Configure Advanced Threat Prevention Features (SRX Only)
Create Security Intel (SecIntel) profiles and advanced anti-malware profiles and apply them in application policies on WAN Edge devices.
Juniper Networks' Advanced Threat Prevention (ATP) for SRX Series Firewalls offers a comprehensive suite of features designed to detect, analyze, and prevent advanced cyber threats. Juniper Mist supports the following features:
- SecIntel Threat Intelligence Feeds—Juniper's curated security intelligence feeds, SecIntel, provide dynamic and automatic updates to identify and block malicious domains, URLs, and IP addresses. In Juniper Mist, SecIntel profiles enable you to block malicious and unwanted traffic such as Command and Control (C&C) communications, compromised IP addresses or IP subnets, and domains connected to malicious activities.
- Advanced Anti-Malware (AAMW)—Juniper Networks Anti-Malware is a security solution that uses cloud-sourced data to protect against advanced cybersecurity threats. This feature detects and blocks malware and unwanted files on the network before they reach an endpoint. In Juniper Mist, you can create anti-malware profiles for WAN Edge devices, detailing which files need cloud analysis and the steps to take when malware is detected.
-
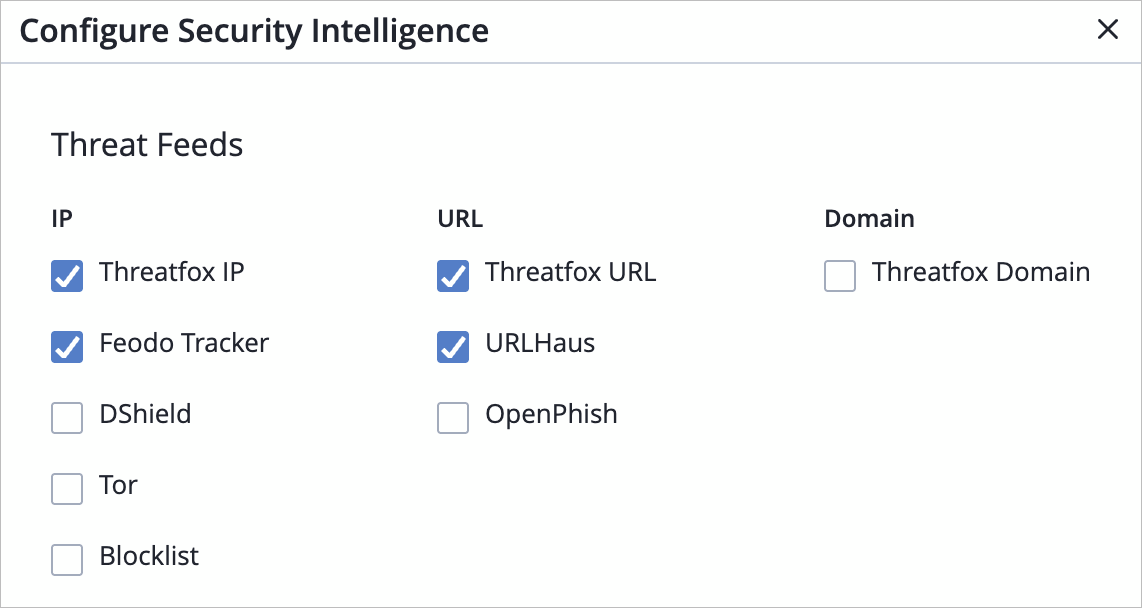
Third-party threat feeds—Sky ATP allows you to enable additional threat intelligence feeds (known malicious IPs, domains and URLs) from external vendors. Once enabled, these feeds will be a part of the Security Intel CC Category on the device. Supported feed types include:
-
IP-based—Threatfox IP, Feodo Tracker, DShield, Tor, Blocklist
-
URL-based—Threatfox URL, URLHaus, OpenPhish
-
Domain-based—Threatfox Domain
-
-
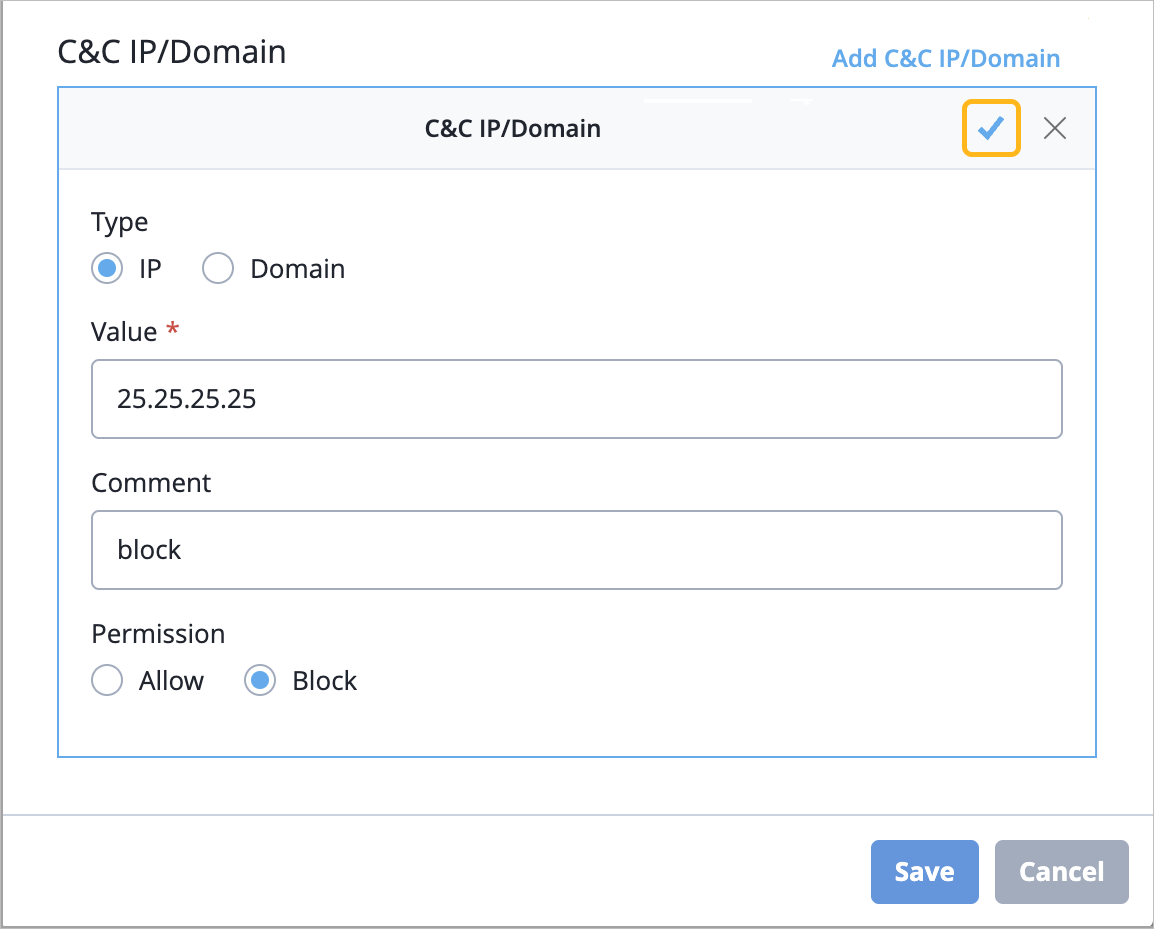
SecIntel custom allowlist and blocklist—You can define customs IP addresses and domains under two categories - Allowlist and Blocklist. These user-defined IP addresses or domains are included under the Security Intel CC Category on the device.
The Advanced Threat Prevention feature is supported on SRX Series Firewalls.
Before You Begin
Ensure you have following available:
- Juniper Advanced Threat Prevention Cloud account and an ATP Cloud Realm created from your account. See Enroll an SRX Series Firewall Using Juniper ATP Cloud Web Portal.
