예: 레이어 3 네트워크에서 액티브-액티브 멀티노드 고가용성으로 IPSec VPN 구성
이 예는 액티브-액티브 멀티노드 고가용성 설정을 위해 IPsec VPN을 구성하고 확인하는 방법을 보여줍니다.
개요
멀티노드 고가용성에서는 참여하는 SRX 시리즈 방화벽이 레이어 3 네트워크에서 독립적인 노드로 작동합니다. 노드는 서로 다른 네트워크에 속한 인접 인프라에 연결됩니다. 암호화된 논리적 섀시 간 링크(ICL)는 라우팅된 네트워크를 통해 노드를 연결합니다. 참여 노드는 시스템 또는 하드웨어 장애 발생 시 빠른 동기화된 페일오버를 보장하기 위해 서로 백업합니다.
멀티노드 고가용성은 여러 서비스 중복 그룹(SRG)을 지원하는 액티브-액티브 모드로 운영할 수 있습니다. 이 모드에서 일부 SRG는 한 노드에서 활성 상태로 유지되고 일부 SRG는 다른 노드에서 활성 상태로 유지됩니다.
멀티노드 고가용성은 여러 SRG(SRG1+)를 사용하여 액티브-액티브 모드에서 IPsec VPN을 지원합니다. 이 모드에서는 SRG 활성에 따라 두 노드 모두에서 여러 활성 터널을 설정할 수 있습니다. 멀티노드 고가용성은 IPsec 터널을 설정하고 종료 IP 주소(끝나는 터널도 식별함)를 SRG에 연결하여 키 교환을 수행합니다. 서로 다른 SRG1+가 각 디바이스에서 활성 상태이거나 백업 상태일 수 있기 때문에 멀티노드 고가용성은 일치하는 트래픽을 해당 활성 SRG1로 효과적으로 조정합니다. 서로 다른 SRG가 서로 다른 노드에서 활성화될 수 있으므로 이러한 SRG에 속하는 터널은 두 노드에서 독립적으로 작동합니다.
멀티노드 고가용성 솔루션에서는 2노드 구성을 지원합니다.
요구 사항
이 예에서 사용되는 하드웨어 및 소프트웨어 구성 요소는 다음과 같습니다.
2개의 SRX 시리즈 방화벽(지원되는 디바이스는 SRX5400, SRX5600 및 SRX5800(SPC3, IOC3, SCB3, SCB4 및 RE3))
Junos OS 릴리스 22.4R1
이 예시에서는 두 개의 주니퍼 네트웍스 MX 시리즈 라우팅 플랫폼을 업스트림/다운스트림 라우터로 사용했습니다.
시작하기 전에
네트워크 요구 사항에 따라 무상태 방화벽 필터링 및 QoS(Quality of Service)를 구성하고 네트워크의 트래픽을 관리하기 위한 적절한 보안 정책을 갖추어야 합니다.
일반적인 고가용성 구축에서는 네트워크의 노스바운드 및 사우스바운드 양에 여러 라우터와 스위치가 있습니다. 이 예시에서는 SRX 시리즈 방화벽의 양쪽에 있는 두 개의 라우터를 사용하고 있습니다. 네트워크 요구 사항에 따라 업스트림 및 다운스트림 라우터를 구성했는지 확인합니다.
명령을
request system software add optional://junos-ike.tgz사용하여 SRX 시리즈 방화벽에 Junos IKE 패키지를 설치합니다. 이junos-ike패키지는 Junos 소프트웨어 패키지(Junos OS 릴리스 20.4R1 이상)에 포함되어 있습니다.
토폴로지
그림 1 은 이 예에서 사용되는 토폴로지를 보여줍니다.
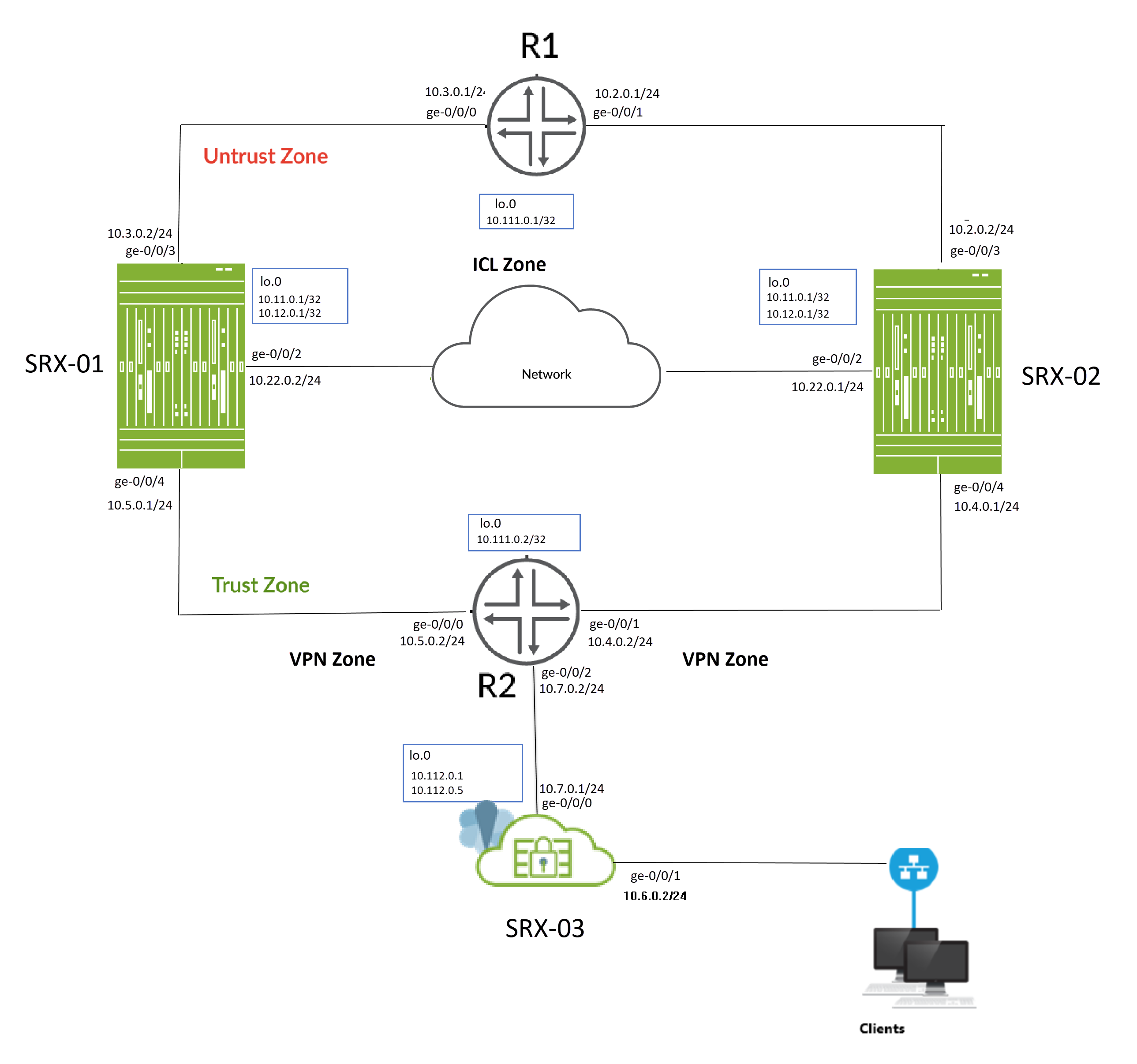 의 멀티노드 고가용성
의 멀티노드 고가용성
토폴로지에서 볼 수 있듯이, 두 개의 SRX 시리즈 방화벽(SRX-1 및 SRX-2)은 신뢰 및 언트러스트 측의 인접 라우터에 연결되어 BGP 인접 관계를 형성합니다. 암호화된 논리적 섀시 간 링크(ICL)는 라우팅된 네트워크를 통해 노드를 연결합니다. 노드는 네트워크를 통해 라우팅 가능한 IP 주소(유동 IP 주소)를 사용하여 서로 통신합니다.
