EN ESTA PÁGINA
Usar perfil de clave para VPN IPsec seguro para Quantum Safe
Configurar el perfil de clave estática para Junos Key Manager
Ejemplo: Configurar el perfil de claves estáticas para VPN de sitio a sitio
Ejemplo: Configurar el perfil de claves estáticas para AutoVPN
Configurar el perfil de clave de Quantum Key Manager para Junos Key Manager
Ejemplo: Configurar el perfil de clave de Quantum Key Manager para VPN IPsec de sitio a sitio
VPN IPsec segura para cuántica
Aprenda a usar y configurar los mecanismos de recuperación de claves fuera de banda en el proceso IKED para negociar con SA de IPsec y IKE con seguridad cuántica.
Descripción general de la seguridad cuántica
El canal de comunicación IPsec se basa en el protocolo de intercambio de claves por Internet (IKE). La IKE mantiene parámetros de seguridad para proteger el tráfico de datos. Los parámetros de seguridad incluyen algoritmos de cifrado y autenticación, y claves asociadas.
Los protocolos de seguridad se basan en algoritmos criptográficos asimétricos como Diffie Hellman (DH) o Elliptic Curve Diffie Hellman (ECDH) para establecer claves que son vulnerables a ataques.
Para evitar ataques de seguridad, el RFC8784 introduce un método fuera de banda. El método fuera de banda agrega una clave secreta en el iniciador y el respondedor. La clave secreta es la clave precompartida postcuántica (PPK).
-
Puede usar PPK además del método de autenticación en IKEv2.
-
PPK proporciona resistencia cuántica a cualquier SA secundaria en las SA IPsec negociadas inicialmente y en cualquier SA IPsec reiked posteriores.
-
Con PPK y la clave de autenticación del mismo nivel, el iniciador y el respondedor pueden detectar una falta de coincidencia de claves.
Descripción general de Junos Key Manager
Puede utilizar Junos Key Manager (JKM) para configurar las teclas estáticas o las claves dinámicas para proteger el plano de datos y el plano de control.
El proceso JKM actúa como un almacén de claves y un proxy entre el cliente o la aplicación criptográfica. El cliente o la aplicación criptográfica requieren una clave para establecer una sesión segura cuántica cifrada y autenticada con un par o una aplicación. La caja fuerte cuántica utiliza el mecanismo de recuperación de claves fuera de banda que permite que dos pares tengan la clave. Los diferentes mecanismos fuera de banda tendrán diferentes protocolos o métodos para comunicarse. El JKM proporciona una interfaz uniforme común para que las aplicaciones cliente o criptográficas se comuniquen.
Mecanismo de recuperación de claves
Dos mecanismos de recuperación de claves fuera de banda en el proceso IKED para negociar con IKE con seguridad cuántica y SA IPsec.
-
Clave estática: con los perfiles de clave estática, puede configurar un ID de clave estática y una clave correspondiente. Se genera el mismo ID de clave estática y la misma clave cada vez que se realiza una solicitud a JKM a través de un perfil de clave estática.
-
Quantum Key Manager: con los perfiles de clave del administrador de claves cuánticas, puede acceder a los dispositivos de distribución cuántica de claves (QKD) y a Quantum Network. La red cuántica genera e intercambia claves cuánticas entre pares. Genera un ID de clave y una clave diferentes cada vez que se solicita a JKM a través de un perfil de clave de administrador de claves cuánticas.
Usar perfil de clave para VPN IPsec seguro para Quantum Safe
Con los perfiles de clave estática, puede configurar un ID de clave estática y una clave correspondiente. Para establecer las SA IPsec seguras cuánticamente, use el perfil de clave estática como perfil de clave precompartida postcuántica (PPK) en la configuración de IPsec-VPN. Utiliza la misma clave e ID de clave para volver a autenticar la SA de IKE existente.
Con los perfiles de perfil de clave del administrador de claves cuánticas, para acceder a las redes cuánticas necesita acceso a los dispositivos QKD. La red cuántica genera e intercambia claves cuánticas entre pares. Puede configurar todos los parámetros necesarios, como el ID de SAE local, la URL del dispositivo QKD, etc. Para establecer SA IPsec, use el perfil de clave del administrador de claves cuánticas como perfil de clave precompartida postcuántica (PPK) en la configuración de VPN IPsec. Utiliza una clave y un ID de clave diferentes para volver a autenticar la SA de IKE existente.
Distribución cuántica de claves
La distribución cuántica de claves (QKD) es un método seguro de distribución de claves que utiliza cuántica. Las redes utilizan canales cuánticos para generar la misma clave en ambos extremos y monitorean el canal cuántico entre los pares. Estas claves son dinámicas, protegen el plano de datos y el plano de control.
Entidad de administración de claves (KME) es el término que usamos para referirnos a los dispositivos QKD en la capa de administración o control. Los dispositivos QKD se conectan entre sí a través de su red cuántica o QKD. El KME se conecta a través de la red pública a través de los canales seguros para intercambiar cualquier mensaje de control. Las aplicaciones, la entidad de aplicación segura (SAE) y los dispositivos interactúan con los KME a través de los canales seguros según la especificación ETSI. HTTPS se combina con la autenticación TLS mutua y permite operaciones seguras a través de la red QKD.
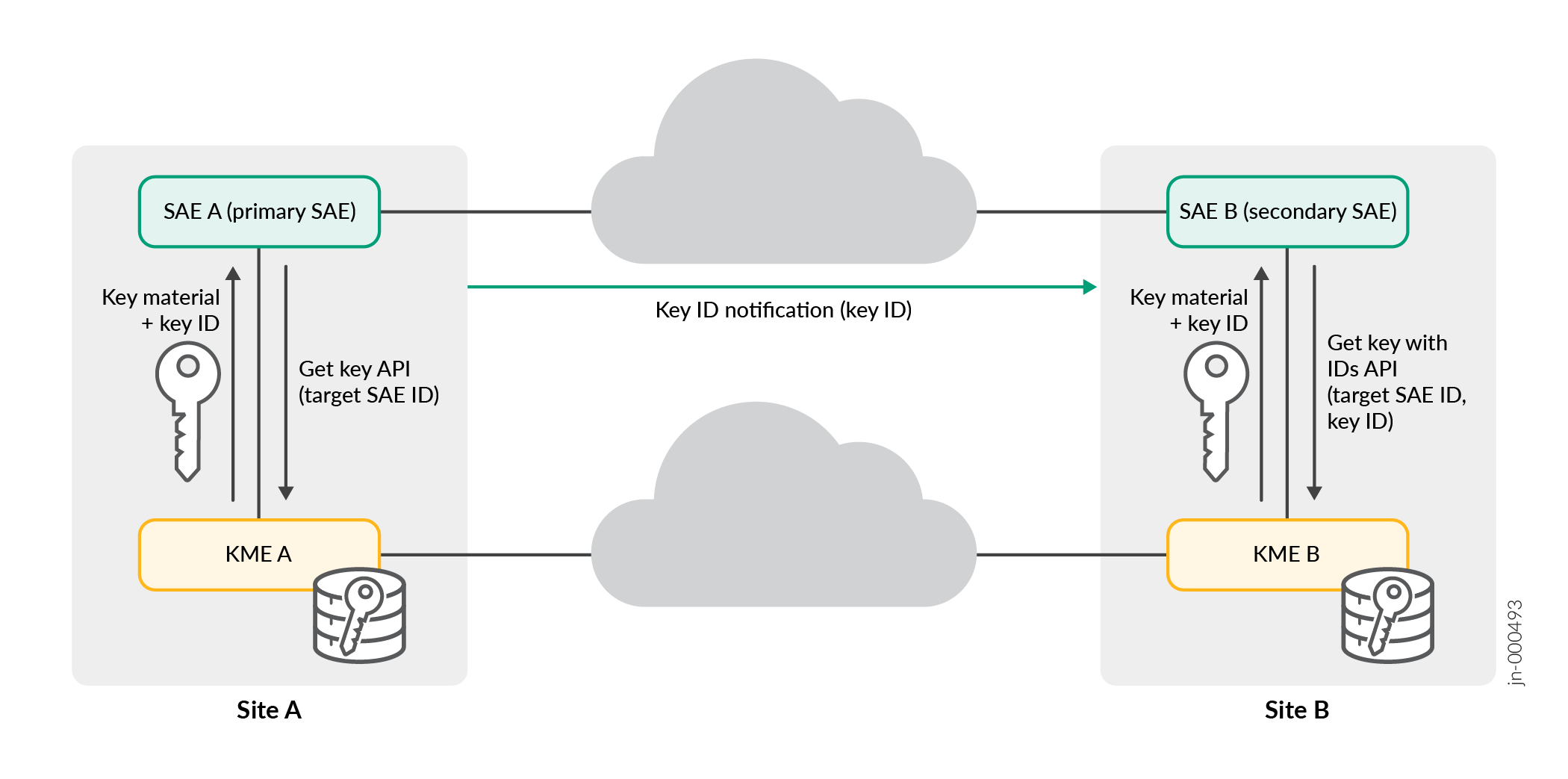
En el describe cómo Figura 1 los dos dispositivos interactúan con sus correspondientes dispositivos QKD para establecer una sesión cuántica segura
-
SAE El rol A es primario. SAE A actúa como iniciador para establecer una sesión cuántica segura con SAE B.
-
El rol de SAE B es secundario. SAE B actúa como respondedor.
-
La SAE A solicita el KME A a través de la API de clave Get para generar y compartir una nueva clave cuántica con SAE B con el ID SAE de destino.
-
El KME A realiza la operación y responde a SAE A con el ID de clave generado y el material clave.
-
KME B recibe el material clave y la clave de identificación generada a través de la red QKD.
-
La SAE A inicia una sesión segura con SAE B directamente utilizando la misma clave e ID de clave.
-
Un intercambio de mensajes establece una sesión segura con SAE B.
-
SAE A envía el ID de clave en texto sin formato o cifrado para la clave cuántica correspondiente que se utiliza para proteger la sesión con SAE B.
-
Una vez que SAE B recibe el ID de clave, SAE B se pone en contacto con KME B a través de la API Get key with IDs para obtener la clave cuántica correspondiente para el ID de clave dado y el ID de SAE de destino o SAE A.
-
Después de que SAE B obtiene la clave, se establece una sesión totalmente segura cuántica entre SAE A y SAE B.
Configurar el perfil de clave estática para Junos Key Manager
En este ejemplo, se muestra cómo configurar el perfil de clave estática para el administrador de claves de Junos. Configure las claves estáticas en las puertas de enlace correspondientes y no sea necesario compartir claves estáticas a través de Internet para establecer el túnel IPsec.
Requisitos
-
Requisitos de hardware: firewall de Juniper Networks® SRX1500 y modelos de dispositivos numerados superiores o firewall virtual vSRX de Juniper Networks® (vSRX3.0).
-
Requisitos de software: versión 22.4R1 o posterior de Junos OS con JUNOS ike y JUNOS Key Manager paquetes.
Descripción general
Con los perfiles basados en claves estáticas, debe configurar un ID de clave estática y una clave correspondiente. Si utiliza el perfil de clave estática en el objeto VPN IPsec, cuando se vuelva a autenticar para la SA de IKE existente, se utilizarán la misma clave e ID de clave.
Configuración
Configure el perfil de clave estática para el administrador de claves de Junos.
user@host# set security key-manager profiles km_profile_1 static key-id ascii-text test-ppk-id user@host# set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
Verificación
Propósito
Compruebe el perfil y las claves de la clave estática.
Acción
Desde el modo operativo, escriba el request security key-manager profiles get profile-keys name km_profile_1 para ver el perfil y las claves de la clave estática.
user@host> request security key-manager profiles get profile-keys name km_profile_1
- Response:
- Status: SUCCESS
- Name: km_profile_1
- Type: Static
- Key-size: 280 bits
- Key-count: 1
- Key-ids:
- test-ppk-id
- Keys:
- 716a776264697031333975356d637938396d32387063676f77657265666e6b6a736467Desde el modo operativo, introduzca el show security key-manager profiles name km_profile_1 detail para ver los detalles del perfil de clave estática.
user@host> show security key-manager profiles name km_profile_1 detail
Name: km_profile_1, Index: 1, Type: Static
Configured-at: 10.09.23 (20:16:34)
Time-elapsed: 0 hrs 2 mins 21 secs
Request stats:
Received: 1
In-progress: 0
Success: 1
Failed: 0
Significado
Muestra request security key-manager profiles get profile-keys name km_profile_1 el estado, el nombre del perfil de clave estática, el tipo, el tamaño de clave, el ID de clave y las claves.
Muestra show security key-manager profiles name km_profile_1 detail el nombre del perfil de clave estática, el tipo y el estado de la solicitud.
Ejemplo: Configurar el perfil de claves estáticas para VPN de sitio a sitio
Utilice este ejemplo de configuración para configurar el perfil de clave estática. Puede usar el perfil de clave estática para proteger una infraestructura VPN de sitio a sitio IPsec.
Puede proteger una infraestructura VPN de sitio a sitio IPsec configurando el perfil de clave estática.
