IPsec 规则和规则集
示例:配置 IKE 动态 SA
此示例说明如何配置 IKE 动态 SA,并包含以下部分。
要求
此示例使用以下硬件和软件组件:
四台安装有多服务接口的 M Series、MX 系列 或 T Series 路由器。
Junos OS 9.4 或更高版本。
在配置此功能之前,不需要除设备启动之外的特殊配置。
概述和拓扑
安全关联 (SA) 是一种单工连接,使两台主机能够通过 IPsec 安全地相互通信。
动态 SA 最适合大规模、地理上分散的网络,在这些环境中,密钥的手册分发、维护和跟踪任务非常艰巨。动态 SA 配置了一组由安全网关协商的提议。密钥在协商过程中生成,无需在配置中指定。动态 SA 包含一个或多个提议,这些提议允许您确定要与对等方协商的协议和算法列表的优先级。
拓扑结构
图 1 显示了包含一组四台路由器的 IPsec 拓扑。此配置要求路由器 2 和 3 使用 IKE 动态 SA、增强型身份验证和加密来建立 IPsec 隧道。路由器 1 和 4 提供基本连接,用于验证 IPsec 隧道是否正常运行。
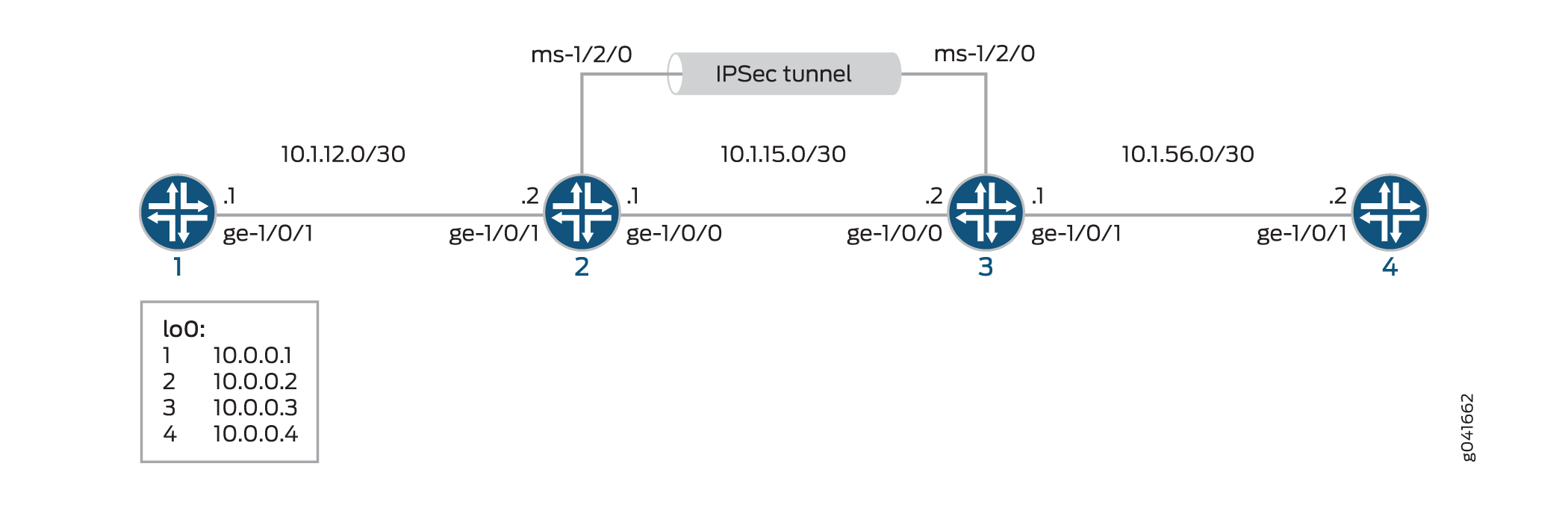
如果未在多服务 PIC 上指定 IKE 提议、IPsec 提议和 IPsec 策略,则 Junos OS 默认为最高级别的加密和身份验证。因此,默认身份验证协议为 ESP,默认身份验证模式为 HMAC-SHA1-96,默认加密模式为 3DES-CBC。
配置
要配置 IKE 动态 SA,请执行以下任务:
此示例中显示的接口类型仅供参考。例如,您可以使用 so- 接口代替 ge- sp- ms-和 。
配置路由器 1
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 1 的 [edit] 层级的 CLI 中。
set interfaces ge-0/0/0 description "to R2 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.12.2/30 set interfaces lo0 unit 0 family inet address 10.0.0.1/32 set routing-options router-id 10.0.0.1 set protocols ospf area 0.0.0.0 interface ge-0/0/0 set protocols ospf area 0.0.0.0 interface lo0.0
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要配置路由器 1 以便与路由器 2 建立 OSPF 连接:
配置以太网接口和环路接口。
[edit interfaces] user@router1# set ge-0/0/0 description "to R2 ge-0/0/0" user@router1# set ge-0/0/0 unit 0 family inet address 10.1.12.2/30 user@router1# set lo0 unit 0 family inet address 10.0.0.1/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
[edit interfaces] user@router1# set ospf area 0.0.0.0 interface ge-0/0/0.0 user@router1# set ospf area 0.0.0.0 interface lo0.0
配置路由器 ID。
[edit routing-options] user@router1# set router-id 10.0.0.1
提交配置。
[edit] user@router1# commit
结果
在配置模式下,输入 show interfaces、 show protocols ospf和 show routing-options 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router1# show interfaces
interfaces {
ge-0/0/0 {
description "To R2 ge-0/0/0";
unit 0 {
family inet {
address 10.1.12.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.1/32;
}
}
}
}
user@router1# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
}
}
}
user@router1# show routing-options
routing-options {
router-id 10.0.0.1;
}
配置路由器 2
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 2 层次结构级别的 CLI 中。
set interfaces ge-0/0/0 description "to R1 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.12.1/30 set interfaces ge-0/0/1 description "to R3 ge-0/0/1" set interfaces ge-0/0/1 unit 0 family inet address 10.1.15.1/30 set interfaces ms-1/2/0 services-options syslog host local services info set interfaces ms-1/2/0 unit 0 family inet set interfaces ms-1/2/0 unit 1 family inet set interfaces ms-1/2/0 unit 1 service-domain inside set interfaces ms-1/2/0 unit 2 family inet set interfaces ms-1/2/0 unit 2 service-domain outside set interfaces lo0 unit 0 family inet address 10.0.0.2/32 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 set protocols ospf area 0.0.0.0 interface ms-1/2/0.1 set routing-options router-id 10.0.0.2 set services ipsec-vpn rule rule-ike term term-ike then remote-gateway 10.1.15.2 set services ipsec-vpn rule rule-ike term term-ike then dynamic ike-policy ike-demo-policy set services ipsec-vpn rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy set services ipsec-vpn rule match-direction input set services ipsec-vpn ike proposal ike-demo-proposal authentication-method pre-shared-keys set services ipsec-vpn ike proposal ike-demo-proposal dh-group group2 set services ipsec-vpn ike policy ike-demo-policy pre-shared proposals demo-proposal set services ipsec-vpn ike policy ike-demo-policy pre-shared pre-shared-key ascii-text keyfordemo set services ipsec-vpn ipsec proposal ipsec-demo-proposal protocol esp set services ipsec-vpn ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec proposals ipsec-demo-proposal set services service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 set services service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 set services service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.1 set services service-set demo-service-set ipsec-vpn-rules rule-ike
