示例:在第 3 层网络中配置多节点高可用性
阅读本主题可了解如何在 SRX 系列防火墙上配置多节点高可用性解决方案。此示例介绍了在 SRX 系列防火墙连接到两端路由器时在主动/备份模式下的配置。
概述
在多节点高可用性方面,参与的 SRX 系列防火墙作为第 3 层网络中的独立节点运行。这些节点连接到属于不同网络的相邻基础架构。加密的逻辑机箱之间链路 (ICL) 通过路由网络连接节点。参与节点相互备份,以确保在发生系统或硬件故障时快速同步故障切换。
在多节点高可用性中,活动性在服务冗余组 (SRG) 级别确定。SRG1 处于活动状态的 SRX 系列防火墙托管浮动 IP 地址,并使用浮动 IP 地址引导流量流向浮动 IP 地址。在故障切换期间,浮动 IP 地址从旧活动节点移动到新的活动节点,并继续通信客户端设备。
我们在多节点高可用性解决方案中支持双节点配置。
要求
此示例使用以下硬件和软件组件:
-
两个 SRX 系列防火墙或 vSRX 虚拟防火墙实例
-
两个瞻博网络 (R) MX960 通用路由平台
-
Junos OS 22.3R1 版
拓扑结构
图 1 显示了此示例中使用的拓扑。
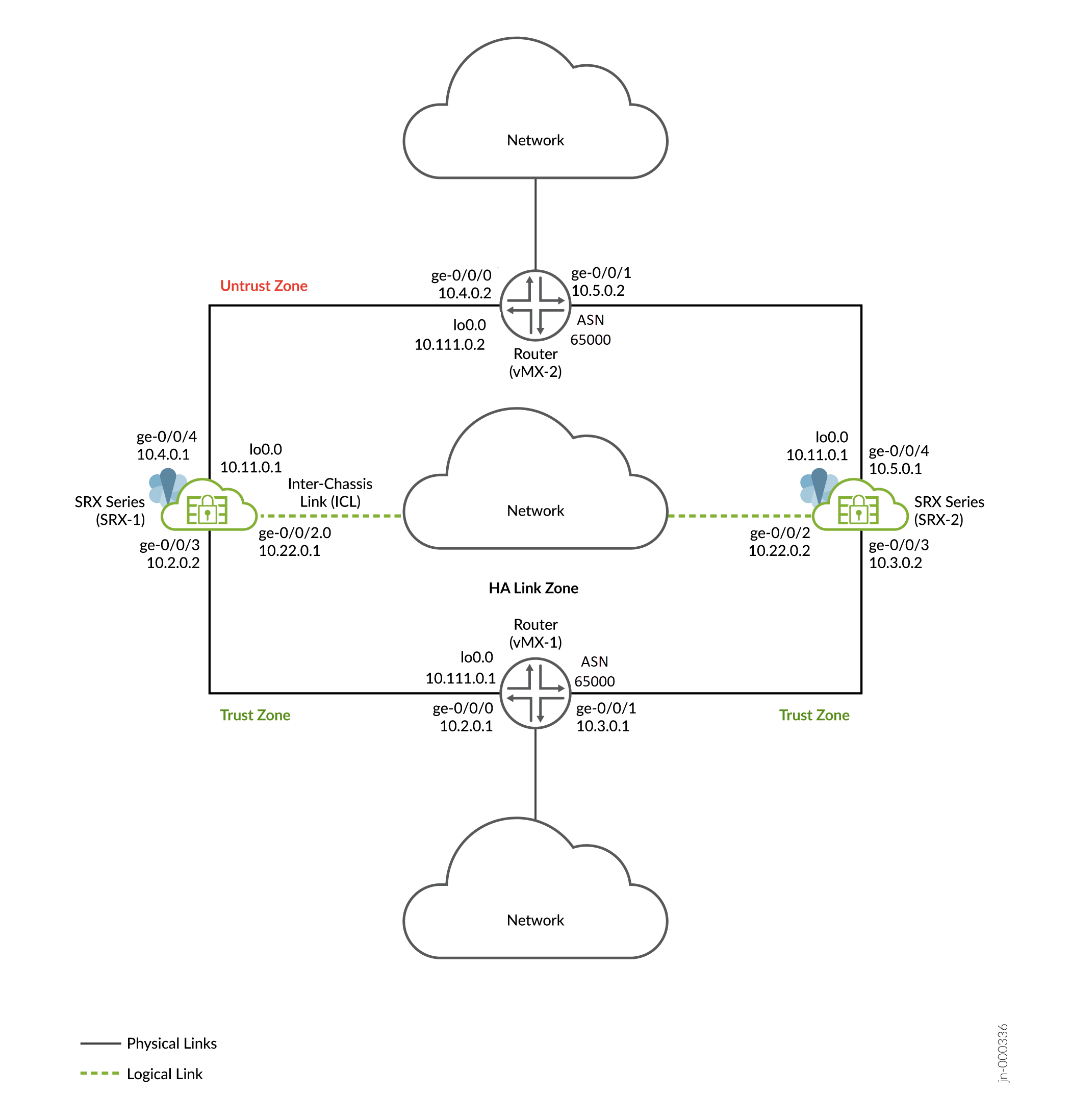 中的多节点高可用性
中的多节点高可用性
如拓扑图所示,两个 SRX 系列防火墙在信任端和非信任端连接到相邻路由器,形成 BGP 邻居关系。加密的逻辑机箱之间链路 (ICL) 通过路由网络连接节点。节点通过网络使用可路由的 IP 地址(浮动 IP 地址)相互通信。环路接口用于托管 SRX 系列和路由器上的 IP 地址。
通常,您可以使用聚合以太网 (AE) 或 SRX 系列防火墙上的收入以太网端口来建立 ICL 连接。在本例中,我们为 ICL 使用了 GE 端口。我们还为 ICL 路径配置了一个路由实例,以确保实现最大分段。
在典型的高可用性部署中,网络的北向和南向两侧有多个路由器和交换机。在本例中,我们在 SRX 系列防火墙的两侧使用了两台路由器。
在此示例中,您将在 SRX 系列防火墙之间建立高可用性,并通过启用高可用性链路加密来保护隧道流量。
您将执行以下任务来构建多节点高可用性设置:
- 通过分配 ID,将一对 SRX 系列防火墙配置为本地节点和对等节点。
- 配置服务冗余组。
- 配置一个环路接口 (lo0.0) 来托管浮动 IP 地址。
- 配置 IP 探针以确定和实施主动性
- 配置主动性实施所需的信号路由,并将其与路由存在策略一起使用。
- 使用 IKEv2 为高可用性 (ICL) 流量配置 VPN 配置文件。
- 配置 BFD 监控选项
- 配置路由策略和路由选项
- 配置适当的安全策略来管理网络中的流量
-
根据您的网络要求配置无状态防火墙过滤和服务质量 (QoS)。
-
根据您的网络要求配置接口和区域。您必须允许用于链路加密的 IKE 和用于配置同步的 SSH 等服务作为与 ICL 关联的安全区域上的主机入站系统服务。
在此示例中,您在 SRX-1 和 SRX-2 上使用静态路由,并将这些路由播发到 BGP 中,以添加指标以确定首选路径中的 SRX 系列防火墙。或者,您可以使用 SRX 系列防火墙上的路由反射器来通告通过 BGP 获知的路由,并相应地配置路由策略以在 BGP 上匹配。
您可以在 SRG0 和 SRG1 上配置以下选项:
-
SRG1:主动/备份信号路由、部署类型、主动性优先级、抢占、虚拟 IP 地址(用于默认网关部署)、主动性探测和备份处理数据包。
-
SRG1:SRG1 上的 BFD 监控、IP 监控和接口监控选项。
-
SRG0:故障时关机和故障时安装路由选项。
在 SRG1 下配置监控(BFD 或 IP 或接口)选项时,建议不要在 SRG0 下配置故障时关闭选项。
对于机箱之间链路 (ICL),建议采用以下配置设置:
- 使用环路 (lo0) 接口和聚合以太网接口 (ae0) 或任何收入以太网接口来建立 ICL。请勿使用专用高可用性端口(控制端口和交换矩阵端口)(如果 SRX 系列防火墙上可用)。
- 将 MTU 设置为 1514
- 在与用于 ICL 的接口相关联的安全区域上允许以下服务
-
IKE、高可用性、SSH
-
协议取决于您需要的路由协议。
-
BFD 来监视相邻路由。
-
从 st0.16000 到 st0.16385 的安全隧道接口 (st0) 保留用于多节点高可用性。这些接口不是用户可配置的接口。您只能使用 st0.0 到 st0.15999 之间的接口。
配置
开始之前
用于多节点高可用性的 SRX 系列防火墙配置需要 Junos IKE 软件包。此软件包可作为 SRX 系列防火墙的默认软件包或可选软件包提供。有关详细信息,请参阅 对 Junos IKE 包的支持 。
如果 SRX 系列防火墙默认未安装该软件包,请使用以下命令进行安装。您需要执行此步骤进行 ICL 加密。
user@host> request system software add optional://junos-ike.tgz Verified junos-ike signed by PackageProductionECP256_2022 method ECDSA256+SHA256 Rebuilding schema and Activating configuration... mgd: commit complete Restarting MGD ... WARNING: cli has been replaced by an updated version: CLI release 20220208.163814_builder.r1239105 built by builder on 2022-02-08 17:07:55 UTC Restart cli using the new version ? [yes,no] (yes)
CLI 快速配置
要快速配置此示例,请复制以下命令,将其粘贴到文本文件中,删除所有换行符,更改详细信息,以便与网络配置匹配,将命令复制并粘贴到层次结构级别的 [edit] CLI 中,然后从配置模式进入。commit
在 SRX-1 设备上
set chassis high-availability local-id 1 set chassis high-availability local-id local-ip 10.22.0.1 set chassis high-availability peer-id 2 peer-ip 10.22.0.2 set chassis high-availability peer-id 2 interface ge-0/0/2.0 set chassis high-availability peer-id 2 vpn-profile IPSEC_VPN_ICL set chassis high-availability peer-id 2 liveness-detection minimum-interval 400 set chassis high-availability peer-id 2 liveness-detection multiplier 5 set chassis high-availability services-redundancy-group 0 peer-id 2 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 2 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/4.0 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 preemption set chassis high-availability services-redundancy-group 1 activeness-priority 200 set interfaces ge-0/0/3 description "trust" unit 0 family inet address 10.2.0.2/16 set interfaces ge-0/0/4 description "untrust" unit 0 family inet address 10.4.0.1/16 set interfaces ge-0/0/2 description "ha_link" unit 0 family inet address 10.22.0.1/24 set interfaces lo0 description "untrust" unit 0 family inet address 10.11.0.1/32 set routing-options autonomous-system 65000 set routing-options static route 10.1.0.0/16 next-hop 10.2.0.1 set routing-options static route 10.6.0.0/16 next-hop 10.4.0.2 set routing-options static route 10.111.0.1 next-hop 10.2.0.1 set routing-options static route 10.111.0.2 next-hop 10.4.0.2 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces ge-0/0/4 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3 set security zones security-zone halink host-inbound-traffic system-services ike set security zones security-zone halink host-inbound-traffic system-services ping set security zones security-zone halink