IP Packet Protection
Some attackers can abuse the IP option fields, the original intent of which was (and still is) to provide special routing controls, diagnostic tools, and security. By misconfiguring these options, attackers produce either incomplete or malformed fields within a packet. Attackers can use these malformed packets to compromise hosts on the network, For more information, see the following topics:
Understanding IP Packet Fragment Protection
As packets traverse different networks, it is sometimes necessary to break a packet into smaller pieces (fragments) based upon the maximum transmission unit (MTU) of each network. IP fragments might contain an attacker's attempt to exploit the vulnerabilities in the packet reassembly code of specific IP stack implementations. When the victim receives these packets, the results can range from processing the packets incorrectly to crashing the entire system. See Figure 1.
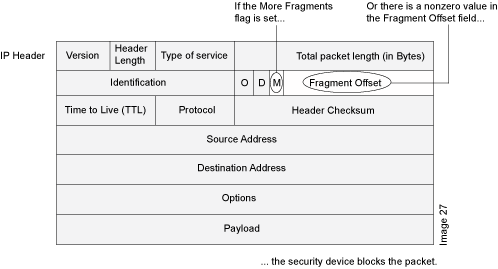
When you enable Junos OS to deny IP fragments on a security zone, it blocks all IP packet fragments that it receives at interfaces bound to that zone.
Junos OS supports IP fragment protection for both IPv4 and IPv6 packets.
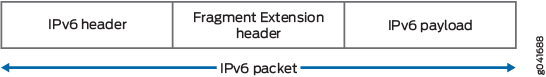
In IPv6 packets, fragment information is not present in the IPv6 header. The fragment information is present in the fragment extension header, which is responsible for IPv6 fragmentation and reassembly. The source node inserts the fragment extension header between the IPv6 header and the payload header if fragmentation is required. See Figure 2.
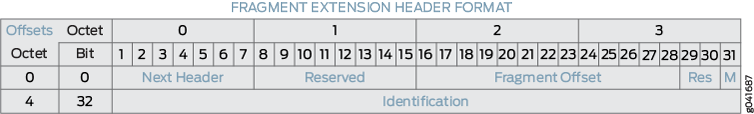
The general format of the fragment extension header is shown in Figure 3.
Example: Dropping Fragmented IP Packets
This example shows how to drop fragmented IP packets.
Requirements
Before you begin, Understand IP packet fragment protection. See Suspicious Packet Attributes Overview.
Overview
When this feature is enabled, Junos OS denies IP fragments on a security zone and blocks all IP packet fragments that are received at interfaces bound to that zone.
In this example, you configure the block fragment screen to drop fragmented IP packets originating from the zone1 security zone.
Topology
Configuration
Procedure
Step-by-Step Procedure
To drop fragmented IP packets:
Configure the screen.
[edit] user@host# set security screen ids-option block-frag ip block-frag
Configure the security zone.
[edit] user@host# set security zones security-zone zone1 screen block-frag
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security screen statistics zone zone-name command.
Understanding Bad IP Option Protection
The IP standard RFC 791, Internet Protocol, specifies a set of eight options that provide special routing controls, diagnostic tools, and security. Although the original, intended uses for these options served worthy ends, people have figured out ways to twist these options to accomplish less commendable objectives.
Either intentionally or accidentally, attackers sometimes configure IP options incorrectly, producing either incomplete or malformed fields. Regardless of the intentions of the person who crafted the packet, the incorrect formatting is anomalous and potentially harmful to the intended recipient. See Figure 4.
