Overview of IPsec
IPsec is a group of protocols you can use to secure transmissions between devices.
Use Feature Explorer to confirm platform and release support for IPsec.
Security Associations Overview
To use IPsec security services, you create SAs between hosts. An SA is a simplex connection that allows two hosts to communicate with each other securely by means of IPsec. There are two types of SAs: manual and dynamic.
Manual SAs require no negotiation; all values, including the keys, are static and specified in the configuration. Manual SAs statically define the Security Parameter Index (SPI) values, algorithms, and keys to be used, and require matching configurations on both ends of the tunnel. Each peer must have the same configured options for communication to take place.
Dynamic SAs require additional configuration. With dynamic SAs, you configure IKE first and then the SA. IKE creates dynamic security associations; it negotiates SAs for IPsec. The IKE configuration defines the algorithms and keys used to establish the secure IKE connection with the peer security gateway. This connection is then used to dynamically agree upon keys and other data used by the dynamic IPsec SA. The IKE SA is negotiated first and then used to protect the negotiations that determine the dynamic IPsec SAs.
Set up user-level tunnels or SAs, including tunnel attribute negotiations and key management. These tunnels can also be refreshed and terminated on top of the same secure channel.
The Junos OS implementation of IPsec supports two modes of security (transport mode and tunnel mode).
See Also
IKE Key Management Protocol Overview
IKE is a key management protocol that creates dynamic SAs; it negotiates SAs for IPsec. An IKE configuration defines the algorithms and keys used to establish a secure connection with a peer security gateway.
IKE does the following:
Negotiates and manages IKE and IPsec parameters
Authenticates secure key exchange
Provides mutual peer authentication by means of shared secrets (not passwords) and public keys
Provides identity protection (in main mode)
IKE occurs over two phases. In the first phase, it negotiates security attributes and establishes shared secrets to form the bidirectional IKE SA. In the second phase, inbound and outbound IPsec SAs are established. The IKE SA secures the exchanges in the second phase. IKE also generates keying material, provides Perfect Forward Secrecy, and exchanges identities.
Starting in Junos OS Release 14.2, when you perform an SNMP walk of the jnxIkeTunnelEntry
object in the jnxIkeTunnelTable table, the Request failed: OID not increasing error message might be generated. This problem occurs only when
simultaneous Internet Key Exchange security associations (IKE SAs) are created, which occurs
when both ends of the SA initiate IKE SA negotiations at the same time. When an SNMP MIB
walk is performed to display IKE SAs, the snmpwalk tool expects the object identifiers (OIDs)
to be in increasing order. However, in the case of simultaneous IKE SAs, the OIDs in the
SNMP table might not be in increasing order. This behavior occurs because the tunnel IDs,
which are part of the OIDs, are allocated based on the initiator of the IKE SA, which can
be on either side of the IKE tunnel.
The following is an example of an SNMP MIB walk that is performed on IKE simultaneous SAs:
jnxIkeTunLocalRole."ipsec_ss_cust554".ipv4."192.0.2.41".47885 = INTEGER: responder(2) >>> This is Initiator SA jnxIkeTunLocalRole."ipsec_ss_cust554".ipv4."192.0.2.41".47392 = INTEGER: initiator(1) >>> This is Responder's SA
The OID comparison fails when the SNMP walk is tunnel ID (47885 and 47392). It cannot be ensured when an SNMP walk is performed that the tunnel IDs are in increasing order because tunnels might be initiated from either side.
To work around this problem, the SNMP MIB walk contains an option, -Cc, to disable check for increasing OIDs. The following is an example of the MIB walk performed on the jnxIkeTunnelEntry table with the -Cc option:
snmpwalk -Os -Cc -c public -v 1 vira jnxIkeTunnelEntry
See Also
IPsec Requirements for Junos-FIPS
In a Junos-FIPS environment, hardware configurations with two Routing Engines must be configured to use IPsec and a private routing instance for all communications between the Routing Engines. IPsec communication between the Routing Engines and AS II FIPS PICs is also required.
See Also
Overview of IPsec
IP Security (IPsec) is a standards based framework for ensuring secure private communication over IP networks. IPsec provides a secure way to authenticate senders and encrypt IP version 4 (IPv4) and version 6 (IPv6) traffic between network devices, such as routers and hosts. IPsec includes data integrity, sender authentication, source data confidentiality, and protection against data replay.
