Juniper Secure Connect Integration with JIMS
Read this topic to learn how SRX Series Firewalls use the push to identity management (PTIM) solution to send VPN connection state events to Juniper Identity Management Service (JIMS).
Juniper® Identity Management Service (JIMS) is a software application that runs on Microsoft Windows. JIMS collects user, device, and group information from different sources and maintains this information for SRX Series Firewalls. The firewall sends the remote access VPN connection state events to JIMS. From these log messages, JIMS extracts the remote access VPN username, mapped IP address, and domain name of Juniper Secure Connect for tracking and troubleshooting.
The firewall can send the log messages to JIMS in two ways:
-
Syslog solution: JIMS receives the system logs (syslogs) related to each user's VPN connection state events, excluding the rekey state, from the SRX Series Firewall. JIMS parses the logs by using the custom regex that you define and stores the information in its database. SRX Series Firewall supports only the syslog solution until Junos OS Release 24.2R1. For more details, see JIMS Identity Producers Syslog Sources.
-
Push to identity management (PTIM) solution: The firewall pushes the VPN connection state events, including the rekey state, along with the IP address and the domain name details of each user. The firewall sends the details directly to JIMS by using the PTIM solution without any interaction with the syslog. Starting from Junos OS Release 24.4R1 onwards, support for PTIM solution is available. We recommend that you use the PTIM solution instead of the syslog solution.
Read further to understand the PTIM solution.
Push to Identity Management Solution Overview
SRX Series Firewalls communicate with JIMS through an HTTP or HTTPS connection. Figure 1 shows the setup between Juniper Secure Connect and JIMS.
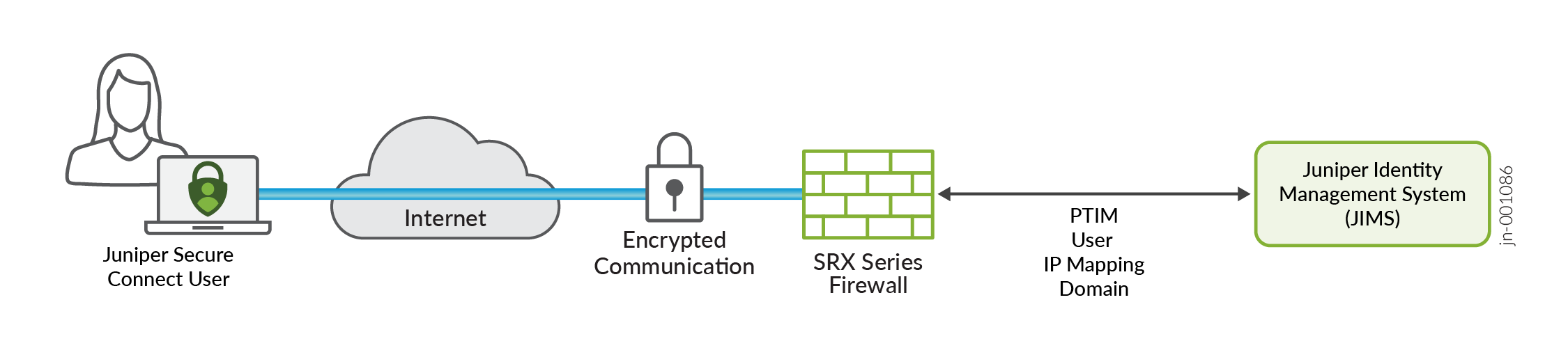
Read the following information to understand how the PTIM solution works:
- To use the PTIM solution, you must run the IPsec VPN services that uses the iked process and configure the identity management service on the firewall.
- The PTIM solution directly reports the VPN connect states such as tunnel connect
(
IKE_VPN_UP_ALARM_USER), tunnel disconnect (IKE_VPN_DOWN_ALARM_USER), and tunnel rekey (IKE_VPN_UP_ALARM_USER) to JIMS. - The solution doesn’t stop the iked process from sending the VPN connect state events to the syslog. The iked process sends these connection state events to both the JIMS server and the firewall's syslog.
-
You cannot configure PTIM when the firewall runs the IPsec VPN service that uses the kmd process.
To enable PTIM, see Enable Push to Identity Management.
Benefits
-
Reliability—Unlike the syslog solution, the PTIM solution supports IPsec VPN rekey events.
-
Ease of integration—Provides an easy integration between Juniper Secure Connect and JIMS, as no additional infrastructure is required.
-
Comprehensive solution—Shares information about context-based policies, such as the prelogon compliance policies that are used to validate the legitimacy of access.
Limitations
-
The firewall sends the username, IP address, and domain name of each user but not the device ID, device OS, and hostname to JIMS.
-
When you attach the same IPsec VPN object in two different remote access profiles, you must use the same domain alias name in the remote access profiles. Avoid configuring different domain alias names for different remote-access profiles that use the same IPsec VPN object. For more information about using domain names, see Enable Push to Identity Management.
See Also
Enable Push to Identity Management
Ensure you meet the following prerequisites on the SRX Series Firewall to send the VPN connect state events to JIMS using the PTIM solution:
-
SRX Series Firewall with Junos OS Release 24.4R1 or later.
-
SRX Series Firewall with the
junos-ikepackage installed for IPsec VPN service. See IPsec VPN Feature Support with New Package.
-
Use the
no-push-to-identity-managementstatement at the[edit security ike gateway gateway-name aaa]hierarchy level to disable the iked process communication with JIMS using the PTIM solution. See identity-management.
See Also
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
