JIMS Administrative User Interface and Configuration
Read this section to know about the JIMS administrative interface and its configuration options.
JIMS User Interface Menu
JIMS user interface consists of three menu.
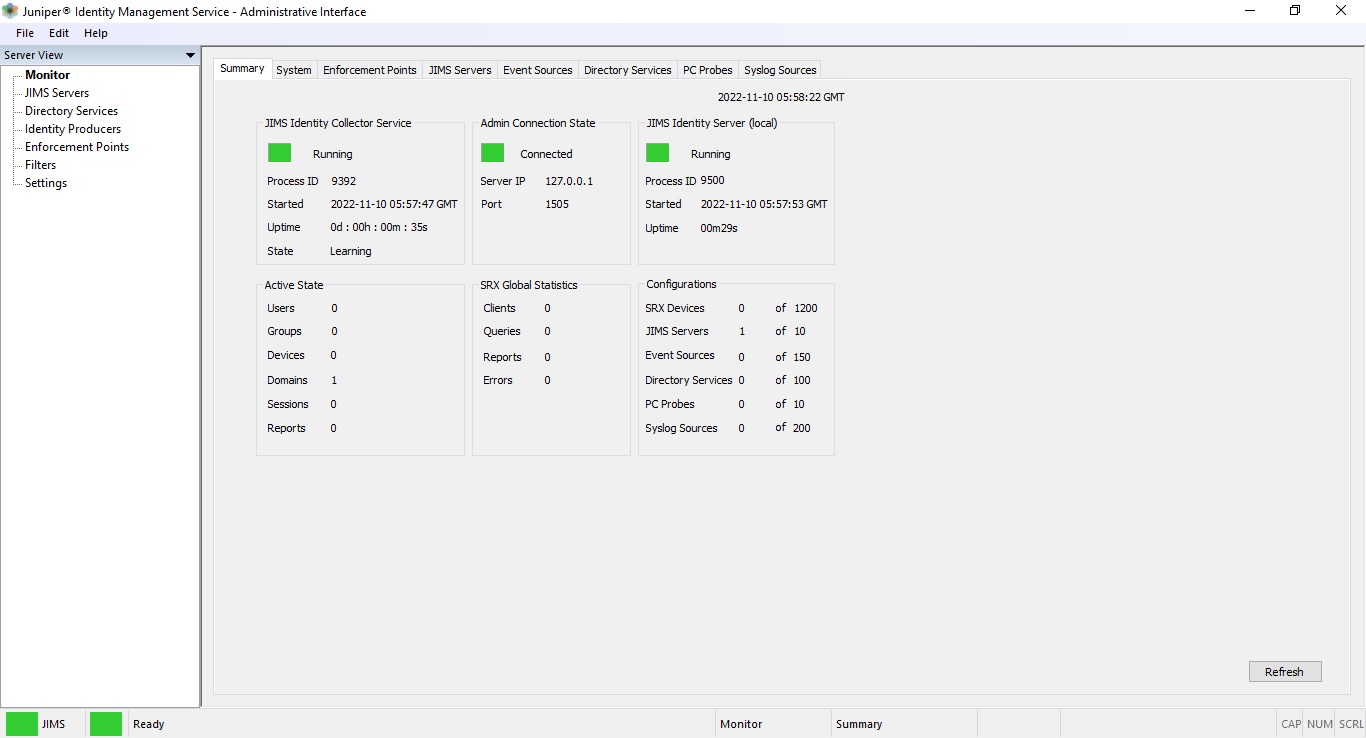
The below illustration captures the JIMS UI.
Figure 2: JIMS UI Screen
| Menu | Description |
|---|---|
| File |
Allows you to import and export the configuration data related to the JIMS. You can use the File menu to connect the JIMS collector to Juniper Secure Edge and reconnect to a lost connection of the UI. |
| Edit | Allows you to copy and search content from the user interface with table/list view. |
| Help | Allows you to find the documentation and information about JIMS such as Version, Build and other Copyright information like Trademark Notice, All Rights Reserved, Attributions and Terms of Licensing. |
The other UI options are listed below.
Monitor
The Monitor menu offers several tabs with different information related to state, events and so on. The Date and Time on the top bar show date and time in GMT format.