SRX-03 디바이스는 멀티노드 고가용성 설정의 피어 디바이스 역할을 하며 SRX-01 및 SRX-02 디바이스와 IPsec VPN 터널을 설정합니다.
다음 작업을 수행하여 멀티노드 고가용성 설정을 빌드합니다.
- ID를 할당하여 한 쌍의 SRX 시리즈 방화벽을 로컬 및 피어 노드로 구성합니다.
- 서비스 중복 그룹(SRG1 및 SRG2)을 구성합니다.
- 유동 IP 주소를 호스팅하고 피어 게이트웨이에 도달하기 위해 루프백 인터페이스(lo0.0)를 구성합니다. 루프백 인터페이스를 사용하면 특정 지점에서 인접 라우터의 트래픽이 유동 IP 주소(즉, 활성 노드)로 전달됩니다.
- 활성 상태 확인 및 적용을 위한 IP 프로브를 구성합니다
- 활성 적용에 필요한 신호 경로를 구성하고 경로 존재 정책과 함께 사용합니다.
- IKEv2를 사용하여 고가용성(ICL) 트래픽에 대한 VPN 프로필을 구성합니다.
- BFD 모니터링 옵션 구성
- 라우팅 정책 및 라우팅 옵션 구성
- 네트워크 요구 사항에 따라 인터페이스와 영역을 구성합니다. 링크 암호화를 위한 IKE(Internet Key Exchange) 및 구성 동기화를 위한 SSH와 같은 서비스를 ICL과 연결된 보안 영역에서 호스트-인바운드 시스템 서비스로 허용해야 합니다.
-
SRX-01 및 SRX-02 디바이스에서 IPsec VPN에 대한 그룹 구성을 생성하여 VPN 피어 디바이스(SRX-03)와 터널을 설정합니다. 구성 그룹을 사용하면 동일한 구성 내에서 재사용되는 공통 요소를 적용할 수 있습니다.
- [groups] 옵션을 사용하여 SRX-03 디바이스와 터널을 설정하고 두 디바이스(SRX-01 및 SRX-02)에서 IPsec VPN 구성 동기화를 활성화하도록 IPsec VPN 옵션을 구성합니다.
- IPsec VPN 옵션으로 VPN 피어 디바이스를 구성합니다.
섀시 간 링크(ICL)의 경우 다음 구성을 권장합니다.
-
일반적으로 SRX 시리즈 방화벽에서 AE(Aggregated Ethernet) 또는 수익 이더넷 포트를 사용하여 ICL 연결을 설정할 수 있습니다. 이 예에서는 ICL에 GE 포트를 사용했습니다. 또한 최대의 세그멘테이션을 보장하기 위해 ICL 경로에 대한 라우팅 인스턴스를 구성했습니다.
- SRX 시리즈 방화벽에서 사용 가능한 경우 전용 HA 포트(제어 및 패브릭 포트)를 사용하지 마십시오.
- 최대 전송 단위(MTU)를 1514로 설정
- ICL에 사용되는 인터페이스와 연관된 보안 영역에서 다음 서비스를 허용합니다
-
IKE, 고가용성, SSH
-
필요한 라우팅 프로토콜에 따른 프로토콜.
-
BFD를 사용하여 이웃 경로를 모니터링합니다.
-
SRG0 및 SRG1+에서 다음 옵션을 구성할 수 있습니다.
SRG0 및 SRG1에서 다음 옵션을 구성할 수 있습니다.
-
SRG1: 활성/백업 신호 경로, 구축 유형, 활성성 우선순위, 선점, 가상 IP 주소(기본 게이트웨이 구축용), 활성성 프로빙 및 백업 패킷 프로세스.
-
SRG1: SRG1의 BFD 모니터링, IP 모니터링 및 인터페이스 모니터링 옵션.
-
SRG0: 실패 시 종료 및 실패 시 설치 경로 옵션.
SRG1에서 모니터링(BFD 또는 IP 또는 인터페이스) 옵션을 구성할 때, SRG0에서 실패 시 shutdown이라는 옵션을 구성하지 않는 것이 좋습니다.
-
SRG1: 활성/백업 신호 경로, 구축 유형, 활성성 우선순위, 선점, 가상 IP 주소(기본 게이트웨이 구축용), 활성성 프로빙 및 백업 패킷 프로세스.
-
SRG1: SRG1의 BFD 모니터링, IP 모니터링 및 인터페이스 모니터링 옵션.
-
SRG0: 실패 시 종료 및 실패 시 설치 경로 옵션.
SRG1에서 모니터링(BFD 또는 IP 또는 인터페이스) 옵션을 구성할 때, SRG0에서 실패 시 shutdown이라는 옵션을 구성하지 않는 것이 좋습니다.
