Off-site Hosts Management
An off-site host is a JSA appliance that can't be accessed through the JSA console in your current deployment. You can configure an off-site host to transfer data to or to receive data from your JSA deployment.
Configuring an Off-site Source
To forward event and flow data to an Event Collector in another deployment, configure the target deployment to include an off-site source so that it knows which computer is sending the data.
To prevent connection errors, when you configure off-site source and target components, deploy the JSA Console with the off-site source first. Then, deploy the JSA console with the off-site target.
On the navigation menu (
 ), click Admin.
), click Admin.In the System Configuration section, click System and License Management.
In the Display list, select Systems.
On the Deployment Actions menu, click Manage Off-site Sources.
Click Add and configure the parameters.
The name can be up to 20 characters in length and can include underscores or hyphens.
Click Save.
Click Manage Connections to specify which JSA hosts you want to receive the data.
The host must have an Event Collector to receive the data.
Repeat the steps to configure all off-site sources that you want to configure.
Deploy the changes and restart the event collection service.
Configuring an Off-site Target
To forward event and flow data to an Event Collector in another deployment, configure the source deployment to include an off-site target so that it knows which computer to send the data to.
You must know the listening ports for the off-site target appliance. By default, the listening port for events is 32004, and 32000 for flows.
To find the listening port on the target appliance, follow these steps:
In the target deployment, click the System and License Management icon.
Select the host and click Deployment Actions >Edit Host.
Click the Component Management settings icon (
 ), and find the ports in the Event Forwarding Listening Port and Flow Forwarding Listening
Port fields.
), and find the ports in the Event Forwarding Listening Port and Flow Forwarding Listening
Port fields.
To prevent connection errors, when you configure off-site source and target components, deploy the JSA Console with the off-site source first. Then, deploy the JSA console with the off-site target.
On the navigation menu (
 ), click Admin.
), click Admin.In the System Configuration section, click System and License Management.
In the Display list, select Systems.
On the Deployment Actions menu, click Manage Off-site Targets.
Click Add and configure the parameters.
The name can be up to 20 characters in length and can include underscores or hyphens.
The default port to listen for events is 32004, and 32000 for flows.
Note:If the off-site target is a managed host with encrypted host connections to its console, port 22 for SSH opens no matter which port is selected in the user interface.
Click Save.
Click Manage Connections to specify which JSA hosts you want to receive the data.
Only hosts that have an Event Collector are shown in the list.
Repeat the steps to configure all off-site targets that you want to configure.
On the Admin tab, click Deploy changes.
Generating Public Keys for JSA Products
To forward normalized events in JSA, you must copy the public key file, /root/.ssh/id_rsa.pub, from the off-site source to the off-site target.
If the off-site source and off-site target are on separate systems, the public key is automatically generated. If the off-site source and target are both on an all-in-one system, the public key is not automatically generated. You must manually generate the public key.
To manually generate the public key, follow these steps:
Use SSH to log in to your system as the root user.
To generate the public key, type the following command:
opt/qradar/bin/ssh-key-generating
Press Enter.
The public and private key pair is generated and saved in the /root/.ssh/id_rsa folder.
Forwarding Filtered Flows
You can set up forwarding of filtered flows. You can use filtered flows to split flow forwarding across multiple boxes, and to forward specific flows for specific investigations.
On the target system, set up the source system as an off-site source.
On the navigation menu (
 ), click Admin.
), click Admin.Click System and License Management > Deployment Actions > Manage Off-Site Sources.
Add the source system IP address, and select Receive Events and/or Receive Flows.
Select Manage Connections and select which host is expecting to receive the off-site connection.
Click Save.
Select Deploy Full Configuration from the Advanced menu for the changes to take effect.
On the source system, set up the forwarding destination, IP address, and port number.
Click Main menu > Admin.
Click Forwarding Destinations > Add.
Set the IP address of the target system and the destination port.
Enter 32000 for the port number on the source system. Port 32000 is used for flow forwarding.
Select Normalized from the Event Format list.
Set up routing rules.
Click Main menu > Admin.
Click Routing Rules > Add.
Select the rules that you want to add.
Note:Rules forward flows that are based on offenses, or based on CRE information when Offline Forwarding is selected on the Routing Rules page.
The flows that are filtered on the Routing Rules screen are forwarded.
Example: Forwarding Normalized Events and Flows
To forward normalized events and flows, configure the target deployment to include an off-site source so that it knows which computer is sending the data. Configure the source deployment to include an off-site target so that it knows which computer to send the data to.
The following diagram shows forwarding event and flow data between deployments.
