Remote Device Services Manager (RDSM) Overview
In some service provider use cases, subscriber services span both a broadband network gateway (BNG) and one or more access nodes. In order to minimize the number of network elements requiring operations support system/business support system (OSS/BSS) integration, the BNG and downstream access nodes are represented to back-office systems as a single, logical system. The service provider’s back-office systems provide external configuration and management, authentication, and provisioning for subscriber services on the BNG and its downstream access nodes. To the back-office systems, including PCRF and TACACS+ applications, the BNG and its nodes represent a single addressable network element. The BNG proxies for the downstream devices for service provisioning and deprovisioning.
Starting in Junos OS Release 18.3R1, MX Series routers used as a BNG support remote-device services by means of the remote device services manager (RDSM, using the rdmd daemon).
Figure 1 shows a sample topology for an MX Series BNG using RDSM. The BNG is connected to OLTs that serve as the downstream, remote devices for provisioning subscriber services, in addition to their conventional role of terminating passive optical network (PON) access per individual subscriber access-lines. The OLTs are logical extensions to the BNG, so that the BNG and its downstream access nodes are presented to back-office systems as a single addressable network element. The BNG uses TCP port forwarding to mediate communications between the remote devices and the back-office system. For more information about TCP port forwarding for remote device management access, see TCP Port Forwarding for Remote Device Management.
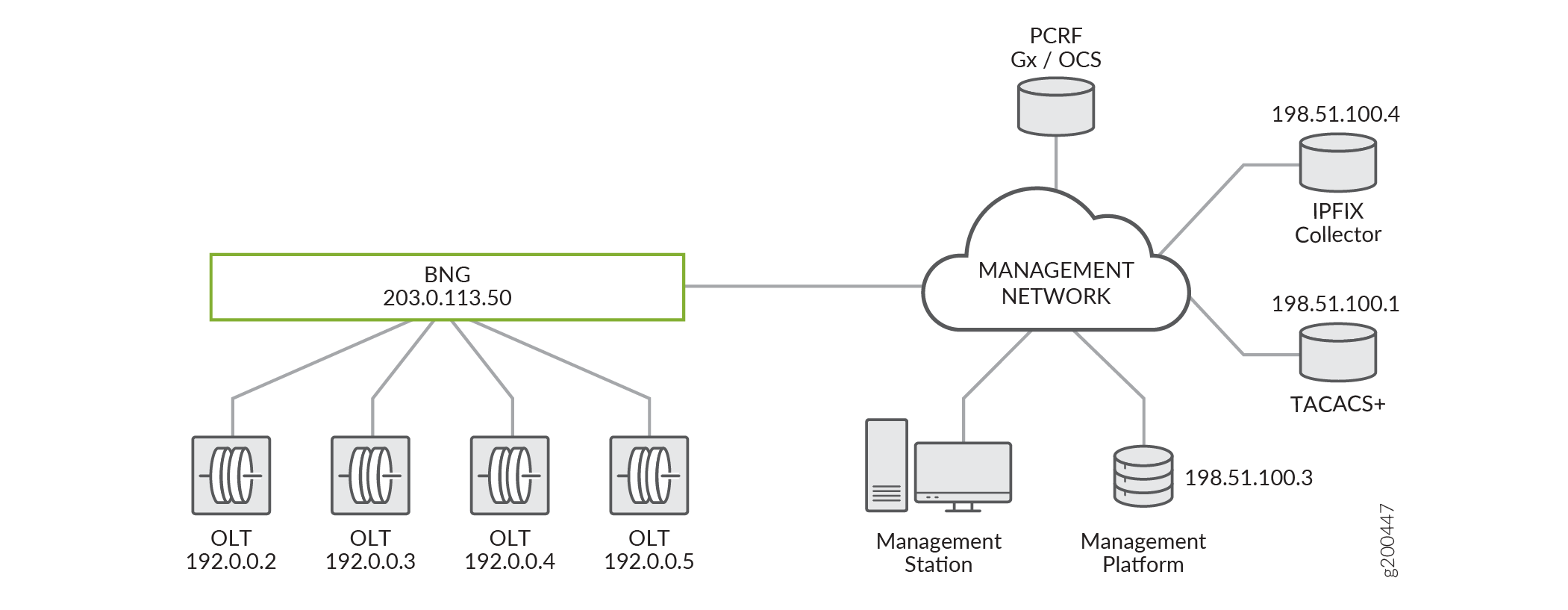
The back-office management and provisioning system uses NETCONF XML protocol over SSH for tasks such as base configuration of the remote device before subscriber negotiation begins, configuration of Layer 2 data paths for new subscribers, displaying remote device status, and troubleshooting the remote device. The BNG demultiplexes requests from the management system to the remote devices. Multiple NETCONF sessions can exist to a single remote device.
In this sample topology, the system includes a management platform, PCRF, TACACS+ server, and an IPFIX collector:
The PCRF sources the subscriber services that are provisioned locally on the MX BNG locally and remotely on the OLTs.
