] 00:11:46, metric 26
> to 172.16.1.1 via st0.1
172.16.1.1/32 *[OSPF/10] 00:11:46, metric 15
> to 172.16.1.1 via st0.1
172.16.1.3/32 *[OSPF/10] 00:11:46, metric 25
> to 172.16.1.1 via st0.1
224.0.0.5/32 *[OSPF/10] 00:16:52, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.1 st0.1 Full 172.16.1.1 128 -
Os seguintes comandos são inseridos no spoke 2:
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 2299162 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 11.1.1.1
user@host> show security ike security-associations detail
IKE peer 11.1.1.1, Index 2299162, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 0
Suggestions accepted: 0
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 28135 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2023
Output bytes : 2030
Input packets: 4
Output packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 a9d301b0 2936/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 44ccf265 2936/ unlim - root 500 11.1.1.1
user@host> show security ipsec security-associations detail
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 31.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:57:48 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:57:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:57:48 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2933 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2311 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2933 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2311 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 36 destinations, 36 routes (35 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:00:09, metric 16
> to 172.16.1.1 via st0.1
25.1.1.0/24 *[OSPF/10] 00:00:09, metric 26
> to 172.16.1.1 via st0.1
172.16.1.1/32 *[OSPF/10] 00:00:09, metric 15
> to 172.16.1.1 via st0.1
172.16.1.2/32 *[OSPF/10] 00:00:09, metric 25
> to 172.16.1.1 via st0.1
224.0.0.5/32 *[OSPF/10] 00:17:52, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.1 st0.1 Full 172.16.1.1 128 -
Significado
O show security ike security-associations comando lista todos os SAs ativos da Fase 1 do IKE. O show security ipsec security-associations comando lista todos os SAs ativos da Fase 2 da IKE. O hub mostra dois túneis ativos, um para cada um deles. Cada spoke mostra um túnel ativo para o hub.
Se nenhum SAs estiver listado para a Fase 1 do IKE, então houve um problema com o estabelecimento da Fase 1. Verifique os parâmetros da política de IKE e as configurações externas da interface em sua configuração. Os parâmetros da proposta da fase 1 devem ser compatíveis com o hub e os spokes.
Se nenhum SAs estiver listado para a Fase 2 do IKE, então houve um problema com o estabelecimento da Fase 2. Verifique os parâmetros da política de IKE e as configurações externas da interface em sua configuração. Os parâmetros da proposta da fase 2 devem ser compatíveis com o hub e os spokes.
O show route protocol ospf comando exibe entradas na tabela de roteamento que foram aprendidas com o protocolo OSPF. O show ospf neighbor comando exibe informações sobre vizinhos OSPF.
Verificando o túnel de atalho entre parceiros
Propósito
O hub AutoVPN pode agir como um sugestão de atalho quando percebe que o tráfego está saindo de um túnel com um de seus spokes e entrando em um túnel com outro spoke. Um novo IPsec SA, ou atalho, é estabelecido entre os dois parceiros de atalho. Em cada parceiro, a rota para a rede por trás de seu parceiro agora aponta para o túnel de atalho em vez de para o túnel entre o parceiro e o sugestão (hub).
Ação
Desde o modo operacional, entre no show security ike security-associations, show route protocol ospfshow security ipsec security-associationse show ospf neighbor comandos nos spokes.
Os seguintes comandos são inseridos no hub:
user@host> show security ike security-associations node0: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 10957048 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 31.1.1.2 10957049 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 21.1.1.2
user@host> show security ike security-associations detail
node0:
--------------------------------------------------------------------------
IKE peer 31.1.1.2, Index 10957048, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Lifetime: Expires in 27781 seconds
Peer ike-id: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 260
Output bytes : 548
Input packets: 3
Output packets: 3
IPSec security associations: 0 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 31.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
IKE peer 21.1.1.2, Index 10957049, Gateway Name: SUGGESTER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Suggester, Peer Capability: Partner
Suggester Shortcut Suggestions Statistics:
Suggestions sent : 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Responder, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Lifetime: Expires in 27804 seconds
Peer ike-id: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 244
Output bytes : 548
Input packets: 3
Output packets: 3
IPSec security associations: 0 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 11.1.1.1:500, Remote: 21.1.1.2:500
Local identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Remote identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node0: -------------------------------------------------------------------------- s Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <201326593 ESP:aes-cbc-256/sha1 44ccf265 2584/ unlim - root 500 31.1.1.2 >201326593 ESP:aes-cbc-256/sha1 a9d301b0 2584/ unlim - root 500 31.1.1.2 <201326594 ESP:aes-cbc-256/sha1 98a2b155 2607/ unlim - root 500 21.1.1.2 >201326594 ESP:aes-cbc-256/sha1 de912bcd 2607/ unlim - root 500 21.1.1.2
user@host> show security ipsec security-associations detail
node0:
--------------------------------------------------------------------------
ID: 201326593 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 31.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 13:09:48 -0800: Bind-interface's address received. Information updated (1 times)
Tue Jan 13 2015 13:09:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Direction: inbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2578 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2001 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2578 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2001 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 201326594 Virtual-system: root, VPN Name: SUGGESTER_VPN
Local Gateway: 11.1.1.1, Remote Gateway: 21.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x608a29
Tunnel events:
Tue Jan 13 2015 13:09:48 -0800: Bind-interface's address received. Information updated (1 times)
Tue Jan 13 2015 13:09:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Direction: inbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 2601 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2023 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 2601 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2023 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 28 destinations, 28 routes (27 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
25.1.1.0/24 *[OSPF/10] 00:04:49, metric 11
> to 172.16.1.2 via st0.1
36.1.1.0/24 *[OSPF/10] 00:04:49, metric 11
> to 172.16.1.3 via st0.1
172.16.1.2/32 *[OSPF/10] 00:04:49, metric 10
> to 172.16.1.2 via st0.1
172.16.1.3/32 *[OSPF/10] 00:04:49, metric 10
> to 172.16.1.3 via st0.1
224.0.0.5/32 *[OSPF/10] 00:05:10, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.3 st0.1 Full 172.16.1.3 128 - 172.16.1.2 st0.1 Full 172.16.1.2 128 -
Os seguintes comandos são inseridos no spoke 1:
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 578872 UP fa05ee6d0f2cfb22 16f5ca836b118c0e IKEv2 11.1.1.1 578873 UP 895e4d9c7c5da7a4 17de7f18b45139b4 IKEv2 31.1.1.2
user@host> show security ike security-associations detail
node0:
--------------------------------------------------------------------------
IKE peer 11.1.1.1, Index 578872, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: fa05ee6d0f2cfb22, Responder cookie: 16f5ca836b118c0e
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 27906 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2495
Output bytes : 2274
Input packets: 6
Output packets: 7
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 21.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
IKE peer 31.1.1.2, Index 578873, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Shortcut, Local Capability: Partner, Peer Capability: Partner