En este ejemplo de configuración, los dispositivos SRX1 y SRX2 usan el perfil de clave estática para obtener las claves QKD en VPN IPsec. Las teclas QKD ayudan a enviar tráfico de forma segura a través de Internet.
|
Tiempo de lectura |
Menos de una hora |
|
Tiempo de configuración |
Menos de una hora |
- Ejemplo de requisitos previos
- Antes de empezar
- Descripción general funcional
- Información general sobre la topología
- Ilustración de topología
- Configuración paso a paso en dispositivos de firewall de la serie SRX
- Verificación
- Apéndice 1: Establecer comandos en todos los dispositivos
- Apéndice 2: Mostrar salida de configuración en DUT
Ejemplo de requisitos previos
|
Requisitos de hardware |
Firewall SRX1500 de Juniper Networks® o modelos de dispositivos numerados superiores o Firewall virtual vSRX de Juniper Networks® (vSRX3.0) |
|
Requisitos de software |
Junos OS versión 22.4R1 o posterior. |
Antes de empezar
|
Ventajas |
|
|
Recursos útiles |
|
|
Saber más |
|
|
Experiencia práctica |
|
|
Seguir leyendo |
Descripción general funcional
| VPN IPSec |
Implemente una topología VPN IPsec en la que los dispositivos de firewall de la serie SRX estén conectados mediante túneles VPN que envían tráfico a través del túnel VPN IPsec. Los túneles VPN se configuran posteriormente para usar claves cuánticas, lo que los convierte en túneles VPN de seguridad cuántica. |
| Puerta de enlace IKE |
Al establecer una conexión segura, la puerta de enlace de IKE utiliza la política de IKE para limitarse al grupo configurado de CA (perfiles de CA) mientras valida el certificado. |
| Propuestas | |
| Propuesta de IKE |
Defina los algoritmos y las claves utilizados para establecer la conexión IKE segura con la puerta de enlace de seguridad del mismo nivel. IKE crea las SA dinámicas y las negocia para IPsec. |
| Propuesta IPsec |
Enumere los protocolos, algoritmos y servicios de seguridad que se negociarán con el par IPsec remoto. |
| Políticas | |
| Política de IKE |
Defina una combinación de parámetros de seguridad (propuestas IKE) que se utilizarán durante la negociación de IKE. |
| Directiva IPsec |
Contener reglas y políticas de seguridad para permitir el tráfico VPN de grupo entre las zonas especificadas. |
| Política de seguridad |
Permite seleccionar el tipo de tráfico de datos que desea proteger mediante las SA de IPsec.
|
|
Perfiles |
|
|
Perfil clave |
Defina cómo los dispositivos de firewall de la serie SRX usan el perfil de clave estática para obtener las claves QKD en VPN IPsec para enviar tráfico de forma segura a través de Internet.
|
| Perfil de PPK |
Indique qué perfil de clave se debe utilizar para establecer SA de IPsec o IKE con seguridad cuántica haciendo referencia al perfil de clave en la puerta de enlace de IKE. |
| Certificados | |
| Certificado de CA | Verifique la identidad de los dispositivos y autentique el vínculo de comunicación entre ellos. |
| Certificado local | Genere PKI e inscríbase con el certificado de CA para su verificación. |
| Certificado KME | Certificado de terceros generado por el proveedor |
| Zonas de seguridad | |
| confiar |
Segmento de red en la zona de acogida |
| no confiar |
Segmento de red en la zona del servidor de destino |
| vpn |
Segmento de red a través del cual interactúan los dispositivos SRX1 y SRX2. |
|
Tareas de verificación primarias |
Verifique que las SA IKE e IPsec establecidas sean seguras para Quantum. |
Información general sobre la topología
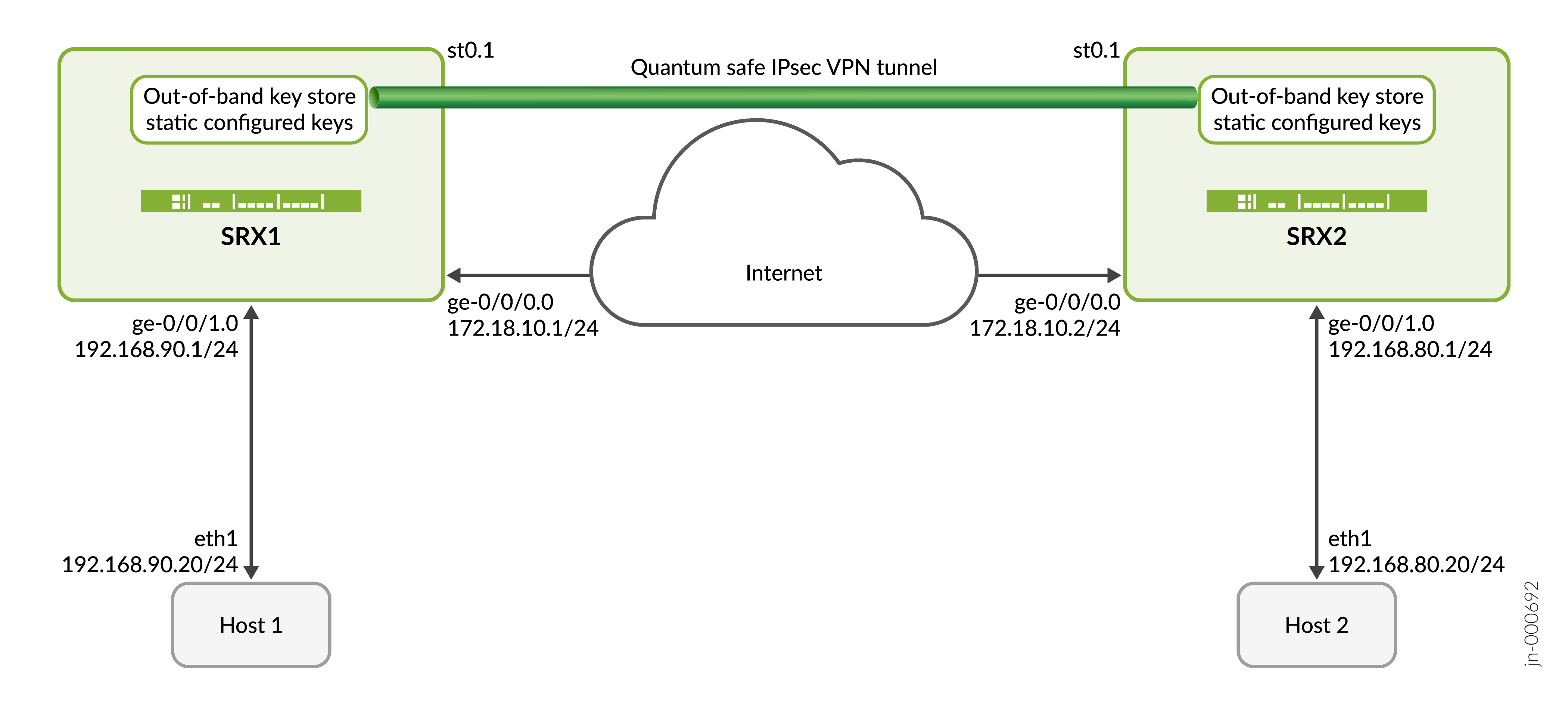
En este ejemplo, SRX1 inicia la negociación de túneles IPsec seguros cuánticamente con SRX2 mediante la clave estática configurada por la CLI. SRX2 responde a esta solicitud verificando la identidad de SRX1 junto con la clave y establece una VPN IPsec segura cuánticamente. Una vez establecido el túnel, el tráfico de datos entre Host1 y Host2 se protege mediante el túnel IPsec establecido.
|
Nombre de host |
Función |
Función |
|---|---|---|
| SRX1 |
Firewall serie SRX capaz de establecer túneles IPsec |
Inicia la negociación de IKE o IPsec SA y establece túneles IPsec de seguridad cuántica con SRX2 mediante la clave estática configurada en SRX1. |
| SRX2 | Firewall serie SRX capaz de establecer túneles IPsec | Responde a la negociación IKE o IPsec SA iniciada por SRX1 y establece túneles IPsec de seguridad cuántica mediante una clave estática configurada en SRX2. |
| Anfitrión1 | Un host dentro de la zona de confianza o lado LAN de SRX1 | Inicia el tráfico del lado del cliente hacia el Host2 |
| Anfitrión2 | Un host dentro de la zona de confianza o en el lado LAN de SRX2 | Responde al tráfico del lado del cliente desde el Host1 |
Ilustración de topología
Configuración paso a paso en dispositivos de firewall de la serie SRX
Para obtener ejemplos completos de configuraciones en el DUT, consulte:
Esta configuración solo se aplica a dispositivos SRX1 y SRX2. Debe realizar los cambios de configuración específicos del dispositivo adecuados.
-
Configure las interfaces.
[edit interfaces] user@srx# set ge-0/0/0 unit 0 family inet address 172.18.10.1/24 user@srx# set st0 unit 1 family inet user@srx# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24
-
Configure un perfil de clave de tipo estático con un identificador de clave y una clave correspondiente.
[edit security key-manager profiles] user@srx# set km_profile_1 static key-id ascii-text test-key-id user@srx# set km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
-
Configure las zonas de seguridad.
[edit security zones] user@srx# set security-zone untrust host-inbound-traffic system-services ike user@srx# set security-zone untrust interfaces ge-0/0/0.0 user@srx# set security-zone vpn interfaces st0.1 user@srx# set security-zone trust host-inbound-traffic system-services ping user@srx# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@srx# set from-zone trust to-zone vpn policy vpn_out match source-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match application any user@srx# set from-zone trust to-zone vpn policy vpn_out then permit user@srx# set from-zone vpn to-zone trust policy vpn_in match source-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match application any user@srx# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security ike proposal] user@srx# set IKE_PROP authentication-method pre-shared-keys user@srx# set IKE_PROP dh-group group14 user@srx# set IKE_PROP authentication-algorithm sha-256 user@srx# set IKE_PROP encryption-algorithm aes-256-cbc user@srx# set IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@srx# set IKE_POL proposals IKE_PROP user@srx# set IKE_POL pre-shared-key ascii-text ipsec-test
[edit security ike gateway] user@srx# set IKE_GW ike-policy IKE_POL user@srx# set IKE_GW address 172.18.10.2 user@srx# set IKE_GW external-interface ge-0/0/0.0 user@srx# set IKE_GW local-address 172.18.10.1 user@srx# set IKE_GW version v2-only user@srx# set IKE_GW ppk-profile km_profile_1
[edit security ipsec proposal] user@srx# set IPSEC_PROP protocol esp user@srx# set IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx# set IPSEC_PROP encryption-algorithm aes-256-cbc user@srx# set IPSEC_PROP lifetime-seconds 2400
[edit security ipsec policy] user@srx# set IPSEC_POL proposals IPSEC_PROP
[edit security ipsec vpn] user@srx# set IPSEC_VPN bind-interface st0.1 user@srx# set IPSEC_VPN ike gateway IKE_GW user@srx# set IPSEC_VPN ike ipsec-policy IPSEC_POL user@srx# set IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@srx# set IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 user@srx# set IPSEC_VPN establish-tunnels immediately
Verificación
En esta sección se proporciona una lista de comandos show que puede usar para comprobar la característica de este ejemplo.
|
Comando |
Tarea de verificación |
|---|---|
|
mostrar detalles de asociaciones de seguridad de IKE |
|
|
mostrar detalles de asociaciones de seguridad IPsec |
|
|
Mostrar estadísticas de seguridad IPsec |
Compruebe las estadísticas de cifrado y descifrado de IPsec. |
|
mostrar detalles de los perfiles de los administradores de claves de seguridad |
|
|
ping 192.168.80.20 fuente 192.168.90.20 recuento 4 |
- Comprobar las SA de IKE
- Comprobar las SA de IPsec
- Comprobar estadísticas de IPsec
- Verificar el perfil del administrador de claves
- Ping del HOST 1 al HOST 2
Comprobar las SA de IKE
Propósito
Verificar las SA de IKE
Acción
Desde el modo operativo, escriba el show security ike security-associations detail comando para ver las SA de IKE.
user@srx> show security ike security-associations detail IKE peer 172.18.10.2, Index 1, Gateway Name: IKE_GW
Role: Initiator, State: UP
Initiator cookie: dee592254e808a2b, Responder cookie: 51f6b1d4a8618332 Exchange type: IKEv2, Authentication method: Pre-shared-keys
Local gateway interface: ge-0/0/2.0 Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 1286 seconds Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576 SRG ID: 0
Remote Access Client Info: Unknown Client Peer ike-id: 172.18.10.2
AAA assigned IP: 0.0.0.0
PPK-profile: km_profile_1 Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc Pseudo random function: hmac-sha256 Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 1058
Output bytes : 1074
Input packets: 4
Output packets: 4
Input fragmented packets: 0
Output fragmented packets: 0
IPSec security associations: 4 created, 1 deleted Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500002
Negotiation type: Quick mode, Role: Initiator, Message ID: 0 Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: 172.18.10.1
Remote identity: 172.18.10.2 Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 1
Response In : 0 Response Out : 1
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0 Res Verify SA Fail : 0
Res Verify DH Group Fail: 0 Res Verify TS Fail : 0
Significado
Los Role: Initiator, State: UPcampos , PPK-profile: km_profile_1 Optional: No, IPSec security associations: 4 createdy Flags: IKE SA is created muestran que las SA de IKE se crearon correctamente.
Comprobar las SA de IPsec
Propósito
Compruebe las SA de IPsec
Acción
Desde el modo operativo, escriba el show security ipsec security-associations detail comando para ver las SA de IPsec.
user@srx> show security ipsec security-associations detail ID: 500002 Virtual-system: root, VPN Name: IPSEC_VPN Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2 Traffic Selector Name: ts1 Local Identity: ipv4(192.168.90.0-192.168.90.255) Remote Identity: ipv4(192.168.80.0-192.168.80.255) TS Type: traffic-selector Version: IKEv2 Quantum Secured: Yes PFS group: N/A SRG ID: 0 DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: IPSEC_POL Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0 Multi-sa, Configured SAs# 0, Negotiated SAs#: 0 Tunnel events: Thu Mar 30 2023 23:43:42: IPsec SA negotiation succeeds (1 times) Location: FPC 0, PIC 0, KMD-Instance 0 Anchorship: Thread 1 Distribution-Profile: default-profile Direction: inbound, SPI: 0x983a0221, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1330 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 662 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1 Direction: outbound, SPI: 0x4112746b, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1330 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 662 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1
Significado
Los Version: IKEv2 Quantum Secured: Yes campos y tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1 muestran que las SA IPsec se crearon correctamente.
La salida de ejemplo confirma las SA de IPsec.
Comprobar estadísticas de IPsec
Propósito
Compruebe las estadísticas de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec statistics comando para ver las estadísticas de IPsec.
user@srx> show security ipsec statistics ESP Statistics: Encrypted bytes: 624 Decrypted bytes: 624 Encrypted packets: 4 Decrypted packets: 4 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Los ESP Statistics campos y AH Statistics muestran las estadísticas de IPsec.
Verificar el perfil del administrador de claves
Propósito
Compruebe el perfil del administrador de claves.
Acción
Desde el modo operativo, introduzca los show security key-manager profiles detalles para ver el perfil del administrador de claves.
user@srx> show security key-manager profiles detail Name: km_profile_1, Index: 1, Type: Static Configured-at: 30.03.23 (23:22:43) Time-elapsed: 1 hrs 16 mins 3 secs Request stats: Received: 1 In-progress: 0 Success: 1 Failed: 0
Significado
Los Name: km_profile_1 campos y Type: Static muestran el perfil del administrador de claves.
Ping del HOST 1 al HOST 2
Propósito
Compruebe la conectividad del HOST 1 al HOST 2.
Acción
Desde el modo operativo, ingrese el ping 192.168.80.20 source 192.168.90.20 count 4 para ver la conectividad desde el HOST 1 al HOST 2.
user@HOST1# ping 192.168.80.20 source 192.168.90.20 count 4 PING 192.168.80.20 (192.168.80.20): 56 data bytes 64 bytes from 192.168.80.1: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.80.1: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.80.1: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.80.1: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.80.1 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
El PING 192.168.80.20 (192.168.80.20): 56 data bytes confirma la conectividad del HOST 1 al HOST 2.
Apéndice 1: Establecer comandos en todos los dispositivos
Establezca la salida del comando en todos los dispositivos.