- Your ATP Cloud account associated with a license. For more information, see Software Licenses for ATP Cloud.
Enrollment of a WAN Edge device in ATP Cloud occurs once a realm is created and either a SecIntel or an AAMW profile is associated with a security policy for that device.
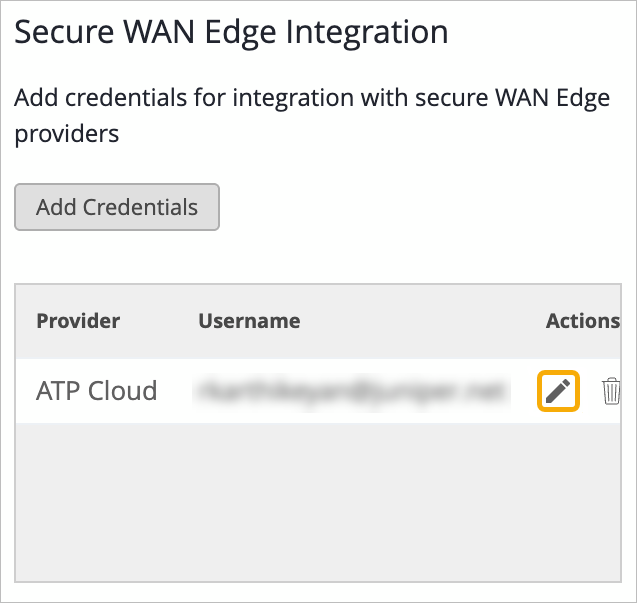
Add Your ATP Credential Details to Your Organization and Specify the Features
Juniper Mist automatically enrolls devices in Cloud ATP Services as required. To integrate Juniper Mist Cloud with ATP Cloud, you need to provide ATP credential details in the Juniper Mist portal.
You'll need to reboot individual or clustered devices enrolled in Cloud ATP Services in order to activate Enhanced Services Mode. This increases the maximum number of services for L7 service processing.
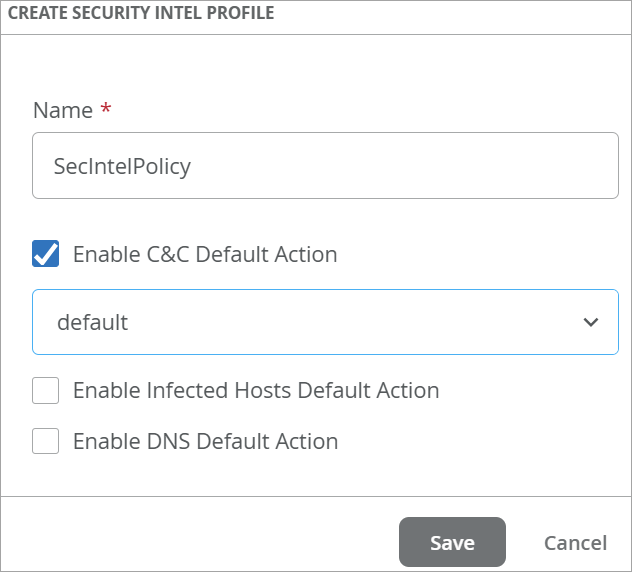
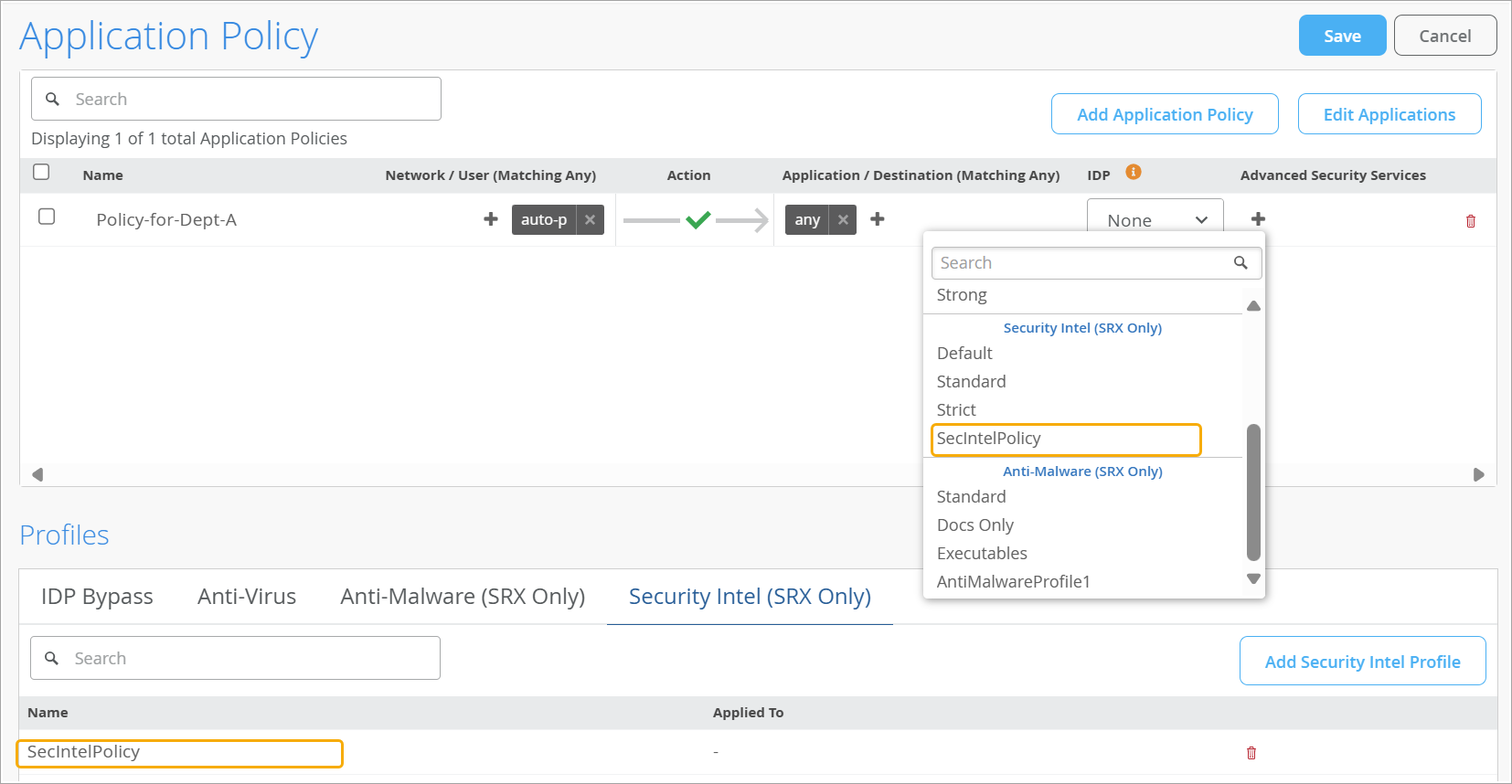
Create Security Intelligence (SecIntel) Profiles
SecIntel offers meticulously curated and verified threat intelligence sourced from Juniper Networks’ Advanced Threat Prevention (ATP) Cloud. This intelligence is delivered to WAN Edge device for effectively blocking Command and Control (C&C) communications at line rate. By enabling automatic and responsive traffic filtering, SecIntel provides real-time threat intelligence.
Many of the feeds include an associated threat score, allowing customers to define security rules and controls that are applied to traffic passing through their devices. The SecIntel security service integrates Juniper threat feeds, including those for C&C communications, malicious domains, and infected hosts. See also: SecIntel Feeds Overview and Benefits.
SecIntel profiles, which can be incorporated into application policies, enable the blocking of malicious and unwanted traffic such as C&C communications, compromised IP addresses or subnets, and domains linked to malicious activities.