Role: Initiator, State: UP
Initiator cookie: 895e4d9c7c5da7a4, Responder cookie: 17de7f18b45139b4
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 21.1.1.2:500, Remote: 31.1.1.2:500
Lifetime: Expires in 28787 seconds
Peer ike-id: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 1855
Output bytes : 1990
Input packets: 2
Output packets: 2
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 21.1.1.2:500, Remote: 31.1.1.2:500
Local identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations node0: -------------------------------------------------------------------------- Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 de912bcd 2709/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 98a2b155 2709/ unlim - root 500 11.1.1.1 <67108868 ESP:aes-cbc-256/sha1 75d0177b 3590/ unlim - root 500 31.1.1.2 >67108868 ESP:aes-cbc-256/sha1 e4919d73 3590/ unlim - root 500 31.1.1.2
user@host> show security ipsec security-associations detail
node0:
--------------------------------------------------------------------------
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 21.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:58:11 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:58:11 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:58:11 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: de912bcd, AUX-SPI: 0
Hard lifetime: Expires in 2701 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2079 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 98a2b155, AUX-SPI: 0
Hard lifetime: Expires in 2701 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2079 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 67108868 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 21.1.1.2, Remote Gateway: 31.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Auto Discovery VPN:
Type: Shortcut, Shortcut Role: Initiator
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x40608a29
Tunnel events:
Tue Jan 13 2015 13:12:52 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 13:12:52 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 13:12:52 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: 75d0177b, AUX-SPI: 0
Hard lifetime: Expires in 3582 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2959 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: e4919d73, AUX-SPI: 0
Hard lifetime: Expires in 3582 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2959 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 29 destinations, 29 routes (28 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:03:29, metric 16
> to 172.16.1.1 via st0.1
36.1.1.0/24 *[OSPF/10] 00:00:35, metric 16
> to 172.16.1.3 via st0.1
172.16.1.1/32 *[OSPF/10] 00:03:29, metric 15
> to 172.16.1.1 via st0.1
172.16.1.3/32 *[OSPF/10] 00:00:35, metric 15
> to 172.16.1.3 via st0.1
224.0.0.5/32 *[OSPF/10] 00:20:22, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.3 st0.1 Full 172.16.1.3 128 - 172.16.1.1 st0.1 Full 172.16.1.1 128
Os seguintes comandos são inseridos no spoke 2:
user@host> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 2299162 UP 2d58d8fbc396762d 46145be580c68be0 IKEv2 11.1.1.1 2299163 UP 895e4d9c7c5da7a4 17de7f18b45139b4 IKEv2 21.1.1.2
user@host> show security ike security-associations detail
IKE peer 11.1.1.1, Index 2299162, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Static, Local Capability: Partner, Peer Capability: Suggester
Partner Shortcut Suggestions Statistics:
Suggestions received: 1
Suggestions accepted: 1
Suggestions declined: 0
Role: Initiator, State: UP
Initiator cookie: 2d58d8fbc396762d, Responder cookie: 46145be580c68be0
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Lifetime: Expires in 27835 seconds
Peer ike-id: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2571
Output bytes : 2290
Input packets: 7
Output packets: 7
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Initiator, Message ID: 0
Local: 31.1.1.2:500, Remote: 11.1.1.1:500
Local identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=suggester, OU=Sales, O=XYZ, L=Sunnyvale, ST=CA, C=US
Flags: IKE SA is created
IKE peer 21.1.1.2, Index 2299163, Gateway Name: PARTNER_GW
Auto Discovery VPN:
Type: Shortcut, Local Capability: Partner, Peer Capability: Partner
Role: Responder, State: UP
Initiator cookie: 895e4d9c7c5da7a4, Responder cookie: 17de7f18b45139b4
Exchange type: IKEv2, Authentication method: RSA-signatures
Local: 31.1.1.2:500, Remote: 21.1.1.2:500
Lifetime: Expires in 28739 seconds
Peer ike-id: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Xauth user-name: not available
Xauth assigned IP: 0.0.0.0
Algorithms:
Authentication : hmac-sha1-96
Encryption : aes256-cbc
Pseudo random function: hmac-sha1
Diffie-Hellman group : DH-group-5
Traffic statistics:
Input bytes : 2066
Output bytes : 1931
Input packets: 3
Output packets: 3
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 31.1.1.2:500, Remote: 21.1.1.2:500
Local identity: DC=XYZ, CN=partner2, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Remote identity: DC=XYZ, CN=partner1, OU=Sales, O=XYZ, L=NewYork, ST=NY, C=US
Flags: IKE SA is created
user@host> show security ipsec security-associations Total active tunnels: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108866 ESP:aes-cbc-256/sha1 a9d301b0 2638/ unlim - root 500 11.1.1.1 >67108866 ESP:aes-cbc-256/sha1 44ccf265 2638/ unlim - root 500 11.1.1.1 <67108868 ESP:aes-cbc-256/sha1 e4919d73 3542/ unlim - root 500 21.1.1.2 >67108868 ESP:aes-cbc-256/sha1 75d0177b 3542/ unlim - root 500 21.1.1.2
user@host> show security ipsec security-associations detail
ID: 67108866 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 31.1.1.2, Remote Gateway: 11.1.1.1
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x8608a29
Tunnel events:
Tue Jan 13 2015 12:57:48 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 12:57:48 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 12:57:48 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: a9d301b0, AUX-SPI: 0
Hard lifetime: Expires in 2632 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2010 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 44ccf265, AUX-SPI: 0
Hard lifetime: Expires in 2632 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2010 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
ID: 67108868 Virtual-system: root, VPN Name: PARTNER_VPN
Local Gateway: 31.1.1.2, Remote Gateway: 21.1.1.2
Local Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Remote Identity: ipv4_subnet(any:0,[0..7]=0.0.0.0/0)
Auto Discovery VPN:
Type: Shortcut, Shortcut Role: Responder
Version: IKEv2
DF-bit: clear, Bind-interface: st0.1
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0x40608aa9
Tunnel events:
Tue Jan 13 2015 13:12:52 -0800: IPSec SA negotiation successfully completed (1 times)
Tue Jan 13 2015 13:12:52 -0800: Tunnel is ready. Waiting for trigger event or peer to trigger negotiation (1 times)
Tue Jan 13 2015 13:12:52 -0800: IKE SA negotiation successfully completed (1 times)
Direction: inbound, SPI: e4919d73, AUX-SPI: 0
Hard lifetime: Expires in 3536 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2958 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Direction: outbound, SPI: 75d0177b, AUX-SPI: 0
Hard lifetime: Expires in 3536 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2958 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha1-96, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
user@host> show route protocol ospf
inet.0: 36 destinations, 36 routes (35 active, 0 holddown, 1 hidden)
Restart Complete
+ = Active Route, - = Last Active, * = Both
10.1.1.0/24 *[OSPF/10] 00:03:55, metric 16
> to 172.16.1.1 via st0.1
25.1.1.0/24 *[OSPF/10] 00:01:02, metric 16
> to 172.16.1.2 via st0.1
172.16.1.1/32 *[OSPF/10] 00:03:55, metric 15
> to 172.16.1.1 via st0.1
172.16.1.2/32 *[OSPF/10] 00:01:02, metric 15
> to 172.16.1.2 via st0.1
224.0.0.5/32 *[OSPF/10] 00:21:38, metric 1
MultiRecv
user@host> show ospf neighbor Address Interface State ID Pri Dead 172.16.1.2 st0.1 Full 172.16.1.2 128 - 172.16.1.1 st0.1 Full 172.16.1.1 128 -
Significado
O show security ike security-associations comando lista todos os SAs ativos da Fase 1 do IKE. O show security ipsec security-associations comando lista todos os SAs ativos da Fase 2 da IKE. O hub ainda mostra dois túneis ativos, um para cada um deles. Cada spoke mostra dois túneis ativos, um para o hub e outro para seu parceiro de atalho.