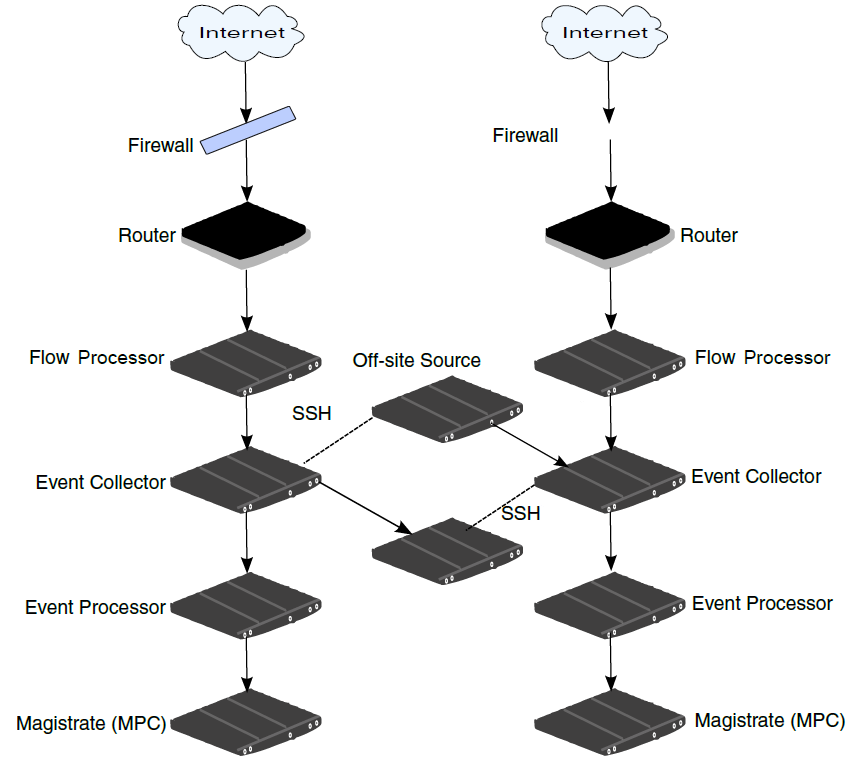
If the off-site source or target is an all-in-one system, the public key is not automatically generated; therefore, you must manually generate the public key. For more information, see Generating public keys for JSA products.
To forward normalized events and flows from Deployment A to Deployment B:
Configure an off-site target in Deployment A.
The off-site target configuration includes the IP address of the Event Collector in Deployment B that receives the data.
Configure an off-site source in Deployment B.
The off-site source configuration includes the IP address and the port number of the Event Collector in Deployment A that is sending the data.
To transfer encrypted data, you must enable encryption on both the off-site source and the off-site target.
To ensure appropriate access, the SSH public key for the source system (Deployment A) must be available to the target system (Deployment B). For example, to enable encryption between Deployment A and Deployment B, follow these steps:
Create ssh keys by using the ssh-keygen -1 -t rsa command, and press enter when prompted about the directory and passphrase.
By default, the id_rsa.pub file is stored in the /root/.ssh directory.
Copy the id_rsa.pub file to the /root/.ssh directory on the Event Collector and on the JSA console in the source system (Deployment A).
Rename the file to authorized_keys.
Ensure that the source system is configured with the appropriate permissions to send event and flow data to the target system.
If you didn't use the chmod 600 authorized_keys command to assign rw owner privileges to the file and the parent directory, use the ssh-copy-id command with the -i parameter to specify that the identity file /root/.ssh/id_rsa.pub be used.
For example, type the following command to append entries or create a new authorized_keys file on the target console with the right privileges. This command does not check for duplicate entries.
ssh-copy-id -i root@10.100.133.80
Configure the source system to ensure that forwarding of events and flows is not interrupted by other configuration activities, such as adding a managed host to one of the consoles.
For example, if a managed host is added to a console that is forwarding events, then an authorized_keys file must exist in the /root/.ssh directory on the managed host. If not, adding a managed host fails. This file is required regardless of whether encryption is used between the managed host and the console.
On the JSA console in the source system (Deployment A), create a ssh_keys_created file under /opt/qradar/conf.
Change the owner and group to nobody and the permission to 775 to make sure that the file can be backed up and restored properly.
chown nobody:nobody /opt/qradar/conf/ssh_keys_created chmod 775 /opt/qradar/conf/ssh_keys_created
To prevent connection errors, deploy the changes in the target system (Deployment B) before you deploy the changes in the source system (Deployment A).
If you update the Event Collector configuration or the monitoring ports, you must manually update the configuration for the off-site source and off-site target to maintain the connection between the two deployments.
If you want to disconnect the source system (Deployment A), you must remove the connections from both deployments. Remove the off-site target from the source system (Deployment A), and then remove the off-site source from the target system (Deployment B).