표 1 은 이 예에서 사용된 인터페이스 구성에 대한 세부 정보를 보여줍니다.
| 디바이스 | 인터페이스 | 영역 | IP 주소 | 구성 |
|---|---|---|---|---|
| SRX-01 | lo0 | 언트러스트 |
10.11.0.1/32 |
유동 IP 주소 IKE(Internet Key Exchange) 게이트웨이 주소 |
| 10.12.0.1/32 |
IKE(Internet Key Exchange) 게이트웨이 주소 |
|||
| ge-0/0/2 |
아이슬 |
10.22.0.2/24 |
ICL 연결 |
|
| ge-0/0/4 |
신뢰 |
10.5.0.1/24 |
R2 라우터에 연결 |
|
| ge-0/0/3 |
언트러스트 |
10.3.0.2/24 |
R1 라우터에 연결 |
|
| SRX-02 | lo0 |
언트러스트 |
10.12.0.1/32 |
유동 IP 주소 IKE(Internet Key Exchange) 게이트웨이 주소 |
| 10.11.0.1/32 |
IKE(Internet Key Exchange) 게이트웨이 주소 |
|||
| ge-0/0/2 |
아이슬 |
10.22.0.1/24 |
ICL 연결 |
|
| ge-0/0/3 |
언트러스트 |
10.2.0.2/24 |
R1 라우터에 연결 |
|
| ge-0/0/4 |
신뢰 |
10.4.0.1/24 |
R2 라우터에 연결 |
|
| SRX-03 | lo0 | 언트러스트 |
10.112.0.1/32 |
IKE(Internet Key Exchange) 게이트웨이 주소 |
| 10.112.0.5/32 |
IKE(Internet Key Exchange) 게이트웨이 주소 |
|||
| ge-0/0/0 |
언트러스트 |
10.7.0.1/24 |
R2 라우터에 연결 |
|
| ge-0/0/2 |
신뢰 |
10.6.0.2/24 |
클라이언트 디바이스에 연결 |
| 에 구성된 | 디바이스 | 인터페이스 | IP 주소 |
|---|---|---|---|
| R2 | lo0 | 10.111.0.2/32 |
R2의 루프백 인터페이스 주소 |
| ge-0/0/1 |
10.4.0.2/24 |
SRX-02에 연결 |
|
| ge-0/0/0 |
10.5.0.2/24 |
SRX-01에 연결 |
|
| ge-0/0/2 |
10.7.0.2/24 |
SRX-03(VPN 피어 디바이스)에 연결 |
|
| R1 | lo0 | 10.111.0.1/32 |
R1의 루프백 인터페이스 주소 |
| ge-0/0/0 |
10.3.0.1/24 |
SRX-01에 연결 |
|
| ge-0/0/1 |
10.2.0.1/24 |
SRX-02에 연결 |
구성
시작하기 전에
멀티노드 고가용성 구성을 위한 SRX 시리즈 방화벽에는 Junos IKE 패키지가 필요합니다. 이 패키지는 SRX 시리즈 방화벽에서 기본 패키지 또는 옵션 패키지로 제공됩니다. 자세한 내용은 Junos IKE 패키지 지원을 참조하십시오.
패키지가 SRX 시리즈 방화벽에 기본적으로 설치되지 않는 경우 다음 명령을 사용하여 설치합니다. ICL 암호화를 위해 이 단계가 필요합니다.
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
CLI 빠른 구성
이 예를 빠르게 구성하려면, 아래 명령을 복사하여 텍스트 파일로 붙여 넣은 다음 모든 라인브레이크를 제거하고, 네트워크 구성을 일치하는 데 필요한 세부 사항을 변경하고, 계층 수준에서 [edit] 명령을 복사하여 CLI에 붙여 넣은 다음, 구성 모드에서 들어갑니다 commit .
SRX-01 디바이스
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability peer-id 2 peer-ip 10.22.0.1 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 set chassis high-availability peer-id 2 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 1 set chassis high-availability services-redundancy-group 2 peer-id 2 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 200 set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.3.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.3.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.5.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.5.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
SRX-02 디바이스
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability peer-id 1 peer-ip 10.22.0.2 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 1 liveness-detection minimum-interval 200 set chassis high-availability peer-id 1 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set chassis high-availability services-redundancy-group 2 peer-id 1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 1 set security ike proposal ICL_IKE_PROP description interchassisa_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.1/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.2.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.4.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 1 family inet6 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/24 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.2.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.2.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.4.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.4.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/24 next-hop 10.4.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.4.0.2
SRX-3 디바이스
set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG1_IKE_PROP dh-group group14 set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG2_IKE_PROP dh-group group14 set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 set security ike gateway SRG1_IKE_GW1 external-interface lo0 set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 set security ike gateway SRG1_IKE_GW1 version v2-only set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 set security ike gateway SRG2_IKE_GW500 external-interface lo0 set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 set security ike gateway SRG2_IKE_GW500 version v2-only set security ipsec proposal SRG1_IPSEC_PROP protocol esp set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set security ipsec proposal SRG2_IPSEC_PROP protocol esp set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces st0.500 set security zones security-zone untrust interfaces ge-0/0/1.0 set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone trust host-inbound-traffic system-services ike set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/2.0 set interfaces ge-0/0/0 description trust set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 set interfaces ge-0/0/1 description untrust set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 set interfaces ge-0/0/2 description trust set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.112.0.1/32 set interfaces lo0 unit 0 family inet address 10.112.0.5/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 500 family inet set routing-options autonomous-system 100 set routing-options static route 10.4.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.5.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
다음 섹션에서는 네트워크에서 멀티노드 고가용성 설정을 설정하는 데 필요한 라우터의 구성 코드 조각을 보여줍니다.
R1 라우터
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.3.0.1/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.2.0.1/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.1/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.1/32 preferred set routing-options autonomous-system 100 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.2.0.1 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.2.0.2 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.3.0.1 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.3.0.2
R2 라우터
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.5.0.2/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.4.0.2/24 set interfaces ge-0/0/2 description srx-3 set interfaces ge-0/0/2 unit 0 family inet address 10.7.0.2/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.2/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.2/32 preferred set routing-options autonomous-system 100 set routing-options static route 10.112.0.0/24 next-hop 10.7.0.1 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.4.0.2 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.4.0.1 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.5.0.2 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.5.0.1
구성
단계별 절차
단계별 절차에서 SRX-01의 구성을 보여줍니다.
