SUR CETTE PAGE
Exemple : Configuration d’un VPN IPSec en haute disponibilité multinodale active-active dans un réseau de couche 3
Cet exemple montre comment configurer et vérifier le VPN IPsec pour une configuration de haute disponibilité multi nodale active-active.
Vue d’ensemble
En haute disponibilité multi-nœuds, les pare-feu SRX Series participants fonctionnent comme des nœuds indépendants dans un réseau de couche 3. Les nœuds sont connectés à des infrastructures adjacentes appartenant à différents réseaux. Une liaison logique interchâssis (ICL) chiffrée relie les nœuds sur un réseau routé. Les nœuds participants se sauvegardent mutuellement pour assurer un basculement rapide et synchronisé en cas de défaillance du système ou du matériel.
Vous pouvez utiliser la haute disponibilité multinodale en mode actif-actif avec la prise en charge de plusieurs groupes de redondance de services (SRG). Dans ce mode, certains SRG restent actifs sur un nœud et d’autres restent actifs sur un autre nœud.
La haute disponibilité multinodale prend en charge le VPN IPsec en mode actif-actif avec plusieurs SRG (SRG1+). Dans ce mode, vous pouvez établir plusieurs tunnels actifs à partir des deux nœuds, en fonction de l’activité SRG. La haute disponibilité multi nodale établit un tunnel IPsec et effectue des échanges de clés en associant l’adresse IP de terminaison (qui identifie également les tunnels se terminant dessus) à la passerelle de recherche. Étant donné que différents SRG1+ peuvent être en état actif ou en état de sauvegarde sur chacun des appareils, la haute disponibilité multinodale dirige efficacement le trafic correspondant vers le SRG1 actif correspondant. Étant donné que différents SRG peuvent être actifs sur différents nœuds, les tunnels appartenant à ces SRG apparaissent sur les deux nœuds de manière indépendante.
Nous prenons en charge une configuration à deux nœuds dans la solution de haute disponibilité multi-nœuds.
Exigences
Cet exemple utilise les composants matériels et logiciels suivants :
Deux pare-feu SRX Series (les appareils pris en charge sont SRX5400, SRX5600 et SRX5800 avec SPC3, IOC3, SCB3, SCB4 et RE3)
Junos OS version 22.4R1
Dans cet exemple, nous avons utilisé deux plates-formes de routage MX Series de Juniper Networks comme routeurs en amont/en aval.
Avant de commencer
Configurez le filtrage du pare-feu sans état et la qualité de service (QoS) en fonction des exigences de votre réseau, et disposez de stratégies de sécurité appropriées pour gérer le trafic sur votre réseau.
Dans un déploiement haute disponibilité classique, vous disposez de plusieurs routeurs et commutateurs sur les côtés nord et sud du réseau. Pour cet exemple, nous utilisons deux routeurs de part et d’autre des pare-feu SRX Series. Assurez-vous d'avoir configuré les routeurs en amont et en aval en fonction des exigences de votre réseau.
Installez le package Junos IKE sur vos pare-feu SRX Series à l’aide de la
request system software add optional://junos-ike.tgzcommande. Lejunos-ikepackage est inclus dans vos packages logiciels Junos (Junos OS version 20.4R1 et ultérieure).
Topologie
La figure 1 illustre la topologie utilisée dans cet exemple.
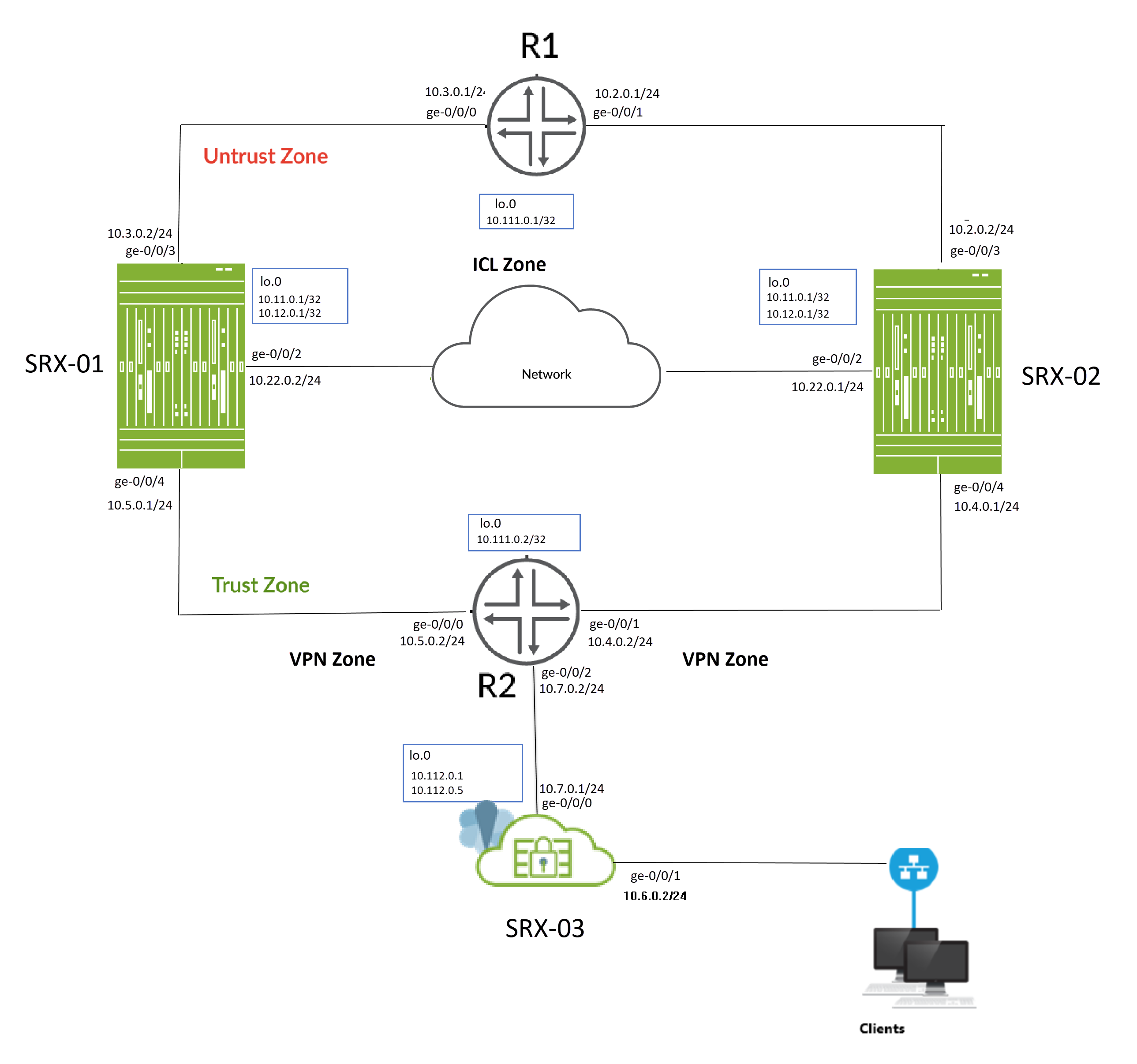 de couche 3
de couche 3
Comme le montre la topologie, deux pare-feu SRX Series (SRX-1 et SRX-2) sont connectés à des routeurs adjacents côté confiance et non confiance, formant un voisinage BGP. Une liaison logique interchâssis (ICL) chiffrée relie les nœuds sur un réseau routé. Les nœuds communiquent entre eux à l’aide d’une adresse IP routable (adresse IP flottante) sur le réseau.
L’équipement SRX-03 agit comme un appareil homologue à la configuration haute disponibilité multi nodale et établit des tunnels VPN IPsec avec les appareils SRX-01 et SRX-02.
Vous allez effectuer les tâches suivantes pour créer une configuration haute disponibilité multi nodale :
- Configurez une paire de pare-feu SRX Series en tant que nœuds locaux et pairs en attribuant des ID.
- Configurez les groupes de redondance des services (SRG1 et SRG2).
- Configurez une interface de bouclage (lo0.0) pour héberger l’adresse IP flottante et atteindre la passerelle homologue. L’utilisation de l’interface de bouclage garantit qu’en tout point, le trafic des routeurs adjacents sera dirigé vers l’adresse IP flottante (c’est-à-dire vers le nœud actif).
- Configurer les sondes IP pour la détermination et l’application de l’activité
- Configurez une route de signal requise pour l’application de l’activité et utilisez-la avec la stratégie Route Exist.
- Configurez un profil VPN pour le trafic haute disponibilité (ICL) à l’aide d’IKEv2.