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要在路由器 2 上配置 OSPF 连接和 IPsec 隧道参数:
配置接口属性。在此步骤中,您将配置两个以太网接口(ge-1/0/0 和 ge-1/0/1)、一个环路接口和一个多服务接口 (ms-1/2/0)。
[edit interfaces] user@router2# set ge-0/0/0 description "to R1 ge-0/0/0" user@router2# set ge-0/0/0 unit 0 family inet address 10.1.12.1/30 user@router2# set ge-0/0/1 description "to R3 ge-0/0/1" user@router2# set ge-0/0/1 unit 0 family inet address 10.1.15.1/30 user@router2# set ms-1/2/0 services-options syslog host local services info user@router2# set ms-1/2/0 unit 0 family inet user@router2# set ms-1/2/0 unit 1 family inet user@router2# set ms-1/2/0 unit 1 service-domain inside user@router2# set ms-1/2/0 unit 2 family inet user@router2# set ms-1/2/0 unit 2 service-domain outside user@router2# set lo0 unit 0 family inet address 10.0.0.2/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
[edit protocols] user@router2# set ospf area 0.0.0.0 interface ge-0/0/0.0 user@router2# set ospf area 0.0.0.0 interface lo0.0 user@router2# set ospf area 0.0.0.0 interface ms-1/2/0.1
配置路由器 ID。
[edit routing-options] user@router2# set router-ID 10.0.0.2
配置 IPsec 规则。在此步骤中,您将配置 IPsec 规则,指定手册 SA 参数,例如远程网关地址、身份验证和加密属性等。
注意:默认情况下,Junos OS 使用 IKE 策略版本 1.0。Junos OS 11.4 及更高版本还支持 IKE 策略 2.0 版,您必须在 上
[edit services ipsec-vpn ike policy policy-name pre-shared]进行配置。[edit services ipsec-vpn] user@router2# set rule rule-ike term term-ike then remote-gateway 10.1.15.2 user@router2# set rule rule-ike term term-ike then dynamic ike-policy ike-demo-policy user@router2# set rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy user@router2# set rule match-direction input user@router2# set ike proposal ike-demo-proposal authentication-method pre-shared-keys user@router2# set ike proposal ike-demo-proposal dh-group group2 user@router2# set ike policy ike-demo-policy pre-shared proposals demo-proposal user@router2# set ike policy ike-demo-policy pre-shared pre-shared-key ascii-text keyfordemo user@router2# set ipsec proposal ipsec-demo-proposal protocol esp user@router2# set ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 user@router2# set ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc user@router2# set ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 user@router2# set ipsec proposals ipsec-demo-proposal
配置下一跃点样式的服务集,指定本地网关地址,并将 IPsec VPN 规则与服务集相关联。
[edit services] user@router2# set service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 user@router2# set service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 user@router2# set service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.1 user@router2# set service-set demo-service-set ipsec-vpn-rules rule-ike
提交配置。
[edit] user@router2# commit
结果
在配置模式下,输入 show interfaces、 show protocols ospf、 show routing-options和 show services 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router1# show interfaces
interfaces {
ge-0/0/0 {
description "To R1 ge-0/0/0";
unit 0 {
family inet {
address 10.1.12.1/30;
}
}
}
ge-0/0/1 {
description "To R3 ge-0/0/1";
unit 0 {
family inet {
address 10.1.15.1/30;
}
}
}
ms-1/2/0 {
services-options {
syslog {
host local {
services info;
}
}
}
unit 0 {
family inet;
}
unit 1 {
family inet;
service-domain inside;
}
unit 2 {
family inet;
service-domain outside;
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.2/32;
}
}
}
}
user@router2# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
interface ms-1/2/0.1;
}
}
}
user@router2# show routing-options
routing-options {
router-id 10.0.0.2;
}
user@router2# show services
services {
ipsec-vpn {
rule rule-ike {
term term-ike {
then {
remote-gateway 10.1.15.2;
dynamic {
ike-policy ike-demo-policy;
ipsec-policy ipsec-demo-policy;
}
}
}
match-direction input;
}
ike {
proposal ike-demo-proposal {
authentication-method pre-shared-keys;
dh-group group2;
}
policy ike-demo-policy {
proposals demo-proposal;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
}
ipsec {
proposal ipsec-demo-proposal {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy ipsec-demo-policy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec-demo-proposal;
}
