EN ESTA PÁGINA
Ejemplo: configurar VPN IPSec en alta disponibilidad de múltiples nodos activo-activo en una red de capa 3
En este ejemplo, se muestra cómo configurar y comprobar VPN IPsec para la configuración de alta disponibilidad multinodo activa-activa.
Descripción general
En alta disponibilidad de múltiples nodos, los firewalls participantes de la serie SRX funcionan como nodos independientes en una red de capa 3. Los nodos están conectados a infraestructuras adyacentes pertenecientes a diferentes redes. Un vínculo de interchasis lógico (ICL) cifrado conecta los nodos a través de una red enrutada. Los nodos participantes se respaldan entre sí para garantizar una tolerancia a fallos rápida y sincronizada en caso de falla del sistema o del hardware.
Puede operar la alta disponibilidad de múltiples nodos en modo activo-activo con soporte de múltiples grupos de redundancia de servicios (SRG). En este modo, algunos SRG permanecen activos en un nodo y otros permanecen activos en otro nodo.
La alta disponibilidad de múltiples nodos admite VPN IPsec en modo activo-activo con varios SRG (SRG1+). En este modo, puede establecer varios túneles activos desde ambos nodos, según la actividad de SRG. La alta disponibilidad multinodo establece un túnel IPsec y realiza intercambios de claves mediante la asociación de la dirección IP de terminación (que también identifica los túneles que terminan en ella) al SRG. Dado que diferentes SRG1+ pueden estar en estado activo o en estado de respaldo en cada uno de los dispositivos, la alta disponibilidad multinodo dirige el tráfico correspondiente de manera efectiva al SRG1 activo correspondiente. Dado que diferentes SRG pueden estar activos en diferentes nodos, los túneles que pertenecen a estos SRG surgen en ambos nodos de forma independiente.
Admitimos una configuración de dos nodos en la solución de alta disponibilidad multinodo.
Requisitos
En este ejemplo, se utilizan los siguientes componentes de hardware y software:
Dos firewalls de la serie SRX (los dispositivos compatibles son SRX5400, SRX5600 y SRX5800 con SPC3, IOC3, SCB3, SCB4 y RE3)
Junos OS versión 22.4R1
En este ejemplo, usamos dos plataformas de enrutamiento de la serie MX de Juniper Networks como enrutadores ascendentes y descendentes.
Antes de empezar
Configure el filtrado de firewall sin estado y la calidad del servicio (QoS) según sus requisitos de red y tenga políticas de seguridad adecuadas para administrar el tráfico en su red.
En una implementación típica de alta disponibilidad, tiene múltiples enrutadores y conmutadores en los lados norte y sur de la red. Para este ejemplo, estamos usando dos enrutadores en ambos lados de firewalls de la serie SRX. Asegúrese de haber configurado los enrutadores ascendentes y descendentes según los requisitos de su red.
Instale el paquete IKE de Junos en sus firewalls de la serie SRX mediante el
request system software add optional://junos-ike.tgzcomando. Eljunos-ikepaquete se incluye en los paquetes de software de Junos (versión 20.4R1 de Junos OS en adelante).
Topología
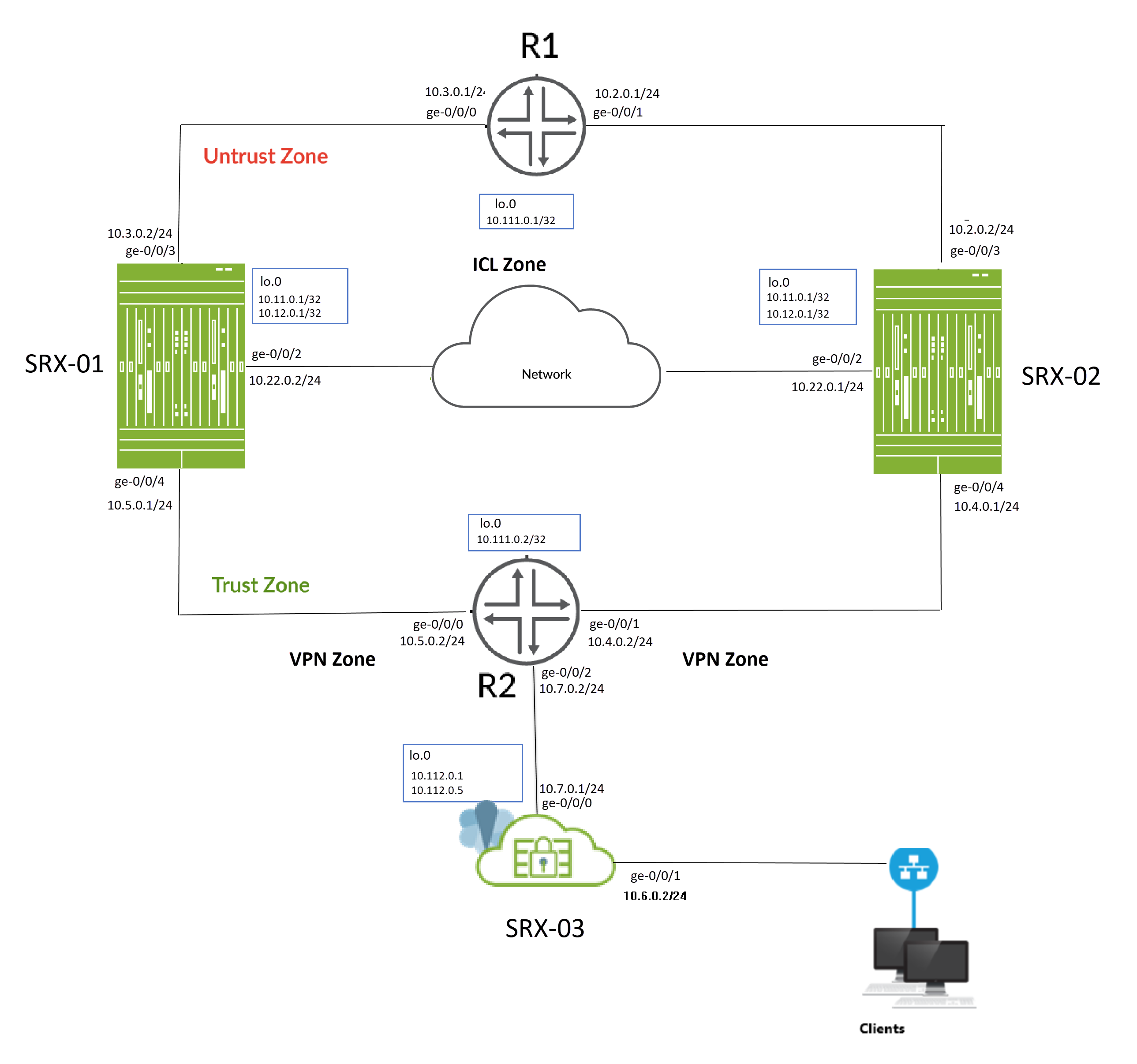
En la figura 1 , se muestra la topología utilizada en este ejemplo.
