ON THIS PAGE
Understanding How the Router Processes Subscriber-Initiated PPP Fast Keepalive Requests
Preventing the Validation of PPP Magic Numbers During PPP Keepalive Exchanges
How to Configure RADIUS-Sourced Connection Status Updates to CPE Devices
Attaching Dynamic Profiles to Static PPP Subscriber Interfaces
Migrating Static PPP Subscriber Configurations to Dynamic Profiles Overview
Configuring Local Authentication in Dynamic Profiles for Static Terminated IPv4 PPP Subscribers
Configuring Tag2 Attributes in Dynamic Profiles for Static Terminated IPv4 PPP Subscribers
Verifying and Managing PPP Configuration for Subscriber Management
PPP Subscriber Access Networks Overview
Dynamic Profiles for PPP Subscriber Interfaces Overview
Subscriber management PPP support enables you to create and attach dynamic profiles for PPP subscriber interfaces. When the PPP subscriber logs in, the router instantiates the specified dynamic profile and then applies the attributes defined in the profile to the interface.
Dynamic profiles are used for both static and dynamic PPP interfaces. For static PPP interfaces, you use the CLI to attach dynamic profiles, which specify PPP options. For dynamic PPP interfaces, the dynamic profile creates the interface, including the PPP options.
Dynamically created interfaces are supported only on PPPoE interfaces.
Unlike traditional PPP support, subscriber management does not allow bi-directional PPP authentication—authentication is performed only by the router, never by the remote peer. The router’s AAA process manages authentication and address assignment for subscriber management. When you configure PPP options for a dynamic profile, you can configure either Challenge Handshake Authentication Protocol (CHAP) or Password Authentication Protocol (PAP) authentication, and you can control the order in which the router negotiates the CHAP and PAP protocols. In addition, for CHAP authentication, you can modify the default length of the CHAP challenge message. Other PPP options, which are either commonly used or mandatory for a traditional PPP interface configuration, are not supported in subscriber management dynamic profiles.
Understanding How the Router Processes Subscriber-Initiated PPP Fast Keepalive Requests
On MX Series routers with Modular Port Concentrators/Modular Interface Cards (MPCs/MICs), the Packet Forwarding Engine on an MPC/MIC processes and responds to Link Control Protocol (LCP) Echo-Request packets that the PPP subscriber (client) initiates and sends to the router. LCP Echo-Request packets and LCP Echo-Reply packets are part of the PPP keepalive mechanism that helps determine whether a link is functioning properly.
Previously, LCP Echo-Request packets and LCP Echo-Reply packets were handled on an MX Series router by the Routing Engine. The mechanism by which LCP Echo-Request packets are processed by the Packet Forwarding Engine instead of by the Routing Engine is referred to as PPP fast keepalives.
- Benefits of PPP Fast Keepalives
- How PPP Fast Keepalive Processing Works
- Statistics Display for PPP Fast Keepalive
- Effect of Changing the Forwarding Class Configuration
- Ignoring a Magic Number Mismatch
Benefits of PPP Fast Keepalives
PPP fast keepalives reduce the time required for keepalive exchanges by enabling the Packet Forwarding Engine to receive LCP Echo-Request packets from the PPP subscriber and respond with LCP Echo-Reply packets, without having to send the LCP packets to the Routing Engine for processing.
PPP fast keepalives provide increased bandwidth on the router to support a larger number of subscribers with improved performance by relieving the Routing Engine from having to process the LCP Echo-Request and Echo-Reply packets.
PPP fast keepalives use negotiated magic numbers to identify potential traffic loopbacks to the router or network issues. You can also disable validation if needed to prevent undesired PPP session termination, for example when the PPP remote peers use arbitrary numbers rather than the negotiated number.
How PPP Fast Keepalive Processing Works
You do not need any special configuration on an MX Series router with MPCs/MICs to enable processing of PPP fast keepalive requests on the Packet Forwarding Engine. The feature is enabled by default, and cannot be disabled.
The following sequence describes how an MX Series router processes LCP Echo-Request packets and LCP Echo-Reply packets on the Packet Forwarding Engine on the MPC/MIC:
The Routing Engine notifies the Packet Forwarding Engine when transmission of keepalive requests is enabled on a PPP logical interface. The notification includes the magic numbers of both the server and the remote client.