The main concepts you need to understand are as follows:
IPsec-Enabled Line Cards
The first choice you need to make when implementing IPsec on a Junos OS-based router is the type of line card you wish to use. The term line card includes Physical Interface Cards (PICs), Modular Interface Cards (MICs), Dense Port Concentrators (DPCs), and Modular Port Concentrators (MPCs). The following line cards support IPsec implementation.
See the specific hardware documentation for your router to determine if the line cards on that router support IPsec.
The following line cards support IPsec:
The Encryption Services (ES) PIC provides encryption services and software support for IPsec.
The Adaptive Services (AS) PIC and the Adaptive Services (AS) II PIC provide IPsec services and other services, such as Network Address Translation (NAT) and stateful firewall.
The AS II Federal Information Processing Standards (FIPS) PIC is a special version of the AS PIC that communicates securely with the Routing Engine by using internal IPsec. You must configure IPsec on the AS II FIPS PIC when you enable FIPS mode on the router. For more information about implementing IPsec on an AS II FIPS PIC installed in a router configured in FIPS mode, see the Secure Configuration Guide for Common Criteria and Junos-FIPS.
The Multiservices PICs supply hardware acceleration for an array of packet processing-intensive services. These services include IPsec services and other services, such as stateful firewall, NAT, IPsec, anomaly detection, and tunnel services.
The Multiservices Dense Port Concentrators (DPCs) provide IPsec services.
The Multiservices Modular Port Concentrators (MS-MPCs) support IPsec services.
The Multiservices Modular Interface Cards (MS-MICs) support IPsec services.
Junos OS extension-provider packages, including the IPsec service package, come preinstalled and preconfigured on MS-MPCs and MS-MICs.
See Also
Authentication Algorithms
Authentication is the process of verifying the identity of the sender. Authentication algorithms use a shared key to verify the authenticity of the IPsec devices. The Junos OS uses the following authentication algorithms:
Message Digest 5 (MD5) uses a one-way hash function to convert a message of arbitrary length to a fixed-length message digest of 128 bits. Because of the conversion process, it is mathematically infeasible to calculate the original message by computing it backwards from the resulting message digest. Likewise, a change to a single character in the message will cause it to generate a very different message digest number.
To verify that the message has not been tampered with, the Junos OS compares the calculated message digest against a message digest that is decrypted with a shared key. The Junos OS uses the MD5 hashed message authentication code (HMAC) variant that provides an additional level of hashing. MD5 can be used with authentication header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Secure Hash Algorithm 1 (SHA-1) uses a stronger algorithm than MD5. SHA-1 takes a message of less than 264 bits in length and produces a 160-bit message digest. The large message digest ensures that the data has not been changed and that it originates from the correct source. The Junos OS uses the SHA-1 HMAC variant that provides an additional level of hashing. SHA-1 can be used with AH, ESP, and IKE.
SHA-256, SHA-384, and SHA-512 (sometimes grouped under the name SHA-2) are variants of SHA-1 and use longer message digests. The Junos OS supports the SHA-256 version of SHA-2, which can process all versions of Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES) encryption.
Encryption Algorithms
Encryption encodes data into a secure format so that it cannot be deciphered by unauthorized users. Like authentication algorithms, a shared key is used with encryption algorithms to verify the authenticity of the IPsec devices. The Junos OS uses the following encryption algorithms:
Data Encryption Standard cipher-block chaining (DES-CBC) is a symmetric secret-key block algorithm. DES uses a key size of 64 bits, where 8 bits are used for error detection and the remaining 56 bits provide encryption. DES performs a series of simple logical operations on the shared key, including permutations and substitutions. CBC takes the first block of 64 bits of output from DES, combines this block with the second block, feeds this back into the DES algorithm, and repeats this process for all subsequent blocks.
Triple DES-CBC (3DES-CBC) is an encryption algorithm that is similar to DES-CBC, but provides a much stronger encryption result because it uses three keys for 168-bit (3 x 56-bit) encryption. 3DES works by using the first key to encrypt the blocks, the second key to decrypt the blocks, and the third key to re-encrypt the blocks.