To create a SecIntel profile:
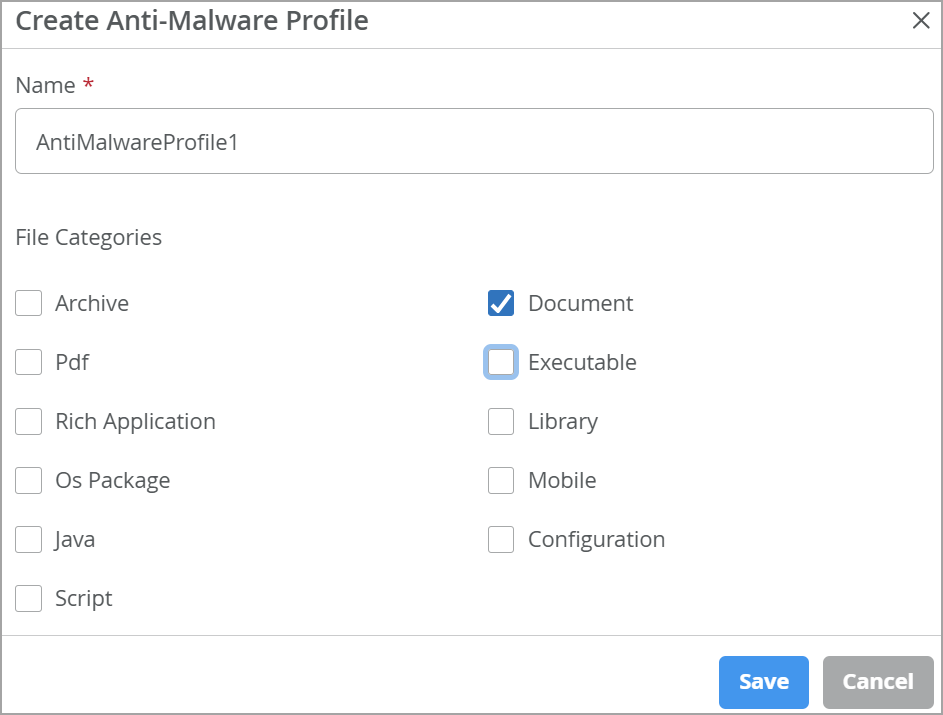
Create Advanced Anti-Malware Profiles
This feature detects and blocks malware and unwanted files on the network before they reach an endpoint. Like SecIntel, anti-malware profiles can be created from the application policy screen and included in an application policy.
To create an Anti-Malware profile:
Apply a Profile to an Application Policy
Before You Begin
In this procedure, you'll apply security profiles to application policies. First, you must complete the following tasks:
-
Create your application policies. For help, see Application Policies.
-
Create your security profiles. For help, see the earlier sections of this topic.
Status Information
You can view basic device monitoring information on the WAN Edges page. From the left menu, navigate to WAN Edges > WAN Edges.
After you click a device on the WAN Edges page, the device details appear. On the details page, you'll see:
-
Advanced Security—The status of security services. A green check mark indicates that the service is active on this device.