The Packet Forwarding Engine receives the LCP Echo-Request packet initiated by the PPP subscriber (client).
The Packet Forwarding Engine validates the peer magic number in the LCP Echo-Request packet, and transmits the corresponding LCP Echo-Reply packet containing the magic number negotiated by the router.
If the Packet Forwarding Engine detects a loop condition in the link, it sends the LCP Echo-Request packet to the Routing Engine for further processing.
The Routing Engine continues to process LCP Echo-Request packets until the loop condition is cleared.
Transmission of keepalive requests from the Packet Forwarding Engine on the router is not currently enabled.
Statistics Display for PPP Fast Keepalive
When an MX Series router with MPCs/MICs is using PPP fast keepalive
for a PPP link, the Keepalive statistics field in the output
of the show interfaces pp0.logical statistics operational command does not include statistics for the number of
keepalive packets received or sent, or the amount of time since the
router received or sent the last keepalive packet.
Effect of Changing the Forwarding Class Configuration
To change the default queue assignment (forwarding class) for
outbound traffic generated by the Routing Engine, you can include
the forwarding-class class-name statement
at the [edit class-of-service host-outbound-traffic] hierarchy
level.
For PPP fast (inline) keepalive LCP Echo-Request and LCP Echo-Reply packets transmitted between an MX Series router with MPCs/MICs and a PPP client, changing the forwarding class configuration takes effect immediately for both new PPP-over-Ethernet (PPPoE), PPP-over-ATM (PPPoA), and L2TP network server (LNS) subscriber sessions created after the configuration change, and for existing PPPoE, PPPoA, and LNS subscriber sessions established before the configuration change.
Ignoring a Magic Number Mismatch
When the Packet Forwarding Engine validates the peer magic number in the received LCP Echo-Request packet, it checks whether the magic number is unexpected. The received number should match the number for the remote peer that was agreed during LCP negotiation. The remote peer number must be different than the local peer number; when they are the same, the expectation is that a loopback condition (traffic is looping back to the local peer) or some other network issue exists.
When the validation check determines that a mismatch is present, meaning that the received remote peer number is different from the negotiated number, the Packet Forwarding Engine sends the failed Echo-Reply packets to the Routing Engine. If an Echo-Reply with a valid magic number is not received within a certain interval, PPP considers this to be a keepalive failure and tears down the PPP session.
Some customer equipment might not negotiate its local magic
number and instead insert an arbitrary value as the magic number it
sends to the router in the keepalive packets. This number is identified
as a mismatch and the session is eventually dropped. Starting in Junos OS Release 18.1R1, this result
can be avoided by configuring the router to not perform a magic number
validation check. Because the mismatch is
never identified, the router continues to exchange PPP keepalive packets
with the remote peer. To configure this behavior, include the ignore-magic-number-mismatch statement in an L2TP group profile,
in the dynamic profile for dynamic PPP subscriber connections terminated
at the router, or in the dynamic profile for dynamic tunneled PPP
subscribers at the LNS.
See Also
RADIUS-Sourced Connection Status Updates to CPE Devices
Starting in Junos OS Release 20.2R1, you can use RADIUS-sourced messages to convey information that the BNG transparently forwards to a CPE device, such as a home gateway. For example, this information might be upstream bandwidth or some other connection rate parameter that the CPE device needs. This capability is useful when you want to dynamically enforce traffic management as close to subscribers as possible.
Ordinarily, you might use the RADIUS standard attribute Reply-Message (18) to convey this information to the CPE device during PPP authentication. However, if you are already using that attribute for something else, you can also use the Juniper Networks Connection-Status-Message VSA (26-4874–218). This VSA is a logical extension to the Reply-Message attribute (18) and has the same format and semantics.
PPP uses a Juniper Networks vendor-specific extension to LCP to send the contents of the Connection-Status-Message VSA to the peer home gateway. PPP includes this information in the Connection-Status-Message option of an LCP Connection-Update-Request message.
RADIUS can send the Connection-Status-Message VSA to authd in the following ways:
-
In the RADIUS Access-Accept message during negotiation and authorization of a PPP session
-
In a RADIUS CoA request at any time for an active PPP session
You might use both of these methods for any given session for business or residential subscribers. The Access-Accept message provides the initial connection parameters. The CoA capability enables you to update connection rate parameters as needed throughout the life of a session. The information carried in the Connection-Status-Message VSA is typically traffic rates that are applied by local configuration such as a dynamic service profile or the corresponding ANCP Port Up message.