- Configurer les options de surveillance BFD
- Configurer une politique de routage et des options de routage
- Configurez les interfaces et les zones en fonction des besoins de votre réseau. Vous devez autoriser des services tels que IKE pour le chiffrement des liens et SSH pour la synchronisation de la configuration en tant que services système entrants sur l’hôte sur la zone de sécurité associée à la liste ICL.
-
Créez une configuration de groupe pour le VPN IPsec sur les appareils SRX-01 et SRX-02 afin de configurer un tunnel avec un appareil homologue VPN (SRX-03). Les groupes de configuration vous permettent d’appliquer des éléments communs qui sont réutilisés dans la même configuration.
- Configurez les options VPN IPsec pour établir des tunnels avec l’appareil SRX-03 et activez la synchronisation de la configuration VPN IPsec sur les deux appareils (SRX-01 et SRX-02) à l’aide de l’option [groups].
- Configurer un appareil homologue VPN avec des options VPN IPsec.
Pour la liaison interchâssis (ICL), nous recommandons la configuration suivante :
-
En général, vous pouvez utiliser Aggregated Ethernet (AE) ou un port Ethernet payant sur les pare-feu SRX Series pour configurer une connexion ICL. Dans cet exemple, nous avons utilisé des ports GE pour l'ICL. Nous avons également configuré une instance de routage pour le chemin ICL afin d'assurer une segmentation maximale.
- N’utilisez pas les ports HA dédiés (ports de contrôle et de fabric) s’ils sont disponibles sur votre pare-feu SRX Series).
- Set MTU de 1514
- Autoriser les services suivants sur la zone de sécurité associée aux interfaces utilisées pour ICL
-
IKE, haute disponibilité, SSH
-
en fonction du protocole de routage dont vous avez besoin.
-
BFD pour surveiller les routes voisines.
-
Vous pouvez configurer les options suivantes sur SRG0 et SRG1+ :
Vous pouvez configurer les options suivantes sur SRG0 et SRG1 :
-
SRG1 : Route du signal actif/de secours, type de déploiement, priorité d’activité, préemption, adresse IP virtuelle (pour les déploiements de passerelle par défaut), sondage d’activité et traitement des paquets de secours.
-
SRG1 : options de surveillance BFD, de surveillance IP et de surveillance d’interface sur SRG1.
-
SRG0 : options de route d’arrêt en cas d’échec et d’installation en cas d’échec.
Lorsque vous configurez les options de surveillance (BFD ou IP ou Interface) sous SRG1, nous vous recommandons de ne pas configurer l’option d’arrêt en cas de défaillance sous SRG0.
-
SRG1 : Route du signal actif/de secours, type de déploiement, priorité d’activité, préemption, adresse IP virtuelle (pour les déploiements de passerelle par défaut), sondage d’activité et traitement des paquets de secours.
-
SRG1 : options de surveillance BFD, de surveillance IP et de surveillance d’interface sur SRG1.
-
SRG0 : options de route d’arrêt en cas d’échec et d’installation en cas d’échec.
Lorsque vous configurez les options de surveillance (BFD ou IP ou Interface) sous SRG1, nous vous recommandons de ne pas configurer l’option d’arrêt en cas de défaillance sous SRG0.
Le Tableau 1 présente les détails sur la configuration des interfaces utilisée dans cet exemple.
| Adresse IP | de la zone | d’interface | de l’équipement | configurée pour |
|---|---|---|---|---|
| SRX-01 | lo0 | Méfiance |
10.11.0.1/32 |
Adresse IP flottante Adresse de la passerelle IKE |
| 10.12.0.1/32 |
Adresse de la passerelle IKE |
|||
| GE-0/0/2 |
ICL |
10.22.0.2/24 |
Connexion ICL |
|
| GE-0/0/4 |
Confiance |
10.5.0.1/24 |
Se connecte au routeur R2 |
|
| GE-0/0/3 |
Méfiance |
10.3.0.2/24 |
Se connecte au routeur R1 |
|
| SRX-02 | lo0 |
Méfiance |
10.12.0.1/32 |
Adresse IP flottante Adresse de la passerelle IKE |
| 10.11.0.1/32 |
Adresse de la passerelle IKE |
|||
| GE-0/0/2 |
ICL |
10.22.0.1/24 |
Connexion ICL |
|
| GE-0/0/3 |
Méfiance |
10.2.0.2/24 |
Se connecte au routeur R1 |
|
| GE-0/0/4 |
Confiance |
10.4.0.1/24 |
Se connecte au routeur R2 |
|
| SRX-03 | lo0 | Méfiance |
10.112.0.1/32 |
Adresse de la passerelle IKE |
| 10.112.0.5/32 |
Adresse de la passerelle IKE |
|||
| GE-0/0/0 |
Méfiance |
10.7.0.1/24 |
Se connecte au routeur R2 |
|
| GE-0/0/2 |
Confiance |
10.6.0.2/24 |
Se connecte à l’appareil client |
| Adresse IP | de l’interface | de l’équipement | configurée pour |
|---|---|---|---|
| R2 | lo0 | 10.111.0.2/32 |
Adresse de l’interface de bouclage de R2 |
| GE-0/0/1 |
10.4.0.2/24 |
Se connecte au SRX-02 |
|
| GE-0/0/0 |
10.5.0.2/24 |
Se connecte au SRX-01 |
|
| GE-0/0/2 |
10.7.0.2/24 |
Se connecte au SRX-03 (appareil homologue VPN) |
|
| R1 | lo0 | 10.111.0.1/32 |
Adresse de l’interface de bouclage de R1 |
| GE-0/0/0 |
10.3.0.1/24 |
Se connecte au SRX-01 |
|
| GE-0/0/1 |
10.2.0.1/24 |
Se connecte au SRX-02 |
La configuration
- Avant de commencer
- Configuration rapide de la CLI
- La configuration
- Configuration (SRX-03) (périphérique homologue VPN)
- Résultats (SRX-01)
- Résultats (SRX-02)
- Résultats (SRX-3) (appareil pair VPN)
Avant de commencer
Le package Junos IKE est requis sur vos pare-feu SRX Series pour une configuration haute disponibilité multi nodale. Ce package est disponible en tant que package par défaut ou en tant que package optionnel sur les pare-feu SRX Series. Voir Prise en charge du package Junos IKE pour plus de détails.
Si le package n’est pas installé par défaut sur votre pare-feu SRX Series, utilisez la commande suivante pour l’installer. Vous avez besoin de cette étape pour le chiffrement ICL.
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
Configuration rapide de la CLI
Pour configurer rapidement cet exemple, copiez les commandes suivantes, collez-les dans un fichier texte, supprimez les sauts de ligne, modifiez tous les détails nécessaires pour qu’ils correspondent à votre configuration réseau, copiez et collez les commandes dans la CLI au niveau de la [edit] hiérarchie, puis entrez commit en mode configuration.