Establecer comandos en SRX1
set security key-manager profiles km_profile_1 static key-id ascii-text test-key-id set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.1/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.2 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.1 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Establecer comandos en SRX2
set security key-manager profiles km_profile_1 static key-id ascii-text test-key-id set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.2/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text “ipsec-test” set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.1 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.2 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Apéndice 2: Mostrar salida de configuración en DUT
SRX1
Desde el modo de configuración, escriba los comandos , , , show security zonesshow security ike gateway IKE_GWshow security ipsec policy IPSEC_POLshow security ipsec vpn IPSEC_VPNshow security ike proposal IKE_PROPshow security ipsec proposal IPSEC_PROPshow security policiesshow security ike policy IKE_POLshow interfacesshow security key-managershow security key-manager profiles Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@srx1# show security key-manager profiles
km_profile_1 {
static {
key-id ascii-text "$9$.mz6pu1hyKBI8X-boajHqmF/hcylK836"; ## SECRET-DATA
key ascii-text "$9$5Q6AhclXNbtuIcyeXxGDikfT369A0Bn/vWLNY2aZUjPQAp0BEcFnyleMXxGDi.mT9CuhSeIElMLXwsaZUikPpu1hSen/eW8XbwJGD"; ## SECRET-DATA
}
}
user@srx1# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$.mz6pu1hyKBI8X-boajHqmF/hcylK836"; ## SECRET-DATA
key ascii-text "$9$5Q6AhclXNbtuIcyeXxGDikfT369A0Bn/vWLNY2aZUjPQAp0BEcFnyleMXxGDi.mT9CuhSeIElMLXwsaZUikPpu1hSen/eW8XbwJGD"; ## SECRET-DATA
}
}
}
user@srx1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.2/24;
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.80.1/24;
address 192.168.90.1/24;
}
family mpls;
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}
user@srx1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
user@srx1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
user@srx1# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx1# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$z0C63/tp0Icrvz39p0Ihcs24aZjqmTn9p"; ## SECRET-DATA
user@srx1# show security ike gateway IKE_GW ike-policy IKE_POL; address [ 172.18.10.1 172.18.10.2 ]; external-interface ge-0/0/0.0; local-address 172.18.10.1; version v2-only; ppk-profile km_profile_1;
user@srx1# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srx1# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srx1# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 192.168.80.0/24;
}
establish-tunnels immediately;
SRX2
Desde el modo de configuración, escriba los comandos , , , show security zonesshow security ike gateway IKE_GWshow security ipsec policy IPSEC_POLshow security ipsec vpn IPSEC_VPNshow security ike proposal IKE_PROPshow security ipsec proposal IPSEC_PROPshow security policiesshow security ike policy IKE_POLshow interfacesshow security key-managershow security key-manager profiles Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@srx2# show security key-manager profiles
km_profile_1 {
static {
key-id ascii-text "$9$Hk5FCA0IhruOvWx-2gGDikT3IRhSrvQF"; ## SECRET-DATA
key ascii-text "$9$zDD33CuyrvNVY0BhreMN-jHqmQF/Ctu1R9A8X7V4oGDikT3uO1RSr69evMLN-jHqf5FtpBylMhSvL7N2gGDiqmTOBEylM9AMXxNY2UjH"; ## SECRET-DATA
}
}user@srx2# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$Hk5FCA0IhruOvWx-2gGDikT3IRhSrvQF"; ## SECRET-DATA
key ascii-text "$9$zDD33CuyrvNVY0BhreMN-jHqmQF/Ctu1R9A8X7V4oGDikT3uO1RSr69evMLN-jHqf5FtpBylMhSvL7N2gGDiqmTOBEylM9AMXxNY2UjH"; ## SECRET-DATA
}
}
}user@srx2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}user@srx2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srx2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srx2# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx2# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$zTi03/tp0Icrvz39p0Ihcs24aZjqmTn9p"; ## SECRET-DATA
user@srx2# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.1; external-interface ge-0/0/0.0; local-address 172.18.10.2; version v2-only; ppk-profile km_profile_1;
user@srx2# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srx2# show security ipsec policy IPSEC_POL
proposals IPSEC_PROP;
[edit]
user@srx2# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}
establish-tunnels immediately;
Ejemplo: Configurar el perfil de claves estáticas para AutoVPN
Utilice este ejemplo de configuración para proteger una infraestructura AutoVPN IPsec configurando el perfil de clave estática.
Puede proteger una infraestructura AutoVPN IPsec configurando el perfil de clave estática.
En este ejemplo de configuración, el Hub, Spoke 1 y Spoke 2 usan perfiles de clave estática para obtener las claves QKD en VPN IPsec. Las teclas QKD ayudan a enviar tráfico de forma segura a través de Internet.
|
Tiempo de lectura |
Menos de una hora |
|
Tiempo de configuración |
Menos de una hora |
- Ejemplo de requisitos previos
- Antes de empezar
- Descripción general funcional
- Información general sobre la topología
- Ilustración de topología
- Configuración paso a paso en el hub
- Configuración paso a paso en dispositivos radiales
- Verificación
- Apéndice 1: Establecer comandos en todos los dispositivos
- Apéndice 2: Mostrar salida de configuración en DUT
Ejemplo de requisitos previos
|
Requisitos de hardware |
|
|
Requisitos de software |
Junos OS versión 22.4R1 o posterior. |
Antes de empezar
|
Ventajas |
|
|
Recursos útiles |
|
|
Saber más |
|
|
Experiencia práctica |
|
|
Seguir leyendo |
Obtenga la dirección de la autoridad de certificación (CA) y la información que necesitan (como la contraseña de desafío) y, a continuación, envíe solicitudes de certificados locales. Consulte Descripción de las solicitudes de certificados locales. Inscribir los certificados digitales en cada dispositivo. Consulte Ejemplo: Cargar certificados locales y de CA manualmente. |
Descripción general funcional
| VPN IPSec |
Implementa una topología VPN IPsec radial donde los radios están conectados por túneles VPN que envían tráfico a través del concentrador. Estos túneles VPN se configuran posteriormente para usar claves cuánticas, lo que los convierte en túneles VPN de seguridad cuántica. |
| Puerta de enlace IKE |
Establece una conexión segura, la puerta de enlace de IKE utiliza la política de IKE para limitarse al grupo configurado de CA (ca-profiles) mientras valida el certificado. |
| Propuestas | |
| Propuesta de IKE |
Define los algoritmos y las claves utilizados para establecer la conexión IKE segura con la puerta de enlace de seguridad del mismo nivel. IKE crea las SA dinámicas y las negocia para IPsec. |
| Propuesta IPsec |
Enumera los protocolos, algoritmos y servicios de seguridad que se negociarán con el par IPsec remoto. |
| Políticas | |
| Política de IKE |
Define una combinación de parámetros de seguridad (propuestas de IKE) que se utilizarán durante la negociación de IKE. |
| Directiva IPsec |
Contiene reglas y políticas de seguridad para permitir el tráfico VPN de grupo entre las zonas especificadas. |
| Política de seguridad |
Permite seleccionar el tipo de tráfico de datos que desea proteger mediante las SA de IPsec.
|
|
Perfiles |
|
|
Perfil clave |
Defina cómo los dispositivos de firewall de la serie SRX se comunican con los dispositivos KME para recuperar claves QKD del servidor KME externo. Los perfiles clave se configuran en el concentrador (HUB_KM_PROFILE_1) y en los radios (SPOKE_1_KM_PROFILE_1 y SPOKE_2_KM_PROFILE_1) por separado.
|
| Perfil de PPK |
Indica qué perfil de clave se debe usar para establecer SA de IPsec o IKE con seguridad cuántica haciendo referencia al perfil de clave en la puerta de enlace de IKE. |
| Certificados | |
| Certificado de CA | Verifica la identidad de los dispositivos y autentica el vínculo de comunicación entre ellos. |
| Certificado local | Genera PKI y la inscribe con el certificado de CA para su verificación. |
| Certificado KME | Certificado de terceros generado por el proveedor. |
| Zonas de seguridad | |
| confiar |
Segmento de red en la zona de host. |
| no confiar |
Segmento de red en la zona del servidor de destino. |
| vpn |
Segmento de red a través del cual interactúa el hub-and-spoke. |
|
Tareas de verificación primarias |
Verifique que las SA IKE e IPsec establecidas sean seguras para Quantum. |
Información general sobre la topología
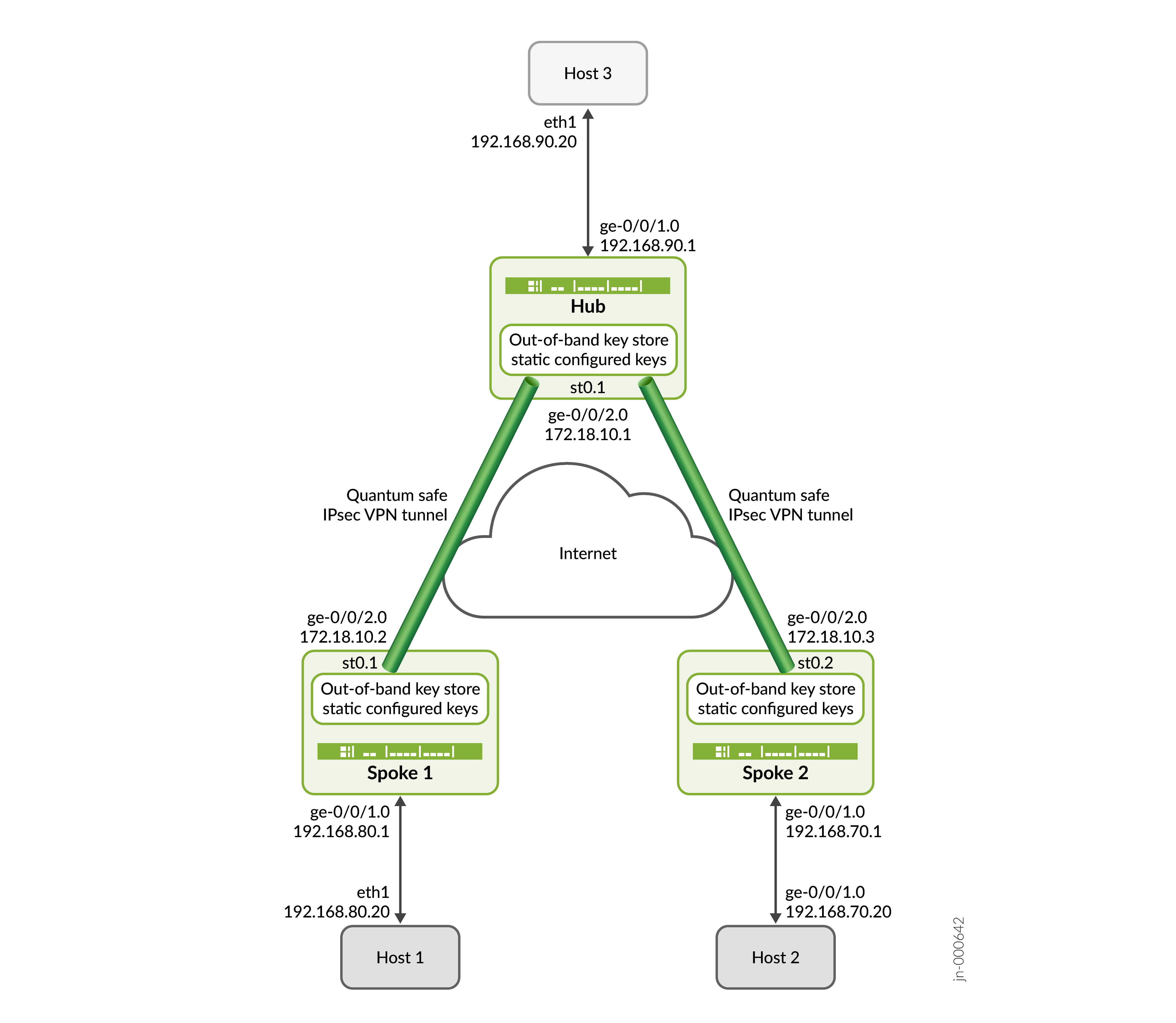
En este ejemplo, SPOKE 1 y SPOKE 2 inician la negociación de túneles IPsec de seguridad cuántica con el concentrador mediante una clave estática configurada por la CLI. El Hub responde a las solicitudes verificando la identidad de Spoke 1 y Spoke 2 junto con sus respectivas claves y establece una VPN IPsec de seguridad cuántica con ambos radios. Una vez establecidos los túneles, el tráfico de datos entre el host 1 y el host 3, y entre el host 2 y el host 3, se protege mediante los túneles IPsec establecidos.
|
Nombre de host |
Función |
Función |
|---|---|---|
| Concentrador | Firewall serie SRX capaz de establecer túneles IPsec | Responde a la negociación IKE o IPsec SA iniciada por SPOKE 1 y SPOKE 2 y establece túneles IPsec de seguridad cuántica mediante una clave estática configurada en el dispositivo Hub. |
| Habló 1 | Firewall serie SRX capaz de establecer túneles IPsec | Inicia la negociación de SA de IKE/IPsec y establece túneles IPsec de seguridad cuántica con el concentrador mediante una clave estática configurada en el radio 1. |
| Habló 2 | Firewall serie SRX capaz de establecer túneles IPsec | Inicia la negociación IKE o IPsec SA y establece túneles IPsec de seguridad cuántica con el concentrador mediante una clave estática configurada en el radio 2. |
| Anfitrión 1 | Host dentro de la zona de confianza o lado LAN de Spoke 1 | Inicia el tráfico del lado del cliente hacia el host 3. |
| Anfitrión 2 | Host dentro de la zona de confianza o en el lado LAN de Spoke 2 | Inicia el tráfico del lado del cliente hacia el host 3. |
| Anfitrión 3 | Host dentro de la zona de confianza o en el lado LAN de HUB | Responde al tráfico del lado del cliente desde el host 1 y el host 2. |
Ilustración de topología
Configuración paso a paso en el hub
Para obtener ejemplos completos de configuraciones en el DUT, consulte:
Esta configuración solo se aplica a los dispositivos Hub. Debe realizar los cambios de configuración específicos del dispositivo adecuados.
-
Configure las interfaces del concentrador.
[edit interfaces] user@hub# set ge-0/0/2 unit 0 family inet address 172.18.10.1/24 user@hub# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24 user@hub# set st0 unit 1 family inet
-
Configure el perfil de CA y el certificado de CA.
[edit security pki] user@hub# set ca-profile Root-CA ca-identity Root-CA user@hub# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@hub# set ca-profile Root-CA revocation-check disable
-
Desde el modo operativo, vincule el certificado de CA al perfil de CA.
user@hub> request security pki ca-certificate enroll ca-profile Root-CA user@hub> request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa user@hub> request security pki local-certificate enroll certificate-id HUB_CRT challenge-password <different> domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA
-
Configure el perfil del administrador de claves estáticas.