If you do not include the lcp-connection-update PPP option in the dynamic client profile, PPP processes the notification
from authd, but takes no action. If LCP on the router is not in the
Opened state, then PPP takes no action on the VSA.
The following steps describe what happens when RADIUS sends the VSA in an Access-Accept message:
-
The authd process receives the Connection-Status-Message VSA in an Access-Accept message from the RADIUS server.
-
The authd process sends the Connection-Status-Message VSA to PPP (jpppd).
-
PPP NCP negotiation takes place between the remote gateway PPP client and PPP on the router.
-
Successful negotiation results in a family activation request. The PPP session enters the Session Up state when the family is activated.
-
If the dynamic client profile includes the
lcp-connection-updatePPP option and LCP on the router is in the Opened state, PPP sends an LCP Connection-Update-Request message to the gateway. This message includes the VSA information in the Connection-Status-Message option.-
If the gateway supports the LCP Connection-Update-Request, it returns an LCP Connection-Update-Ack message to the router. The home gateway LCP must be in the Opened state when it receives the request, otherwise it discards the request.
-
If the gateway does not support the LCP Connection-Update-Request, it returns an LCP Code-Reject message to the router.
Note:If the gateway does not respond, the router retries the update request. It uses the PPP default values of up to a maximum of 10 retries with an interval of 3 seconds between the attempts.
Note:If you do not include the
lcp-connection-updatePPP option in the dynamic client profile, PPP processes the notification from authd, but takes no action. If the option is present but LCP on the router is not in the Opened state, PPP takes no action regarding the VSA. -
The following steps describe what happens when RADIUS sends the VSA in a CoA request. This assumes that NCP negotiation was already successful and the session is active.
-
The authd process receives the Connection-Status-Message VSA in a CoA request from the RADIUS server.
-
The authd process sends the Connection-Status-Message VSA to PPP (jpppd).
-
If the dynamic client profile includes the
lcp-connection-updatePPP option and LCP on the router is in the Opened state, PPP sends an LCP Connection-Update-Request message to the gateway. This message includes the VSA information in the Connection-Status-Message option.-
If the gateway supports the LCP Connection-Update-Request, it returns an LCP Connection-Update-Ack message to the router. The home gateway LCP must be in the Opened state when it receives the request, otherwise it discards the request.
-
If the gateway does not support the LCP Connection-Update-Request, it returns an LCP Code-Reject message to the router.
Note:If the gateway does not respond, the router retries the update request. It uses the PPP default values of up to a maximum of 10 retries with an interval of 3 seconds between the attempts.
-
If the home gateway fails to receive a Connection-Update-Request message, the router retries sending the message. The router also retries the request when it does not receive either a Connection-Update-Ack or an LCP Code-Reject back from the gateway, or when something is wrong with the Ack message. The default retry interval is 3 seconds. The router will retry the message up to the default 10 times before it quits. If the router exhausts all the retry attempts without receiving an appropriate Connection-Update-Ack message, it logs the message as if it had received a PPP Code-Reject message.
RADIUS can include multiple instances of the Connection-Status-Message VSA in either the Access-Accept message or a CoA request. If this occurs, authd uses only the first instance and ignores any others.
The Access-Accept or CoA requests might contain other attributes besides the Connection-Status-Message VSA, but there is no interdependency between the VSA and any other attributes. This is true even when the message includes the Activate-Service (26–65) or Deactivate-Service (26–66) VSAs. The lack of dependency means that even if authd does not successfully apply the other attributes, it still sends the connection info to PPP, which in turn sends the VSA contents to the home gateway.
Similarly, authd applies any other attributes and returns a CoA response regardless of whether PPP successfully communicates the content of the Connection-Status-Message VSA to the remote gateway. This is true even when the CoA contains only the Connection-Status-Message VSA. This capability is necessary because not all gateways will accept the LCP extension used in this feature.
Message and Option Formats
Figure 1 shows the format for Connection-Update-Request and Connection-Update-Ack messages. The formats are the same, but Table 1shows that some field values are different for the two messages.