Appareil SRX-01
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability peer-id 2 peer-ip 10.22.0.1 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 set chassis high-availability peer-id 2 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 1 set chassis high-availability services-redundancy-group 2 peer-id 2 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 200 set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.3.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.3.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.5.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.5.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
Appareil SRX-02
set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 1 family inet6 set groups vpn_config interfaces st0 unit 500 family inet set groups vpn_config interfaces st0 unit 500 family inet6 set apply-groups vpn_config set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability peer-id 1 peer-ip 10.22.0.2 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile ICL_IPSEC_VPN set chassis high-availability peer-id 1 liveness-detection minimum-interval 200 set chassis high-availability peer-id 1 liveness-detection multiplier 3 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX set chassis high-availability services-redundancy-group 1 managed-services ipsec set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set chassis high-availability services-redundancy-group 2 peer-id 1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.12.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/3.0 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4 set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX set chassis high-availability services-redundancy-group 2 managed-services ipsec set chassis high-availability services-redundancy-group 2 preemption set chassis high-availability services-redundancy-group 2 activeness-priority 1 set security ike proposal ICL_IKE_PROP description interchassisa_link_encr_tunnel set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys set security ike proposal ICL_IKE_PROP dh-group group14 set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal ICL_IKE_PROP lifetime-seconds 300 set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL set security ike gateway ICL_IKE_GW version v2-only set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel set security ipsec proposal ICL_IPSEC_PROP protocol esp set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces ge-0/0/3.0 set security zones security-zone vpn host-inbound-traffic system-services ike set security zones security-zone vpn host-inbound-traffic protocols all set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/4.0 set security zones security-zone icl_zone host-inbound-traffic system-services ike set security zones security-zone icl_zone host-inbound-traffic system-services ping set security zones security-zone icl_zone host-inbound-traffic system-services high-availability set security zones security-zone icl_zone host-inbound-traffic system-services ssh set security zones security-zone icl_zone host-inbound-traffic protocols bfd set security zones security-zone icl_zone host-inbound-traffic protocols bgp set security zones security-zone icl_zone interfaces ge-0/0/2.0 set interfaces ge-0/0/1 unit 0 family inet set interfaces ge-0/0/2 description inter_chassis_link set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.1/24 set interfaces ge-0/0/3 description untrust set interfaces ge-0/0/3 unit 0 family inet address 10.2.0.2/24 set interfaces ge-0/0/4 description trust set interfaces ge-0/0/4 unit 0 family inet address 10.4.0.1/24 set interfaces lo0 apply-groups-except global set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.11.0.1/32 set interfaces lo0 unit 0 family inet address 10.12.0.1/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 1 family inet6 set policy-options prefix-list SRG1_PFX 10.11.0.0/24 set policy-options prefix-list SRG2_PFX 10.12.0.0/24 set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.7.0.0/24 orlonger set policy-options route-filter-list srg1_rf_list 10.1.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.9.0.0/24 orlonger set policy-options route-filter-list srg2_rf_list 10.8.0.0/24 orlonger set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 1 then metric 10 set policy-options policy-statement mnha-route-policy term 1 then accept set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 set policy-options policy-statement mnha-route-policy term 2 then metric 20 set policy-options policy-statement mnha-route-policy term 2 then accept set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 3 then metric 10 set policy-options policy-statement mnha-route-policy term 3 then accept set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 set policy-options policy-statement mnha-route-policy term 4 then metric 20 set policy-options policy-statement mnha-route-policy term 4 then accept set policy-options policy-statement mnha-route-policy term default then reject set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0 set protocols bgp group trust type internal set protocols bgp group trust local-address 10.2.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust local-as 100 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust neighbor 10.2.0.1 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.4.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust local-as 100 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust neighbor 10.4.0.2 set routing-options autonomous-system 100 set routing-options static route 10.7.0.0/24 next-hop 10.4.0.2 set routing-options static route 10.112.0.0/24 next-hop 10.4.0.2
Appareil SRX-3
set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG1_IKE_PROP dh-group group14 set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set security ike proposal SRG2_IKE_PROP dh-group group14 set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 set security ike gateway SRG1_IKE_GW1 external-interface lo0 set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 set security ike gateway SRG1_IKE_GW1 version v2-only set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 set security ike gateway SRG2_IKE_GW500 external-interface lo0 set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 set security ike gateway SRG2_IKE_GW500 version v2-only set security ipsec proposal SRG1_IPSEC_PROP protocol esp set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set security ipsec proposal SRG2_IPSEC_PROP protocol esp set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately set security policies default-policy permit-all set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic protocols all set security zones security-zone untrust interfaces st0.1 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone untrust interfaces st0.500 set security zones security-zone untrust interfaces ge-0/0/1.0 set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone trust host-inbound-traffic system-services ike set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/2.0 set interfaces ge-0/0/0 description trust set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 set interfaces ge-0/0/1 description untrust set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 set interfaces ge-0/0/2 description trust set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 set interfaces lo0 description untrust set interfaces lo0 unit 0 family inet address 10.112.0.1/32 set interfaces lo0 unit 0 family inet address 10.112.0.5/32 set interfaces st0 unit 1 family inet set interfaces st0 unit 500 family inet set routing-options autonomous-system 100 set routing-options static route 10.4.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.5.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
Les sections suivantes présentent les extraits de configuration des routeurs requis pour configurer la haute disponibilité multi nodale dans le réseau.
Routeur R1
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.3.0.1/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.2.0.1/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.1/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.1/32 preferred set routing-options autonomous-system 100 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.2.0.1 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.2.0.2 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.3.0.1 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.3.0.2
Routeur R2
set interfaces ge-0/0/0 description srx_1 set interfaces ge-0/0/0 unit 0 family inet address 10.5.0.2/24 set interfaces ge-0/0/1 description srx_2 set interfaces ge-0/0/1 unit 0 family inet address 10.4.0.2/24 set interfaces ge-0/0/2 description srx-3 set interfaces ge-0/0/2 unit 0 family inet address 10.7.0.2/24 set interfaces lo0 description loopback set interfaces lo0 unit 0 family inet address 10.111.0.2/32 primary set interfaces lo0 unit 0 family inet address 10.111.0.2/32 preferred set routing-options autonomous-system 100 set routing-options static route 10.112.0.0/24 next-hop 10.7.0.1 set protocols bgp group srx2_group type internal set protocols bgp group srx2_group local-address 10.4.0.2 set protocols bgp group srx2_group local-as 100 set protocols bgp group srx2_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx2_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx2_group bfd-liveness-detection multiplier 3 set protocols bgp group srx2_group neighbor 10.4.0.1 set protocols bgp group srx1_group type internal set protocols bgp group srx1_group local-address 10.5.0.2 set protocols bgp group srx1_group local-as 100 set protocols bgp group srx1_group bfd-liveness-detection minimum-interval 500 set protocols bgp group srx1_group bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group srx1_group bfd-liveness-detection multiplier 3 set protocols bgp group srx1_group neighbor 10.5.0.1
La configuration
Procédure étape par étape
Nous montrons la configuration du SRX-01 dans la procédure étape par étape.
L’exemple suivant vous oblige à naviguer à différents niveaux dans la hiérarchie de configuration. Pour obtenir des instructions sur la procédure à suivre, consultez Utilisation de l’éditeur CLI en mode Configuration dans le Guide de l’utilisateur de la CLI.
Configurez les interfaces.
[edit] user@srx-1# set interfaces ge-0/0/2 description inter_chassis_link user@srx-1# set interfaces ge-0/0/2 unit 0 family inet address 10.22.0.2/24 user@srx-1# set interfaces ge-0/0/3 description untrust user@srx-1# set interfaces ge-0/0/3 unit 0 family inet address 10.3.0.2/24 user@srx-1# set interfaces ge-0/0/4 description trust user@srx-1# set interfaces ge-0/0/4 unit 0 family inet address 10.5.0.1/24
Utilisez les interfaces ge-0/0/3 et ge-0/0/4 pour vous connecter aux routeurs en amont et en aval et utilisez l’interface ge-0/0/2 pour configurer l’ICL.
Configurez les interfaces de bouclage.
[edit] user@srx-1# set interfaces lo0 apply-groups-except global user@srx-1# set interfaces lo0 description untrust user@srx-1# set interfaces lo0 unit 0 family inet address 10.11.0.1/32 user@srx-1# set interfaces lo0 unit 0 family inet address 10.12.0.1/32 user@srx-1# set interfaces st0 unit 1
Attribuez les adresses IP 10.11.0.1 et 10.12.0.1 à l’interface de bouclage. Nous utiliserons 10.11.0.1 comme adresse IP flottante et 10.12.0.1 comme adresse de passerelle IKE.
Configurez les zones de sécurité, attribuez des interfaces aux zones et spécifiez les services système autorisés pour les zones de sécurité.
[edit] user@srx-1# set security zones security-zone vpn host-inbound-traffic system-services ike user@srx-1# set security zones security-zone vpn host-inbound-traffic protocols all user@srx-1# set security zones security-zone vpn interfaces st0.1 user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ike user@srx-1# set security zones security-zone untrust host-inbound-traffic system-services ping user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone untrust host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone untrust interfaces lo0.0 user@srx-1# set security zones security-zone untrust interfaces ge-0/0/3.0 user@srx-1# set security zones security-zone trust host-inbound-traffic system-services all user@srx-1# set security zones security-zone trust host-inbound-traffic protocols all user@srx-1# set security zones security-zone trust interfaces ge-0/0/4.0 user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ike user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ping user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services high-availability user@srx-1# set security zones security-zone icl_zone host-inbound-traffic system-services ssh user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bfd user@srx-1# set security zones security-zone icl_zone host-inbound-traffic protocols bgp user@srx-1# set security zones security-zone icl_zone interfaces ge-0/0/2.0
Attribuez aux interfaces ge-0/0/3 et ge-0/0/4 respectivement les zones de confiance et de non-confiance. Assignez l’interface lo0.0 à la zone non approuvée pour vous connecter sur le réseau IP. Affectez l’interface ge-0/0/2 à la zone ICL. Vous utilisez cette zone pour configurer l’ICL. Attribuez l’interface de tunnel sécurisé à la zone de sécurité VPN.
- Configurez les détails du nœud local et du nœud pair, tels que l’ID du nœud, les adresses lP du nœud local et du nœud pair, et l’interface du nœud pair.
[edit] user@srx-1# set chassis high-availability local-id 1 user@srx-1# set chassis high-availability local-id local-ip 10.22.0.2 user@srx-1# set chassis high-availability peer-id 2 peer-ip 10.22.0.1 user@srx-1# set chassis high-availability peer-id 2 interface ge-0/0/2.0
Vous utiliserez l'interface ge-0/0/2 pour communiquer avec le nœud pair à l'aide de l'ICL.