The TACACS+ server is used to authenticate and validate access to the remote device, perform system accounting, and control operator access. The remote device dynamically initiates a TACACs+ TCP session in response to NETCONF protocol configuration from an external management platform or station. The BNG multiplexes requests from the remote devices to the TACACS+ server.
For remote device access from the back-office system, the server initiates TACACS+ authentication for the following conditions:
The BNG initiates service configuration for a remote device. The TACACS+ server authenticates the session when the NETCONF TCP socket used by the BNG to provision or deprovision the remote service is opened. After authentication, the session is maintained without authentication or authorization for each remote procedure call (RPC) used for the service action.
The external management station is used to configure the remote device or access it for monitoring (
showcommands) or troubleshooting.
The IPFIX collector receives records containing system and connection-level statistics and other information from the MX BNG, which operates as an IPFIX mediator between the OLTs (IPFIX exporters) and the external IPFIX collector. The BNG proxies for the downstream devices. It acts as an IPFIX collector to receive data from the remote devices and as an IPFIX exporter to send data upstream over a single TCP or TLS session to the collector. For more information about using the BNG as an IPFIX mediator, see IPFIX Mediation on the BNG.
Remote Services
The MX BNG represents a single point of management to external authority for all subscriber services, local and remote. The remote services are also represented by locally configured dynamic service profiles that are referenced by external authority in the same way as local services on the BNG. Consequently, there is a consistent interface between external authority and the BNG for all service actions. The NETCONF XML Management Protocol is used for provisioning and deprovisioning the remote services.
Local subscriber services are defined by dynamic service profiles with zero or more arguments to satisfy subscriber-specific policies. External authorities, such as PCRF, generally use a referential model to provide services. The PCRF charging rule specifies the name of the dynamic service profile and argument values that are applied during subscriber negotiation for service provisioning (activation) or as an update after the subscriber is active. The service is presented to the remote device by the RDSM XML dictionary for that device to parse, interpret, and apply, allowing the charging-rule or service from external authority to be opaquely passed to the remote device with minimal processing. The remote service profile might include one or more variables to define service parameters.
However, remote services can also be applied in a non-referential manner. In this case, the external authority specifies the remote service referentially as it would for a local service. The remote service profile includes one or more variables to define service parameters. The RDSM then uses the data dictionary assigned to the remote device to configure the service on that device. The content of the RDSM dictionary for a device is different depending on whether the service provider uses the referential or non-referential method.
The remote dynamic service profile is very lightweight compared to a local service profile, which can include a large number of configuration stanzas. A remote dynamic service profile contains only two things:
You must specify that the dynamic profile type is
remote-device-service. That configuration prevents the profile from being used as a local service profile. This means that you cannot configure a dynamic service profile to be dual-purpose (both local and remote).The remote service profile can optionally include a variable stanza to pass argument values to the remote device. The variable stanza can be used for either the referential or non-referential methods.
Any additional configuration fails commit check. Because the remote service profile is so specific, a dedicated service profile is required for each remote service. For the external authority, this means that each remote service requires a separate PCRF charging rule.
Process Flows for RDSM Provisioning and Deprovisioning
Subscriber services are provisioned and deprovisioned as follows:
Provisioned during subscriber login. The services can be sourced from the PCRF in response to initiation with Gx CCR-I/CCR-A message exchanges.
Deprovisioned during subscriber logout.
Provisioned or deprovisioned for active subscriber sessions in response to external authority, such as Gx RAR messages from the PCRF.
Figure 2 shows the process flow when RDSM successfully provisions services on three eligible remote devices, OLT1, OLT2, and OLT3, by instantiating the upstreamBW service profile.