The Monitor menu consists of 8 tabs:
| Menu | Description |
|---|---|
| Summary |
|
| System |
Lists all the systems configured. |
| Enforcement Points |
Lists all configured Enforcement Points with device specific statistics. For a more detailed explanation and configuration steps, see Enforcement Points |
| JIMS Servers |
Lists all configured JIMS Server with specific statistics. For a more detailed explanation and configuration steps, see JIMS Server |
| Event Sources |
Lists all configured Event Sources with specific statistics. For a more detailed explanation and configuration steps, see Directory services |
| Directory Services |
Lists all configured Directory Services with specific statistics. For a more detailed explanation and configuration steps, see JIMS Server |
| PC Probes |
Lists all configured username and the order of execution including probe statistics. For a more detailed explanation and configuration steps, see Identity Producers |
| Syslog Sources |
Lists all configured Syslog clients sending data to JIMS with specific statistics. For a more detailed explanation and configuration steps, see Identity Producers |
JIMS Server
When JIMS is installed, it automatically configures the local JIMS server. If you use Contrail® Service Orchestration (CSO) or Juniper® Secure Edge these need to be configured manually.
For the configuration steps, see JIMS Server
Directory services
You must configure at least one directory server for JIMS Collector to collect users, devices, and group memberships. Currently, only Active Directory is supported.
If you plan to use multiple directory server with the same credentials, you can create a template to reduce the input for each directory server.
For the configuration steps, see Directory Services
Identity Producers
You can configure Identity Producers to gather user and device status events. JIMS uses this information to provide IP address-to-username mappings. JIMS also provides device names with domain names to the enforcement points (SRX Series Firewalls).
The identity producers offers many tabs that are listed below.
Event Sources are used to collect the username and associated IP-address. This creates an IP_address-to-username mapping as well as a device name with a domain name from a Microsoft Domain Controller or Microsoft Exchange Server. You can navigate to event sources from Server View > Identity Producers
If you plan to use multiple Event Sources with the same credentials, you can create a template to reduce the input for each event source server.
For the configuration steps, see Add Event Source
PC Probes are a complement to event sources and Syslog events for all the Windows devices connected in the domain. When the event source that is missing a domain and username is associated with an IP address, the pc probe initiates a WMI call to the specific device to collect the missing information. The WMI information contains sensitive data. Ensure that the JIMS Collector does not send WMI probes to untrusted networks. You can navigate to pc probes from Server View > Identity Providers
For the configuration steps, see Add PC Probe
Syslog Sources are used to collect user and device mapping from an IP from other systems such as a VPN concentrator, network access control (NAC) system, a wireless access controller and so on. You can navigate to syslog sources from Server View > Identity Producers
Syslog is used as a regular expression (regex), instead of a template offered by other functions. Syslog uses a base configuration that is specific to each syslog client type. You can use an already created base configuration for Juniper® Secure Connect to log the users that are active at logon and logoff events.
For the configuration steps, see Add Syslog Source
Enforcement Points
You must configure enforcement points. Otherwise, the SRX Series Firewalls cannot pull user, device, and group information to enforce identity aware policies (user firewall).
If you have many SRX Series Firewalls with the same client id and client secret, you can create a template to reduce the input for each SRX Series Firewall.
For the configuration steps, see Add Enforcement Points in JIMS UI
JIMS with SRX Series Firewall
Juniper Identity Management Service (JIMS) is a Windows service application designed to collect and manage user, device, and group information from Active Directory domains.
For using the Juniper Identity Management Service, your enforcement points (SRX Series Firewalls and NFXs) are required to be configured properly to get identity information from JIMS.
The enforcement points use the primary JIMS server until the connection declares the server as lost. Periodically, the enforcement point probes the failed primary server and reverts to it once it becomes available again without any user intervention.
The connection to the JIMS server should only use HTTPS transport, which encrypts the communication between the enforcement point and the JIMS server. Both the enforcement points and JIMS server authenticate the connection using a client ID and client secret, which generates an access token. This access token must be present in each query to the JIMS server.
There are two methods for obtaining user identity information from JIMS:
-
Batch queries:
SRX sends a batch query message to JIMS every 5 seconds by default to obtain available identity information.
-
IP queries:
When SRX is missing information about a specific IP-address, it can send an ip-query to JIMS which then returns its status for that specific ip-address. If JIMS does not contain an entry for the specified IP address, SRX will threat this IP as it is an unknown-user.