[edit security key-manager profiles] user@hub# set HUB_KM_PROFILE_1 static key-id ascii-text test-key-id user@hub# set HUB_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
Configure el radio concentrador en la VPN IPsec. Esto incluye la configuración de las zonas de seguridad, las políticas de seguridad y los certificados relevantes para autenticar las identidades de los dispositivos y sus vínculos de comunicación.
[edit security ike proposal] user@hub# set HUB_IKE_PROP authentication-method rsa-signatures user@hub# set HUB_IKE_PROP dh-group group14 user@hub# set HUB_IKE_PROP authentication-algorithm sha-256 user@hub# set HUB_IKE_PROP encryption-algorithm aes-256-cbc user@hub# set HUB_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@hub# set HUB_IKE_POL proposals HUB_IKE_PROP user@hub# set HUB_IKE_POL certificate local-certificate HUB_CRT
[edit security ike gateway] user@hub# set HUB_IKE_GW local-address 172.18.10.1 user@hub# set HUB_IKE_GW ike-policy HUB_IKE_POL user@hub# set HUB_IKE_GW external-interface ge-0/0/2.0 user@hub# set HUB_IKE_GW local-identity distinguished-name user@hub# set HUB_IKE_GW dynamic ike-user-type group-ike-id user@hub# set HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper user@hub# set HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 user@hub# set HUB_IKE_GW version v2-only
[edit security ipsec proposal] user@hub# set HUB_IPSEC_PROP protocol esp user@hub# set HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@hub# set HUB_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec policy] user@hub# set HUB_IPSEC_POL proposals HUB_IPSEC_PROP
[edit security ipsec vpn] user@hub# set HUB_IPSEC_VPN bind-interface st0.1 user@hub# set HUB_IPSEC_VPN ike gateway HUB_IKE_GW user@hub# set HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL user@hub# set HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@hub# set HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0
[edit security zones] user@hub# set security-zone untrust host-inbound-traffic system-services ike user@hub# set security-zone untrust interfaces ge-0/0/2.0 user@hub# set security-zone vpn interfaces st0.1 user@hub# set security-zone trust host-inbound-traffic system-services ping user@hub# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@hub# set from-zone trust to-zone vpn policy vpn_out match source-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match application any user@hub# set from-zone trust to-zone vpn policy vpn_out then permit user@hub# set from-zone vpn to-zone trust policy vpn_in match source-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match application any user@hub# set from-zone vpn to-zone trust policy vpn_in then permit
Configuración paso a paso en dispositivos radiales
Para obtener ejemplos completos de configuraciones en el DUT, consulte:
Esta configuración es aplicable para dispositivos Spoke 1 y Spoke 2. Para otros dispositivos, debe realizar los cambios de configuración específicos del dispositivo.
-
Configure las interfaces radiales.
[edit interfaces] user@spoke# set ge-0/0/2 unit 0 family inet address 172.18.10.2/24 user@spoke# set ge-0/0/1 unit 0 family inet address 192.168.80.1/24 user@spoke# set st0 unit 1 family inet
-
Configure hub-spoke en la VPN IPsec. Esto incluye la configuración de las zonas de seguridad, las políticas de seguridad y los certificados relevantes para autenticar las identidades de los dispositivos y sus vínculos de comunicación.
[edit security ike proposal] user@spoke# set SPOKE_1_IKE_PROP authentication-method rsa-signatures user@spoke# set SPOKE_1_IKE_PROP dh-group group14 user@spoke# set SPOKE_1_IKE_PROP authentication-algorithm sha-256 user@spoke# set SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc user@spoke# set SPOKE_1_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@spoke# set SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP user@spoke# set SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW address 172.18.10.1 user@spoke# set SPOKE_1_IKE_GW local-address 172.18.10.2 user@spoke# set SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL user@spoke# set SPOKE_1_IKE_GW external-interface ge-0/0/2.0 user@spoke# set SPOKE_1_IKE_GW local-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW remote-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 user@spoke# set SPOKE_1_IKE_GW version v2-only
[edit security ipsec proposal] user@spoke# set SPOKE_1_IPSEC_PROP protocol esp user@spoke# set SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@spoke# set SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec policy] user@spoke# set SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP
[edit security ipsec vpn] user@spoke# set SPOKE_1_IPSEC_VPN bind-interface st0.1 user@spoke# set SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW user@spoke# set SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24
[edit security zones] user@spoke# set security-zone untrust host-inbound-traffic system-services ike user@spoke# set security-zone untrust interfaces ge-0/0/2.0 user@spoke# set security-zone vpn interfaces st0.1 user@spoke# set security-zone trust host-inbound-traffic system-services ping user@spoke# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@spoke# set from-zone trust to-zone vpn policy vpn_out match source-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match application any user@spoke# set from-zone trust to-zone vpn policy vpn_out then permit user@spoke# set from-zone vpn to-zone trust policy vpn_in match source-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match application any user@spoke# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki ] user@spoke# set ca-profile Root-CA ca-identity Root-CA user@spoke# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@spoke# set ca-profile Root-CA revocation-check disable
user@spoke> request security pki ca-certificate enroll ca-profile Root-CA user@spoke> request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa user@spoke> request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <different> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA
-
Configure el perfil del administrador de claves estáticas.
[edit security key-manager profiles] user@spoke# set SPOKE_1_KM_PROFILE_1 static key-id ascii-text test-key-id user@spoke# set SPOKE_1_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
Verificación
En esta sección se proporciona una lista de comandos show que puede usar para comprobar la característica de este ejemplo.
| Comando | Tarea de verificación |
|---|---|
|
mostrar detalles de asociaciones de seguridad de IKE |
|
|
mostrar detalles de asociaciones de seguridad IPsec |
|
|
Mostrar estadísticas de seguridad IPsec |
PropósitoCompruebe las estadísticas de cifrado y descifrado de IPsec. |
|
mostrar detalles de los perfiles de los administradores de claves de seguridad |
|
|
ping 192.168.90.20 fuente 192.168.80.20 recuento 4 |
- Comprobar las SA de IKE
- Comprobar las SA de IPsec
- Comprobar estadísticas de IPsec
- Verificar el perfil del administrador de claves
- Ping del host 1 al host 3 o viceversa
- Ping del host 2 al host 3 o viceversa
Comprobar las SA de IKE
Propósito
Compruebe las SA de IKE.
Acción
Desde el modo operativo, escriba el show security ike security-associations detail comando para ver las SA de IKE.
user@hub> show security ike security-associations detail
IKE peer 172.18.10.2, Index 2123, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 0e40ccdcee1b54bd, Responder cookie: 43964f5cc4d4491c
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 2840 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2610
Output bytes : 2571
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500440
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
IKE peer 172.18.10.3, Index 2124, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 651bf4a52a9375ec, Responder cookie: d9a9c95c27e3f929
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Lifetime: Expires in 2901 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2610
Output bytes : 2571
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500441
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
Significado
Los Role: Responder, State: UPcampos , PPK-profile: HUB_KM_PROFILE_1, IPSec security associations: 2 created, 0 deletedy Flags: IKE SA is created muestran que las SA de IKE se crearon correctamente.
Comprobar las SA de IPsec
Propósito
Compruebe las SA de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec security-associations detail comando para ver las SA de IPsec.
user@hub> show security ipsec security-associations detail
ID: 500440 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.80.0-192.168.80.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Thu Jul 20 2023 10:44:19: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x649d371f, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2840 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2183 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2123
Direction: outbound, SPI: 0xd5ef611e, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2840 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2183 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2123
ID: 500441 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.3
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.70.0-192.168.70.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Thu Jul 20 2023 10:45:19: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0xa0d3ba32, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2901 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2258 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2124
Direction: outbound, SPI: 0xe54414e3, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2901 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2258 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2124
Significado
Los Quantum Secured: Yescampos , Passive mode tunneling: Disabled, Policy-name: HUB_IPSEC_POLy IPsec SA negotiation succeeds (1 times) muestran que las SA de IPsec se crearon correctamente.
Comprobar estadísticas de IPsec
Propósito
Compruebe las estadísticas de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec statistics comando para ver las estadísticas de IPsec.
user@hub> show security ipsec statistics ESP Statistics: Encrypted bytes: 1248 Decrypted bytes: 1248 Encrypted packets: 8 Decrypted packets: 8 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Los ESP Statistics campos y AH Statistics muestran las estadísticas de IPsec.
Verificar el perfil del administrador de claves
Propósito
Compruebe el perfil del administrador de claves.
Acción
Desde el modo operativo, escriba el show security key-manager profiles detail comando para ver el perfil del administrador de claves.
user@hub> show security key-manager profiles detail
Name: HUB_KM_PROFILE_1, Index: 4, Type: Static
Configured-at: 20.07.23 (09:59:06)
Time-elapsed: 1 hrs 2 mins 7 secs
Request stats:
Received: 2
In-progress: 0
Success: 2
Failed: 0Significado
Los Name: HUB_KM_PROFILE_1 campos y Type: Static muestran el perfil del administrador clave
Ping del host 1 al host 3 o viceversa
Propósito
Compruebe la conectividad del host 1 al host 3.
Acción
Desde el modo operativo, escriba el ping 192.168.90.20 source 192.168.80.20 count 4 comando para ver la conectividad del host 1 al host 3.
user@HOST1# ping 192.168.90.20 source 192.168.80.20 count 4 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.90.20 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
El PING 192.168.80.20 (192.168.80.20): 56 data bytes confirma la conectividad del HOST 1 al HOST 3.
Ping del host 2 al host 3 o viceversa
Propósito
Compruebe la conectividad del host 2 al host 3.
Acción
Desde el modo operativo, ingrese el ping 192.168.90.20 source 192.168.80.20 count 4 para ver la conectividad del host 2 al host 3.
user@HOST1# ping 192.168.90.20 source 192.168.70.20 count 4 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.90.20 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
El PING 192.168.80.20 (192.168.80.20): 56 data bytes confirma la conectividad del HOST 2 al HOST 3.
Apéndice 1: Establecer comandos en todos los dispositivos
Establezca la salida del comando en todos los dispositivos.
Establecer comandos en el hub
set security ike proposal HUB_IKE_PROP dh-group group14 set security ike proposal HUB_IKE_PROP authentication-algorithm sha-256 set security ike proposal HUB_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal HUB_IKE_PROP lifetime-seconds 3600 set security ike policy HUB_IKE_POL proposals HUB_IKE_PROP set security ike policy HUB_IKE_POL certificate local-certificate HUB_CRT set security ike gateway HUB_IKE_GW local-address 172.18.10.1 set security ike gateway HUB_IKE_GW ike-policy HUB_IKE_POL set security ike gateway HUB_IKE_GW external-interface ge-0/0/2.0 set security ike gateway HUB_IKE_GW local-identity distinguished-name set security ike gateway HUB_IKE_GW dynamic ike-user-type group-ike-id set security ike gateway HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper set security ike gateway HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 set security ike gateway HUB_IKE_GW version v2-only set security ipsec proposal HUB_IPSEC_PROP protocol esp set security ipsec proposal HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal HUB_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP set security ipsec vpn HUB_IPSEC_VPN bind-interface st0.1 set security ipsec vpn HUB_IPSEC_VPN ike gateway HUB_IKE_GW set security ipsec vpn HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.1/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Establecer comandos en el radio 1
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <different> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA set security key-manager profiles SPOKE_1_KM_PROFILE_1 static key-id ascii-text test-key-id set security key-manager profiles SPOKE_1_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_1_IKE_PROP dh-group group14 set security ike proposal SPOKE_1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_1_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP set security ike policy SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT set security ike gateway SPOKE_1_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_1_IKE_GW local-address 172.18.10.2 set security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL set security ike gateway SPOKE_1_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_1_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 set security ike gateway SPOKE_1_IKE_GW version v2-only set security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP set security ipsec vpn SPOKE_1_IPSEC_VPN bind-interface st0.1 set security ipsec vpn SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW set security ipsec vpn SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.2/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Establecer comandos en Spoke 2
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_2_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_2_CRT challenge-password <different> domain-name spoke_2.juniper.net email spoke_2@juniper.net subject DC=juniper,CN=spoke_2.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA set security key-manager profiles SPOKE_2_KM_PROFILE_1 static key-id ascii-text test-key-id set security key-manager profiles SPOKE_2_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_2_IKE_PROP dh-group group14 set security ike proposal SPOKE_2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_2_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_2_IKE_POL proposals SPOKE_IKE_PROP set security ike policy SPOKE_2_IKE_POL certificate local-certificate SPOKE_2_CRT set security ike gateway SPOKE_2_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_2_IKE_GW local-address 172.18.10.3 set security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL set security ike gateway SPOKE_2_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_2_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW ppk-profile SPOKE_2_KM_PROFILE_1 set security ike gateway SPOKE_2_IKE_GW version v2-only set security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_2_IPSEC_POL proposals SPOKE_2_IPSEC_PROP set security ipsec vpn SPOKE_2_IPSEC_VPN bind-interface st0.2 set security ipsec vpn SPOKE_2_IPSEC_VPN ike gateway SPOKE_2_IKE_GW set security ipsec vpn SPOKE_2_IPSEC_VPN ike ipsec-policy SPOKE_2_IPSEC_POL set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 local-ip 192.168.70.0/24 set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.3/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.70.1/24 set interfaces st0 unit 2 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.2 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Apéndice 2: Mostrar salida de configuración en DUT
Concentrador
Desde el modo de configuración, confirme la configuración introduciendo los show security ike proposal HUB_IKE_PROPcomandos , show security ike policy HUB_IKE_POL, show security ike gateway HUB_IKE_GW, show security zonesshow security ipsec vpn HUB_IPSEC_VPNshow interfacesshow security ipsec proposal HUB_IPSEC_PROPshow security ipsec policy HUB_IPSEC_POLy .show security policies Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@hub# show security ike proposal HUB_IKE_PROP dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@hub# show security ike policy HUB_IKE_POL
proposals HUB_IKE_PROP;
certificate {
local-certificate HUB_CRT;user@hub# show security ike gateway HUB_IKE_GW
ike-policy HUB_IKE_POL;
dynamic {
distinguished-name {
wildcard C=us,DC=juniper;
}
ike-user-type group-ike-id;
}
local-identity distinguished-name;
external-interface ge-0/0/2.0;
local-address 172.18.10.1;
version v2-only;
ppk-profile HUB_KM_PROFILE_1;user@hub# show security ipsec proposal HUB_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@hub# show security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP;
user@hub# show security ipsec vpn HUB_IPSEC_VPN
bind-interface st0.1;
ike {
gateway HUB_IKE_GW;
ipsec-policy HUB_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 0.0.0.0/0;
}user@hub# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}user@hub# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
user@hub# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}Habló 1
Desde el modo de configuración, escriba los comandos , , , show security ike policy SPOKE_1_IKE_POLshow security ipsec vpn SPOKE_1_IPSEC_VPNshow interfacesshow security policiesshow security pkishow security ipsec proposal SPOKE_1_IPSEC_PROPshow security zonesshow security ike gateway SPOKE_1_IKE_GWshow security ipsec policy SPOKE_1_IPSEC_POLshow security ike proposal SPOKE_1_IKE_PROPshow security key-manager profiles SPOKE_1_KM_PROFILE_1show security pki ca-profile Root-CA Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@spoke1# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
user@spoke1# show security key-manager profiles SPOKE_1_KM_PROFILE_1
static {
key-id ascii-text "$9$cJ5SvLdVYoZjs2qmTFAt1RhSMXoaZUjqWL"; ## SECRET-DATA
key ascii-text "$9$mfF/IRSWX-9AORhyW8aZUj.PQFn/tuz3lKMXbwgoJGqf/Ctu1RTzhSyeW8aZUHkPn6AIEyO1SeMWdVgoJUjqCA0IEyz3yKvW-d4aZ"; ## SECRET-DATA
}
user@spoke1# show security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke1# show security ike policy SPOKE_1_IKE_POL
proposals SPOKE_1_IKE_PROP;
certificate {
local-certificate SPOKE_1_CRT;
}
user@spoke1# show security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.2; version v2-only; ppk-profile SPOKE_1_KM_PROFILE_1;
user@spoke1# show security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke1# show security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP;
user@spoke1# show security ipsec vpn SPOKE_1_IPSEC_VPN
bind-interface st0.1;
ike {
gateway SPOKE_1_IKE_GW;
ipsec-policy SPOKE_1_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}user@spoke1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}
user@spoke1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@spoke1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
user@spoke1# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
}Habló 2
Desde el modo de configuración, escriba los show security pkicomandos , show security key-manager, show security ike proposal SPOKE_2_IKE_PROP, , show interfacesshow security policiesshow security ike gateway SPOKE_2_IKE_GWshow security ipsec proposal SPOKE_2_IPSEC_PROPshow security ipsec vpn SPOKE_2_IPSEC_VPNshow security zonesshow security ike policy SPOKE_2_IKE_POL Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@spoke2# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
}
user@spoke2# show security key-manager
profiles {
SPOKE_2_KM_PROFILE_1 {
static {
key-id ascii-text "$9$C4Y8ABEleWx-wM8goGjPf369A1hx7-VwgIE"; ## SECRET-DATA
key ascii-text "$9$15SRyKdVYGjqvW7Vw2GUn/CtBIcylK8XSr4aZjPfz369ORKM8X-VhSwY2oGUn/Cu0IleWdb27-YoZG.mz36CtOMWxdb2Sr2aJGq.Fn/"; ## SECRET-DATA
}
}
}
user@spoke2# show security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke2# show security ike policy SPOKE_2_IKE_POL
proposals SPOKE_IKE_PROP;
certificate {
local-certificate SPOKE_2_CRT;
}
user@spoke2# show security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.3; version v2-only; ppk-profile SPOKE_2_KM_PROFILE_1;
user@spoke2# show security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke2# show security ipsec vpn SPOKE_2_IPSEC_VPN
bind-interface st0.2;
ike {
gateway SPOKE_2_IKE_GW;
ipsec-policy SPOKE_2_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.70.0/24;
remote-ip 192.168.90.0/24;
}user@spoke2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@spoke2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.2;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@spoke2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}Configurar el perfil de clave de Quantum Key Manager para Junos Key Manager
En este ejemplo, se muestra cómo configurar el perfil de clave cuántica para el administrador de claves de Junos. Configure el perfil de clave del administrador de claves cuánticas para generar y enviar las claves generadas para establecer un túnel VPN IPsec seguro para cuántica.
