Nesta página
Exemplo: Configure o perfil de chaves estáticas para VPN de site para site
Exemplo: Configure o perfil de chaves estáticas para AutoVPN
Configure o perfil chave do gerente de chaves quânticas para o Junos Key Manager
Exemplo: Configure o perfil chave do gerente de chave quântica para VPN IPsec de site para site
VPN IPsec com segurança quântica
Saiba como usar e configurar os mecanismos de recuperação de chave fora de banda no processo IKED para negociar com IKE e SAs IPsec seguros quânticos.
Visão geral da segurança quântica
O canal de comunicação IPsec conta com o protocolo Internet Key Exchange (IKE). O IKE mantém parâmetros de segurança para proteger o tráfego de dados. Os parâmetros de segurança incluem algoritmos de criptografia e autenticação e chaves associadas.
Os protocolos de segurança contam com algoritmos criptográficos assimétricos, como Diffie Hellman (DH) ou Diffie Hellman da Curva Elíptica (ECDH) para estabelecer que as chaves são vulneráveis a ataques.
Para evitar ataques de segurança, o RFC8784 introduz um método fora de banda. O método fora de banda adiciona uma chave secreta no iniciador e no respondente. A chave secreta é a chave pré-compartilhada pós-quântica (PPK).
-
Você pode usar o PPK, além do método de autenticação no IKEv2.
-
O PPK oferece resistência quântica a qualquer SAs infantil em SAs IPsec negociados iniciais e quaisquer SAs IPsec re-iked subsequentes.
-
Com a chave de PPK e autenticação por pares, o iniciador e o respondente podem detectar uma incompatibilidade de chave.
Visão geral do Junos Key Manager
Você pode usar o Junos Key Manager (JKM) para configurar as chaves estáticas ou as chaves dinâmicas para proteger o plano de dados e o plano de controle.
O processo JKM funciona como uma loja-chave e um proxy entre o cliente ou o aplicativo de criptografia. O cliente ou aplicativo de criptografia requer uma chave para estabelecer uma sessão de segurança quântica criptografada e autenticada com peer ou aplicativo. O cofre quântico usa o mecanismo de recuperação de chave fora da banda que permite que dois pares tenham a chave. Diferentes mecanismos fora de banda terão diferentes protocolos ou métodos para se comunicar. O JKM oferece uma interface uniforme comum para que os aplicativos de cliente ou cripto se comuniquem.
Mecanismo de recuperação de chave
Dois mecanismos de recuperação de chave fora de banda no processo IKED para negociar com IKE e SAs IPsec seguros quânticos.
-
Chave estática — com perfis chave estáticos, você pode configurar uma ID de chave estática e uma chave correspondente. A mesma ID e chave chave estática é gerada sempre que uma solicitação à JKM é gerada em um perfil chave estático.
-
Gerente de chave quântica — com perfis chave de gerenciamento de chave quântica, você pode acessar os dispositivos de distribuição de chave quântica (QKD) e a Rede Quântica. A Rede Quântica gera e troca chaves quânticas entre pares. Gera uma ID e uma chave chave diferentes todas as vezes solicitadas à JKM em um perfil chave de gerente de chave quântica.
Use o perfil chave para VPN IPsec com segurança quântica
Com perfis chave estáticos, você pode configurar uma ID de chave estática e uma chave correspondente. Para estabelecer os SAs IPsec com segurança quântica, use o perfil chave estático como perfil de chave pré-compartilhada (PPK) pós-quântica na configuração IPsec-VPN. Usa a mesma chave e a ID chave para re-autenticar a SA IKE existente.
Com perfis de perfil de gerente de chave quântica, para acessar as Redes Quânticas, você precisa de acesso aos dispositivos QKD. A Rede Quântica gera e troca chaves quânticas entre pares. Você pode configurar todos os parâmetros necessários, como O ID SAE local, URL para o dispositivo QKD e assim por diante. Para estabelecer SAs IPsec, use o perfil chave do gerente de chave quântica como perfil de chave pré-compartilhada (PPK) pós-quântica na configuração de VPN IPsec. Usa uma chave diferente e uma ID chave para re-autenticar a SA IKE existente.
Distribuição de chave quântica
A distribuição de chave quântica (QKD) é um método de distribuição de chave segura que usa o quantum. As redes usam canais quânticos para gerar a mesma chave em ambas as extremidades e monitorar o canal quântico entre os pares. Essas chaves são dinâmicas, protegem o plano de dados e o plano de controle.
Entidade de gerenciamento chave (KME) é o termo que usamos para consultar os dispositivos QKD na camada de gerenciamento ou controle. Os dispositivos QKD se conectam entre si por meio de sua rede quântica ou QKD. Os KMEs se conectam pela rede pública através dos canais seguros para a troca de mensagens de controle. Os aplicativos, Secure Application Entity (SAEs) e dispositivos interagem com KMEs através dos canais seguros de acordo com a especificação ETSI. O HTTPS combina com a autenticação de TLS mútua e permite operações seguras na rede QKD.
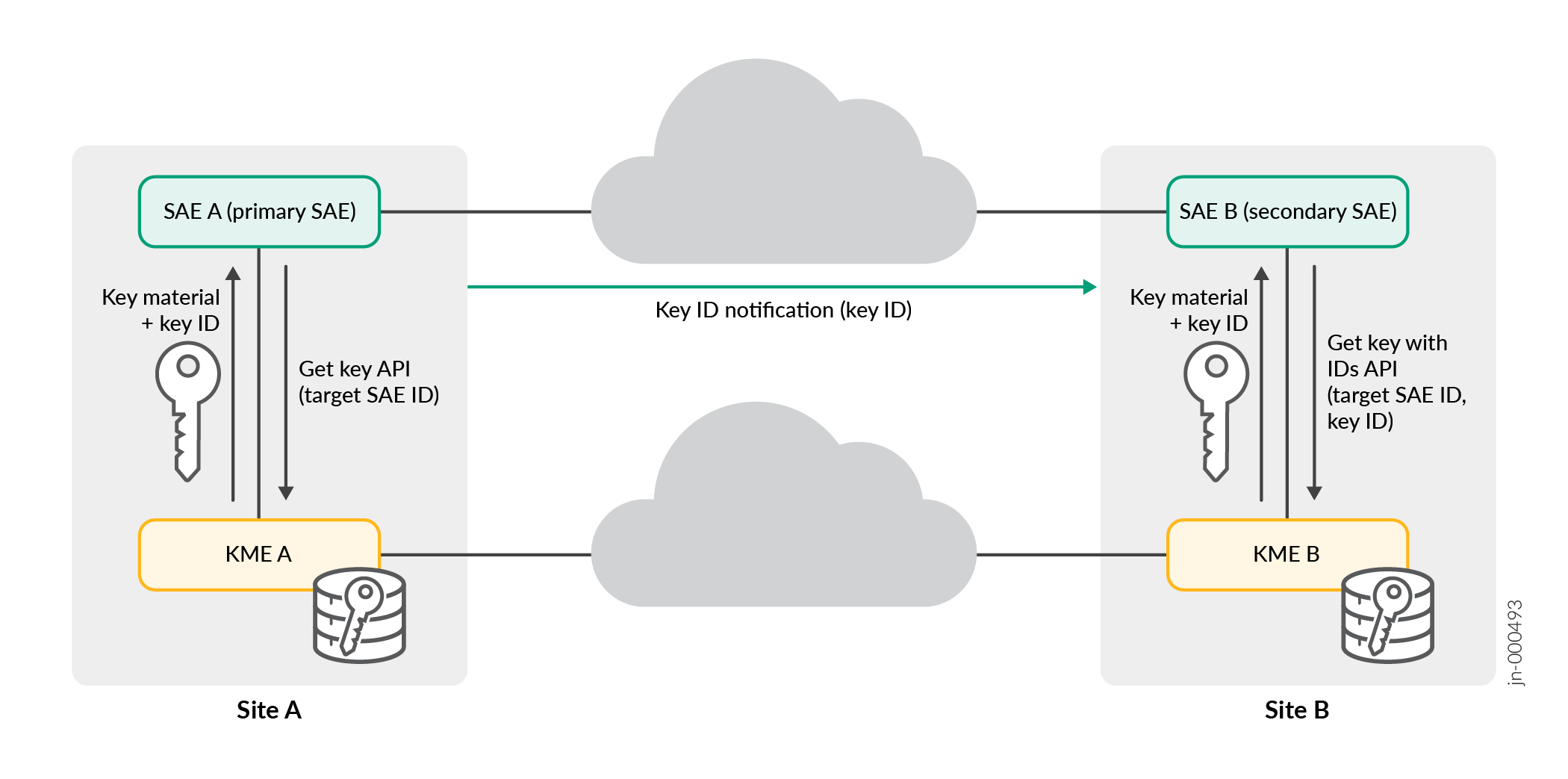
Figura 1 Nos descreve como os dois dispositivos interagem com seus dispositivos QKD correspondentes para estabelecer uma sessão de segurança quântica
-
A função SAE A é primária. O SAE A atua como o iniciador para estabelecer uma sessão de segurança quântica com SAE B.
-
A função SAE B é secundária. O SAE B atua como o respondente.
-
O SAE A solicita o KME A através da API chave get para gerar e compartilhar uma nova chave quântica com SAE B com O ID SAE alvo.