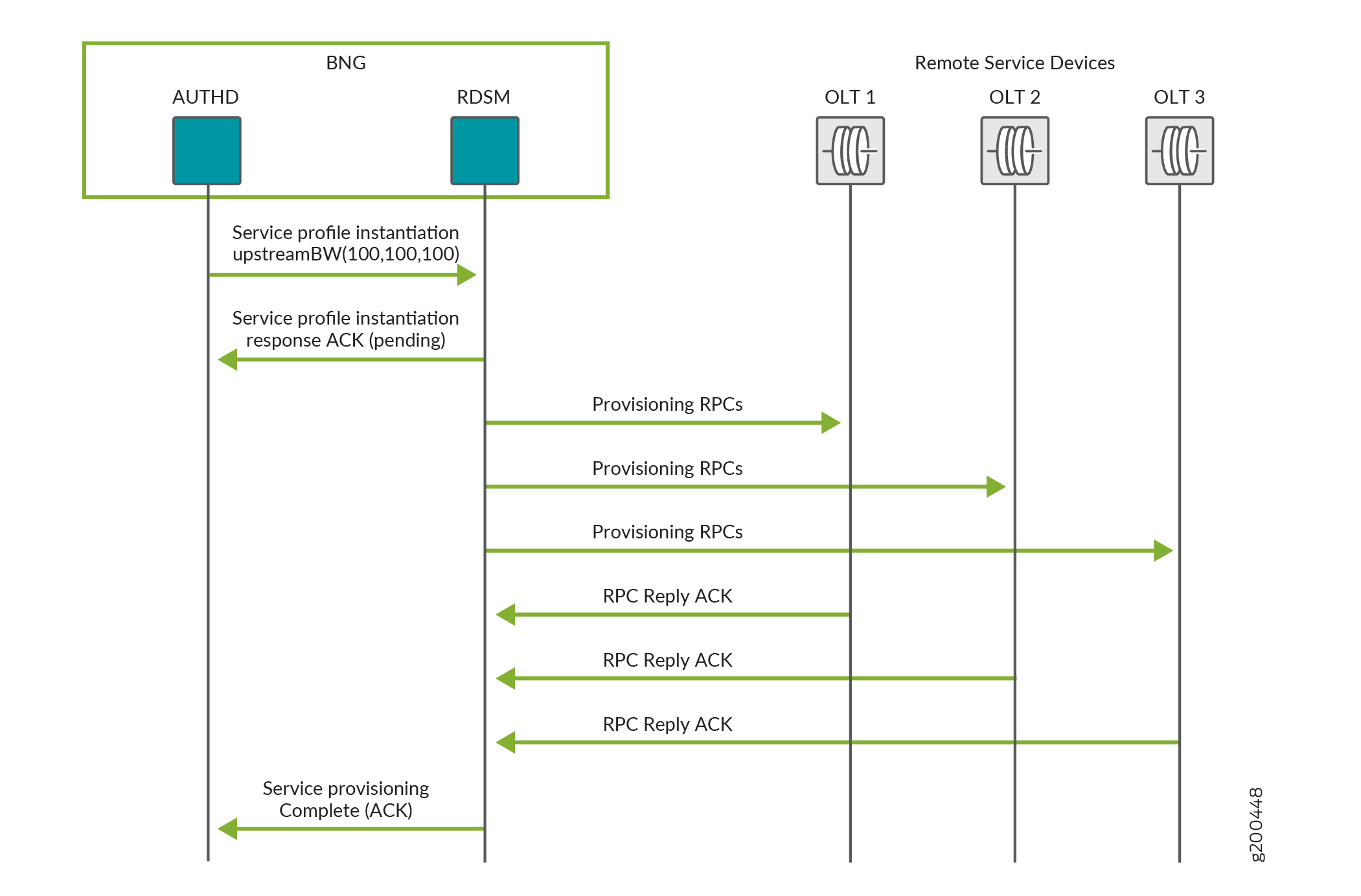
Service provisioning begins when a subscriber logs in and authd sends a request to RDSM to instantiate the remote service profile on eligible remote devices during the negotiation.
RDSM establishes a list of remote devices that are eligible for the service to be provisioned:
The Layer 2 access domain for the device must match the subscriber location. The access domain consists of a configured list of VLAN ranges or individual VLAN IDs. The subscriber’s outer VLAN tag must be on this list.
The NETCONF TCP connection to the device must be up. Although a device in the down state is not eligible for provisioning, it might be available for reconfiguration if it transitions later to the up state.
RDSM performs an initial validation before it responds to the remote service profile instantiation request:
When validation passes, RDSM sends a service profile instantiation pending ACK response to authd. The service provisioning is now pending.
If validation fails, RDSM returns a NACK response to authd and abandons service provisioning.
The validation checks performed by RDSM typically do not fail for active subscriber sessions. Reasons for failure include the following:
No remote device has a subscriber location that matches the access domain.
The dictionary located on the BNG does not include an entry for the requested remote service profile. Consequently there are no RPCs to provide the service variables and install the service.
RDSM resolves any required parameters for each remote device; at a minimum, this includes the subscriber identifier.
RDSM then uses the dedicated NETCONF session to each of the eligible devices to issue a series of RPC calls as specified in the dictionary for provisioning the service.
Service provisioning takes place in parallel for the eligible devices. Provisioning fails for a device when either of the following occurs:
The RDSM receives an explicit error for any RPC call.
The response times out.
The following ERRMSG event is logged in either case:
remote device device-name ip-address service service-name provisioning failed for subscriber subscriber-idRemote devices that are successfully provisioned return an ACK response to RDSM.
If one or more remote devices fails to be provisioned, RDSM rolls back the service on every remote device that was successfully provisioned. RDSM uses the dedicated NETCONF session to each of these devices to issue a series of RPC calls as specified in the dictionary for deprovisioning the service.
RDSM sends an out-of-band notification to authd to report whether the remote service was provisioned on the remote devices.
When provisioning is successful for all remote devices, RDSM sends a service provisioning complete response to authd.
If one or more of the eligible remote devices fails to be provisioned, RDSM reports a provisioning failure to authd.
Figure 3 shows the process flow when RDSM successfully updates subscriber services on three eligible remote devices, OLT1, OLT2, and OLT3 by instantiating the upstreamBW service profile with different parameter values than were used during login.