}
}
service-set demo-service-set {
next-hop-service {
inside-service-interface ms-1/2/0.1;
outside-service-interface ms-1/2/0.2;
}
ipsec-vpn-options {
local-gateway 10.1.15.1;
}
ipsec-vpn-rules rule-ike;
}
service-set demo-service-set {
next-hop-service {
inside-service-interface ms-1/2/0.1;
outside-service-interface ms-1/2/0.2;
}
ipsec-vpn-options {
local-gateway 10.1.15.2;
}
ipsec-vpn-rules rule-ike;
}
配置路由器 3
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 3 的 [edit] 层级的 CLI 中。
set interfaces ge-0/0/0 description "to R4 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.56.1/30 set interfaces ge-0/0/1 description "to R2 ge-0/0/1" set interfaces ge-0/0/1 unit 0 family inet address 10.1.15.2/30 set interfaces ms-1/2/0 services-options syslog host local services info set interfaces ms-1/2/0 unit 0 family inet set interfaces ms-1/2/0 unit 1 family inet set interfaces ms-1/2/0 unit 1 service-domain inside set interfaces ms-1/2/0 unit 2 family inet set interfaces ms-1/2/0 unit 2 service-domain outside set interfaces lo0 unit 0 family inet address 10.0.0.3/32 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 set protocols ospf area 0.0.0.0 interface ms-1/2/0.1 set routing-options router-id 10.0.0.3 set services ipsec-vpn rule rule-ike term term-ike then remote-gateway 10.1.15.1 set services ipsec-vpn rule rule-ike term term-ike then dynamic ike-policy ike-demo-policy set services ipsec-vpn rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy set services ipsec-vpn rule match-direction input set services ipsec-vpn ike proposal ike-demo-proposal authentication-method pre-shared-keys set services ipsec-vpn ike proposal ike-demo-proposal dh-group group2 set services ipsec-vpn ike policy ike-demo-policy pre-shared proposals demo-proposal set services ipsec-vpn ike policy ike-demo-policy pre-shared pre-shared-key ascii-text keyfordemo set services ipsec-vpn ipsec proposal ipsec-demo-proposal protocol esp set services ipsec-vpn ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc set services ipsec-vpn ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 set services ipsec-vpn ipsec proposals ipsec-demo-proposal set services service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 set services service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 set services service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.2 set services service-set demo-service-set ipsec-vpn-rules rule-ike
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要在路由器 3 上配置 OSPF 连接和 IPsec 隧道参数:
配置接口属性。在此步骤中,您将配置两个以太网接口(ge-1/0/0 和 ge-1/0/1)、一个环路接口和一个多服务接口 (ms-1/2/0)。
[edit interfaces] user@router3# set ge-0/0/0 description "to R4 ge-0/0/0" user@router3# set ge-0/0/0 unit 0 family inet address 10.1.56.1/30 user@router3# set ge-0/0/1 description "to R2 ge-0/0/1" user@router3# set ge-0/0/1 unit 0 family inet address 10.1.15.2/30 user@router3# set ms-1/2/0 services-options syslog host local services info user@router3# set ms-1/2/0 unit 0 family inet user@router3# set ms-1/2/0 unit 1 family inet user@router3# set ms-1/2/0 unit 1 service-domain inside user@router3# set ms-1/2/0 unit 2 family inet user@router3# set ms-1/2/0 unit 2 service-domain outside user@router3# set lo0 unit 0 family inet address 10.0.0.3/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
[edit protocols] user@router3# set ospf area 0.0.0.0 interface ge-0/0/0.0 user@router3# set ospf area 0.0.0.0 interface lo0.0 user@router3# set ospf area 0.0.0.0 interface ms-1/2/0.1
配置路由器 ID。
[edit routing-options] user@router3# set router-id 10.0.0.3
配置 IPsec 规则。在此步骤中,您将配置 IPsec 规则并指定手册 SA 参数,例如远程网关地址、身份验证和加密属性等。