-
O KME A realiza a operação e responde ao SAE A com o ID chave gerado e o material chave.
-
O KME B recebe o material chave e a chave de ID gerada na rede QKD.
-
O SAE A inicia uma sessão segura com SAE B usando diretamente a mesma chave e ID chave.
-
Uma troca de mensagens estabelece uma sessão segura com o SAE B.
-
O SAE A envia o ID chave em texto simples ou criptografado para a chave quântica correspondente que é usada para proteger a sessão com SAE B.
-
Assim que o SAE B recebe o ID chave, o SAE B entra em contato com o KME B através da chave Get com IDs API para obter a chave quântica correspondente para a ID chave e ID sae alvo ou SAE A.
-
Após o SAE B receber a chave, uma sessão totalmente protegida por quantum estabelece entre SAE A e SAE B.
Configure o perfil chave estático para o Junos Key Manager
Este exemplo mostra como configurar o perfil chave estático para o gerenciador chave do Junos. Configure as chaves estáticas em gateways interessados e não precise compartilhar chaves estáticas pela Internet para estabelecer o túnel IPsec.
Requisitos
-
Requisitos de hardware — Juniper Networks® SRX1500 firewall e modelos de dispositivos de maior número ou firewall virtual vSRX da Juniper Networks® (vSRX3.0).
-
Requisitos de software — Versão do Junos OS 22.4R1 ou posterior com JUNOS ike e JUNOS Key Manager pacotes.
Visão geral
Com perfis baseados em chave estática, você precisa configurar uma ID de chave estática e uma chave correspondente. Se você usar o perfil chave estático no objeto VPN IPsec, quando a re-autenticação para IKE SA existente a mesma chave e ID chave são usadas.
Configuração
Configure o perfil chave estático para o gerente-chave do Junos.
user@host# set security key-manager profiles km_profile_1 static key-id ascii-text test-ppk-id user@host# set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
Verificação
Propósito
Verifique o perfil e as chaves da chave estática.
Ação
Desde o request security key-manager profiles get profile-keys name km_profile_1 modo operacional, entre para ver o perfil e as chaves da chave estática.
user@host> request security key-manager profiles get profile-keys name km_profile_1
- Response:
- Status: SUCCESS
- Name: km_profile_1
- Type: Static
- Key-size: 280 bits
- Key-count: 1
- Key-ids:
- test-ppk-id
- Keys:
- 716a776264697031333975356d637938396d32387063676f77657265666e6b6a736467Do modo operacional, digite show security key-manager profiles name km_profile_1 detail para visualizar os detalhes estáticos do perfil da chave.
user@host> show security key-manager profiles name km_profile_1 detail
Name: km_profile_1, Index: 1, Type: Static
Configured-at: 10.09.23 (20:16:34)
Time-elapsed: 0 hrs 2 mins 21 secs
Request stats:
Received: 1
In-progress: 0
Success: 1
Failed: 0
Significado
Ele request security key-manager profiles get profile-keys name km_profile_1 exibe o status, nome de perfil de chave estática, tipo, tamanho da chave, ID da chave e chaves.
Ele show security key-manager profiles name km_profile_1 detail exibe o nome, tipo e status de solicitação de chave estática.
Exemplo: Configure o perfil de chaves estáticas para VPN de site para site
Use este exemplo de configuração para configurar o perfil chave estático. Você pode usar o perfil de chave estática para proteger uma infraestrutura de VPN IPsec de site para local.
Você pode proteger uma infraestrutura de VPN IPsec de site para local configurando o perfil chave estático.
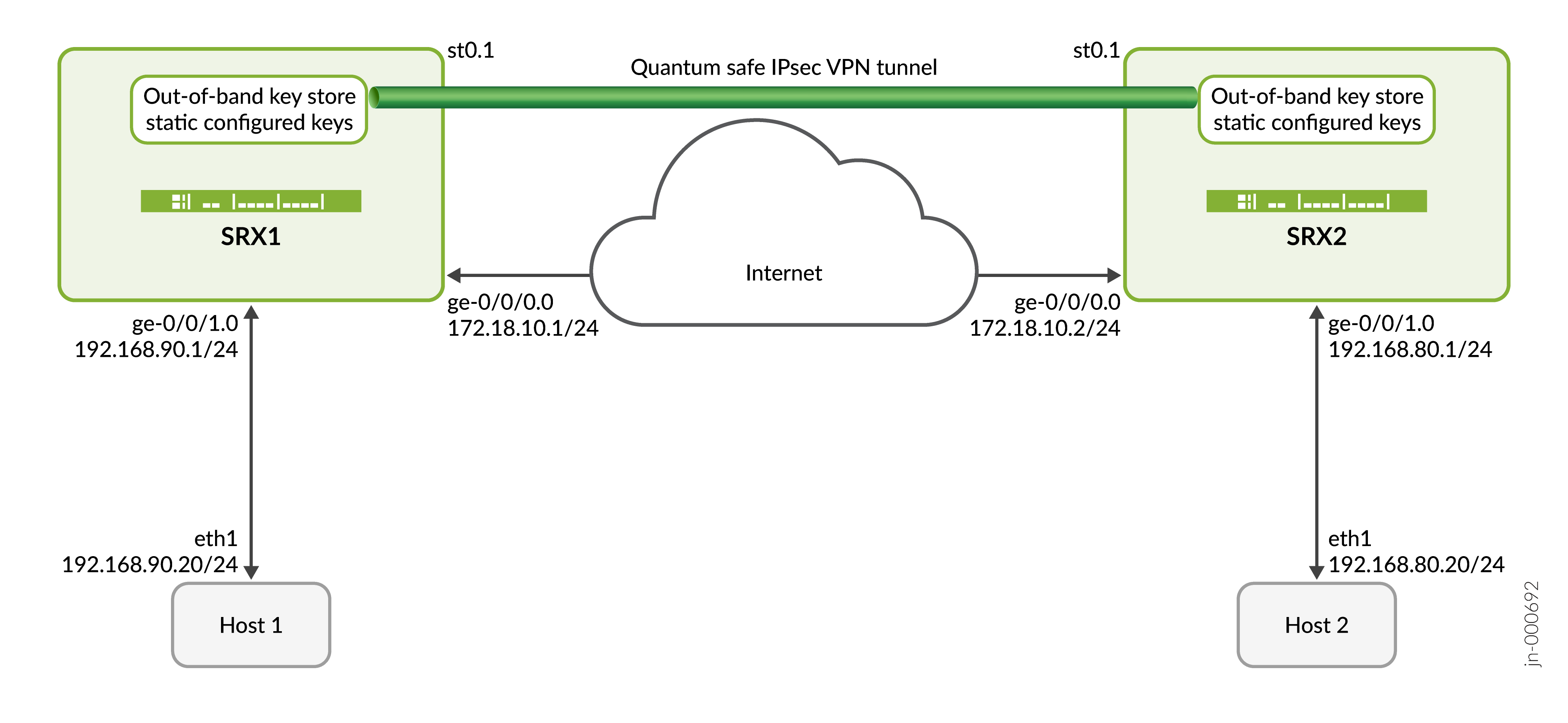
Neste exemplo de configuração, os dispositivos SRX1 e SRX2 usam o perfil chave estático para buscar as chaves QKD na VPN IPsec. As chaves QKD ajudam a enviar tráfego com segurança pela Internet.
|
Tempo de leitura |
Menos de uma hora |
|
Tempo de configuração |
Menos de uma hora |
- Pré-requisitos de exemplo
- Antes de começar
- Visão geral funcional
- Visão geral da topologia
- Ilustração de topologia
- Configuração passo a passo em dispositivos de firewall da Série SRX
- Verificação
- Apêndice 1: Definir comandos em todos os dispositivos
- Apêndice 2: Mostrar saída de configuração no DUT
Pré-requisitos de exemplo
|
Requisitos de hardware |
Juniper Networks® SRX1500 firewall ou modelos de dispositivos de maior número ou firewall virtual vSRX da Juniper Networks® (vSRX3.0) |
|
Requisitos de software |
Versão Junos OS 22.4R1 ou posterior. |
Antes de começar
|
Benefícios |
|
|
Recursos úteis |
|
|
Saiba mais |
|
|
Experiência prática |
|
|
Saiba mais |
Visão geral funcional
| IPsec VPN |
Implante uma topologia de VPN IPsec onde os dispositivos de firewall da Série SRX são conectados por túneis VPN que enviam tráfego pelo túnel VPN IPsec. Os túneis VPN são configurados posteriormente para usar chaves quânticas, tornando-os túneis VPN com segurança quântica. |
| Gateway IKE |
Estabeleça uma conexão segura, o gateway IKE usa a política de IKE para se limitar ao grupo configurado de CAs (ca-profiles) enquanto valida o certificado. |
| Propostas | |
| Proposta de IKE |
Defina os algoritmos e as chaves usadas para estabelecer a conexão IKE segura com o gateway de segurança por pares. O IKE cria os SAs dinâmicos e os negocia para o IPsec. |
| Proposta de IPsec |
Liste protocolos, algoritmos e serviços de segurança a serem negociados com o peer IPsec remoto. |
| Políticas | |
| Política de IKE |
Definir uma combinação de parâmetros de segurança (propostas de IKE) a serem usados durante a negociação da IKE. |
| Política de IPsec |
Contenha regras e políticas de segurança para permitir o tráfego de VPN em grupo entre as zonas especificadas. |
| Política de segurança |
Permite que você selecione o tipo de tráfego de dados para proteger por meio dos SAs IPsec.
