例:レイヤー 3 ネットワークのアクティブ/アクティブ マルチノード高可用性で IPSec VPN を構成する
この例では、アクティブ/アクティブ型マルチノード高可用性セットアップ用の IPsec VPN を構成および検証する方法を示します。
概要
マルチノード高可用性では、参加するSRXシリーズファイアウォールがレイヤー3ネットワーク内の独立したノードとして動作します。ノードは、異なるネットワークに属する隣接するインフラストラクチャに接続されます。暗号化されたシャーシ間論理リンク(ICL)は、ルーティングされたネットワーク上でノードを接続します。参加ノードは相互にバックアップを行い、システムまたはハードウェアに障害が発生した場合に、高速同期フェイルオーバーを確保します。
マルチノード高可用性は、複数のサービス冗長性グループ(SRG)をサポートし、アクティブ/アクティブモードで運用できます。このモードでは、一部のSRGは1つのノードでアクティブを維持し、一部のSRGは別のノードでアクティブなままになります。
マルチノード高可用性は、複数のSRG(SRG1+)を使用してアクティブ/アクティブモードでIPsec VPNをサポートします。このモードでは、SRGのアクティブ性に基づいて、両方のノードから複数のアクティブなトンネルを確立できます。マルチノードの高可用性は、IPsecトンネルを確立し、終端IPアドレス(終端するトンネルも識別します)をSRGに関連付けることで、鍵交換を実行します。デバイスごとに異なるSRG1+がアクティブ状態またはバックアップ状態になる可能性があるため、マルチノードの高可用性は、一致するトラフィックを対応するアクティブなSRG1に効果的に誘導します。異なるSRGが異なるノードでアクティブになる可能性があるため、これらのSRGに属するトンネルは、両方のノードで独立して起動します。
マルチノード高可用性ソリューションでは、2ノード構成をサポートしています。
要件
この例では、以下のハードウェアおよびソフトウェアコンポーネントを使用しています。
2つのSRXシリーズファイアウォール(サポートされるデバイスは、SPC3、IOC3、SCB3、SCB4、RE3を搭載したSRX5400、SRX5600、SRX5800です)
Junos OSリリース22.4R1
この例では、アップストリーム/ダウンストリームルーターとして2台のジュニパーネットワークスMXシリーズルーティングプラットフォームを使用しました。
始める前に
ネットワーク要件に従ってステートレスファイアウォールのフィルタリングとサービス品質(QoS)を設定し、ネットワーク内のトラフィックを管理するための適切なセキュリティポリシーを設定します。
一般的な高可用性導入では、ネットワークのノースバウンド側とサウスバウンド側に複数のルーターとスイッチがあります。この例では、SRXシリーズファイアウォールの両側で2台のルーターを使用しています。ネットワーク要件に従ってアップストリームとダウンストリームのルーターを設定していることを確認します。
request system software add optional://junos-ike.tgzコマンドを使用して、SRXシリーズファイアウォールにJunos IKEパッケージをインストールします。junos-ikeパッケージは、Junosソフトウェアパッケージ(リリース20.4R1以降Junos OS)に含まれています。
トポロジー
図1 は、この例で使用されているトポロジーを示しています。
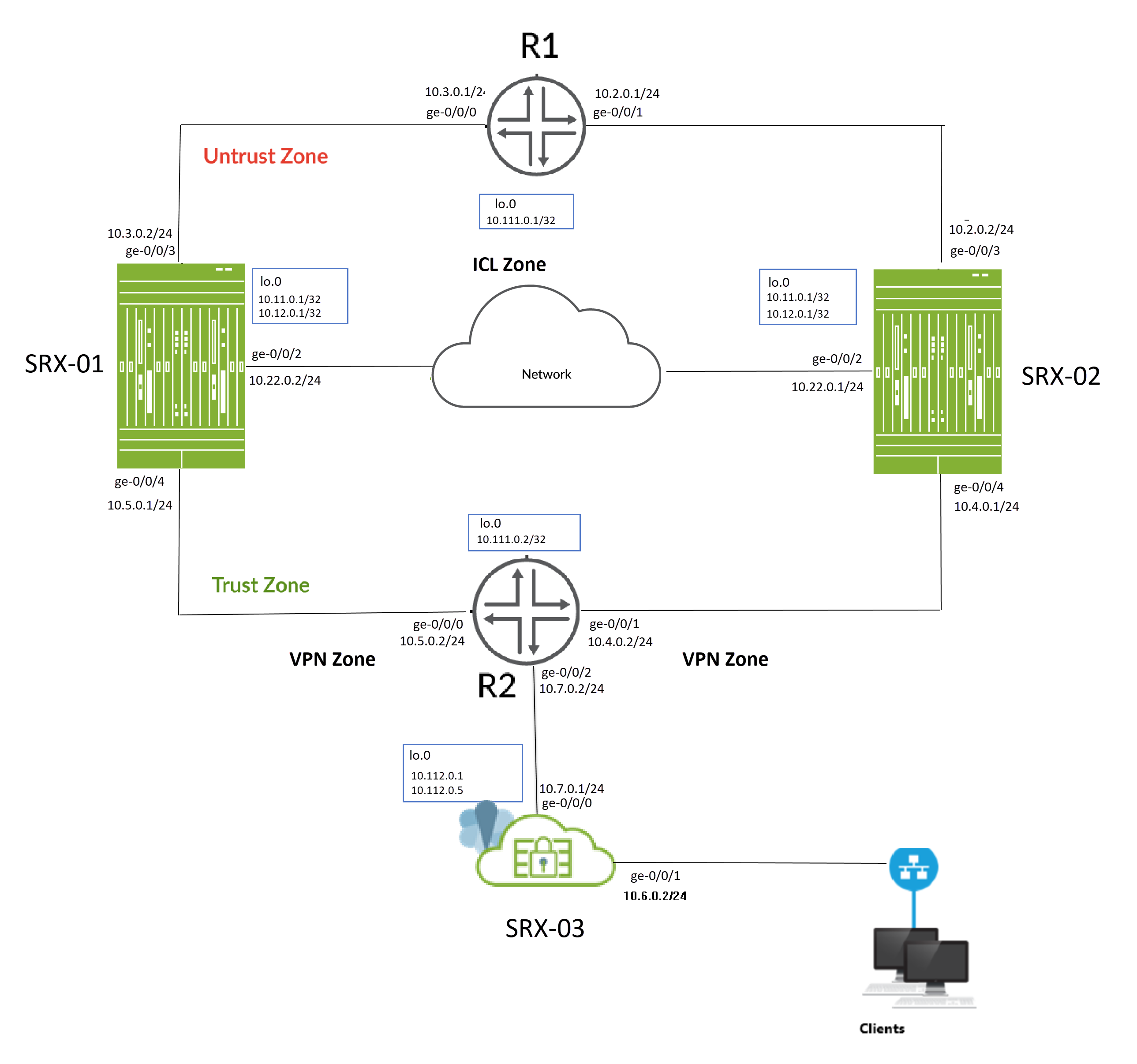 におけるマルチノード高可用性
におけるマルチノード高可用性
トポロジーに示すように、2つのSRXシリーズファイアウォール(SRX-1およびSRX-2)が信頼側と信頼できない側で隣接するルーターに接続され、BGPネイバーシップを形成しています。暗号化されたシャーシ間論理リンク(ICL)は、ルーティングされたネットワーク上でノードを接続します。ノードは、ネットワーク上でルーティング可能なIPアドレス(フローティングIPアドレス)を使用して相互に通信します。
SRX-03デバイスは、マルチノード高可用性セットアップのピアデバイスとして機能し、SRX-01およびSRX-02デバイスとのIPsec VPNトンネルを確立します。
以下のタスクを実行して、マルチノード高可用性セットアップを構築します。
- IDを割り当てて、SRXシリーズファイアウォールのペアをローカルノードおよびピアノードとして設定します。
- サービス冗長性グループ(SRG1およびSRG2)を設定します。
- フローティングIPアドレスをホストし、ピアゲートウェイに到達するようにループバックインターフェイス(lo0.0)を設定します。ループバックインターフェイスを使用することで、任意の時点で、隣接するルーターからのトラフィックがフローティングIPアドレス(つまりアクティブノード)に向かって誘導されます。
- アクティビティの判定と適用のためのIPプローブの設定
- アクティビティの適用に必要な信号ルートを設定し、ルートが存在するポリシーと併せて使用します。
- IKEv2を使用して、高可用性(ICL)トラフィック用のVPNプロファイルを構成します。
- BFD監視オプションを設定する
- ルーティングポリシーとルーティングオプションを設定する
- ネットワーク要件に応じてインターフェイスとゾーンを設定します。リンク暗号化用の IKE や設定同期用の SSH などのサービスを、ICL に関連付けられたセキュリティーゾーン上のホストインバウンドシステムサービスとして許可する必要があります。
-
SRX-01 および SRX-02 デバイスで IPsec VPN のグループ構成を作成して、VPN ピア デバイス(SRX-03)とのトンネルを設定します。設定グループを使用すると、同じ設定内で再利用される共通の要素を適用できます。
- IPsec VPNオプションを設定して、SRX-03デバイスとのトンネルを確立し、[groups]オプションを使用して両方のデバイス(SRX-01およびSRX-02)でIPsec VPN設定の同期を有効にします。
- IPsec VPNオプションを使用してVPNピアデバイスを設定します。
シャーシ間リンク(ICL)の場合、以下の設定を推奨します。
-
一般に、SRXシリーズファイアウォールのアグリゲートイーサネット(AE)または収益イーサネットポートを使用して、ICL接続を設定できます。この例では、ICLにGEポートを使用しました。また、ICLパスにルーティングインスタンスを設定して、セグメンテーションを最大限に高めています。
- 専用のHAポート(コントロールポートとファブリックポート)は、SRXシリーズファイアウォールで利用可能な場合は使用しないでください。
- MTUを1514に設定
- ICLに使用されるインターフェイスに関連付けられたセキュリティゾーンで、以下のサービスを許可します
-
IKE、高可用性、SSH
-
必要なルーティングプロトコルに応じたプロトコル。
-
BFD を使用して隣接ルートを監視します。
-
SRG0およびSRG1+では、以下のオプションを設定できます。
SRG0 および SRG1 では、以下のオプションを設定できます。
-
SRG1: アクティブ/バックアップ信号ルート、導入タイプ、アクティブ性優先度、プリエンプション、仮想IPアドレス(デフォルトゲートウェイ導入用)、アクティブ性プローブ、バックアップ時のパケット処理
-
SRG1:SRG1のBFD監視、IP監視、インターフェイス監視オプション。
-
SRG0: 障害時にシャットダウンし、障害時にインストールするルート オプション。
SRG1 で監視(BFD、IP、またはインターフェイス)オプションを設定する場合、SRG0 の下には障害発生時のシャットダウン オプションを設定しないことをお勧めします。
-
SRG1: アクティブ/バックアップ信号ルート、導入タイプ、アクティブ性優先度、プリエンプション、仮想IPアドレス(デフォルトゲートウェイ導入用)、アクティブ性プローブ、バックアップ時のパケット処理
-
SRG1:SRG1のBFD監視、IP監視、インターフェイス監視オプション。
-
SRG0: 障害時にシャットダウンし、障害時にインストールするルート オプション。
SRG1 で監視(BFD、IP、またはインターフェイス)オプションを設定する場合、SRG0 の下には障害発生時のシャットダウン オプションを設定しないことをお勧めします。
表1は 、この例で使用されているインターフェイス設定の詳細を示しています。
| デバイス | インターフェイスゾーン | IP | アドレス | に設定されています |
|---|---|---|---|---|
| SRX-01 | lo0 | 信頼できない |
10.11.0.1/32 |
フローティングIPアドレス IKEゲートウェイアドレス |
| 10.12.0.1/32 |
IKEゲートウェイアドレス |
|||
| ge-0/0/2 |
ICL |
10.22.0.2/24 |
ICLの接続 |
|
| ge-0/0/4 |
信頼 |
10.5.0.1/24 |
R2 ルーターに接続します。 |
|
| ge-0/0/3 |
信頼できない |
10.3.0.2/24 |
R1 ルーターに接続します |
|
| SRX-02 | lo0 |
信頼できない |
10.12.0.1/32 |
フローティングIPアドレス IKEゲートウェイアドレス |
| 10.11.0.1/32 |
IKEゲートウェイアドレス |
|||
| ge-0/0/2 |
ICL |
10.22.0.1/24 |
ICLの接続 |
|
| ge-0/0/3 |
信頼できない |
10.2.0.2/24 |
R1 ルーターに接続します |
|
| ge-0/0/4 |
信頼 |
10.4.0.1/24 |
R2 ルーターに接続します。 |
|
| SRX-03 | lo0 | 信頼できない |
10.112.0.1/32 |
IKEゲートウェイアドレス |
| 10.112.0.5/32 |
IKEゲートウェイアドレス |
|||
| ge-0/0/0 |
信頼できない |
10.7.0.1/24 |
R2 ルーターに接続します。 |
|
| ge-0/0/2 |
信頼 |
10.6.0.2/24 |
クライアントデバイスに接続します。 |
| に設定された | デバイス | インターフェイス | IPアドレス |
|---|---|---|---|
| R2 | lo0 | 10.111.0.2/32 |
R2のループバックインターフェイスアドレス |
| ge-0/0/1 |
10.4.0.2/24 |
SRX-02に接続 |
|
| ge-0/0/0 |
10.5.0.2/24 |
SRX-01に接続 |
|
| ge-0/0/2 |
10.7.0.2/24 |