 de capa 3
de capa 3
Como se muestra en la topología, dos firewalls de la serie SRX (SRX-1 y SRX-2) están conectados a enrutadores adyacentes en el lado de confianza y no confianza formando una vecindad BGP. Un vínculo de interchasis lógico (ICL) cifrado conecta los nodos a través de una red enrutada. Los nodos se comunican entre sí mediante una dirección IP (dirección IP flotante) enrutable a través de la red.
El dispositivo SRX-03 actúa como un dispositivo par para la configuración de alta disponibilidad multinodo y establece túneles VPN IPsec con los dispositivos SRX-01 y SRX-02.
Realizará las siguientes tareas para crear una configuración de alta disponibilidad multinodo:
- Configure un par de firewalls de la serie SRX como nodos locales y pares mediante la asignación de ID.
- Configure los grupos de redundancia de servicios (SRG1 y SRG2).
- Configure una interfaz de circuito cerrado (lo0.0) para alojar la dirección IP flotante y comunicarse con la puerta de enlace par. El uso de la interfaz de circuito cerrado garantiza que, en cualquier punto dado, el tráfico de los enrutadores adyacentes se dirigirá hacia la dirección IP flotante (es decir, hacia el nodo activo).
- Configure los sondeos IP para la determinación de la actividad y el cumplimiento
- Configure una ruta de señal necesaria para el cumplimiento de la actividad y utilícela junto con la política de que la ruta existe.
- Configure un perfil VPN para el tráfico de alta disponibilidad (ICL) mediante IKEv2.
- Configurar las opciones de supervisión de BFD
- Configurar una política de enrutamiento y opciones de enrutamiento
- Configure interfaces y zonas según sus requisitos de red. Debe permitir servicios como IKE para el cifrado de vínculos y SSH para la sincronización de configuraciones como servicios del sistema de entrada de host en la zona de seguridad asociada con la ICL.
-
Cree una configuración de grupo para VPN IPsec en dispositivos SRX-01 y SRX-02 para configurar un túnel con el dispositivo par VPN (SRX-03). Los grupos de configuración permiten aplicar elementos comunes que se reutilizan dentro de la misma configuración.
- Configure las opciones de VPN IPsec para establecer túneles con el dispositivo SRX-03 y habilite la sincronización de la configuración de VPN IPsec en ambos dispositivos (SRX-01 y SRX-02) mediante la opción [groups].
- Configure el dispositivo par VPN con las opciones VPN VPN VPN.
Para el vínculo de interchasis (ICL), recomendamos la siguiente configuración:
-
En general, puede usar Ethernet agregada (AE) o un puerto Ethernet de ingresos en los firewalls de la serie SRX para configurar una conexión ICL. En este ejemplo, hemos usado puertos GE para la ICL. También configuramos una instancia de enrutamiento para la ruta ICL a fin de garantizar la máxima segmentación.
- No use los puertos de alta disponibilidad dedicados (puertos de control y estructura) si están disponibles en el firewall de la serie SRX).
- Conjunto UMT de 1514
- Permita los siguientes servicios en la zona de seguridad asociada con las interfaces usadas para ICL
-
IKE, alta disponibilidad, SSH
-
Protocolos según el protocolo de enrutamiento que necesite.
-
BFD para monitorear las rutas vecinas.
-
Puede configurar las siguientes opciones en SRG0 y SRG1+:
Puede configurar las siguientes opciones en SRG0 y SRG1:
-
SRG1: Ruta de señal activa/de respaldo, tipo de despliegue, prioridad de actividad, preferencia, dirección IP virtual (para despliegues de puerta de enlace predeterminados), sondeo de actividad y paquete de proceso en respaldo.
-
SRG1: Opciones de supervisión de BFD, supervisión de IP y supervisión de interfaces en SRG1.
-
SRG0: opciones de ruta de apagado en caso de error e instalación en caso de error.
Cuando configure las opciones de supervisión (BFD o IP o interfaz) en SRG1, se recomienda no configurar la opción de apagado en caso de error en SRG0.
-
SRG1: Ruta de señal activa/de respaldo, tipo de despliegue, prioridad de actividad, preferencia, dirección IP virtual (para despliegues de puerta de enlace predeterminados), sondeo de actividad y paquete de proceso en respaldo.
-
SRG1: Opciones de supervisión de BFD, supervisión de IP y supervisión de interfaces en SRG1.
-
SRG0: opciones de ruta de apagado en caso de error e instalación en caso de error.
Cuando configure las opciones de supervisión (BFD o IP o interfaz) en SRG1, se recomienda no configurar la opción de apagado en caso de error en SRG0.