host-inbound-traffic system-services high-availability set security zones security-zone halink host-inbound-traffic system-services ssh set security zones security-zone halink host-inbound-traffic protocols bfd set security zones security-zone halink host-inbound-traffic protocols bgp set security zones security-zone halink interfaces ge-0/0/2 set security policies default-policy permit-all set system services netconf ssh set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys set security ike proposal MNHA_IKE_PROP dh-group group14 set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL set security ike gateway MNHA_IKE_GW version v2-only set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel set security ipsec proposal MNHA_IPSEC_PROP protocol esp set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1 table inet.0 set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2 table inet.0 set policy-options policy-statement mnha-route-policy term 1 from protocol static set policy-options policy-statement mnha-route-policy term 1 from protocol direct set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists set policy-options policy-statement mnha-route-policy term 1 then accept metric 10 set policy-options policy-statement mnha-route-policy term 2 from protocol static set policy-options policy-statement mnha-route-policy term 2 from protocol direct set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists set policy-options policy-statement mnha-route-policy term 2 then accept metric 20 set policy-options policy-statement mnha-route-policy term 3 from protocol static set policy-options policy-statement mnha-route-policy term 3 from protocol direct set policy-options policy-statement mnha-route-policy term 3 then accept metric 30 set policy-options policy-statement mnha-route-policy term default then reject set protocols bgp group trust type internal set protocols bgp group trust local-address 10.2.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust neighbor 10.2.0.1 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust local-as 65000 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.4.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust neighbor 10.4.0.2 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust local-as 65000
在 SRX-2 设备上
set chassis high-availability local-id 2 set chassis high-availability local-id local-ip 10.22.0.2 set chassis high-availability peer-id 1 peer-ip 10.22.0.1 set chassis high-availability peer-id 1 interface ge-0/0/2.0 set chassis high-availability peer-id 1 vpn-profile IPSEC_VPN_ICL set chassis high-availability peer-id 1 liveness-detection minimum-interval 400 set chassis high-availability peer-id 1 liveness-detection multiplier 5 set chassis high-availability services-redundancy-group 0 peer-id 1 set chassis high-availability services-redundancy-group 1 deployment-type routing set chassis high-availability services-redundancy-group 1 peer-id 1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 src-ip 10.5.0.1 set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 session-type singlehop set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.5.0.2 interface ge-0/0/4.0 set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 set chassis high-availability services-redundancy-group 1 activeness-priority 1 set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys set security ike proposal MNHA_IKE_PROP dh-group group14 set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL set security ike gateway MNHA_IKE_GW version v2-only set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel set security ipsec proposal MNHA_IPSEC_PROP protocol esp set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL set interfaces ge-0/0/3 description "trust" unit 0 family inet address 10.3.0.2/16 set interfaces ge-0/0/4 description "untrust" unit 0 family inet address 10.5.0.1/16 set interfaces ge-0/0/2 description "ha_link" unit 0 family inet address 10.22.0.2/24 set interfaces lo0 description "untrust" unit 0 family inet address 10.11.0.1/32 set routing-options autonomous-system 65000 set routing-options static route 10.1.0.0/16 next-hop 10.3.0.1 set routing-options static route 10.6.0.0/16 next-hop 10.5.0.2 set routing-options static route 10.111.0.1 next-hop 10.3.0.1 set routing-options static route 10.111.0.2 next-hop 10.5.0.2 