Automated Threat Remediation for the Enterprise
This use case deploys Juniper Connected Security for an enterprise and illustrates how to secure your network.
Protecting the Campus and Branch
Maintaining reliable and secure campus and branch networks is vital to organizations. With the proliferation of mobile devices and cloud services, securing them has become a fundamental strategic part of enterprise cybersecurity.
Threat remediation is comprised of 2 parts:
Threat detection
Enforcement
Threat Detection
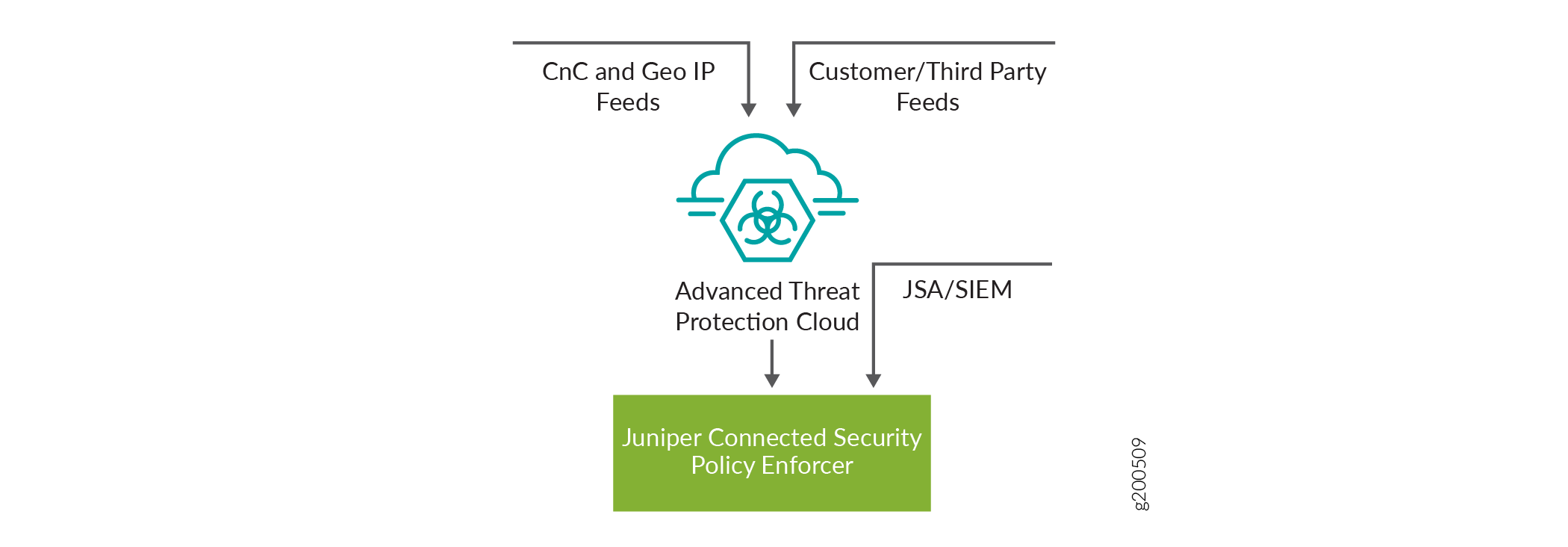
Advanced Threat Prevention Cloud (ATP Cloud) receives threat intelligence and detects threats from these sources:
ATP Cloud feeds, where zero-day and known malware can be detected.
Custom and third-party feeds, where custom blacklists, whitelists, infected hosts, dynamic addresses, and DDoS threats can be detected.
Command & Control (C&C) and Geo IP feeds, where botnet traffic and geo-specific security controls can be detected.
The Juniper Connected Security Policy Controller (comprised of Security Director and Policy Enforcer) controls and enforces threat remediation policies across the network framework (firewalls, routers, and switches). The JSA Series Secure Analytics Appliance (physical and virtual) feeds into the Juniper Connected Security Policy Controller.