다음 예에서는 구성 계층에서 다양한 수준을 탐색해야 합니다. 이를 수행하는 방법에 대한 지침은 CLI 사용자 가이드의 구성 모드에서 CLI 편집기 사용을 참조하십시오.
인터페이스를 구성합니다.
[edit] user@srx-1# set interfaces ge-0/0/2 description inter_chassis_link user@srx-1# set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 user@srx-1# set interfaces ge-0/0/3 description untrust user@srx-1# set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 user@srx-1# set interfaces ge-0/0/4 description trust user@srx-1# set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24
ge-0/0/3 및 ge-0/0/4 인터페이스를 사용하여 업스트림 및 다운스트림 라우터에 연결하고 ge-0/0/2 인터페이스를 사용하여 ICL을 설정합니다.
루프백 인터페이스를 구성합니다.
[edit] user@srx-1# set interfaces lo0 apply-groups-except global user@srx-1# set interfaces lo0 description untrust user@srx-1# set interfaces lo0 unit 0 family inet address 10.11.0.1/32 user@srx-1# set interfaces lo0 unit 0 family inet address 10.12.0.1/32 user@srx-1# set interfaces st0 unit 1
IP 주소 10.11.0.1 및 10.12.0.1을 루프백 인터페이스에 할당합니다. 10.11.0.1을 유동 IP 주소로, 10.12.0.1을 IKE 게이트웨이 주소로 사용합니다.
보안 영역을 구성하고, 영역에 인터페이스를 할당하고, 보안 영역에 허용되는 시스템 서비스를 지정합니다.
[edit] user@srx-1# set security zones security-zone vpn host-inbound-traffic system-services ike user@srx-1# set security zones security-zone vpn host-inbound-traffic protocols all user@srx-1# set security zones security-zone vpn interfaces st0.1 user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ike user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ping user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone untrust interfaces lo0.0 user@srx-1# set security zones security-zone untrust interfaces ge-0/0/3.0 user@srx-1# set security zones security-zone trust host-inbound-traffic system-services all user@srx-1# set security zones security-zone trust host-inbound-traffic protocols all user@srx-1# set security zones security-zone trust interfaces ge-0/0/4.0 user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ike user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ping user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services high-availability user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ssh user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone icl_zone interfaces ge-0/0/2.0
인터페이스 ge-0/0/3 및 ge-0/0/4에 각각 신뢰 및 신뢰할 수 없는 영역을 할당합니다. IP 네트워크를 통해 연결하기 위해 신뢰할 수 없는 영역에 lo0.0 인터페이스를 할당합니다. 인터페이스 ge-0/0/2를 ICL 영역에 할당합니다. 이 영역을 사용하여 ICL을 설정할 수 있습니다. VPN 보안 영역에 보안 터널 인터페이스를 할당합니다.
- 노드 ID, 로컬 노드 및 피어 노드의 lP 주소, 피어 노드의 인터페이스와 같은 로컬 노드 및 피어 노드 세부 정보를 모두 구성합니다.
[edit] user@srx-1# set chassis high-availability local-id 1 user@srx-1# set chassis high-availability local-id local-ip 10.22.0.2 user@srx-1# set chassis high-availability peer-id 2 peer-ip 10.22.0.1 user@srx-1# set chassis high-availability peer-id 2 interface ge-0/0/2.0
ICL을 사용하여 피어 노드와 통신하기 위해 ge-0/0/2 인터페이스를 사용합니다.
IPSEC_VPN_ICL IPSec VPN 프로필을 피어 노드에 연결합니다.
[edit] user@srx-1# set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN
노드 간에 보안 ICL 링크를 설정하려면 이 구성이 필요합니다.
피어 노드에 대한 BFD(Bidirectional Forwarding Detection) 프로토콜 옵션을 구성합니다.
[edit] user@srx-1# set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 user@srx-1# set chassis high-availability peer-id 2 liveness-detection multiplier 3
-
서비스 중복 그룹 SRG1 및 SRG2를 구성합니다.
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 deployment-type routing user@srx-1# set chassis high-availability services-redundancy-group 1 peer-id 2 user@srx-1# set chassis high-availability services-redundancy-group 2 peer-id 2
SRG1 및 SRG2 모두의 활성성 결정 매개 변수를 설정합니다.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.11.0.1
유동 IP 주소를 소스 IP 주소(SRG1의 경우 10.11.0.1, SRG2의 경우 10.12.0.1)로 사용하고 업스트림 라우터의 IP 주소를 활성 성 결정 프로브의 대상 IP 주소(10.111.0.1)로 사용합니다.
IP 모니터링 및 활성 프로빙을 위해 최대 64개의 IP 주소를 구성할 수 있습니다. 총 64개의 IP 주소는 IPv4와 IPv6 주소 수의 합계입니다)
SRG1 및 SRG2에 대한 BFD 모니터링 매개 변수를 구성하여 네트워크 장애를 탐지합니다.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4
활성 적용에 필요한 활성 신호 경로를 구성합니다.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 user@srx-1# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 user@srx-1# set chassis high-availability services-redundancy-group 1 preemption user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-priority 1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 user@srx-1# set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 user@srx-1# set chassis high-availability services-redundancy-group 2 preemption user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-priority 200
참고: 정책-옵션 문에서 route-exists 정책과 함께 활성 신호 경로를 지정해야 합니다. withif-route-exists조건을 구성할active-signal-route때 HA 모듈은 이 경로를 라우팅 테이블에 추가합니다.IKE(Internet Key Exchange) 게이트웨이의 로컬 주소를 포함하여 IP 접두사 목록을 생성하고 IP 접두사 목록을 SRG1 및 SRG2에 연결합니다.
SRG1
[edit] user@srx-1# set policy-options prefix-list SRG1_PFX 10.11.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX
SRG2
[edit] user@srx-1# set policy-options prefix-list SRG2_PFX 10.12.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX
이 구성은 특정 IPsec VPN 터널을 특정 보안 디바이스에 고정합니다.
SRG1 및 SRG2 모두에서 IPsec VPN 서비스를 활성화합니다.
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 managed-services ipsec user@srx-1# set chassis high-availability services-redundancy-group 2 managed-services ipsec
ICL에 대한 IPSec VPN 옵션을 구성합니다.
IKE(Internet Key Exchange) 구성을 정의합니다. IKE(Internet Key Exchange) 구성은 보안 연결을 설정하는 데 사용되는 알고리즘과 키를 정의합니다.