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust host-inbound-traffic system-services ping set security zones security-zone untrust host-inbound-traffic protocols bfd set security zones security-zone untrust host-inbound-traffic protocols bgp set security zones security-zone untrust interfaces ge-0/0/4 set security zones security-zone untrust interfaces lo0.0 set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/3 set security zones security-zone halink host-inbound-traffic system-services ike set security zones security-zone halink host-inbound-traffic system-services ping set security zones security-zone halink host-inbound-traffic system-services high-availability set security zones security-zone halink host-inbound-traffic system-services ssh set security zones security-zone halink host-inbound-traffic protocols bfd set security zones security-zone halink host-inbound-traffic protocols bgp set security zones security-zone halink interfaces ge-0/0/2 set security policies default-policy permit-all set system services netconf ssh set policy-options route-filter-list loopback 10.11.0.0/24 orlonger set policy-options route-filter-list ipsec 10.6.0.0/16 orlonger set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1 table inet.0 set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2 table inet.0 set policy-options policy-statement mnha-route-policy term 1 from protocol static set policy-options policy-statement mnha-route-policy term 1 from protocol direct set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists set policy-options policy-statement mnha-route-policy term 1 then accept metric 10 set policy-options policy-statement mnha-route-policy term 2 from protocol static set policy-options policy-statement mnha-route-policy term 2 from protocol direct set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists set policy-options policy-statement mnha-route-policy term 2 then accept metric 20 set policy-options policy-statement mnha-route-policy term 3 from protocol static set policy-options policy-statement mnha-route-policy term 3 from protocol direct set policy-options policy-statement mnha-route-policy term 3 then accept metric 35 set policy-options policy-statement mnha-route-policy term default then reject set protocols bgp group trust type internal set protocols bgp group trust local-address 10.3.0.2 set protocols bgp group trust export mnha-route-policy set protocols bgp group trust neighbor 10.3.0.1 set protocols bgp group trust bfd-liveness-detection minimum-interval 500 set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group trust bfd-liveness-detection multiplier 3 set protocols bgp group trust local-as 65000 set protocols bgp group untrust type internal set protocols bgp group untrust local-address 10.5.0.1 set protocols bgp group untrust export mnha-route-policy set protocols bgp group untrust neighbor 10.5.0.2 set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group untrust bfd-liveness-detection multiplier 3 set protocols bgp group untrust local-as 65000
以下章节显示了在网络中设置多节点高可用性设置所需的路由器上的配置片段。
路由器 (VMX-1)
set interfaces ge-0/0/2 description lan unit 0 family inet address 10.1.0.1/16 set interfaces ge-0/0/0 description ha unit 0 family inet address 10.2.0.1/16 set interfaces ge-0/0/1 description ha unit 0 family inet address 10.3.0.1/16 set interfaces lo0 description "loopback" unit 0 family inet address 10.111.0.1 primary preferred set routing-options autonomous-system 65000 set protocols bgp group mnha_r0 type internal set protocols bgp group mnha_r0 local-address 10.2.0.1 set protocols bgp group mnha_r0 neighbor 10.2.0.2 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0 local-as 65000 set protocols bgp group mnha_r0_b type internal set protocols bgp group mnha_r0_b local-address 10.3.0.1 set protocols bgp group mnha_r0_b neighbor 10.3.0.2 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0_b local-as 65000
路由器 (VMX-2)