Attachez le profil VPN IPsec IPSEC_VPN_ICL au nœud homologue.
[edit] user@srx-1# set chassis high-availability peer-id 2 vpn-profile ICL_IPSEC_VPN
Cette configuration vous sera nécessaire pour établir une liaison ICL sécurisée entre les nœuds.
Configurez les options de protocole BFD (Bidirectional Forwarding Detection) pour le nœud homologue.
[edit] user@srx-1# set chassis high-availability peer-id 2 liveness-detection minimum-interval 200 user@srx-1# set chassis high-availability peer-id 2 liveness-detection multiplier 3
-
Configurez les groupes de redondance des services SRG1 et SRG2.
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 deployment-type routing user@srx-1# set chassis high-availability services-redundancy-group 1 peer-id 2 user@srx-1# set chassis high-availability services-redundancy-group 2 peer-id 2
Configurez les paramètres de détermination de l’activité SRG1 et SRG2.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip 10.111.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-probe dest-ip src-ip 10.11.0.1
Utilisez l’adresse IP flottante comme adresse IP source (10.11.0.1 pour SRG1 et 10.12.0.1 pour SRG2) et les adresses IP des routeurs en amont comme adresse IP de destination (10.111.0.1) pour la sonde de détermination de l’activité.
Vous pouvez configurer jusqu’à 64 adresses IP pour la surveillance IP et les sondages d’activité. Le total de 64 adresses IP est la somme du nombre d’adresses IPv4 et IPv6)
Configurez les paramètres de surveillance BFD pour le SRG1 et le SRG2 afin de détecter les défaillances du réseau.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 1 monitor interface ge-0/0/4
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 session-type singlehop user@srx-1# set chassis high-availability services-redundancy-group 2 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/3.0 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/3 user@srx-1# set chassis high-availability services-redundancy-group 2 monitor interface ge-0/0/4
Configurez une route de signal active requise pour l’application de l’activité.
SRG1
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 user@srx-1# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 user@srx-1# set chassis high-availability services-redundancy-group 1 preemption user@srx-1# set chassis high-availability services-redundancy-group 1 activeness-priority 1
SRG2
[edit] user@srx-1# set chassis high-availability services-redundancy-group 2 active-signal-route 10.49.1.1 user@srx-1# set chassis high-availability services-redundancy-group 2 backup-signal-route 10.49.1.2 user@srx-1# set chassis high-availability services-redundancy-group 2 preemption user@srx-1# set chassis high-availability services-redundancy-group 2 activeness-priority 200
Remarque : Vous devez spécifier la route de signal active ainsi que la stratégie route-exists dans l’instruction policy-options. Lorsque vous configurez laactive-signal-routecondition withif-route-exists, le module HA ajoute cette route à la table de routage.Créez une liste de préfixes IP en incluant l’adresse locale de la passerelle IKE et associez la liste de préfixes IP à SRG1 et SRG2 :
SRG1
[edit] user@srx-1# set policy-options prefix-list SRG1_PFX 10.11.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 1 prefix-list SRG1_PFX
SRG2
[edit] user@srx-1# set policy-options prefix-list SRG2_PFX 10.12.0.0/24 user@srx-1# set chassis high-availability services-redundancy-group 2 prefix-list SRG2_PFX
Cette configuration ancre un certain tunnel VPN IPsec à un équipement de sécurité particulier.
Activez le service VPN IPsec sur SRG1 et SRG2.
[edit] user@srx-1# set chassis high-availability services-redundancy-group 1 managed-services ipsec user@srx-1# set chassis high-availability services-redundancy-group 2 managed-services ipsec
Configurez les options VPN IPSec pour l’ICL.
Définir la configuration d’Internet Key Exchange (IKE). Une configuration IKE définit les algorithmes et les clés utilisés pour établir une connexion sécurisée.
[edit] user@srx-1# set security ike proposal ICL_IKE_PROP description interchassis_link_encr_tunnel user@srx-1# set security ike proposal ICL_IKE_PROP authentication-method pre-shared-keys user@srx-1# set security ike proposal ICL_IKE_PROP dh-group group14 user@srx-1# set security ike proposal ICL_IKE_PROP authentication-algorithm sha-256 user@srx-1# set security ike proposal ICL_IKE_PROP encryption-algorithm aes-256-cbc user@srx-1# set security ike proposal ICL_IKE_PROP lifetime-seconds 300 user@srx-1# set security ike policy ICL_IKE_POL description interchassis_link_encr_tunnel user@srx-1# set security ike policy ICL_IKE_POL proposals ICL_IKE_PROP user@srx-1# set security ike policy ICL_IKE_POL pre-shared-key ascii-text "$ABC123" user@srx-1# set security ike gateway ICL_IKE_GW ike-policy ICL_IKE_POL user@srx-1# set security ike gateway ICL_IKE_GW version v2-only
Pour la fonctionnalité haute disponibilité multi-nœuds, vous devez configurer la version IKE comme suit :
v2-only-
Spécifiez le protocole de proposition IPsec et l’algorithme de chiffrement. Spécifiez les options IPsec pour créer un tunnel IPsec entre deux appareils participants afin de sécuriser la communication VPN.
[edit] user@srx-1# set security ipsec proposal ICL_IPSEC_PROP description interchassis_link_encr_tunnel user@srx-1# set security ipsec proposal ICL_IPSEC_PROP protocol esp user@srx-1# set security ipsec proposal ICL_IPSEC_PROP encryption-algorithm aes-256-gcm user@srx-1# set security ipsec proposal ICL_IPSEC_PROP lifetime-seconds 300 user@srx-1# set security ipsec policy ICL_IPSEC_POL description interchassis_link_encr_tunnel user@srx-1# set security ipsec policy ICL_IPSEC_POL proposals ICL_IPSEC_PROP user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ha-link-encryption user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike gateway ICL_IKE_GW user@srx-1# set security ipsec vpn ICL_IPSEC_VPN ike ipsec-policy ICL_IPSEC_POL
ha-link-encryptionoption, l’ICL est chiffré pour sécuriser le flux de trafic à haute disponibilité entre les nœuds.Le même nom VPN ICL_IPSEC_VPN doit être mentionné vpn_profile dans la
set chassis high-availability peer-id <id> vpn-profile vpn_profileconfiguration.
Configurez la stratégie de sécurité.
[edit] user@srx-1# set security policies default-policy permit-all
Pour cet exemple, nous avons configuré une stratégie pour autoriser tout le trafic. Nous vous recommandons vivement de créer des stratégies de sécurité conformes aux exigences de votre réseau pour autoriser le trafic autorisé par votre stratégie d’organisation et refuser tout autre trafic. Nous avons utilisé la stratégie par défaut à des fins de démonstration uniquement dans cet exemple.
Configurez les options de routage.
[edit] user@srx-1# set routing-options autonomous-system 100 user@srx-1# set routing-options static route 10.7.0.0/16 next-hop 10.5.0.2 user@srx-1# set routing-options static route 10.112.0.0/24 next-hop 10.5.0.2
Configurez les options de stratégie.
[edit] user@srx-1# set policy-options route-filter-list srg1_rf_list 10.11.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.7.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg1_rf_list 10.1.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.12.0.0/24 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.9.0.0/16 orlonger user@srx-1# set policy-options route-filter-list srg2_rf_list 10.8.0.0/16 orlonger user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 1 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from route-filter-list srg1_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists_srg1 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 2 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 3 from condition active_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then metric 10 user@srx-1# set policy-options policy-statement mnha-route-policy term 3 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from route-filter-list srg2_rf_list user@srx-1# set policy-options policy-statement mnha-route-policy term 4 from condition backup_route_exists_srg2 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then metric 20 user@srx-1# set policy-options policy-statement mnha-route-policy term 4 then accept user@srx-1# set policy-options policy-statement mnha-route-policy term default then reject user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet 10.39.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet 10.49.1.1/32 user@srx-1# set policy-options condition active_route_exists_srg2 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet 10.39.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg1 if-route-exists address-family inet table inet.0 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet 10.49.1.2/32 user@srx-1# set policy-options condition backup_route_exists_srg2 if-route-exists address-family inet table inet.0
Configurez la route du signal actif 10.39.1.1 (SRG1) et 10.49.1.1 (SRG2) avec la condition de correspondance de route (
if-route-exists). La haute disponibilité multinodale ajoute cette route à la table de routage lorsque le nœud passe au rôle actif. Le nœud commence également à annoncer la route de préférence la plus élevée. Configurez la route du signal de secours (10.39.1.2 et 10.49.1.2) pour annoncer le nœud de secours avec une priorité moyenne. En cas de défaillance, la liaison haute disponibilité est interrompue et le nœud actif actuel libère son rôle principal et supprime la route de signal actif. Le nœud de secours détecte alors la condition via ses sondes et passe au rôle actif. La préférence de route est permutée pour diriger tout le trafic vers le nouveau nœud actifConfigurez les options de sessions d’appairage BFD et spécifiez des minuteries de détection d’activité.