[edit] user@srx-1# set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel user@srx-1# set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys user@srx-1# set security ike proposal ICL_IKE_PROP dh-group group14 user@srx-1# set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 user@srx-1# set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc user@srx-1# set security ike proposal ICL_IKE_PROP lifetime-seconds 300 user@srx-1# set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel user@srx-1# set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP user@srx-1# set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" user@srx-1# set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL user@srx-1# set security ike gateway ICL_IKE_GW version v2-only
멀티노드 고가용성 기능의 경우, IKE 버전을 다음과 같이 구성해야 합니다.
v2-only-
IPsec 제안 프로토콜 및 암호화 알고리즘을 지정합니다. IPsec 옵션을 지정하여 두 참가자 디바이스 사이에 IPsec 터널을 생성하여 VPN 통신을 보호합니다.
[edit] user@srx-1# set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel user@srx-1# set security ipsec proposal ICL_IPSEC_PROP protocol esp user@srx-1# set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm user@srx-1# set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 user@srx-1# set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel user@srx-1# set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL
ha-link-encryption노드 간의 고가용성 트래픽 플로우를 보호하기 위해 ICL이 암호화됩니다.구성에서
set chassis high-availability peer-id <id> vpn-profile vpn_profile동일한 VPN 이름 ICL_IPSEC_VPN 언급 vpn_profile 해야 합니다.
보안 정책을 구성합니다.
[edit] user@srx-1# set security policies default-policy permit-all
이 예제에서는 모든 트래픽을 허용하는 정책을 구성했습니다. 네트워크 요구 사항에 따라 보안 정책을 생성하여 조직 정책에서 허용하는 트래픽을 허용하고 다른 모든 트래픽은 거부하는 것이 좋습니다. 이 예제에서만 데모 목적으로 기본 정책을 사용했습니다.
라우팅 옵션을 구성합니다.
[edit] user@srx-1# set routing-options autonomous-system 100 user@srx-1# set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 user@srx-1# set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
정책 옵션을 구성합니다.
[edit] user@srx-1# set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term default then reject user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0
경로 일치 조건(
if-route-exists)을 사용하여 활성 신호 경로 10.39.1.1(SRG1) 및 10.49.1.1(SRG2)을 구성합니다. 멀티노드 고가용성은 노드가 활성 역할로 이동할 때 이 경로를 라우팅 테이블에 추가합니다. 또한 노드는 더 높은 선호 경로를 보급하기 시작합니다. 백업 신호 경로(10.39.1.2 및 10.49.1.2)를 구성하여 중간 우선순위로 백업 노드를 보급합니다. 장애가 발생할 경우 고가용성 링크가 다운되고 현재 활성 노드가 기본 역할을 해제하고 active-signal-route를 제거합니다. 이제 백업 노드는 프로브를 통해 상태를 감지하고 활성 역할로 전환합니다. 모든 트래픽을 새 활성 노드로 이동하도록 경로 기본 설정이 전환됩니다BFD 피어링 세션 옵션을 구성하고 활성 감지 타이머를 지정합니다.
[edit] user@srx-1# set protocols bgp group trust type internal user@srx-1# set protocols bgp group trust local-address 10.3.0.2 user@srx-1# set protocols bgp group trust export mnha-route-policy user@srx-1# set protocols bgp group trust local-as 100 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group trust neighbor 10.3.0.1 user@srx-1# set protocols bgp group untrust type internal user@srx-1# set protocols bgp group untrust local-address 10.5.0.1 user@srx-1# set protocols bgp group untrust export mnha-route-policy user@srx-1# set protocols bgp group untrust local-as 100 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group untrust neighbor 10.5.0.2
IPsec VPN 구성(SRX-1 및 SRX-2)
피어 SRX 시리즈 방화벽과의 IPsec VPN 연결을 설정하는 방법은 다음과 같습니다. 이 예에서는 모든 IPsec VPN 구성 문을 vpn_config라는 JUNOS 구성 그룹 안에 배치합니다.
- 구성 맨 위에 구성 그룹을
vpn_config만들고 IPsec VPN 특정 세부 정보를 구성합니다.[edit] set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 500 family inet
vpn_config 구성 그룹에서 문을 상속하려면 구성에 apply-groups 문을 포함합니다.
[edit] user@srx-1# set apply-groups vpn_config
구성(SRX-03) (VPN 피어 디바이스)
단계별 절차
IKE(Internet Key Exchange) 제안을 생성합니다.
[edit] user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG1_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG2_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600
IKE(Internet Key Exchange) 정책을 정의합니다.
[edit] user@srx-3# set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP user@srx-3# set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" user@srx-3# set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP user@srx-3# set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123"
IKE(Internet Key Exchange) 게이트웨이를 생성하고, 주소를 정의하고, 외부 인터페이스 및 버전을 지정합니다.
[edit] user@srx-3# set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 user@srx-3# set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 external-interface lo0 user@srx-3# set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 version v2-only user@srx-3# set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 user@srx-3# set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 user@srx-3# set security ike gateway SRG2_IKE_GW500 external-interface lo0 user@srx-3# set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 user@srx-3# set security ike gateway SRG2_IKE_GW500 version v2-only
IPsec 제안을 생성합니다.
[edit] user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800
IPsec 정책을 생성합니다.
[edit] user@srx-3# set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP user@srx-3# set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP
IPsec 제안 참조(IKE 게이트웨이, IPsec 정책, 바인딩할 인터페이스 및 트래픽 선택기)를 지정합니다.
[edit] user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately
보안 정책을 생성합니다.
[edit] user@srx-3# set security policies default-policy permit-all
이 예제에서는 모든 트래픽을 허용하는 정책을 구성했습니다. 네트워크 요구 사항에 따라 보안 정책을 생성하여 조직 정책에서 허용하는 트래픽을 허용하고 다른 모든 트래픽은 거부하는 것이 좋습니다. 이 예제에서만 데모 목적으로 기본 정책을 사용했습니다.
인터페이스를 구성합니다.
[edit] user@srx-3# set interfaces ge-0/0/0 description trust user@srx-3# set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 user@srx-3# set interfaces ge-0/0/1 description untrust user@srx-3# set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 user@srx-3# set interfaces ge-0/0/2 description trust user@srx-3# set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 user@srx-3# set interfaces lo0 description untrust user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.1/32 user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.5/32 user@srx-3# set interfaces st0 unit 1 family inet user@srx-3# set interfaces st0 unit 500 family inet
보안 영역을 정의하고 인터페이스를 추가합니다.