set interfaces ge-0/0/0 description HA unit 0 family inet address 10.4.0.2/16 set interfaces ge-0/0/1 description HA unit 0 family inet address 10.5.0.2/16 set interfaces ge-0/0/2 description trust unit 0 family inet address 10.6.0.1/16 set interfaces lo0 description "loopback" unit 0 family inet address 10.111.0.2 primary preferred set routing-options autonomous-system 65000 set protocols bgp group mnha_r0 type internal set protocols bgp group mnha_r0 local-address 10.4.0.2 set protocols bgp group mnha_r0 neighbor 10.4.0.1 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0 bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0 local-as 65000 set protocols bgp group mnha_r0_b type internal set protocols bgp group mnha_r0_b local-address 10.5.0.2 set protocols bgp group mnha_r0_b neighbor 10.5.0.1 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection minimum-receive-interval 500 set protocols bgp group mnha_r0_b bfd-liveness-detection multiplier 3 set protocols bgp group mnha_r0_b local-as 65000
配置
分步程序
我们将在分步过程中展示 SRX-1 的配置。
下面的示例要求您在各个配置层级中进行导航。有关如何执行此作的说明,请参阅《CLI 用户指南》中的在配置模式下使用 CLI 编辑器。
-
配置接口。
[edit] user@host# set interfaces ge-0/0/3 description "trust" unit 0 family inet address 10.2.0.2/16 user@host# set interfaces ge-0/0/4 description "untrust" unit 0 family inet address 10.4.0.1/16 user@host# set interfaces ge-0/0/2 description "ha_link" unit 0 family inet address 10.22.0.1/24
我们使用 ge-0/0/3 和 ge-0/0/4 接口连接到上游和下游路由器,并使用 ge-0/0/2 接口设置 ICL。
-
配置环路接口。
[edit] user@host# set interfaces lo0 description "untrust" unit 0 family inet address 10.11.0.1/32
分配给环路接口的 IP 地址 (10.11.0.1) 将用作浮动 IP 地址。
使用环路接口可确保在任何给定点上,来自相邻路由器的流量都将被引导至浮动 IP 地址(即指向活动节点)。
-
配置安全区域,为区域分配接口,并为安全区域指定允许的系统服务。
[edit] user@host# set security zones security-zone untrust host-inbound-traffic system-services ike user@host# set security zones security-zone untrust host-inbound-traffic system-services ping user@host# set security zones security-zone untrust host-inbound-traffic protocols bfd user@host# set security zones security-zone untrust host-inbound-traffic protocols bgp user@host# set security zones security-zone untrust interfaces ge-0/0/4 user@host# set security zones security-zone untrust interfaces lo0.0 user@host# set security zones security-zone trust host-inbound-traffic system-services all user@host# set security zones security-zone trust host-inbound-traffic protocols all user@host# set security zones security-zone trust interfaces ge-0/0/3 user@host# set security zones security-zone halink host-inbound-traffic system-services ike user@host# set security zones security-zone halink host-inbound-traffic system-services ping user@host# set security zones security-zone halink host-inbound-traffic system-services high-availability user@host# set security zones security-zone halink host-inbound-traffic system-services ssh user@host# set security zones security-zone halink host-inbound-traffic protocols bfd user@host# set security zones security-zone halink host-inbound-traffic protocols bgp user@host# set security zones security-zone halink interfaces ge-0/0/2
将接口 ge-0/0/3 和 ge-0/0/4 分别分配信任和非信任区域。将 lo0.0 接口分配给 untrust 区域以通过公共 IP 网络进行连接。将接口 ge-0/0/2 分配给 halink 区域。使用此区域来设置 ICL。
-
配置路由选项。
[edit] user@host# set routing-options autonomous-system 65000 user@host# set routing-options static route 10.1.0.0/16 next-hop 10.2.0.1 user@host# set routing-options static route 10.6.0.0/16 next-hop 10.4.0.2 user@host# set routing-options static route 10.111.0.1 next-hop 10.2.0.1 user@host# set routing-options static route 10.111.0.2 next-hop 10.4.0.2
- 配置本地节点和对等节点详细信息,例如节点 ID、本地节点和对等节点的 lP 地址以及对等节点的接口。
[edit] user@host# set chassis high-availability local-id 1 user@host# set chassis high-availability local-id local-ip 10.22.0.1 user@host# set chassis high-availability peer-id 2 peer-ip 10.22.0.2 user@host# set chassis high-availability peer-id 2 interface ge-0/0/2.0 user@host# set chassis high-availability peer-id 2 vpn-profile IPSEC_VPN_ICL
您将使用 ge-0/0/2 接口与使用 ICL 的对等节点进行通信。
-
将 IPsec VPN 配置文件IPSEC_VPN_ICL连接到对等节点。
[edit] user@host# set chassis high-availability peer-id 2 vpn-profile IPSEC_VPN_ICL
您需要此配置在节点之间建立安全的 ICL 链路。
-
为对等节点配置双向转发检测 (BFD) 协议选项。
[edit] user@host# set chassis high-availability peer-id 2 liveness-detection minimum-interval 400 user@host# set chassis high-availability peer-id 2 liveness-detection multiplier 5
-
将对等节点 ID 2 与服务冗余组 0 (SRG0) 相关联。
[edit] user@host# set chassis high-availability services-redundancy-group 0 peer-id 2
-
配置服务冗余组 1 (SRG1)。
[edit] user@host# set chassis high-availability services-redundancy-group 0 peer-id 2 user@host# set chassis high-availability services-redundancy-group 1 deployment-type routing user@host# set chassis high-availability services-redundancy-group 1 peer-id 2
.