SRX-03(VPNピアデバイス)に接続します。 |
|
| R1 | lo0 | 10.111.0.1/32 |
R1のループバックインターフェイスアドレス |
| ge-0/0/0 |
10.3.0.1/24 |
SRX-01に接続 |
|
| ge-0/0/1 |
10.2.0.1/24 |
SRX-02に接続 |
設定
始める前に
マルチノード高可用性用 SRXシリーズファイアウォールの設定には、Junos IKE パッケージが必要です。このパッケージは、SRXシリーズファイアウォールのデフォルトパッケージまたはオプションパッケージとして利用できます。詳細については、「 Junos IKEパッケージのサポート 」を参照してください。
パッケージがSRXシリーズファイアウォールにデフォルトでインストールされていない場合は、次のコマンドを使用してインストールします。ICL暗号化には、このステップが必要です。
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
CLIクイックコンフィグレーション
この例をすばやく設定するには、以下のコマンドをコピーしてテキストファイルに貼り付け、改行を削除し、ネットワーク設定に一致させる必要がある詳細情報を変更し、コマンドを [edit] 階層レベルでCLIにコピーアンドペーストして、設定モードから commit を入力します。
SRX-01デバイス
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability peer-id 2 peer-ip 10.22.0.1 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 set chassis high-availability peer-id 2 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 1 set chassis high-availability services-redundancy-group 2 peer-id 2 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 200 set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.3.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.3.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.5.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.5.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
SRX-02デバイス
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability peer-id 1 peer-ip 10.22.0.2 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 1 liveness-detection minimum-interval 200 set chassis high-availability peer-id 1 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set chassis high-availability services-redundancy-group 2 peer-id 1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 1 set security ike proposal ICL_IKE_PROP description interchassisa_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.1/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.2.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.4.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 1 family inet6 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/24 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.2.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.2.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.4.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.4.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/24 next-hop 10.4.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.4.0.2
SRX-3デバイス
set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG1_IKE_PROP dh-group group14 set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG2_IKE_PROP dh-group group14 set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 set security ike gateway SRG1_IKE_GW1 external-interface lo0 set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 set security ike gateway SRG1_IKE_GW1 version v2-only set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 set security ike gateway SRG2_IKE_GW500 external-interface lo0 set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 set security ike gateway SRG2_IKE_GW500 version v2-only set security ipsec proposal SRG1_IPSEC_PROP protocol esp set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set security ipsec proposal SRG2_IPSEC_PROP protocol esp set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces st0.500 set security zones security-zone untrust interfaces ge-0/0/1.0 set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone trust host-inbound-traffic system-services ike set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/2.0 set interfaces ge-0/0/0 description trust set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 set interfaces ge-0/0/1 description untrust set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 set interfaces ge-0/0/2 description trust set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.112.0.1/32 set interfaces lo0 unit 0 family inet address 10.112.0.5/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 500 family inet set routing-options autonomous-system 100 set routing-options static route 10.4.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.5.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
以下のセクションでは、ネットワークでマルチノード高可用性の設定に必要なルーターの設定スニペットを示します。
R1ルーター
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.3.0.1/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.2.0.1/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.1/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.1/32 preferred set routing-options autonomous-system 100 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.2.0.1 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.2.0.2 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.3.0.1 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.3.0.2
R2ルーター