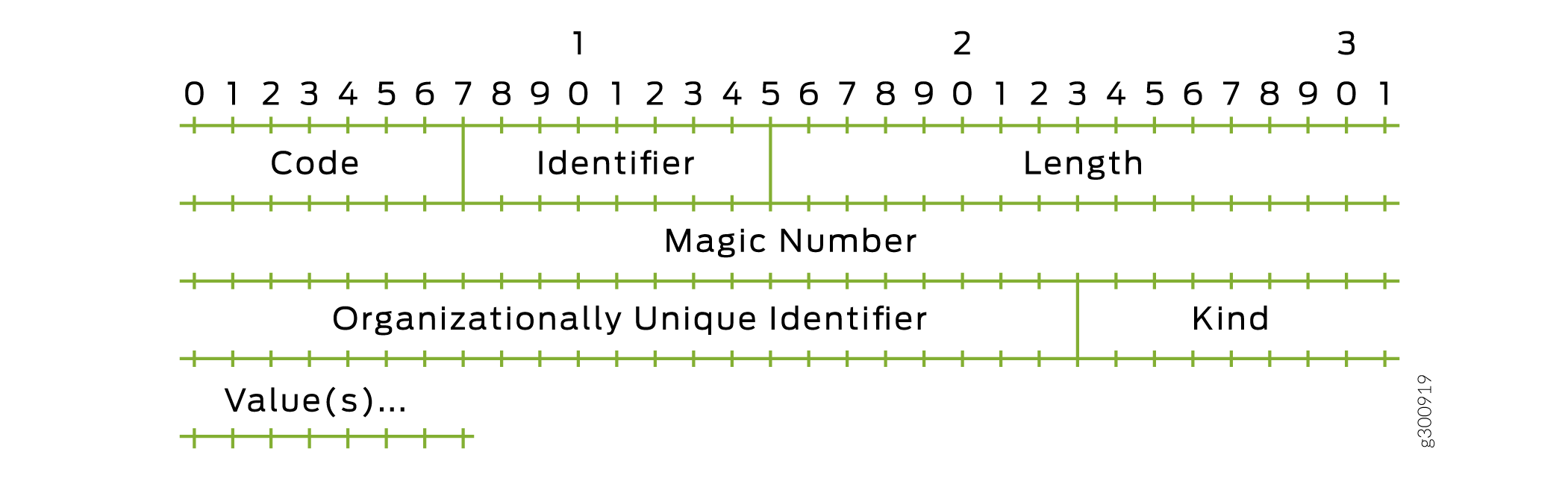
|
Field |
Connection-Update-Request |
Connection-Update-Ack |
|---|---|---|
|
Code |
0 for vendor-specific |
0 for vendor-specific |
|
Identifier |
Identifier for vendor-specific packet |
Same identifier as in the Connection-Update-Request message. If this value does not match, the router logs the error and discards the packet. This enables the request message to be retried, just as if the gateway had not received it. |
|
Length |
Number of bytes in the packet: 12 plus the length of the Connection-Status-Message option |
Number of bytes in the Connection-Update-Ack packet: 12 |
|
Magic Number |
Negotiated value for the local PPP magic number |
Negotiated value for the local PPP magic number |
|
Organizationally Unique Identifier (OUI) |
00-21-59 for Juniper Networks |
00-21-59 for Juniper Networks |
|
Kind |
1 for Session-Update |
2 for Session-Ack. For any other value, the router logs the error and the discards the packet. This enables the request message to be retried, just as if the gateway had not received it. |
|
Values |
Connection-Status-Message option in TLV format |
No values are supported |
You can configure how the PPP magic numbers are used.
-
If you configure
ignore-magic-number-mismatchPPP option, you are preventing the magic numbers from being validated. PPP ignores a mismatch between the magic numbers in the request and Ack messages. If there are no other validation errors, PPP accepts the Connection-Update-Ack message. -
If you do not configure
ignore-magic-number-mismatchPPP option, the magic numbers go through validation. If the magic number in the Ack message does not match the gateway’s magic number established during LCP negotiation, the router logs the error and discards the Connection-Update-Ack message as an invalid response. This enables the request message to be retried, just as if the gateway had not received it.
