Configuring Encryption Interfaces
Configuring Encryption Interfaces
When you configure the encryption interface, you associate the
configured SA with a logical interface. This configuration defines
the tunnel, including the logical unit, tunnel addresses, maximum
transmission unit (MTU), optional interface addresses, and the name
of the IPsec SA to apply to traffic. To configure an encryption
interface, include the following statements at the [edit interfaces
es-fpc/pic/port unit logical-unit-number] hierarchy level:
family inet { ipsec-sa ipsec-sa; # name of security association to apply to packet address address; # local interface address inside local VPN destination address; # destination address inside remote VPN } tunnel { source source-address; destination destination-address; }
The addresses configured as the tunnel source and destination are the addresses in the outer IP header of the tunnel.
You must configure the tunnel source address locally on the router, and the tunnel destination address must be a valid address for the security gateway terminating the tunnel.
The ES Physical Interface Card (PIC) is supported on M Series and T Series routers.
The SA must be a valid tunnel-mode SA. The interface address and destination address listed are optional. The destination address allows the user to configure a static route to encrypt traffic. If a static route uses that destination address as the next hop, traffic is forwarded through the portion of the tunnel in which encryption occurs.
- Specifying the Security Association Name for Encryption Interfaces
- Configuring the MTU for Encryption Interfaces
- Example: Configuring an Encryption Interface
Specifying the Security Association Name for Encryption Interfaces
The security association is the set of properties that defines
the protocols for encrypting Internet traffic. To configure encryption
interfaces, you specify the SA name associated with the interface
by including the ipsec-sa statement at the [edit interfaces
es-fpc/pic/port unit logical-unit-number family inet] hierarchy level:
ipsec-sa sa-name;
For information about configuring the security association, see Configuring Filters for Traffic Transiting the ES PIC.
Configuring the MTU for Encryption Interfaces
The protocol MTU value for encryption interfaces must always
be less than the default interface MTU value of 3900 bytes; the
configuration fails to commit if you select a greater value. To set
the MTU value, include the mtu statement at the [edit
interfaces interface-name unit logical-unit-number family inet] hierarchy level:
mtu bytes;
For more information, see the Junos OS Network Interfaces Library for Routing Devices.
Example: Configuring an Encryption Interface
Configure an IPsec tunnel as a logical interface on the ES PIC.
The logical interface specifies the tunnel through which the encrypted
traffic travels. The ipsec-sa statement associates the
security profile with the interface.
[edit interfaces]
es-0/0/0 {
unit 0 {
tunnel {
source 10.5.5.5; # tunnel source address
destination 10.6.6.6; # tunnel destination address
}
family inet {
ipsec-sa manual-sa1; # name of security association to apply to packet
mtu 3800;
address 10.1.1.8/32 { # local interface address inside local VPN
destination 10.2.2.254; # destination address inside remote VPN
}
}
}
Configuring Filters for Traffic Transiting the ES PIC
This section contains the following topics:
- Traffic Overview
- Configuring the Security Association
- Configuring an Outbound Traffic Filter
- Applying the Outbound Traffic Filter
- Configuring an Inbound Traffic Filter
- Applying the Inbound Traffic Filter to the Encryption Interface
Traffic Overview
Traffic configuration defines the traffic that must flow through the tunnel. You configure outbound and inbound firewall filters, which identify and direct traffic to be encrypted and confirm that decrypted traffic parameters match those defined for the given tunnel. The outbound filter is applied to the LAN or WAN interface for the incoming traffic you want to encrypt. The inbound filter is applied to the ES PIC to check the policy for traffic coming in from the remote host. Because of the complexity of configuring a router to forward packets, no automatic checking is done to ensure that the configuration is correct.
The valid firewall filters statements for IPsec are destination-port, source-port, protocol, destination-address, and source-address.
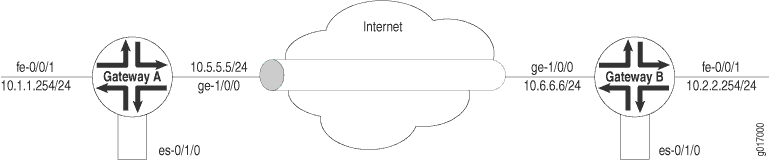
In Figure 1, Gateway A protects the
network 10.1.1.0/24, and Gateway B protects the network 10.2.2.0/24. The gateways are connected by an IPsec tunnel.
For more information about firewalls, see the Routing Policies, Firewall Filters, and Traffic Policers User Guide.