[edit] user@srx-3# set security zones security-zone untrust host-inbound-traffic system-services all user@srx-3# set security zones security-zone untrust host-inbound-traffic protocols all user@srx-3# set security zones security-zone untrust interfaces st0.1 user@srx-3# set security zones security-zone untrust interfaces lo0.0 user@srx-3# set security zones security-zone untrust interfaces st0.500 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/1.0 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/0.0 user@srx-3# set security zones security-zone trust host-inbound-traffic system-services all user@srx-3# set security zones security-zone trust host-inbound-traffic protocols all user@srx-3# set security zones security-zone trust interfaces ge-0/0/2.0
고정 경로를 구성합니다.
[edit] user@srx-3# set routing-options autonomous-system 100 user@srx-3# set routing-options static route 10.4.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.5.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
결과(SRX-01)
구성 모드에서 다음 명령을 입력하여 구성을 확인합니다.
출력에 의도한 구성이 표시되지 않으면 이 예의 구성 지침을 반복하여 수정합니다.
[edit]
user@srx-1# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-1# show chassis high-availability
local-id 1 local-ip 10.22.0.2;
peer-id 2 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
services-redundancy-group 2 {
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
[edit]
user@srx-1# show security ike
proposal ICL_IKE_PROP {
description interchassis_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-1# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-1# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/16 orlonger;
10.1.0.0/16 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/16 orlonger;
10.8.0.0/16 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-1# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/16 next-hop 10.5.0.2;
route 10.112.0.0/24 next-hop 10.5.0.2;
}
[edit]
user@srx-1# show security zones
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-1# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.3.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.5.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1;
}
디바이스 구성이 완료되면 구성 모드에서 들어갑니다 commit .
결과 (SRX-02)
구성 모드에서 다음 명령을 입력하여 구성을 확인합니다. 출력에 의도한 구성이 표시되지 않으면 이 예의 구성 지침을 반복하여 수정합니다.
[edit]
user@srx-2# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-2# show chassis high-availability
local-id 2 local-ip 10.22.0.1;
peer-id 1 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
services-redundancy-group 2 {
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
[edit]
user@srx-2# show security ike
proposal ICL_IKE_PROP {
description interchassisa_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-2# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-2# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/24 orlonger;
10.1.0.0/24 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/24 orlonger;
10.8.0.0/24 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-2# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/24 next-hop 10.4.0.2;
route 10.112.0.0/24 next-hop 10.4.0.2;
}
[edit]
user@srx-2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-2# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.2.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.4.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1 {
family inet;
}
}
디바이스 구성이 완료되면 구성 모드에서 들어갑니다 commit .
user@host# commit warning: High Availability Mode changed, please reboot the device to avoid undesirable behavior commit complete
결과(SRX-3) (VPN 피어 디바이스)
구성 모드에서 다음 명령을 입력하여 구성을 확인합니다. 출력에 의도한 구성이 표시되지 않으면 이 예의 구성 지침을 반복하여 수정합니다.
[edit]
user@srx-3# show security ike
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.11.0.1;
external-interface lo0;
local-address 10.112.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.12.0.1;
external-interface lo0;
local-address 10.112.0.5;
version v2-only;
}
[edit]
user@srx-3# show security ipsec
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.7.0.2/32;
remote-ip 10.1.0.2/32;
}
establish-tunnels immediately;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts1 {
local-ip 10.9.0.2/32;
remote-ip 10.8.0.2/32;
}
establish-tunnels immediately;
}
[edit]
user@srx-3# show routing-options
autonomous-system 100;
static {
route 10.4.0.0/24 next-hop 10.7.0.2;
route 10.5.0.0/24 next-hop 10.7.0.2;
route 10.11.0.0/24 next-hop 10.7.0.2;
route 10.12.0.0/24 next-hop 10.7.0.2;
route 10.111.0.1/32 next-hop 10.7.0.2;
route 10.111.0.2/32 next-hop 10.7.0.2;
}
[edit]
user@srx-3# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
lo0.0;
st0.500;
ge-0/0/1.0;
ge-0/0/0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-3# show interfaces
ge-0/0/0 {
description trust;
unit 0 {
family inet {
address 10.7.0.1/24;
}
}
}
ge-0/0/1 {
description untrust;
unit 0 {
family inet {
address 10.6.0.2/24;
}
}
}
ge-0/0/2 {
description trust;
unit 0 {
family inet {
address 10.9.0.1/24;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.112.0.1/32;
address 10.112.0.5/32;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 500 {
family inet;
}
}
디바이스 구성이 완료되면 구성 모드에서 들어갑니다 commit .
검증
구성이 제대로 작동하고 있는지 확인합니다.
- 멀티노드 고가용성 세부 정보 확인
- 멀티노드 고가용성 세부 정보 확인
- 멀티노드 고가용성 피어 노드 상태 확인
- 멀티노드 고가용성 서비스 중복 그룹 확인
- 섀시 간 링크(ICL) 암호화 상태 확인
- 링크 암호화 터널 통계 확인
- 섀시 간 링크 활성 피어 확인
- VPN 상태 확인
- IPsec 보안 연결 세부 정보 표시
- SRG당 활성 피어 표시
- SRG 매핑에 대한 IP 접두사 표시
- BGP 세션 정보를 표시합니다.
멀티노드 고가용성 세부 정보 확인
목적
보안 디바이스에 구성된 멀티노드 고가용성 설정의 세부 정보를 보고 확인합니다.
작업
운영 모드에서 다음 명령을 실행합니다.
SRX-1에서
user@srx-01> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
SRX-2에서
user@srx-02> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.1
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
의미
명령 출력에서 다음 세부 사항을 확인합니다.
IP 주소 및 ID와 같은 로컬 노드 및 피어 노드 세부 정보.
필드
Encrypted: YES는 트래픽이 보호되고 있음을 나타냅니다.필드
Deployment Type: ROUTING는 레이어 3 모드 구성, 즉 네트워크의 양쪽에 라우터가 있음을 나타냅니다.필드
Services Redundancy Group: 1Services Redundancy Group: 2는 해당 노드에서 SRG1 및 SRG2(활성 또는 백업)의 상태를 나타냅니다.
멀티노드 고가용성 세부 정보 확인
목적
보안 디바이스에 구성된 멀티노드 고가용성 설정의 세부 정보를 보고 확인합니다.
작업
운영 모드에서 다음 명령을 실행합니다.