Requisitos
-
Requisitos de hardware: firewall de Juniper Networks® SRX1500 y modelos de dispositivos numerados superiores o firewall virtual vSRX de Juniper Networks® (vSRX3.0).
-
Requisitos de software: versión 22.4R1 o posterior de Junos OS con JUNOS ike y JUNOS Key Manager paquetes.
-
Utilice cualquier dispositivo QKD compatible con el estándar ETSI Quantum Key Distribution (QKD) Rest API para la comunicación.
-
Cargue los certificados locales en el dispositivo. Le recomendamos que proporcione una ruta completa al certificado.
Descripción general
Los dispositivos de firewall de la serie SRX utilizan la VPN IPsec para enviar tráfico de forma segura a través de Internet. Configure el perfil de clave del administrador de claves cuánticas en la VPN IPsec para volver a autenticar la SA de IKE existente y una nueva clave y clave.
El perfil de clave del administrador de claves cuánticas utiliza un método de distribución segura de claves basado en QKD para generar y distribuir claves que son seguras desde el punto de vista cuántico. Estas claves son dinámicas.
Configuración
-
Configure el certificado de CA.
user@host# set security pki ca-profile Root-CA ca-identity Root-CA user@host# set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@host# set security pki ca-profile Root-CA revocation-check disable
-
Cargue el certificado de CA.
user@host> request security pki local-certificate load certificate-id SAE_A filename SAE_A.cert key SAE_A.key
-
Inscriba el certificado de CA.
user@host> request security pki ca-certificate enroll ca-profile Root-CA
-
Configure el perfil del administrador de claves cuánticas.
user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager url https://kme.juniper.net user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager local-sae-id SAE_A user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_A_CERT user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
Verificación
Propósito
Compruebe el perfil y las claves de Quantum Key Manager.
Acción
Desde el modo operativo, escriba el show security pki ca-certificate ca-profile Root-CA para ver el perfil de CA y los certificados de CA.
user@host> show security pki ca-certificate ca-profile Root-CA
LSYS: root-logical-system
CA profile: Root-CA
Certificate identifier: Root-CA
Issued to: Root-CA, Issued by: C = IN, ST = WestBengal, O = JuniperNetworks, CN = Root-CA
Validity:
Not before: 09-11-2023 09:03 UTC
Not after: 03-24-2044 09:03 UTC
Public key algorithm: rsaEncryption(4096 bits)
Keypair Location: Keypair generated locallyDesde el modo operativo, escriba el show security pki local-certificate certificate-id SAE_A_CERT para ver los certificados locales de PKI.
user@host> show security pki local-certificate certificate-id SAE_A_CERT
LSYS: root-logical-system
Certificate identifier: SAE_A_CERT
Issued to: SAE_A, Issued by: C = IN, ST = WestBengal, O = JuniperNetworks, CN = ROOT_CA
Validity:
Not before: 08-28-2023 04:54 UTC
Not after: 03-10-2044 04:54 UTC
Public key algorithm: rsaEncryption(2048 bits)
Keypair Location: Keypair generated locallyDesde el modo operativo, escriba el perfil y las claves del request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B administrador de claves del dispositivo par para ver.
user@host> request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B
- Response:
- Status: SUCCESS
- Name: km_profile_1
- Type: quantum-key-manager
- Key-size: 256 bits
- Key-count: 1
- Key-ids:
- 002420bd-7a03-4725-9c41-6969d8e1815a
- Keys:
- 728d21c4a05fe2f73c7b2f58d1e3631dc68fcfaca16be12ca3fc7715079db0f9Desde el modo operativo, ingrese el para ver los detalles del show security key-manager profiles name KM_PROFILE_1 detail perfil del administrador de claves.
user@host> show security key-manager profiles name KM_PROFILE_1 detail
Name: KM_PROFILE_1, Index: 2, Type: quantum-key-manager
Configured-at: 11.09.23 (02:04:32)
Time-elapsed: 0 hrs 20 mins 23 secs
Url: https://kme.juniper.net
Local-sae-id: SAE_A
Local-certificate-id: SAE_A_CERT
Trusted-cas: [ Root-CA ]
Peer-sae-ids: N/A
Default-key-size: N/A
Request stats:
Received: 0
In-progress: 0
Success: 0
Failed: 0Significado
Muestra el show security pki ca-certificate ca-profile Root-CA nombre del perfil de CA PKI, el identificador de certificado, la validez, el algoritmo de clave pública, etc.
Muestra show security pki local-certificate certificate-id SAE_A_CERT el nombre del perfil de CA local, el identificador de certificado, la validez, el algoritmo de clave pública, etc.
El muestra el request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B perfil y las claves del administrador de claves del dispositivo par.
Muestra show security key-manager profiles name KM_PROFILE_1 detail el nombre del perfil del administrador de claves de seguridad, la dirección URL, las solicitudes, etc.
Ejemplo: Configurar el perfil de clave de Quantum Key Manager para VPN IPsec de sitio a sitio
Utilice este ejemplo de configuración para proteger una infraestructura VPN de sitio a sitio IPsec configurando el perfil de clave del administrador de claves cuánticas.
Puede proteger una infraestructura VPN de sitio a sitio IPsec configurando el perfil de clave de Quantum Key Manager.
En este ejemplo de configuración, los dispositivos SRX1 y SRX2 usan el perfil de administrador de claves cuánticas para obtener las claves QKD en VPN IPsec. Las teclas QKD ayudan a enviar tráfico de forma segura a través de Internet.
|
Tiempo de lectura |
Menos de una hora |
|
Tiempo de configuración |
Menos de una hora |
- Ejemplo de requisitos previos
- Antes de empezar
- Descripción general funcional
- Información general sobre la topología
- Ilustración de topología
- Configuración paso a paso en dispositivos de firewall de la serie SRX
- Verificación
- Apéndice 1: Establecer comandos en todos los dispositivos
- Apéndice 2: Mostrar salida de configuración en DUT
Ejemplo de requisitos previos
|
Requisitos de hardware |
Firewall SRX1500 de Juniper Networks® o modelos de dispositivos numerados superiores o Firewall virtual vSRX de Juniper Networks® (vSRX3.0) |
|
Requisitos de software |
Junos OS versión 22.4R1 o posterior. |
Antes de empezar
|
Ventajas |
|
|
Recursos útiles |
|
|
Saber más |
|
|
Experiencia práctica |
|
|
Seguir leyendo |
Descripción general funcional
| VPN IPSec |
Implementa una topología VPN IPsec radial donde los radios están conectados por túneles VPN que envían tráfico a través del concentrador. Estos túneles VPN se configuran posteriormente para usar claves cuánticas, lo que los convierte en túneles VPN de seguridad cuántica. |
| Puerta de enlace IKE |
Establece una conexión segura. La puerta de enlace de IKE utiliza la política de IKE para limitarse al grupo configurado de perfiles de entidad de certificación (CA) mientras valida el certificado. |
| Propuestas | |
| Propuesta de IKE |
Define los algoritmos y las claves utilizados para establecer la conexión IKE segura con la puerta de enlace de seguridad del mismo nivel. IKE crea las asociaciones de seguridad dinámica (SA) y las negocia para IPsec. |
| Propuesta IPsec |
Enumera los protocolos, algoritmos y servicios de seguridad que se negociarán con el par IPsec remoto. |
| Políticas | |
| Política de IKE |
Define una combinación de parámetros de seguridad (propuestas de IKE) que se utilizarán durante la negociación de IKE. |
| Directiva IPsec |
Contiene reglas y políticas de seguridad para permitir el tráfico VPN de grupo entre las zonas especificadas. |
| Política de seguridad |
Permite seleccionar el tipo de tráfico de datos que desea proteger mediante las SA de IPsec.
|
|
Perfiles |
|
|
Perfil clave |
Define cómo los dispositivos de firewall de la serie SRX se comunican con los dispositivos KME para recuperar claves QKD del servidor KME externo. Los perfiles clave se configuran en el concentrador (HUB_KM_PROFILE_1) y en los radios (SPOKE_1_KM_PROFILE_1 y SPOKE_2_KM_PROFILE_1) por separado.
|
| Perfil de PPK |
Indica qué perfil de clave se debe usar para establecer SA de IPsec o IKE con seguridad cuántica haciendo referencia al perfil de clave en la puerta de enlace de IKE. |
| Certificados | |
| Certificado de CA | Verifica la identidad de los dispositivos y autentica el vínculo de comunicación. |
| Certificado local | Genera PKI y la inscribe con el certificado de CA para su verificación. |
| Certificado KME | Certificado de terceros generado por el proveedor. |
| Zonas de seguridad | |
| confiar |
Segmento de red en la zona de host. |
| no confiar |
Segmento de red en la zona del servidor de destino. |
| vpn |
Segmento de red a través del cual interactúan el hub y los radios. |
|
Tareas de verificación primarias |
Verifique que las SA IKE e IPsec establecidas sean seguras para Quantum. |
Información general sobre la topología
En este ejemplo, protegemos los túneles VPN IPsec SRX1 y SRX2 mediante el uso de claves cuánticas generadas por dispositivos KME de terceros. Los dispositivos KME (KME-A y KME-B) están conectados entre sí a través de un canal cuántico que es altamente seguro y capaz de identificar amenazas. Usando este canal, los dispositivos SRX1 y SRX2 recuperan claves cuánticas de su dispositivo KME correspondiente y lo combinan con las claves existentes para hacer que los túneles VPN sean seguros cuánticamente.
|
Nombre de host |
Función |
Función |
|---|---|---|
| SRX1 | Dispositivo de firewall serie SRX capaz de establecer túneles IPsec | Inicia la negociación IKE o IPsec SA y establece túneles IPsec de seguridad cuántica con SRX2 mediante la clave QKD obtenida del dispositivo QKD KME-A. |
| SRX2 | Dispositivo de firewall serie SRX capaz de establecer túneles IPsec | Responde a la negociación IKE o IPsec SA y establece túneles IPsec de seguridad cuántica mediante la clave QKD del dispositivo QKD KME-B. |
| HOST1 | Host dentro de la zona de confianza o lado LAN de SRX1 | Inicia el tráfico del lado del cliente hacia el HOST 2 |
| HOST2 | Host dentro de la zona de confianza o lado LAN de SRX2 | Responde al tráfico del lado del cliente desde el HOST 1. |
| KME-A | Dispositivo QKD de un proveedor externo | Proporciona claves QKD en respuesta a solicitudes de claves de SRX1. |
| KME-B | Dispositivo QKD de un proveedor externo | Proporciona claves QKD en respuesta a solicitudes de claves de SRX2. |
Ilustración de topología
Configuración paso a paso en dispositivos de firewall de la serie SRX
Para obtener ejemplos completos de configuraciones en el DUT, consulte:
Esta configuración es aplicable a dispositivos SRX1 y SRX2. Para otros dispositivos, debe realizar los cambios de configuración específicos del dispositivo adecuados.
-
Configure las interfaces.
[edit interfaces] user@srx# set ge-0/0/0 unit 0 family inet address 172.18.10.1/24 user@srx# set st0 unit 1 family inet user@srx# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24
-
Configure un perfil clave de tipo quantum-key-manager con los parámetros must o recomendados.