Figure 1: Advanced Security Status Details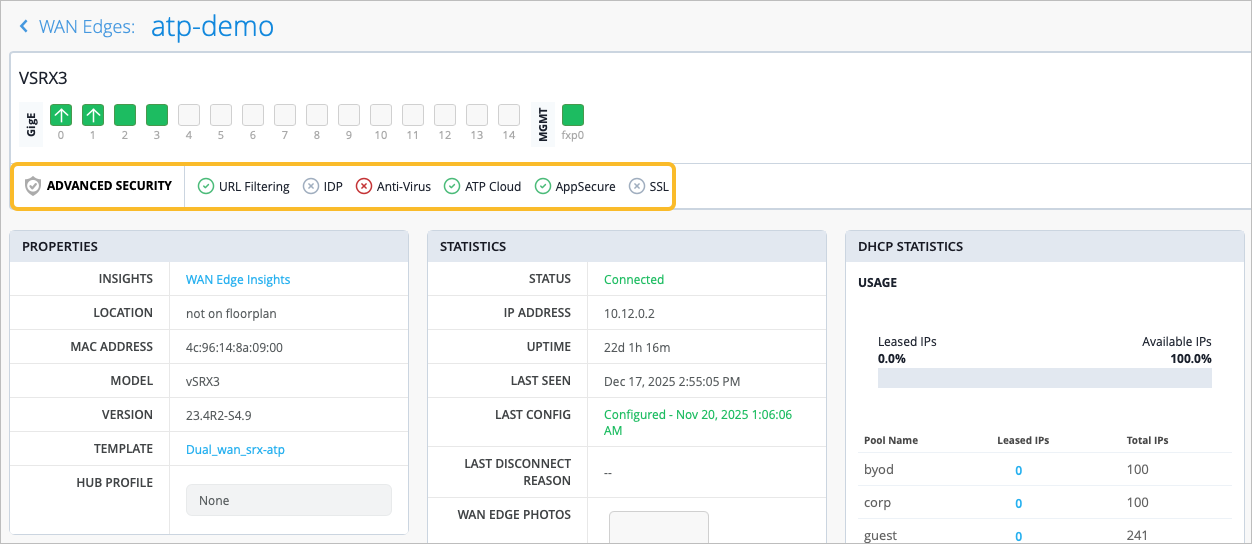
-
Properties—Click WAN Edge Insights to view recent events and other information on the Insights page.
Figure 2: WAN Edge Events Details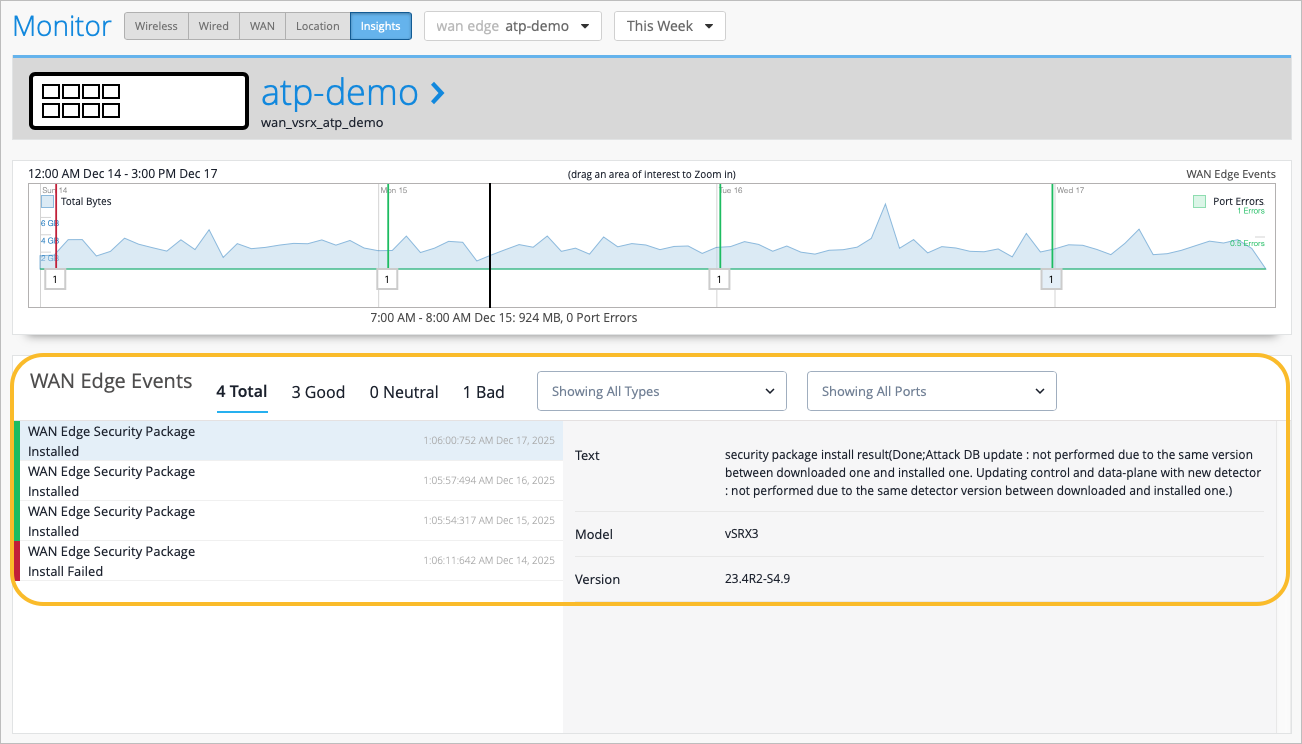 Tip:
Tip:-
By default, the Insights page shows only today's events, but you can select a time period from the drop-down menu near the top-right corner of the page.