SRX-01에서
user@srx-01> show chassis high-availability information detail
Node level Information:
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
HA Peer Conn events:
Jan 31 00:55:19.249 : HA Peer 180.100.1.1 BFD conn came up
Cold Synchronization:
Status:
Cold synchronization completed for: N/A
Cold synchronization failed for: N/A
Cold synchronization not known for: N/A
Current Monitoring Weight: 0
Progress:
CS Prereq 1 of 1 SPUs completed
1. if_state sync 1 SPUs completed
2. ha peer conn 1 SPUs completed
3. policy data sync 1 SPUs completed
4. cp ready 1 SPUs completed
5. VPN data sync 1 SPUs completed
6. IPID data sync 1 SPUs completed
7. All SPU ready 1 SPUs completed
8. AppID ready 1 SPUs completed
9. Tunnel Sess ready 1 SPUs completed
CS RTO sync 1 of 1 SPUs completed
CS Postreq 1 of 1 SPUs completed
Statistics:
Number of cold synchronization completed: 0
Number of cold synchronization failed: 0
Events:
Jan 31 00:55:24.616 : Cold sync for PFE is Post-req check in process
Jan 31 00:55:25.615 : Cold sync for PFE is Completed
SPU monitoring:
Status: Enabled
Current monitoring weight: 0
Statistics:
SPU up count: 1
NPC up count: 0
SPU down count: 0
NPC down count: 0
Chassis info processing error count: 0
Loopback Information:
PIC Name Loopback Nexthop Mbuf
-------------------------------------------------
Success Success Success
Hardware monitoring:
Status:
Activation status: Enabled
Ctrl Plane Hardware errors: 0
Data Plane Hardware errors: 0
SRGS Information:
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: ACTIVE
Last Advertised Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.347 : SRG[1] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:56:33.046 : SRG[1] state HOLD -> BACKUP, Reason: Peer state Active received
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:12.695 : SRG[1] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
SRGS Information:
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: BACKUP
Last Advertised Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.439 : SRG[2] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:55:24.263 : SRG[2] state HOLD -> ACTIVE, Reason: Local Priority Higher
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:13.698 : SRG[2] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
의미
명령 출력에서 다음 세부 사항을 확인합니다.
필드
Services: [ IPSEC ]는 각 SRG에 대한 연결된 IPSec VPN을 나타냅니다.필드
BFD Monitoring,Interface Monitoring, 모니터링Split-brain Prevention Probe Info세부 정보를 표시합니다.필드
Cold Synchronization는SRG State Change Events현재 상태 및 최근 변경 사항에 대한 세부 정보를 제공합니다.필드
Services Redundancy Group: 1Services Redundancy Group: 2는 해당 노드에서 SRG1 및 SRG2(활성 또는 백업)의 상태를 나타냅니다.
명령 출력에서 IP 180.100.1.2와 같은 IP 주소는 Junos OS에 의해 내부적으로 생성되며 이러한 주소는 라우팅 테이블을 방해하지 않습니다.
멀티노드 고가용성 피어 노드 상태 확인
목적
피어 노드 세부 정보를 보고 확인합니다.
작업
운영 모드의 SRX-01 및 SRX-02에서 다음 명령을 실행합니다.
SRX-01
user@srx-01> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
SRX-02
user@srx-02> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.1
Internal Peer-IP: 180.100.1.2
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 6 4
SRG Status Ack 4 4
Attribute Msg 2 1
Attribute Ack 1 1
의미
명령 출력에서 다음 세부 사항을 확인합니다.
사용된 인터페이스, IP 주소, ID와 같은 피어 노드 세부 정보
암호화 상태, 연결 상태 및 콜드 동기화 상태
노드 전반의 패킷 통계.
멀티노드 고가용성 서비스 중복 그룹 확인
목적
SRG가 구성되고 올바르게 작동하는지 확인합니다.
작업
운영 모드의 두 보안 디바이스 모두에서 다음 명령을 실행합니다.
SRX-02의 SRG1
user@srx-02> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRX-02의 SRG2
user@srx-02> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
SRX-01의 SRG1
user@srx-01> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRX-01의 SRG2
user@srx-01> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
의미
명령 출력에서 다음 세부 사항을 확인합니다.
구축 유형, 상태, 활성 및 백업 신호 경로와 같은 피어 노드 세부 정보.
분할 뇌 방지 프로브, IP 모니터링 및 BFD 모니터링 상태.
연관된 IP 접두사 테이블입니다.
섀시 간 링크(ICL) 암호화 상태 확인
목적
섀시 간 링크(ICL) 상태를 확인합니다.
작업
SRX-01에서 다음 명령을 실행합니다.
user@srx-01> show security ipsec security-associations ha-link-encryption Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <495002 ESP:aes-gcm-256/aes256-gcm 0x0008d9c7 236/ unlim - root 500 10.22.0.1 >495002 ESP:aes-gcm-256/aes256-gcm 0x0001a573 236/ unlim - root 500 10.22.0.1
user@srx-01> show security ike security-associations ha-link-encryption Index State Initiator cookie Responder cookie Mode Remote Address 16776938 UP 9f8fe46ce3be92f8 44e6b3fd74cc9294 IKEv2 10.22.0.1
user@srx-01> show security ipsec security-associations ha-link-encryption detail
ID: 495002 Virtual-system: root, VPN Name: ICL_IPSEC_VPN
Local Gateway: 10.22.0.2, Remote Gateway: 10.22.0.1
Traffic Selector Name: __ICL_IPSEC_VPN__multi_node__
Local Identity: ipv4(180.100.1.2-180.100.1.2)
Remote Identity: ipv4(180.100.1.1-180.100.1.1)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: No
PFS group: N/A
SRG ID: 0
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.16000, Policy-name: ICL_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
HA Link Encryption Mode: Multi-Node
Location: FPC -, PIC -, KMD-Instance -
Anchorship: Thread -
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x0008d9c7, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
Direction: outbound, SPI: 0x0001a573, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
의미
명령 출력은 다음 정보를 제공합니다.
로컬 게이트웨이 및 원격 게이트웨이 세부 정보입니다.
PIC의 각 스레드에 대한 IPsec SA 쌍입니다.
HA 링크 암호화 모드(다음 줄 참조):
HA Link Encryption Mode: Multi-Node사용된 인증 및 암호화 알고리즘
명령 출력에 표시된 IP 범위(180.100.1.x)는 ICL IPsec 트래픽 선택기 역할을 합니다. 시스템은 이 IP 범위를 동적으로 할당하므로 변경하거나 수정하지 않는 것이 중요합니다. 또한 더 넓은 180.x.x.x IP 범위에 대해 BFD(Bidirectional Forwarding Detection)가 자동으로 활성화됩니다.