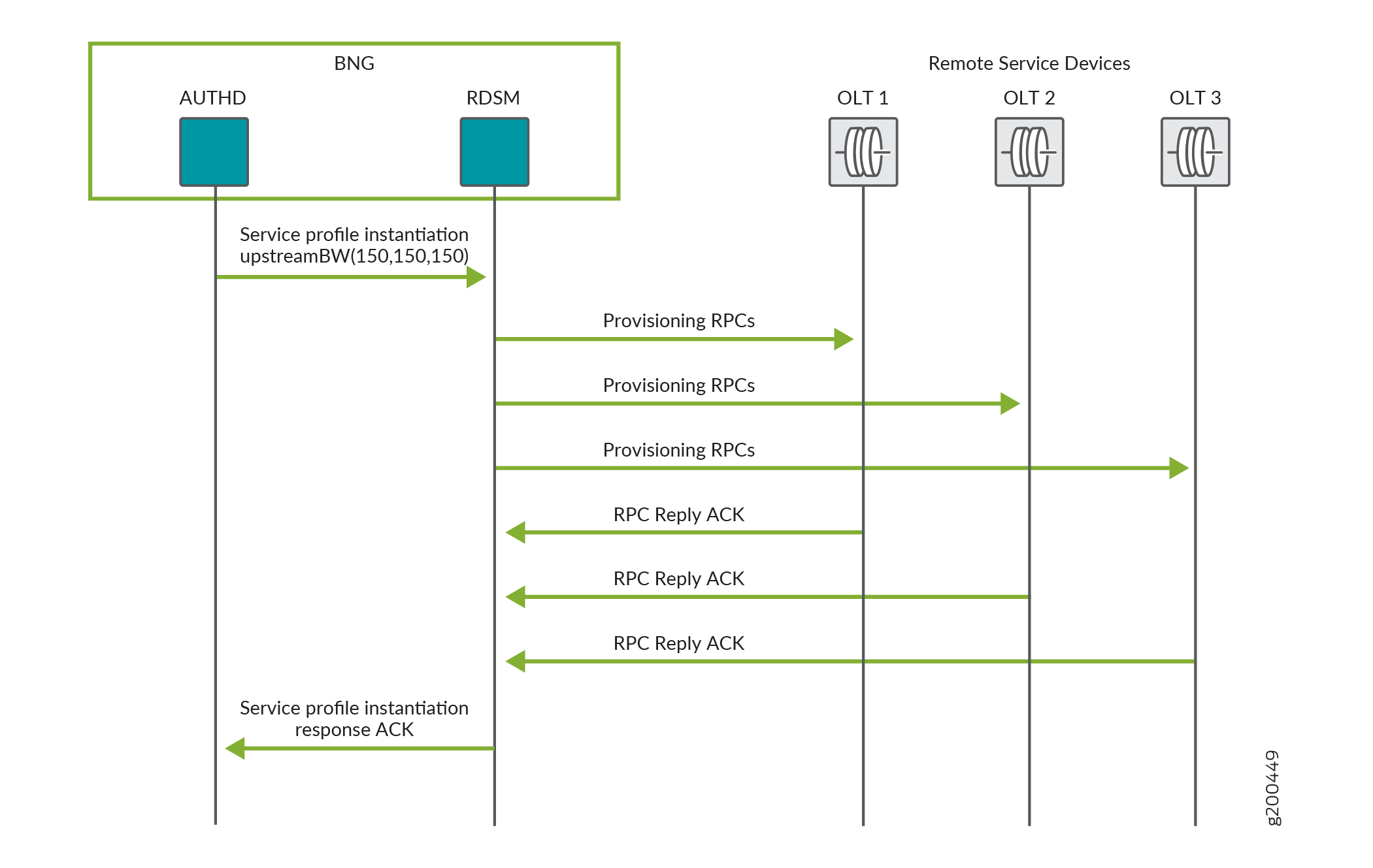
Updating subscriber services begins when authd sends a request to RDSM to instantiate the remote service profile to update the service. The process flow is the same as for the subscriber login flow, except that RDSM does not respond to the instantiation request until all processing required to provision the service is complete. That means that when the validation check passes, RDSM does not send a service profile instantiation pending ACK response to authd; if validation fails, RDSM does return a NACK response to authd and abandons service deprovisioning.
Figure 4 shows the process flow when RDSM successfully deprovisions services to update the three eligible remote devices, OLT1, OLT2, and OLT3, by deinstantiating the upstreamBW service profile.
The deprovisioning process flow is the same for both a subscriber logout and an update request from authd.
RDSM does not respond to authd until all required processing to deprovision the service has completed (including any retry of failures); this allows subscriber logout to proceed regardless of the deprovisioning outcome.
Service deprovisioning typically does not fail; if it does, then you may have to take some corrective action on the remote device for deprovisioning to succeed.