-
设置 SRG1 的活性确定参数。
[edit] user@host# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip 10.111.0.1 user@host# set chassis high-availability services-redundancy-group 1 activeness-probe dest-ip src-ip 10.11.0.1
使用浮动 IP 地址作为源 IP 地址 (10.11.0.1),将上游路由器的 IP 地址用作目标 IP 地址 (10.111.0.1),用于主动性确定探测。
您最多可以配置 64 个 IP 地址,用于 IP 监控和主动性探测。总共 64 个 IP 地址是 IPv4 和 IPv6 地址数量的总和)
-
为 SRG1 配置 BFD 监控参数,以检测网络故障。
[edit] user@host# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 src-ip 10.4.0.1 user@host# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 session-type singlehop user@host# set chassis high-availability services-redundancy-group 1 monitor bfd-liveliness 10.4.0.2 interface ge-0/0/4.0
-
配置主动性实施所需的活动信号路由。
[edit] user@host# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 user@host# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 user@host# set chassis high-availability services-redundancy-group 1 preemption user@host# set chassis high-availability services-redundancy-group 1 activeness-priority 200
您分配的活动信号路由 IP 地址将用于路由首选项通告。
注意:您必须在 policy-options 语句中指定活动信号路由以及 route-exists 策略。配置active-signal-routewithif-route-exists条件时,高可用性模块会将此路由添加到路由表中。 -
配置策略选项。
[edit] user@host# set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1 table inet.0 user@host# set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2 table inet.0 user@host# set policy-options policy-statement mnha-route-policy term 1 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 1 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 1 from condition active_route_exists user@host# set policy-options policy-statement mnha-route-policy term 1 then accept metric 10 user@host# set policy-options policy-statement mnha-route-policy term 2 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 2 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 2 from condition backup_route_exists user@host# set policy-options policy-statement mnha-route-policy term 2 then accept metric 20 user@host# set policy-options policy-statement mnha-route-policy term 3 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 3 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 3 then accept metric 30 user@host# set policy-options policy-statement mnha-route-policy term default then reject
使用路由匹配条件 (
if-route-exists) 配置活动信号路由 10.39.1.1。 -
配置安全策略。
[edit] user@host# set security policies default-policy permit-all
确保已根据网络要求配置安全策略。
-
为多节点高可用性定义互联网密钥交换 (IKE) 配置。IKE 配置定义用于建立安全连接的算法和密钥。
[edit] user@host# set security ike proposal MNHA_IKE_PROP description mnha_link_encr_tunnel user@host# set security ike proposal MNHA_IKE_PROP authentication-method pre-shared-keys user@host# set security ike proposal MNHA_IKE_PROP dh-group group14 user@host# set security ike proposal MNHA_IKE_PROP authentication-algorithm sha-256 user@host# set security ike proposal MNHA_IKE_PROP encryption-algorithm aes-256-cbc user@host# set security ike proposal MNHA_IKE_PROP lifetime-seconds 3600 user@host# set security ike policy MNHA_IKE_POL description mnha_link_encr_tunnel user@host# set security ike policy MNHA_IKE_POL proposals MNHA_IKE_PROP user@host# set security ike policy MNHA_IKE_POL pre-shared-key ascii-text "$ABC123" user@host# set security ike gateway MNHA_IKE_GW ike-policy MNHA_IKE_POL user@host# set security ike gateway MNHA_IKE_GW version v2-only
对于多节点高可用性功能,您必须将 IKE 版本配置为
v2-only -
指定 IPsec 提议协议和加密算法。指定 IPsec 选项以在两个参与设备之间创建 IPsec 隧道,以保护 VPN 通信。
[edit] user@host# set security ipsec proposal MNHA_IPSEC_PROP description mnha_link_encr_tunnel user@host# set security ipsec proposal MNHA_IPSEC_PROP protocol esp user@host# set security ipsec proposal MNHA_IPSEC_PROP encryption-algorithm aes-256-gcm user@host# set security ipsec proposal MNHA_IPSEC_PROP lifetime-seconds 3600 user@host# set security ipsec policy MNHA_IPSEC_POL description mnha_link_encr_tunnel user@host# set security ipsec policy MNHA_IPSEC_POL proposals MNHA_IPSEC_PROP user@host# set security ipsec vpn IPSEC_VPN_ICL ha-link-encryption user@host# set security ipsec vpn IPSEC_VPN_ICL ike gateway MNHA_IKE_GW user@host# set security ipsec vpn IPSEC_VPN_ICL ike ipsec-policy MNHA_IPSEC_POL
ha-link-encryption选项会对 ICL 进行加密,以确保节点之间的高可用性流量信息流的安全。在机箱高可用性配置中必须提及 vpn_profile IPSEC_VPN_ICL相同的 VPN 名称。
-
配置 BFD 对等会话选项并指定活跃度检测计时器。
[edit] user@host# set protocols bgp group trust type internal user@host# set protocols bgp group trust local-address 10.2.0.2 user@host# set protocols bgp group trust export mnha-route-policy user@host# set protocols bgp group trust neighbor 10.2.0.1 user@host# set protocols bgp group trust bfd-liveness-detection minimum-interval 500 user@host# set protocols bgp group trust bfd-liveness-detection minimum-receive-interval 500 user@host# set protocols bgp group trust bfd-liveness-detection multiplier 3 user@host# set protocols bgp group trust local-as 65000 user@host# set protocols bgp group untrust type internal user@host# set protocols bgp group untrust local-address 10.4.0.1 user@host# set protocols bgp group untrust export mnha-route-policy user@host# set protocols bgp group untrust neighbor 10.4.0.2 user@host# set protocols bgp group untrust bfd-liveness-detection minimum-interval 500 user@host# set protocols bgp group untrust bfd-liveness-detection minimum-receive-interval 500 user@host# set protocols bgp group untrust bfd-liveness-detection multiplier 3 user@host# set protocols bgp group untrust local-as