|
|
Perfis |
|
|
Perfil chave |
Definir como os dispositivos de firewall da Série SRX usam o perfil chave estático para buscar as chaves QKD na VPN IPsec para enviar tráfego com segurança pela Internet.
|
| Perfil do PPK |
Indique qual perfil chave usar para estabelecer SAs de IKE ou IPsec com segurança quântica fazendo referência ao perfil chave no gateway IKE. |
| Certificados | |
| Certificado de CA | Verifique a identidade dos dispositivos e autenticar o link de comunicação entre eles. |
| Certificado local | Gere o PKI e inscreva-o com o certificado ca para verificação. |
| Certificado KME | Certificado de terceiros gerado por fornecedor |
| Zonas de segurança | |
| confiança |
Segmento de rede na zona de host |
| desconfiança |
Segmento de rede na zona de servidor de destino |
| VPN |
Segmento de rede pelo qual os dispositivos SRX1 e SRX2 interagem. |
|
Tarefas primárias de verificação |
Verifique se os SAs IKE e IPsec estabelecidos são seguros em quantum. |
Visão geral da topologia
Neste exemplo, o SRX1 inicia a negociação de túneis IPsec com segurança quântica com SRX2 usando chave estática configurada para CLI. O SRX2 responde a essa solicitação verificando a identidade do SRX1 junto com a chave e estabelece uma VPN IPsec com segurança quântica. Uma vez estabelecido o túnel, o tráfego de dados entre o Host1 e o Host2 fica seguro usando o túnel IPsec estabelecido.
|
Nome de host |
Função |
Função |
|---|---|---|
| SRX1 |
Firewall da Série SRX capaz de estabelecer túneis IPsec |
Inicia a negociação de IKE ou IPsec SA e estabelece túneis de IPsec com segurança quântica com SRX2 usando chave estática configurada no SRX1. |
| SRX2 | Firewall da Série SRX capaz de estabelecer túneis IPsec | Responde à negociação IKE ou IPsec SA iniciada pelo SRX1 e estabelece túneis IPsec com segurança quântica usando chave estática configurada no SRX2. |
| Host1 | Um host dentro da zona confiável ou lado LAN do SRX1 | Inicia o tráfego do lado do cliente em direção ao Host2 |
| Host2 | Um host dentro da zona confiável ou lado LAN do SRX2 | Responde ao tráfego do lado cliente do Host1 |
Ilustração de topologia
Configuração passo a passo em dispositivos de firewall da Série SRX
Para ver configurações de amostra completas no DUT, veja:
Essa configuração é aplicável apenas para dispositivos SRX1 e SRX2. Você deve fazer as alterações de configuração específicas do dispositivo apropriadas.
-
Configure as interfaces.
[edit interfaces] user@srx# set ge-0/0/0 unit 0 family inet address 172.18.10.1/24 user@srx# set st0 unit 1 family inet user@srx# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24
-
Configure um perfil chave do tipo estático com um key-id e uma chave correspondente.
[edit security key-manager profiles] user@srx# set km_profile_1 static key-id ascii-text test-key-id user@srx# set km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
-
Configure as zonas de segurança.
[edit security zones] user@srx# set security-zone untrust host-inbound-traffic system-services ike user@srx# set security-zone untrust interfaces ge-0/0/0.0 user@srx# set security-zone vpn interfaces st0.1 user@srx# set security-zone trust host-inbound-traffic system-services ping user@srx# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@srx# set from-zone trust to-zone vpn policy vpn_out match source-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match application any user@srx# set from-zone trust to-zone vpn policy vpn_out then permit user@srx# set from-zone vpn to-zone trust policy vpn_in match source-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match application any user@srx# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security ike proposal] user@srx# set IKE_PROP authentication-method pre-shared-keys user@srx# set IKE_PROP dh-group group14 user@srx# set IKE_PROP authentication-algorithm sha-256 user@srx# set IKE_PROP encryption-algorithm aes-256-cbc user@srx# set IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@srx# set IKE_POL proposals IKE_PROP user@srx# set IKE_POL pre-shared-key ascii-text ipsec-test
[edit security ike gateway] user@srx# set IKE_GW ike-policy IKE_POL user@srx# set IKE_GW address 172.18.10.2 user@srx# set IKE_GW external-interface ge-0/0/0.0 user@srx# set IKE_GW local-address 172.18.10.1 user@srx# set IKE_GW version v2-only user@srx# set IKE_GW ppk-profile km_profile_1
[edit security ipsec proposal] user@srx# set IPSEC_PROP protocol esp user@srx# set IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx# set IPSEC_PROP encryption-algorithm aes-256-cbc user@srx# set IPSEC_PROP lifetime-seconds 2400
[edit security ipsec policy] user@srx# set IPSEC_POL proposals IPSEC_PROP
[edit security ipsec vpn] user@srx# set IPSEC_VPN bind-interface st0.1 user@srx# set IPSEC_VPN ike gateway IKE_GW user@srx# set IPSEC_VPN ike ipsec-policy IPSEC_POL user@srx# set IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@srx# set IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 user@srx# set IPSEC_VPN establish-tunnels immediately
Verificação
Esta seção fornece uma lista de comandos de exibição que você pode usar para verificar o recurso neste exemplo.
|
Comando |
Tarefa de verificação |
|---|---|
|
mostrar segurança ike detalhes de associações de segurança |
|
|
mostrar detalhes das associações de segurança ipsec de segurança |
|
|
mostrar estatísticas de segurança ipsec |
Verifique as estatísticas de criptografia e descriptografia do IPsec. |
|
mostrar detalhes dos perfis dos principais gerentes de segurança |
|
|
ping 192.168.80.20 fonte 192.168.90.20 contagem 4 |
- Verifique os SAs de IKE
- Verifique os SAs IPsec
- Verifique as estatísticas do IPsec
- Verificar o perfil do gerente-chave
- Ping do HOST 1 para HOST 2
Verifique os SAs de IKE
Propósito
Verifique os SAs de IKE
Ação
Desde o modo operacional, entre no show security ike security-associations detail comando para ver os SAs IKE.
user@srx> show security ike security-associations detail IKE peer 172.18.10.2, Index 1, Gateway Name: IKE_GW
Role: Initiator, State: UP
Initiator cookie: dee592254e808a2b, Responder cookie: 51f6b1d4a8618332 Exchange type: IKEv2, Authentication method: Pre-shared-keys
Local gateway interface: ge-0/0/2.0 Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 1286 seconds Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576 SRG ID: 0
Remote Access Client Info: Unknown Client Peer ike-id: 172.18.10.2
AAA assigned IP: 0.0.0.0
PPK-profile: km_profile_1 Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc Pseudo random function: hmac-sha256 Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 1058
Output bytes : 1074
Input packets: 4
Output packets: 4
Input fragmented packets: 0
Output fragmented packets: 0
IPSec security associations: 4 created, 1 deleted Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500002
Negotiation type: Quick mode, Role: Initiator, Message ID: 0 Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: 172.18.10.1
Remote identity: 172.18.10.2 Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 1
Response In : 0 Response Out : 1
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0 Res Verify SA Fail : 0
Res Verify DH Group Fail: 0 Res Verify TS Fail : 0
Significado
Os Role: Initiator, State: UPcampos e IPSec security associations: 4 createdPPK-profile: km_profile_1 Optional: NoFlags: IKE SA is created os campos mostram que os SAs IKE foram criados com sucesso.
Verifique os SAs IPsec
Propósito
Verifique os SAs IPsec
Ação
Do modo operacional, entre no show security ipsec security-associations detail comando para ver os SAs IPsec.
user@srx> show security ipsec security-associations detail ID: 500002 Virtual-system: root, VPN Name: IPSEC_VPN Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2 Traffic Selector Name: ts1 Local Identity: ipv4(192.168.90.0-192.168.90.255) Remote Identity: ipv4(192.168.80.0-192.168.80.255) TS Type: traffic-selector Version: IKEv2 Quantum Secured: Yes PFS group: N/A SRG ID: 0 DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: IPSEC_POL Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0 Multi-sa, Configured SAs# 0, Negotiated SAs#: 0 Tunnel events: Thu Mar 30 2023 23:43:42: IPsec SA negotiation succeeds (1 times) Location: FPC 0, PIC 0, KMD-Instance 0 Anchorship: Thread 1 Distribution-Profile: default-profile Direction: inbound, SPI: 0x983a0221, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1330 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 662 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1 Direction: outbound, SPI: 0x4112746b, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1330 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 662 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1
Significado
Os Version: IKEv2 Quantum Secured: Yes campos e os campos tunnel-establishment: establish-tunnels-immediately IKE SA Index: 1 mostram que os SAs IPsec foram criados com sucesso.
A saída de amostra confirma os SAs IPsec.
Verifique as estatísticas do IPsec
Propósito
Verifique as estatísticas do IPsec.