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.5.0.2/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.4.0.2/24 set interfaces ge-0/0/2 description srx-3 set interfaces ge-0/0/2 unit 0 family inet address 10.7.0.2/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.2/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.2/32 preferred set routing-options autonomous-system 100 set routing-options static route 10.112.0.0/24 next-hop 10.7.0.1 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.4.0.2 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.4.0.1 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.5.0.2 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.5.0.1
設定
ステップバイステップの手順
SRX-01の設定を順を追って説明します。
次の例では、設定階層のさまざまなレベルに移動する必要があります。その方法の詳細については、『CLIユーザーガイド』の「構成モードでのCLIエディターの使用」を参照してください。
インターフェイスを設定します。
[edit] user@srx-1# set interfaces ge-0/0/2 description inter_chassis_link user@srx-1# set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 user@srx-1# set interfaces ge-0/0/3 description untrust user@srx-1# set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 user@srx-1# set interfaces ge-0/0/4 description trust user@srx-1# set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24
ge-0/0/3およびge-0/0/4インターフェイスを使用してアップストリームおよびダウンストリームルーターに接続し、ge-0/0/2インターフェイスを使用してICLを設定します。
ループバックインターフェイスを設定します。
[edit] user@srx-1# set interfaces lo0 apply-groups-except global user@srx-1# set interfaces lo0 description untrust user@srx-1# set interfaces lo0 unit 0 family inet address 10.11.0.1/32 user@srx-1# set interfaces lo0 unit 0 family inet address 10.12.0.1/32 user@srx-1# set interfaces st0 unit 1
ループバックインターフェイスにIPアドレス10.11.0.1および10.12.0.1を割り当てます。フローティングIPアドレスとして10.11.0.1を、IKEゲートウェイアドレスとして10.12.0.1を使用します。
セキュリティゾーンを設定し、ゾーンにインターフェイスを割り当て、セキュリティゾーンで許可されるシステムサービスを指定します。
[edit] user@srx-1# set security zones security-zone vpn host-inbound-traffic system-services ike user@srx-1# set security zones security-zone vpn host-inbound-traffic protocols all user@srx-1# set security zones security-zone vpn interfaces st0.1 user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ike user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ping user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone untrust interfaces lo0.0 user@srx-1# set security zones security-zone untrust interfaces ge-0/0/3.0 user@srx-1# set security zones security-zone trust host-inbound-traffic system-services all user@srx-1# set security zones security-zone trust host-inbound-traffic protocols all user@srx-1# set security zones security-zone trust interfaces ge-0/0/4.0 user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ike user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ping user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services high-availability user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ssh user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone icl_zone interfaces ge-0/0/2.0
インターフェイスge-0/0/3とge-0/0/4に、それぞれtrustゾーンとuntrustゾーンを割り当てます。lo0.0インターフェイスをuntrustゾーンに割り当てて、IPネットワーク経由で接続します。インターフェイスge-0/0/2をICLゾーンに割り当てます。このゾーンを使用してICLを設定します。VPN セキュリティ ゾーンにセキュア トンネル インターフェイスを割り当てます。
- ノードID、ローカルノードとピアノードのlPアドレス、ピアノードのインターフェイスなど、ローカルノードとピアノードの両方の詳細を設定します。
[edit] user@srx-1# set chassis high-availability local-id 1 user@srx-1# set chassis high-availability local-id local-ip 10.22.0.2 user@srx-1# set chassis high-availability peer-id 2 peer-ip 10.22.0.1 user@srx-1# set chassis high-availability peer-id 2 interface ge-0/0/2.0
ICLを使用してピアノードと通信するために、ge-0/0/2インターフェイスを使用します。
IPsec VPNプロファイルIPSEC_VPN_ICLをピアノードにアタッチします。
[edit] user@srx-1# set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN
ノード間のセキュアなICLリンクを確立するには、この設定が必要です。
ピアノードのBFD(双方向フォワーディング検出)プロトコルオプションを設定します。
[edit] user@srx-1# set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 user@srx-1# set chassis high-availability peer-id 2 liveness-detection multiplier 3
-
サービス冗長性グループSRG1およびSRG2を設定します。
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 deployment-type routing user@srx-1# set chassis high-availability services-redundancy-group 1 peer-id 2 user@srx-1# set chassis high-availability services-redundancy-group 2 peer-id 2
SRG1 と SRG2 の両方のアクティブ性判定パラメータをセットアップします。
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.11.0.1
フローティングIPアドレスを送信元IPアドレス(SRG1の場合は10.11.0.1、SRG2の場合は10.12.0.1)として、アップストリームルーターのIPアドレスを宛先IPアドレス(10.111.0.1)としてアクティブ性判定プローブに使用します。
IP監視とアクティビティプローブ用に最大64個のIPアドレスを設定できます。合計64個のIPアドレスは、IPv4とIPv6アドレスの数の合計です)
SRG1 と SRG2 の BFD 監視パラメーターを設定して、ネットワークの障害を検出します。
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4
アクティブ性の適用に必要なアクティブ信号ルートを設定します。