See Preventing the Validation of PPP Magic Numbers During PPP Keepalive Exchanges for more information about magic numbers.
Figure 2 shows the format for the Connection-Status-Message options. Table 2 lists the field values.
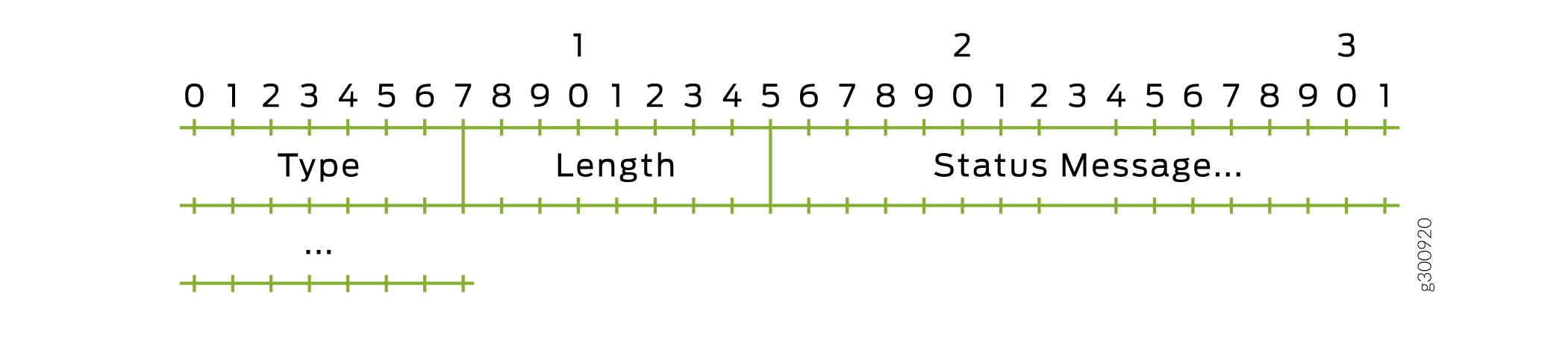
|
Field |
Value |
|---|---|
|
Type |
1 |
|
Length |
Number of bytes in the option; 2 plus the length of the message. The message length can be from 1 through 247 bytes. |
|
Status Message |
Contents of the Connection-Status-Message VSA |
Configure Dynamic Profiles for PPP
A dynamic profile acts as a template that enables you to create, update, or remove a configuration that includes attributes for client access (such as, interface or protocol) or service (such as, IGMP). Using dynamic profiles, you can consolidate all of the common attributes of a client (and eventually a group of clients) and apply the attributes simultaneously.
After dynamic profiles are created, the profiles reside in a profile library on the router. You
can then use the dynamic-profile statement to attach profiles to
interfaces. To assign a dynamic profile to a PPP interface, you can include the
dynamic-profile statement at the [edit interfaces
interface-name unit logical-unit-number
ppp-options] hierarchy level:
[edit interfaces interface-name unit logical-unit-number ppp-options] dynamic-profile profile-name;
To monitor the configuration, issue the show interfaces interface-name command.
For information about dynamic profiles, see Dynamic Profiles Overview in the Junos Subscriber Access Configuration Guide.
For information about creating dynamic profiles, see Configuring a Basic Dynamic Profile in the Junos Subscriber Access Configuration Guide.
For information about assigning a dynamic profile to a PPP interface, see Attaching Dynamic Profiles to Static PPP Subscriber Interfaces in the Junos Subscriber Access Configuration Guide.
For information about using dynamic profiles to authenticate PPP subscribers, see Configuring Dynamic Authentication for PPP Subscribers.
Dynamic profiles for PPP subscribers are supported only on PPPoE interfaces for this release.
Preventing the Validation of PPP Magic Numbers During PPP Keepalive Exchanges
PPP magic numbers are negotiated between peers during LCP negotiation. The peers must have different magic numbers. When the numbers are the same, it indicates that there may be a loopback in traffic sent by the local peer. In this case, the local peer sends a new number to the remote peer. If the magic number returned by the remote peer is different than the latest number sent by the local peer, then the numbers are agreed. Otherwise, the exchange of magic numbers continues until a valid (different) number is received or the process times out, in which case the session is dropped.