En la tabla 1 se muestran los detalles de la configuración de interfaces que se utilizan en este ejemplo.
| interfaz | del dispositivo | Dirección IP | configurada para | |
|---|---|---|---|---|
| SRX-01 | lo0 | No confiar |
10.11.0.1/32 |
Dirección IP flotante Dirección de puerta de enlace IKE |
| 10.12.0.1/32 |
Dirección de puerta de enlace IKE |
|||
| GE-0/0/2 |
ICL |
10.22.0.2/24 |
Conexión de ICL |
|
| GE-0/0/4 |
Confianza |
10.5.0.1/24 |
Se conecta al enrutador R2 |
|
| GE-0/0/3 |
No confiar |
10.3.0.2/24 |
Se conecta al enrutador R1 |
|
| SRX-02 | lo0 |
No confiar |
10.12.0.1/32 |
Dirección IP flotante Dirección de puerta de enlace IKE |
| 10.11.0.1/32 |
Dirección de puerta de enlace IKE |
|||
| GE-0/0/2 |
ICL |
10.22.0.1/24 |
Conexión de ICL |
|
| GE-0/0/3 |
No confiar |
10.2.0.2/24 |
Se conecta al enrutador R1 |
|
| GE-0/0/4 |
Confianza |
10.4.0.1/24 |
Se conecta al enrutador R2 |
|
| SRX-03 | lo0 | No confiar |
10.112.0.1/32 |
Dirección de puerta de enlace IKE |
| 10.112.0.5/32 |
Dirección de puerta de enlace IKE |
|||
| GE-0/0/0 |
No confiar |
10.7.0.1/24 |
Se conecta al enrutador R2 |
|
| GE-0/0/2 |
Confianza |
10.6.0.2/24 |
Se conecta al dispositivo del cliente |
| Dirección IP de | la interfaz | deldispositivo | configurada para |
|---|---|---|---|
| R2 | lo0 | 10.111.0.2/32 |
Dirección de interfaz de circuito cerrado de R2 |
| GE-0/0/1 |
10.4.0.2/24 |
Se conecta a SRX-02 |
|
| GE-0/0/0 |
10.5.0.2/24 |
Se conecta a SRX-01 |
|
| GE-0/0/2 |
10.7.0.2/24 |
Se conecta a SRX-03 (dispositivo par VPN) |
|
| R1 | lo0 | 10.111.0.1/32 |
Dirección de interfaz de circuito cerrado de R1 |
| GE-0/0/0 |
10.3.0.1/24 |
Se conecta a SRX-01 |
|
| GE-0/0/1 |
10.2.0.1/24 |
Se conecta a SRX-02 |
Configuración
- Antes de empezar
- Configuración rápida de CLI
- Configuración
- Configuración (SRX-03) (dispositivo par VPN)
- Resultados (SRX-01)
- Resultados (SRX-02)
- Resultados (SRX-3) (dispositivo par VPN)
Antes de empezar
Se requiere el paquete IKE de Junos en sus firewalls de la serie SRX para la configuración de alta disponibilidad de múltiples nodos. Este paquete está disponible como un paquete predeterminado o como un paquete opcional en los firewalls de la serie SRX. Consulte Soporte para el paquete IKE de Junos para obtener más detalles.
Si el paquete no está instalado de forma predeterminada en el firewall de la serie SRX, utilice el siguiente comando para instalarlo. Necesita este paso para el cifrado ICL.
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
Configuración rápida de CLI
Para configurar rápidamente este ejemplo, copie los siguientes comandos, péguelos en un archivo de texto, elimine los saltos de línea, cambie los detalles necesarios para que coincidan con su configuración de red, copie y pegue los comandos en la CLI en el nivel de jerarquía y, luego, ingrese commit desde el [edit] modo de configuración.
Dispositivo SRX-01
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability peer-id 2 peer-ip 10.22.0.1 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 set chassis high-availability peer-id 2 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 1 set chassis high-availability services-redundancy-group 2 peer-id 2 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 200 set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.3.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.3.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.5.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.5.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
Dispositivo SRX-02
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability peer-id 1 peer-ip 10.22.0.2 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 1 liveness-detection minimum-interval 200 set chassis high-availability peer-id 1 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set chassis high-availability services-redundancy-group 2 peer-id 1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 1 set security ike proposal ICL_IKE_PROP description interchassisa_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.1/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.2.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.4.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 1 family inet6 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/24 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.2.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.2.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.4.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.4.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/24 next-hop 10.4.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.4.0.2
Dispositivo SRX-3
set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG1_IKE_PROP dh-group group14 set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG2_IKE_PROP dh-group group14 set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 set security ike gateway SRG1_IKE_GW1 external-interface lo0 set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 set security ike gateway SRG1_IKE_GW1 version v2-only set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 set security ike gateway SRG2_IKE_GW500 external-interface lo0 set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 set security ike gateway SRG2_IKE_GW500 version v2-only set security ipsec proposal SRG1_IPSEC_PROP protocol esp set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set security ipsec proposal SRG2_IPSEC_PROP protocol esp set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces st0.500 set security zones security-zone untrust interfaces ge-0/0/1.0 set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone trust host-inbound-traffic system-services ike set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/2.0 set interfaces ge-0/0/0 description trust set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 set interfaces ge-0/0/1 description untrust set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 set interfaces ge-0/0/2 description trust set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.112.0.1/32 set interfaces lo0 unit 0 family inet address 10.112.0.5/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 500 family inet set routing-options autonomous-system 100 set routing-options static route 10.4.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.5.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
En las siguientes secciones, se muestran los fragmentos de configuración en los enrutadores necesarios para configurar la configuración de alta disponibilidad multinodo en la red.
Enrutador R1
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.3.0.1/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.2.0.1/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.1/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.1/32 preferred set routing-options autonomous-system 100 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.2.0.1 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.2.0.2 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.3.0.1 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.3.0.2
Enrutador R2
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.5.0.2/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.4.0.2/24 set interfaces ge-0/0/2 description srx-3 set interfaces ge-0/0/2 unit 0 family inet address 10.7.0.2/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.2/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.2/32 preferred set routing-options autonomous-system 100 set routing-options static route 10.112.0.0/24 next-hop 10.7.0.1 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.4.0.2 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.4.0.1 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.5.0.2 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.5.0.1
Configuración
Procedimiento paso a paso
Mostramos la configuración de SRX-01 en el procedimiento paso a paso.
En el ejemplo siguiente, debe explorar por varios niveles en la jerarquía de configuración. Para obtener instrucciones sobre cómo hacerlo, consulte Uso del editor de CLI en el modo de configuración de la Guía del usuario de CLI.
Configure Interfaces.