O show route protocol ospf comando mostra a inclusão de rotas para o parceiro e para o hub.
Exemplo: Configuração de ADVPN com OSPFv3 para tráfego IPv6
Este exemplo mostra como configurar um hub ADVPN e dois spokes para criar um túnel de atalho e alterar a topologia de roteamento para que o host chegue ao outro lado sem enviar tráfego pelo hub. Este exemplo configura a ADVPN para ambiente IPv6 usando o OSPFv3 para encaminhar pacotes pelos túneis vpn.
Requisitos
Este exemplo usa os seguintes componentes de hardware e software:
-
Três firewalls da Série SRX suportados como hub ADVPN e spokes
-
O Junos OS Release 18.1R1 ou posteriores é liberado se o seu firewall executa o processo kmd.
-
O Junos OS Release 24.2R1 ou posteriores é liberado se o seu firewall estiver executando o processo iked.
Antes de começar:
-
Obtenha o endereço da autoridade de certificado (CA) e as informações que eles exigem (como a senha do desafio) quando você enviar solicitações de certificados locais.
Você deve estar familiarizado com o protocolo de roteamento dinâmico usado para encaminhar pacotes pelos túneis vpn.
Visão geral
Este exemplo mostra a configuração de um hub ADVPN e as configurações subsequentes de dois spokes.
Neste exemplo, a primeira etapa é inscrever certificados digitais em cada dispositivo usando o Protocolo de Inscrição de Certificados Simples (SCEP). Os certificados para os spokes contêm o valor "SLT" da unidade organizacional (OU) no campo de assunto; o hub está configurado com um ID IKE em grupo para combinar com o valor "SLT" no campo de OU.
Os spokes estabelecem conexões de VPN IPsec para o hub, o que permite que eles se comuniquem entre si, bem como recursos de acesso no hub. As opções de túnel de IKE da Fase 1 e Fase 2 configuradas no hub ADVPN e todos os spokes devem ter os mesmos valores. Tabela 4 mostra as opções usadas neste exemplo.
|
Opção |
Value |
|---|---|
|
Proposta de IKE: |
|
|
Método de autenticação |
Certificados digitais RSA |
|
Grupo Diffie-Hellman (DH) |
19 |
|
Algoritmo de autenticação |
SHA-384 |
|
Algoritmo de criptografia |
AES 256 CBC |
|
Política de IKE: |
|
|
Modo |
Principal |
|
Proposta de IPsec: |
|
|
Protocolo |
ESP |
|
Segundos de vida útil |
3000 |
|
Algoritmo de criptografia |
AES 256 GCM |
|
Política de IPsec: |
|
|
Grupo Perfect Forward Secrecy (PFS) |
19 |
A mesma autoridade de certificado (CA) está configurada em todos os dispositivos.
Tabela 5 mostra as opções configuradas no hub e em todos os spokes.
|
Opção |
Hub |
Todos os spokes |
|---|---|---|
|
Gateway IKE: |
||
|
Endereço IP remoto |
Dinâmico |
2001:db8:2000:1 |
|
ID remoto de IKE |
Nome distinto (DN) no certificado de spoke com a corda |
DN no certificado do hub |
|
Local IKE ID |
DN no certificado do hub |
DN no certificado do spoke |
|
Interface externa |
reth1 |
Falei 1: ge-0/0/0,0 Falei 2: ge-0/0/0,0 |
|
VPN: |
||
|
Interface de vinculação |
st0.1 |
st0.1 |
|
Estabelecer túneis |
(não configurado) |
estabelecer túneis imediatamente |
Tabela 6 mostra as opções de configuração que são diferentes em cada spoke.
|
Opção |
Spoke 1 |
Spoke 2 |
|---|---|---|
|
interface st0.1 |
2001:db8:9000:2/64 |
2001:db8:9000:3/64 |
|
Interface à rede interna |
(ge-0/0/1,0) 2001:db8:4000:1/64 |
(ge-0/0/1,0) 2001:db8:6000:1/64 |
|
Interface à Internet |
(ge-0/0/0,0) 2001:db8:3000:2/64 |
(ge-0/0/0,0) 2001:db8:5000:2/64 |
As informações de roteamento para todos os dispositivos são trocadas pelos túneis vpn.
Neste exemplo, a política de segurança padrão que permite todo o tráfego é usada para todos os dispositivos. Políticas de segurança mais restritivas devem ser configuradas para ambientes de produção. Veja a visão geral das políticas de segurança.
Topologia
Figura 8 mostra que os firewalls da Série SRX serão configurados para ADVPN neste exemplo.
Configuração
Para configurar a ADVPN, execute essas tarefas:
A primeira seção descreve como obter ca e certificados locais on-line usando o Protocolo de inscrição de certificados simples (SCEP) no hub e dispositivos spoke.
- Inscreva certificados de dispositivos com SCEP
- Configuração do Hub
- Configuração do Spoke 1
- Configuração do Spoke 2
Inscreva certificados de dispositivos com SCEP
Procedimento passo a passo
Para inscrever certificados digitais com o SCEP no hub:
-
Configure o CA.
[edit] user@host# set security pki ca-profile ca-profile1 ca-identity ca-profile1 user@host# set security pki ca-profile ca-profile1 enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set security pki ca-profile ca-profile1 revocation-check disable user@host# commit
-
Inscreva-se no certificado ca.
user@host> request security pki ca-certificate enroll ca-profile ca-profile1
Digite yes o prompt para carregar o certificado ca.
-
Gere um par chave.
user@host> request security pki generate-key-pair certificate-id Local1
-
Inscreva-se no certificado local.
user@host> request security pki local-certificate enroll ca-profile ca-profile1 certificate-id Local1 domain-name example.net email hub@example.net ip-address 10.1.1.1 subject DC=example.net,CN=hub,OU=SLT,O=example,L=Bengaluru,ST=KA,C=IN challenge-password <password>
-
Verifique o certificado local.
user@host> show security pki local-certificate detail Certificate identifier: Local1 Certificate version: 3 Serial number: 40a6d5f300000000258d Issuer: Common name: CASERVER1, Domain component: net, Domain component: internal Subject: Organization: example, Organizational unit: SLT, Country: IN, State: KA, Locality: Bengaluru, Common name: hub, Domain component: example.net Subject string: C=IN, DC=example.net, ST=KA, L=Bengaluru, O=example, OU=SLT, CN=hub Alternate subject: "hub@example.net", example.net, 10.1.1.1 Validity: Not before: 11- 6-2012 09:39 Not after: 11- 6-2013 09:49 Public key algorithm: rsaEncryption(1024 bits) 30:81:89:02:81:81:00:c9:c9:cc:30:b6:7a:86:12:89:b5:18:b3:76 01:2d:cc:65:a8:a8:42:78:cd:d0:9a:a2:c0:aa:c4:bd:da:af:88:f3 2a:78:1f:0a:58:e6:11:2c:81:8f:0e:7c:de:86:fc:48:4c:28:5b:8b 34:91:ff:2e:91:e7:b5:bd:79:12:de:39:46:d9:fb:5c:91:41:d1:da 90:f5:09:00:9b:90:07:9d:50:92:7d:ff:fb:3f:3c:bc:34:e7:e3:c8 ea:cb:99:18:b4:b6:1d:a8:99:d3:36:b9:1b:36:ef:3e:a1:fd:48:82 6a:da:22:07:da:e0:d2:55:ef:57:be:09:7a:0e:17:02:03:01:00:01 Signature algorithm: sha1WithRSAEncryption Distribution CRL: http://ca-server1/CertEnroll/CASERVER1.crl file://\\ca-server1\CertEnroll\CASERVER1.crl Fingerprint: e1:f7:a1:a6:1e:c3:97:69:a5:07:9b:09:14:1a:c7:ae:09:f1:f6:35 (sha1) a0:02:fa:8d:5c:63:e5:6d:f7:f4:78:56:ac:4e:b2:c4 (md5) Auto-re-enrollment: Status: Disabled Next trigger time: Timer not started
Procedimento passo a passo
Para inscrever certificados digitais no SCEP no spoke 1:
-
Configure o CA.