软件升级的配置选项(可选)
在多节点高可用性中,在软件升级期间,您可以通过更改路由来分流流量。使用以下步骤添加故障配置时的安装路由。在这里,流量仍可通过该节点,且接口保持开启。
查看 多节点高可用性中的软件升级, 了解详细信息。
-
为升级期间用于分流流量的路由创建专用的自定义虚拟路由器。
user@host# set routing-instances MNHA-signal-routes instance-type virtual-router
- 为 SRG0 配置 install route on failure 语句。
user@host# set chassis high-availability services-redundancy-group 0 install-on-failure-route 10.39.1.3 routing-instance MNHA-signal-routes user@host# set chassis high-availability services-redundancy-group 1 active-signal-route 10.39.1.1 routing-instance MNHA-signal-routes user@host# set chassis high-availability services-redundancy-group 1 backup-signal-route 10.39.1.2 routing-instance MNHA-signal-routes
当节点发生故障时,路由表将安装语句中提到的路由。
- 创建匹配的路由策略,该策略将路由称为具有属性的
route-exists条件。示例:以下配置片段显示,您已将 SRG0 的路由配置为 IP 地址为 10.39.1.3 作为故障时安装路由。路由策略语句将路由 10.39.1.3 作为
if-route-exists条件,策略语句将条件作为匹配术语之一引用。user@host# set policy-options condition active_route_exists if-route-exists address-family inet 10.39.1.1/32 user@host# set policy-options condition active_route_exists if-route-exists address-family inet table MNHA-signal-routes.inet.0 user@host# set policy-options condition backup_route_exists if-route-exists address-family inet 10.39.1.2/32 user@host# set policy-options condition backup_route_exists if-route-exists address-family inet table MNHA-signal-routes.inet.0 user@host# set policy-options condition failure_route_exists if-route-exists address-family inet 10.39.1.3/32 user@host# set policy-options condition failure_route_exists if-route-exists address-family inet table MNHA-signal-routes.inet.0
user@host# set policy-options policy-statement mnha-route-policy term 4 from protocol static user@host# set policy-options policy-statement mnha-route-policy term 4 from protocol direct user@host# set policy-options policy-statement mnha-route-policy term 4 from condition failure_route_exists user@host# set policy-options policy-statement mnha-route-policy term 4 then metric 100 user@host# set policy-options policy-statement mnha-route-policy term 4 then accept
结果 (SRX-1)
在配置模式下,输入以下命令以确认您的配置。
如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
user@host# show chassis high-availability
local-id 1 local-ip 10.22.0.1;
peer-id 2 {
peer-ip 10.22.0.2;
interface ge-0/0/2.0;
vpn-profile IPSEC_VPN_ICL;
liveness-detection {
minimum-interval 400;
multiplier 5;
}
}
services-redundancy-group 0 {
peer-id {
2;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
2;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.4.0.2 {
src-ip 10.4.0.1;
session-type singlehop;
interface ge-0/0/4.0;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
preemption;
activeness-priority 200;
}
[edit]
user@host# show security ike
proposal MNHA_IKE_PROP {
description mnha_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy MNHA_IKE_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IKE_PROP ;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway MNHA_IKE_GW {
ike-policy MNHA_IKE_POL ;
version v2-only;
}
[edit]
user@host# show security ipsec
proposal MNHA_IPSEC_PROP {
description mnha_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy MNHA_IPSEC_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IPSEC_PROP;
}
vpn IPSEC_VPN_ICL {
ha-link-encryption;
ike {
gateway MNHA_IKE_GW;
ipsec-policy MNHA_IPSEC_POL;
}
}
[edit]
user@host# show policy-options
policy-statement mnha-route-policy {
term 1 {
from {
protocol [ static direct ];
condition active_route_exists;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
protocol [ static direct ];
condition backup_route_exists;
}
then {
metric 20;
accept;
}
}
term 3 {
from protocol [ static direct ];
then {
metric 30;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@host# show routing-options
autonomous-system 65000;
static {
route 10.1.0.0/16 next-hop 10.2.0.1;
route 10.6.0.0/16 next-hop 10.4.0.2;
route 10.111.0.1/32 next-hop 10.2.0.1;
route 10.111.0.2/32 next-hop 10.4.0.2;
}
[edit]
user@host# show security zones security-zone
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/4.0;
lo0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/3.0;
}
}
security-zone halink {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show interfaces
ge-0/0/2 {
description ha_link;
unit 0 {
family inet {
address 10.22.0.1/24;
}
}
}
ge-0/0/3 {
description trust;
unit 0 {
family inet {
address 10.2.0.2/16;
}
}
}
ge-0/0/4 {
description untrust;
unit 0 {
family inet {
address 10.4.0.1/16;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
}
}
}
如果完成设备配置,请从配置模式进入。commit
结果 (SRX-2)