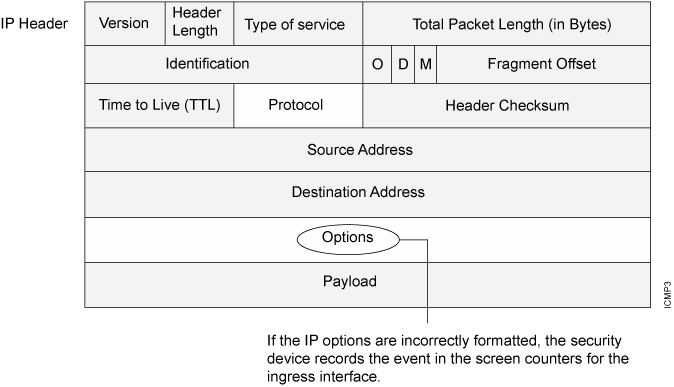
When you enable the bad IP option protection screen option, Junos OS blocks packets when any IP option in the IP packet header is incorrectly formatted. Additionally, Junos OS records the event in the event log.
Junos OS supports bad IP option protection for both IPv4 and IPv6 packets.
Example: Blocking IP Packets with Incorrectly Formatted Options
This example shows how to block large ICMP packets with incorrectly formatted options.
Requirements
Before you begin, Understand bad IP option protection. See Suspicious Packet Attributes Overview.
Overview
When you enable the bad IP option protection screen option, Junos OS blocks packets when any IP option in the IP packet header is incorrectly formatted. Additionally, Junos OS records the event in the event log.
In this example, you configure the IP bad option screen to block large ICMP packets originating from the zone1 security zone.
Topology
Configuration
Procedure
Step-by-Step Procedure
To detect and block IP packets with incorrectly formatted IP options:
Configure the screen.
[edit] user@host# set security screen ids-option ip-bad-option ip bad-option
Note:Currently this screen option is applicable only to IPv4.
Configure a security zone.
[edit] user@host# set security zones security-zone zone1 screen ip-bad-option
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security screen statistics zone zone-name command.
Understanding Unknown Protocol Protection
Based on the latest IANA protocol numbers document, the protocol types with ID numbers of 143 or greater are reserved and undefined at this time. Precisely because these protocols are undefined, there is no way to know in advance if a particular unknown protocol is benign or malicious.
Unless your network makes use of a nonstandard protocol with an ID number of 143 or greater, a cautious stance is to block such unknown elements from entering your protected network. See Figure 5.
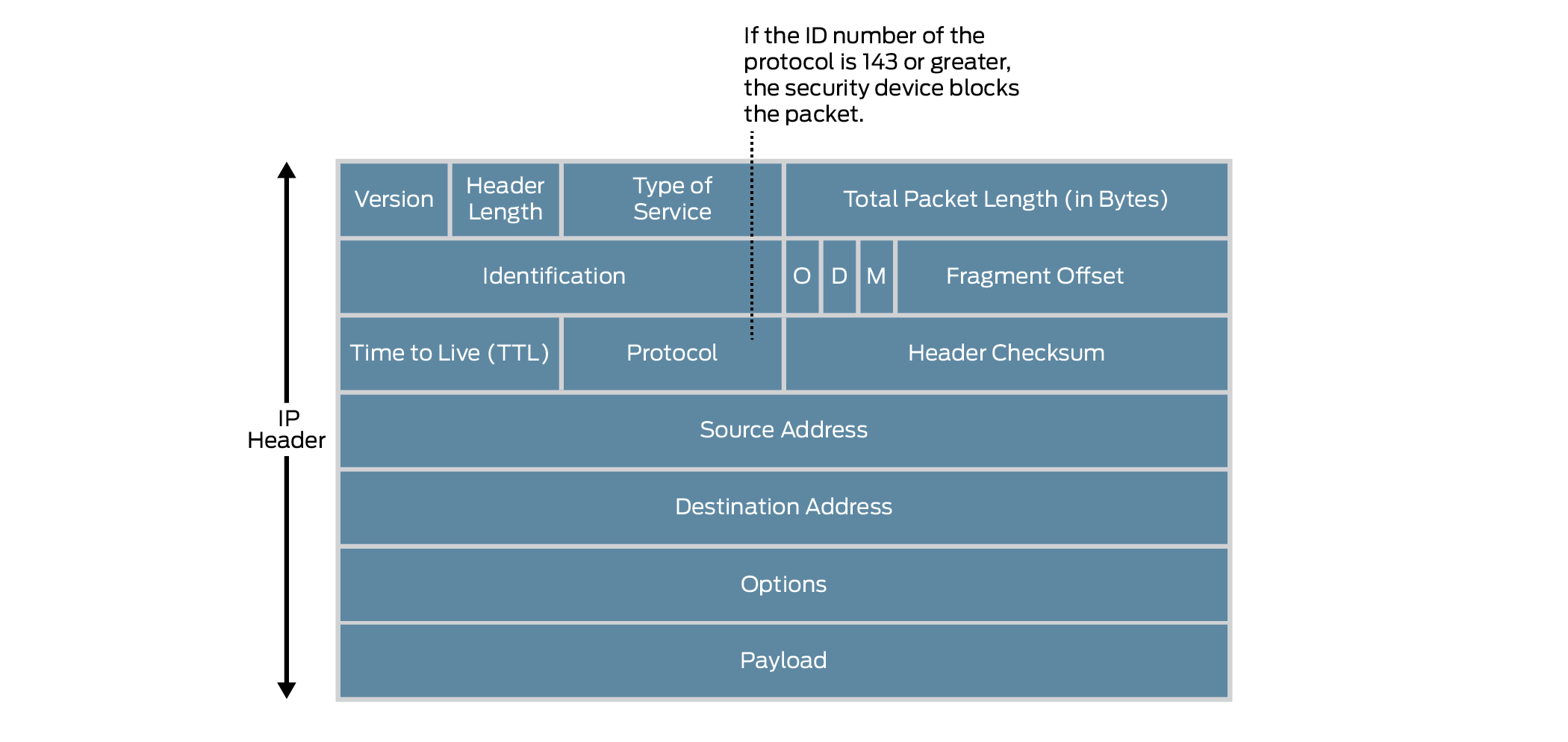
When you enable the unknown protocol protection screen option, Junos OS drops packets when the protocol field contains a protocol ID number of 143 or greater by default.
