ON THIS PAGE
Explicit Web Proxy
Explicit Web Proxy
Explicit Proxy provides a method for steering traffic from any client device to the SRX Series Firewall. The SRX Series Firewall accepts connections from clients, resolves DNS, forwards connections to the specified destination servers, and then gets the response from the server on behalf of the client. In such configuration, the firewall acts an intermediary between clients and servers. Here, all communication between client and server goes through the firewall that is configured as proxy server.
You can configure your SRX Series Firewall interface as explicit web proxy for applying proxy for IPv4 HTTP and HTTPS traffic. Explicit web proxy support is not available for IPv6 traffic.
To deploy explicit proxy, manually configure the browser’s settings on client device to send requests to SRX SeriesFirewall. In most standard browsers, you can specify the proxy address and port.
SRX Series Firewalls support explicit proxy configuration to obtain the user or device identity information from active directory, identity-management server, LDAP server, and physical SRX Series Firewalls.
How Explicit Proxy Works?
In this example, a client initiates HTTP connection to reach www.example.com. Client device first connects with SRX Series Firewall acting as explicit proxy on (172.16.10.254 and port 31280).
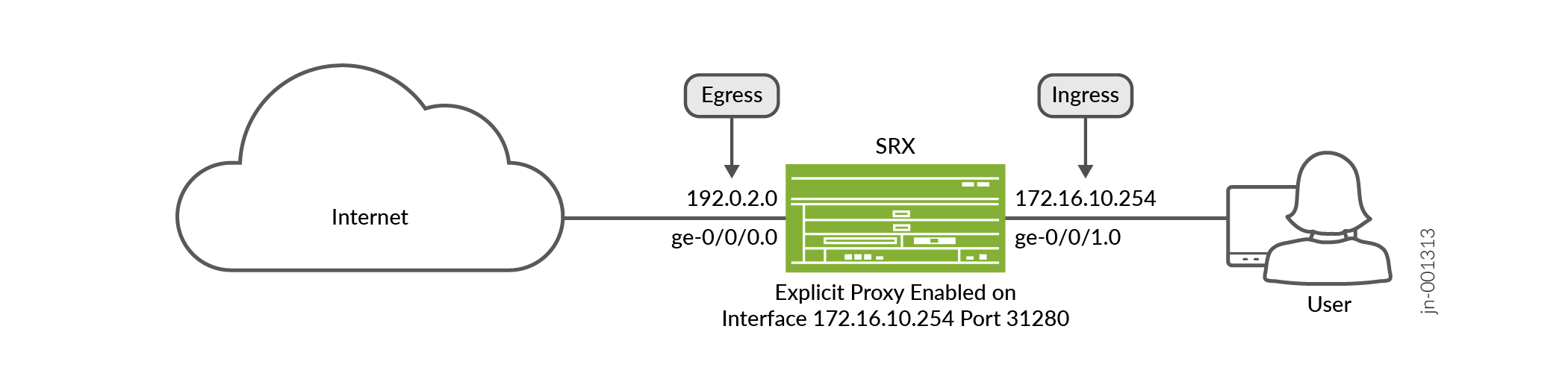
The client network connects to the SRX Series Firewall on ge-0/0/1 interface with IP address 172.16.10.254. SRX Series Firewall connects to Internet using the interface ge-0/0/0 with IP address 192.0.2.0.
Prerequisite-
Ensure that the client configure proxy settings on the client browser.
For each session initiated by the client browser, the SRX Series Firewall creates two sessions:
S1: Session originating from client browser to explicit web proxy
S2: Session originating from explicit web proxy to actual destination server.
Table 1 provides details on the explicit web proxy sessions.
| Session Type | Source IP/Port | Destination IP/Port | Policy | Comments |
|---|---|---|---|---|
| Client to SRX Series Firewall (S1) | Client IP / dynamic port range | SRX Series Firewall interface IP (172.16.10.254) / fixed port (31280) | Security policy/unified policy (explicitly configured on SRX Series Firewall) | Client traffic directly comes to the SRX Series Firewall interface where explicit proxy profile is configured. |
| SRX Series Firewall to actual destination server (S2) | SRX Series Firewallegress interface IP (192.0.2.0)/ dynamic port range | End server as resolved by DNS or in explicit proxy request | Implicitly inherited from S1 | SRX Series Firewall establishes the connection with actual server. |
Benefits
- Explicit web proxy secures network by controlling and filtering the inbound and outbound traffic.
- Explicit web proxy performs DNS resolution on client's behalf.
Steps to Configure Explicit Proxy on SRX Series Firewall
To manage explicit proxy for connections to your network, you must:
- Configure the explicit proxy profile.