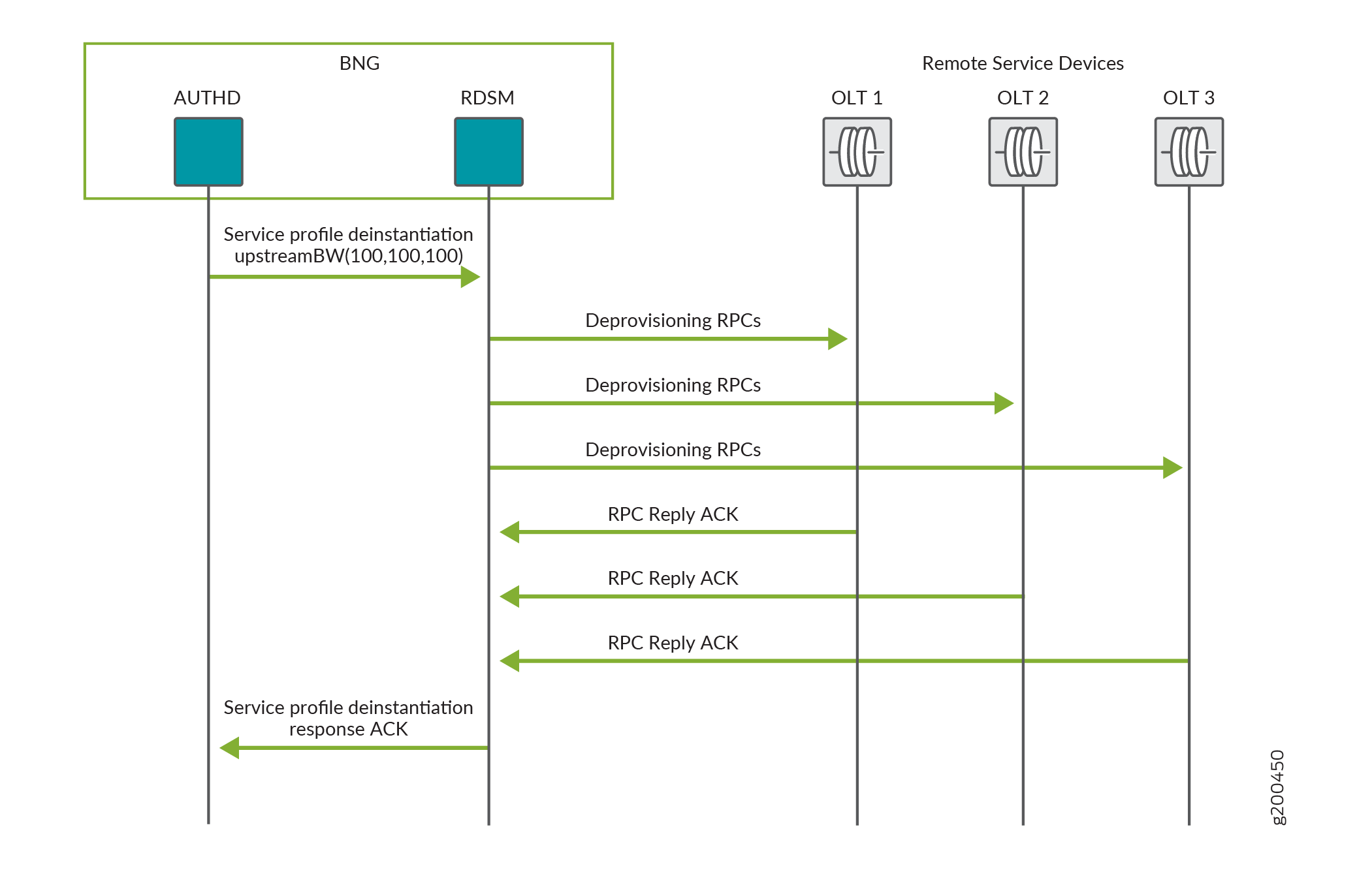
Service deprovisioning begins when either of the following occurs:
A subscriber logs out and authd sends a request to RDSM to deinstantiate the remote service profile on eligible remote devices.
authd sends an update request to RDSM to deinstantiate the remote service profile on eligible remote devices.
RDSM maintains a list of remote devices that are provisioned with the service. If the NETCONF TCP connection to the device is down, deprovisioning is not attempted because it is assumed to have occurred by some other means. For example, the device may have been reconfigured with a default, baseline configuration and subsequent operator action initiated reconfiguration by the BNG for all active subscriber services.
RDSM performs an initial validation before it responds to the remote service profile deinstantiation request:
When validation passes, RDSM does not send a response to authd.
If validation fails, RDSM returns a NACK response to authd and abandons service deprovisioning. Reasons for a validation failure include the following:
No configured remote device is in the up state.
The dictionary located on the BNG does not include an entry for the requested remote service profile or deprovisioning action. Consequently there are no RPCs to provide the service variables and remove the service.
The validation checks performed by RDSM typically do not fail for active subscriber sessions.
RDSM resolves any required parameters for each remote device; at a minimum, this includes the subscriber identifier.