The SA and ES interface for security Gateway A are configured as follows:
[edit security ipsec]
security-association manual-sa1 {
manual {
direction bidirectional {
protocol esp;
spi 2312;
authentication {
algorithm hmac-md5-96;
key ascii-text 1234123412341234;
}
encryption {
algorithm 3des-cbc;
key ascii-text 123456789009876543211234;
}
}
}
}
[edit interfaces es-0/1/0]
unit 0 {
tunnel {
source 10.5.5.5;
destination 10.6.6.6;
}
family inet {
ipsec-sa manual-sa1;
address 10.1.1.8/32 {
destination 10.2.2.254;
}
}
}
Configuring the Security Association
To configure the SA, include the security-association statement at the [edit security] hierarchy level:
security-association name {
mode (tunnel | transport);
manual {
direction (inbound | outbound | bi-directional) {
auxiliary-spi auxiliary-spi-value;
spi spi-value;
protocol (ah | esp | bundle);
authentication {
algorithm (hmac-md5-96 | hmac-sha1-96);
key (ascii-text key | hexadecimal key);
}
encryption {
algorithm (des-cbc | 3des-cbc);
key (ascii-text key | hexadecimal key);
}
}
dynamic {
replay-window-size (32 | 64);
ipsec-policy policy-name;
}
}
}
For more information about configuring an SA, see the Junos OS Administration Library for Routing Devices. For information about applying the SA to an interface, see 147531Specifying the Security Association Name for Encryption Interfaces.
Configuring an Outbound Traffic Filter
To configure the outbound traffic filter, include the filter statement at the [edit firewall] hierarchy level:
filter filter-name {
term term-name {
from {
match-conditions;
}
then {
action;
action-modifiers;
}
}
}
For more information, see the Routing Policies, Firewall Filters, and Traffic Policers User Guide.
Example: Configuring an Outbound Traffic Filter
Firewall filters for outbound traffic direct the traffic through the desired IPsec tunnel and ensure that the tunneled traffic goes out the appropriate interface (see Figure 1). Here, an outbound firewall filter is created on security Gateway A; it identifies the traffic to be encrypted and adds it to the input side of the interface that carries the internal virtual private network (VPN) traffic:
[edit firewall]
filter ipsec-encrypt-policy-filter {
term term1 {
from {
source-address { # local network
10.1.1.0/24;
}
destination-address { # remote network
10.2.2.0/24;
}
}
then ipsec-sa manual-sa1; # apply SA name to packet
term default {
then accept;
}
The source address, port, and protocol on the outbound traffic filter must match the destination address, port, and protocol on the inbound traffic filter. The destination address, port, and protocol on the outbound traffic filter must match the source address, port, and protocol on the inbound traffic filter.
Applying the Outbound Traffic Filter
After you have configured the outbound firewall filter, you
apply it by including the filter statement at the [edit interfaces interface-name unit logical-unit-number family inet] hierarchy level:
filter { input filter-name; }
Example: Applying the Outbound Traffic Filter
Apply the outbound traffic filter. The outbound filter is applied
on the Fast Ethernet interface at the [edit interfaces fe-0/0/1
unit 0 family inet] hierarchy level. Any packet matching the
IPsec action term (term 1) on the input filter (ipsec-encrypt-policy-filter), configured on the Fast Ethernet interface, is directed to the
ES PIC interface at the [edit interfaces es-0/1/0 unit 0 family
inet] hierarchy level. So, if a packet arrives from the source
address 10.1.1.0/24 and goes to the destination address 10.2.2.0/24, the Packet Forwarding Engine directs the packet
to the ES PIC interface, which is configured with the manual-sa1 SA. The ES PIC receives the packet, applies the manual-sa1 SA, and sends the packet through the tunnel.
The router must have a route to the tunnel end point; add a static route if necessary.
[edit interfaces]
fe-0/0/1 {
unit 0 {
family inet {
filter {
input ipsec-encrypt-policy-filter;
}
address 10.1.1.254/24;
}
}
}
Configuring an Inbound Traffic Filter
To configure an inbound traffic filter, include the filter statement at the [edit firewall] hierarchy level:
filter filter-name {
term term-name {
from {
match-conditions;
}
then {
action;
action-modifiers;
}
}
}
For more information, see the Routing Policies, Firewall Filters, and Traffic Policers User Guide.
Example: Configuring an Inbound Traffic Filter
Configure an inbound firewall filter. This filter performs the final IPsec policy check and is created on security gateway A. The policy check ensures that only packets that match the traffic configured for this tunnel are accepted.
[edit firewall]
filter ipsec-decrypt-policy-filter {
term term1 { # perform policy check
from {
source-address { # remote network
10.2.2.0/24;
}
destination-address { # local network
10.1.1.0/24;
}
then accept;
Applying the Inbound Traffic Filter to the Encryption Interface
After you create the inbound firewall filter, you can apply
it to the ES PIC. To apply the filter to the ES PIC, include the filter statement at the [edit interfaces es-fpc/pic/port unit logical-unit-number family inet filter] hierarchy level:
filter {
input filter;
}
The input filter is the name of the filter applied to received traffic. For a configuration example, see Example: Configuring an Inbound Traffic Filter. For more information about firewall filters, see the Routing Policies, Firewall Filters, and Traffic Policers User Guide.
Example: Applying the Inbound Traffic Filter to the Encryption Interface
Apply the inbound firewall filter (ipsec-decrypt-policy-filter) to the decrypted packet to perform the final policy check. The
IPsec manual-sa1 SA is referenced at the [edit interfaces
es-1/2/0 unit 0 family inet] hierarchy level and decrypts the
incoming packet.