在配置模式下,输入以下命令以确认您的配置。如果输出未显示预期的配置,请重复此示例中的配置说明进行更正。
[edit]
user@host# show chassis high-availability
local-id 2 local-ip 10.22.0.2;
peer-id 1 {
peer-ip 10.22.0.1;
interface ge-0/0/2.0;
vpn-profile IPSEC_VPN_ICL;
liveness-detection {
minimum-interval 400;
multiplier 5;
}
}
services-redundancy-group 0 {
peer-id {
1;
}
}
services-redundancy-group 1 {
deployment-type routing;
peer-id {
1;
}
activeness-probe {
dest-ip {
10.111.0.1;
src-ip 10.11.0.1;
}
}
monitor {
bfd-liveliness 10.5.0.2 {
src-ip 10.5.0.1;
session-type singlehop;
interface ge-0/0/4.0;
}
}
active-signal-route {
10.39.1.1;
}
backup-signal-route {
10.39.1.2;
}
activeness-priority 1;
}
[edit]
user@host# show security ike
proposal MNHA_IKE_PROP {
description mnha_link_encr_tunnel;
authentication-method pre-shared-keys;
dh-group group14;
authentication-algorithm sha-256;
encryption-algorithm aes-256-cbc;
lifetime-seconds 3600;
}
policy MNHA_IKE_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IKE_PROP ;
pre-shared-key ascii-text "$ABC123"; ## SECRET-DATA
}
gateway MNHA_IKE_GW {
ike-policy MNHA_IKE_POL ;
version v2-only;
}
[edit]
user@host# show security ipsec
proposal MNHA_IPSEC_PROP {
description mnha_link_encr_tunnel;
protocol esp;
encryption-algorithm aes-256-gcm;
lifetime-seconds 3600;
}
policy MNHA_IPSEC_POL {
description mnha_link_encr_tunnel;
proposals MNHA_IPSEC_PROP;
}
vpn IPSEC_VPN_ICL {
ha-link-encryption;
ike {
gateway MNHA_IKE_GW;
ipsec-policy MNHA_IPSEC_POL;
}
}
[edit]
user@host# show policy-options
route-filter-list loopback {
10.11.0.0/24 orlonger;
}
route-filter-list ipsec {
10.6.0.0/16 orlonger;
}
policy-statement mnha-route-policy {
term 1 {
from {
protocol [ static direct ];
condition active_route_exists;
}
then {
metric 10;
accept;
}
}
term 2 {
from {
protocol [ static direct ];
condition backup_route_exists;
}
then {
metric 20;
accept;
}
}
term 3 {
from protocol [ static direct ];
then {
metric 35;
accept;
}
}
term default {
then reject;
}
}
condition active_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.1/32;
table inet.0;
}
}
}
}
condition backup_route_exists {
if-route-exists {
address-family {
inet {
10.39.1.2/32;
table inet.0;
}
}
}
}
[edit]
user@host# show routing-options
autonomous-system 65000;
static {
route 10.1.0.0/16 next-hop 10.3.0.1;
route 10.6.0.0/16 next-hop 10.5.0.2;
route 10.111.0.1/32 next-hop 10.3.0.1;
route 10.111.0.2/32 next-hop 10.5.0.2;
}
[edit]
user@host# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/4.0;
lo0.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/3.0;
}
}
security-zone halink {
host-inbound-traffic {
system-services {
ike;
ping;
high-availability;
ssh;
}
protocols {
bfd;
bgp;
}
}
interfaces {
ge-0/0/2.0;
}
}
[edit]
user@host# show interfaces
root@10.52.45.4# show interfaces
ge-0/0/2 {
description ha_link;
unit 0 {
family inet {
address 10.22.0.2/24;
}
}
}
ge-0/0/3 {
description trust;
unit 0 {
family inet {
address 10.3.0.2/16;
}
}
}
ge-0/0/4 {
description untrust;
unit 0 {
family inet {
address 10.5.0.1/16;
}
}
}
lo0 {
description untrust;
unit 0 {
family inet {
address 10.11.0.1/32;
}
}
}
如果完成设备配置,请从配置模式进入。commit
user@host# commit warning: High Availability Mode changed, please reboot the device to avoid undesirable behavior commit complete
验证
确认配置工作正常。
- 检查多节点高可用性详细信息
- 检查多节点高可用性对等节点状态
- 检查多节点高可用性服务冗余组
- 验证故障切换前后的多节点高可用性状态
- 验证机箱间链路 (ICL) 加密状态
- 验证链路加密隧道统计信息
- 验证机箱间链路活动对等方
检查多节点高可用性详细信息
目的
查看并验证安全设备上配置的多节点高可用性设置的详细信息。
行动
在作模式下,运行以下命令:
在 SRX-1 上
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 1
Local-IP: 10.22.0.1
HA Peer Information:
Peer Id: 2 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 2
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: READY
在 SRX-2 上
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
意义
从命令输出中验证以下详细信息:
-
本地节点和对等节点详细信息,例如 IP 地址和 ID。
-
该字段
Encrypted: YES表示流量已受到保护。 -
该字段
Deployment Type: ROUTING表示第 3 层模式配置,即网络两端都有路由器。 -
该字段
Services Redundancy Group: 1指示该节点上 SRG1 的状态(ACTIVE 或 BACKUP)。
检查多节点高可用性对等节点状态
目的
查看并验证对等节点详细信息。
行动
在作模式下,运行以下命令:
SRX-1
user@host> user@host> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 2 IP address: 10.22.0.2 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.1
Internal Peer-IP: 180.100.1.2
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 4
SRG Status Ack 4 3
Attribute Msg 4 2
Attribute Ack 2 2
SRX-2
user@host> show chassis high-availability peer-info
HA Peer Information:
Peer-ID: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Internal Interface: st0.16000
Internal Local-IP: 180.100.1.2
Internal Peer-IP: 180.100.1.1
Internal Routing-instance: __juniper_private1__
Packet Statistics:
Receive Error : 0 Send Error : 0
Packet-type Sent Received
SRG Status Msg 4 3
SRG Status Ack 3 4
Attribute Msg 3 2
Attribute Ack 2 2
意义
从命令输出中验证以下详细信息:
-
对等节点详细信息,例如使用的接口、IP 地址和 ID
-
加密状态、连接状态和冷同步状态
-
整个节点的数据包统计信息。
检查多节点高可用性服务冗余组
目的
验证 SRG 是否已配置且工作正常。
行动
在作模式下,运行以下命令:
对于 SRG0:
user@host> show chassis high-availability services-redundancy-group 0
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 2