[edit] user@srx-1# set protocols bgp group trust type internal user@srx-1# set protocols bgp group trust local-address 10.3.0.2 user@srx-1# set protocols bgp group trust export mnha-route-policy user@srx-1# set protocols bgp group trust local-as 100 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group trust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group trust neighbor 10.3.0.1 user@srx-1# set protocols bgp group untrust type internal user@srx-1# set protocols bgp group untrust local-address 10.5.0.1 user@srx-1# set protocols bgp group untrust export mnha-route-policy user@srx-1# set protocols bgp group untrust local-as 100 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 user@srx-1# set protocols bgp group untrust bfd-liveness-detection multiplier 3 user@srx-1# set protocols bgp group untrust neighbor 10.5.0.2
Configuration VPN IPsec (SRX-1 et SRX-2)
Procédez comme suit pour configurer la connexion VPN IPsec au pare-feu homologue de SRX Series. Dans cet exemple, vous allez placer toutes vos instructions de configuration VPN IPsec dans un groupe de configuration JUNOS nommé vpn_config.
- Créez un groupe
vpn_configde configuration en haut de la configuration et configurez les détails spécifiques au VPN IPsec.[edit] set groups vpn_config when peers SRX-01 set groups vpn_config when peers SRX-02 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG1_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys set groups vpn_config security ike proposal SRG2_IKE_PROP dh-group group14 set groups vpn_config security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 set groups vpn_config security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ike proposal SRG2_IKE_PROP lifetime-seconds 3600 set groups vpn_config security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP set groups vpn_config security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP set groups vpn_config security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123" set groups vpn_config security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 set groups vpn_config security ike gateway SRG1_IKE_GW1 address 10.112.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 external-interface lo0 set groups vpn_config security ike gateway SRG1_IKE_GW1 local-address 10.11.0.1 set groups vpn_config security ike gateway SRG1_IKE_GW1 version v2-only set groups vpn_config security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 set groups vpn_config security ike gateway SRG2_IKE_GW500 address 10.112.0.5 set groups vpn_config security ike gateway SRG2_IKE_GW500 external-interface lo0 set groups vpn_config security ike gateway SRG2_IKE_GW500 local-address 10.12.0.1 set groups vpn_config security ike gateway SRG2_IKE_GW500 version v2-only set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP protocol esp set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc set groups vpn_config security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800 set groups vpn_config security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL501 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL502 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec policy SRG2_IPSEC_POL503 proposals SRG2_IPSEC_PROP set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.1.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.7.0.2/32 set groups vpn_config security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels on-traffic set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 local-ip 10.8.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts500 remote-ip 10.9.0.2/32 set groups vpn_config security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels on-traffic set groups vpn_config security zones security-zone vpn host-inbound-traffic system-services ike set groups vpn_config security zones security-zone vpn host-inbound-traffic protocols all set groups vpn_config security zones security-zone vpn interfaces st0.1 set groups vpn_config security zones security-zone vpn interfaces st0.500 set groups vpn_config interfaces st0 unit 1 family inet set groups vpn_config interfaces st0 unit 500 family inet
Inclure l’instruction apply-groups dans la configuration pour hériter des instructions du groupe de configuration vpn_config,
[edit] user@srx-1# set apply-groups vpn_config
Configuration (SRX-03) (périphérique homologue VPN)
Procédure étape par étape
Créez la proposition IKE.
[edit] user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG1_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG1_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG1_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG1_IKE_PROP lifetime-seconds 3600 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-method pre-shared-keys user@srx-3# set security ike proposal SRG2_IKE_PROP dh-group group14 user@srx-3# set security ike proposal SRG2_IKE_PROP authentication-algorithm sha-256 user@srx-3# set security ike proposal SRG2_IKE_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ike proposal SRG2_IKE_PROP lifetime-seconds 3600
Définir des stratégies IKE.
[edit] user@srx-3# set security ike policy SRG1_IKE_POL1 proposals SRG1_IKE_PROP user@srx-3# set security ike policy SRG1_IKE_POL1 pre-shared-key ascii-text "$ABC123" user@srx-3# set security ike policy SRG2_IKE_POL500 proposals SRG2_IKE_PROP user@srx-3# set security ike policy SRG2_IKE_POL500 pre-shared-key ascii-text "$ABC123"
Créez une passerelle IKE, définissez l’adresse, spécifiez les interfaces externes et la version.
[edit] user@srx-3# set security ike gateway SRG1_IKE_GW1 ike-policy SRG1_IKE_POL1 user@srx-3# set security ike gateway SRG1_IKE_GW1 address 10.11.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 external-interface lo0 user@srx-3# set security ike gateway SRG1_IKE_GW1 local-address 10.112.0.1 user@srx-3# set security ike gateway SRG1_IKE_GW1 version v2-only user@srx-3# set security ike gateway SRG2_IKE_GW500 ike-policy SRG2_IKE_POL500 user@srx-3# set security ike gateway SRG2_IKE_GW500 address 10.12.0.1 user@srx-3# set security ike gateway SRG2_IKE_GW500 external-interface lo0 user@srx-3# set security ike gateway SRG2_IKE_GW500 local-address 10.112.0.5 user@srx-3# set security ike gateway SRG2_IKE_GW500 version v2-only
Créer des propositions IPsec.
[edit] user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG1_IPSEC_PROP lifetime-seconds 1800 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP protocol esp user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP encryption-algorithm aes-256-cbc user@srx-3# set security ipsec proposal SRG2_IPSEC_PROP lifetime-seconds 1800
Créez des politiques IPsec.
[edit] user@srx-3# set security ipsec policy SRG1_IPSEC_POL1 proposals SRG1_IPSEC_PROP user@srx-3# set security ipsec policy SRG2_IPSEC_POL500 proposals SRG2_IPSEC_PROP
Spécifiez les références de proposition IPsec (passerelle IKE, stratégie IPsec, interface à lier et sélecteurs de trafic).
[edit] user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 bind-interface st0.1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike gateway SRG1_IKE_GW1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 ike ipsec-policy SRG1_IPSEC_POL1 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 local-ip 10.7.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 traffic-selector ts1 remote-ip 10.1.0.2/32 user@srx-3# set security ipsec vpn SRG1_IPSEC_VPN1 establish-tunnels immediately user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 bind-interface st0.500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike gateway SRG2_IKE_GW500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 ike ipsec-policy SRG2_IPSEC_POL500 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 local-ip 10.9.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 traffic-selector ts1 remote-ip 10.8.0.2/32 user@srx-3# set security ipsec vpn SRG2_IPSEC_VPN500 establish-tunnels immediately
Créez une stratégie de sécurité.
[edit] user@srx-3# set security policies default-policy permit-all
Pour cet exemple, nous avons configuré une stratégie pour autoriser tout le trafic. Nous vous recommandons vivement de créer des stratégies de sécurité conformes aux exigences de votre réseau pour autoriser le trafic autorisé par votre stratégie d’organisation et refuser tout autre trafic. Nous avons utilisé la stratégie par défaut à des fins de démonstration uniquement dans cet exemple.
Configurez les interfaces.
[edit] user@srx-3# set interfaces ge-0/0/0 description trust user@srx-3# set interfaces ge-0/0/0 unit 0 family inet address 10.7.0.1/24 user@srx-3# set interfaces ge-0/0/1 description untrust user@srx-3# set interfaces ge-0/0/1 unit 0 family inet address 10.6.0.2/24 user@srx-3# set interfaces ge-0/0/2 description trust user@srx-3# set interfaces ge-0/0/2 unit 0 family inet address 10.9.0.1/24 user@srx-3# set interfaces lo0 description untrust user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.1/32 user@srx-3# set interfaces lo0 unit 0 family inet address 10.112.0.5/32 user@srx-3# set interfaces st0 unit 1 family inet user@srx-3# set interfaces st0 unit 500 family inet
Définissez des zones de sécurité et ajoutez des interfaces.
[edit] user@srx-3# set security zones security-zone untrust host-inbound-traffic system-services all user@srx-3# set security zones security-zone untrust host-inbound-traffic protocols all user@srx-3# set security zones security-zone untrust interfaces st0.1 user@srx-3# set security zones security-zone untrust interfaces lo0.0 user@srx-3# set security zones security-zone untrust interfaces st0.500 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/1.0 user@srx-3# set security zones security-zone untrust interfaces ge-0/0/0.0 user@srx-3# set security zones security-zone trust host-inbound-traffic system-services all user@srx-3# set security zones security-zone trust host-inbound-traffic protocols all user@srx-3# set security zones security-zone trust interfaces ge-0/0/2.0
Configurez les routes statiques.