Defina el certificado de CA, configure la URL del servidor KME, configure el SAE-ID para que lo utilice el extremo local, configure el certificado correspondiente para el SAE-ID local y configure el certificado de CA definido previamente.
[edit security pki] user@srx# set ca-profile ROOT_CA_CERT ca-identity RootCA
[edit security key-manager profiles] user@srx# set km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net
[edit security key-manager profiles] user@srx# set km_profile_1 quantum-key-manager local-sae-id SAE_A user@srx# set km_profile_1 quantum-key-manager local-certificate-id SAE_A_CERT user@srx# set km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT
Configure VPN IPsec de sitio a sitio. Esto incluye la configuración de las zonas de seguridad, las políticas de seguridad y los certificados relevantes para autenticar las identidades de los dispositivos y sus vínculos de comunicación.
[edit security zones] user@srx# set security-zone untrust host-inbound-traffic system-services ike user@srx# set security-zone untrust interfaces ge-0/0/0.0 user@srx# set security-zone vpn interfaces st0.1 user@srx# set security-zone trust host-inbound-traffic system-services ping user@srx# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@srx# set from-zone trust to-zone vpn policy vpn_out match source-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match application any user@srx# set from-zone trust to-zone vpn policy vpn_out then permit user@srx# set from-zone vpn to-zone trust policy vpn_in match source-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match application any user@srx# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security ike proposal] user@srx# set IKE_PROP authentication-method pre-shared-keys user@srx# set IKE_PROP dh-group group14 user@srx# set IKE_PROP authentication-algorithm sha-256 user@srx# set IKE_PROP encryption-algorithm aes-256-cbc user@srx# set IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@srx# set IKE_POL proposals IKE_PROP user@srx# set IKE_POL pre-shared-key ascii-text ipsec-test
[edit security ike gateway] user@srx# set IKE_GW ike-policy IKE_POL user@srx# set IKE_GW address 172.18.10.2 user@srx# set IKE_GW external-interface ge-0/0/0.0 user@srx# set IKE_GW local-address 172.18.10.1 user@srx# set IKE_GW version v2-only user@srx# set IKE_GW ppk-profile km_profile_1
[edit security ipsec proposal] user@srx# set IPSEC_PROP protocol esp user@srx# set IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx# set IPSEC_PROP encryption-algorithm aes-256-cbc user@srx# set IPSEC_PROP lifetime-seconds 2400
[edit security ipsec policy] user@srx# set IPSEC_POL proposals IPSEC_PROP
[edit security ipsec vpn] user@srx# set IPSEC_VPN bind-interface st0.1 user@srx# set IPSEC_VPN ike gateway IKE_GW user@srx# set IPSEC_VPN ike ipsec-policy IPSEC_POL user@srx# set IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@srx# set IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 user@srx# set IPSEC_VPN establish-tunnels immediately
Verificación
En esta sección se proporciona una lista de comandos show que puede usar para comprobar la característica de este ejemplo.
| Comando | Tarea de verificación |
|---|---|
|
mostrar detalles de asociaciones de seguridad de IKE |
|
|
mostrar detalles de asociaciones de seguridad IPsec |
|
|
Mostrar estadísticas de seguridad IPsec |
Compruebe las estadísticas de cifrado y descifrado de IPsec. |
|
mostrar detalles de los perfiles de los administradores de claves de seguridad |
Verifique las estadísticas del perfil clave. |
|
ping 192.168.80.20 fuente 192.168.90.20 recuento 5 |
Ping del HOST 1 al HOST 2 o viceversa. |
- Comprobar las SA de IKE
- Comprobar las SA de IPsec
- Comprobar estadísticas de IPsec
- Verificar el perfil del administrador de claves
- Ping del HOST 1 al HOST 2 o viceversa
Comprobar las SA de IKE
Propósito
Compruebe las SA de IKE.
Acción
Desde el modo operativo, escriba el show security ike security-associations detail comando para ver las SA de IKE.
user@srx> show security ike security-associations detail IKE peer 172.18.10.2, Index 21, Gateway Name: IKE_GW Role: Initiator, State: UP Initiator cookie: 5a417d46cef3207d, Responder cookie: 57b9a17516bee31b Exchange type: IKEv2, Authentication method: Pre-shared-keys Local gateway interface: ge-0/0/2.0 Routing instance: default Local: 172.18.10.1:500, Remote: 172.18.10.2:500 Lifetime: Expires in 3445 seconds Reauth Lifetime: Disabled IKE Fragmentation: Enabled, Size: 576 SRG ID: 0 Remote Access Client Info: Unknown Client Peer ike-id: 172.18.10.2 AAA assigned IP: 0.0.0.0 PPK-profile: km_profile_1 Optional: No State : Used Algorithms: Authentication : hmac-sha256-128 Encryption : aes256-cbc Pseudo random function: hmac-sha256 Diffie-Hellman group : DH-group-14 Traffic statistics: Input bytes : 783 Output bytes : 831 Input packets: 2 Output packets: 2 Input fragmented packets: 0 Output fragmented packets: 0 IPSec security associations: 2 created, 0 deleted Phase 2 negotiations in progress: 1 IPSec Tunnel IDs: 500003 Negotiation type: Quick mode, Role: Initiator, Message ID: 0 Local: 172.18.10.1:500, Remote: 172.18.10.2:500 Local identity: 172.18.10.1 Remote identity: 172.18.10.2 Flags: IKE SA is created IPsec SA Rekey CREATE_CHILD_SA exchange stats: Initiator stats: Responder stats: Request Out : 0 Request In : 0 Response In : 0 Response Out : 0 No Proposal Chosen In : 0 No Proposal Chosen Out : 0 Invalid KE In : 0 Invalid KE Out : 0 TS Unacceptable In : 0 TS Unacceptable Out : 0 Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0 Res Verify SA Fail : 0 Res Verify DH Group Fail: 0 Res Verify TS Fail : 0
Significado
Los Role: Initiator, State: UPcampos , PPK-profile: km_profile_1, IPSec security associations: 2 created, 0 deleted Phase 2 negotiations in progress: 1y Flags: IKE SA is created muestran que las SA de IKE se crearon correctamente.
Comprobar las SA de IPsec
Propósito
Compruebe las SA de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec security-associations detail comando para ver las SA de IPsec.
user@srx> show security ipsec security-associations detail ID: 500003 Virtual-system: root, VPN Name: IPSEC_VPN Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2 Traffic Selector Name: ts1 Local Identity: ipv4(192.168.90.0-192.168.90.255) Remote Identity: ipv4(192.168.80.0-192.168.80.255) TS Type: traffic-selector Version: IKEv2 Quantum Secured: Yes PFS group: N/A SRG ID: 0 DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: IPSEC_POL Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0 Multi-sa, Configured SAs# 0, Negotiated SAs#: 0 Tunnel events: Fri Mar 31 2023 01:41:52: IPsec SA negotiation succeeds (1 times) Location: FPC 0, PIC 0, KMD-Instance 0 Anchorship: Thread 1 Distribution-Profile: default-profile Direction: inbound, SPI: 0xd1e1549c, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1916 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1349 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21 Direction: outbound, SPI: 0xb5883167, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1916 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1349 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21
Significado
Los Quantum Secured: Yescampos , Policy-name: IPSEC_POL, IPsec SA negotiation succeeds (1 times)y tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21 muestran que las SA de IPsec se crearon correctamente.
Comprobar estadísticas de IPsec
Propósito
Compruebe las estadísticas de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec statistics comando para ver las estadísticas de IPsec.
user@srx> show security ipsec statistics ESP Statistics: Encrypted bytes: 780 Decrypted bytes: 780 Encrypted packets: 5 Decrypted packets: 5 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Los ESP Statistics campos y AH Statistics muestran las estadísticas de IPsec.
Verificar el perfil del administrador de claves
Propósito
Compruebe el perfil del administrador de claves.
Acción
Desde el modo operativo, escriba el show security key-manager profiles detail comando para ver el perfil del administrador de claves.
user@srx> show security key-manager profiles detail Name: km_profile_1, Index: 3, Type: Quantum-key-manager Configured-at: 31.03.23 (01:40:50) Time-elapsed: 0 hrs 11 mins 30 secs Url: https://www.kme_a-qkd-server.net Local-sae-id: SAE_A Local-certificate-id: SAE_A_CERT Trusted-cas: [ ROOT_CA_CERT ] Peer-sae-ids: N/A Default-key-size: N/A Request stats: Received: 1 In-progress: 0 Success: 1 Failed: 0
Significado
Los Name: km_profile_1 campos y Quantum-key-manager muestran el perfil del administrador de claves.
Ping del HOST 1 al HOST 2 o viceversa
Propósito
Compruebe la conectividad del HOST 1 al HOST 2.
Acción
Desde el modo operativo, introduzca el ping 192.168.80.20 source 192.168.90.20 recuento 5 para ver la conectividad del HOST 1 al HOST 2.
user@HOST1# ping 192.168.80.20 source 192.168.90.20 count 5 PING 192.168.80.20 (192.168.80.20): 56 data bytes count 5 64 bytes from 192.168.80.1: icmp_seq=0 ttl=64 time=0.998 ms 64 bytes from 192.168.80.1: icmp_seq=1 ttl=64 time=1.594 ms 64 bytes from 192.168.80.1: icmp_seq=2 ttl=64 time=1.395 ms 64 bytes from 192.168.80.1: icmp_seq=3 ttl=64 time=1.536 ms 64 bytes from 192.168.80.1: icmp_seq=4 ttl=64 time=1.838 ms --- 192.168.80.1 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.998/1.472/1.838/0.277 ms Data traffic is successfully flowing between the HOSTs
Significado
El PING 192.168.80.20 (192.168.80.20): 56 data bytes count 5 confirma la conectividad del HOST 1 al HOST 2.
Apéndice 1: Establecer comandos en todos los dispositivos
Establezca la salida del comando en todos los dispositivos.
Establecer comandos en SRX1
set security pki ca-profile ROOT_CA_CERT ca-identity RootCA set security key-manager profiles km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net set security key-manager profiles km_profile_1 quantum-key-manager local-sae-id SAE_A set security key-manager profiles km_profile_1 quantum-key-manager local-certificate-id SAE_A_CERT set security key-manager profiles km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.1/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.2 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.1 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Establecer comandos en SRX2
set security pki ca-profile ROOT_CA_CERT ca-identity RootCA set security key-manager profiles km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net set security key-manager profiles km_profile_1 quantum-key-manager local-sae-id SAE_B set security key-manager profiles km_profile_1 quantum-key-manager local-certificate-id SAE_B_CERT set security key-manager profiles km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.2/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.1 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.2 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Apéndice 2: Mostrar salida de configuración en DUT
Mostrar la salida del comando en el DUT.
SRX1
user@srk1# show security pki
ca-profile ROOT_CA_CERT {
ca-identity RootCA;
}
user@srk1# show security key-manager
profiles {
km_profile_1 {
quantum-key-manager {
url https://www.kme_a-qkd-server.net;
local-sae-id SAE_A;
local-certificate-id SAE_A_CERT;
trusted-cas ROOT_CA_CERT;
}
}
}user@srk1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@srk1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srk1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srk1# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srk1# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$Nadwg4aUH.5Nds4aUiHuO1RhrvWxVs4"; ## SECRET-DATA
user@srk1# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.2; external-interface ge-0/0/0.0; local-address 172.18.10.1; version v2-only; ppk-profile km_profile_1;
user@srk1# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srk1# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srk1# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 192.168.80.0/24;
}
establish-tunnels immediately;SRX 2
user@srx2# show security key-manager
profiles {
km_profile_1 {
quantum-key-manager {
url https://www.kme_a-qkd-server.net;
local-sae-id SAE_B;
local-certificate-id SAE_B_CERT;
trusted-cas ROOT_CA_CERT;
}
}
}user@srx2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@srx2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srx2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srx2# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx2# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.1; external-interface ge-0/0/0.0; local-address 172.18.10.2; version v2-only; ppk-profile km_profile_1;
user@srx2# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$P5z6/Cu1EyP5F/CuB1-VwYgJDi.TF/"; ## SECRET-DATA
user@srx2# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srx2# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}
establish-tunnels immediately;Ejemplo: Configurar la topología AutoVPN IPsec con seguridad cuántica mediante el perfil de clave de Quantum Key Manager
Utilice este ejemplo de configuración para proteger una infraestructura AutoVPN IPsec configurando el perfil de clave del administrador de claves cuánticas.
El Hub, Spoke 1 y Spoke 2 utilizan perfiles de clave del administrador de claves cuánticas para comunicarse con KME Hub, KME Spoke 1 y KME Spoke 2 para obtener las claves QKD y establecer túneles VPN IPsec.
Tiempo de lectura |
Menos de una hora. |
Tiempo de configuración |
Menos de una hora. |
- Ejemplo de requisitos previos
- Antes de empezar
- Descripción general funcional
- Información general sobre la topología
- Ilustración de topología
- Configuración paso a paso en el hub
- Configuración paso a paso en dispositivos radiales
- Verificación
- Apéndice 1: Establecer comandos en todos los dispositivos
- Apéndice 2: Mostrar salida de configuración en DUT
Ejemplo de requisitos previos
Requisitos de hardware |
|
Requisitos de software |
Junos OS versión 22.4R1 o posterior. |
Antes de empezar
Ventajas |
|
Recursos útiles |
|
Saber más |
|
Experiencia práctica |
|
Seguir leyendo |
Descripción general funcional
Tabla 20 Proporciona un resumen rápido de los componentes de configuración implementados en este ejemplo.
| VPN IPSec | Implemente una topología VPN IPsec radial donde los radios estén conectados por túneles VPN que envían tráfico a través del concentrador. Estos túneles VPN se configuran posteriormente para usar claves cuánticas, lo que los convierte en túneles VPN de seguridad cuántica. |
| Puerta de enlace IKE | Al establecer una conexión segura, la puerta de enlace de IKE utiliza la política de IKE para limitarse al grupo configurado de CA (perfiles de CA) mientras valida el certificado. |
| Propuestas | |
| Propuesta de IKE | Defina los algoritmos y las claves utilizados para establecer la conexión IKE segura con la puerta de enlace de seguridad del mismo nivel. IKE crea las SA dinámicas y las negocia para IPsec. |
| Propuesta IPsec | Enumere los protocolos, algoritmos y servicios de seguridad que se negociarán con el par IPsec remoto. |
| Políticas | |
| Política de IKE | Defina una combinación de parámetros de seguridad (propuestas IKE) que se utilizarán durante la negociación de IKE. |
| Directiva IPsec | Contener reglas y políticas de seguridad para permitir el tráfico VPN de grupo entre las zonas especificadas. |
| Política de seguridad | Permite seleccionar el tipo de tráfico de datos que desea proteger mediante las SA de IPsec.
|
Perfiles |
|
| Perfil clave | Defina cómo los dispositivos SRX se comunican con los dispositivos KME para recuperar claves QKD del servidor KME externo. Los perfiles clave se configuran en el concentrador (HUB_KM_PROFILE_1) y en los radios (SPOKE_1_KM_PROFILE_1 y SPOKE_2_KM_PROFILE_1) por separado. Configure SPOKE-1 y SPOKE-2 para que las aplicaciones y servicios recuperen claves QKD del servidor externo.
|
| Perfil de PPK | Indique qué perfil de clave se debe utilizar para establecer SA de IPsec o IKE con seguridad cuántica haciendo referencia al perfil de clave en la puerta de enlace de IKE. |
| Certificados | |
| Certificado de CA | Verifique la identidad de los dispositivos y autentique el vínculo de comunicación entre ellos. |
| Certificado local | Genere PKI e inscríbase con el certificado de CA para su verificación. |
| Certificado KME | Certificado de terceros generado por el proveedor. |
| Zonas de seguridad | |
| confiar | Segmento de red en la zona de host. |
| no confiar | Segmento de red en la zona del servidor de destino. |
| vpn | Segmento de red a través del cual interactúan el hub y los radios. |
Tareas de verificación primarias |
Verifique que las SA IKE e IPsec establecidas sean seguras para Quantum. |
Información general sobre la topología
En este ejemplo, protegemos los túneles VPN IPsec radiales mediante claves cuánticas generadas por dispositivos KME de terceros. Los dispositivos KME (KME-Hub, KME-Spoke 1 y KME-Spoke 2) están conectados entre sí a través de un canal cuántico que es altamente seguro y capaz de identificar amenazas. Usando este canal, los dispositivos radiales recuperan claves cuánticas de su dispositivo KME correspondiente y lo fusionan con las claves existentes para hacer que los túneles VPN sean seguros cuánticamente.
