Overview
Welcome to the Juniper ATP Appliance Traffic Collectors Quick Start Guide.
When linked logically to the Core, the Juniper ATP Appliance Traffic Collectors continuously monitor and inspect all network traffic for malware objects; extracting and sending objects to the Core for Windows or Mac OS X object analysis and detection. Juniper ATP Appliance Web/ Email Collectors efficiently separate traffic monitoring and inspection from behavioral analysis, multi-platform detonation and context reasoning.
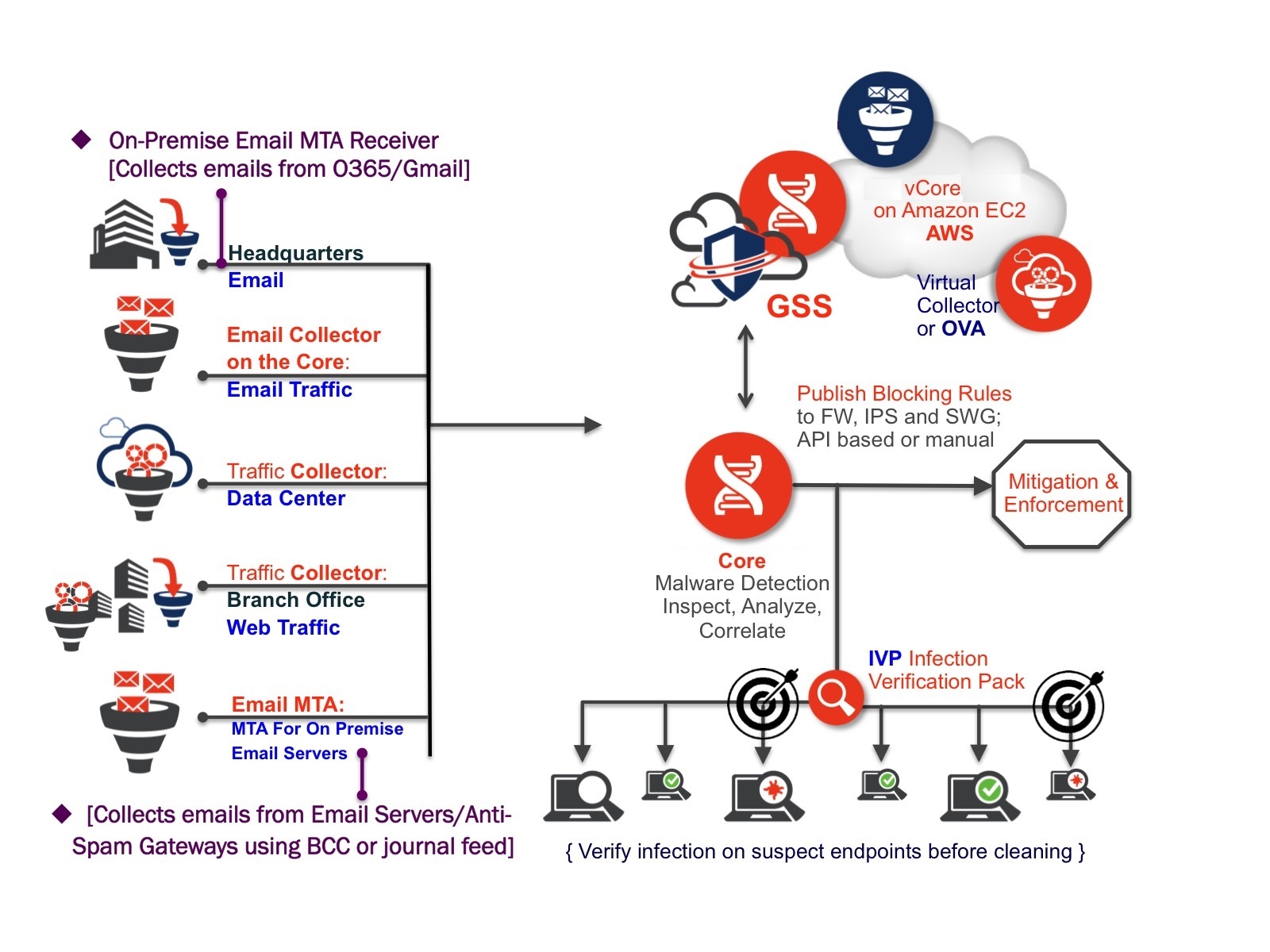
All detected threats and breaches are analyzed by the detonation and intelligence engines within the Juniper ATP Appliance Core, then aggregated and reported in real-time to the Juniper ATP Appliance Central Manager Web UI. In the Web UI, all threats are detailed with corresponding context-specific mitigation options.
Use this guide to install a Juniper ATP Appliance Traffic Collector and to configure its logical connection to a network switch TAP port and a Juniper ATP Appliance Core/CM or All-in-One Server.
For hardware specifications and set up instructions, refer to the Juniper Networks Advanced Threat Prevention 700 Appliance Hardware Guide.
For information about installing the Small Form Factor Collector ISO to a Mac Mini, refer to Installing the Small Form Factor Collector ISO to a Mac Mini.
To configure an inside outside data path SPAN-traffic proxy, or management network proxy, refer to the CLI Command Reference Guide.
This document assumes you have already installed and configured the Juniper ATP Appliance Core/Central Manager or All-in-One Server. Refer to the respective Quick Start Guides for combined and separate Core/Central Manager Server(s), All-in-One, and/or Mac OS X installations.
Firewall & Management Network Interface Connectivity
Connectivity requirements for the Juniper ATP Appliance management interface (eth0) allow for transfer of inspected network objects, live malware behavior analysis, intelligence reporting, and product updates. If the enterprise network firewall uses an outgoing “default allow” rule, this is sufficient. Otherwise, create the following firewall rules:
SSH port 443 should be open from the Collector to the Core/CM or All-in-One (for traffic inspection and malware behavior analysis).
IMPORTANT: Primary Core/CM and Secondary Cores/Mac Cores must be on the same network, and allow all ports, with no Port Address (PAT) or Network Address Translation (NAT).
All GSS communications for security and content auto-updates are handled by the Core/ CM or All-in-One system.