Ação
Do modo operacional, entre no show security ipsec statistics comando para ver as estatísticas do IPsec.
user@srx> show security ipsec statistics ESP Statistics: Encrypted bytes: 624 Decrypted bytes: 624 Encrypted packets: 4 Decrypted packets: 4 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Os ESP Statistics campos e os campos AH Statistics mostram as estatísticas do IPsec.
Verificar o perfil do gerente-chave
Propósito
Verifique o perfil do gerente chave.
Ação
Do modo operacional, digite os show security key-manager profiles detalhes para visualizar o perfil do gerente chave.
user@srx> show security key-manager profiles detail Name: km_profile_1, Index: 1, Type: Static Configured-at: 30.03.23 (23:22:43) Time-elapsed: 1 hrs 16 mins 3 secs Request stats: Received: 1 In-progress: 0 Success: 1 Failed: 0
Significado
Os Name: km_profile_1 campos e os campos Type: Static mostram o perfil chave do gerente.
Ping do HOST 1 para HOST 2
Propósito
Verifique a conectividade do HOST 1 ao HOST 2.
Ação
A partir do modo operacional, entre na contagem de ping 192.168.80.20 fonte 192.168.90.20 4 para visualizar a conectividade do HOST 1 ao HOST 2.
user@HOST1# ping 192.168.80.20 source 192.168.90.20 count 4 PING 192.168.80.20 (192.168.80.20): 56 data bytes 64 bytes from 192.168.80.1: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.80.1: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.80.1: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.80.1: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.80.1 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
A PING 192.168.80.20 (192.168.80.20): 56 data bytes confirmação da conectividade do HOST 1 ao HOST 2.
Apêndice 1: Definir comandos em todos os dispositivos
Definir saída de comando em todos os dispositivos.
Definir comandos no SRX1
set security key-manager profiles km_profile_1 static key-id ascii-text test-key-id set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.1/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.2 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.1 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Definir comandos no SRX2
set security key-manager profiles km_profile_1 static key-id ascii-text test-key-id set security key-manager profiles km_profile_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.2/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text “ipsec-test” set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.1 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.2 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Apêndice 2: Mostrar saída de configuração no DUT
SRX1
A partir do modo de configuração, confirme sua configuração entrando nos show security ike proposal IKE_PROPshow security ipsec proposal IPSEC_PROPshow interfacesshow security zonesshow security key-managershow security key-manager profilesshow security ike policy IKE_POLshow security ike gateway IKE_GWshow security policiesshow security ipsec policy IPSEC_POLcomandos e show security ipsec vpn IPSEC_VPN comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@srx1# show security key-manager profiles
km_profile_1 {
static {
key-id ascii-text "$9$.mz6pu1hyKBI8X-boajHqmF/hcylK836"; ## SECRET-DATA
key ascii-text "$9$5Q6AhclXNbtuIcyeXxGDikfT369A0Bn/vWLNY2aZUjPQAp0BEcFnyleMXxGDi.mT9CuhSeIElMLXwsaZUikPpu1hSen/eW8XbwJGD"; ## SECRET-DATA
}
}
user@srx1# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$.mz6pu1hyKBI8X-boajHqmF/hcylK836"; ## SECRET-DATA
key ascii-text "$9$5Q6AhclXNbtuIcyeXxGDikfT369A0Bn/vWLNY2aZUjPQAp0BEcFnyleMXxGDi.mT9CuhSeIElMLXwsaZUikPpu1hSen/eW8XbwJGD"; ## SECRET-DATA
}
}
}
user@srx1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.2/24;
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.80.1/24;
address 192.168.90.1/24;
}
family mpls;
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}
user@srx1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
user@srx1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
user@srx1# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx1# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$z0C63/tp0Icrvz39p0Ihcs24aZjqmTn9p"; ## SECRET-DATA
user@srx1# show security ike gateway IKE_GW ike-policy IKE_POL; address [ 172.18.10.1 172.18.10.2 ]; external-interface ge-0/0/0.0; local-address 172.18.10.1; version v2-only; ppk-profile km_profile_1;
user@srx1# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srx1# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srx1# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 192.168.80.0/24;
}
establish-tunnels immediately;
SRX2
A partir do modo de configuração, confirme sua configuração entrando nos show security ike proposal IKE_PROPshow security ipsec proposal IPSEC_PROPshow interfacesshow security zonesshow security key-managershow security key-manager profilesshow security ike policy IKE_POLshow security ike gateway IKE_GWshow security policiesshow security ipsec policy IPSEC_POLcomandos e show security ipsec vpn IPSEC_VPN comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@srx2# show security key-manager profiles
km_profile_1 {
static {
key-id ascii-text "$9$Hk5FCA0IhruOvWx-2gGDikT3IRhSrvQF"; ## SECRET-DATA
key ascii-text "$9$zDD33CuyrvNVY0BhreMN-jHqmQF/Ctu1R9A8X7V4oGDikT3uO1RSr69evMLN-jHqf5FtpBylMhSvL7N2gGDiqmTOBEylM9AMXxNY2UjH"; ## SECRET-DATA
}
}user@srx2# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$Hk5FCA0IhruOvWx-2gGDikT3IRhSrvQF"; ## SECRET-DATA
key ascii-text "$9$zDD33CuyrvNVY0BhreMN-jHqmQF/Ctu1R9A8X7V4oGDikT3uO1RSr69evMLN-jHqf5FtpBylMhSvL7N2gGDiqmTOBEylM9AMXxNY2UjH"; ## SECRET-DATA
}
}
}user@srx2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}user@srx2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srx2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srx2# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx2# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$zTi03/tp0Icrvz39p0Ihcs24aZjqmTn9p"; ## SECRET-DATA
user@srx2# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.1; external-interface ge-0/0/0.0; local-address 172.18.10.2; version v2-only; ppk-profile km_profile_1;
user@srx2# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srx2# show security ipsec policy IPSEC_POL
proposals IPSEC_PROP;
[edit]
user@srx2# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}
establish-tunnels immediately;
Exemplo: Configure o perfil de chaves estáticas para AutoVPN
Use este exemplo de configuração para proteger uma infraestrutura IPsec AutoVPN configurando o perfil chave estático.
Você pode proteger uma infraestrutura IPsec AutoVPN configurando o perfil chave estático.
Neste exemplo de configuração, o Hub, Spoke 1 e Spoke 2 usam perfis-chave estáticos para buscar as chaves QKD na VPN IPsec. As chaves QKD ajudam a enviar tráfego com segurança pela Internet.
|
Tempo de leitura |
Menos de uma hora |
|
Tempo de configuração |
Menos de uma hora |
- Pré-requisitos de exemplo
- Antes de começar
- Visão geral funcional
- Visão geral da topologia
- Ilustração de topologia
- Configuração passo a passo no hub
- Configuração passo a passo em dispositivos spoke
- Verificação
- Apêndice 1: Definir comandos em todos os dispositivos
- Apêndice 2: Mostrar saída de configuração no DUT
Pré-requisitos de exemplo
|
Requisitos de hardware |
|
|
Requisitos de software |
Versão Junos OS 22.4R1 ou posterior. |
Antes de começar
|
Benefícios |
|
|
Recursos úteis |
|
|
Saiba mais |
|
|
Experiência prática |
|
|
Saiba mais |
Obtenha o endereço da autoridade de certificado (CA) e as informações que eles exigem (como a senha do desafio) e então você envia solicitações de certificados locais. Veja a compreensão das solicitações de certificados locais. Inscreva os certificados digitais em cada dispositivo. Veja exemplo: Carregamento manual de CA e certificados locais. |
Visão geral funcional
| IPsec VPN |
Implanta uma topologia de VPN IPsec hub-and-spoke onde os spokes são conectados por túneis VPN que enviam tráfego pelo hub. Esses túneis VPN são configurados posteriormente para usar chaves quânticas, tornando-os túneis VPN com segurança quântica. |
| Gateway IKE |
Estabelece uma conexão segura, o gateway IKE usa a política de IKE para se limitar ao grupo configurado de CAs (ca-profiles) enquanto valida o certificado. |
| Propostas | |
| Proposta de IKE |
Define os algoritmos e as chaves usadas para estabelecer a conexão IKE segura com o gateway de segurança por pares. O IKE cria os SAs dinâmicos e os negocia para o IPsec. |
| Proposta de IPsec |
Lista protocolos, algoritmos e serviços de segurança a serem negociados com o peer IPsec remoto. |
| Políticas | |
| Política de IKE |
Define uma combinação de parâmetros de segurança (propostas de IKE) a serem usados durante a negociação da IKE. |
| Política de IPsec |
Contém regras e políticas de segurança para permitir o tráfego de VPN em grupo entre as zonas especificadas. |
| Política de segurança |
Permite que você selecione o tipo de tráfego de dados para proteger por meio dos SAs IPsec.
|
|
Perfis |
|
|
Perfil chave |
Definir como os dispositivos de firewall da Série SRX se comunicam com os dispositivos KME para recuperar chaves QKD do servidor KME externo. Os principais perfis estão configurados no hub (HUB_KM_PROFILE_1) e spokes (SPOKE_1_KM_PROFILE_1 e SPOKE_2_KM_PROFILE_1) separadamente.