[edit] user@host# set security pki ca-profile ca-profile1 ca-identity ca-profile1 user@host# set security pki ca-profile ca-profile1 enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set security pki ca-profile ca-profile1 revocation-check disable user@host# commit
-
Inscreva-se no certificado ca.
user@host> request security pki ca-certificate enroll ca-profile ca-profile1
Digite yes o prompt para carregar o certificado ca.
-
Gere um par chave.
user@host> request security pki generate-key-pair certificate-id Local1
-
Inscreva-se no certificado local.
user@host> request security pki local-certificate enroll ca-profile ca-profile1 certificate-id Local1 domain-name example.net email spoke1@example.net ip-address 10.2.2.1 subject DC=example.net,CN=spoke1,OU=SLT,O=example,L=Mysore,ST=KA,C=IN challenge-password <password>
-
Verifique o certificado local.
user@host> show security pki local-certificate detail Certificate identifier: Local1 Certificate version: 3 Serial number: 40a7975f00000000258e Issuer: Common name: CASERVER1, Domain component: net, Domain component: internal Subject: Organization: example, Organizational unit: SLT, Country: IN, State: KA, Locality: Mysore, Common name: spoke1, Domain component: example.net Subject string: C=IN, DC=example.net, ST=KA, L=Mysore, O=example, OU=SLT, CN=spoke1 Alternate subject: "spoke1@example.net", example.net, 10.2.2.1 Validity: Not before: 11- 6-2012 09:40 Not after: 11- 6-2013 09:50 Public key algorithm: rsaEncryption(1024 bits) 30:81:89:02:81:81:00:d8:45:09:77:cd:36:9a:6f:58:44:18:91:db b0:c7:8a:ee:c8:d7:a6:d2:e2:e7:20:46:2b:26:1a:92:e2:4e:8a:ce c9:25:d9:74:a2:81:ad:ea:e0:38:a0:2f:2d:ab:a6:58:ac:88:35:f4 90:01:08:33:33:75:2c:44:26:f8:25:18:97:96:e4:28:de:3b:35:f2 4a:f5:92:b7:57:ae:73:4f:8e:56:71:ab:81:54:1d:75:88:77:13:64 1b:6b:01:96:15:0a:1c:54:e3:db:f8:ec:ec:27:5b:86:39:c1:09:a1 e4:24:1a:19:0d:14:2c:4b:94:a4:04:91:3f:cb:ef:02:03:01:00:01 Signature algorithm: sha1WithRSAEncryption Distribution CRL: http://ca-server1/CertEnroll/CASERVER1.crl file://\\ca-server1\CertEnroll\CASERVER1.crl Fingerprint: b6:24:2a:0e:96:5d:8c:4a:11:f3:5a:24:89:7c:df:ea:d5:c0:80:56 (sha1) 31:58:7f:15:bb:d4:66:b8:76:1a:42:4a:8a:16:b3:a9 (md5) Auto-re-enrollment: Status: Disabled Next trigger time: Timer not startedA unidade organizacional (OU) mostrada no campo de assunto é
SLT. A configuração de IKE no hub incluiou=SLTidentificar o spoke.
Procedimento passo a passo
Para inscrever certificados digitais no SCEP no spoke 2:
-
Configure o CA.
[edit] user@host# set security pki ca-profile ca-profile1 ca-identity ca-profile1 user@host# set security pki ca-profile ca-profile1 enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set security pki ca-profile ca-profile1 revocation-check disable user@host# commit
-
Inscreva-se no certificado ca.
user@host> request security pki ca-certificate enroll ca-profile ca-profile1
Digite yes o prompt para carregar o certificado ca.
-
Gere um par chave.
user@host> request security pki generate-key-pair certificate-id Local1
-
Inscreva-se no certificado local.
user@host> request security pki local-certificate enroll ca-profile ca-profile1 certificate-id Local1 domain-name example.net email spoke2@example.net ip-address 10.3.3.1 subject DC=example.net,CN=spoke2,OU=SLT,O=example,L=Tumkur,ST=KA,C=IN challenge-password <password>
-
Verifique o certificado local.
user@host> show security pki local-certificate detail Certificate identifier: Local1 Certificate version: 3 Serial number: 40bb71d400000000258f Issuer: Common name: CASERVER1, Domain component: net, Domain component: internal Subject: Organization: example, Organizational unit: SLT, Country: IN, State: KA, Locality: Tumkur, Common name: spoke2, Domain component: example.net Subject string: C=IN, DC=example.net, ST=KA, L=Tumkur, O=example, OU=SLT, CN=spoke2 Alternate subject: "spoke2@example.net", example.net, 10.3.3.1 Validity: Not before: 11- 6-2012 10:02 Not after: 11- 6-2013 10:12 Public key algorithm: rsaEncryption(1024 bits) 30:81:89:02:81:81:00:b6:2e:e2:da:e6:ac:57:e4:5d:ff:de:f6:89 27:d6:3e:1b:4a:3f:b2:2d:b3:d3:61:ed:ed:6a:07:d9:8a:d2:24:03 77:1a:fe:84:e1:12:8a:2d:63:6e:bf:02:6b:15:96:5a:4f:37:a0:46 44:09:96:c0:fd:bb:ab:79:2c:5d:92:bd:31:f0:3b:29:51:ce:89:8e 7c:2b:02:d0:14:5b:0a:a9:02:93:21:ea:f9:fc:4a:e7:08:bc:b1:6d 7c:f8:3e:53:58:8e:f1:86:13:fe:78:b5:df:0b:8e:53:00:4a:46:11 58:4a:38:e9:82:43:d8:25:47:7d:ef:18:f0:ef:a7:02:03:01:00:01 Signature algorithm: sha1WithRSAEncryption Distribution CRL: http://ca-server1/CertEnroll/CASERVER1.crl file://\\ca-server1\CertEnroll\CASERVER1.crl Fingerprint: 1a:6d:77:ac:fd:94:68:ce:cf:8a:85:f0:39:fc:e0:6b:fd:fe:b8:66 (sha1) 00:b1:32:5f:7b:24:9c:e5:02:e6:72:75:9e:a5:f4:77 (md5) Auto-re-enrollment: Status: Disabled Next trigger time: Timer not startedA unidade organizacional (OU) mostrada no campo de assunto é
SLT. A configuração de IKE no hub incluiou=SLTidentificar o spoke.
