ICMP and SYN Fragment Attacks
An ICMP flood typically occurs when ICMP echo request messages overload the victim, causing resources to stop responding to valid traffic. A fragmented SYN packet is anomalous, and as such, it is suspect. When a victim receives these packets, the results can range from processing packets incorrectly to crashing the entire system, For more information, see the following topics:
Understanding ICMP Fragment Protection
Internet Control Message Protocol (ICMP) provides error reporting and network probe capabilities. Because ICMP packets contain very short messages, there is no legitimate reason for ICMP packets to be fragmented. If an ICMP packet is so large that it must be fragmented, something is amiss.
When you enable the ICMP fragment protection screen option, Junos OS blocks any ICMP packet that has the More Fragments flag set or that has an offset value indicated in the offset field. See Figure 1.
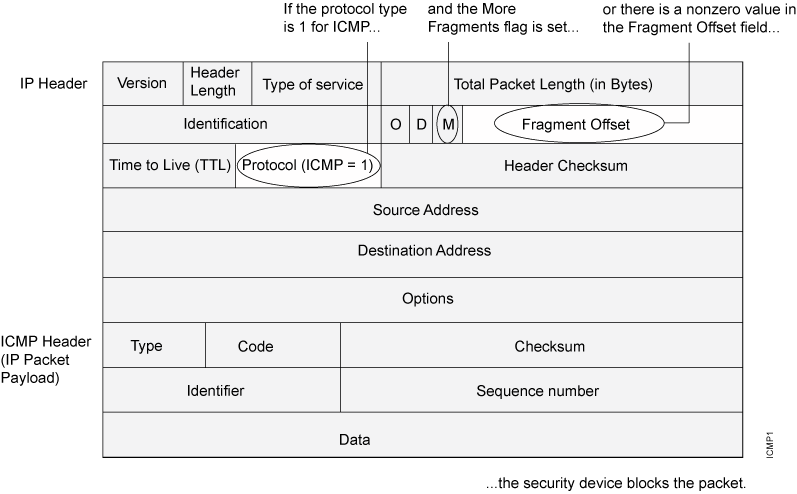
Junos OS supports ICMP fragment protection for ICMPv6 packets.
Example: Blocking Fragmented ICMP Packets
This example shows how to block fragmented ICMP packets.
Requirements
Before you begin, Understand ICMP fragment protection. See Suspicious Packet Attributes Overview.
Overview
When you enable the ICMP fragment protection screen option, Junos OS blocks any ICMP packet that has the more fragments flag set or that has an offset value indicated in the offset field.
In this example, you configure the ICMP fragment screen to block fragmented ICMP packets originating from the zone1 security zone.
Topology
Configuration
Procedure
Step-by-Step Procedure
To block fragmented ICMP packets:
Configure the screen.
[edit] user@host# set security screen ids-option icmp-fragment icmp fragment
Configure a security zone.
[edit] user@host# set security zones security-zone zone1 screen icmp-fragment
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security screen statistics zone zone-name command.
Understanding Large ICMP Packet Protection
Internet Control Message Protocol (ICMP) provides error reporting and network probe capabilities. Because ICMP packets contain very short messages, there is no legitimate reason for large ICMP packets. If an ICMP packet is unusually large, something is amiss.
See Figure 2.
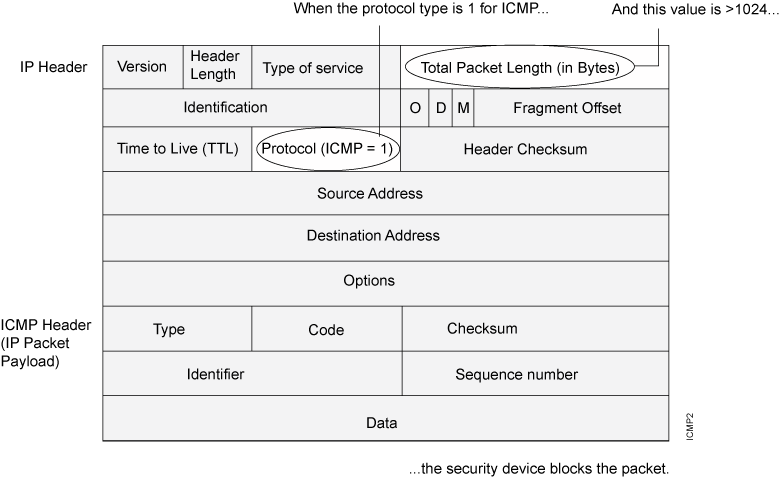
When you enable the large size ICMP packet protection screen option, Junos OS drops ICMP packets with a length greater than 1024 bytes.
Junos OS supports large ICMP packet protection for both ICMP and ICMPv6 packets.
Example: Blocking Large ICMP Packets
This example shows how to block large ICMP packets.
Requirements
Before you begin, Understand large ICMP packet protection. See Suspicious Packet Attributes Overview.
Overview
When you enable the large ICMP packet protection screen option, Junos OS drops ICMP packets that are larger than 1024 bytes.
In this example, you configure the ICMP large screen to block large ICMP packets originating from the zone1 security zone.
Topology
Configuration
Procedure
Step-by-Step Procedure
To block large ICMP packets:
Configure the screen.
[edit] user@host# set security screen ids-option icmp-large icmp large
Configure a security zone.