When you enable the unknown protocol protection screen option for IPv6 protocol, Junos OS drops packets when the protocol field contains a protocol ID number of 143 or greater by default.
Example: Dropping Packets Using an Unknown Protocol
This example shows how to drop packets using an unknown protocol.
Requirements
Before you begin, Understand unknown protocol protection. See Suspicious Packet Attributes Overview.
Overview
When you enable the unknown protocol protection screen option, Junos OS drops packets when the protocol field contains a protocol ID number of 137 or greater by default.
In this example, you configure the unknown protocol screen to block packets with an unknown protocol originating from the zone1 security zone.
Topology
Configuration
Procedure
Step-by-Step Procedure
To drop packets that use an unknown protocol:
Configure the unknown protocol screen.
[edit] user@host# set security screen ids-option unknown-protocol ip unknown-protocol
Configure a security zone.
[edit] user@host# set security zones security-zone zone1 screen unknown-protocol
If you are done configuring the device, commit the configuration.
[edit] user@host# commit
Verification
To verify the configuration is working properly,
enter the show security screen statistics zone zone-name command.
Understanding Allowlists for IP Block Fragment Screen
Junos OS provides the administrative option to configure an allowlist of trusted IP addresses on IP block fragment screen. When you enable IP block fragmentation in a zone, Junos OS denies IP fragments and blocks all IP packet fragments. All the fragmented IP packets will be dropped. To avoid these packets dropping and instead allow these packets to bypass the IP block fragmentation check, you must configure IP block fragment allowlist.
When you configure allowlist on IP block fragment screen, the traffic from source addresses in the allowlist groups bypasses the IP block fragmentation check. IP block fragment allowlist supports both IPv4 and IPv6 addresses and in each allowlist, there can be up to 32 IP address prefixes. You can configure single address or subnet address.
Benefits of IP Block Fragment Allowlist
- IP block fragment allowlist bypasses the IP block fragmentation check to allow fragmented IP packets from specific sources.