Configuração do Hub
Configuração rápida da CLI
Para configurar rapidamente este exemplo, copie os seguintes comandos, cole-os em um arquivo de texto, remova quaisquer quebras de linha, altere todos os detalhes necessários para combinar com a configuração da sua rede, copiar e colar os comandos na CLI no nível de [edit] hierarquia e, em seguida, entrar no commit modo de configuração.
set chassis cluster reth-count 2 set chassis cluster node 0 set chassis cluster node 1 set chassis cluster redundancy-group 0 node 0 priority 254 set chassis cluster redundancy-group 0 node 1 priority 1 set chassis cluster redundancy-group 1 node 0 priority 254 set chassis cluster redundancy-group 1 node 1 priority 1 set security pki ca-profile ROOT-CA ca-identity ROOT-CA set security pki ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll set security pki ca-profile ROOT-CA enrollment retry 5 set security pki ca-profile ROOT-CA enrollment retry-interval 0 set security pki ca-profile ROOT-CA revocation-check disable set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group19 set security ike proposal IKE_PROP authentication-algorithm sha-384 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 6000 set security ike policy IKE_POL mode main set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate HUB set security ike gateway IKE_GWA_1 ike-policy IKE_POL set security ike gateway IKE_GWA_1 dynamic distinguished-name wildcard OU=SLT set security ike gateway IKE_GWA_1 dynamic ike-user-type group-ike-id set security ike gateway IKE_GWA_1 dead-peer-detection always-send set security ike gateway IKE_GWA_1 dead-peer-detection interval 10 set security ike gateway IKE_GWA_1 dead-peer-detection threshold 3 set security ike gateway IKE_GWA_1 local-identity distinguished-name set security ike gateway IKE_GWA_1 external-interface reth1 set security ike gateway IKE_GWA_1 advpn partner disable set security ike gateway IKE_GWA_1 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3000 set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group19 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPNA_1 bind-interface st0.1 set security ipsec vpn IPSEC_VPNA_1 ike gateway IKE_GWA_1 set security ipsec vpn IPSEC_VPNA_1 ike ipsec-policy IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols ospf3 set security zones security-zone untrust interfaces reth1.0 set security zones security-zone untrust interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols ospf3 set security zones security-zone trust interfaces reth0.0 set interfaces ge-0/0/0 gigether-options redundant-parent reth1 set interfaces ge-0/0/1 gigether-options redundant-parent reth0 set interfaces ge-7/0/0 gigether-options redundant-parent reth1 set interfaces ge-7/0/1 gigether-options redundant-parent reth0 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth0 unit 0 family inet set interfaces reth0 unit 0 family inet6 address 2001:db8:1000::1/64 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth1 unit 0 family inet set interfaces reth1 unit 0 family inet6 address 2001:db8:2000::1/64 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet6 address 2001:db8:9000::1/64 set routing-options rib inet6.0 static route 2001:db8:3000::0/64 next-hop 2001:db8:2000::2 set routing-options rib inet6.0 static route 2001:db8:5000::0/64 next-hop 2001:db8:2000::2 set protocols ospf3 area 0.0.0.0 interface reth0.0 set protocols ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter instruções sobre como fazer isso, veja Usando o Editor de CLI no modo de configuração.
Para configurar o hub:
-
Configure as interfaces.
[edit interfaces] user@host# set ge-0/0/0 gigether-options redundant-parent reth1 user@host# set ge-0/0/1 gigether-options redundant-parent reth0 user@host# set ge-7/0/0 gigether-options redundant-parent reth1 user@host# set ge-7/0/1 gigether-options redundant-parent reth0 user@host# set reth0 redundant-ether-options redundancy-group 1 user@host# set reth0 unit 0 family inet user@host# set reth0 unit 0 family inet6 address 2001:db8:1000::1/64 user@host# set reth1 redundant-ether-options redundancy-group 1 user@host# set reth1 unit 0 family inet user@host# set reth1 unit 0 family inet6 address 2001:db8:2000::1/64 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet6 address 2001:db8:9000::1/64
-
Configure o protocolo de roteamento.
[edit protocols ospf3] user@host# set ospf3 area 0.0.0.0 interface reth0.0 user@host# set ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors [edit routing-options] user@host# set rib inet6.0 static route 2001:db8:3000::0/64 next-hop 2001:db8:2000::2 user@host# set rib inet6.0 static route 2001:db8:5000::0/64 next-hop 2001:db8:2000::2
-
Configure as opções de Fase 1.
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group19 user@host# set authentication-algorithm sha-384 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 6000 [edit security ike policy IKE_POL] user@host# set mode main user@host# set proposals IKE_PROP user@host# set certificate local-certificate HUB [edit security ike gateway IKE_GWA_1] user@host# set ike-policy IKE_POL user@host# set dynamic distinguished-name wildcard OU=SLT user@host# set ike-user-type group-ike-id user@host# set dead-peer-detection always-send user@host# set dead-peer-detection interval 10 user@host# set dead-peer-detection threshold 3 user@host# set local-identity distinguished-name user@host# set external-interface reth1 user@host# set version v2-only
-
Configure as opções de Fase 2.
[edit security ipsec proposal IPSEC_PROP] user@host# set protocol esp user@host# set encryption-algorithm aes-256-gcm user@host# set lifetime-seconds 3000 [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group19 user@host# set proposals IPSEC_PROP [edit security ipsec vpn IPSEC_VPNA_1] user@host# set bind-interface st0.1 user@host# set ike gateway IKE_GWA_1 user@host# set ike ipsec-policy IPSEC_POL
-
Configure zonas.
[edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces reth1.0 user@host# set interfaces st0.1 [edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces reth0.0
-
Configure a política de segurança padrão.
[edit security policies] user@host# set default-policy permit-all
-
Configure o perfil da CA.
[edit security pki] user@host# set ca-profile ROOT-CA ca-identity ROOT-CA user@host# set ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set ca-profile ROOT-CA enrollment retry 5 user@host# set ca-profile ROOT-CA enrollment retry-interval 0 user@host# set pki ca-profile ROOT-CA revocation-check disable
-
Configure o cluster do chassi
[edit chassis cluster] set reth-count 2 set node 0 set node 1 set redundancy-group 0 node 0 priority 254 set redundancy-group 0 node 1 priority 1 set redundancy-group 1 node 0 priority 254 set redundancy-group 1 node 1 priority 1
Resultados
A partir do modo de configuração, confirme sua configuração inserindo os show interfacesshow security ipsecshow protocolsshow security ikeshow security zonesshow routing-optionsshow security policiescomandos e show security pki show chassis cluster comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
[edit]
user@host# show interfaces
ge-0/0/0 {
gigether-options {
redundant-parent reth1;
}
}
ge-0/0/1 {
gigether-options {
redundant-parent reth0;
}
}
reth0 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet;
family inet6 {
address 2001:db8:1000::1/64;
}
}
}
reth1 {
redundant-ether-options {
redundancy-group 1;
}
unit 0 {
family inet;
family inet6 {
address 2001:db8:2000::1/64;
}
}
}
st0 {
unit 1 {
multipoint;
family inet6 {
address 2001:db8:9000::1/64 {
primary;
}
}
}
}
[edit]
user@host# show protocols
ospf3 {
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
demand-circuit;
dynamic-neighbors;
}
interface ge-0/0/1.0;
interface reth0.0;
}
}
[edit]
user@host# show routing-options
rib inet6.0 {
static {
route 2001:db8:3000::/64 next-hop 2001:db8:2000::2;
route 2001:db8:5000::/64 next-hop 2001:db8:2000::2;
}
}
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 6000;
}
policy IKE_POL {
mode main;
proposals IKE_PROP;
certificate {
local-certificate HUB;
}
}
gateway IKE_GWA_1 {
ike-policy IKE_POL;
dynamic {
distinguished-name {
wildcard OU=SLT;
}
ike-user-type group-ike-id;
}
dead-peer-detection {
always-send;
interval 10;
threshold 3;
}
local-identity distinguished-name;
external-interface reth1;
advpn {
partner {
disable;
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3000;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group19;
}
proposals IPSEC_PROP;
}
vpn IPSEC_VPNA_1 {
bind-interface st0.1;
ike {
gateway IKE_GWA_1;
ipsec-policy IPSEC_POL;
}
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
st0.1;
reth1.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
reth0.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security pki
ca-profile ROOT-CA {
ca-identity ROOT-CA;
enrollment {
url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll;
retry 5;
retry-interval 0;
}
revocation-check {
disable;
}
}
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Configuração do Spoke 1
Configuração rápida da CLI
Para configurar rapidamente este exemplo, copie os seguintes comandos, cole-os em um arquivo de texto, remova quaisquer quebras de linha, altere todos os detalhes necessários para combinar com a configuração da sua rede, copiar e colar os comandos na CLI no nível de [edit] hierarquia e, em seguida, entrar no commit modo de configuração.