[edit] user@srx-1# set interfaces ge-0/0/2 description inter_chassis_link user@srx-1# set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 user@srx-1# set interfaces ge-0/0/3 description untrust user@srx-1# set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 user@srx-1# set interfaces ge-0/0/4 description trust user@srx-1# set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24
Utilice las interfaces ge-0/0/3 y ge-0/0/4 para conectarse a los enrutadores ascendentes y descendentes, y utilice la interfaz ge-0/0/2 para configurar la ICL.
Configure las interfaces circuito cerrado.
[edit] user@srx-1# set interfaces lo0 apply-groups-except global user@srx-1# set interfaces lo0 description untrust user@srx-1# set interfaces lo0 unit 0 family inet address 10.11.0.1/32 user@srx-1# set interfaces lo0 unit 0 family inet address 10.12.0.1/32 user@srx-1# set interfaces st0 unit 1
Asigne las direcciones IP 10.11.0.1 y 10.12.0.1 a la interfaz de circuito cerrado. Usaremos 10.11.0.1 como dirección IP flotante y 10.12.0.1 como dirección de puerta de enlace IKE.
Configure zonas de seguridad, asigne interfaces a las zonas y especifique los servicios del sistema permitidos para las zonas de seguridad.
[edit] user@srx-1# set security zones security-zone vpn host-inbound-traffic system-services ike user@srx-1# set security zones security-zone vpn host-inbound-traffic protocols all user@srx-1# set security zones security-zone vpn interfaces st0.1 user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ike user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ping user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone untrust interfaces lo0.0 user@srx-1# set security zones security-zone untrust interfaces ge-0/0/3.0 user@srx-1# set security zones security-zone trust host-inbound-traffic system-services all user@srx-1# set security zones security-zone trust host-inbound-traffic protocols all user@srx-1# set security zones security-zone trust interfaces ge-0/0/4.0 user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ike user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ping user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services high-availability user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ssh user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone icl_zone interfaces ge-0/0/2.0
Asigne a las interfaces ge-0/0/3 y ge-0/0/4 las zonas de confianza y no confianza respectivamente. Asigne la interfaz lo0.0 a la zona de no confianza para conectarse a través de la red IP. Asigne la interfaz ge-0/0/2 a la zona ICL. Esta zona se usa para configurar la ICL. Asigne la interfaz de túnel seguro a la zona de seguridad VPN.
- Configure los detalles del nodo local y del nodo par, como el ID del nodo, las direcciones lP del nodo local y del nodo par, y la interfaz para el nodo par.
[edit] user@srx-1# set chassis high-availability local-id 1 user@srx-1# set chassis high-availability local-id local-ip 10.22.0.2 user@srx-1# set chassis high-availability peer-id 2 peer-ip 10.22.0.1 user@srx-1# set chassis high-availability peer-id 2 interface ge-0/0/2.0
Usará la interfaz ge-0/0/2 para comunicarse con el nodo par mediante la ICL.
Adjunte el perfil VPN IPsec IPSEC_VPN_ICL al nodo par.
[edit] user@srx-1# set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN
Necesitará esta configuración para establecer un vínculo ICL seguro entre los nodos.
Configure las opciones de protocolo de detección de reenvío bidireccional (BFD) para el nodo par.
[edit] user@srx-1# set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 user@srx-1# set chassis high-availability peer-id 2 liveness-detection multiplier 3
-
Configure los grupos de redundancia de servicios SRG1 y SRG2.
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 deployment-type routing user@srx-1# set chassis high-availability services-redundancy-group 1 peer-id 2 user@srx-1# set chassis high-availability services-redundancy-group 2 peer-id 2
Configuración de los parámetros de determinación de la actividad SRG1 y SRG2.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.11.0.1
Utilice la dirección IP flotante como dirección IP de origen (10.11.0.1 para SRG1 y 10.12.0.1 para SRG2) y las direcciones IP de los enrutadores ascendentes como dirección IP de destino (10.111.0.1) para la sonda de determinación de actividad.
Puede configurar hasta 64 direcciones IP para el monitoreo de IP y el sondeo de actividad. El total de 64 direcciones IP es la suma del número de direcciones IPv4 e IPv6)
Configure los parámetros de supervisión de BFD para SRG1 y SRG2 a fin de detectar errores en la red.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4
Configure una ruta de señal activa necesaria para el cumplimiento de la actividad.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 user@srx-1# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 user@srx-1# set chassis high-availability services-redundancy-group 1 preemption user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-priority 1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 user@srx-1# set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 user@srx-1# set chassis high-availability services-redundancy-group 2 preemption user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-priority 200
Nota: Debe especificar la ruta de señal activa junto con la política route-exists en la instrucción policy-options. Cuando configure laactive-signal-routecondición withif-route-exists, el módulo de alta disponibilidad agrega esta ruta a la tabla de enrutamiento.Cree una lista de prefijos IP incluyendo la dirección local de la puerta de enlace de IKE y asocie la lista de prefijos IP a SRG1 y SRG2:
SRG1
[edit] user@srx-1# set policy-options prefix-list SRG1_PFX 10.11.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX
SRG2
[edit] user@srx-1# set policy-options prefix-list SRG2_PFX 10.12.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX
Esta configuración ancla un determinado túnel VPN IPsec a un dispositivo de seguridad determinado.
Habilite el servicio VPN IPsec en SRG1 y SRG2.
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 managed-services ipsec user@srx-1# set chassis high-availability services-redundancy-group 2 managed-services ipsec
Configure las opciones de VPN de VPN IPSec para la ICL.
Defina la configuración del intercambio de claves por red (IKE). Una configuración de IKE define los algoritmos y las claves que se usan para establecer una conexión segura.
[edit] user@srx-1# set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel user@srx-1# set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys user@srx-1# set security ike proposal ICL_IKE_PROP dh-group group14 user@srx-1# set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 user@srx-1# set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc user@srx-1# set security ike proposal ICL_IKE_PROP lifetime-seconds 300 user@srx-1# set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel user@srx-1# set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP user@srx-1# set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" user@srx-1# set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL user@srx-1# set security ike gateway ICL_IKE_GW version v2-only
Para la función de alta disponibilidad multinodo, debe configurar la versión de IKE como
v2-only-
Especifique el protocolo de propuesta de IPsec y el algoritmo de cifrado. Especifique las opciones de IPsec para crear un túnel IPsec entre dos dispositivos participantes para proteger la comunicación VPN.