[edit] user@srx-3# set routing-options autonomous-system 100 user@srx-3# set routing-options static route 10.4.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.5.0.0/16 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.11.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.12.0.0/24 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.1/32 next-hop 10.7.0.2 user@srx-3# set routing-options static route 10.111.0.2/32 next-hop 10.7.0.2
Résultats (SRX-01)
En mode configuration, confirmez votre configuration en entrant les commandes suivantes.
Si la sortie n’affiche pas la configuration prévue, répétez les instructions de configuration de cet exemple pour la corriger.
[edit]
user@srx-1# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-1# show chassis high-availability
local-id 1 local-ip 10.22.0.2;
peer-id 2 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
services-redundancy-group 2 {
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
[edit]
user@srx-1# show security ike
proposal ICL_IKE_PROP {
description interchassis_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-1# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-1# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/16 orlonger;
10.1.0.0/16 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/16 orlonger;
10.8.0.0/16 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-1# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/16 next-hop 10.5.0.2;
route 10.112.0.0/24 next-hop 10.5.0.2;
}
[edit]
user@srx-1# show security zones
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-1# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.3.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.5.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1;
}
Si vous avez terminé de configurer l’appareil, entrez en commit mode configuration.
Résultats (SRX-02)
En mode configuration, confirmez votre configuration en entrant les commandes suivantes. Si la sortie n’affiche pas la configuration prévue, répétez les instructions de configuration de cet exemple pour la corriger.
[edit]
user@srx-2# show groups vpn_config
when {
peers [ SRX-01 SRX-02 ];
}
security {
ike {
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.112.0.1;
external-interface lo0;
local-address 10.11.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.112.0.5;
external-interface lo0;
local-address 10.12.0.1;
version v2-only;
}
}
ipsec {
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL501 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL502 {
proposals SRG2_IPSEC_PROP;
}
policy SRG2_IPSEC_POL503 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.1.0.2/32;
remote-ip 10.7.0.2/32;
}
establish-tunnels on-traffic;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts500 {
local-ip 10.8.0.2/32;
remote-ip 10.9.0.2/32;
}
establish-tunnels on-traffic;
}
}
zones {
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
st0.500;
}
}
}
}
interfaces {
st0 {
unit 1 {
family inet;
family inet6;
}
unit 500 {
family inet;
family inet6;
}
}
}
[edit]
user@srx-2# show chassis high-availability
local-id 2 local-ip 10.22.0.1;
peer-id 1 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile ICL_IPSEC_VPN;
liveness-detection {
minimum-interval 200;
multiplier 3;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
prefix-list SRG1_PFX;
managed-services ipsec;
preemption;
activeness-priority 200;
}
services-redundancy-group 2 {
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.12.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/3.0;
}
interface {
ge-0/0/3;
ge-0/0/4;
}
}
active-signal-route {
10.49.1.1;
}
backup-signal-route {
10.49.1.2;
}
prefix-list SRG2_PFX;
managed-services ipsec;
preemption;
activeness-priority 1;
}
[edit]
user@srx-2# show security ike
proposal ICL_IKE_PROP {
description interchassisa_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 300;
}
policy ICL_IKE_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway ICL_IKE_GW {
ike-policy ICL_IKE_POL;
version v2-only;
}
[edit]
user@srx-2# show security ipsec
proposal ICL_IPSEC_PROP {
description interchassis_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 300;
}
policy ICL_IPSEC_POL {
description interchassis_link_encr_tunnel;
proposals ICL_IPSEC_PROP;
}
vpn ICL_IPSEC_VPN {
ha-link-encryption;
ike {
gateway ICL_IKE_GW;
ipsec-policy ICL_IPSEC_POL;
}
}
[edit]
user@srx-2# show policy-options
prefix-list SRG1_PFX {
10.11.0.0/24;
}
prefix-list SRG2_PFX {
10.12.0.0/24;
}
route-filter-list srg1_rf_list {
10.11.0.0/24 orlonger;
10.7.0.0/24 orlonger;
10.1.0.0/24 orlonger;
}
route-filter-list srg2_rf_list {
10.12.0.0/24 orlonger;
10.9.0.0/24 orlonger;
10.8.0.0/24 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
route-filter-list srg1_rf_list;
condition active_route_exists_srg1;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
route-filter-list srg1_rf_list;
condition backup_route_exists_srg1;
}
then {
metric 20;
accept;
}
}
term 3 {
from {
route-filter-list srg2_rf_list;
condition active_route_exists_srg2;
}
then {
metric 10;
accept;
}
}
term 4 {
from {
route-filter-list srg2_rf_list;
condition backup_route_exists_srg2;
}
then {
metric 20;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition active_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg1 {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
condition backup_route_exists_srg2 {
if-route-exists {
address-family {
inet {
10.49.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@srx-2# show routing-options
autonomous-system 100;
static {
route 10.7.0.0/24 next-hop 10.4.0.2;
route 10.112.0.0/24 next-hop 10.4.0.2;
}
[edit]
user@srx-2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
lo0.0;
ge-0/0/3.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone icl_zone {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-2# show interfaces
ge-0/0/1 {
unit 0 {
family inet;
}
}
ge-0/0/2 {
description inter_chassis_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description untrust;
unit 0 {
family inet {
address 10.2.0.2/24;
}
}
}
ge-0/0/4 {
description trust;
unit 0 {
family inet {
address 10.4.0.1/24;
}
}
}
lo0 {
apply-groups-except global;
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
address 10.12.0.1/32;
}
}
}
st0 {
unit 1 {
family inet;
}
}
Si vous avez terminé de configurer l’appareil, entrez en commit mode configuration.
user@host# commit warning: High Availability Mode changed, please reboot the device to avoid undesirable behavior commit complete
Résultats (SRX-3) (appareil pair VPN)
En mode configuration, confirmez votre configuration en entrant les commandes suivantes. Si la sortie n’affiche pas la configuration prévue, répétez les instructions de configuration de cet exemple pour la corriger.
[edit]
user@srx-3# show security ike
proposal SRG1_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
proposal SRG2_IKE_PROP {
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy SRG1_IKE_POL1 {
proposals SRG1_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
policy SRG2_IKE_POL500 {
proposals SRG2_IKE_PROP;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway SRG1_IKE_GW1 {
ike-policy SRG1_IKE_POL1;
address 10.11.0.1;
external-interface lo0;
local-address 10.112.0.1;
version v2-only;
}
gateway SRG2_IKE_GW500 {
ike-policy SRG2_IKE_POL500;
address 10.12.0.1;
external-interface lo0;
local-address 10.112.0.5;
version v2-only;
}
[edit]
user@srx-3# show security ipsec
proposal SRG1_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
proposal SRG2_IPSEC_PROP {
protocol esp;
authentication-algorithm hmac-sha-256-128;
encryption-algorithm aes-256-cbc;
lifetime-seconds 1800;
}
policy SRG1_IPSEC_POL1 {
proposals SRG1_IPSEC_PROP;
}
policy SRG2_IPSEC_POL500 {
proposals SRG2_IPSEC_PROP;
}
vpn SRG1_IPSEC_VPN1 {
bind-interface st0.1;
ike {
gateway SRG1_IKE_GW1;
ipsec-policy SRG1_IPSEC_POL1;
}
traffic-selector ts1 {
local-ip 10.7.0.2/32;
remote-ip 10.1.0.2/32;
}
establish-tunnels immediately;
}
vpn SRG2_IPSEC_VPN500 {
bind-interface st0.500;
ike {
gateway SRG2_IKE_GW500;
ipsec-policy SRG2_IPSEC_POL500;
}
traffic-selector ts1 {
local-ip 10.9.0.2/32;
remote-ip 10.8.0.2/32;
}
establish-tunnels immediately;
}
[edit]
user@srx-3# show routing-options
autonomous-system 100;
static {
route 10.4.0.0/24 next-hop 10.7.0.2;
route 10.5.0.0/24 next-hop 10.7.0.2;
route 10.11.0.0/24 next-hop 10.7.0.2;
route 10.12.0.0/24 next-hop 10.7.0.2;
route 10.111.0.1/32 next-hop 10.7.0.2;
route 10.111.0.2/32 next-hop 10.7.0.2;
}
[edit]
user@srx-3# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
st0.1;
lo0.0;
st0.500;
ge-0/0/1.0;
ge-0/0/0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ike;
}
protocols {
all;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@srx-3# show interfaces
ge-0/0/0 {
description trust;
unit 0 {
family inet {
address 10.7.0.1/24;
}
}
}
ge-0/0/1 {
description untrust;
unit 0 {
family inet {
address 10.6.0.2/24;
}
}
}
ge-0/0/2 {
description trust;
unit 0 {
family inet {
address 10.9.0.1/24;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.112.0.1/32;
address 10.112.0.5/32;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 500 {
family inet;
}
}
Si vous avez terminé de configurer l’appareil, entrez en commit mode configuration.