|
| Perfil do PPK |
Indica qual perfil chave usar para estabelecer SAs IKE ou IPsec com segurança quântica fazendo referência ao perfil chave no gateway IKE. |
| Certificados | |
| Certificado de CA | Verifica a identidade dos dispositivos e autentica o link de comunicação entre eles. |
| Certificado local | Gera PKI e o inscreve no certificado CA para verificação. |
| Certificado KME | Certificado de terceiros gerado pelo fornecedor. |
| Zonas de segurança | |
| confiança |
Segmento de rede na zona de host. |
| desconfiança |
Segmento de rede na zona de servidor de destino. |
| VPN |
Segmento de rede por meio do qual o hub-and-spoke interage. |
|
Tarefas primárias de verificação |
Verifique se os SAs IKE e IPsec estabelecidos são seguros em quantum. |
Visão geral da topologia
Neste exemplo, o SPOKE 1 e o SPOKE 2 iniciam a negociação de túneis IPsec com segurança quântica com o Hub usando a chave estática configurada por CLI. O Hub responde às solicitações verificando a identidade do Spoke 1 e Spoke 2 juntamente com suas respectivas chaves e estabelece uma VPN IPsec com segurança quântica com ambos os spokes. Assim que os túneis forem estabelecidos, o tráfego de dados entre o Host 1 e o Host 3 e entre o Host 2 e o Host 3 ficam seguros usando os túneis IPsec estabelecidos.
|
Nome de host |
Função |
Função |
|---|---|---|
| Hub | Firewall da Série SRX capaz de estabelecer túneis IPsec | Responde à negociação de IKE ou IPsec SA iniciada pelo SPOKE 1 e SPOKE 2 e estabelece túneis de IPsec com segurança quântica usando chave estática configurada no dispositivo Hub. |
| Spoke 1 | Firewall da Série SRX capaz de estabelecer túneis IPsec | Inicia a negociação de IKE/IPsec SA e estabelece túneis de IPsec com segurança quântica com o Hub usando chave estática configurada no Spoke 1. |
| Spoke 2 | Firewall da Série SRX capaz de estabelecer túneis IPsec | Inicia a negociação de IKE ou IPsec SA e estabelece túneis de IPsec com segurança quântica com o Hub usando chave estática configurada no Spoke 2. |
| Host 1 | Host dentro da zona confiável ou lado LAN do Spoke 1 | Inicia o tráfego do lado do cliente em direção ao Host 3. |
| Host 2 | Host dentro da zona confiável ou lado LAN do Spoke 2 | Inicia o tráfego do lado do cliente em direção ao Host 3. |
| Host 3 | Host dentro da zona confiável ou lado LAN do HUB | Responde ao tráfego do lado cliente do Host 1 e Host 2. |
Ilustração de topologia
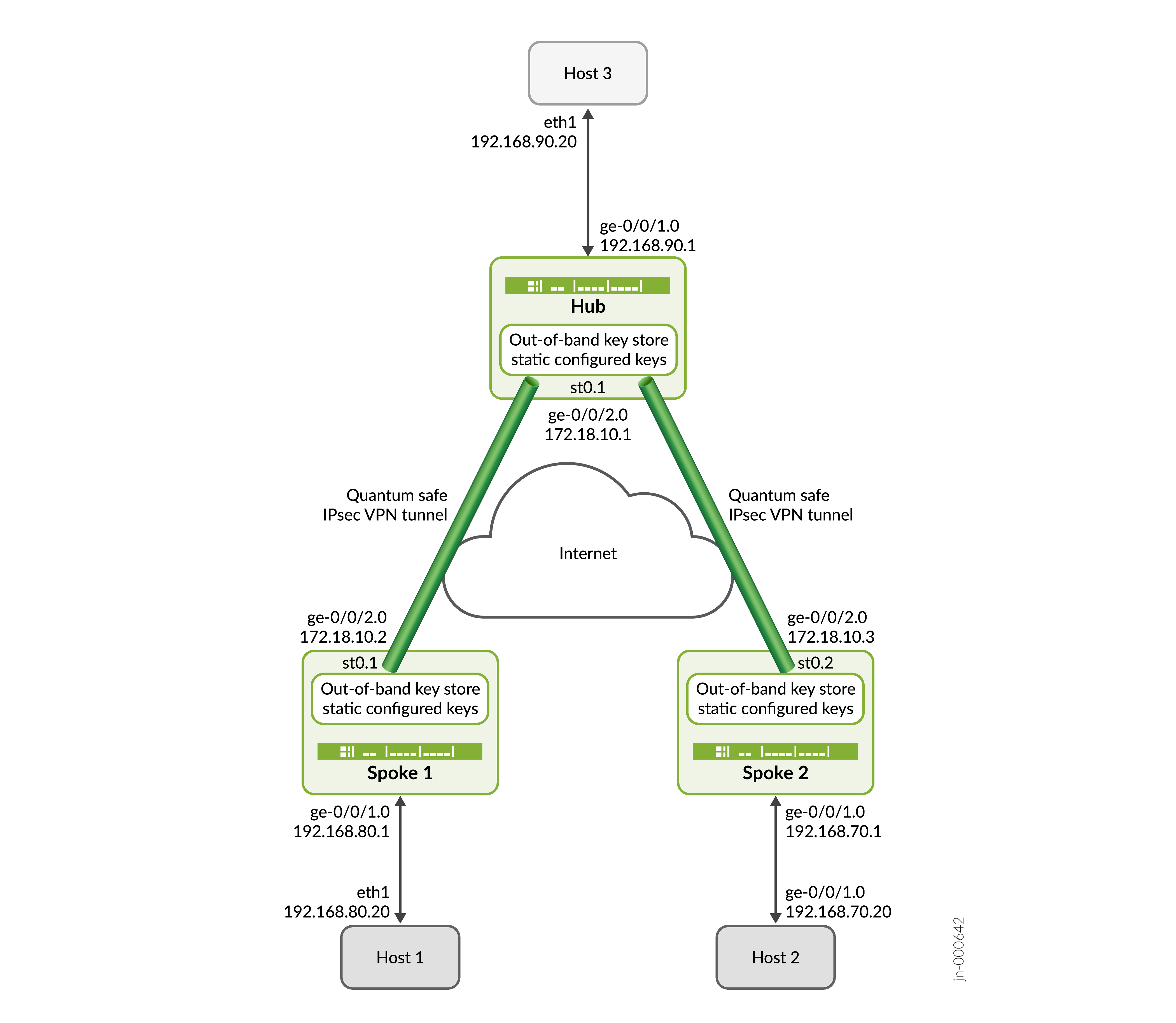
Configuração passo a passo no hub
Para ver configurações de amostra completas no DUT, veja:
Essa configuração é aplicável apenas para os dispositivos Hub. Você deve fazer as alterações de configuração específicas do dispositivo apropriadas.
-
Configure as interfaces de hub.
[edit interfaces] user@hub# set ge-0/0/2 unit 0 family inet address 172.18.10.1/24 user@hub# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24 user@hub# set st0 unit 1 family inet
-
Configure o perfil da CA e o certificado ca.
[edit security pki] user@hub# set ca-profile Root-CA ca-identity Root-CA user@hub# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@hub# set ca-profile Root-CA revocation-check disable
-
A partir do modo operacional, vincule o certificado ca ao perfil ca.
user@hub> request security pki ca-certificate enroll ca-profile Root-CA user@hub> request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa user@hub> request security pki local-certificate enroll certificate-id HUB_CRT challenge-password <different> domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA
-
Configure o perfil de gerente de chave estática.
[edit security key-manager profiles] user@hub# set HUB_KM_PROFILE_1 static key-id ascii-text test-key-id user@hub# set HUB_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
Configure o hub-spoke na VPN IPsec. Isso inclui a configuração das zonas de segurança, políticas de segurança e certificados relevantes para autenticar identidades de dispositivos e seus links de comunicação.
[edit security ike proposal] user@hub# set HUB_IKE_PROP authentication-method rsa-signatures user@hub# set HUB_IKE_PROP dh-group group14 user@hub# set HUB_IKE_PROP authentication-algorithm sha-256 user@hub# set HUB_IKE_PROP encryption-algorithm aes-256-cbc user@hub# set HUB_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@hub# set HUB_IKE_POL proposals HUB_IKE_PROP user@hub# set HUB_IKE_POL certificate local-certificate HUB_CRT
[edit security ike gateway] user@hub# set HUB_IKE_GW local-address 172.18.10.1 user@hub# set HUB_IKE_GW ike-policy HUB_IKE_POL user@hub# set HUB_IKE_GW external-interface ge-0/0/2.0 user@hub# set HUB_IKE_GW local-identity distinguished-name user@hub# set HUB_IKE_GW dynamic ike-user-type group-ike-id user@hub# set HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper user@hub# set HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 user@hub# set HUB_IKE_GW version v2-only
[edit security ipsec proposal] user@hub# set HUB_IPSEC_PROP protocol esp user@hub# set HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@hub# set HUB_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec policy] user@hub# set HUB_IPSEC_POL proposals HUB_IPSEC_PROP
[edit security ipsec vpn] user@hub# set HUB_IPSEC_VPN bind-interface st0.1 user@hub# set HUB_IPSEC_VPN ike gateway HUB_IKE_GW user@hub# set HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL user@hub# set HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@hub# set HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0
[edit security zones] user@hub# set security-zone untrust host-inbound-traffic system-services ike user@hub# set security-zone untrust interfaces ge-0/0/2.0 user@hub# set security-zone vpn interfaces st0.1 user@hub# set security-zone trust host-inbound-traffic system-services ping user@hub# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@hub# set from-zone trust to-zone vpn policy vpn_out match source-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match application any user@hub# set from-zone trust to-zone vpn policy vpn_out then permit user@hub# set from-zone vpn to-zone trust policy vpn_in match source-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match application any user@hub# set from-zone vpn to-zone trust policy vpn_in then permit
Configuração passo a passo em dispositivos spoke
Para ver configurações de amostra completas no DUT, veja:
Essa configuração é aplicável para dispositivos Spoke 1 e Spoke 2. Para outros dispositivos, você deve fazer alterações de configuração específicas do dispositivo apropriadas.
