Use Custom Options to Configure Secure Edge Connector
Use custom options to configure tunnel provisioning or to support site-to-site VPN.
Juniper Mist™ offers custom option for tunnel provisioning. With minimal configuration, your WAN Edge device can establish connections to the SSE using either IPsec or GRE protocols.
Configure Tunnel Provisioning
Before You Begin: Ensure you have the local and remote network account details on hand.
To configure tunnel:
Configure a Site-to-Site VPN
Support for Site-to-Site VPN
You can set up site-to-site VPN using custom option for tunnel provisioning.
A site-to-site VPN is a secure, software-defined network connection that links two or more remote sites over the internet. This type of VPN is crucial for enterprises looking to connect branch offices, data centers, or other remote locations securely and efficiently.
Go to the Juniper Mist portal and navigate to the Secure Edge Connector section at the WAN Edge Templates level, hub profile, or site level.
Click Add Providers and select the Custom option.
Enter the necessary details for tunnel provisioning, such as local and remote network account details, IP addresses, and preshared keys
Define the IKEv2 and IPsec proposals, including encryption and authentication algorithms, Diffie-Hellman groups, and lifetimes. You must select IKE and IPsec values which match the device on another end of the tunnel.
Assign WAN interfaces for primary and secondary tunnels.
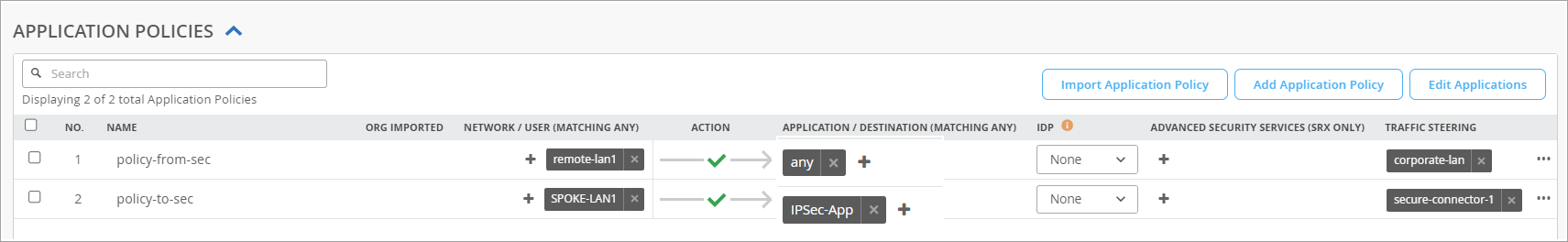
Create a Traffic Steering profile. This profile defines how traffic is routed through the VPN tunnel. This profile is then used in an Application Policy to apply these settings to specific types of traffic.
Create inbound or outbound Application Policies. If you want to allow traffic from the remote network to enter your local network, you need to create a Network representing the remote network. Attach this network to the Custom Secure Edge Connector (SEC) Provider and use it as the source in an Application Policy.
Verification
On Juniper Mist portal, you can verify the established tunnels details in WAN Insights of the device once WAN Edge Tunnel Auto Provision Succeeded event appears under WAN Edge Events.
Once you update the template, the IPsec configuration will be pushed to the WAN Edge device. For first time IPSec deployment, the system takes time to download the software and configuration.
Once the IPSec configuration has been deployed, you can see the IPsec status by navigating to WAN Edge > WAN Edge Name > Secure Edge Connector Details.
You can view BGP neighbor status by navigating to Monitor > Insights > WAN Edge.
To verify the BGP over GRE session you created, you can use the WAN Edge testing tools:
-
WAN Edge > Utilities > Testing Tools.
Open the BGP > Summary tab, or Routes > Show Routes.