[edit] user@srx-1# set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel user@srx-1# set security ipsec proposal ICL_IPSEC_PROP protocol esp user@srx-1# set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm user@srx-1# set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 user@srx-1# set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel user@srx-1# set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL
ha-link-encryptionse cifra la ICL para garantizar un flujo de tráfico de alta disponibilidad entre los nodos.Se debe mencionar el mismo nombre de VPN ICL_IPSEC_VPN vpn_profile en la
set chassis high-availability peer-id <id> vpn-profile vpn_profileconfiguración.
Configure la política de seguridad.
[edit] user@srx-1# set security policies default-policy permit-all
En este ejemplo, hemos configurado una política para permitir todo el tráfico. Le recomendamos encarecidamente que cree políticas de seguridad según los requisitos de su red para permitir el tráfico permitido por la política de su organización y denegar el resto del tráfico. Hemos usado la directiva predeterminada para el propósito de demostración solo en este ejemplo.
Configure las opciones de enrutamiento.
[edit] user@srx-1# set routing-options autonomous-system 100 user@srx-1# set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 user@srx-1# set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
Configure las opciones de directiva.
[edit] user@srx-1# set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term default then reject user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0
Configure la ruta de señal activa 10.39.1.1 (SRG1) y 10.49.1.1 (SRG2) con la condición de coincidencia de ruta (
if-route-exists). La alta disponibilidad multinodo agrega esta ruta a la tabla de enrutamiento cuando el nodo se mueve al rol activo. El nodo también comienza a anunciar la ruta de preferencia más alta. Configure la ruta de señal de respaldo (10.39.1.2 y 10.49.1.2) para anunciar el nodo de respaldo con una prioridad media. En caso de que se produzca algún error, el vínculo de alta disponibilidad deja de funcionar y el nodo activo actual libera su función principal y elimina la ruta de señal activa. Ahora, el nodo de respaldo detecta la condición a través de sus sondeos y pasa a la función activa. La preferencia de ruta se intercambia para dirigir todo el tráfico al nuevo nodo activoConfigure las opciones de sesiones de emparejamiento de BFD y especifique los temporizadores de detección de vida.
[edit] user@srx-1# set protocols bgp group trust type internal user@srx-1# set protocols bgp group trust local-address 10.3.0.2 user@srx-1# set protocols bgp group trust export mnha-route-policy user@srx-1# set protocols bgp group trust local-as 100 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group trust neighbor 10.3.0.1 user@srx-1# set protocols bgp group untrust type internal user@srx-1# set protocols bgp group untrust local-address 10.5.0.1 user@srx-1# set protocols bgp group untrust export mnha-route-policy user@srx-1# set protocols bgp group untrust local-as 100 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group untrust neighbor 10.5.0.2
Configuración de VPN IPsec (SRX-1 y SRX-2)
Siga estos pasos para configurar la conexión VPN IPsec con el firewall par de la serie SRX. En este ejemplo, colocará todas las instrucciones de configuración de VPN IPsec dentro de un grupo de configuración de JUNOS denominado vpn_config.
- Cree un grupo
vpn_configde configuración en la parte superior de la configuración y configure los detalles específicos de VPN IPsec.[edit] set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 500 family inet
Incluya la instrucción apply-groups en la configuración para heredar las instrucciones del grupo de configuración vpn_config,
[edit] user@srx-1# set apply-groups vpn_config
Configuración (SRX-03) (dispositivo par VPN)
Procedimiento paso a paso
Cree la propuesta de ICR.
[edit] user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG1_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG2_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600
Defina las políticas de ICR.
[edit] user@srx-3# set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP user@srx-3# set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" user@srx-3# set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP user@srx-3# set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123"
Cree una puerta de enlace ICR, defina la dirección, especifique las interfaces externas y la versión.
[edit] user@srx-3# set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 user@srx-3# set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 external-interface lo0 user@srx-3# set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 version v2-only user@srx-3# set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 user@srx-3# set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 user@srx-3# set security ike gateway SRG2_IKE_GW500 external-interface lo0 user@srx-3# set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 user@srx-3# set security ike gateway SRG2_IKE_GW500 version v2-only
Cree propuestas IPsec.
[edit] user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800
Cree políticas IPsec.
[edit] user@srx-3# set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP user@srx-3# set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP
Especifique las referencias de propuesta de IPsec (puerta de enlace de IKE, política de IPsec, interfaz para enlazar y selectores de tráfico).
[edit] user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately
Cree una política de seguridad.
[edit] user@srx-3# set security policies default-policy permit-all
En este ejemplo, hemos configurado una política para permitir todo el tráfico. Le recomendamos encarecidamente que cree políticas de seguridad según los requisitos de su red para permitir el tráfico permitido por la política de su organización y denegar el resto del tráfico. Hemos usado la directiva predeterminada para el propósito de demostración solo en este ejemplo.
Configure las interfaces.
[edit] user@srx-3# set interfaces ge-0/0/0 description trust user@srx-3# set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 user@srx-3# set interfaces ge-0/0/1 description untrust user@srx-3# set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 user@srx-3# set interfaces ge-0/0/2 description trust user@srx-3# set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 user@srx-3# set interfaces lo0 description untrust user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.1/32 user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.5/32 user@srx-3# set interfaces st0 unit 1 family inet user@srx-3# set interfaces st0 unit 500 family inet
Defina zonas de seguridad y agregue interfaces.
[edit] user@srx-3# set security zones security-zone untrust host-inbound-traffic system-services all user@srx-3# set security zones security-zone untrust host-inbound-traffic protocols all user@srx-3# set security zones security-zone untrust interfaces st0.1 user@srx-3# set security zones security-zone untrust interfaces lo0.0 user@srx-3# set security zones security-zone untrust interfaces st0.500 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/1.0 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/0.0 user@srx-3# set security zones security-zone trust host-inbound-traffic system-services all user@srx-3# set security zones security-zone trust host-inbound-traffic protocols all user@srx-3# set security zones security-zone trust interfaces ge-0/0/2.0
Configure las rutas estáticas.