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 user@srx-1# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 user@srx-1# set chassis high-availability services-redundancy-group 1 preemption user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-priority 1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 user@srx-1# set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 user@srx-1# set chassis high-availability services-redundancy-group 2 preemption user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-priority 200
注:policy-optionsステートメントでroute-existsポリシーとともにアクティブな信号ルートを指定する必要があります。if-route-exists条件でactive-signal-routeを設定すると、HAモジュールこのルートをルーティングテーブルに追加します。IKEゲートウェイのローカルアドレスを含めてIPプレフィックスリストを作成し、IPプレフィックスリストをSRG1とSRG2に関連付けます。
SRG1
[edit] user@srx-1# set policy-options prefix-list SRG1_PFX 10.11.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX
SRG2
[edit] user@srx-1# set policy-options prefix-list SRG2_PFX 10.12.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX
この設定は、特定のIPsec VPNトンネルを特定のセキュリティデバイスに固定します。
SRG1 と SRG2 の両方で IPsec VPN サービスを有効にします。
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 managed-services ipsec user@srx-1# set chassis high-availability services-redundancy-group 2 managed-services ipsec
ICLのIPSec VPNオプションを設定します。
Internet Key Exchange(IKE)設定を定義します。IKE設定は、セキュアな接続の確立に使用するアルゴリズムとキーを定義します。
[edit] user@srx-1# set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel user@srx-1# set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys user@srx-1# set security ike proposal ICL_IKE_PROP dh-group group14 user@srx-1# set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 user@srx-1# set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc user@srx-1# set security ike proposal ICL_IKE_PROP lifetime-seconds 300 user@srx-1# set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel user@srx-1# set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP user@srx-1# set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" user@srx-1# set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL user@srx-1# set security ike gateway ICL_IKE_GW version v2-only
マルチノード高可用性機能では、IKEバージョンを
v2-only-
IPsecプロポーザルプロトコルと暗号化アルゴリズムを指定します。IPsecオプションを指定して、2台の参加デバイス間にIPsecトンネルを作成し、VPN通信を保護します。
[edit] user@srx-1# set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel user@srx-1# set security ipsec proposal ICL_IPSEC_PROP protocol esp user@srx-1# set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm user@srx-1# set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 user@srx-1# set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel user@srx-1# set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL
ha-link-encryptionオプションを指定すると、ICLが暗号化され、ノード間の高可用性トラフィックフローが保護されます。set chassis high-availability peer-id <id> vpn-profile vpn_profile設定でvpn_profileに同じVPN名ICL_IPSEC_VPNを記載する必要があります。
セキュリティポリシーを設定します。
[edit] user@srx-1# set security policies default-policy permit-all
この例では、すべてのトラフィックを許可するポリシーを設定しました。ネットワーク要件に従ってセキュリティポリシーを作成し、組織のポリシーで許可されているトラフィックを許可し、それ以外のトラフィックはすべて拒否することを強くお勧めします。この例では、デモ目的でのみデフォルトポリシーを使用しています。
ルーティングオプションを設定します。
[edit] user@srx-1# set routing-options autonomous-system 100 user@srx-1# set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 user@srx-1# set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
ポリシーオプションを設定します。
[edit] user@srx-1# set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term default then reject user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0
アクティブ信号ルート10.39.1.1(SRG1)および10.49.1.1(SRG2)をルート一致条件(
if-route-exists)で設定します。マルチノードの高可用性は、ノードがアクティブなロールに移動すると、このルートをルーティングテーブルに追加します。また、ノードは、より高い優先度の高いルートのアドバタイズを開始します。バックアップ信号ルート(10.39.1.2および10.49.1.2)を設定して、バックアップノードを中程度の優先度でアドバタイズします。障害が発生した場合、高可用性リンクはダウンし、現在のアクティブなノードはプライマリロールを解放し、アクティブシグナルルートを削除します。これで、バックアップ ノードがプローブを通じて状態を検出し、アクティブ ロールに遷移します。ルート優先度がスワップされ、すべてのトラフィックを新しいアクティブノードに駆動しますBFDピアリングセッションオプションを設定し、ライブ検出タイマーを指定します。
[edit] user@srx-1# set protocols bgp group trust type internal user@srx-1# set protocols bgp group trust local-address 10.3.0.2 user@srx-1# set protocols bgp group trust export mnha-route-policy user@srx-1# set protocols bgp group trust local-as 100 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group trust neighbor 10.3.0.1 user@srx-1# set protocols bgp group untrust type internal user@srx-1# set protocols bgp group untrust local-address 10.5.0.1 user@srx-1# set protocols bgp group untrust export mnha-route-policy user@srx-1# set protocols bgp group untrust local-as 100 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group untrust neighbor 10.5.0.2
IPsec VPN設定(SRX-1およびSRX-2)
以下の手順を使用して、ピアSRXシリーズファイアウォールとのIPsec VPN接続を設定します。この例では、すべてのIPsec VPN設定ステートメントをvpn_configという名前のJUNOS設定グループ内に配置します。
- 設定の最上位に構成グループ
vpn_configを作成し、IPsec VPN固有の詳細を設定します。[edit] set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 500 family inet
apply-groupsステートメントを設定に含めて、vpn_config設定グループからステートメントを継承します。
