Benefits of Juniper Connected Security
Based on an inside-out security model, the Juniper Connected Security platform delivers pervasive security and automated threat remediation without complexity. It is a user intent-based policy model that provides consistent policy enforcement across multiple enforcement domains, and robust visibility and management. User intent-based policies are created according to logical business structures such as: users/groups, geographical locations, applications, or threat risks. This enables network devices (switches, routers, firewalls and other security devices) to share information, resources, and when threats are detected, dynamically adapt to take remediation actions within the network. Automation is prevalent throughout Juniper Connected Security.
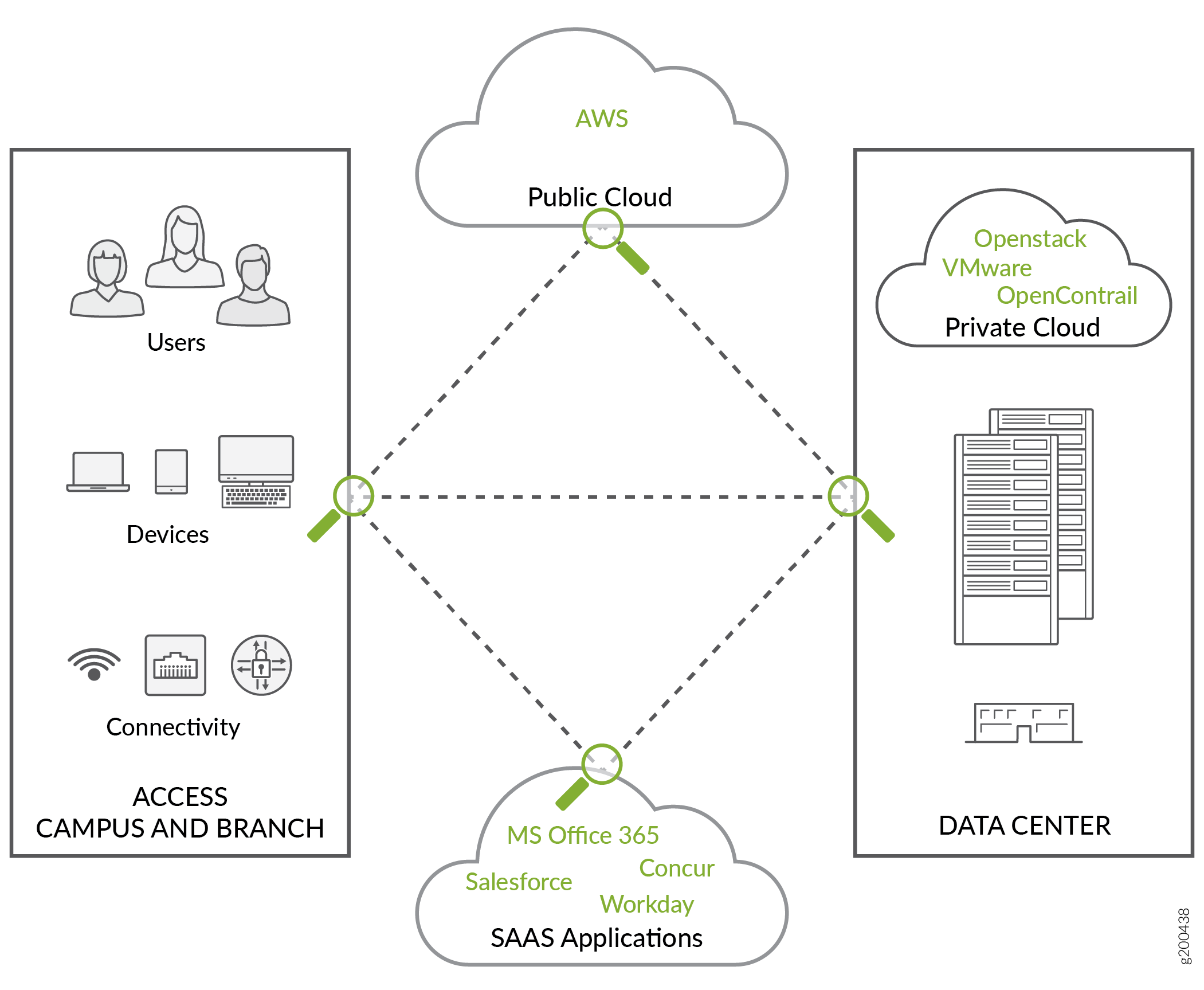
The elements in the Juniper Connected Security provide the following benefits:
Centralized management and visibility. You gain visibility of North–South traffic and the ability to block (and view certain traffic when using the ATP Appliance) East–West traffic when a threat is detected originating from an internal source. The entire network infrastructure is operationalized and managed as a single enforcement domain. As each device in Juniper Connected Security meets the security requirement, it is configured with the same policy as other devices, thereby reducing administrative overhead and simplifying the operation of the whole network.
Comprehensive security. Firewalls are right-sized for their application in the network, and their capabilities are consistent across different deployment models ranging from on-premises physical deployment or private clouds in a data center, to public clouds, to software as a service (SaaS) applications. The Juniper Connected Security extends security on both public and private cloud environments by integrating with native cloud mechanisms to isolate infected hosts within the public cloud (such as AWS) and private cloud (such as Contrail and VMWare NSX) environments. This enables administrators to provide a uniform security policy and threat protection on application resources irrespective of whether they reside on campus, in a local data center, or in a public or private cloud.
Protection from advanced malware. Elements of the Juniper Connected Security (ATP Cloud integrated with SRX/vSRX, and Advanced Threat Prevention Appliance) automatically detect known and unknown threats. The Juniper Connected Security platform gathers and transforms the threat intelligence information into actionable items for the various enforcement points, such as blocking or quarantining those threats at the network layer to prevent further propagation.
Multi-vendor integration. Juniper Connected Security adopts an open, multivendor ecosystem to detect and enforce security across Juniper products and solutions, as well as on third-party devices through Juniper’s ecosystem partners. A portfolio of APIs provides integration with ecosystem partners and vendors in public and private clouds, as well as with SaaS applications. This fosters a collaborative and comprehensive approach to network security.
Access and application mobility. Elements of the Juniper Connected Security secure and consolidate threats from different sources to protect network access for all users, devices (laptops, mobile devices, and so on) and connectivity methods (wireless and wired).