[edit services ipsec-vpn] user@router3# set rule rule-ike term term-ike then remote-gateway 10.1.15.1 user@router3# set rule rule-ike term term-ike then dynamic ike-policy ike-demo-policy user@router3# set rule rule-ike term term-ike then dynamic ipsec-policy ipsec-demo-policy user@router3# set rule match-direction input user@router3# set ike proposal ike-demo-proposal authentication-method pre-shared-keys user@router3# set ike proposal ike-demo-proposal dh-group group2 user@router3# set ike policy ike-demo-policy pre-shared proposals demo-proposal user@router3# set ike policy ike-demo-policy pre-shared pre-shared-key ascii-text keyfordemo user@router3# set ipsec proposal ipsec-demo-proposal protocol esp user@router3# set ipsec proposal ipsec-demo-proposal authentication-algorithm hmac-sha1-96 user@router3# set ipsec proposal ipsec-demo-proposal encryption-algorithm 3des-cbc user@router3# set ipsec policy ipsec-demo-policy perfect-forward-secrecy keys group2 user@router3# set ipsec proposals ipsec-demo-proposal
配置下一跃点样式的服务集,指定本地网关地址,并将 IPsec VPN 规则与服务集相关联。
[edit services] user@router3# set service-set demo-service-set next-hop-service inside-service-interface ms-1/2/0.1 user@router3# set service-set demo-service-set next-hop-service outside-service-interface ms-1/2/0.2 user@router3# set service-set demo-service-set ipsec-vpn-options local-gateway 10.1.15.2 user@router3# set service-set demo-service-set ipsec-vpn-rules rule-ike
提交配置。
[edit] user@router3# commit
结果
在配置模式下,输入 show interfaces、 show protocols ospf、 show routing-options和 show services 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router3# show interfaces
interfaces {
ge-0/0/0 {
description "To R4 ge-0/0/0";
unit 0 {
family inet {
address 10.1.56.1/30;
}
}
}
ge-0/0/1 {
description "To R2 ge-0/0/1";
unit 0 {
family inet {
address 10.1.15.2/30;
}
}
}
ms-1/2/0 {
services-options {
syslog {
host local {
services info;
}
}
}
unit 0 {
family inet {
}
unit 1 {
family inet;
service-domain inside;
}
unit 2 {
family inet;
service-domain outside;
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.3/32;
}
}
}
}
}
user@router3# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
interface ms-1/2/0.1;
}
}
}
user@router3# show routing-options
routing-options {
router-id 10.0.0.3;
}
user@router3# show services
services {
ipsec-vpn {
rule rule-ike {
term term-ike {
then {
remote-gateway 10.1.15.1;
dynamic {
ike-policy ike-demo-policy;
ipsec-policy ipsec-demo-policy;
}
}
}
match-direction input;
}
ike {
proposal ike-demo-proposal {
authentication-method pre-shared-keys;
dh-group group2;
}
policy ike-demo-policy {
proposals demo-proposal;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
}
ipsec {
proposal ipsec-demo-proposal {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
}
policy ipsec-demo-policy {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec-demo-proposal;
}
}
}
配置路由器 4
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,然后将命令复制并粘贴到路由器 4 层次结构级别的 CLI 中。
set interfaces ge-0/0/0 description "to R3 ge-0/0/0" set interfaces ge-0/0/0 unit 0 family inet address 10.1.56.2/30 set interfaces lo0 unit 0 family inet address 10.0.0.4/32 set protocols ospf area 0.0.0.0 interface ge-0/0/0.0 set protocols ospf area 0.0.0.0 interface lo0.0 set routing-options router-id 10.0.0.4
分步程序
下面的示例要求您在各个配置层级中进行导航。有关导航 CLI 的信息,请参阅 《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
要设置与路由器 4 的 OSPF 连接,请执行以下作
配置接口。在此步骤中,您将配置一个以太网接口 (ge-1/0/1) 和一个环路接口。
user@router4# set interfaces ge-0/0/0 description "to R3 ge-0/0/0" user@router4# set interfaces ge-0/0/0 unit 0 family inet address 10.1.56.2/30 user@router4# set interfaces lo0 unit 0 family inet address 10.0.0.4/32
指定 OSPF 区域,并将接口与 OSPF 区域相关联。
user@router4# set protocols ospf area 0.0.0.0 interface ge-0/0/0 user@router4# set protocols ospf area 0.0.0.0 interface lo0.0
配置路由器 ID。
[edit routing-options] user@router4# set router-id 10.0.0.4
结果
在配置模式下,输入 show interfaces、 show protocols ospf和 show routing-options 命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的说明以更正配置
user@router4# show interfaces
interfaces {
ge-0/0/0 {
description "To R3 ge-0/0/0";
unit 0 {
family inet {
address 10.1.56.2/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 10.0.0.4/32;
}
}
}
}
user@router4# show protocols ospf
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0;
}
}
}
user@router4# show routing-options
routing-options {
router-id 10.0.0.4;
}
验证
验证您在路由器 1 上的工作
目的
验证路由器 1 是否正常运行。
行动
在作模式下,对路由器 4 上的 ge-0/0/0 接口输入 ping 10.1.56.2 命令,以通过 IPsec 隧道发送流量