Vérification
Vérifiez que la configuration fonctionne correctement.
- Vérifier les détails de la haute disponibilité multi nodale
- Vérifier les détails de la haute disponibilité multi nodale
- Vérifier l’état du nœud homologue à haute disponibilité multinodale
- Vérifier les groupes de redondance du service de haute disponibilité multinodale
- Vérifier l’état du chiffrement des liaisons interchâssis (ICL)
- Vérification des statistiques de tunnel de chiffrement des liens
- Vérifier les homologues actifs de la liaison interchâssis
- Confirmer l’état du VPN
- Afficher les détails de l’association de sécurité IPsec
- Affichage des pairs actifs par SRG
- Afficher le préfixe IP au mappage SRG
- Afficher les informations de session BGP.
Vérifier les détails de la haute disponibilité multi nodale
Objet
Affichez et vérifiez les détails de la configuration de la haute disponibilité multi nœuds configurée sur votre équipement de sécurité.
Mesures à prendre
En mode opérationnel, exécutez la commande suivante :
Sur SRX-1
user@srx-01> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Sur SRX-2
user@srx-02> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.1
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signification
Vérifiez ces détails à partir de la sortie de la commande :
Détails du nœud local et du nœud pair, tels que l’adresse IP et l’ID.
Le champ
Encrypted: YESindique que le trafic est protégé.Le champ
Deployment Type: ROUTINGindique une configuration en mode Couche 3, c’est-à-dire que le réseau comporte des routeurs des deux côtés.Le champ
Services Redundancy Group: 1etServices Redundancy Group: 2indiquer l’état du SRG1 et du SRG2 (actif ou de secours) sur ce nœud.
Vérifier les détails de la haute disponibilité multi nodale
Objet
Affichez et vérifiez les détails de la configuration de la haute disponibilité multi nœuds configurée sur votre équipement de sécurité.
Mesures à prendre
En mode opérationnel, exécutez la commande suivante :
Sur SRX-01
user@srx-01> show chassis high-availability information detail
Node level Information:
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.2
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
HA Peer Conn events:
Jan 31 00:55:19.249 : HA Peer 180.100.1.1 BFD conn came up
Cold Synchronization:
Status:
Cold synchronization completed for: N/A
Cold synchronization failed for: N/A
Cold synchronization not known for: N/A
Current Monitoring Weight: 0
Progress:
CS Prereq 1 of 1 SPUs completed
1. if_state sync 1 SPUs completed
2. ha peer conn 1 SPUs completed
3. policy data sync 1 SPUs completed
4. cp ready 1 SPUs completed
5. VPN data sync 1 SPUs completed
6. IPID data sync 1 SPUs completed
7. All SPU ready 1 SPUs completed
8. AppID ready 1 SPUs completed
9. Tunnel Sess ready 1 SPUs completed
CS RTO sync 1 of 1 SPUs completed
CS Postreq 1 of 1 SPUs completed
Statistics:
Number of cold synchronization completed: 0
Number of cold synchronization failed: 0
Events:
Jan 31 00:55:24.616 : Cold sync for PFE is Post-req check in process
Jan 31 00:55:25.615 : Cold sync for PFE is Completed
SPU monitoring:
Status: Enabled
Current monitoring weight: 0
Statistics:
SPU up count: 1
NPC up count: 0
SPU down count: 0
NPC down count: 0
Chassis info processing error count: 0
Loopback Information:
PIC Name Loopback Nexthop Mbuf
-------------------------------------------------
Success Success Success
Hardware monitoring:
Status:
Activation status: Enabled
Ctrl Plane Hardware errors: 0
Data Plane Hardware errors: 0
SRGS Information:
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: ACTIVE
Last Advertised Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.347 : SRG[1] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:56:33.046 : SRG[1] state HOLD -> BACKUP, Reason: Peer state Active received
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:12.695 : SRG[1] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
SRGS Information:
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Hold Timer: 1
Services: [ IPSEC ]
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Peer Information:
Failure Events: NONE
Peer Id: 2
Last Advertised HA Status: BACKUP
Last Advertised Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
SRG State Change Events:
Jan 31 00:52:14.439 : SRG[2] state UNKNOWN -> HOLD, Reason: State machine start
Jan 31 00:55:24.263 : SRG[2] state HOLD -> ACTIVE, Reason: Local Priority Higher
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
Probe status events:
Jan 31 00:54:13.698 : SRG[2] HA probe dst 10.111.0.1 became unreachable, Reason: UNKNOWN
Signification
Vérifiez ces détails à partir de la sortie de la commande :
Le champ
Services: [ IPSEC ]indique le VPN IPSec associé pour chaque SRG.Les champs
BFD Monitoring,Interface Monitoring,Split-brain Prevention Probe Infoaffichent les détails de la surveillance.Les champs
Cold Synchronization,SRG State Change Eventsfournissent des détails sur l’état actuel et les modifications récentes.Le champ
Services Redundancy Group: 1etServices Redundancy Group: 2indiquer l’état du SRG1 et du SRG2 (actif ou de secours) sur ce nœud.
Dans la sortie de la commande, les adresses IP telles que IP 180.100.1.2 sont générées en interne par Junos OS et ces adresses n’interfèrent pas avec les tables de routage.
Vérifier l’état du nœud homologue à haute disponibilité multinodale
Objet
Affichez et vérifiez les détails du nœud pair.
Mesures à prendre
À partir du mode opérationnel, exécutez la commande suivante sur SRX-01 et SRX-02 :
SRX-01
user@srx-01> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 6
SRG Status Ack 4 4
Attribute Msg 1 1
Attribute Ack 1 1
SRX-02
user@srx-02> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 1 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.1
Internal Peer-IP: 180.100.1.2
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 6 4
SRG Status Ack 4 4
Attribute Msg 2 1
Attribute Ack 1 1
Signification
Vérifiez ces détails à partir de la sortie de la commande :
Détails du nœud homologue tels que l’interface utilisée, l’adresse IP et l’ID
État de chiffrement, état de connexion et état de synchronisation à froid
Statistiques de paquets sur le nœud.
Vérifier les groupes de redondance du service de haute disponibilité multinodale
Objet
Vérifiez que les SRG sont configurés et fonctionnent correctement.
Mesures à prendre
En mode opérationnel, exécutez la commande suivante sur les deux équipements de sécurité :
SRG1 sur SRX-02
user@srx-02> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRG2 sur SRX-02
user@srx-02> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
SRG1 sur SRX-01
user@srx-01> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: NOT INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
SRG2 sur SRX-01
user@srx-01> show chassis high-availability services-redundancy-group 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 2
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: NOT READY
Signal Route Info:
Active Signal Route:
IP: 10.49.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.49.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.12.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UNKNOWN
SRC-IP: 10.5.0.1 DST-IP: 10.5.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/3.0
State: INSTALLED
Interface Monitoring:
Status: UP
IF Name: ge-0/0/4 State: Up
IF Name: ge-0/0/3 State: Up
IP SRGID Table:
SRGID IP Prefix Routing Table
2 10.12.0.0/24 default
Signification
Vérifiez ces détails à partir de la sortie de la commande :
Détails du nœud pair tels que le type de déploiement, l’état, les routes des signaux actifs et de secours.
Sonde de prévention Split-Brain, surveillance IP et état de surveillance BFD.
Table des préfixes IP associés.
Vérifier l’état du chiffrement des liaisons interchâssis (ICL)
Objet
Vérifiez l’état de la liaison interchâssis (ICL).
Mesures à prendre
Exécutez la commande suivante sur SRX-01 :
user@srx-01> show security ipsec security-associations ha-link-encryption Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <495002 ESP:aes-gcm-256/aes256-gcm 0x0008d9c7 236/ unlim - root 500 10.22.0.1 >495002 ESP:aes-gcm-256/aes256-gcm 0x0001a573 236/ unlim - root 500 10.22.0.1
user@srx-01> show security ike security-associations ha-link-encryption Index State Initiator cookie Responder cookie Mode Remote Address 16776938 UP 9f8fe46ce3be92f8 44e6b3fd74cc9294 IKEv2 10.22.0.1
user@srx-01> show security ipsec security-associations ha-link-encryption detail
ID: 495002 Virtual-system: root, VPN Name: ICL_IPSEC_VPN
Local Gateway: 10.22.0.2, Remote Gateway: 10.22.0.1
Traffic Selector Name: __ICL_IPSEC_VPN__multi_node__
Local Identity: ipv4(180.100.1.2-180.100.1.2)
Remote Identity: ipv4(180.100.1.1-180.100.1.1)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: No
PFS group: N/A
SRG ID: 0
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.16000, Policy-name: ICL_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
HA Link Encryption Mode: Multi-Node
Location: FPC -, PIC -, KMD-Instance -
Anchorship: Thread -
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x0008d9c7, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
Direction: outbound, SPI: 0x0001a573, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 200 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 115 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 16776938
Signification
La sortie de la commande fournit les informations suivantes :
Détails de la passerelle locale et de la passerelle distante.