Componentes de topología |
Función |
Función |
|---|---|---|
Hub |
Firewall serie SRX capaz de establecer túneles IPsec | Responde a la negociación de IKE o IPsec SA y establece túneles IPsec de seguridad cuántica mediante la clave QKD del dispositivo QKD KME-HUB en SPOKE-1 y SPOKE-2. |
SPOKE-1 |
Firewall serie SRX capaz de establecer túneles IPsec | Inicia la negociación de IKE o IPsec SA y establece túneles IPsec de seguridad cuántica con concentrador mediante la clave QKD del KME-SPOKE-1 dispositivo QKD. |
SPOKE-2 |
Firewall serie SRX capaz de establecer túneles IPsec | Inicia la negociación de IKE o IPsec SA y establece túneles IPsec de seguridad cuántica con concentrador mediante la clave QKD del KME-SPOKE-2 dispositivo QKD. |
HOST-1 |
El host dentro de la zona de confianza o en el lado LAN de SPOKE 1. Host 1 está protegido por SPOKE 1. |
Inicia el tráfico del lado del cliente hacia HOST-3 |
HOST-2 |
El host dentro de la zona de confianza o en el lado LAN de SPOKE 2. Host 2 está protegido por SPOKE 2. |
Inicia el tráfico del lado del cliente hacia HOST-3 |
HOST- 3 |
Aloje dentro de la zona de confianza o en el lado LAN del concentrador. Host 3 está asegurado por Hub. |
Responde al tráfico del lado del cliente desde HOST-1 y HOST-2 |
KME-HUB |
Dispositivo QKD de terceros | Proporciona claves QKD en respuesta a solicitudes clave de HUB |
KME-SPOKE-1 |
Dispositivo QKD de terceros | Proporciona claves QKD en respuesta a solicitudes clave de SPOKE-1 |
KME-SPOKE-2 |
Dispositivo QKD de terceros | Proporciona claves QKD en respuesta a solicitudes clave de SPOKE-2 |
Ilustración de topología
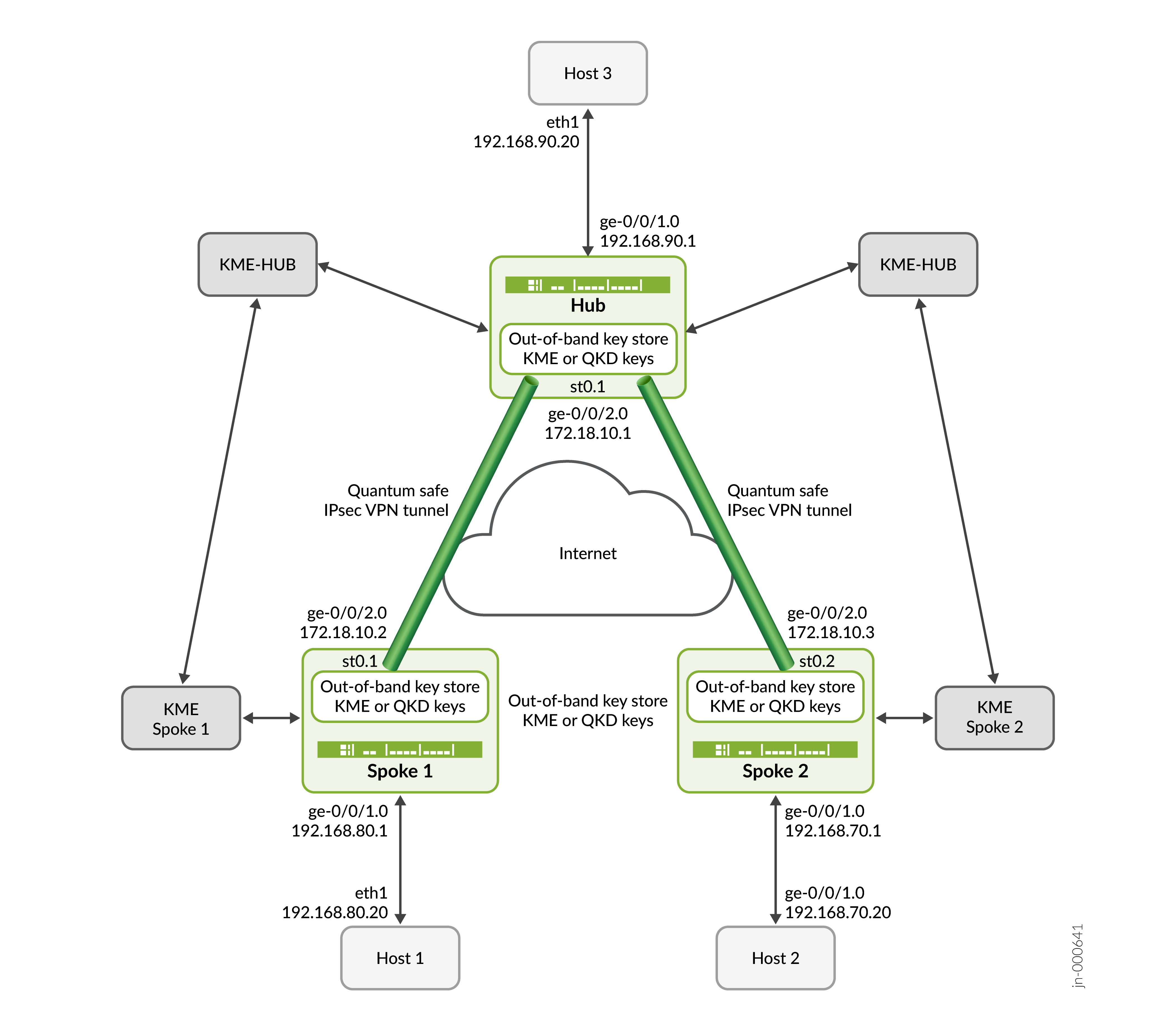
Configuración paso a paso en el hub
Para obtener ejemplos completos de configuraciones en los dispositivos radiales, consulte:
Configure las interfaces del concentrador.
[edit interfaces] user@hub# set ge-0/0/2 unit 0 family inet address 172.18.10.1/24 user@hub# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24 user@hub# set st0 unit 1 family inet
Configure la VPN radial de concentrador IPsec. Esto incluye la configuración de las zonas de seguridad, las políticas de seguridad y los certificados relevantes para autenticar las identidades de los dispositivos y sus vínculos de comunicación.
Configure el concentrador para obtener el certificado de CA del servidor de CA o cargue un certificado de CA disponible localmente desde el dispositivo.
Nota:Los certificados KME deben configurarse según las instrucciones del proveedor externo.
Configure la propuesta y la política de IPsec. Configure la política, la propuesta y la puerta de enlace de IKE para la VPN IPsec.
[edit security zones] user@hub# set security-zone untrust host-inbound-traffic system-services ike user@hub# set security-zone untrust interfaces ge-0/0/2.0 user@hub# set security-zone vpn interfaces st0.1 user@hub# set security-zone trust host-inbound-traffic system-services ping user@hub# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@hub# set from-zone trust to-zone vpn policy vpn_out match source-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match application any user@hub# set from-zone trust to-zone vpn policy vpn_out then permit user@hub# set from-zone vpn to-zone trust policy vpn_in match source-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match application any user@hub# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki] user@hub# set ca-profile Root-CA ca-identity Root-CA user@hub# set ca-profile Root-CA enrollment url url-to-CA-server user@hub# set ca-profile Root-CA revocation-check disable
user@hub> request security pki ca-certificate enroll ca-profile Root-CA
user@hub> request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa user@hub> request security pki local-certificate enroll certificate-id HUB_CRT challenge-password password domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA user@hub> request security pki local-certificate load certificate-id SAE_HUB filename SAE_HUB.cert key SAE_HUB.key
[edit security ike proposal] user@hub# set HUB_IKE_PROP authentication-method rsa-signatures user@hub# set HUB_IKE_PROP dh-group group14 user@hub# set HUB_IKE_PROP authentication-algorithm sha-256 user@hub# set HUB_IKE_PROP encryption-algorithm aes-256-cbc user@hub# set HUB_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@hub# set HUB_IKE_POL proposals HUB_IKE_PROP user@hub# set HUB_IKE_POL certificate local-certificate HUB_CRT
[edit security ike gateway] user@hub# set HUB_IKE_GW local-address 172.18.10.1 user@hub# set HUB_IKE_GW ike-policy HUB_IKE_POL user@hub# set HUB_IKE_GW external-interface ge-0/0/2.0 user@hub# set HUB_IKE_GW local-identity distinguished-name user@hub# set HUB_IKE_GW dynamic ike-user-type group-ike-id user@hub# set HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper user@hub# set HUB_IKE_GW version v2-only
[edit security ipsec proposal] user@hub# set HUB_IPSEC_PROP protocol esp user@hub# set HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@hub# set HUB_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec vpn] user@hub# set HUB_IPSEC_VPN bind-interface st0.1 user@hub# set HUB_IPSEC_VPN ike gateway HUB_IKE_GW user@hub# set HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL user@hub# set HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@hub# set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0
[edit security ipsec policy] user@hub# set HUB_IPSEC_POL proposals HUB_IPSEC_PROP
Configure el perfil de clave del administrador de claves cuánticas para recuperar claves cuánticas del dispositivo KME-Hub correspondiente.
[edit security key-manager profiles] user@hub# set HUB_KM_PROFILE_1 quantum-key-manager url kme-server-urlset security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_HUB user@hub# set HUB_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_HUB_CERT user@hub# set HUB_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
Vincule el perfil de clave del administrador de claves cuánticas como el perfil ppk de la puerta de enlace IKE para que los túneles VPN sean seguros cuánticamente.
[edit security ike gateway] user@hub# set HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1
Cuando termine de configurar el dispositivo, ingrese commit en el modo de configuración.
Configuración paso a paso en dispositivos radiales
Para obtener ejemplos completos de configuraciones en los dispositivos, consulte:
Esta configuración es aplicable para dispositivos Spoke 1 y Spoke 2; debe realizar los cambios de configuración específicos del dispositivo adecuados.
Configure las interfaces radiales.
[edit interfaces] user@spoke# set ge-0/0/2 unit 0 family inet address 172.18.10.2/24 user@spoke# set ge-0/0/1 unit 0 family inet address 192.168.80.1/24 user@spoke# set st0 unit 1 family inet
Configure la VPN radial de concentrador IPsec. Esto incluye la configuración de las zonas de seguridad, las políticas de seguridad y los certificados relevantes para autenticar las identidades de los dispositivos y sus vínculos de comunicación.
Configure el concentrador para obtener el certificado de CA del servidor de CA o cargue un certificado de CA disponible localmente desde el dispositivo.
Nota:Los certificados KME deben configurarse según las instrucciones del proveedor externo.
Configure la propuesta y la política de IPsec. Configure la política, la propuesta y la puerta de enlace de IKE para la VPN IPsec.
[edit security zones] user@spoke# set security-zone untrust host-inbound-traffic system-services ike user@spoke# set security-zone untrust interfaces ge-0/0/2.0 user@spoke# set security-zone vpn interfaces st0.1 user@spoke# set security-zone trust host-inbound-traffic system-services ping user@spoke# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@spoke# set from-zone trust to-zone vpn policy vpn_out match source-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match application any user@spoke# set from-zone trust to-zone vpn policy vpn_out then permit user@spoke# set from-zone vpn to-zone trust policy vpn_in match source-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match application any user@spoke# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki] user@spoke# set ca-profile Root-CA ca-identity Root-CA user@spoke# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@spoke# set ca-profile Root-CA revocation-check disable
user@spoke> request security pki ca-certificate enroll ca-profile Root-CA
user@spoke> request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa user@spoke> request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <password> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA user@spoke> request security pki local-certificate load certificate-id SAE_SPOKE_1 filename SAE_SPOKE_1.cert key SAE_SPOKE_1.key
[edit security ike proposal] user@spoke# set SPOKE_1_IKE_PROP authentication-method rsa-signatures user@spoke# set SPOKE_1_IKE_PROP dh-group group14 user@spoke# set SPOKE_1_IKE_PROP authentication-algorithm sha-256 user@spoke# set SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc user@spoke# set SPOKE_1_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@spoke# set SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP user@spoke# set SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW address 172.18.10.1 user@spoke# set SPOKE_1_IKE_GW local-address 172.18.10.2 user@spoke# set SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL user@spoke# set SPOKE_1_IKE_GW external-interface ge-0/0/2.0 user@spoke# set SPOKE_1_IKE_GW local-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW remote-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW version v2-only
[edit security ipsec proposal] user@spoke# set SPOKE_1_IPSEC_PROP protocol esp user@spoke# set SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@spoke# set SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec vpn] user@spoke# set SPOKE_1_IPSEC_VPN bind-interface st0.1 user@spoke# set SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW user@spoke# set SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24
[edit security ipsec policy] user@spoke# set SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP
Configure el perfil de clave del administrador de claves cuánticas para recuperar claves cuánticas del dispositivo radial correspondiente.