[edit] user@srx-3# set routing-options autonomous-system 100 user@srx-3# set routing-options static route 10.4.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.5.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
Resultados (SRX-01)
Desde el modo de configuración, ingrese los siguientes comandos para confirmar la configuración.
Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración de este ejemplo para corregirla.
[edit]
user@srx-1# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-1# show chassis high-availability
local-id 1 local-ip 10.22.0.2;
peer-id 2 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
services-redundancy-group 2 {
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
[edit]
user@srx-1# show security ike
proposal ICL_IKE_PROP {
description interchassis_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-1# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-1# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/16 orlonger;
10.1.0.0/16 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/16 orlonger;
10.8.0.0/16 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-1# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/16 next-hop 10.5.0.2;
route 10.112.0.0/24 next-hop 10.5.0.2;
}
[edit]
user@srx-1# show security zones
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-1# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.3.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.5.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1;
}
Cuando termine de configurar el dispositivo, ingrese commit desde el modo de configuración.
Resultados (SRX-02)
Desde el modo de configuración, ingrese los siguientes comandos para confirmar la configuración. Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración de este ejemplo para corregirla.
[edit]
user@srx-2# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-2# show chassis high-availability
local-id 2 local-ip 10.22.0.1;
peer-id 1 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
services-redundancy-group 2 {
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
[edit]
user@srx-2# show security ike
proposal ICL_IKE_PROP {
description interchassisa_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-2# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-2# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/24 orlonger;
10.1.0.0/24 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/24 orlonger;
10.8.0.0/24 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-2# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/24 next-hop 10.4.0.2;
route 10.112.0.0/24 next-hop 10.4.0.2;
}
[edit]
user@srx-2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-2# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.2.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.4.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1 {
family inet;
}
}
Cuando termine de configurar el dispositivo, ingrese commit desde el modo de configuración.
user@host# commit warning: High Availability Mode changed, please reboot the device to avoid undesirable behavior commit complete
Resultados (SRX-3) (dispositivo par VPN)
Desde el modo de configuración, ingrese los siguientes comandos para confirmar la configuración. Si el resultado no muestra la configuración deseada, repita las instrucciones de configuración de este ejemplo para corregirla.
[edit]
user@srx-3# show security ike
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.11.0.1;
external-interface lo0;
local-address 10.112.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.12.0.1;
external-interface lo0;
local-address 10.112.0.5;
version v2-only;
}
[edit]
user@srx-3# show security ipsec
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.7.0.2/32;
remote-ip 10.1.0.2/32;
}
establish-tunnels immediately;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts1 {
local-ip 10.9.0.2/32;
remote-ip 10.8.0.2/32;
}
establish-tunnels immediately;
}
[edit]
user@srx-3# show routing-options
autonomous-system 100;
static {
route 10.4.0.0/24 next-hop 10.7.0.2;
route 10.5.0.0/24 next-hop 10.7.0.2;
route 10.11.0.0/24 next-hop 10.7.0.2;
route 10.12.0.0/24 next-hop 10.7.0.2;
route 10.111.0.1/32 next-hop 10.7.0.2;
route 10.111.0.2/32 next-hop 10.7.0.2;
}
[edit]
user@srx-3# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
lo0.0;
st0.500;
ge-0/0/1.0;
ge-0/0/0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-3# show interfaces
ge-0/0/0 {
description trust;
unit 0 {
family inet {
address 10.7.0.1/24;
}
}
}
ge-0/0/1 {
description untrust;
unit 0 {
family inet {
address 10.6.0.2/24;
}
}
}
ge-0/0/2 {
description trust;
unit 0 {
family inet {
address 10.9.0.1/24;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.112.0.1/32;
address 10.112.0.5/32;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 500 {
family inet;
}
}
Cuando termine de configurar el dispositivo, ingrese commit desde el modo de configuración.
Verificación
Confirme que la configuración funcione correctamente.
- Compruebe los detalles de alta disponibilidad de multinodo
- Compruebe los detalles de alta disponibilidad de multinodo
- Compruebe el estado del nodo par de alta disponibilidad de múltiples nodos
- Comprobar grupos de redundancia del servicio de alta disponibilidad multinodo
- Verificar el estado de cifrado del vínculo de interchasis (ICL)
- Verificar estadísticas de túnel de cifrado de vínculos
- Verificar pares activos del vínculo de interchasis
- Confirmar el estado de VPN
- Mostrar detalles de la asociación de seguridad IPsec
- Mostrar pares activos por SRG
- Mostrar el prefijo IP a la asignación de SRG
- Muestra la información de la sesión del BGP.
Compruebe los detalles de alta disponibilidad de multinodo
Propósito
Vea y verifique los detalles de la configuración de alta disponibilidad multinodo configurada en su dispositivo de seguridad.
Acción
Desde el modo operativo, ejecute el siguiente comando:
En SRX-1
user@srx-01> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
En SRX-2
user@srx-02> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.1
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Significado
Compruebe estos detalles en el resultado del comando:
Detalles del nodo local y del nodo par, como la dirección IP y el ID.
El campo
Encrypted: YESindica que el tráfico está protegido.El campo
Deployment Type: ROUTINGindica una configuración de modo de capa 3, es decir, la red tiene enrutadores en ambos lados.El campo
Services Redundancy Group: 1eServices Redundancy Group: 2indicar el estado de SRG1 y SRG2 (activo o de respaldo) en ese nodo.
Compruebe los detalles de alta disponibilidad de multinodo
Propósito
Vea y verifique los detalles de la configuración de alta disponibilidad multinodo configurada en su dispositivo de seguridad.
