ON THIS PAGE
Juniper Secure Connect
Read this topic to get an overview about Juniper Secure Connect solution.
Juniper Secure Connect is a client-based SSL-VPN application that allows you to securely connect and access protected resources on your network. This application when combined with the firewall helps organizations quickly achieve dynamic, flexible, and adaptable connectivity from devices anywhere across the globe. Juniper Secure Connect extends visibility and enforcement from client to cloud using secure VPN connections.
Juniper Secure Connect application includes:
-
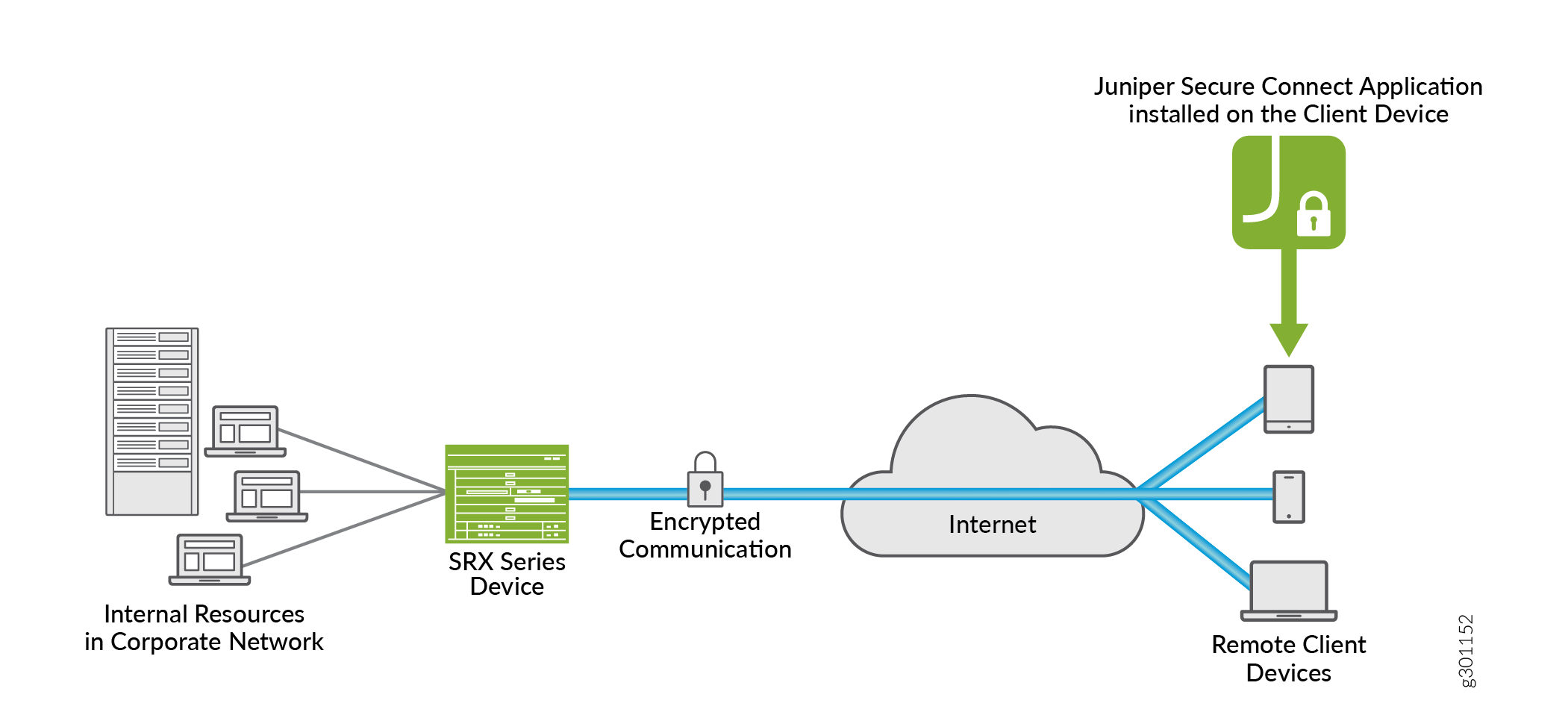
SRX Series Firewall—Serves as an entry and exit point for communication between users with Juniper Secure Connect and the protected resources on the corporate network or in cloud.
-
Juniper Secure Connect application—Secures connectivity between the host clients running Microsoft Windows, Apple macOS, Google Android, and iOS operating systems and the protected resources. Juniper Secure Connect application connects through a VPN tunnel to the firewall to gain access to the protected resources in the network.
Figure 1 illustrates the Juniper Secure Connect remote access solution for establishing secure VPN connectivity for remote users at different locations.
To work with Juniper Secure Connect, see System Requirements.
|
Feature |
Description |
|---|---|
|
Multi-Platform support |
Supports Windows, macOS, Android, and iOS platforms. |
|
Windows Pre-domain logon |
Allows users to logon to the local Windows system through an already established VPN tunnel (using Windows Pre-Logon), so that it is authenticated to the central Windows domain or Active Directory. |
|
Configuration support |
Validates automatically that the most current policy is available before establishing the connection. |
|
Biometric user authentication |
Allows the user to protect their credentials using the operating system’s built-in biometric authentication support. |
|
Multi-Factor Authentication (MFA) |
Allows you to use multi-factor authentication to extend the authentication. |
|
Juniper Secure Connect license |
Licenses are available in 1 year and 3 year subscription models. |
Benefits of Juniper Secure Connect
-
Secure remote access from anywhere with VPN
-
Simple user experience
-
Easy management of remote clients, policies, and VPN events from a single console (using J-Web)
What's Next
-
To configure Juniper Secure Connect, see Juniper Secure Connect User Guide.
-
See the CLI configuration statements related to Juniper Secure Connect at:
default-profile, windows-logon, certificate, traceoptions, profile, global-options, client-config, and remote-access.
The Junos-FIPS devices do not support web-management statement
at [edit system services] hierarchy level. For detailed list of
Junos-FIPS configuration restrictions on the FIPS compliant
firewalls,
see platform specific Junos-FIPS configuration restrictions on the Juniper Tech
Library. Search for the specific
firewall
and navigate to System Admin Guides > FIPS Evaluated Configuration
Guide.