set security pki ca-profile ROOT-CA ca-identity ROOT-CA set security pki ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll set security pki ca-profile ROOT-CA enrollment retry 5 set security pki ca-profile ROOT-CA enrollment retry-interval 0 set security pki ca-profile ROOT-CA revocation-check disable set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group19 set security ike proposal IKE_PROP authentication-algorithm sha-384 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 6000 set security ike policy IKE_POL mode main set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate SPOKE1 set security ike gateway IKE_GW_SPOKE_1 ike-policy IKE_POL set security ike gateway IKE_GW_SPOKE_1 address 2001:db8:2000::1 set security ike gateway IKE_GW_SPOKE_1 dead-peer-detection always-send set security ike gateway IKE_GW_SPOKE_1 dead-peer-detection interval 10 set security ike gateway IKE_GW_SPOKE_1 dead-peer-detection threshold 3 set security ike gateway IKE_GW_SPOKE_1 local-identity distinguished-name set security ike gateway IKE_GW_SPOKE_1 remote-identity distinguished-name container OU=SLT set security ike gateway IKE_GW_SPOKE_1 external-interface ge-0/0/0.0 set security ike gateway IKE_GW_SPOKE_1 advpn suggester disable set security ike gateway IKE_GW_SPOKE_1 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3000 set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group19 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN_SPOKE_1 bind-interface st0.1 set security ipsec vpn IPSEC_VPN_SPOKE_1 ike gateway IKE_GW_SPOKE_1 set security ipsec vpn IPSEC_VPN_SPOKE_1 ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN_SPOKE_1 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols ospf3 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols ospf3 set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 family inet6 address 2001:db8:3000::2/64 set interfaces ge-0/0/1 unit 0 family inet6 address 2001:db8:4000::1/64 set interfaces st0 unit 1 multipoint set interfaces st0 unit 1 family inet6 address 2001:db8:9000::2/64 set routing-options rib inet6.0 static route 2001:db8:2000::0/64 next-hop 2001:db8:3000::1 set protocols ospf3 area 0.0.0.0 interface ge-0/0/1.0 set protocols ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter instruções sobre como fazer isso, veja Usando o Editor de CLI no modo de configuração.
Para configurar o spoke 1:
-
Configure interfaces.
[edit interfaces] user@host# set ge-0/0/0 unit 0 family inet6 address 2001:db8:3000::2/64 user@host# set ge-0/0/1 unit 0 family inet6 address 2001:db8:4000::1/64 user@host# set st0 unit 1 multipoint user@host# set st0 unit 1 family inet6 address 2001:db8:9000::2/64
-
Configure o protocolo de roteamento.
[edit protocols ospf3] set area 0.0.0.0 interface ge-0/0/1.0 set area 0.0.0.0 interface st0.1 interface-type p2mp set area 0.0.0.0 interface st0.1 dynamic-neighbors [edit routing-options] user@host# set rib inet6.0 static route 2001:db8:2000::/64 next-hop 2001:db8:3000::1
-
Configure as opções de Fase 1.
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group19 user@host# set authentication-algorithm sha-384 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 6000 [edit security ike policy IKE_POL] user@host# set mode main user@host# set proposals IKE_PROP user@host# set certificate local-certificate SPOKE1 [edit security ike gateway IKE_GW_SPOKE_1] user@host# set ike-policy IKE_POL user@host# set address 2001:db8:2000::1 user@host# set dead-peer-detection always-send user@host# set dead-peer-detection interval 10 user@host# set dead-peer-detection threshold 3 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=SLT user@host# set external-interface ge-0/0/0.0 user@host# set advpn suggester disable user@host# set version v2-only
-
Configure as opções de Fase 2.
[edit security ipsec proposal IPSEC_PROPl] user@host# set protocol esp user@host# set encryption-algorithm aes-256-gcm user@host# set lifetime-seconds 3000 [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group19 user@host# set proposals IPSEC_PROP [edit security ipsec vpn IPSEC_VPN_SPOKE_1] user@host# set bind-interface st0.1 user@host# set ike gateway IKE_GW_SPOKE_1 user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
-
Configure zonas.
[edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces st0.1 user@host# set interfaces ge-0/0/0.0 [edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces ge-0/0/1.0
-
Configure a política de segurança padrão.
[edit security policies] user@host# set default-policy permit-all
-
Configure o perfil da CA.
[edit security pki] user@host# set ca-profile ROOT-CA ca-identity ROOT-CA user@host# set ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set ca-profile ROOT-CA enrollment retry 5 user@host# set ca-profile ROOT-CA enrollment retry-interval 0 user@host# set ca-profile ROOT-CA revocation-check disable
Resultados
A partir do modo de configuração, confirme sua configuração inserindo os show interfacesshow security ipsecshow protocolsshow security ikeshow security zonesshow routing-optionsshow security policiescomandos e show security pki comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
family inet6 {
address 2001:db8:3000::2/64;
}
}
}
ge-0/0/1 {
unit 0 {
family inet6 {
address 2001:db8:4000::1/64;
}
}
}
st0 {
unit 1 {
multipoint;
family inet6 {
address 2001:db8:9000::2/64;
}
}
}
[edit]
user@host# show protocols
ospf3 {
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
dynamic-neighbors;
}
interface ge-0/0/1.0;
}
}
[edit]
user@host# show routing-options
rib inet6.0 {
static {
route 2001:db8:2000::/64 next-hop [ 2001:db8:3000::1 2001:db8:5000::1 ];
}
}
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 6000;
}
policy IKE_POL {
mode main;
proposals IKE_PROP;
certificate {
local-certificate SPOKE1;
}
}
gateway IKE_GW_SPOKE_1 {
ike-policy IKE_POL;
address 2001:db8:2000::1;
dead-peer-detection {
always-send;
interval 10;
threshold 3;
}
local-identity distinguished-name;
remote-identity distinguished-name container OU=SLT;
external-interface ge-0/0/0.0;
advpn {
suggester {
disable;
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3000;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group19;
}
proposals IPSEC_PROP;
}
vpn IPSEC_VPN_SPOKE_1 {
bind-interface st0.1;
ike {
gateway IKE_GW_SPOKE_1;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
st0.1;
ge-0/0/0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
ge-0/0/1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security pki
ca-profile ROOT-CA {
ca-identity ROOT-CA;
enrollment {
url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll;
retry 5;
retry-interval 0;
}
revocation-check {
disable;
}
}
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Configuração do Spoke 2
Configuração rápida da CLI
Para configurar rapidamente este exemplo, copie os seguintes comandos, cole-os em um arquivo de texto, remova quaisquer quebras de linha, altere todos os detalhes necessários para combinar com a configuração da sua rede, copiar e colar os comandos na CLI no nível de [edit] hierarquia e, em seguida, entrar no commit modo de configuração.