[edit] user@host# set security zones security-zone zone1 screen icmp-large
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security screen statistics zone zone-name command.
Understanding SYN Fragment Protection
The IP encapsulates a TCP SYN segment in the IP packet that initiates a TCP connection. Because the purpose of this packet is to initiate a connection and invoke a SYN/ACK segment in response, the SYN segment typically does not contain any data. Because the IP packet is small, there is no legitimate reason for it to be fragmented.
A fragmented SYN packet is anomalous, and, as such, it is suspect. To be cautious, block such unknown elements from entering your protected network. See Figure 3.
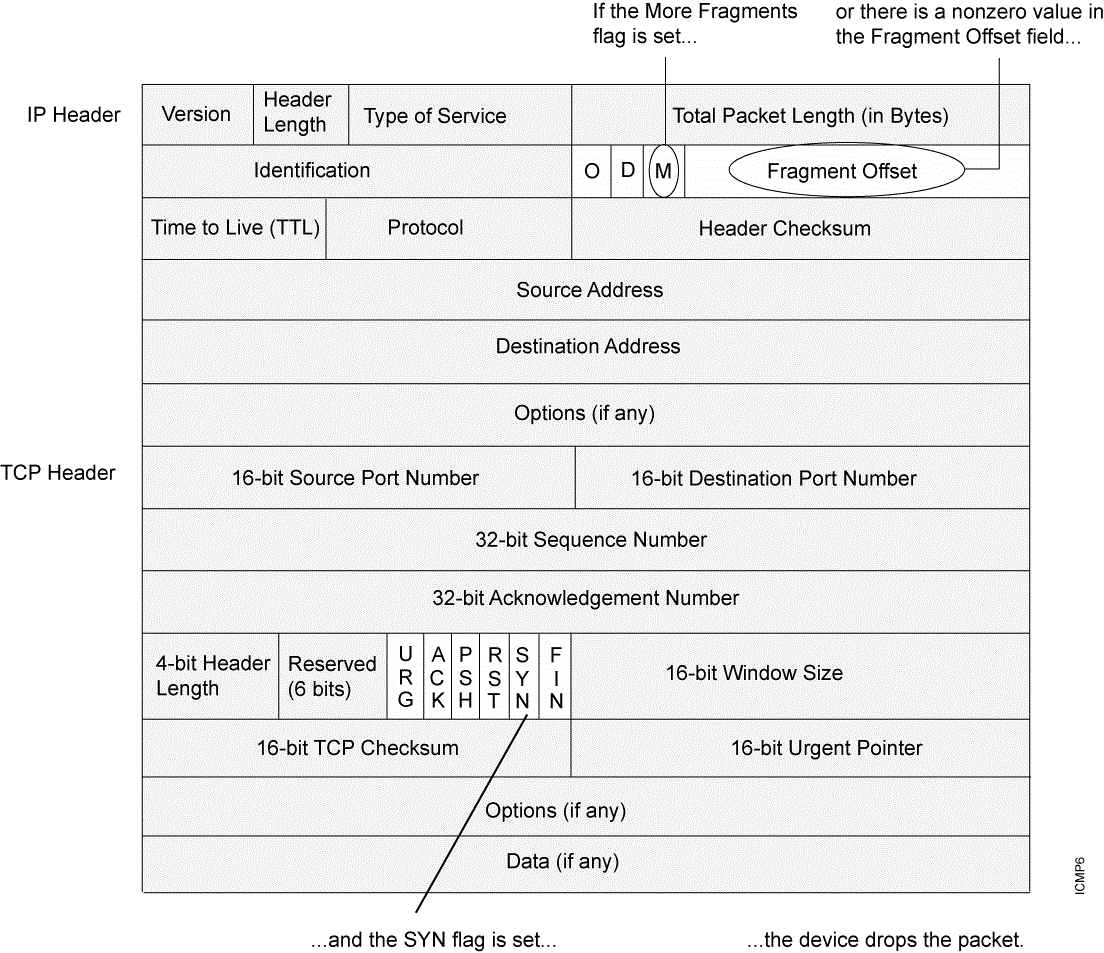
When you enable the SYN fragment detection screen option, Junos OS detects packets when the IP header indicates that the packet has been fragmented and the SYN flag is set in the TCP header. Junos OS records the event in the screen counters list for the ingress interface.
Junos OS supports SYN fragment protection for both IPv4 and IPv6 packets.
Example: Dropping IP Packets Containing SYN Fragments
This example shows how to drop IP packets containing SYN fragments.
Requirements
Before you begin, Understand IP packet fragment protection. See Suspicious Packet Attributes Overview.
Overview
When you enable the SYN fragment detection screen option, Junos OS detects packets when the IP header indicates that the packet has been fragmented and the SYN flag is set in the TCP header. Also, Junos OS records the event in the screen counters list for the ingress interface.
In this example, you configure the SYN fragment screen to drop fragmented SYN packets originating from the zone1 security zone.
Topology
Configuration
Procedure
Step-by-Step Procedure
To drop IP packets containing SYN fragments:
Configure the screen.
[edit] user@host# set security screen ids-option syn-frag tcp syn-frag
Configure the security zone.
[edit] user@host# set security zones security-zone zone1 screen syn-frag
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security screen statistics zone zone-name command.