[edit security key-manager profiles] user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_1-qkd-server.net user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_1 user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_1_CERT user@spoke# set profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
Vincule el perfil de clave del administrador de claves cuánticas como el perfil ppk de la puerta de enlace IKE para que los túneles VPN sean seguros cuánticamente.
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1
Cuando termine de configurar el dispositivo, ingrese commit en el modo de configuración.
Verificación
En esta sección se proporciona una lista de comandos show que puede usar para comprobar la característica de este ejemplo.
| Comando | Tarea de verificación |
|---|---|
|
mostrar detalles de asociaciones de seguridad de IKE |
Compruebe las SA de IKE. |
|
mostrar detalles de asociaciones de seguridad IPsec |
Compruebe las SA de IPsec. |
|
Mostrar estadísticas de seguridad IPsec |
Compruebe las estadísticas de cifrado y descifrado de IPsec. |
|
mostrar detalles de los perfiles de los administradores de claves de seguridad |
Verifique las estadísticas del perfil clave. |
|
ping 192.168.90.20 fuente 192.168.80.20 recuento 4 |
Ping del host 1 al host 3. |
|
ping 192.168.90.20 fuente 192.168.70.20 recuento 4 |
Ping del host 2 al host 3. |
- Comprobar las SA de IKE
- Comprobar las SA de IPsec
- Comprobar estadísticas de IPsec
- Verificar el perfil del administrador de claves
- Ping del host 1 al host 3
- Ping del host 2 al host 3
Comprobar las SA de IKE
Propósito
Compruebe las SA de IKE.
Acción
Desde el modo operativo, escriba el show security ike security-associations detail comando para ver las SA de IKE.
user@hub> show security ike security-associations detail
IKE peer 172.18.10.3, Index 2161, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: bccc74c70f0b81b9, Responder cookie: 872d364f15b29c28
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Lifetime: Expires in 3464 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2661
Output bytes : 2586
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500446
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
IKE peer 172.18.10.2, Index 2162, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 5e17d5924c619788, Responder cookie: 15f1e3c4252ba6f8
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 3464 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2645
Output bytes : 2586
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500447
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0 Significado
La salida de ejemplo confirma las SA de IKE.
Comprobar las SA de IPsec
Propósito
Compruebe las SA de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec security-associations detail comando para ver las SA de IPsec.
user@hub> show security ipsec security-associations detail
ID: 500446 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.3
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.70.0-192.168.70.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Fri Jul 21 2023 00:31:08: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0xcf48c0c9, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2778 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2161
Direction: outbound, SPI: 0x86c9ba76, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2778 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2161
ID: 500447 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.80.0-192.168.80.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Fri Jul 21 2023 00:31:08: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x4275d756, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2772 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2162
Direction: outbound, SPI: 0xe37b5568, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2772 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2162Significado
La salida de ejemplo confirma las SA de IPsec.
Comprobar estadísticas de IPsec
Propósito
Compruebe las estadísticas de IPsec.
Acción
Desde el modo operativo, escriba el show security ipsec statistics comando para ver las estadísticas de IPsec.
user@hub> show security ipsec statistics ESP Statistics: Encrypted bytes: 1560 Decrypted bytes: 1560 Encrypted packets: 10 Decrypted packets: 10 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
La salida de ejemplo confirma las estadísticas de IPsec.
Verificar el perfil del administrador de claves
Propósito
Compruebe el perfil del administrador de claves.
Acción
Desde el modo operativo, ingrese el show security key-manager profiles detail comando y verifique el Success campo en la Request stats opción.
user@hub> show security key-manager profiles detail
Name: HUB_KM_PROFILE_1, Index: 6, Type: Quantum-key-manager
Configured-at: 21.07.23 (00:14:00)
Time-elapsed: 0 hrs 19 mins 24 secs
Url: https://kme.juniper.net:8080
Local-sae-id: SAE_HUB
Local-certificate-id: SAE_HUB_CERT
Trusted-cas: [ ROOT_CA_CERT ]
Peer-sae-ids: N/A
Default-key-size: N/A
Request stats:
Received: 2
In-progress: 0
Success: 2
Failed: 0
Significado
La salida de ejemplo confirma el perfil del administrador de claves cuánticas.
Ping del host 1 al host 3
Propósito
Compruebe la conectividad del host 1 al host 3.
Acción
Desde el modo operativo, escriba el ping 192.168.90.20 source 192.168.80.20 count 5 comando para ver la conectividad del host 1 al host 3.
user@host1# ping 192.168.90.20 source 192.168.80.20 count 5 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms 64 bytes from 192.168.90.20: icmp_seq=4 ttl=64 time=1.515 ms --- 192.168.90.20 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
La salida de ejemplo confirma la conectividad del host 1 al host 3.
Ping del host 2 al host 3
Propósito
Compruebe la conectividad del host 2 al host 3.
Acción
Desde el modo operativo, escriba el ping 192.168.90.20 source 192.168.80.20 count 5 comando para ver la conectividad del host 2 al host 3.
user@host2# ping 192.168.90.20 source 192.168.70.20 count 5 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms 64 bytes from 192.168.90.20: icmp_seq=4 ttl=64 time=1.759 ms --- 192.168.90.20 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
La salida de ejemplo confirma la conectividad del host 2 al host 3.
Apéndice 1: Establecer comandos en todos los dispositivos
Establezca la salida del comando en todos los dispositivos.
Establecer comandos en el hub
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id HUB_CRT challenge-password <password> domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_HUB filename SAE_HUB.cert key SAE_HUB.key set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager url https://www.kme_hub-qkd-server.net set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_HUB set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_HUB_CERT set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal HUB_IKE_PROP authentication-method rsa-signatures set security ike proposal HUB_IKE_PROP dh-group group14 set security ike proposal HUB_IKE_PROP authentication-algorithm sha-256 set security ike proposal HUB_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal HUB_IKE_PROP lifetime-seconds 3600 set security ike policy HUB_IKE_POL proposals HUB_IKE_PROP set security ike policy HUB_IKE_POL certificate local-certificate HUB_CRT set security ike gateway HUB_IKE_GW local-address 172.18.10.1 set security ike gateway HUB_IKE_GW ike-policy HUB_IKE_POL set security ike gateway HUB_IKE_GW external-interface ge-0/0/2.0 set security ike gateway HUB_IKE_GW local-identity distinguished-name set security ike gateway HUB_IKE_GW dynamic ike-user-type group-ike-id set security ike gateway HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper set security ike gateway HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 set security ike gateway HUB_IKE_GW version v2-only set security ipsec proposal HUB_IPSEC_PROP protocol esp set security ipsec proposal HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal HUB_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP set security ipsec vpn HUB_IPSEC_VPN bind-interface st0.1 set security ipsec vpn HUB_IPSEC_VPN ike gateway HUB_IKE_GW set security ipsec vpn HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.1/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Establecer comandos en el radio 1
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <password> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_SPOKE_1 filename SAE_SPOKE_1.cert key SAE_SPOKE_1.key set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_1-qkd-server.net set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_1 set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_1_CERT set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_1_IKE_PROP dh-group group14 set security ike proposal SPOKE_1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_1_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP set security ike policy SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT set security ike gateway SPOKE_1_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_1_IKE_GW local-address 172.18.10.2 set security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL set security ike gateway SPOKE_1_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_1_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 set security ike gateway SPOKE_1_IKE_GW version v2-only set security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP set security ipsec vpn SPOKE_1_IPSEC_VPN bind-interface st0.1 set security ipsec vpn SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW set security ipsec vpn SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.2/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Establecer comandos en Spoke 2
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_2_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_2_CRT challenge-password <password> domain-name spoke_2.juniper.net email spoke_2@juniper.net subject DC=juniper,CN=spoke_2.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_SPOKE_2 filename SAE_SPOKE_2.cert key SAE_SPOKE_2.key set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_2-qkd-server.net set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_2 set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_2_CERT set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_2_IKE_PROP dh-group group14 set security ike proposal SPOKE_2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_2_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_2_IKE_POL proposals SPOKE_IKE_PROP set security ike policy SPOKE_2_IKE_POL certificate local-certificate SPOKE_2_CRT set security ike gateway SPOKE_2_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_2_IKE_GW local-address 172.18.10.3 set security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL set security ike gateway SPOKE_2_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_2_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW ppk-profile SPOKE_2_KM_PROFILE_1 set security ike gateway SPOKE_2_IKE_GW version v2-only set security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_2_IPSEC_POL proposals SPOKE_2_IPSEC_PROP set security ipsec vpn SPOKE_2_IPSEC_VPN bind-interface st0.2 set security ipsec vpn SPOKE_2_IPSEC_VPN ike gateway SPOKE_2_IKE_GW set security ipsec vpn SPOKE_2_IPSEC_VPN ike ipsec-policy SPOKE_2_IPSEC_POL set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 local-ip 192.168.70.0/24 set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.3/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.70.1/24 set interfaces st0 unit 2 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.2 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Apéndice 2: Mostrar salida de configuración en DUT
Mostrar la salida del comando en el DUT.
Concentrador
Desde el modo de configuración, escriba los comandos , , ,show interfacesshow security ipsec policy HUB_IPSEC_POLshow security ipsec vpn HUB_IPSEC_VPNshow security zones security-zone untrustshow security policies from-zone trust to-zone vpnshow security policies from-zone vpn to-zone trustshow security ike gateway HUB_IKE_GWshow security zones security-zone trustshow security ike policy HUB_IKE_POLshow security ipsec proposal HUB_IPSEC_PROPshow security ike proposal HUB_IKE_PROPshow security key-managershow security pki ca-profile Root-CA Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@hub# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@hub# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$7VNs4UDkPT3Hq9A01yrWLxNYoPfTz3924"; ## SECRET-DATA
key ascii-text "$9$RraElM7NbwgJ-VkPTFAtxNdws4GUHqmTaZ36AtOBwY24UHfTz9A0JGu1IhrlGDjHmTFn/9p0fT39p0hc-VwgGiPfzn9pJGqfQnpurev8xds2aDjqX7"; ## SECRET-DATA
}
}
HUB_KM_PROFILE_1 {
quantum-key-manager {
url https://www.kme_hub-qkd-server.net;
local-sae-id SAE_HUB;
local-certificate-id SAE_HUB_CERT;
trusted-cas Root-CA;
}
}
}
user@hub# show security ike proposal HUB_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@hub# show security ike policy HUB_IKE_POL
proposals HUB_IKE_PROP;
certificate {
local-certificate HUB_CRT;
}user@hub# show security ike gateway HUB_IKE_GW
ike-policy HUB_IKE_POL;
dynamic {
distinguished-name {
wildcard C=us,DC=juniper;
}
ike-user-type group-ike-id;
}
local-identity distinguished-name;
external-interface ge-0/0/2.0;
local-address 172.18.10.1;
version v2-only;
ppk-profile HUB_KM_PROFILE_1;
user@hub# show security ipsec proposal HUB_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@hub# show security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP;
user@hub# show security ipsec vpn HUB_IPSEC_VPN
bind-interface st0.1;
ike {
gateway HUB_IKE_GW;
ipsec-policy HUB_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 0.0.0.0/0;
}user@hub# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@hub# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@hub# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@hub# show security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@hub# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
st0 {
unit 1 {
family inet;
}
}Habló 1
Desde el modo de configuración, escriba los comandos , , ,show security policies from-zone vpn to-zone trustshow security ipsec policy SPOKE_1_IPSEC_POLshow security ipsec vpn SPOKE_1_IPSEC_VPNshow interfacesshow security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security ike gateway SPOKE_1_IKE_GWshow security zones security-zone untrustshow security ike policy SPOKE_1_IKE_POLshow security ipsec proposal SPOKE_1_IPSEC_PROPshow security ike proposal SPOKE_1_IKE_PROPshow security key-manager profiles SPOKE_1_KM_PROFILE_1show security pki ca-profile Root-CA Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@spoke1# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@spoke1# show security key-manager profiles SPOKE_1_KM_PROFILE_1
quantum-key-manager {
url https://www.kme_spoke_1-qkd-server.net;
local-sae-id SAE_SPOKE_1;
local-certificate-id SAE_SPOKE_1_CERT;
trusted-cas Root-CA;
}user@spoke1# show security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke1# show security ike policy SPOKE_1_IKE_POL
proposals SPOKE_1_IKE_PROP;
certificate {
local-certificate SPOKE_1_CRT;
}user@spoke1# show security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.2; version v2-only; ppk-profile SPOKE_1_KM_PROFILE_1;
user@spoke1# show security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke1# show security ipsec vpn SPOKE_1_IPSEC_VPN
bind-interface st0.1;
ike {
gateway SPOKE_1_IKE_GW;
ipsec-policy SPOKE_1_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}user@spoke1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
st0 {
unit 1 {
family inet;
}
} user@spoke1# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@spoke1# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@spoke1# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@spoke1# security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}Habló 2
Desde el modo de configuración, escriba los comandos , , ,show security policies from-zone vpn to-zone trustshow security ipsec policy SPOKE_1_IPSEC_POLshow security ipsec vpn SPOKE_1_IPSEC_VPNshow interfacesshow security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security ike gateway SPOKE_1_IKE_GWshow security zones security-zone untrustshow security ike policy SPOKE_1_IKE_POLshow security ipsec proposal SPOKE_1_IPSEC_PROPshow security ike proposal SPOKE_1_IKE_PROPshow security key-manager profiles SPOKE_1_KM_PROFILE_1show security pki ca-profile Root-CA Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración en este ejemplo para corregirla.
user@spoke2# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@spoke2# show security key-manager profiles SPOKE_2_KM_PROFILE_1
quantum-key-manager {
url https://www.kme_spoke_2-qkd-server.net;
local-sae-id SAE_SPOKE_2;
local-certificate-id SAE_SPOKE_2_CERT;
trusted-cas Root-CA;
}user@spoke2# show security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke2# show security ike policy SPOKE_2_IKE_POL
##
## Warning: Referenced proposal is not defined
##
proposals SPOKE_IKE_PROP;
certificate {
local-certificate SPOKE_2_CRT;
}
user@spoke2# show security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.3; version v2-only; ppk-profile SPOKE_2_KM_PROFILE_1;
user@spoke2# show security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke2# show security ipsec policy SPOKE_2_IPSEC_POL
proposals SPOKE_2_IPSEC_PROP;
[edit]
user@spoke2# show security ipsec vpn SPOKE_2_IPSEC_VPN
bind-interface st0.2;
ike {
gateway SPOKE_2_IKE_GW;
ipsec-policy SPOKE_2_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.70.0/24;
remote-ip 192.168.90.0/24;
}user@spoke2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}
user@spoke2# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@spoke2# show security zones security-zone vpn
interfaces {
st0.1;
st0.2;
}
user@spoke2# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@spoke2# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
user@spoke2# show security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}