Enforcement
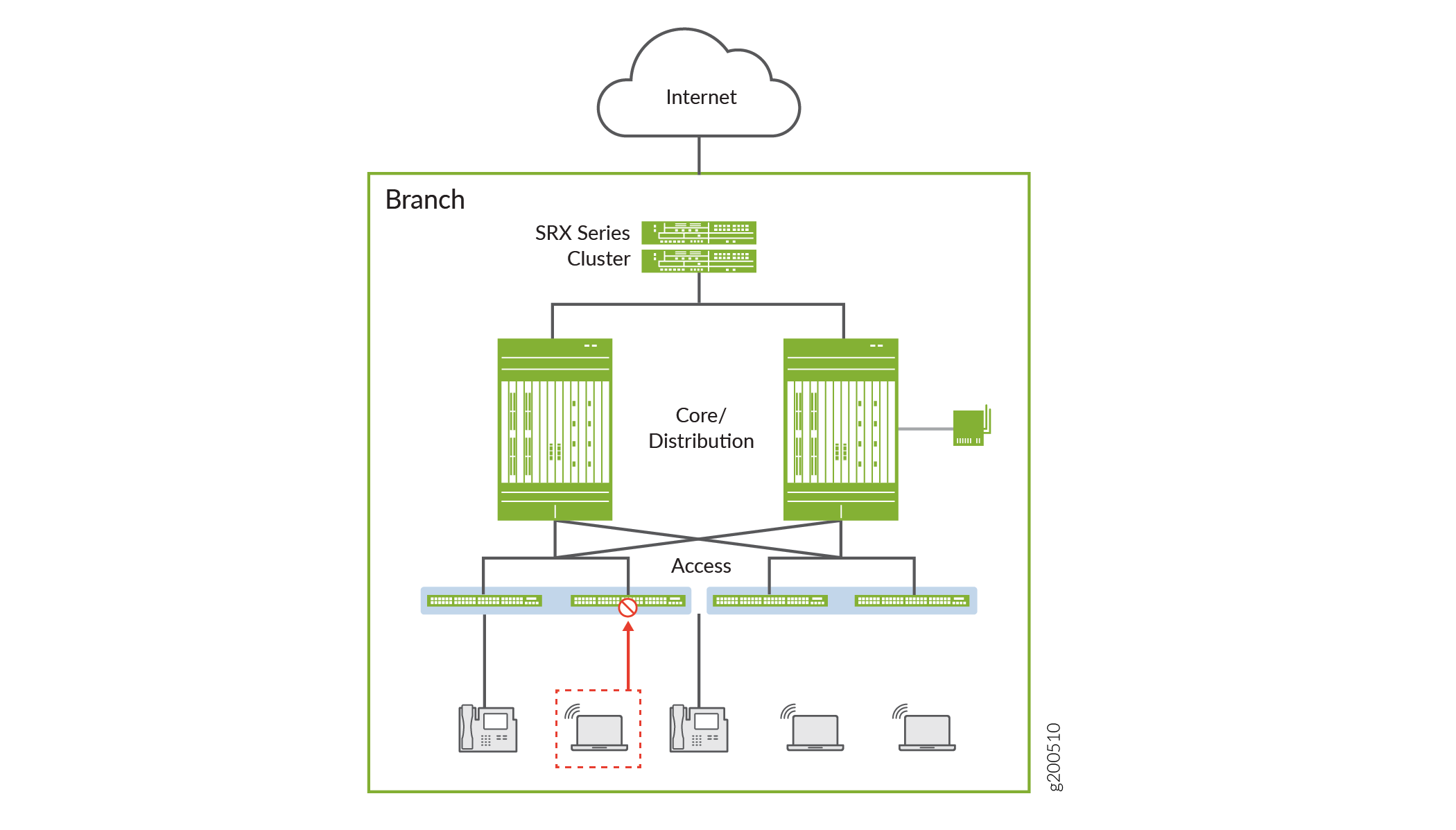
With information learned from threat detection, Policy Enforcer automatically updates security policies in the campus and branch with dynamic address entries and deploys new enforcement to the following network levels:
Security and firewall level: Juniper Networks SRX Series devices
Core and distribution level: Juniper Networks MX/vMX Series routers
Access level containing the following switches:
Juniper Networks EX Series and QFX Series switches
Access switches configured with third-party connectors, such as ForeScout CounterACT
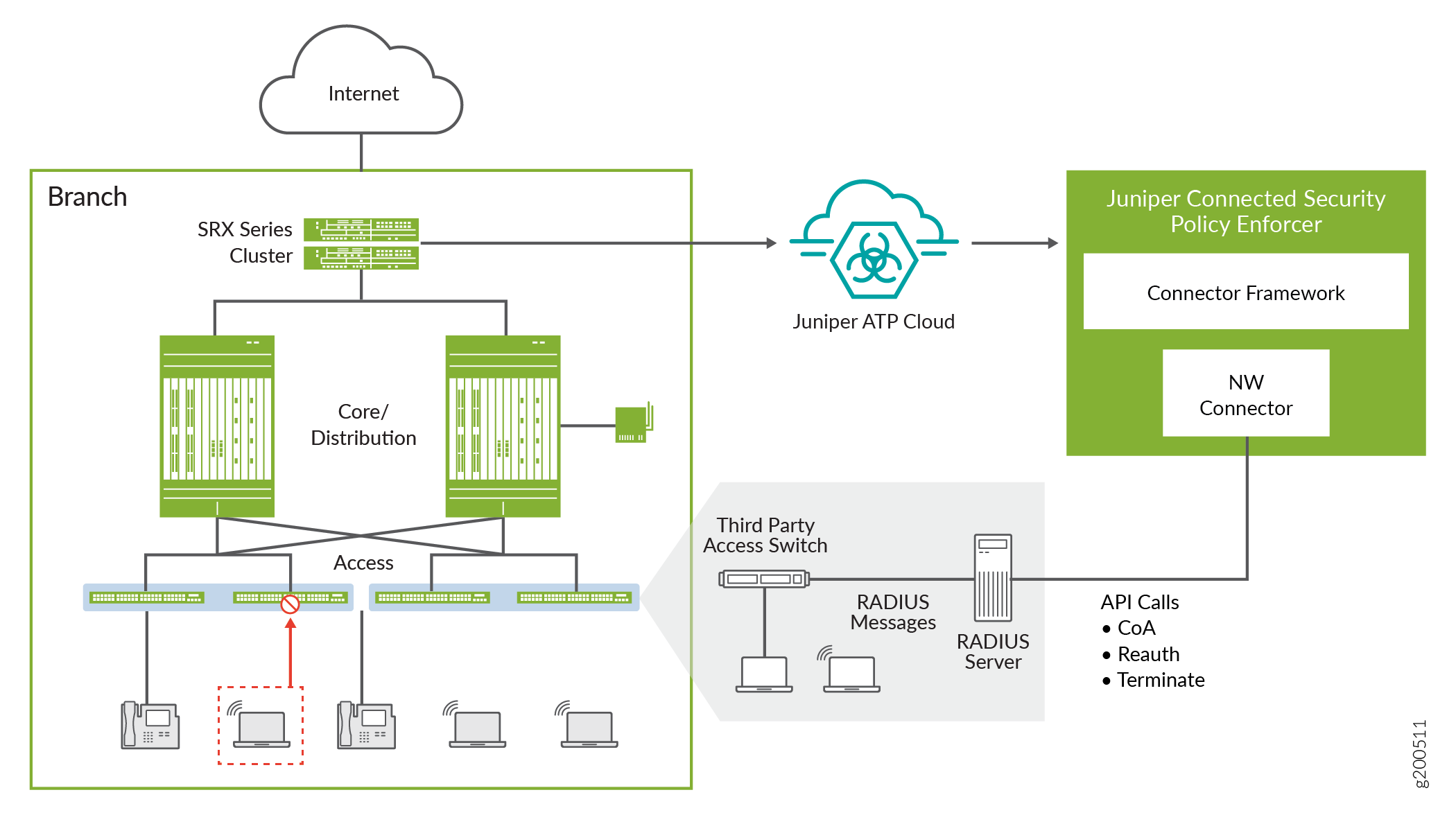
Juniper Connected Security protects the campus and branch physical network by performing real-time remediation of infected hosts and prevents infected end points from moving across different parts of the network. By reducing the time to remediate threats, the amount of time that the network is exposed to attacks is reduced.