[edit] user@srx-1# set apply-groups vpn_config
設定(SRX-03)(VPNピアデバイス)
ステップバイステップの手順
IKEプロポーザルを作成します。
[edit] user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG1_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG2_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600
IKEポリシーを定義します。
[edit] user@srx-3# set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP user@srx-3# set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" user@srx-3# set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP user@srx-3# set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123"
IKEゲートウェイを作成し、アドレスを定義し、外部インターフェイスとバージョンを指定します。
[edit] user@srx-3# set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 user@srx-3# set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 external-interface lo0 user@srx-3# set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 version v2-only user@srx-3# set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 user@srx-3# set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 user@srx-3# set security ike gateway SRG2_IKE_GW500 external-interface lo0 user@srx-3# set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 user@srx-3# set security ike gateway SRG2_IKE_GW500 version v2-only
IPsecプロポーザルを作成します。
[edit] user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800
IPsecポリシーを作成します。
[edit] user@srx-3# set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP user@srx-3# set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP
IPsecプロポーザルの参照(IKEゲートウェイ、IPsecポリシー、バインドするインターフェイス、トラフィックセレクター)を指定します。
[edit] user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately
セキュリティポリシーを作成します。
[edit] user@srx-3# set security policies default-policy permit-all
この例では、すべてのトラフィックを許可するポリシーを設定しました。ネットワーク要件に従ってセキュリティポリシーを作成し、組織のポリシーで許可されているトラフィックを許可し、それ以外のトラフィックはすべて拒否することを強くお勧めします。この例では、デモ目的でのみデフォルトポリシーを使用しています。
インターフェイスを設定します。
[edit] user@srx-3# set interfaces ge-0/0/0 description trust user@srx-3# set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 user@srx-3# set interfaces ge-0/0/1 description untrust user@srx-3# set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 user@srx-3# set interfaces ge-0/0/2 description trust user@srx-3# set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 user@srx-3# set interfaces lo0 description untrust user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.1/32 user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.5/32 user@srx-3# set interfaces st0 unit 1 family inet user@srx-3# set interfaces st0 unit 500 family inet
セキュリティゾーンを定義し、インターフェイスを追加します。
[edit] user@srx-3# set security zones security-zone untrust host-inbound-traffic system-services all user@srx-3# set security zones security-zone untrust host-inbound-traffic protocols all user@srx-3# set security zones security-zone untrust interfaces st0.1 user@srx-3# set security zones security-zone untrust interfaces lo0.0 user@srx-3# set security zones security-zone untrust interfaces st0.500 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/1.0 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/0.0 user@srx-3# set security zones security-zone trust host-inbound-traffic system-services all user@srx-3# set security zones security-zone trust host-inbound-traffic protocols all user@srx-3# set security zones security-zone trust interfaces ge-0/0/2.0
静的ルートを設定します。
[edit] user@srx-3# set routing-options autonomous-system 100 user@srx-3# set routing-options static route 10.4.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.5.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
結果 (SRX-01)
設定モードから、以下のコマンドを入力して設定を確認します。
出力に意図した設定が表示されない場合は、この例の設定手順を繰り返して修正します。
[edit]
user@srx-1# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-1# show chassis high-availability
local-id 1 local-ip 10.22.0.2;
peer-id 2 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
services-redundancy-group 2 {
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
[edit]
user@srx-1# show security ike
proposal ICL_IKE_PROP {
description interchassis_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-1# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-1# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/16 orlonger;
10.1.0.0/16 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/16 orlonger;
10.8.0.0/16 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-1# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/16 next-hop 10.5.0.2;
route 10.112.0.0/24 next-hop 10.5.0.2;
}
[edit]
user@srx-1# show security zones
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-1# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.3.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.5.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1;
}