user@router1>ping 10.1.56.2 PING 10.1.56.2 (10.1.56.2): 56 data bytes 64 bytes from 10.1.56.2: icmp_seq=0 ttl=254 time=1.351 ms 64 bytes from 10.1.56.2: icmp_seq=1 ttl=254 time=1.187 ms 64 bytes from 10.1.56.2: icmp_seq=2 ttl=254 time=1.172 ms 64 bytes from 10.1.56.2: icmp_seq=3 ttl=254 time=1.154 ms 64 bytes from 10.1.56.2: icmp_seq=4 ttl=254 time=1.156 ms ^C --- 10.1.56.2 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.154/1.204/1.351/0.074 ms
意义
输出显示路由器 1 能够通过 IPsec 隧道到达路由器 4。
验证您在路由器 2 上的工作
目的
验证 IKE SA 协商是否成功。
行动
在作模式下,输入命令 show services ipsec-vpn ike security-associations 。
user@router2>show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 10.1.15.2 Matured 03075bd3a0000003 4bff26a5c7000003 Main
要验证 IPsec 安全关联是否处于活动状态,请发出命令 show services ipsec-vpn ipsec security-associations detail 。请注意,SA 包含多服务 PIC 固有的默认设置,例如,用于协议的 ESP 和用于身份验证算法的 HMAC-SHA1-96。
在作模式下,输入命令 show services ipsec-vpn ipsec security-associations detail 。
user@router2> show services ipsec-vpn ipsec security-associations detail Service set: demo-service-set Rule: rule-ike, Term: term-ike, Tunnel index: 1 Local gateway: 10.1.15.1, Remote gateway: 10.1.15.2 Local identity: ipv4_subnet(any:0,[0..7]=10.1.12.0/24) Remote identity: ipv4_subnet(any:0,[0..7]=10.1.56.0/24) Direction: inbound, SPI: 2666326758, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 26863 seconds Hard lifetime: Expires in 26998 seconds Anti-replay service: Enabled, Replay window size: 64 Direction: outbound, SPI: 684772754, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 26863 seconds Hard lifetime: Expires in 26998 seconds Anti-replay service: Enabled, Replay window size: 64
要验证流量是否正在通过双向 IPsec 隧道传输,请发出以下 show services ipsec-vpn statistics 命令:
在作模式下,输入命令 show services ipsec-vpn statistics 。
user@router2> show services ipsec-vpn ipsec statistics PIC: ms-1/2/0, Service set: demo-service-set ESP Statistics: Encrypted bytes: 2248 Decrypted bytes: 2120 Encrypted packets: 27 Decrypted packets: 25 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0
意义
show services ipsec-vpn ipsec security-associations detail命令输出显示您配置的 SA 属性。
命令输出显示 show services ipsec-vpn ipsec statistics 通过 IPsec 隧道的流量。
验证您在路由器 3 上的工作
目的
验证路由器 3 上的 IKE SA 协商是否成功。
行动
在作模式下,输入命令 show services ipsec-vpn ike security-associations 。要成功,路由器 3 上的 SA 必须包含在您在路由器 2 上指定的相同设置。
user@router3>show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 10.1.15.1 Matured 03075bd3a0000003 4bff26a5c7000003 Main
要验证 IPsec SA 是否处于活动状态,请发出命令 show services ipsec-vpn ipsec security-associations detail 。要成功,路由器 3 上的 SA 必须包含在您在路由器 2 上指定的相同设置。
在作模式下,输入命令 show services ipsec-vpn ipsec security-associations detail 。
user@router3>show services ipsec-vpn ipsec security-associations detail Service set: demo-service-set Rule: rule-ike, Term: term-ike, Tunnel index: 1 Local gateway: 10.1.15.2, Remote gateway: 10.1.15.1 Local identity: ipv4_subnet(any:0,[0..7]=10.1.56.0/24) Remote identity: ipv4_subnet(any:0,[0..7]=10.1.12.0/24) Direction: inbound, SPI: 684772754, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 26598 seconds Hard lifetime: Expires in 26688 seconds Anti-replay service: Enabled, Replay window size: 64 Direction: outbound, SPI: 2666326758, AUX-SPI: 0 Mode: tunnel, Type: dynamic, State: Installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Soft lifetime: Expires in 26598 seconds Hard lifetime: Expires in 26688 seconds Anti-replay service: Enabled, Replay window size: 64
要验证流量是否正在通过双向 IPsec 隧道传输,请发出以下 show services ipsec-vpn statistics 命令:
在作模式下,输入命令 show services ipsec-vpn ike security-associations 。
user@router3>show services ipsec-vpn ipsec statistics PIC: ms-1/2/0, Service set: demo-service-set ESP Statistics: Encrypted bytes: 2120 Decrypted bytes: 2248 Encrypted packets: 25 Decrypted packets: 27 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0
意义
show services ipsec-vpn ipsec security-associations detail命令输出显示您配置的 SA 属性。
命令输出显示 show services ipsec-vpn ipsec statistics 通过 IPsec 隧道的流量。
验证您在路由器 4 上的工作
目的
验证 IKE SA 协商是否成功。
行动
在作模式下,对路由器 1 上的 ge-0/0/0 接口输入 ping 10.1.12.2 命令,以通过 IPsec 隧道发送流量。