The Packet Forwarding Engine directs IPsec packets to the ES
PIC. It uses the packet’s security parameter index (SPI), protocol,
and destination address to look up the SA configured on one of the
ES interfaces. The IPsec manual-sa1 SA is referenced at
the [edit interfaces es-1/2/0 unit 0 family inet] hierarchy
level and is used to decrypt the incoming packet. When the packets
are processed (decrypted, authenticated, or both), the input firewall
filter (ipsec-decrypt-policy-filter) is applied on the
decrypted packet to perform the final policy check. term1 defines the decrypted (and verified) traffic and performs the required
policy check. For information about term1, see Example: Configuring an Inbound Traffic Filter.
The inbound traffic filter is applied after the ES PIC has processed the packet, so the decrypted traffic is defined as any traffic that the remote gateway is encrypting and sending to this router. IKE uses this filter to determine the policy required for a tunnel. This policy is used during the negotiation with the remote gateway to find the matching SA configuration.
[edit interfaces]
es-1/2/0 {
unit 0 {
tunnel {
source 10.5.5.5; # tunnel source address
destination 10.6.6.6; # tunnel destination address
}
family inet {
filter {
input ipsec-decrypt-policy-filter;
}
ipsec-sa manual-sa1; # SA name applied to packet
address 10.1.1.8/32 { # local interface address inside local VPN
destination 10.2.2.254; # destination address inside remote VPN
}
}
}
Configuring an ES Tunnel Interface for a Layer 3 VPN
To configure an ES tunnel interface for a Layer 3 VPN, you need to configure an ES tunnel interface on the provider edge (PE) router and on the customer edge (CE) router. You also need to configure IPsec on the PE and CE routers. For more information about configuring an ES tunnel for a Layer 3 VPN, see the Junos OS VPNs Library for Routing Devices.
Configuring ES PIC Redundancy
You can configure ES PIC redundancy on M Series and T Series
routers that have multiple ES PICs. With ES PIC redundancy, one ES
PIC is active and another ES PIC is on standby. When the primary ES
PIC has a servicing failure, the backup becomes active, inherits all
the tunnels and SAs, and acts as the new next hop for IPsec traffic.
Reestablishment of tunnels on the backup ES PIC does not require new
Internet Key Exchange (IKE) negotiations. If the primary ES PIC comes
online, it remains in standby and does not preempt the backup. To
determine which PIC is currently active, use the show ipsec redundancy command.
ES PIC redundancy is supported on M Series and T Series routers.
To configure an ES PIC as the backup, include the backup-interface statement at the [edit interfaces fpc/pic/port es-options] hierarchy
level:
backup-interface es-fpc/pic/port;
Example: Configuring ES PIC Redundancy
After you create the inbound firewall filter, apply it to the
primary ES PIC. Here, the inbound firewall filter (ipsec-decrypt-policy-filter) is applied on the decrypted packet to perform the final policy
check. The IPsec manual-sa1 SA is referenced at the [edit interfaces es-1/2/0 unit 0 family inet] hierarchy level
and decrypts the incoming packet. This example does not show SA and
filter configuration. For information about SA and filter configuration,
see the Junos OS Administration Library for Routing Devices, the Routing Policies, Firewall Filters, and Traffic Policers User Guide, and Example: Configuring an Inbound
Traffic Filter.
[edit interfaces]
es-1/2/0 {
es-options {
backup-interface es-1/0/0;
}
unit 0 {
tunnel {
source 10.5.5.5;
destination 10.6.6.6;
}
family inet {
ipsec-sa manual-sa1;
filter {
input ipsec-decrypt-policy-filter;
}
address 10.1.1.8/32 {
destination 10.2.2.254;
}
}
}
}
Configuring IPsec Tunnel Redundancy
You can configure IPsec tunnel redundancy by specifying a backup destination address. The local router sends keepalives to determine the remote site’s reachability. When the peer is no longer reachable, a new tunnel is established. For up to 60 seconds during failover, traffic is dropped without notification being sent. Figure 2 shows IPsec primary and backup tunnels.
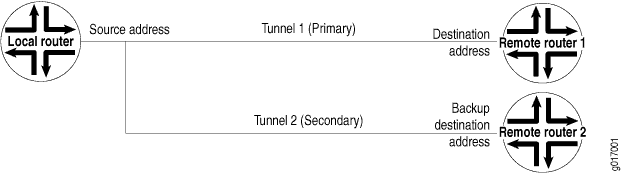
To configure IPsec tunnel redundancy, include the backup-destination statement at the [edit interfaces unit logical-unit-number tunnel] hierarchy level:
backup-destinationaddress; destination address; source address;
Tunnel redundancy is supported on M Series and T Series routers.
The primary and backup destinations must be on different routers.
The tunnels must be distinct from each other and policies must match.
For more information about tunnels, see Tunnel Interface Configuration on MX Series Routers Overview.