Acción
Desde el modo operativo, ejecute el siguiente comando:
En SRX-01
user@srx-01> show chassis high-availability information detail
Node level Information:
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
HA Peer Conn events:
Jan 31 00:55:19.249 : HA Peer 180.100.1.1 BFD conn came up
Cold Synchronization:
Status:
Cold synchronization completed for: N/A
Cold synchronization failed for: N/A
Cold synchronization not known for: N/A
Current Monitoring Weight: 0
Progress:
CS Prereq 1 of 1 SPUs completed
1. if_state sync 1 SPUs completed
2. ha peer conn 1 SPUs completed
3. policy data sync 1 SPUs completed
4. cp ready 1 SPUs completed
5. VPN data sync 1 SPUs completed
6. IPID data sync 1 SPUs completed
7. All SPU ready 1 SPUs completed
8. AppID ready 1 SPUs completed
9. Tunnel Sess ready 1 SPUs completed
CS RTO sync 1 of 1 SPUs completed
CS Postreq 1 of 1 SPUs completed
Statistics:
Number of cold synchronization completed: 0
Number of cold synchronization failed: 0
Events:
Jan 31 00:55:24.616 : Cold sync for PFE is Post-req check in process
Jan 31 00:55:25.615 : Cold sync for PFE is Completed
SPU monitoring:
Status: Enabled
Current monitoring weight: 0
Statistics:
SPU up count: 1
NPC up count: 0
SPU down count: 0
NPC down count: 0
Chassis info processing error count: 0
Loopback Information:
PIC Name Loopback Nexthop Mbuf
-------------------------------------------------
Success Success Success
Hardware monitoring:
Status:
Activation status: Enabled
Ctrl Plane Hardware errors: 0
Data Plane Hardware errors: 0
SRGS Information:
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: ACTIVE
Last Advertised Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.347 : SRG[1] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:56:33.046 : SRG[1] state HOLD -> BACKUP, Reason: Peer state Active received
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:12.695 : SRG[1] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
SRGS Information:
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: BACKUP
Last Advertised Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.439 : SRG[2] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:55:24.263 : SRG[2] state HOLD -> ACTIVE, Reason: Local Priority Higher
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:13.698 : SRG[2] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
Significado
Compruebe estos detalles en el resultado del comando:
El campo
Services: [ IPSEC ]indica la VPN IPSec asociada para cada SRG.Los campos
BFD Monitoring,Interface Monitoring,Split-brain Prevention Probe Infomuestran detalles de monitoreo.Los campos
Cold Synchronization,SRG State Change Eventsproporcionan detalles sobre el estado actual y los cambios recientes.El campo
Services Redundancy Group: 1eServices Redundancy Group: 2indicar el estado de SRG1 y SRG2 (activo o de respaldo) en ese nodo.
En la salida del comando, las direcciones IP como IP 180.100.1.2 se generan internamente mediante Junos OS y estas direcciones no interfieren con las tablas de enrutamiento.
Compruebe el estado del nodo par de alta disponibilidad de múltiples nodos
Propósito
Vea y verifique los detalles del nodo par.
Acción
Desde el modo operativo, ejecute el siguiente comando en SRX-01 y SRX-02:
SRX-01
user@srx-01> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
SRX-02
user@srx-02> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.1
Internal Peer-IP: 180.100.1.2
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 6 4
SRG Status Ack 4 4
Attribute Msg 2 1
Attribute Ack 1 1
Significado
Compruebe estos detalles en el resultado del comando:
Detalles del nodo par, como la interfaz utilizada, la dirección IP y el ID
Estado de cifrado, estado de conexión y estado de sincronización en frío
Estadísticas de paquetes en todo el nodo.
Comprobar grupos de redundancia del servicio de alta disponibilidad multinodo
Propósito
Compruebe que los SRG estén configurados y funcionen correctamente.
Acción
Desde el modo operativo, ejecute el siguiente comando en ambos dispositivos de seguridad:
SRG1 en SRX-02
user@srx-02> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRG2 en SRX-02
user@srx-02> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
SRG1 en SRX-01
user@srx-01> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRG2 en SRX-01
user@srx-01> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
Significado
Compruebe estos detalles en el resultado del comando:
Detalles del nodo emparejado, como el tipo de despliegue, el estado, las rutas de señal activas y de respaldo.
Sonda de prevención de cerebro dividido, monitoreo de IP y estado de monitoreo de BFD.
Tabla de prefijos IP asociada.
Verificar el estado de cifrado del vínculo de interchasis (ICL)
Propósito
Verifique el estado del vínculo de interchasis (ICL).
Acción
Ejecute el comando siguiente en SRX-01:
user@srx-01> show security ipsec security-associations ha-link-encryption Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <495002 ESP:aes-gcm-256/aes256-gcm 0x0008d9c7 236/ unlim - root 500 10.22.0.1 >495002 ESP:aes-gcm-256/aes256-gcm 0x0001a573 236/ unlim - root 500 10.22.0.1
user@srx-01> show security ike security-associations ha-link-encryption Index State Initiator cookie Responder cookie Mode Remote Address 16776938 UP 9f8fe46ce3be92f8 44e6b3fd74cc9294 IKEv2 10.22.0.1
user@srx-01> show security ipsec security-associations ha-link-encryption detail
ID: 495002 Virtual-system: root, VPN Name: ICL_IPSEC_VPN
Local Gateway: 10.22.0.2, Remote Gateway: 10.22.0.1
Traffic Selector Name: __ICL_IPSEC_VPN__multi_node__
Local Identity: ipv4(180.100.1.2-180.100.1.2)
Remote Identity: ipv4(180.100.1.1-180.100.1.1)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: No
PFS group: N/A
SRG ID: 0
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.16000, Policy-name: ICL_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
HA Link Encryption Mode: Multi-Node
Location: FPC -, PIC -, KMD-Instance -
Anchorship: Thread -
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x0008d9c7, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
Direction: outbound, SPI: 0x0001a573, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
Significado
La salida del comando proporciona la siguiente información:
La puerta de enlace local y los detalles de la puerta de enlace remota.
El par SA IPsec para cada subproceso de la PIC.
Modo de cifrado de vínculo con alta disponibilidad (como se muestra en la línea siguiente):
HA Link Encryption Mode: Multi-NodeAlgoritmos de autenticación y cifrado utilizados
El rango de IP (180.100.1.x) que se muestra en la salida del comando sirve como selector de tráfico IPsec de ICL. El sistema asigna dinámicamente este rango de IP, y es fundamental no alterarlo ni modificarlo. Además, BFD (detección de reenvío bidireccional) se habilitará automáticamente para el rango IP 180.x.x.x más amplio.