-
In the WAN Edge Events list, you can click an event to see a summary on the right side of the page.
-
View Security Events
The Juniper Mist Security Events page, accessible through Site > WAN Edge > Security Events, provides a centralized view of security-related events. It displays a log of security events detected by Juniper Mist to monitor the security posture of the network. Users can filter and view details allowing for proactive security response and analysis.
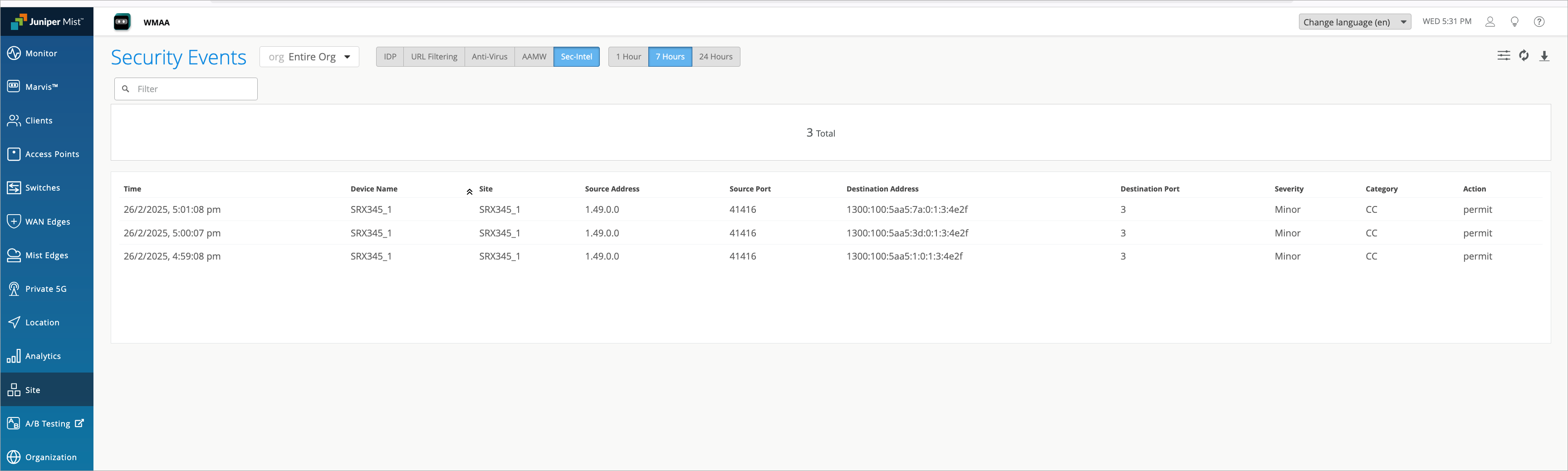
Click one of the tabs AAMW (Advanced Anti-Malware) or SecIntel to see the related security event details. In the example above, the page shows incident details for Command and Control (C&C) with a severity level of Minor. It also indicates the action taken, which is Permit in this case. Additionally, you can view other information such as the device name, site, source and destination addresses, and source and destination ports information.