对于 SRG1:
user@host> show chassis high-availability services-redundancy-group 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 200
Preemption: ENABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 2
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: READY
Signal Route Info:
Active Signal Route:
IP: 10.39.1.1
Routing Instance: default
Status: INSTALLED
Backup Signal Route:
IP: 10.39.1.2
Routing Instance: default
Status: NOT INSTALLED
Split-brain Prevention Probe Info:
DST-IP: 10.111.0.1
SRC-IP: 10.11.0.1
Routing Instance: default
Status: NOT RUNNING
Result: N/A Reason: N/A
BFD Monitoring:
Status: UP
SRC-IP: 10.4.0.1 DST-IP: 10.4.0.2
Routing Instance: default
Type: SINGLE-HOP
IFL Name: ge-0/0/4.0
State: UP
意义
从命令输出中验证以下详细信息:
-
对等节点详细信息,例如部署类型、状态以及活动和备份信号路由。
-
虚拟 IP IP 地址和虚拟 MAC 地址等信息。
-
IP 监控和 BFD 监控状态。
验证故障切换前后的多节点高可用性状态
目的
在多节点高可用性设置中检查故障切换前后节点状态的变化。
行动
要检查备份节点 (SRX-2) 上的多节点高可用性状态,请在作模式下运行以下命令:
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: UP
Cold Sync Status: COMPLETE
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: BACKUP
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: COMPLETE
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : ACTIVE
Health Status: HEALTHY
Failover Readiness: N/A
在该 Services Redundancy Group: 1 部分下,您可以看到该 Status: BACKUP 字段。此字段值表示 SRG 1 的状态为备份。
在活动节点(SRX-1 设备)上启动故障切换,然后在备份节点(SRX-2 设备)上再次运行命令。
user@host> show chassis high-availability information
Node failure codes:
HW Hardware monitoring LB Loopback monitoring
MB Mbuf monitoring SP SPU monitoring
CS Cold Sync monitoring SU Software Upgrade
Node Status: ONLINE
Local-id: 2
Local-IP: 10.22.0.2
HA Peer Information:
Peer Id: 1 IP address: 10.22.0.1 Interface: ge-0/0/2.0
Routing Instance: default
Encrypted: YES Conn State: DOWN
Cold Sync Status: IN PROGRESS
Services Redundancy Group: 0
Current State: ONLINE
Peer Information:
Peer Id: 1
SRG failure event codes:
BF BFD monitoring
IP IP monitoring
IF Interface monitoring
CP Control Plane monitoring
Services Redundancy Group: 1
Deployment Type: ROUTING
Status: ACTIVE
Activeness Priority: 1
Preemption: DISABLED
Process Packet In Backup State: NO
Control Plane State: READY
System Integrity Check: N/A
Failure Events: NONE
Peer Information:
Peer Id: 1
Status : BACKUP
Health Status: HEALTHY
Failover Readiness: READY
请注意,在该 Services Redundancy Group: 1 部分下,SRG1 的状态已从 BACKUP 更改为 ACTIVE。
您还可以在该Peer Information部分下查看对等节点详细信息。输出显示对等方的状态为 BACKUP。
验证机箱间链路 (ICL) 加密状态
目的
验证机箱间链路 (ICL) 状态。
行动
在作模式下,运行以下命令:
user@host> show security ipsec security-associations ha-link-encryption detail
ID: 495001 Virtual-system: root, VPN Name: IPSEC_VPN_ICL
Local Gateway: 10.22.0.1, Remote Gateway: 10.22.0.2
Traffic Selector Name: __IPSEC_VPN_ICL__multi_node__
Local Identity: ipv4(180.100.1.1-180.100.1.1)
Remote Identity: ipv4(180.100.1.2-180.100.1.2)
TS Type: traffic-selector
Version: IKEv2
PFS group: N/A
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.16000, Tunnel MTU: 0, Policy-name: MNHA_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
HA Link Encryption Mode: Multi-Node
Location: FPC -, PIC -, KMD-Instance -
Anchorship: Thread -
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x0005a7ec, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3597 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2900 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 4294966273
Direction: outbound, SPI: 0x000a2aba, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3597 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2900 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: aes256-gcm, Encryption: aes-gcm (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-immediately
Location: FPC 0, PIC 0, KMD-Instance 0
Anchorship: Thread 0
IKE SA Index: 4294966273
意义
命令输出提供以下信息:
-
本地网关和远程网关详细信息。
-
PIC 中每个线程的 IPsec SA 对。
-
高可用性链路加密模式(如下行所示):
HA Link Encryption Mode: Multi-Node -
使用的身份验证和加密算法
注意:命令输出中显示的 IP 范围 (180.100.1.x) 用作 ICL IPsec 流量选择器。系统会动态分配此 IP 范围,因此不能更改或修改它。此外,BFD(双向转发检测)将自动启用,以覆盖更广泛的 180.x.x.x IP 范围。
验证链路加密隧道统计信息
目的
验证活动节点和备份节点上的链路加密隧道统计信息。
行动
在作模式下,运行以下命令:
user@host> show security ipsec statistics ha-link-encryption ESP Statistics: Encrypted bytes: 984248 Decrypted bytes: 462519 Encrypted packets: 9067 Decrypted packets: 8797 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
意义
如果看到 VPN 中有数据包丢失的问题,可以多次运行命令 show security ipsec statistics ha-link-encryption 以验证加密和解密数据包计数器是否在递增。还应检查其他错误计数器是否也在递增。
使用此命令清除 clear security ipsec security-associations ha-link-encryption 所有 IPsec 统计信息。
验证机箱间链路活动对等方
目的
仅查看 ICL 活动对等方,不查看常规 IKE 活动对等方。
行动
在作模式下,运行以下命令:
SRX-1
user@host> show security ike active-peer ha-link-encryption
Remote Address Port Peer IKE-ID AAA username Assigned IP
10.22.0.2 500 10.22.0.2 not available 0.0.0.0
SRX-2
user@host> show security ike active-peer ha-link-encryption Remote Address Port Peer IKE-ID AAA username Assigned IP 10.22.0.1 500 10.22.0.1 not available 0.0.0.0
意义
命令输出仅显示 ICL 的活动对等方,以及活动对等方正在使用的对等方地址和端口等详细信息。