user@router4>ping 10.1.12.2 PING 10.1.12.2 (10.1.12.2): 56 data bytes 64 bytes from 10.1.12.2: icmp_seq=0 ttl=254 time=1.350 ms 64 bytes from 10.1.12.2: icmp_seq=1 ttl=254 time=1.161 ms 64 bytes from 10.1.12.2: icmp_seq=2 ttl=254 time=1.124 ms 64 bytes from 10.1.12.2: icmp_seq=3 ttl=254 time=1.142 ms 64 bytes from 10.1.12.2: icmp_seq=4 ttl=254 time=1.139 ms 64 bytes from 10.1.12.2: icmp_seq=5 ttl=254 time=1.116 ms ^C --- 10.1.12.2 ping statistics --- 6 packets transmitted, 6 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.116/1.172/1.350/0.081 ms
要确认流量通过 IPsec 隧道传输,请向路由器 1 上的 ge-0/0/0 接口发出 traceroute 命令。请注意,路径中未引用路由器 2 和 3 之间的物理接口;流量通过路由器 3 上的自适应服务 IPsec 内部接口进入 IPsec 隧道,通过路由器 2 上的环路接口,最后在路由器 1 上的 ge-0/0/0 接口结束。
在作模式下,输入 traceroute 10.1.12.2。
user@router4>traceroute 10.1.12.2 traceroute to 10.1.12.2 (10.1.12.2), 30 hops max, 40 byte packets 1 10.1.15.2 (10.1.15.2) 0.987 ms 0.630 ms 0.563 ms 2 10.0.0.2 (10.0.0.2) 1.194 ms 1.058 ms 1.033 ms 3 10.1.12.2 (10.1.12.2) 1.073 ms 0.949 ms 0.932 ms
意义
ping 10.1.12.2输出显示路由器 4 能够通过 IPsec 隧道到达路由器 1。
输出显示 traceroute 10.1.12.2 流量通过 IPsec 隧道传输。
配置 IPsec 规则
要配置 IPsec 规则,请在层次结构级别添加该 rule 语句并指定规则名称 [edit services ipsec-vpn] :
[edit services ipsec-vpn] rule rule-name { match-direction (input | output); term term-name { from { destination-address address; ipsec-inside-interface interface-name; source-address address; } then { anti-replay-window-size bits; backup-remote-gateway address; clear-dont-fragment-bit; dynamic { ike-policy policy-name; ipsec-policy policy-name; } initiate-dead-peer-detection; dead-peer-detection { interval seconds; threshold number; } manual { direction (inbound | outbound | bidirectional) { authentication { algorithm (hmac-md5-96 | hmac-sha1-96); key (ascii-text key | hexadecimal key); } auxiliary-spi spi-value; encryption { algorithm algorithm; key (ascii-text key | hexadecimal key); } protocol (ah | bundle | esp); spi spi-value; } } no-anti-replay; remote-gateway address; syslog; tunnel-mtu bytes; } } }
每个 IPsec 规则都由一组术语组成,类似于防火墙过滤器。
术语由以下内容组成:
from语句 — 指定包含和排除的匹配条件和应用。then语句 — 指定要由路由器软件执行的作和作修饰符。
以下部分介绍如何配置 IPsec 规则的组件:
配置 IPsec 规则的匹配方向
每个规则都必须包含一个match-direction语句,用于指定是在接口的输入端还是输出端应用匹配。要配置匹配的应用位置,请在层次结构级别包含[edit services ipsec-vpn rule rule-name]该match-direction (input | output)语句:
[edit services ipsec-vpn rule rule-name] match-direction (input | output);
ACX 系列路由器不支持 match-direction AS output。
匹配方向用于通过 AS 或多服务 PIC 的流量。将数据包发送至 PIC 时,方向信息也会随之携带。
对于接口服务集,数据包的方向取决于数据包是进入还是离开应用了服务集的接口。
有了下一跳点服务集,数据包的方向由用于将数据包路由到 AS 或多服务 PIC 的接口决定。如果使用内部接口路由数据包,则输入数据包方向。如果使用外部接口将数据包定向到 PIC,则输出数据包方向。
在 AS 或多服务 PIC 上,将执行流查找。如果未找到流,则执行规则处理。服务集中的所有规则都会被考虑在内。在规则处理过程中,系统会将数据包方向与规则方向进行比较。仅考虑方向信息与数据包方向匹配的规则。
在 IPsec 规则中配置匹配条件
要在 IPsec 规则中配置匹配条件,请在[edit services ipsec-vpn rule rule-name term term-name]层次结构级别包含该from语句:
[edit services ipsec-vpn rule rule-name term term-name] from { destination-address address; ipsec-inside-interface interface-name; source-address address; }
您可以使用源地址或目标地址作为匹配条件,其配置方式与配置防火墙过滤器的方式相同;有关更多信息,请参阅 Junos OS 路由协议库。
IPsec 服务支持 IPv4 和 IPv6 地址格式。如果未专门配置源地址或目标地址,则使用默认值 0.0.0.0/0 (IPv4 ANY)。要将 IPv6 ANY (0::0/128) 用作源地址或目标地址,必须对其进行显式配置。
ACX 系列上的 IPsec 服务支持 IPv4 地址格式。如果未专门配置源地址或目标地址,则使用默认值 0.0.0.0/0 (IPv4 ANY)。
仅对于下一跃点样式的服务集,该ipsec-inside-interface语句允许您将逻辑接口分配给由于此匹配条件而建立的隧道。inside-service-interface您可以在层次结构级别配置[edit services service-set name next-hop-service]的语句允许您将 和 .2 指定.1为内部和外部接口。但是,您可以使用语句配置多个自适应服务逻辑接口service-domain inside,并使用其中一个接口来配置语ipsec-inside-interface句。
Junos OS 评估您在语句中 from 配置的条件。如果在同一下一跃点样式服务集中配置了多个链路类型隧道, ipsec-inside-interface 则如果所有隧道的源地址和目的地址均为 0.0.0.0/0 (ANY-ANY),则该值使规则查找模块能够将特定隧道与其他隧道区分开来。
配置该 ipsec-inside-interface 语句时,不支持接口样式的服务集。
包含“any-any”匹配条件的术语提供了特殊情况(通常是因为省略了该 from 语句)。如果隧道中存在任意任意匹配,则不需要流量,因为此隧道中的所有流量都使用相同的安全关联 (SA),并且数据包选择器不会发挥重要作用。因此,这些隧道将使用基于数据包的 IPsec。此策略可在 PIC 上节省部分流资源,用于需要基于流服务的其他隧道。
以下配置示例显示了任意-任意隧道配置,其中不带 from 语句 term-1。子句中 from 缺少选择器将导致基于数据包的 IPsec 服务。
services {
ipsec-vpn {
rule rule-1 {
term term-1 {
then {
remote-gateway 10.1.0.1;
dynamic {
ike-policy ike_policy;
ipsec-policy ipsec_policy;
}
}
}
match-direction input;
}
.....