- Configure explicit proxy on an interface. This interface must be connected to client network. The client browsers use this IP address to forward requests to the SRX Series device. You can configure and attach multiple explicit proxy profiles to a particular IP address in the interface. However, you must ensure that there must not be overlapping ports between the explicit proxy profiles.
- Use security policies to control the explicit web proxy traffic.
- Configure default-policy for the explicit proxy.
Configure Explicit Proxy
-
Configure explicit web proxy profile
exp-proxy-profileto reach the interfacege-0/0/0.user@host# set services web-proxy explicit-proxy profile exp-proxy-profile listening-port 31280 user@host# set services web-proxy explicit-proxy profile exp-proxy-profile preferred-egress-source-ip default-egress-ipThe
default-egress-ipis the egress source IP address associated with outgoing interface. -
Configure interface that is used to enable explicit web proxy.
user@host# set interfaces ge-0/0/1 unit 0 explicit-proxy profile exp-proxy-profile
Configure Security Policy
You must configure and enforce security policies to manage the traffic for the explicit proxy. Explicit proxy profile needs a set of unique security policies or unified policies. The firewall determines which profile to leverage for a policy lookup based on the ingress interface and port combination. Once the firewall identifies the explicit proxy profile for a flow, it performs a policy lookup.
SRX Series Firewall uses the following sequence for the policy lookup:
- Source IP address, source-port, protocol, and source identity
- DNS-based destination IP resolution
- URL category detection
- Dynamic Layer 7 application match
- DNS-based destination resolved IP reputation
- Hardcoded destination IP address or reputation of hardcoded destination IP address
You can configure the explicit proxy profile rule-base using the following statement:
You can notice that this policy, similar to the global policies, does not need security zones.
To attach a security policy with explicit proxy profile, the profile name
mentioned in policy configuration must match with the name of the explicit proxy
profile configured under web-proxy services (set services web-proxy
explicit-proxy profile <profile-name>).
-
Define a security policy to control the explicit web proxy traffic.
set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match source-address any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match destination-address any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match application any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match dynamic-application any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy then log session-close commit
Default Policy for Explicit Proxy
In case the traffic matches to any of the explicit proxy profiles but does not match any of the policies under the explicit proxy profile, the firewall applies the default policy action. You can configure the default policy in the explicit proxy profile.
In case no matching explicit proxy profile found for a given traffic, the firewall performs the policy lookup based on configured zone and global policies.
You can configure only one default policy per explicit proxy profile.
Limitations
For explicit proxy profile policies, the match condition does not support:
- Source or destination zone
- Source and destination Layer 3 VPN VRF group
Post-match application services do not support:
- Secure web proxy
- GPRS Tunneling protocol
- GPRS stream control transport protocol (SCTP)
- Unified Access control enforcement of policy (UAC)
- WAN acceleration (Legacy WX)
- Legacy Intrusion detection and prevention.
- APBR
See Also
Use Case Scenarios
Configure SSL Proxy
Secure Sockets Layer (SSL) Proxy provides deep packet inspection and decryption of outbound SSL or Transport Layer Security (TLS) traffic for security inspection and policy enforcement on Web traffic received.
Ensure to enable SSL proxy to decrypt sessions so that the advanced security services are applied for inspection, detection, and mitigation. For details, see SSL Proxy Configuration Overview.
-
Apply the SSL proxy profile,
SSL_FPto the explicit web proxy profile,exp-proxy-profileto permit the traffic.set services web-proxy explicit-proxy profile exp-proxy-profile ssl-proxy profile-name SSL_FP Commit
Configure Content Security Filtering
Content Security provides comprehensive security solution that integrates multiple features like antivirus, anti-spam, content filtering, and web filtering on the received web traffic.
You can apply advanced security service profiles for the features IDP, ATP, AppQos, and so on to the proxy traffic. For details, see Content Security.
-
Specify the Content Security policy to be applied on the traffic that matches the conditions specified in the security policy.
set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match source-address any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match destination-address any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match application any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match dynamic-application any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy then permit application-services utm-policy CON-SEC-POL set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy then log session-close commit
Configure Identity Aware Firewall
Identity Aware Firewall enforces network access policies based on individual user identities, allow or block traffic according to predefined rules associated with each user on the received web traffic.
You can use identity sources such as Active Directory, JIMS, UAC, Aruba Clearpass and so on to authenticate users. For more information on identity source, see Identity-Sources.
-
Configure a security policy to use identify parameters that match with the
source-identityspecification.set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match source-address any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match destination-address any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match application any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match source-identity any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy match dynamix-application any set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy then permit application-services utm-policy ORG_EWF_POL set security policies explicit-proxy profile exp-proxy-profile policy exp-proxy-policy then log session-close commit
All the use case features are enabled independently with multiple policies or can be combined on the same policy to expand the threat inspection capabilities.