デバイスの設定が完了したら、設定モードから commit を入力します。
結果 (SRX-02)
設定モードから、以下のコマンドを入力して設定を確認します。出力に意図した設定が表示されない場合は、この例の設定手順を繰り返して修正します。
[edit]
user@srx-2# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-2# show chassis high-availability
local-id 2 local-ip 10.22.0.1;
peer-id 1 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
services-redundancy-group 2 {
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
[edit]
user@srx-2# show security ike
proposal ICL_IKE_PROP {
description interchassisa_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-2# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-2# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/24 orlonger;
10.1.0.0/24 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/24 orlonger;
10.8.0.0/24 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-2# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/24 next-hop 10.4.0.2;
route 10.112.0.0/24 next-hop 10.4.0.2;
}
[edit]
user@srx-2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-2# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.2.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.4.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1 {
family inet;
}
}
デバイスの設定が完了したら、設定モードから commit を入力します。
user@host# commit warning: High Availability Mode changed, please reboot the device to avoid undesirable behavior commit complete
結果(SRX-3)(VPNピアデバイス)
設定モードから、以下のコマンドを入力して設定を確認します。出力に意図した設定が表示されない場合は、この例の設定手順を繰り返して修正します。
[edit]
user@srx-3# show security ike
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.11.0.1;
external-interface lo0;
local-address 10.112.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.12.0.1;
external-interface lo0;
local-address 10.112.0.5;
version v2-only;
}
[edit]
user@srx-3# show security ipsec
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.7.0.2/32;
remote-ip 10.1.0.2/32;
}
establish-tunnels immediately;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts1 {
local-ip 10.9.0.2/32;
remote-ip 10.8.0.2/32;
}
establish-tunnels immediately;
}
[edit]
user@srx-3# show routing-options
autonomous-system 100;
static {
route 10.4.0.0/24 next-hop 10.7.0.2;
route 10.5.0.0/24 next-hop 10.7.0.2;
route 10.11.0.0/24 next-hop 10.7.0.2;
route 10.12.0.0/24 next-hop 10.7.0.2;
route 10.111.0.1/32 next-hop 10.7.0.2;
route 10.111.0.2/32 next-hop 10.7.0.2;
}
[edit]
user@srx-3# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
lo0.0;
st0.500;
ge-0/0/1.0;
ge-0/0/0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-3# show interfaces
ge-0/0/0 {
description trust;
unit 0 {
family inet {
address 10.7.0.1/24;
}
}
}
ge-0/0/1 {
description untrust;
unit 0 {
family inet {
address 10.6.0.2/24;
}
}
}
ge-0/0/2 {
description trust;
unit 0 {
family inet {
address 10.9.0.1/24;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.112.0.1/32;
address 10.112.0.5/32;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 500 {
family inet;
}
}
デバイスの設定が完了したら、設定モードから commit を入力します。
検証
設定が正常に機能していることを確認します。
- マルチノード高可用性の詳細を確認する
- マルチノード高可用性の詳細を確認する
- マルチノード高可用性ピアノードステータスの確認
- マルチノード高可用性サービス冗長性グループの確認
- シャーシ間リンク(ICL)暗号化ステータスの確認
- リンク暗号化トンネル統計情報の検証
- シャーシ間リンクアクティブピアの確認
- VPNステータスの確認
- IPsecセキュリティアソシエーションの詳細を表示する
- SRGごとのアクティブピアの表示
- IPプレフィックスからSRGへのマッピングを表示する
- BGPセッション情報を表示します。
マルチノード高可用性の詳細を確認する
目的
セキュリティデバイスに設定されたマルチノード高可用性設定の詳細を表示および検証します。
アクション
動作モードから、以下のコマンドを実行します。
SRX-1では
user@srx-01> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
SRX-2では
user@srx-02> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.1
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
意味
コマンド出力からこれらの詳細を確認します。
ローカルノードとピアノードの詳細(IP アドレスや ID など)
フィールド
Encrypted: YESは、トラフィックが保護されていることを示します。フィールド
Deployment Type: ROUTINGは、レイヤー3モード設定、つまり、ネットワークの両側にルーターがあることを示します。フィールド
Services Redundancy Group: 1とServices Redundancy Group: 2は、そのノード上のSRG1およびSRG2のステータス(アクティブまたはバックアップ)を示します。
マルチノード高可用性の詳細を確認する
目的
セキュリティデバイスに設定されたマルチノード高可用性設定の詳細を表示および検証します。
アクション
動作モードから、以下のコマンドを実行します。
SRX-01の場合
user@srx-01> show chassis high-availability information detail
Node level Information:
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
HA Peer Conn events:
Jan 31 00:55:19.249 : HA Peer 180.100.1.1 BFD conn came up
Cold Synchronization:
Status:
Cold synchronization completed for: N/A
Cold synchronization failed for: N/A
Cold synchronization not known for: N/A
Current Monitoring Weight: 0
Progress:
CS Prereq 1 of 1 SPUs completed
1. if_state sync 1 SPUs completed
2. ha peer conn 1 SPUs completed
3. policy data sync 1 SPUs completed
4. cp ready 1 SPUs completed
5. VPN data sync 1 SPUs completed
6. IPID data sync 1 SPUs completed
7. All SPU ready 1 SPUs completed
8. AppID ready 1 SPUs completed
9. Tunnel Sess ready 1 SPUs completed
CS RTO sync 1 of 1 SPUs completed
CS Postreq 1 of 1 SPUs completed
Statistics:
Number of cold synchronization completed: 0
Number of cold synchronization failed: 0
Events:
Jan 31 00:55:24.616 : Cold sync for PFE is Post-req check in process
Jan 31 00:55:25.615 : Cold sync for PFE is Completed
SPU monitoring:
Status: Enabled
Current monitoring weight: 0
Statistics:
SPU up count: 1
NPC up count: 0
SPU down count: 0
NPC down count: 0
Chassis info processing error count: 0
Loopback Information:
PIC Name Loopback Nexthop Mbuf
-------------------------------------------------
Success Success Success
Hardware monitoring:
Status:
Activation status: Enabled
Ctrl Plane Hardware errors: 0
Data Plane Hardware errors: 0
SRGS Information:
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: ACTIVE
Last Advertised Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.347 : SRG[1] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:56:33.046 : SRG[1] state HOLD -> BACKUP, Reason: Peer state Active received
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:12.695 : SRG[1] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
SRGS Information:
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: BACKUP
Last Advertised Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.439 : SRG[2] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:55:24.263 : SRG[2] state HOLD -> ACTIVE, Reason: Local Priority Higher
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:13.698 : SRG[2] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
意味
コマンド出力からこれらの詳細を確認します。
フィールド
Services: [ IPSEC ]は、各SRGに関連するIPSec VPNを示します。BFD Monitoring、Interface Monitoring、Split-brain Prevention Probe Infoフィールドには、監視の詳細が表示されます。Cold Synchronizationフィールドには、現在のステータスと最近の変更SRG State Change Events詳細が表示されます。フィールド
Services Redundancy Group: 1とServices Redundancy Group: 2は、そのノード上のSRG1およびSRG2(アクティブまたはバックアップ)のステータスを示します。
コマンド出力では、IP 180.100.1.2などのIPアドレスはJunos OSによって内部的に生成され、これらのアドレスはルーティングテーブルに干渉しません。
マルチノード高可用性ピアノードステータスの確認
目的
ピアノードの詳細を表示および検証します。
アクション
動作モードから、SRX-01 および SRX-02 で以下のコマンドを実行します。
SRX-01
user@srx-01> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
SRX-02
user@srx-02> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.1
Internal Peer-IP: 180.100.1.2
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 6 4
SRG Status Ack 4 4
Attribute Msg 2 1
Attribute Ack 1 1
意味
コマンド出力からこれらの詳細を確認します。
使用されているインターフェイス、IPアドレス、IDなどのピアノードの詳細
暗号化ステータス、接続ステータス、コールド同期ステータス
ノード全体のパケット統計情報
マルチノード高可用性サービス冗長性グループの確認
目的
SRG が正しく設定され、動作していることを確認します。
アクション
動作モードから、両方のセキュリティデバイスで以下のコマンドを実行します。
SRX-02 上の SRG1
user@srx-02> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRX-02上のSRG2
user@srx-02> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
SRX-01 の SRG1
user@srx-01> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRX-01 上の SRG2
user@srx-01> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
意味
コマンド出力からこれらの詳細を確認します。
導入タイプ、ステータス、アクティブおよびバックアップ信号ルートなどのピアノードの詳細。
スプリットブレイン防止プローブ、IP監視、BFD監視ステータス
関連付けられたIPプレフィックステーブル。
シャーシ間リンク(ICL)暗号化ステータスの確認
目的
シャーシ間リンク(ICL)ステータスを確認します。
アクション
SRX-01で次のコマンドを実行します。
user@srx-01> show security ipsec security-associations ha-link-encryption Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <495002 ESP:aes-gcm-256/aes256-gcm 0x0008d9c7 236/ unlim - root 500 10.22.0.1 >495002 ESP:aes-gcm-256/aes256-gcm 0x0001a573 236/ unlim - root 500 10.22.0.1
user@srx-01> show security ike security-associations ha-link-encryption Index State Initiator cookie Responder cookie Mode Remote Address 16776938 UP 9f8fe46ce3be92f8 44e6b3fd74cc9294 IKEv2 10.22.0.1
user@srx-01> show security ipsec security-associations ha-link-encryption detail
ID: 495002 Virtual-system: root, VPN Name: ICL_IPSEC_VPN
Local Gateway: 10.22.0.2, Remote Gateway: 10.22.0.1
Traffic Selector Name: __ICL_IPSEC_VPN__multi_node__
Local Identity: ipv4(180.100.1.2-180.100.1.2)
Remote Identity: ipv4(180.100.1.1-180.100.1.1)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: No
PFS group: N/A
SRG ID: 0
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.16000, Policy-name: ICL_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
HA Link Encryption Mode: Multi-Node
Location: FPC -, PIC -, KMD-Instance -
Anchorship: Thread -
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x0008d9c7, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
Direction: outbound, SPI: 0x0001a573, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
意味
コマンド出力は、以下の情報を提供します。
ローカルゲートウェイとリモートゲートウェイの詳細。
PIC内の各スレッドのIPsec SAペア
HAリンク暗号化モード(次の行を参照):
HA Link Encryption Mode: Multi-Node使用される認証および暗号化アルゴリズム
コマンド出力に示されているIP範囲(180.100.1.x)は、ICL IPsecトラフィックセレクターとして機能します。このIP範囲はシステムによって動的に割り当てられるため、変更や修正を行わないことが不可欠です。さらに、BFD(双方向フォワーディング検出)が、より広い180.x.x.x IP範囲に対して自動的に有効になります。
リンク暗号化トンネル統計情報の検証
目的
アクティブノードとバックアップノードの両方で、リンク暗号化トンネルの統計を確認します。
アクション
SRX-01で次のコマンドを実行します。