RDSM then uses the dedicated NETCONF session to each of the eligible devices to issue a series of RPC calls as specified in the dictionary for deprovisioning the service. Service deprovisioning takes place in parallel for the eligible devices. Deprovisioning fails for a device when either of the following occurs:
The RDSM receives an explicit error for any RPC call.
The response times out.
In either case, RDSM retries the deprovisioning action up to 5 times, at 5-second intervals. If the attempts all fail, then the following ERRMSG event is logged in either case:
remote device device-name ip-address service service-name de-provisioning failed for subscriber subscriber-idRemote devices that are successfully deprovisioned return an ACK response to RDSM.
RDSM sends an out-of-band notification to authd to report whether the remote service was deprovisioned on the remote devices.
When deprovisioning is successful, RDSM sends a service deprovisioning complete response to authd, which then completes the subscriber logout.
In the case of an update request rather than a subscriber logout, RDSM sends a service profile deinstantiation complete response to authd, which completes the service session clean-up.
If one or more of the eligible remote devices fails to be deprovisioned, RDSM reports a deprovisioning failure to authd.
RDSM Dictionary for Implementing Service Actions
An XML dictionary stored locally on the BNG is an integral component of remote device service management. Each remote service provisioned by the external authority must have an entry in an RDSM dictionary on the BNG. The dictionary translates the PCRF-sourced charging rule to a set of vendor-specific remote procedure calls (RPCs) in the entry associated with the service. The RPCs then provision or deprovision the service. Because the RPCs are vendor-specific, so is the dictionary. This means that separate dictionaries are required for each vendor’s remote device. For a given vendor’s devices, different software releases on the devices may require different dictionaries as well.
The dictionary format is sufficiently flexible to support both referential services and non-referential services, where:
A referential service means that the entire service, including arguments, is presented opaquely to the remote device as received from external authority via the RDSM dictionary. The dynamic service profile can include a variable stanza that is used by the dictionary during translation of the arguments. The remote device parses, interprets and applies the arguments on its own without any interpretation or parsing by the BNG.
A non-referential service means that all arguments supplied by the external authority must be resolved and provided to the remote device individually by one or more RPCs. In this case, the dynamic service profile may require a variable stanza that is used by the dictionary during translation of the arguments.
In either case, the dictionary must specify the means—typically a Layer 2 location—to identify the subscriber suitable for the remote device to distinguish one subscriber from another.
The XML RDSM dictionary has the following general format:
<junos-rdm-dictionary>
<junos-rdm-parameters>
<junos-rdm-parameter>
<junos-rdm-name>...</junos-rdm-name>
<junos-rdm-source>...</junos-rdm-source>
<junos-rdm-index>...</junos-rdm-index>
</junos-rdm-parameter>
<junos-rdm-parameter>
...
</junos-rdm-parameter>
</junos-rdm-parameters>
<junos-rdm-services> <junos-rdm-service>
<junos-rdm-name>...</junos-rdm-name>
<junos-rdm-provision>
<junos-rdm-service-configuration>
...
</junos-rdm-service-configuration>
</junos-rdm-provision>
<junos-rdm-deprovision>
<junos-rdm-service-configuration>
...
</junos-rdm-service-configuration>
</junos-rdm-deprovision>
</junos-rdm-service>
</junos-rdm-services>
<junos-rdm-open-configuration>
<junos-rdm-rpc>...</junos-rdm-rpc>
<junos-rdm-rpc>...</junos-rdm-rpc>
</junos-rdm-open-configuration>
<junos-rdm-edit-configuration>
<junos-rdm-rpc>...</junos-rdm-rpc>
<junos-rdm-rpc>...</junos-rdm-rpc>
<junos-rdm-rpc>...</junos-rdm-rpc>
</junos-rdm-edit-configuration>
<junos-rdm-commit-configuration>
<junos-rdm-rpc>...</junos-rdm-rpc>
<junos-rdm-rpc>...</junos-rdm-rpc>
</junos-rdm-commit-configuration>
<junos-rdm-close-configuration>
<junos-rdm-rpc>...</junos-rdm-rpc>
<junos-rdm-rpc>...</junos-rdm-rpc>
</junos-rdm-close-configuration>
</junos-rdm-dictionary>
Table 1 defines the individual components of the dictionary.