}
在专用模式和共享模式下,我们都可向具有任意-任意匹配的链路类型隧道以及具有任意-任意匹配的动态隧道提供无流 IPsec 服务。
对于链路类型隧道,服务集中支持无流和基于流的混合 IPsec。如果服务集在子句中 from 包含某些带有任意匹配的术语和带有选择器的某些术语,则将为任意任意隧道提供基于数据包的服务,并为其他带有选择器的隧道提供基于流的服务。
对于非链路类型隧道,如果服务集同时包含任意-任意术语和基于选择器的术语,则将向所有隧道提供基于流的服务。
在 IPsec 规则中配置作
要在 IPsec 规则中配置作,请在[edit services ipsec-vpn rule rule-name term term-name]层次结构级别包含该then语句:
[edit services ipsec-vpn rule rule-name term term-name] then { anti-replay-window-size bits; backup-remote-gateway address; clear-dont-fragment-bit; dynamic { ike-policy policy-name; ipsec-policy policy-name; } initiate-dead-peer-detection; dead-peer-detection { interval seconds; threshold number; } manual { direction (inbound | outbound | bidirectional) { authentication { algorithm (hmac-md5-96 | hmac-sha1-96); key (ascii-text key | hexadecimal key); } auxiliary-spi spi-value; encryption { algorithm algorithm; key (ascii-text key | hexadecimal key); } protocol (ah | bundle | esp); spi spi-value; } } no-anti-replay; remote-gateway address; syslog; tunnel-mtu bytes; }
主要 IPsec作是配置动态或手册 SA:
配置动态 SA 的方法是在层次结构级别包含
dynamic[edit services ipsec-vpn rule rule-name term term-name then]语句,并引用在和层次结构级别配置[edit services ipsec-vpn ipsec][edit services ipsec-vpn ike]的策略。可以通过在层次结构级别包含
manual[edit services ipsec-vpn rule rule-name term term-name then]该语句来配置手册 SA。
您可以配置以下附加属性:
启用 IPsec 数据包分片
要在 IPsec 隧道中启用 IP 版本 4 (IPv4) 数据包分段,请在层次结构级别包含[edit services ipsec-vpn rule rule-name term term-name then]该clear-dont-fragment-bit语句:
[edit services ipsec-vpn rule rule-name term term-name then] clear-dont-fragment-bit;
设置该 clear-dont-fragment-bit 语句将清除数据包头中的不分段 (DF) 位,无论数据包大小如何。如果数据包大小超过隧道最大传输单元 (MTU) 值,则数据包将在封装前进行分片。对于 IPsec 隧道,无论接口 MTU 设置如何,默认 MTU 值均为 1500。
配置目的地址以进行失效对等方检测
要指定 IPsec 流量定向到的远程地址,请在层次结构级别包含该 remote-gateway 语句 [edit services ipsec-vpn rule rule-name term term-name then] :
[edit services ipsec-vpn rule rule-name term term-name then] remote-gateway address;
要指定备份远程地址,请在层次结构级别包含[edit services ipsec-vpn rule rule-name term term-name then]以下backup-remote-gateway语句:
[edit services ipsec-vpn rule rule-name term term-name then] backup-remote-gateway address;
这两个语句同时支持 IPv4 和 IPv6 地址格式。
配置该 backup-remote-gateway 语句可启用失效对等方检测 (DPD) 协议,用于监控隧道状态和远程对等方可用性。当语句定义 remote-gateway 的主隧道处于活动状态时,备用隧道处于备用模式。如果 DPD 协议确定主远程网关地址不再可访问,则会建立一条指向备份地址的新隧道。
如果在定义的 10 秒间隔内没有来自对等方的传入流量,则路由器会将隧道检测为非活动状态。全局计时器每 10 秒轮询一次所有隧道,自适应服务 (AS) 或多服务物理接口卡 (PIC) 会发送一条消息,列出所有非活动隧道。如果隧道变为非活动状态,路由器将采取以下步骤故障转移到备份地址:
自适应服务消息触发 DPD 协议向对等方发送 hello 消息。
如果未收到确认,则以 2 秒的间隔发送两次重试,然后宣布隧道失效。
如果隧道被宣布失效或存在 IPsec 第 1 阶段协商超时,则将进行故障切换。主隧道将置于备用模式,备份将变为活动状态。