After the numbers are agreed upon, the peers include their respective magic numbers when they exchange PPP keepalive (Echo-Request/Echo-Reply) packets. The Packet Forwarding Engine validates the received magic number for each exchange. A mismatch occurs when the PPP magic number received from the remote peer does not match the value agreed upon during LCP negotiation. When the validation check determines that a mismatch is present, the Packet Forwarding Engine sends the failed Echo-Request packet to the Routing Engine. If an Echo-Reply with a valid magic number is not received within a certain interval, PPP considers this to be a keepalive failure and tears down the PPP session.
In some circumstances, this behavior is not desirable. Some customer equipment does not negotiate its local magic number; instead, it inserts an arbitrary value as the magic number it sends to the router in the keepalive packets. By default, this number is identified as a mismatch and the session is eventually dropped. This result can be avoided by preventing the Packet Forwarding Engine from performing the magic number validation check. Because the mismatch is never identified, the router continues to exchange PPP keepalive packets with the remote peer.
Disable the magic number validation check by including the ignore-magic-number-mismatch statement as one of the PPP options
applied in a dynamic PPP profile, L2TP LNS dynamic profile, or L2TP
group profile. Configuring this statement has no effect on LCP magic
number negotiation or on the exchange of keepalives when the remote
peer magic number is the expected negotiated number.
Because magic number validation is not performed, the Packet Forwarding Engine does not detect whether the remote peer sends the local peer’s magic number, which would indicate a loopback or other network issue. This is considered to be an unlikely situation, because LCP negotiation completed successfully, meaning no loopback was present at that time.
To configure dynamic profiles to prevent the Packet Forwarding Engine from detecting mismatches in magic numbers:
Configure the PPP option.
For dynamic PPP subscriber connections terminated at the router:
[edit dynamic-profiles profile-name interfaces pp0 unit “$junos-interface-unit” ppp-options] user@host# set ignore-magic-number-mismatch
For dynamic tunneled PPP subscribers on LNS inline service interfaces:
[edit dynamic-profiles profile-name interfaces "$junos-interface-ifd-name" unit “$junos-interface-unit” ppp-options] user@host# set ignore-magic-number-mismatch
You can use the show ppp interface interface-name extensive command to view
whether the magic numbers are ignored.
How to Configure RADIUS-Sourced Connection Status Updates to CPE Devices
You can use RADIUS-sourced messages to convey information that the BNG transparently forwards to a CPE device, such as a home gateway. For example, this information might be upstream bandwidth or some other connection rate parameter that the CPE device needs.
When you enable this feature, PPP can act on a Connection-Status-Message VSA (26–218) received by authd in either a RADIUS Access-Accept message or a CoA message. PPP then conveys the contents of the VSA in an LCP Connection-Update-Request message to the remote peer. This action requires the following to be true:
At least the first address family has been successfully negotiated and the session is active.
The router LCP is in the Opened state.
Otherwise PPP takes no action on the VSA. If you do not enable
the lcp-connection-update option, PPP processes the notification
from authd, but takes no action.
You configure this capability in the dynamic client profile associated with subscribers using the CPE device. In practice, you are adding this to numerous other features in the client profile. This example shows only the specific configuration for this feature. This feature also requires you to configure VSA 26-218 on your RADIUS server; that is outside the scope of this documentation.
To configure the connection status updates in a dynamic profile for PPP subscriber interfaces:
You can use the show ppp interface extensive command
for the PPP logical interface to determine whether LCP connection
updates are successful. You can monitor the relevant statistics with
the show system subscriber-management statistics ppp command.
Attaching Dynamic Profiles to Static PPP Subscriber Interfaces
You can attach a dynamic profile to a static PPP subscriber interface. When a PPP subscriber logs in, the specified dynamic profile is instantiated and the services defined in the profile are applied to the interface.
To attach a dynamic profile to a static PPP subscriber interface:
Migrating Static PPP Subscriber Configurations to Dynamic Profiles Overview
This topic discusses several considerations for migrating certain static, terminated IPv4 PPP subscriber configurations to dynamic configurations using dynamic profiles. Service providers managing static subscribers on routers with legacy Junos OS releases (earlier than Junos OS Release 15.1R4) have requirements for migrating their static subscribers to being managed with dynamic profiles on routers running enhanced subscriber management (Junos OS Release 15.1R4 and later releases). Starting in Junos OS Release 18.2R1, several enhancements have been added to facilitate the transition of these static service provider configurations to dynamic profiles.