user@srx-01> show security ipsec statistics ha-link-encryption ESP Statistics: Encrypted bytes: 106294156 Decrypted bytes: 51961287 Encrypted packets: 979531 Decrypted packets: 989651 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
意味
VPN 全体でパケット損失の問題が発生した場合、 show security ipsec statistics ha-link-encryption コマンドを数回実行して、暗号化および復号化されたパケット カウンターが増加していることを確認できます。また、他のエラー カウンターが増加しているかどうかも確認する必要があります。
clear security ipsec security-associations ha-link-encryptionコマンドを使用して、すべてのIPsec統計情報をクリアします。
シャーシ間リンクアクティブピアの確認
目的
ICLアクティブピアのみ表示し、通常のIKEアクティブピアは表示しません。
アクション
SRX-01 および SRX-02 デバイスで以下のコマンドを実行します。
SRX-1
user@srx-01> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.1 500 10.22.0.1 not available 0.0.0.0
SRX-2
user@srx-02> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.2 500 10.22.0.2 not available 0.0.0.0
意味
コマンド出力には、ICLのアクティブピアのみと、アクティブピアが使用しているピアアドレスやポートなどの詳細が表示されます。
VPNステータスの確認
目的
SRGレベルでIKEセキュリティアソシエーションのステータスを確認して、IKEステータスを確認します。
アクション
SRX-1、SRX-2、およびSRX-3(VPNピアデバイス)で以下のコマンドを実行します。
SRX-01
user@srx-01> show security ike security-associations srg-id 1
Index State Initiator cookie Responder cookie Mode Remote Address
16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-01> show security ike security-associations srg-id 2
Index State Initiator cookie Responder cookie Mode Remote Address
33554536 UP 9944aaf1ab914b42 15cef0da496bdd92 IKEv2 10.112.0.5
SRX-02
user@srx-02> show security ike security-associations srg-id 1 Index State Initiator cookie Responder cookie Mode Remote Address 16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-02> show security ike security-associations srg-id 2 Index State Initiator cookie Responder cookie Mode Remote Address 33554534 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.112.0.5
SRX-3(VPNピアデバイス)
user@srx-03> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 5929032 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.12.0.1 5929033 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.11.0.1
意味
出力は以下を示しています。
- リモートピアのIPアドレス。
- 両方のリモートピアで UP と表示されている状態は、フェーズ 1 確立の関連付けが成功したことを示します。
- リモートピアIPアドレス、IKEポリシー、外部インターフェイスはすべて正しい。
IPsecセキュリティアソシエーションの詳細を表示する
目的
SRG IDで識別される個々のIPsec SAの詳細を表示します。
アクション
SRXシリーズファイアウォールで次のコマンドを実行します。
SRX-1
user@srx-01> show security ipsec security-associations srg-id 1 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1210/ unlim - root 500 10.112.0.1 >17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1210/ unlim - root 500 10.112.0.1
user@srx-01> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1382/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1382/ unlim - root 500 10.112.0.5
SRX-02
user@srx-02> show security ipsec security-associations srg-id 1
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1286/ unlim - root 500 10.112.0.1
>17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1286/ unlim - root 500 10.112.0.1
user@srx-02> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1461/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1461/ unlim - root 500 10.112.0.5
SRX-03
user@srx-03> show security ipsec security-associations
Total active tunnels: 2 Total Ipsec sas: 2
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<67108865 ESP:aes-cbc-256/sha256 6d1e9c89 1392/ unlim - root 500 10.11.0.1
>67108865 ESP:aes-cbc-256/sha256 c50520d4 1392/ unlim - root 500 10.11.0.1
<67108866 ESP:aes-cbc-256/sha256 f41d091c 1570/ unlim - root 500 10.12.0.1
>67108866 ESP:aes-cbc-256/sha256 9feb290c 1570/ unlim - root 500 10.12.0.1
意味
出力にはVPNの状態が表示されます。
SRGごとのアクティブピアの表示
目的
使用しているピアアドレスとポートを持つ、接続されたアクティブピアのリストを表示します。
アクション
SRXシリーズファイアウォールで以下のコマンドを実行します。
SRX-01
user@srx-01> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-01> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
SRX-02
user@srx-02> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-02> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
意味
出力には、接続されたデバイスのリストと、使用されたピアアドレスとポートに関する詳細が表示されます。
IPプレフィックスからSRGへのマッピングを表示する
目的
IPプレフィックスからSRGへのマッピング情報を表示します。
アクション
SRX-01デバイスで以下のコマンドを実行します。
user@srx-01> show chassis high-availability prefix-srgid-table
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
2 10.12.0.0/24 default
意味
出力は、設定でSRGにマッピングされたIPアドレスプレフィックスを示しています。
BGPセッション情報を表示します。
目的
BGPとそのネイバーに関する概要情報を表示して、ピアからルートを受信しているかどうかを判断します。
アクション
SRXシリーズファイアウォールで以下のコマンドを実行します。
SRX-1デバイス
user@srx-01> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.3.0.1 100 37 40 0 0 15:43 Establ
inet.0: 0/0/0/0
10.5.0.2 100 37 40 0 0 15:42 Establ
inet.0: 0/0/0/0
SRX-2デバイス
user@srx-02> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn St ate|#Active/Received/Accepted/Damped...
10.2.0.1 100 842 846 0 0 6:18:40 Es tabl
inet.0: 0/0/0/0
10.4.0.2 100 842 846 0 0 6:18:42 Es tabl
inet.0: 0/0/0/0
意味
出力は、BGPセッションが確立され、ピアが更新メッセージを交換していることを示しています。