Verificar estadísticas de túnel de cifrado de vínculos
Propósito
Compruebe las estadísticas del túnel de cifrado de vínculos en los nodos activos y de respaldo.
Acción
Ejecute el comando siguiente en SRX-01:
user@srx-01> show security ipsec statistics ha-link-encryption ESP Statistics: Encrypted bytes: 106294156 Decrypted bytes: 51961287 Encrypted packets: 979531 Decrypted packets: 989651 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Si ve problemas de pérdida de paquetes en una VPN, puede ejecutar el show security ipsec statistics ha-link-encryption comando varias veces para comprobar que los contadores de paquetes cifrados y descifrados se incrementan. También debe comprobar si el resto de los contadores de errores se incrementan.
Utilice el clear security ipsec security-associations ha-link-encryption comando para borrar todas las estadísticas de IPsec.
Verificar pares activos del vínculo de interchasis
Propósito
Vea solo los pares activos de ICL, pero no los pares activos de IKE regulares.
Acción
Ejecute los siguientes comandos en dispositivos SRX-01 y SRX-02:
SRX-1
user@srx-01> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.1 500 10.22.0.1 not available 0.0.0.0
SRX-2
user@srx-02> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.2 500 10.22.0.2 not available 0.0.0.0
Significado
La salida del comando muestra solo el par activo de la ICL con detalles como las direcciones del par y los puertos que utiliza el par activo.
Confirmar el estado de VPN
Propósito
Confirme el estado de VPN comprobando el estado de cualquier asociación de seguridad de IKE en el nivel de SRG.
Acción
Ejecute los siguientes comandos en SRX-1, SRX-2 y SRX-3 (dispositivo par VPN):
SRX-01
user@srx-01> show security ike security-associations srg-id 1
Index State Initiator cookie Responder cookie Mode Remote Address
16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-01> show security ike security-associations srg-id 2
Index State Initiator cookie Responder cookie Mode Remote Address
33554536 UP 9944aaf1ab914b42 15cef0da496bdd92 IKEv2 10.112.0.5
SRX-02
user@srx-02> show security ike security-associations srg-id 1 Index State Initiator cookie Responder cookie Mode Remote Address 16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-02> show security ike security-associations srg-id 2 Index State Initiator cookie Responder cookie Mode Remote Address 33554534 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.112.0.5
SRX-3 (dispositivo par VPN)
user@srx-03> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 5929032 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.12.0.1 5929033 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.11.0.1
Significado
El resultado indica que:
- Direcciones IP de los pares remotos.
- El estado que aparece ACTIVO para ambos pares remotos indica la asociación correcta del establecimiento de la fase 1.
- La dirección IP del par remoto, la política de IKE y las interfaces externas son correctas.
Mostrar detalles de la asociación de seguridad IPsec
Propósito
Muestra los detalles de SA de IPsec individuales identificados por los ID de SRG.
Acción
Ejecute el comando siguiente en los firewalls de la serie SRX:
SRX-1
user@srx-01> show security ipsec security-associations srg-id 1 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1210/ unlim - root 500 10.112.0.1 >17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1210/ unlim - root 500 10.112.0.1
user@srx-01> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1382/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1382/ unlim - root 500 10.112.0.5
SRX-02
user@srx-02> show security ipsec security-associations srg-id 1
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1286/ unlim - root 500 10.112.0.1
>17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1286/ unlim - root 500 10.112.0.1
user@srx-02> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1461/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1461/ unlim - root 500 10.112.0.5
SRX-03
user@srx-03> show security ipsec security-associations
Total active tunnels: 2 Total Ipsec sas: 2
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<67108865 ESP:aes-cbc-256/sha256 6d1e9c89 1392/ unlim - root 500 10.11.0.1
>67108865 ESP:aes-cbc-256/sha256 c50520d4 1392/ unlim - root 500 10.11.0.1
<67108866 ESP:aes-cbc-256/sha256 f41d091c 1570/ unlim - root 500 10.12.0.1
>67108866 ESP:aes-cbc-256/sha256 9feb290c 1570/ unlim - root 500 10.12.0.1
Significado
El resultado muestra el estado de la VPN.
Mostrar pares activos por SRG
Propósito
Muestra la lista de pares activos conectados con direcciones de pares y puertos que están utilizando.
Acción
Ejecute los siguientes comandos en los firewalls de la serie SRX:
SRX-01
user@srx-01> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-01> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
SRX-02
user@srx-02> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-02> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
Significado
El resultado muestra la lista de dispositivos conectados con detalles sobre las direcciones de los pares y los puertos utilizados.
Mostrar el prefijo IP a la asignación de SRG
Propósito
Muestra el prefijo IP a la información de asignación de SRG.
Acción
Ejecute el siguiente comando en un dispositivo SRX-01.
user@srx-01> show chassis high-availability prefix-srgid-table
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
2 10.12.0.0/24 default
Significado
El resultado muestra los prefijos de dirección IP asignados a SRG en la configuración.
Muestra la información de la sesión del BGP.
Propósito
Muestra información resumida sobre BGP y sus vecinos para determinar si se reciben rutas de los pares.
Acción
Ejecute los siguientes comandos en los firewalls de la serie SRX:
Dispositivo SRX-1
user@srx-01> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.3.0.1 100 37 40 0 0 15:43 Establ
inet.0: 0/0/0/0
10.5.0.2 100 37 40 0 0 15:42 Establ
inet.0: 0/0/0/0
Dispositivo SRX-2
user@srx-02> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn St ate|#Active/Received/Accepted/Damped...
10.2.0.1 100 842 846 0 0 6:18:40 Es tabl
inet.0: 0/0/0/0
10.4.0.2 100 842 846 0 0 6:18:42 Es tabl
inet.0: 0/0/0/0
Significado
El resultado muestra que la sesión BGP está establecida y que los pares están intercambiando mensajes de actualización.