Advanced Encryption Standard (AES) is a next-generation encryption method based on the Rijndael algorithm developed by Belgian cryptographers Dr. Joan Daemen and Dr. Vincent Rijmen. It uses a 128-bit block and three different key sizes (128, 192, and 256 bits). Depending on the key size, the algorithm performs a series of computations (10, 12, or 14 rounds) that include byte substitution, column mixing, row shifting, and key addition. The use of AES in conjunction with IPsec is defined in RFC 3602, The AES-CBC Cipher Algorithm and Its Use with IPsec.
Starting In Junos OS Release 17.3R1, Advanced Encryption Standard in Galois/Counter Mode (AES-GCM) is supported for MS-MPCs and MS-MICs. However, in Junos FIPS mode, AES-GCM is not supported in Junos OS Release 17.3R1. Starting in Junos OS Release 17.4R1, AES-GCM is supported in Junos FIPS mode. AES-GCM is an authenticated encryption algorithm designed to provide both authentication and privacy. AES-GCM uses universal hashing over a binary Galois field to provide authenticated encryption and allows authenticated encryption at data rates of tens of Gbps.
See Also
IPsec Protocols
IPsec protocols determine the type of authentication and encryption applied to packets that are secured by the router. The Junos OS supports the following IPsec protocols:
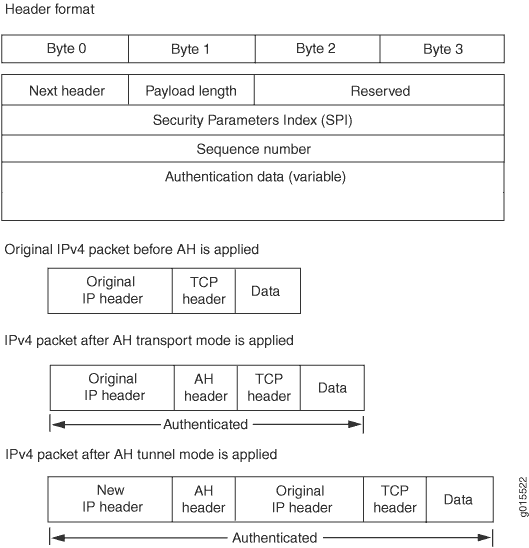
AH—Defined in RFC 2402, AH provides connectionless integrity and data origin authentication for IPv4 and IPv6 packets. It also provides protection against replays. AH authenticates as much of the IP header as possible, as well as the upper-level protocol data. However, some IP header fields might change in transit. Because the value of these fields might not be predictable by the sender, they cannot be protected by AH. In an IP header, AH can be identified with a value of
51in theProtocolfield of an IPv4 packet and theNext Headerfield of an IPv6 packet. An example of the IPsec protection offered by AH is shown in Figure 1.Note:AH is not supported on the T Series, M120, and M320 routers.
ESP—Defined in RFC 2406, ESP can provide encryption and limited traffic flow confidentiality, or connectionless integrity, data origin authentication, and an anti-replay service. In an IP header, ESP can be identified a value of
50in theProtocolfield of an IPv4 packet and theNext Headerfield of an IPv6 packet. An example of the IPsec protection offered by ESP is shown in Figure 2.