set security pki ca-profile ROOT-CA ca-identity ROOT-CA set security pki ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll set security pki ca-profile ROOT-CA enrollment retry 5 set security pki ca-profile ROOT-CA enrollment retry-interval 0 set security pki ca-profile ROOT-CA revocation-check disable set security ike proposal IKE_PROP authentication-method rsa-signatures set security ike proposal IKE_PROP dh-group group19 set security ike proposal IKE_PROP authentication-algorithm sha-384 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 6000 set security ike policy IKE_POL mode main set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL certificate local-certificate SPOKE2 set security ike gateway IKE_GW_SPOKE_2 ike-policy IKE_POL set security ike gateway IKE_GW_SPOKE_2 address 2001:db8:2000::1 set security ike gateway IKE_GW_SPOKE_2 dead-peer-detection always-send set security ike gateway IKE_GW_SPOKE_2 dead-peer-detection interval 10 set security ike gateway IKE_GW_SPOKE_2 dead-peer-detection threshold 3 set security ike gateway IKE_GW_SPOKE_2 local-identity distinguished-name set security ike gateway IKE_GW_SPOKE_2 remote-identity distinguished-name container OU=SLT set security ike gateway IKE_GW_SPOKE_2 external-interface ge-0/0/0.0 set security ike gateway IKE_GW_SPOKE_2 advpn suggester disable set security ike gateway IKE_GW_SPOKE_2 version v2-only set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal IPSEC_PROP lifetime-seconds 3000 set security ipsec policy IPSEC_POL perfect-forward-secrecy keys group19 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN_SPOKE_2 bind-interface st0.1 set security ipsec vpn IPSEC_VPN_SPOKE_2 ike gateway IKE_GW_SPOKE_2 set security ipsec vpn IPSEC_VPN_SPOKE_2 ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN_SPOKE_2 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols ospf3 set security zones security-zone trust interfaces ge-0/0/1.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust host-inbound-traffic protocols ospf3 set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces ge-0/0/0.0 set interfaces ge-0/0/0 unit 0 family inet6 address 2001:db8:5000::2/64 set interfaces ge-0/0/1 unit 0 family inet6 address 2001:db8:6000::1/64 set interfaces st0 unit 1 family inet6 address 2001:db8:9000::3/64 set routing-options rib inet6.0 static route 2001:db8:2000::/64 next-hop 2001:db8:5000::1 set protocols ospf3 area 0.0.0.0 interface ge-0/0/1.0 set protocols ospf3 area 0.0.0.0 interface st0.1 interface-type p2mp set protocols ospf3 area 0.0.0.0 interface st0.1 dynamic-neighbors
Procedimento passo a passo
O exemplo a seguir exige que você navegue por vários níveis na hierarquia de configuração. Para obter instruções sobre como fazer isso, veja Usando o Editor de CLI no modo de configuração.
Para configurar o spoke 2:
-
Configure interfaces.
[edit interfaces] user@host# set ge-0/0/0 unit 0 family inet6 address 2001:db8:5000::2/64 user@host# set ge-0/0/1 unit 0 family inet6 address 2001:db8:6000::1/64 user@host# set st0 unit 1 family inet6 address 2001:db8:9000::3/64
-
Configure o protocolo de roteamento.
[edit protocols ospf3] user@host# set area 0.0.0.0 interface st0.1 interface-type p2mp user@host# set area 0.0.0.0 interface st0.1 dynamic-neighbors user@host# set area 0.0.0.0 interface ge-0/0/1.0 [edit routing-options] user@host# set rib inet6.0 static route 2001:db8:2000::/64 next-hop 2001:db8:5000::1
-
Configure as opções de Fase 1.
[edit security ike proposal IKE_PROP] user@host# set authentication-method rsa-signatures user@host# set dh-group group19 user@host# set authentication-algorithm sha-384 user@host# set encryption-algorithm aes-256-cbc user@host# set lifetime-seconds 6000 [edit security ike policy IKE_POL] user@host# set mode main user@host# set proposals IKE_PROP user@host# set certificate local-certificate SPOKE2 [edit security ike gateway IKE_GW_SPOKE_2] user@host# set ike-policy IKE_POL user@host# set address 2001:db8:2000::1 user@host# set dead-peer-detection always-send user@host# set dead-peer-detection interval 10 user@host# set dead-peer-detection threshold 3 user@host# set local-identity distinguished-name user@host# set remote-identity distinguished-name container OU=SLT user@host# set external-interface ge-0/0/0.0 user@host# set advpn suggester disable user@host# set version v2-only
-
Configure as opções de Fase 2.
[edit security ipsec proposal IPSEC_PROPl] user@host# set protocol esp user@host# set encryption-algorithm aes-256-gcm user@host# set lifetime-seconds 3000 [edit security ipsec policy IPSEC_POL] user@host# set perfect-forward-secrecy keys group19 user@host# set proposals IPSEC_PROP [edit security ipsec vpn IPSEC_VPN_SPOKE_2] user@host# set bind-interface st0.1 user@host# set ike gateway IKE_GW_SPOKE_2 user@host# set ike ipsec-policy IPSEC_POL user@host# set establish-tunnels immediately
-
Configure zonas.
[edit security zones security-zone untrust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces st0.1 user@host# set interfaces ge-0/0/0.0 [edit security zones security-zone trust] user@host# set host-inbound-traffic system-services all user@host# set host-inbound-traffic protocols ospf3 user@host# set interfaces ge-0/0/1.0
-
Configure a política de segurança padrão.
[edit security policies] user@host# set default-policy permit-all
-
Configure o perfil da CA.