Local Authentication
Some providers with static configurations might use CPE devices that do not support any authentication protocols, not even CHAP or PAP. The providers might use PPPoE service name tables as a rudimentary method to authenticate and authorize the subscribers on static PPPoE logical interfaces. If the subscriber ACI or ARI do not match a table entry, then the PPP PADI and PADR packets are typically dropped. Legacy Junos OS releases do not support subscribers configured with no-authentication for the authentication method.
For subscribers where the CPE does not support authentication protocols such as PAP and CHAP, you can configure usernames and passwords locally. The router uses these values when it contacts the RADIUS server for authentication.
To configure the username for local authentication, include the
username-includestatement in the PPP options for the dynamic logical interface. You can define the name based on one or more of the following attributes: MAC address, Agent Circuit ID, Agent Remote ID, and domain name. By default, a period (.) is the delimiter between elements of the name, but you can define other characters instead.To configure the password for local authentication, include the
passwordstatement in the PPP options for the dynamic logical interface.
You can use the same dynamic profile to support both CPEs that do not support an authentication protocol and CPEs that do.
CPE-Sourced Address Assignment
For some static configurations, the subscriber address is not assigned by using RADIUS or a local address pool on the router. Instead, the CPE has a static address configured for the subscriber; during IPCP negotiation, the CPE requests the router to assign that address to the subscriber.
Starting in Junos OS Release 18.2R1, you can assign a wildcard address of 255.255.255.255 to the Framed-Route-Address attribute [8] in the configuration for your RADIUS server. When RADIUS returns the attribute with that value, jpppd automatically accepts the subscriber IP address assignment provided by the client in an IPCP configure-request message rather than assigning another address.
Tag2 Route Attribute
In some configurations, static PPP subscriber interfaces are configured in different VRFs. Each VRF configuration has static routes that point to static PPP subscriber interfaces as the next-hop address. These routes might have the tag2 attribute configured; it is required by MP-BGP to apply the appropriate local preference and community when it advertises the routes.
Starting in Junos OS Release 18.2R1, you can configure your RADIUS server to include the tag2 attribute in the Framed-Route attribute [22] when it authenticates a subscriber.
You must also configure the dynamic profile to derive the tag2 value from the Framed-Route attribute. To do so, specify the $junos-framed-route-tag2 predefined variable to be used when the access route is dynamically instantiated. Alternatively, you can configure the dynamic profile to provide a specific tag2 value for a specific access route prefix.
See Junos OS Predefined Variables for more information about predefined variables.
Benefits
Local authentication enables authentication with locally stored passwords and usernames for subscribers when the CPE does not support authentication protocols such as PAP and CHAP.
CPE-sourced address assignment enables the router to accept statically configured subscriber IP addresses requested by the CPE rather than assigning the address from a local or externally sourced address pool.
The tag2 attribute enables more detailed specification of routes.
Configuring Local Authentication in Dynamic Profiles for Static Terminated IPv4 PPP Subscribers
Some providers with static configurations might use CPE devices that do not support any authentication protocols, not even CHAP or PAP. The providers might use PPPoE service name tables as a rudimentary method to authenticate and authorize the subscribers on static PPPoE logical interfaces. If the subscriber ACI or ARI does not match a table entry, then the PPP PADI and PADR packets are typically dropped.
Starting in Junos OS Release 18.2R1, you can configure usernames and passwords locally for clients that do not support authentication protocols such as PAP and CHAP. The router uses these values when it contacts the RADIUS server for authentication. This aids in the migration of the static subscribers to using dynamic profiles on a router running enhanced subscriber management.