-
Configure as interfaces de spoke.
[edit interfaces] user@spoke# set ge-0/0/2 unit 0 family inet address 172.18.10.2/24 user@spoke# set ge-0/0/1 unit 0 family inet address 192.168.80.1/24 user@spoke# set st0 unit 1 family inet
-
Configure o hub-spoke na VPN IPsec. Isso inclui a configuração das zonas de segurança, políticas de segurança e certificados relevantes para autenticar identidades de dispositivos e seus links de comunicação.
[edit security ike proposal] user@spoke# set SPOKE_1_IKE_PROP authentication-method rsa-signatures user@spoke# set SPOKE_1_IKE_PROP dh-group group14 user@spoke# set SPOKE_1_IKE_PROP authentication-algorithm sha-256 user@spoke# set SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc user@spoke# set SPOKE_1_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@spoke# set SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP user@spoke# set SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW address 172.18.10.1 user@spoke# set SPOKE_1_IKE_GW local-address 172.18.10.2 user@spoke# set SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL user@spoke# set SPOKE_1_IKE_GW external-interface ge-0/0/2.0 user@spoke# set SPOKE_1_IKE_GW local-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW remote-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 user@spoke# set SPOKE_1_IKE_GW version v2-only
[edit security ipsec proposal] user@spoke# set SPOKE_1_IPSEC_PROP protocol esp user@spoke# set SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@spoke# set SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec policy] user@spoke# set SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP
[edit security ipsec vpn] user@spoke# set SPOKE_1_IPSEC_VPN bind-interface st0.1 user@spoke# set SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW user@spoke# set SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24
[edit security zones] user@spoke# set security-zone untrust host-inbound-traffic system-services ike user@spoke# set security-zone untrust interfaces ge-0/0/2.0 user@spoke# set security-zone vpn interfaces st0.1 user@spoke# set security-zone trust host-inbound-traffic system-services ping user@spoke# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@spoke# set from-zone trust to-zone vpn policy vpn_out match source-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match application any user@spoke# set from-zone trust to-zone vpn policy vpn_out then permit user@spoke# set from-zone vpn to-zone trust policy vpn_in match source-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match application any user@spoke# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki ] user@spoke# set ca-profile Root-CA ca-identity Root-CA user@spoke# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@spoke# set ca-profile Root-CA revocation-check disable
user@spoke> request security pki ca-certificate enroll ca-profile Root-CA user@spoke> request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa user@spoke> request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <different> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA
-
Configure o perfil de gerente de chave estática.
[edit security key-manager profiles] user@spoke# set SPOKE_1_KM_PROFILE_1 static key-id ascii-text test-key-id user@spoke# set SPOKE_1_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg
Verificação
Esta seção fornece uma lista de comandos de exibição que você pode usar para verificar o recurso neste exemplo.
| Comando | Tarefa de verificação |
|---|---|
|
mostrar segurança ike detalhes de associações de segurança |
|
|
mostrar detalhes das associações de segurança ipsec de segurança |
|
|
mostrar estatísticas de segurança ipsec |
PropósitoVerifique as estatísticas de criptografia e descriptografia do IPsec. |
|
mostrar detalhes dos perfis dos principais gerentes de segurança |
|
|
ping 192.168.90.20 fonte 192.168.80.20 contagem 4 |
- Verifique os SAs de IKE
- Verifique os SAs IPsec
- Verifique as estatísticas do IPsec
- Verificar o perfil do gerente-chave
- Ping do Host 1 para Host 3 ou vice-versa
- Ping do Host 2 para Host 3 ou vice-versa
Verifique os SAs de IKE
Propósito
Verifique os SAs de IKE.
Ação
Desde o modo operacional, entre no show security ike security-associations detail comando para ver os SAs IKE.
user@hub> show security ike security-associations detail
IKE peer 172.18.10.2, Index 2123, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 0e40ccdcee1b54bd, Responder cookie: 43964f5cc4d4491c
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 2840 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2610
Output bytes : 2571
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500440
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
IKE peer 172.18.10.3, Index 2124, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 651bf4a52a9375ec, Responder cookie: d9a9c95c27e3f929
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Lifetime: Expires in 2901 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2610
Output bytes : 2571
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500441
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
Significado
Os Role: Responder, State: UPcampos e IPSec security associations: 2 created, 0 deletedPPK-profile: HUB_KM_PROFILE_1Flags: IKE SA is created os campos mostram que os SAs IKE foram criados com sucesso.
Verifique os SAs IPsec
Propósito
Verifique os SAs IPsec.
Ação
Do modo operacional, entre no show security ipsec security-associations detail comando para ver os SAs IPsec.
user@hub> show security ipsec security-associations detail
ID: 500440 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.80.0-192.168.80.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Thu Jul 20 2023 10:44:19: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x649d371f, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2840 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2183 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2123
Direction: outbound, SPI: 0xd5ef611e, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2840 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2183 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2123
ID: 500441 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.3
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.70.0-192.168.70.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Thu Jul 20 2023 10:45:19: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0xa0d3ba32, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2901 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2258 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2124
Direction: outbound, SPI: 0xe54414e3, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 2901 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2258 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2124
Significado
Os Quantum Secured: Yescampos e Policy-name: HUB_IPSEC_POLPassive mode tunneling: DisabledIPsec SA negotiation succeeds (1 times) os campos mostram que os SAs IPsec são criados com sucesso.
Verifique as estatísticas do IPsec
Propósito
Verifique as estatísticas do IPsec.
Ação
Do modo operacional, entre no show security ipsec statistics comando para ver as estatísticas do IPsec.
user@hub> show security ipsec statistics ESP Statistics: Encrypted bytes: 1248 Decrypted bytes: 1248 Encrypted packets: 8 Decrypted packets: 8 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Os ESP Statistics campos e os campos AH Statistics mostram as estatísticas do IPsec.
Verificar o perfil do gerente-chave
Propósito
Verifique o perfil do gerente chave.
Ação
Do modo operacional, insira o show security key-manager profiles detail comando para visualizar o perfil do gerente chave.
user@hub> show security key-manager profiles detail
Name: HUB_KM_PROFILE_1, Index: 4, Type: Static
Configured-at: 20.07.23 (09:59:06)
Time-elapsed: 1 hrs 2 mins 7 secs
Request stats:
Received: 2
In-progress: 0
Success: 2
Failed: 0Significado
Os Name: HUB_KM_PROFILE_1 campos e os campos Type: Static mostram o perfil do gerente-chave
Ping do Host 1 para Host 3 ou vice-versa
Propósito
Verifique a conectividade do Host 1 ao Host 3.
Ação
Do modo operacional, entre no ping 192.168.90.20 source 192.168.80.20 count 4 comando para visualizar a conectividade do Host 1 ao Host 3.
user@HOST1# ping 192.168.90.20 source 192.168.80.20 count 4 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.90.20 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
A PING 192.168.80.20 (192.168.80.20): 56 data bytes confirmação da conectividade do HOST 1 ao HOST 3.
Ping do Host 2 para Host 3 ou vice-versa
Propósito
Verifique a conectividade do Host 2 ao Host 3.
Ação
Do modo operacional, entre no ping 192.168.90.20 source 192.168.80.20 count 4 ponto de vista da conectividade do Host 2 ao Host 3.
user@HOST1# ping 192.168.90.20 source 192.168.70.20 count 4 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms --- 192.168.90.20 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
A PING 192.168.80.20 (192.168.80.20): 56 data bytes confirmação da conectividade do HOST 2 ao HOST 3.
Apêndice 1: Definir comandos em todos os dispositivos
Definir saída de comando em todos os dispositivos.