[edit security pki] user@host# set ca-profile ROOT-CA ca-identity ROOT-CA user@host# set ca-profile ROOT-CA enrollment url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll user@host# set ca-profile ROOT-CA enrollment retry 5 user@host# set ca-profile ROOT-CA enrollment retry-interval 0 user@host# set ca-profile ROOT-CA revocation-check disable
Resultados
A partir do modo de configuração, confirme sua configuração inserindo os show interfacesshow security ipsecshow protocolsshow security ikeshow security zonesshow routing-optionsshow security policiescomandos e show security pki comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
family inet6 {
address 2001:db8:5000::2/64;
}
}
}
ge-0/0/1 {
unit 0 {
family inet6 {
address 2001:db8:6000::1/64;
}
}
}
st0 {
unit 1 {
family inet6 {
address 2001:db8:9000::3/64;
}
}
}
[edit]
user@host# show protocols
ospf3 {
area 0.0.0.0 {
interface st0.1 {
interface-type p2mp;
dynamic-neighbors;
}
interface ge-0/0/1.0;
}
}
[edit]
user@host# show routing-options
rib inet6.0 {
static {
route 2001:db8:2000::/64 next-hop [ 2001:db8:3000::1 2001:db8:5000::1 ];
}
}
[edit]
user@host# show security ike
proposal IKE_PROP {
authentication-method rsa-signatures;
dh-group group19;
authentication-algorithm sha-384;
encryption-algorithm aes-256-cbc;
lifetime-seconds 6000;
}
policy IKE_POL {
mode main;
proposals IKE_PROP;
certificate {
local-certificate SPOKE2;
}
}
gateway IKE_GW_SPOKE_2 {
ike-policy IKE_POL;
address 2001:db8:2000::1;
dead-peer-detection {
always-send;
interval 10;
threshold 3;
}
local-identity distinguished-name;
remote-identity distinguished-name container OU=SLT;
external-interface ge-0/0/0.0;
advpn {
suggester {
disable
}
}
version v2-only;
}
[edit]
user@host# show security ipsec
proposal IPSEC_PROP {
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3000;
}
policy IPSEC_POL {
perfect-forward-secrecy {
keys group19;
}
proposals IPSEC_PROP;
}
vpn IPSEC_VPN_SPOKE_2 {
bind-interface st0.1;
ike {
gateway IKE_GW_SPOKE_2;
ipsec-policy IPSEC_POL;
}
establish-tunnels immediately;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
ge-0/0/0.0;
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
ospf3;
}
}
interfaces {
ge-0/0/1.0;
}
}
[edit]
user@host# show security policies
default-policy {
permit-all;
}
[edit]
user@host# show security pki
ca-profile ROOT-CA {
ca-identity ROOT-CA;
enrollment {
url http://2001:db8:1710:f00::2/certsrv/mscep/mscep.dll;
retry 5;
retry-interval 0;
}
revocation-check {
disable;
}
}
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Verificação
Confirme se a configuração está funcionando corretamente.
- Verificação do status do IKE
- Verificando o status do IPsec
- Verificando túneis de próximo salto IPsec
- Verificação do OSPFv3
Verificação do status do IKE
Propósito
Verifique o status do IKE.
Ação
A partir do modo operacional, entre no show security ike sa comando.
user@host> show security ike sa Index State Initiator cookie Responder cookie Mode Remote Address 4295070 UP 2001:db8:1ad4ba7a115fa229 2001:db8:32e6382a058bb296 Main 2001:db8:3000::2 295069 UP 2001:db8:88a1520c20cbbe04 2001:db8:7fa4c8e365393c48 Main 2001:db8:5000::2
Significado
O show security ike sa comando lista todos os SAs ativos da Fase 1 do IKE. Se nenhum SAs estiver listado, houve um problema com o estabelecimento da Fase 1. Verifique os parâmetros da política de IKE e as configurações externas da interface em sua configuração. Os parâmetros da proposta da fase 1 devem ser compatíveis com o hub e os spokes.
Verificando o status do IPsec
Propósito
Verifique o status do IPsec.
Ação
A partir do modo operacional, entre no show security ipsec sa comando.
user@host> show security ipsec sa Total active tunnels: 2 Total Ipsec sas: 2 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <67108881 ESP:aes-gcm-256/None 3dba3f80 2979/ unlim - root 500 2001:db8:5000::2 >67108881 ESP:aes-gcm-256/None 46746d5d 2979/ unlim - root 500 2001:db8:5000::2 <67108882 ESP:aes-gcm-256/None 16dceb60 2992/ unlim - root 500 2001:db8:3000::2 >67108882 ESP:aes-gcm-256/None 681209c2 2992/ unlim - root 500 2001:db8:3000::2
Significado
O show security ipsec sa comando lista todos os SAs ativos da Fase 2 da IKE. Se nenhum SAs estiver listado, houve um problema com o estabelecimento da Fase 2. Verifique os parâmetros da política de IKE e as configurações externas da interface em sua configuração. Os parâmetros da proposta da fase 2 devem ser compatíveis com o hub e os spokes.
Verificando túneis de próximo salto IPsec
Propósito
Verifique os túneis IPsec de próximo salto.
Ação
A partir do modo operacional, entre no show security ipsec next-hop-tunnels comando.
user@host> show security ipsec next-hop-tunnels Next-hop gateway interface IPSec VPN name Flag IKE-ID XAUTH username 2001:db8:9000::2 st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE1 Not-Available 2001:db8:9000::3 st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE2 Not-Available 2001:db8::5668:ad10:fcd8:10c8 st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE2 Not-Available 2001:db8::5668:ad10:fcd8:112f st0.1 IPSEC_VPNA_1 Auto C=US, DC=example.net, ST=CA, L=Sunnyvale, O=example, OU=SLT, CN=SPOKE1 Not-Available
Significado
Os gateways de próximo salto são os endereços IP para as st0 interfaces dos spokes. O próximo salto deve ser associado com o nome VPN IPsec correto.
Verificação do OSPFv3
Propósito
Verifique se o OSPFv3 faz referência aos endereços IP para as st0 interfaces dos spokes.
Ação
A partir do modo operacional, entre no show ospf3 neighbor interface comando.
user@host> show ospf3 neighbor interface
ID Interface State Pri Dead
2001:db8:9000:2 st0.1 Full 128 -
Neighbor-address 2001:db8::5668:ad10:fcd8:110e
2001:db8:20:54:49.693 INFO ${ret} = ID Interface State Pri Dead
2001:db8:9000:3 st0.1 Full 128 -
Neighbor-address 2001:db8::5668:ad10:fcd8:110ePermitindo que o OSPF atualize rotas rapidamente após a criação de túneis de atalho da ADVPN
Problema
Descrição
O OSPF pode levar até 9 segundos para atualizar uma rota de atalho na tabela de roteamento. Pode levar até 10 segundos antes que o tráfego seja encaminhado para o túnel de atalho.
Sintomas
Quando um túnel de atalho é estabelecido entre dois parceiros de atalho, o OSPF inicia um pacote de olá OSPF. Devido ao tempo do estabelecimento do túnel de atalho e da instalação do vizinho OSPF, o primeiro pacote no túnel pode ser descartado. Isso pode fazer com que o OSPF tente novamente estabelecer uma adjacência OSPF.
Por padrão, o intervalo em que o OSPF tenta estabelecer uma adjacência é de 10 segundos. Depois que um túnel de atalho é estabelecido, pode levar mais de 10 segundos para que o OSPF estabeleça uma adjacência entre os parceiros.
Solução
Configurar um intervalo de nova tentativa menor, como 1 ou 2 segundos, pode permitir que o OSPF estabeleça adjacências mais rapidamente no túnel de atalho. Por exemplo, use as seguintes configurações:
[edit] set protocols ospf area 0.0.0.0 interface st0.1 retransmit-interval 1 set protocols ospf area 0.0.0.0 interface st0.1 dead-interval 40
Consulte também
Multicast específico da plataforma no comportamento da ADVPN
Use o Feature Explorer para confirmar o suporte de plataforma e versão para recursos específicos.
Use a tabela a seguir para revisar comportamentos específicos da plataforma para sua plataforma.
|
Plataforma |
Diferença |
|---|---|
|
Série SRX |
|
Tabela de histórico de alterações
A compatibillidadde com o recurso dependerá da platadorma e versão utilizada. Use o Feature Explorer para saber se o recurso é compatível com sua plataforma.
p2mp tipo de interface é introduzido para PIM para VPN IPsec com processode kmd.