To configure local authentication:
The username takes the following format when you include all the options and use the default delimiter:
mac-address.circuit-id.remote-id@domain-name
For example, consider the following sample configuration, where the ACI is aci1002, the ARI is ari349, and the MAC address is 00:00:5e:00:53:ff:
[edit dynamic-profiles profile-name interfaces "$junos-interface-ifd-name" unit "$junos-interface-unit" ppp-options local-authentication] user@host# set username-include circuit-id user@host# set username-include remote-id user@host# set username-include mac-address user@host# set username-include domain-name example.com user@host# set username-include delimiter - user@host# set password $ABC123$ABC123
This configuration results in a local password of $ABC123$ABC123 for the following unique local username:
0000.5e00.53ff-aci1002-ari349@example.com
Configuring Tag2 Attributes in Dynamic Profiles for Static Terminated IPv4 PPP Subscribers
In some configurations, PPP subscribers use static routes with a tag2 attribute. For example, MP-BGP uses tag2 to enable it to apply the appropriate local-preference and community when it advertises routes. When you migrate these subscribers to using dynamic profiles on a router running enhanced subscriber management, you can configure the tag2 attribute by configuring a specific value for a route or by deriving the value from a RADIUS server. This support is first available in Junos OS Release 18.2R1.
To configure a specific tag2 value for a route:
Specify the value.
[edit dynamic-profiles profile-name routing-options access route prefix] user@host# set tag2 route-tag2
To derive the tag2 value from a RADIUS server:
Configure your RADIUS server to include the tag2 attribute in the Framed-Route attribute [22] when it authenticates a subscriber. Consult your RADIUS server documentation for configuration information. The configuration might look something like the following example:
user@sub.example.com User-Password := "$ABC123" Service-Type = Framed-User, Framed-Protocol = PPP, Framed-Route += "198.51.100.0/24 203.0.113.27 tag 5 distance 10 tag2 3"
Configure the dynamic profile to use the $junos-framed-route-tag2 predefined variable to dynamically derive the tag2 value from the Framed-Route attribute.
[edit dynamic-profiles profile-name routing-options access route "$junos-framed-route-ip-address-prefix] user@host# set tag2 $junos-framed-route-tag2
The $junos-framed-route-ip-address-prefix predefined variable derives the IPv4 address prefix for the access route from the Framed-Route attribute as well.
Configuring Dynamic Authentication for PPP Subscribers
You can configure a dynamic profile that includes PPP authentication that enables PPP clients to dynamically access the network. You can specify either CHAP or PAP authentication. Optionally, you can also control the order in which the router negotiates the CHAP and PAP protocols.
For
dynamic interfaces, the router supports unidirectional authentication
only—the router always functions as the authenticator. When
you configure PPP authentication in a dynamic profile, CHAP authentication
supports the challenge-length option, which enables you
to configure the minimum length and maximum length of the CHAP challenge
message. Neither CHAP authentication nor PAP authentication supports
any other configuration options, including the passive statement.
Dynamic profiles for PPP subscribers are supported only on PPPoE interfaces.
To configure authentication in a dynamic profile for PPP subscriber interfaces:
Modifying the CHAP Challenge Length
You can modify the default minimum length and maximum length of the Challenge Handshake Authentication Protocol (CHAP) challenge message that the router sends to a PPP client. The CHAP challenge message, which contains information that is unique to a particular PPP subscriber session, is used as part of the authentication mechanism between the router and the client to verify the identity of the client for access to the router.
By default, the minimum length of the CHAP challenge is 16 bytes, and the maximum length is 32 bytes. You can override this default to configure the CHAP challenge minimum length and maximum length in the range 8 bytes through 63 bytes.
We recommend that you configure both the minimum length and the maximum length of the CHAP challenge to at least 16 bytes.
Before you begin:
Configure the CHAP protocol on the interface.
For dynamic PPP subscriber interfaces, see Configuring Dynamic Authentication for PPP Subscribers.
For static interfaces with PPP encapsulation, see Configuring the PPP Challenge Handshake Authentication Protocol.
To configure the minimum and maximum length of the CHAP challenge message:
Example: Minimum PPPoE Dynamic Profile
This example shows the minimum configuration for a dynamic profile
that is used for static PPPoE interfaces. The configuration must include
the interfaces pp0 stanza.
dynamic-profiles {
ppp-profile-1 {
interfaces {
pp0 {
unit "$junos-interface-unit";
}
}
}
}
Verifying and Managing PPP Configuration for Subscriber Management
Purpose
View or clear information about PPP configuration for subscriber management.
Action
To display information about PPP interfaces:
user@host> show ppp interface
To display PPP statistics information:
user@host> show ppp statistics
To display PPP session summary information:
user@host> show ppp summary
To display PPP address-pool information:
user@host>show ppp address-pool
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