Paire de SA IPsec pour chaque thread dans le PIC.
Mode de chiffrement des liens HA (comme indiqué dans la ligne suivante) :
HA Link Encryption Mode: Multi-NodeAlgorithmes d’authentification et de chiffrement utilisés
La plage d’adresses IP (180.100.1.x) affichée dans la sortie de la commande sert de sélecteur de trafic ICL IPsec. Le système attribue dynamiquement cette plage d’adresses IP et il est essentiel de ne pas l’altérer ou la modifier. De plus, la détection de transfert bidirectionnel (BFD) sera automatiquement activée pour la plage IP 180.x.x.x.
Vérification des statistiques de tunnel de chiffrement des liens
Objet
Vérifiez les statistiques de tunnel de chiffrement des liens sur les nœuds actifs et de secours.
Mesures à prendre
Exécutez la commande suivante sur SRX-01 :
user@srx-01> show security ipsec statistics ha-link-encryption ESP Statistics: Encrypted bytes: 106294156 Decrypted bytes: 51961287 Encrypted packets: 979531 Decrypted packets: 989651 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Signification
Si vous constatez des problèmes de perte de paquets sur un VPN, vous pouvez exécuter la show security ipsec statistics ha-link-encryption commande plusieurs fois pour vérifier que les compteurs de paquets chiffrés et déchiffrés s’incrémentent. Vous devez également vérifier si les autres compteurs d’erreurs s’incrémentent.
Utilisez la clear security ipsec security-associations ha-link-encryption commande pour effacer toutes les statistiques IPsec.
Vérifier les homologues actifs de la liaison interchâssis
Objet
Afficher uniquement les homologues actifs ICL, mais pas les homologues actifs IKE réguliers.
Mesures à prendre
Exécutez les commandes suivantes sur les périphériques SRX-01 et SRX-02 :
SRX-1
user@srx-01> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.1 500 10.22.0.1 not available 0.0.0.0
SRX-2
user@srx-02> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.2 500 10.22.0.2 not available 0.0.0.0
Signification
La sortie de commande affiche uniquement l’homologue actif de l’ICL avec des détails tels que les adresses et les ports d’homologue utilisés par l’homologue actif.
Confirmer l’état du VPN
Objet
Confirmez l’état VPN en vérifiant l’état de toutes les associations de sécurité IKE au niveau de la SSR.
Mesures à prendre
Exécutez les commandes suivantes sur SRX-1, SRX-2 et SRX-3 (appareil homologue VPN) :
SRX-01
user@srx-01> show security ike security-associations srg-id 1
Index State Initiator cookie Responder cookie Mode Remote Address
16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-01> show security ike security-associations srg-id 2
Index State Initiator cookie Responder cookie Mode Remote Address
33554536 UP 9944aaf1ab914b42 15cef0da496bdd92 IKEv2 10.112.0.5
SRX-02
user@srx-02> show security ike security-associations srg-id 1 Index State Initiator cookie Responder cookie Mode Remote Address 16777319 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.112.0.1
user@srx-02> show security ike security-associations srg-id 2 Index State Initiator cookie Responder cookie Mode Remote Address 33554534 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.112.0.5
SRX-3 (appareil homologue VPN)
user@srx-03> show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 5929032 UP 366d174d847f8c71 2f654c6f1c463d80 IKEv2 10.12.0.1 5929033 UP 19e7cd4e503eeb2e 0800a7ceaafda740 IKEv2 10.11.0.1
Signification
Le résultat indique que :
- Adresses IP des pairs distants.
- L’affichage de l’état UP pour les deux pairs distants indique l’association réussie de l’établissement de la phase 1.
- L’adresse IP du pair distant, la stratégie IKE et les interfaces externes sont correctes.
Afficher les détails de l’association de sécurité IPsec
Objet
Affichez les détails des SA IPsec individuelles identifiées par des ID SRG.
Mesures à prendre
Exécutez la commande suivante sur les pare-feu SRX Series :
SRX-1
user@srx-01> show security ipsec security-associations srg-id 1 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1210/ unlim - root 500 10.112.0.1 >17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1210/ unlim - root 500 10.112.0.1
user@srx-01> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1382/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1382/ unlim - root 500 10.112.0.5
SRX-02
user@srx-02> show security ipsec security-associations srg-id 1
Total active tunnels: 1 Total IPsec sas: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<17277223 ESP:aes-cbc-256/sha256 0xc50520d4 1286/ unlim - root 500 10.112.0.1
>17277223 ESP:aes-cbc-256/sha256 0x6d1e9c89 1286/ unlim - root 500 10.112.0.1
user@srx-02> show security ipsec security-associations srg-id 2 Total active tunnels: 1 Total IPsec sas: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <34054437 ESP:aes-cbc-256/sha256 0x9feb290c 1461/ unlim - root 500 10.112.0.5 >34054437 ESP:aes-cbc-256/sha256 0xf41d091c 1461/ unlim - root 500 10.112.0.5
SRX-03
user@srx-03> show security ipsec security-associations
Total active tunnels: 2 Total Ipsec sas: 2
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<67108865 ESP:aes-cbc-256/sha256 6d1e9c89 1392/ unlim - root 500 10.11.0.1
>67108865 ESP:aes-cbc-256/sha256 c50520d4 1392/ unlim - root 500 10.11.0.1
<67108866 ESP:aes-cbc-256/sha256 f41d091c 1570/ unlim - root 500 10.12.0.1
>67108866 ESP:aes-cbc-256/sha256 9feb290c 1570/ unlim - root 500 10.12.0.1
Signification
La sortie affiche l’état du VPN.
Affichage des pairs actifs par SRG
Objet
Affichez la liste des homologues actifs connectés avec les adresses et les ports qu’ils utilisent.
Mesures à prendre
Exécutez les commandes suivantes sur les pare-feu SRX Series :
SRX-01
user@srx-01> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-01> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
SRX-02
user@srx-02> show security ike active-peer srg-id 1 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.1 500 10.112.0.1 not available 0.0.0.0
user@srx-02> show security ike active-peer srg-id 2 Remote Address Port Peer IKE-ID AAA username Assigned IP 10.112.0.5 500 10.112.0.5 not available 0.0.0.0
Signification
La sortie affiche la liste des appareils connectés avec des détails sur les adresses homologues et les ports utilisés.
Afficher le préfixe IP au mappage SRG
Objet
Afficher le préfixe IP aux informations de mappage SRG.
Mesures à prendre
Exécutez la commande suivante sur l’équipement SRX-01.
user@srx-01> show chassis high-availability prefix-srgid-table
IP SRGID Table:
SRGID IP Prefix Routing Table
1 10.11.0.0/24 default
2 10.12.0.0/24 default
Signification
La sortie montre les préfixes d’adresses IP mappés aux SRG dans la configuration.
Afficher les informations de session BGP.
Objet
Affichez des informations récapitulatives sur le protocole BGP et ses voisins pour déterminer si des routes sont reçues des pairs.
Mesures à prendre
Exécutez les commandes suivantes sur les pare-feu SRX Series :
Appareil SRX-1
user@srx-01> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Received/Accepted/Damped...
10.3.0.1 100 37 40 0 0 15:43 Establ
inet.0: 0/0/0/0
10.5.0.2 100 37 40 0 0 15:42 Establ
inet.0: 0/0/0/0
Appareil SRX-2
user@srx-02> show bgp summary
Threading mode: BGP I/O
Default eBGP mode: advertise - accept, receive - accept
Groups: 2 Peers: 2 Down peers: 0
Table Tot Paths Act Paths Suppressed History Damp State Pending
inet.0
0 0 0 0 0 0
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn St ate|#Active/Received/Accepted/Damped...
10.2.0.1 100 842 846 0 0 6:18:40 Es tabl
inet.0: 0/0/0/0
10.4.0.2 100 842 846 0 0 6:18:42 Es tabl
inet.0: 0/0/0/0
Signification
La sortie indique que la session BGP est établie et que les homologues échangent des messages de mise à jour.