Definir comandos no hub
set security ike proposal HUB_IKE_PROP dh-group group14 set security ike proposal HUB_IKE_PROP authentication-algorithm sha-256 set security ike proposal HUB_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal HUB_IKE_PROP lifetime-seconds 3600 set security ike policy HUB_IKE_POL proposals HUB_IKE_PROP set security ike policy HUB_IKE_POL certificate local-certificate HUB_CRT set security ike gateway HUB_IKE_GW local-address 172.18.10.1 set security ike gateway HUB_IKE_GW ike-policy HUB_IKE_POL set security ike gateway HUB_IKE_GW external-interface ge-0/0/2.0 set security ike gateway HUB_IKE_GW local-identity distinguished-name set security ike gateway HUB_IKE_GW dynamic ike-user-type group-ike-id set security ike gateway HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper set security ike gateway HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 set security ike gateway HUB_IKE_GW version v2-only set security ipsec proposal HUB_IPSEC_PROP protocol esp set security ipsec proposal HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal HUB_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP set security ipsec vpn HUB_IPSEC_VPN bind-interface st0.1 set security ipsec vpn HUB_IPSEC_VPN ike gateway HUB_IKE_GW set security ipsec vpn HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.1/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Definir comandos no Spoke 1
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <different> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA set security key-manager profiles SPOKE_1_KM_PROFILE_1 static key-id ascii-text test-key-id set security key-manager profiles SPOKE_1_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_1_IKE_PROP dh-group group14 set security ike proposal SPOKE_1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_1_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP set security ike policy SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT set security ike gateway SPOKE_1_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_1_IKE_GW local-address 172.18.10.2 set security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL set security ike gateway SPOKE_1_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_1_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 set security ike gateway SPOKE_1_IKE_GW version v2-only set security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP set security ipsec vpn SPOKE_1_IPSEC_VPN bind-interface st0.1 set security ipsec vpn SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW set security ipsec vpn SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.2/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Definir comandos no Spoke 2
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_2_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_2_CRT challenge-password <different> domain-name spoke_2.juniper.net email spoke_2@juniper.net subject DC=juniper,CN=spoke_2.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA set security key-manager profiles SPOKE_2_KM_PROFILE_1 static key-id ascii-text test-key-id set security key-manager profiles SPOKE_2_KM_PROFILE_1 static key ascii-text qjwbdip139u5mcy89m28pcgowerefnkjsdg set security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_2_IKE_PROP dh-group group14 set security ike proposal SPOKE_2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_2_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_2_IKE_POL proposals SPOKE_IKE_PROP set security ike policy SPOKE_2_IKE_POL certificate local-certificate SPOKE_2_CRT set security ike gateway SPOKE_2_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_2_IKE_GW local-address 172.18.10.3 set security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL set security ike gateway SPOKE_2_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_2_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW ppk-profile SPOKE_2_KM_PROFILE_1 set security ike gateway SPOKE_2_IKE_GW version v2-only set security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_2_IPSEC_POL proposals SPOKE_2_IPSEC_PROP set security ipsec vpn SPOKE_2_IPSEC_VPN bind-interface st0.2 set security ipsec vpn SPOKE_2_IPSEC_VPN ike gateway SPOKE_2_IKE_GW set security ipsec vpn SPOKE_2_IPSEC_VPN ike ipsec-policy SPOKE_2_IPSEC_POL set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 local-ip 192.168.70.0/24 set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.3/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.70.1/24 set interfaces st0 unit 2 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.2 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Apêndice 2: Mostrar saída de configuração no DUT
Hub
A partir do modo de configuração, confirme sua configuração inserindo os show security zonesshow security ike gateway HUB_IKE_GWshow security ike policy HUB_IKE_POLshow security ike proposal HUB_IKE_PROPshow security ipsec policy HUB_IPSEC_POLshow security ipsec vpn HUB_IPSEC_VPNshow security ipsec proposal HUB_IPSEC_PROPshow interfacescomandos e show security policies comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@hub# show security ike proposal HUB_IKE_PROP dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@hub# show security ike policy HUB_IKE_POL
proposals HUB_IKE_PROP;
certificate {
local-certificate HUB_CRT;user@hub# show security ike gateway HUB_IKE_GW
ike-policy HUB_IKE_POL;
dynamic {
distinguished-name {
wildcard C=us,DC=juniper;
}
ike-user-type group-ike-id;
}
local-identity distinguished-name;
external-interface ge-0/0/2.0;
local-address 172.18.10.1;
version v2-only;
ppk-profile HUB_KM_PROFILE_1;user@hub# show security ipsec proposal HUB_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@hub# show security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP;
user@hub# show security ipsec vpn HUB_IPSEC_VPN
bind-interface st0.1;
ike {
gateway HUB_IKE_GW;
ipsec-policy HUB_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 0.0.0.0/0;
}user@hub# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}user@hub# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}
user@hub# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}Spoke 1
A partir do modo de configuração, confirme sua configuração inserindo os show security ipsec vpn SPOKE_1_IPSEC_VPNshow security zonesshow security ike proposal SPOKE_1_IKE_PROPshow security ike policy SPOKE_1_IKE_POLshow security ike gateway SPOKE_1_IKE_GWshow security key-manager profiles SPOKE_1_KM_PROFILE_1show security pki ca-profile Root-CAshow security ipsec policy SPOKE_1_IPSEC_POLshow interfacesshow security ipsec proposal SPOKE_1_IPSEC_PROPshow security policiescomandos e show security pki comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@spoke1# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
user@spoke1# show security key-manager profiles SPOKE_1_KM_PROFILE_1
static {
key-id ascii-text "$9$cJ5SvLdVYoZjs2qmTFAt1RhSMXoaZUjqWL"; ## SECRET-DATA
key ascii-text "$9$mfF/IRSWX-9AORhyW8aZUj.PQFn/tuz3lKMXbwgoJGqf/Ctu1RTzhSyeW8aZUHkPn6AIEyO1SeMWdVgoJUjqCA0IEyz3yKvW-d4aZ"; ## SECRET-DATA
}
user@spoke1# show security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke1# show security ike policy SPOKE_1_IKE_POL
proposals SPOKE_1_IKE_PROP;
certificate {
local-certificate SPOKE_1_CRT;
}
user@spoke1# show security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.2; version v2-only; ppk-profile SPOKE_1_KM_PROFILE_1;
user@spoke1# show security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke1# show security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP;
user@spoke1# show security ipsec vpn SPOKE_1_IPSEC_VPN
bind-interface st0.1;
ike {
gateway SPOKE_1_IKE_GW;
ipsec-policy SPOKE_1_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}user@spoke1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
}
user@spoke1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@spoke1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
user@spoke1# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
}Spoke 2
A partir do modo de configuração, confirme sua configuração inserindo os show security pkishow security ike proposal SPOKE_2_IKE_PROPshow security ike gateway SPOKE_2_IKE_GWshow security ike policy SPOKE_2_IKE_POLshow security key-managershow security ipsec vpn SPOKE_2_IPSEC_VPNshow interfacesshow security ipsec proposal SPOKE_2_IPSEC_PROPshow security zonescomandos e show security policies comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@spoke2# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}
}
user@spoke2# show security key-manager
profiles {
SPOKE_2_KM_PROFILE_1 {
static {
key-id ascii-text "$9$C4Y8ABEleWx-wM8goGjPf369A1hx7-VwgIE"; ## SECRET-DATA
key ascii-text "$9$15SRyKdVYGjqvW7Vw2GUn/CtBIcylK8XSr4aZjPfz369ORKM8X-VhSwY2oGUn/Cu0IleWdb27-YoZG.mz36CtOMWxdb2Sr2aJGq.Fn/"; ## SECRET-DATA
}
}
}
user@spoke2# show security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke2# show security ike policy SPOKE_2_IKE_POL
proposals SPOKE_IKE_PROP;
certificate {
local-certificate SPOKE_2_CRT;
}
user@spoke2# show security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.3; version v2-only; ppk-profile SPOKE_2_KM_PROFILE_1;
user@spoke2# show security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke2# show security ipsec vpn SPOKE_2_IPSEC_VPN
bind-interface st0.2;
ike {
gateway SPOKE_2_IKE_GW;
ipsec-policy SPOKE_2_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.70.0/24;
remote-ip 192.168.90.0/24;
}user@spoke2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@spoke2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/2.0;
}
}
security-zone vpn {
interfaces {
st0.2;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@spoke2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}Configure o perfil chave do gerente de chaves quânticas para o Junos Key Manager
Este exemplo mostra como configurar o perfil de chave quântica para o gerenciador-chave do Junos. Configure o perfil chave do gerenciador de chaves quânticas para gerar e enviar as chaves geradas para estabelecer um túnel VPN IPsec com segurança quântica.
Requisitos
-
Requisitos de hardware — Juniper Networks® SRX1500 firewall e modelos de dispositivos de maior número ou firewall virtual vSRX da Juniper Networks® (vSRX3.0).
-
Requisitos de software — Versão do Junos OS 22.4R1 ou posterior com JUNOS ike e JUNOS Key Manager pacotes.
-
Use qualquer dispositivo QKD com suporte a ETSI Quantum Key Distribution (QKD) padrão rest API para comunicação.
-
Carregue os certificados locais no dispositivo. Recomendamos que você fornecesse o caminho completo para o certificado.
Visão geral
Os dispositivos de firewall da Série SRX usam a VPN IPsec para enviar tráfego com segurança pela Internet. Configure o perfil chave do gerenciador de chaves quânticas na VPN IPsec para re-autenticar a SA IKE existente e uma nova chave e chave.
O perfil chave do gerente de chave quântica usa um método de distribuição de chave segura baseado em QKD para gerar e distribuir chaves que são seguras quânticas. Essas chaves são dinâmicas.