如果与备用隧道的协商超时,路由器将切换回主隧道。如果两个对等方都关闭,它将尝试故障切换六次。然后,系统将停止故障切换并恢复到原始配置,主隧道处于活动状态,备份隧道处于备用模式。
您还可以在层次结构级别包含[edit services ipsec-vpn rule rule-name term term-name then]以下initiate-dead-peer-detection语句,而无需配置备份远程网关,从而启用 DPD hello 消息的触发:
[edit services ipsec-vpn rule rule-name term term-name then] initiate-dead-peer-detection; dead-peer-detection { interval seconds; threshold number; }
此外,对于 IKEv1 SA,您可以在使用initiate-dead-peer-detection语句时在语句下dead-peer-detection设置 interval 和 threshold options。从 Junos OS 17.2R1 版开始,和threshold选项interval也适用于 IKEv2 SA。在 Junos OS 17.1 及更低版本中,interval和threshold选项不适用于使用默认值的 IKEv2 SA。间隔是对等方在发送 DPD 请求数据包之前等待来自其目标对等方的流量的时间量,阈值是在对等方被视为不可用之前要发送的最大不成功 DPD 请求数。
监控行为与语句中 backup-remote-gateway 描述的相同。此配置使路由器能够在备份 IPsec 网关不存在时启动 DPD 查询,并在无法访问 IKE 对等方时清理 IKE 和 IPsec SA。
如果 DPD 协议确定主远程网关地址不再可访问,则会建立一条指向备份地址的新隧道。但是,如果配置 initiate-dead-peer-detection 没有备份远程网关地址,并且 DPD 协议确定主远程网关地址不再可访问,则隧道将被宣布为失效,并清理 IKE 和 IPsec SA。
有关 DPD 协议的详细信息,请参阅 RFC 3706, 一种基于流量的不工作互联网密钥交换 (IKE) 对等方检测方法。
配置或禁用 IPsec 防重放
要配置 IPsec 防重放窗口的大小,请在层次结构级别包含[edit services ipsec-vpn rule rule-name term term-name then]该anti-replay-window-size语句:
[edit services ipsec-vpn rule rule-name term term-name then] anti-replay-window-size bits;
anti-replay-window-size 可以采用 64 到 4096 位范围内的值。AS PIC 的默认值为 64 位,多服务 PIC 和 DPC 的默认值为 128 位。AS PIC 可支持 1024 位的最大重放窗口大小,而多服务 PIC 和 DPC 可支持 4096 位的最大重放窗口大小。当软件提交 IPsec 配置时,密钥管理进程 (kmd) 无法区分服务接口类型。因此,如果 AS PIC 的最大防重放窗口大小超过 1024,则提交将成功,并且不会生成任何错误消息。但是,即使 的 anti-replay-window-size 配置值更大,软件也会在内部将 AS PIC 的防重放窗口大小设置为 1024 位。
要禁用 IPsec 防重放功能,请在层次结构级别包含[edit services ipsec-vpn rule rule-name term term-name then]以下no-anti-replay语句:
[edit services ipsec-vpn rule rule-name term term-name then] no-anti-replay;
默认情况下,防重放服务处于启用状态。有时,这可能会导致与其他供应商设备的互作性问题。
指定 IPsec 隧道的 MTU
要为 IPsec 隧道配置特定的最大传输单元 (MTU) 值,请在层次结构级别包含[edit services ipsec-vpn rule rule-name term term-name then]该tunnel-mtu语句:
[edit services ipsec-vpn rule rule-name term term-name then] tunnel-mtu bytes;
此tunnel-mtu设置是为 IPsec 隧道配置 MTU 值的唯一位置。不支持在层次结构级别包含mtu[edit interfaces sp-fpc/pic/port unit logical-unit-number family inet]设置。
配置 IPsec 规则集
该rule-set语句定义了一组 IPsec 规则,用于确定路由器软件对数据流中的数据包执行的作。您可以通过指定规则名称和配置术语来定义每个规则。然后,您可以通过在层次结构级别包含[edit services ipsec-vpn]该语句并为每个规则添加一个rule语句来rule-set指定规则的顺序:
[edit services ipsec-vpn] rule-set rule-set-name { rule rule-name; }
路由器软件将按您在配置中指定的顺序处理规则。如果规则中的术语与数据包匹配,路由器将执行相应的作,并且规则处理将停止。如果规则中没有与数据包匹配的术语,则处理会继续执行规则集中的下一个规则。如果没有规则与数据包匹配,则默认情况下将丢弃数据包。
也可以看看
变更历史表
是否支持某项功能取决于您使用的平台和版本。使用 功能资源管理器 确定您的平台是否支持某个功能。
threshold选项
interval也适用于 IKEv2 SA。