링크 암호화 터널 통계 확인
목적
활성 노드와 백업 노드 모두에서 링크 암호화 터널 통계를 확인합니다.
작업
SRX-01에서 다음 명령을 실행합니다.
user@srx-01> show security ipsec statistics ha-link-encryption ESP Statistics: Encrypted bytes: 106294156 Decrypted bytes: 51961287 Encrypted packets: 979531 Decrypted packets: 989651 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
의미
VPN 전반에서 패킷 손실 문제가 발견되면 명령을 여러 번 실행 show security ipsec statistics ha-link-encryption 하여 암호화 및 복호화된 패킷 카운터가 증가하고 있는지 확인할 수 있습니다. 또한 다른 오류 카운터가 증가하는지 확인해야 합니다.
이 명령을 사용하여 clear security ipsec security-associations ha-link-encryption 모든 IPsec 통계를 지웁니다.
섀시 간 링크 활성 피어 확인
목적
ICL 활성 피어만 볼 수 있고 일반 IKE 활성 피어는 볼 수 없습니다.
작업
SRX-01 및 SRX-02 디바이스에서 다음 명령을 실행합니다.
SRX-1
user@srx-01> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.1 500 10.22.0.1 not available 0.0.0.0
SRX-2
user@srx-02> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.2 500 10.22.0.2 not available 0.0.0.0
의미
명령 출력에는 활성 피어가 사용 중인 피어 주소 및 포트와 같은 세부 정보와 함께 ICL의 활성 피어만 표시됩니다.
VPN 상태 확인
목적
SRG 수준에서 IKE(Internet Key Exchange) 보안 연결 상태를 확인하여 VPN 상태를 확인합니다.
작업
SRX-1, SRX-2 및 SRX-3(VPN 피어 디바이스)에서 다음 명령을 실행합니다.
SRX-01
user@srx-01> show security ike security-associations srg-id 1
Index State Initiator cookie Responder cookie Mode Remote Address
16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-01> show security ike security-associations srg-id 2
Index State Initiator cookie Responder cookie Mode Remote Address
33554536 UP 9944aaf1ab914b42 15cef0da496bdd92 IKEv2 10.112.0.5
SRX-02
user@srx-02> show security ike security-associations srg-id 1 Index State Initiator cookie Responder cookie Mode Remote Address 16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-02> show security ike security-associations srg-id 2 Index State Initiator cookie Responder cookie Mode Remote Address 33554534 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.112.0.5
SRX-3(VPN 피어 디바이스)
user@srx-03> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 5929032 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.12.0.1 5929033 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.11.0.1
의미
출력은 다음을 나타냅니다.
- 원격 피어의 IP 주소입니다.
- 두 원격 피어 모두에 대해 UP으로 표시된 상태는 1단계 설정의 성공적인 연결을 나타냅니다.
- 원격 피어 IP 주소, IKE(Internet Key Exchange) 정책 및 외부 인터페이스가 모두 정확합니다.
IPsec 보안 연결 세부 정보 표시
목적
SRG ID로 식별된 개별 IPsec SA 세부 정보를 표시합니다.
작업
SRX 시리즈 방화벽에서 다음 명령을 실행합니다.
SRX-1
user@srx-01> show security ipsec security-associations srg-id 1 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1210/ unlim - root 500 10.112.0.1 >17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1210/ unlim - root 500 10.112.0.1
user@srx-01> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1382/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1382/ unlim - root 500 10.112.0.5
SRX-02
user@srx-02> show security ipsec security-associations srg-id 1
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1286/ unlim - root 500 10.112.0.1
>17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1286/ unlim - root 500 10.112.0.1
user@srx-02> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1461/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1461/ unlim - root 500 10.112.0.5
SRX-03
user@srx-03> show security ipsec security-associations
Total active tunnels: 2 Total Ipsec sas: 2
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<67108865 ESP:aes-cbc-256/sha256 6d1e9c89 1392/ unlim - root 500 10.11.0.1
>67108865 ESP:aes-cbc-256/sha256 c50520d4 1392/ unlim - root 500 10.11.0.1
<67108866 ESP:aes-cbc-256/sha256 f41d091c 1570/ unlim - root 500 10.12.0.1
>67108866 ESP:aes-cbc-256/sha256 9feb290c 1570/ unlim - root 500 10.12.0.1
의미
출력은 VPN의 상태를 표시합니다.
SRG당 활성 피어 표시
목적
사용 중인 피어 주소 및 포트가 있는 연결된 활성 피어의 목록을 표시합니다.
작업
SRX 시리즈 방화벽에서 다음 명령을 실행합니다.
SRX-01
user@srx-01> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-01> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
SRX-02
user@srx-02> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-02> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
의미
출력에는 사용된 피어 주소 및 포트에 대한 세부 정보와 함께 연결된 디바이스 목록이 표시됩니다.
SRG 매핑에 대한 IP 접두사 표시
목적
SRG 매핑 정보에 대한 IP 접두사를 표시합니다.
작업
SRX-01 디바이스에서 다음 명령을 실행합니다.
user@srx-01> show chassis high-availability prefix-srgid-table
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
2 10.12.0.0/24 default
의미
출력은 설정에서 SRG에 매핑된 IP 주소 접두사를 보여줍니다.
BGP 세션 정보를 표시합니다.
목적
BGP 및 해당 인접 라우터에 대한 요약 정보를 표시하여 피어에서 경로를 수신하는지 판별합니다.
작업
SRX 시리즈 방화벽에서 다음 명령을 실행합니다.
SRX-1 디바이스
user@srx-01> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.3.0.1 100 37 40 0 0 15:43 Establ
inet.0: 0/0/0/0
10.5.0.2 100 37 40 0 0 15:42 Establ
inet.0: 0/0/0/0
SRX-2 디바이스
user@srx-02> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn St ate|#Active/Received/Accepted/Damped...
10.2.0.1 100 842 846 0 0 6:18:40 Es tabl
inet.0: 0/0/0/0
10.4.0.2 100 842 846 0 0 6:18:42 Es tabl
inet.0: 0/0/0/0
의미
출력은 BGP 세션이 설정되고 피어가 업데이트 메시지를 교환하고 있음을 보여줍니다.