In the SRX, it’s possible to define filters which can be used to filter out identity information known to JIMS. You can either subscribe to certain domains and or include or exclude information related to certain ip-prefixes defined by address-book entries or address-sets. Changes to these filters will only take place during the next batch query.
You can select up to xxx address-book/sets entries for include or exclude filters, and the total number of xxx address-book entries is combined by both sets and books.
You can add a maximum of 25 domains to the filter list. Each address-set can
include x number of address book entries, if address-sets are included in an
address-set, set services user-identification identity-management
filter
You can refresh the user identity information in your identity management
authentication table obtained from JIMS. Identity information will be update
during the next batch query, clear services user-identification
authentication-table authentication-source
identity-management
To search user identity information and validate the authentication source to
grant access to the device, use run show services
user-identification authentication-table authentication-source
all
The following configuration illustrates a basic JIMS server configuration on an SRX Series Firewall:
root@srx1# show services user-identification
identity-management
authentication-entry-timeout 120;
invalid-authentication-entry-timeout 10;
connection {
connect-method https;
port 443;
primary {
address 70.0.0.250;
client-id abcd;
client-secret "$9$86jLdsaJDkmTUj"; ## SECRET-DATA
}
secondary {
address 70.0.0.251;
client-id otest;
client-secret "$9$W0K8-woaUH.5GD"; ## SECRET-DATA
}
}
batch-query {
items-per-batch 500;
query-interval 5;
}For detailed configuration steps, see Configuration of JIMS with SRX Series Firewall
Filters
JIMS enables you to specify the IP address ranges to include in or exclude from reports that the JIMS server sends to the SRX Series Firewalls. You can also specify Active Directory user groups to include in the reports. These filters are applied to all the SRX Series Firewalls in your network. You can also apply the IPv4 address filters in the later release versions.
JIMS supports both an IPv6 filter from the SRX Series Firewall query and a system-level IPv6 filter. The system-level filter works to filter the IP addresses from the event sources. The system-level IP filters are configured through the JIMS Administrative Interface. JIMS server includes or excludes the IP sessions when the JIMS server receives the logon events from the configured event sources.
For example, let us consider that 192.x.x.x is added as the exclude IP address in the system-level filter on the JIMS server. When a user with 192.x.x.x logs on to the domain controller, JIMS server ignores the session for this user. Thus, no entry with 192.x.x.x is sent to the SRX Series Firewall.
The IPv6 filters used by the SRX Series Firewall query are configured on the SRX Series Firewall. The SRX Series Firewall includes or excludes the IP addresses in the batch query that it sends to the JIMS server. The JIMS server replies with the entries based on the filters received from the SRX Series Firewall. However, note that the SRX Series Firewalls only apply filters within the context of the system-level filter. For example, If 192.0.2.0/24 is configured on the SRX Series Firewall as the include filter, the SRX Series Firewall sends the query with 192.0.2.0/24 as the include subnet to JIMS sever. JIMS server replies with the entries within this subnet only, although the JIMS server holds lots of entries other than 192.0.2.0/24.
In addition, the JIMS server allows you to filter by:
-
Groups—You define the Active Directory user groups to include in reports. Group filters are applied to all the SRX Series Firewalls in your network.
-
User/Device Event—Event filters on the JIMS server enable you to apply a filter in your network to define users or devices to exclude from reports that the JIMS server sends to SRX Series Firewalls. The User/Device event filter performs regular expression matching to filter specific users or devices by name. The filter ignores events associated with a particular user or device.
For SRX Series Firewalls running Junos OS Release, JIMS applies the filters that it receives from individual SRX Series Firewalls. If you configure the filters for JIMS, the service first applies its own filters to all the SRX Series Firewalls in your network, and then applies the filters that it receives from the individual SRX Series Firewalls.
For detailed configuration steps, see Add Filters
Settings
The Settings menu consists of two tabs:
-
General
-
Logging
Settings on the server view allows you to change the configured values of ports used by JIMS. You can also change the digital certificate that is used for the JIMS local server. Navigate to General from Server View > Settings.
For detailed configuration steps, see Configure the General section
The Logging menu item on the server view allows you to change the log levels. Change the log levels only if Juniper advises changing logs for troubleshooting. Navigate to Logging from Server View > Settings
For detailed configuration steps, see Configure the Logging section