junos-rdm-parameters |
Parameter block that lists individual parameters that configure the service. |
junos-rdm-parameter |
Individual parameter. |
junos-rdm-name |
In the parameter block, this element identifies the subscriber on the remote device or the PCRF argument. Use the subscription-id for the subscriber and the name of the argument for any argument specified in the PCRF. |
junos-rdm-source |
Source of the parameter value:
|
junos-rdm-index |
Index, such as an enumerated type value, that resolves the parameter from the specified source. The subscriber-session source requires this to map the parameter to an SDB attribute used to resolve the parameter value. For example, for some use cases, the PCRF subscription-id is stored in the subscriber SDB entry that is referenced by an index (attribute type) to resolve this parameter. |
junos-rdm-services |
Service block that lists one or more remote services supported by the device. |
junos-rdm-service |
Individual remote service defined by service name, provisioning configuration, and deprovisioning configuration. |
junos-rdm-name |
In the service block, this element is the name of the service. It is the base service name, without arguments, of the service sourced from the PCRF. |
junos-rdm-provision |
Provisioning block that includes provisioning configuration. |
junos-rdm-deprovision |
Deprovisioning block that includes deprovisioning configuration. |
junos-rdm-service-configuration |
Service configuration that includes one or more RPCs to provision or deprovision the service. When arguments are specified in the PCRF service for provisioning, the RPCs include those arguments. |
junos-rdm-open-configuration |
Block that includes zero or more RPCs to begin configuration of the remote device. |
junos-rdm-edit-configuration |
Block that includes one or more RPCs to edit the configuration and apply service provisioning or deprovisioning actions to the device in bulk, by referencing the junos-rdm-provision or junos-rdm-deprovision block for the specified service. The configuration for each service that is part of the bulk update to the remote device is included. |
junos-rdm-commit-configuration |
Block that includes zero or more RPCs to commit the edits to the remote device. |
junos-rdm-close-configuration |
Block that includes zero or more RPCs to end configuration of the remote device. |
junos-rdm-rpc |
Individual RPC to configure the remote device. |
For remote device configuration, the edit configuration is always required to provision or deprovision the service. In some use cases, the open, commit, and close configuration blocks might be optional.
Additional Features for Use with an RDSM Access Model
The features in this section are not required for RDSM, but may be useful in certain use cases or topologies.
A locally generated username is used in interactions with an
external authority to authenticate dynamic VLAN, DHCPv4, and DHCPv6
subscribers. Typically, subscriber VLAN tags are included in the username
by configuring the interface-name option for the username-include statement.
Similarly, subscriber VLAN tags are included in the subscription
identifier for PCRF interactions by configuring the interface-name option for the subscription-id-data-include statement.
By convention, the interface name has the following format in both cases:
underlying-IFD-name:outer-vlan-tag[-inner-vlan-tag]
For some use cases with the RDSM access model, the outer VLAN tag is unique across the system. This means that you can use a different format that excludes the underlying IFD name:
outer-vlan-tag[-inner-vlan-tag]
To generate the username format without the underlying IFD name,
you specify the vlan-tags option instead of the interface-name option with the username-include statement. See Configuring VLAN Interface Username Information for
AAA Authentication and Creating
Unique Usernames for DHCP Clientsfor more information.
To generate the subscription ID format without the underlying
IFD name, you specify the vlan-tags option instead of the interface-name option with the subscription-id-data-include statement. See Configuring the PCRF Partition for more
information.
Some customer networks might have more than one deployment model or use case that results in the MX Series BNG for each case interacting with the same PCRF back-end. In this situation, you might need to distinguish between the use cases for the PCRF.
The Diameter Capability Exchange messages between peers carry the Diameter Product-Name AVP. You can configure nondefault values for the use cases so the PCRF can discriminate between the messages. See Messages Used by Diameter Applications and Diameter AVPs and Diameter Applications for more information.
Response to the External Authority by authd on Success or Failure
How authd responds to the external authority depends on the following:
The operation being performed for example, provisioning during subscriber login versus updating an existing subscriber session.
The external authority, Gx (PCRF).
Table 2 describes how the authd response varies when the service provisioning or deprovisioning actions are successful.
Operation |
Gx |
|---|---|
Login |
authd initiates CCR-I/CCA-I message exchange to provision the subscriber session. When all services in the CCA-I are provisioned, authd sends a CCR-U message that indicates the service is active for each charging-rule in the CCA-I. Status reporting for local dynamic services is delayed until remote services provisioning completes. |
Update |
Deprovisioning is applied before provisioning for services included in the same PCRF RAR message. When deprovisioning and provisioning is completed for all service actions included in the PCRF RAA, authd sends an RAA response with a Rule-Report that indicates the service inactive/active state for each charging rule specified in the RAR. Status reporting for local dynamic services is delayed until remote services processing completes. |
Logout |
authd initiates a CCR-T/CCA-T message exchange to notify PCRF of subscriber termination. authd initiates deprovisioning for all services configured for the subscriber session. |
Service device in the up state after the |
authd takes no further action when it receives an out-of-band notification from RDSM that the service action succeeded. For example, it does not send a CCR-U message that indicates the service is active for the corresponding charging rule. |
Table 3 describes how the authd response varies when the service provisioning or deprovisioning actions fail.