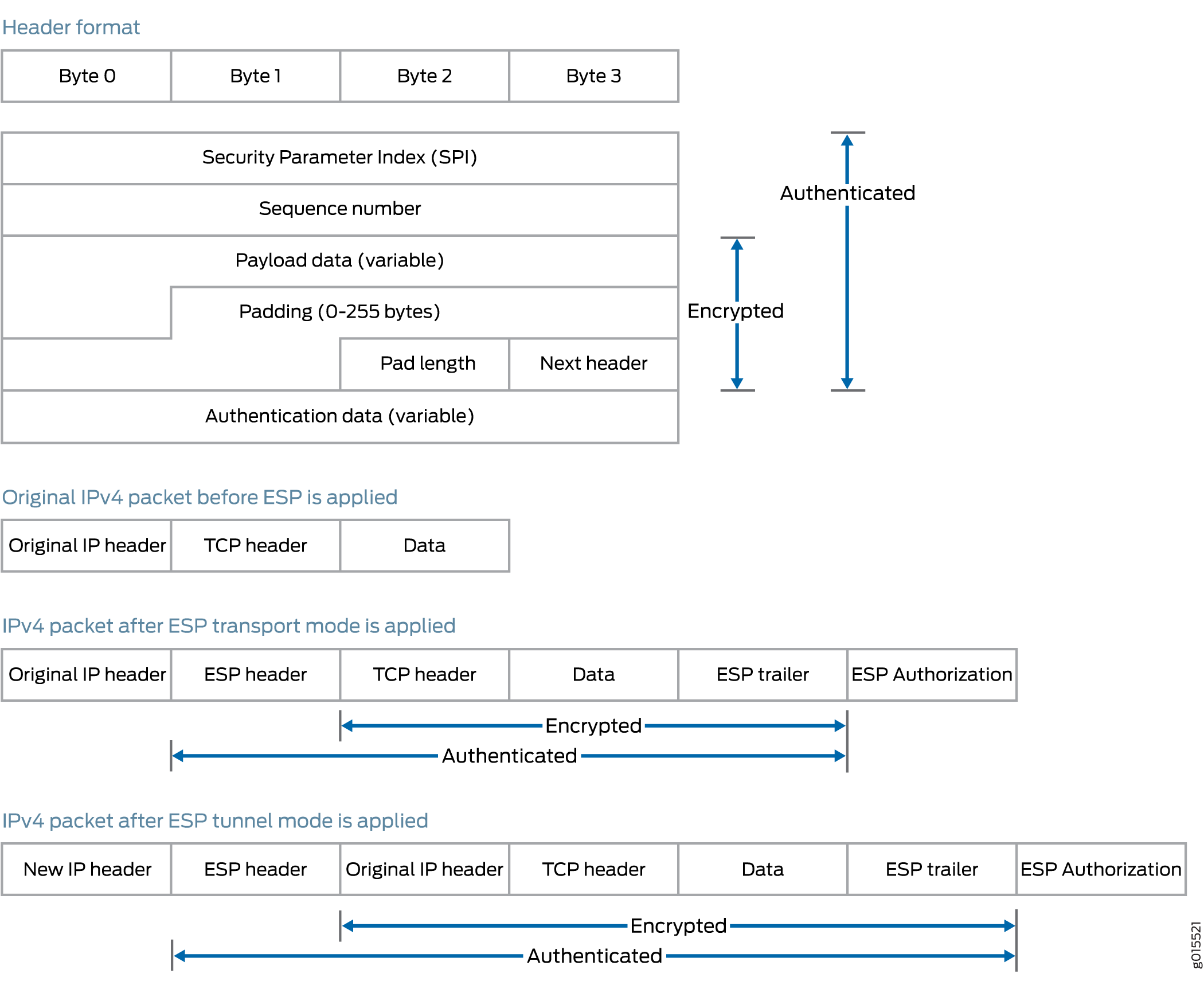
Bundle—When you compare AH with ESP, there are some benefits and shortcomings in both protocols. ESP provides a decent level of authentication and encryption, but does so only for part of the IP packet. Conversely, although AH does not provide encryption, it does provide authentication for the entire IP packet. Because of this, the Junos OS offers a third form of IPsec protocol called a protocol bundle. The bundle option offers a hybrid combination of AH authentication with ESP encryption.
See Also
Supported IKE and IPsec Ciphers for SRX Series Devices
Use the following tables to review the ciphers supported on your SRX Series platform.
|
Ciphers (IKE) |
SRX1500 |
SRX1600 |
SRX2300, SRX4120 |
SRX4100, SRX4200 and SRX4300 |
SRX4600, and SRX4700 |
SRX5400, SRX5600, and SRX5800 |
|---|---|---|---|---|---|---|
|
AES-128-GCM |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
AES-192-GCM |
No |
No |
No |
No |
No |
No |
|
AES-256-GCM |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
Ciphers (IPSec) |
SRX1500 |
SRX1600 |
SRX2300, SRX4120 |
SRX4100, SRX4200 and SRX4300 |
SRX4600, and SRX4700 |
SRX5400, SRX5600, and SRX5800 |
|---|---|---|---|---|---|---|
|
AES-128-GCM |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
AES-192-GCM |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
|
AES-256-GCM |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
Request failed: OID not increasing error message might be generated.