Operation |
Gx |
|---|---|
Login |
authd initiates a CCR-I/CCA-I exchange to provision the subscriber session. When authd receives notification of failure in the service profile instantiation response or out-of-band from RDSM, authd stops processing any remaining services. authd sends a CCR-U message that reports the following:
authd allows the subscriber session negotiation to complete and reach the active state. |
Update |
Deprovisioning is applied before provisioning for services included in the same PCRF RAR message. The process varies depending on the actions that fail.
|
Logout |
authd initiates a CCR-T/CCA-T message exchange to notify PCRF of subscriber termination. authd initiates deprovisioning for all services configured for the subscriber session. When authd receives notification of failure in the service profile instantiation response or out-of-band from RDSM, authd continues with the logout, including deprovisioning any remaining services. |
Last service device in down state after the |
authd takes no further action when it receives an out-of-band notification from RDSM that the service action failed. For example, it does not send a CCR-U that indicates the service is inactive for the corresponding charging rule. Affected subscriber sessions are maintained. |
Operator Reconfiguration of Remote Devices
In some circumstances, you might need to manually provision services on a remote device to resynchronize the device with all matching subscriber services that are active and configured on at least one other remote device. Manual provisioning is required in the following scenarios:
A new remote device is connected to the BNG after one or more subscriber sessions have been negotiated on other remote devices and remote services have been provisioned on those devices.
The NETCONF session to a remote device with one or more provisioned remote services transitions to the down state, then later recovers and transitions back to the up state. This is effectively the same as a new device being connected to the BNG.
After the NETCONF session is established to the remote device in either of these situations, an ERRMSG event is logged that the device is up. No remote services are currently provisioned on the device. RDSM establishes a list of subscriber remote services that are eligible to be provisioned on the device. These services must be either active or in the process of being provisioned. A separate ERRMSG event is logged, indicating that services are pending reconfiguration:
remote device device-name ip-address has number services pending
reconfiguration
You use the request services remote-device-management reconfigure
service-device command to provision all active (or in process)
subscriber services that map to the access domain associated with
the device. The reconfiguration request triggers bulk provisioning
of services on the device. If the provisioning of one service fails,
the entire bulk provisioning is considered a failure and any successfully
provisioned services are rolled back. In this case you have to issue
the command again. The rollback applies only to each bulk provisioning
attempt, so you can control the effects of a bulk provisioning failure
by setting a bulk limit.
The remote device is eligible to be automatically provisioned with subscriber services without operator intervention for subscriber logins that occur after the NETCONF session is established.
You can issue a reconfiguration request at any time when the remote device is up. When remote device reconfiguration begins, any new service actions resulting from new subscriber negotiation or existing subscriber update or logout are delayed for the remote device until reconfiguration completes. Also, a reconfiguration request may be performed at any time when the remote device is up. This means that a remote device may be connected to the network and accept new subscriber services provisioning before existing subscribers are provisioned by the reconfiguration request.
The following steps show the RDSM process flow for reconfiguration requests:
RDSM maintains a list of remote devices that are provisioned with the service. If the NETCONF TCP connection to the device is down, deprovisioning is not attempted because it is assumed to have occurred by some other means. For example, the device may have been reconfigured with a default, baseline configuration and subsequent operator action initiated reconfiguration by the BNG for all active subscriber services.
RDSM performs the following as a bulk operation, where the bulk size maybe up to total number of subscriber services to be provisioned:
Validates the service before it responds to the reconfiguration request. For example, validation fails when the dictionary located on the BNG does not include an entry for the requested remote service profile or provisioning action, because there are no RPCs to provide the service variables and add the service.
Resolves any required parameters for each remote device; at a minimum, this includes the subscriber identifier.
Uses the dedicated NETCONF session to the remote device to issue a series of RPC calls as specified in the dictionary for provisioning the service. Provisioning fails for a device when either of the following occurs:
The RDSM receives an explicit error for any RPC call.
The response times out.
In either case, RDSM rolls back all service that were successfully provisioned by the bulk operation, reconfiguration is abandoned and RDSM logs the following ERRMSG event:
remote device device-name ip-address reconfiguration failed
If provisioning completes for all the subscriber services on the remote device, RDSM logs the following ERRMSG event:
remote device device-name ip-address reconfiguration succeeded
External Notification for Service Processing ERRMSG Events
Table 4 lists the ERRMSG events that authd can communicate to external management systems and the information that is included in the notifications. Successful remote service actions are only reported to an external authority and do not generate an ERRMSG log.
ERRMSG Event |
Device Name |
IP Address |
Current State |
Number of Services Pending Reconfiguration |
Service Name |
Subscriber Identifier |
|---|---|---|---|---|---|---|
Remote device status change from up to down or down to up |
✓ |
✓ |
✓ |
– |
– |
– |
Remote device has services pending reconfiguration |
✓ |
✓ |
– |
✓ |
– |
– |
Remote device reconfiguration completion (success or failure) |
✓ |
✓ |
✓ |
– |
– |
– |
Subscriber remote service provisioning failure |
✓ |
✓ |
– |
– |
✓ |
✓ |
Subscriber remote service deprovisioning failure |
✓ |
✓ |
– |
– |
✓ |
✓ |
Benefits of Remote Device Service Management
Enables topologies where subscriber services span both the MX Series BNG and its access nodes to form a single, logical system.
Simplifies BNG and remote device configuration and management in topologies that use external management and provisioning systems. The remote devices typically have private addresses unknown to the external system, so the external system addresses only the MX Series BNG.
Adds a new service profile type for remote services to easily differentiate remote and local services.