Configuração
-
Configure o certificado ca.
user@host# set security pki ca-profile Root-CA ca-identity Root-CA user@host# set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@host# set security pki ca-profile Root-CA revocation-check disable
-
Carregue o certificado ca.
user@host> request security pki local-certificate load certificate-id SAE_A filename SAE_A.cert key SAE_A.key
-
Inscreva-se no certificado ca.
user@host> request security pki ca-certificate enroll ca-profile Root-CA
-
Configure o perfil de gerente de chave quântica.
user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager url https://kme.juniper.net user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager local-sae-id SAE_A user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_A_CERT user@host# set security key-manager profiles KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
Verificação
Propósito
Verifique o perfil e as chaves da chave do gerente de chave quântica.
Ação
A partir do modo operacional, digite show security pki ca-certificate ca-profile Root-CA para visualizar o perfil da CA e os certificados de CA.
user@host> show security pki ca-certificate ca-profile Root-CA
LSYS: root-logical-system
CA profile: Root-CA
Certificate identifier: Root-CA
Issued to: Root-CA, Issued by: C = IN, ST = WestBengal, O = JuniperNetworks, CN = Root-CA
Validity:
Not before: 09-11-2023 09:03 UTC
Not after: 03-24-2044 09:03 UTC
Public key algorithm: rsaEncryption(4096 bits)
Keypair Location: Keypair generated locallyA partir do modo operacional, insira a show security pki local-certificate certificate-id SAE_A_CERT visualização dos certificados locais de PKI.
user@host> show security pki local-certificate certificate-id SAE_A_CERT
LSYS: root-logical-system
Certificate identifier: SAE_A_CERT
Issued to: SAE_A, Issued by: C = IN, ST = WestBengal, O = JuniperNetworks, CN = ROOT_CA
Validity:
Not before: 08-28-2023 04:54 UTC
Not after: 03-10-2044 04:54 UTC
Public key algorithm: rsaEncryption(2048 bits)
Keypair Location: Keypair generated locallyDesde o modo operacional, digite o perfil e as chaves do request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B gerenciador de chaves do dispositivo peer.
user@host> request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B
- Response:
- Status: SUCCESS
- Name: km_profile_1
- Type: quantum-key-manager
- Key-size: 256 bits
- Key-count: 1
- Key-ids:
- 002420bd-7a03-4725-9c41-6969d8e1815a
- Keys:
- 728d21c4a05fe2f73c7b2f58d1e3631dc68fcfaca16be12ca3fc7715079db0f9A partir do modo operacional, digite para visualizar os show security key-manager profiles name KM_PROFILE_1 detail principais detalhes do perfil do gerente.
user@host> show security key-manager profiles name KM_PROFILE_1 detail
Name: KM_PROFILE_1, Index: 2, Type: quantum-key-manager
Configured-at: 11.09.23 (02:04:32)
Time-elapsed: 0 hrs 20 mins 23 secs
Url: https://kme.juniper.net
Local-sae-id: SAE_A
Local-certificate-id: SAE_A_CERT
Trusted-cas: [ Root-CA ]
Peer-sae-ids: N/A
Default-key-size: N/A
Request stats:
Received: 0
In-progress: 0
Success: 0
Failed: 0Significado
O show security pki ca-certificate ca-profile Root-CA display exibe nome do perfil PKI CA, identificador de certificados, validade, algoritmo de chave pública e assim por diante.
Ele show security pki local-certificate certificate-id SAE_A_CERT exibe o nome do perfil local da CA, identificador de certificados, validade, algoritmo de chave pública e assim por diante.
O request security key-manager profiles get profile-keys name km_profile_1 peer-sae-id SAE_B dispositivo exibe o perfil e as chaves do gerenciador de chaves do dispositivo peer.
Ele show security key-manager profiles name KM_PROFILE_1 detail exibe o nome do perfil do gerenciador de chave de segurança, URL, solicitações e assim por diante.
Exemplo: Configure o perfil chave do gerente de chave quântica para VPN IPsec de site para site
Use este exemplo de configuração para proteger uma infraestrutura de VPN de site para local IPsec configurando o perfil chave do gerente de chave quântica.
Você pode proteger uma infraestrutura de VPN de site para local IPsec configurando o perfil chave de gerenciamento de chave quântica.
Neste exemplo de configuração, os dispositivos SRX1 e SRX2 usam o perfil de gerente de chave quântica para buscar as chaves QKD na VPN IPsec. As chaves QKD ajudam a enviar tráfego com segurança pela Internet.
|
Tempo de leitura |
Menos de uma hora |
|
Tempo de configuração |
Menos de uma hora |
- Pré-requisitos de exemplo
- Antes de começar
- Visão geral funcional
- Visão geral da topologia
- Ilustração de topologia
- Configuração passo a passo em dispositivos de firewall da Série SRX
- Verificação
- Apêndice 1: Definir comandos em todos os dispositivos
- Apêndice 2: Mostrar saída de configuração no DUT
Pré-requisitos de exemplo
|
Requisitos de hardware |
Juniper Networks® SRX1500 firewall ou modelos de dispositivos de maior número ou firewall virtual vSRX da Juniper Networks® (vSRX3.0) |
|
Requisitos de software |
Versão Junos OS 22.4R1 ou posterior. |
Antes de começar
|
Benefícios |
|
|
Recursos úteis |
|
|
Saiba mais |
|
|
Experiência prática |
|
|
Saiba mais |
Visão geral funcional
| IPsec VPN |
Implanta uma topologia de VPN IPsec hub-and-spoke onde os spokes são conectados por túneis VPN que enviam tráfego pelo hub. Esses túneis VPN são configurados posteriormente para usar chaves quânticas, tornando-os túneis VPN com segurança quântica. |
| Gateway IKE |
Estabelece uma conexão segura. O gateway IKE usa a política IKE para se limitar aos perfis configurados de autoridade de certificado (CA) enquanto valida o certificado. |
| Propostas | |
| Proposta de IKE |
Define os algoritmos e as chaves usadas para estabelecer a conexão IKE segura com o gateway de segurança por pares. O IKE cria as associações de segurança dinâmica (SAs) e as negocia com o IPsec. |
| Proposta de IPsec |
Lista protocolos, algoritmos e serviços de segurança a serem negociados com o peer IPsec remoto. |
| Políticas | |
| Política de IKE |
Define uma combinação de parâmetros de segurança (propostas de IKE) a serem usados durante a negociação da IKE. |
| Política de IPsec |
Contém regras e políticas de segurança para permitir o tráfego de VPN em grupo entre as zonas especificadas. |
| Política de segurança |
Permite que você selecione o tipo de tráfego de dados para proteger por meio dos SAs IPsec.
|
|
Perfis |
|
|
Perfil chave |
Define como os dispositivos de firewall da Série SRX se comunicam com os dispositivos KME para recuperar as chaves QKD do servidor KME externo. Os principais perfis estão configurados no hub (HUB_KM_PROFILE_1) e spokes (SPOKE_1_KM_PROFILE_1 e SPOKE_2_KM_PROFILE_1) separadamente.
|
| Perfil do PPK |
Indica qual perfil chave usar para estabelecer SAs IKE ou IPsec com segurança quântica fazendo referência ao perfil chave no gateway IKE. |
| Certificados | |
| Certificado de CA | Verifica a identidade dos dispositivos e autentica o link de comunicação. |
| Certificado local | Gera PKI e o inscreve no certificado CA para verificação. |
| Certificado KME | Certificado de terceiros gerado pelo fornecedor. |
| Zonas de segurança | |
| confiança |
Segmento de rede na zona de host. |
| desconfiança |
Segmento de rede na zona de servidor de destino. |
| VPN |
Segmento de rede por meio do qual o hub e os spokes interagem. |
|
Tarefas primárias de verificação |
Verifique se os SAs IKE e IPsec estabelecidos são seguros em quantum. |
Visão geral da topologia
Neste exemplo, protegemos os túneis de VPN SRX1 e SRX2 IPsec usando chaves quânticas geradas por dispositivos KME de terceiros. Os dispositivos KME (KME-A e KME-B) estão conectados entre si por meio de um canal quântico altamente seguro e capaz de identificar ameaças. Usando este canal, os dispositivos SRX1 e SRX2 recuperam chaves quânticas de seu dispositivo KME correspondente e as fundem com as chaves existentes para tornar os túneis VPN quânticos seguros.
|
Nome de host |
Função |
Função |
|---|---|---|
| SRX1 | Dispositivo de firewall da Série SRX capaz de estabelecer túneis IPsec | Inicia a negociação de IKE ou IPsec SA e estabelece túneis de IPsec com segurança quântica com SRX2 usando chave QKD rebuscada do dispositivo QKD KME-A. |
| SRX2 | Dispositivo de firewall da Série SRX capaz de estabelecer túneis IPsec | Responde à negociação de IKE ou IPsec SA e estabelece túneis IPsec com segurança quântica usando chave QKD do dispositivo QKD KME-B. |
| HOST1 | Host dentro da zona confiável ou lado LAN do SRX1 | Inicia o tráfego lateral do cliente em direção ao HOST 2 |
| HOST2 | Host dentro da zona confiável ou lado LAN do SRX2 | Responde ao tráfego do lado cliente do HOST 1. |
| KME-A | Dispositivo QKD de fornecedor terceirizado | Fornece chaves QKD em resposta às principais solicitações do SRX1. |
| KME-B | Dispositivo QKD de fornecedor terceirizado | Fornece chaves QKD em resposta às principais solicitações do SRX2. |
Ilustração de topologia
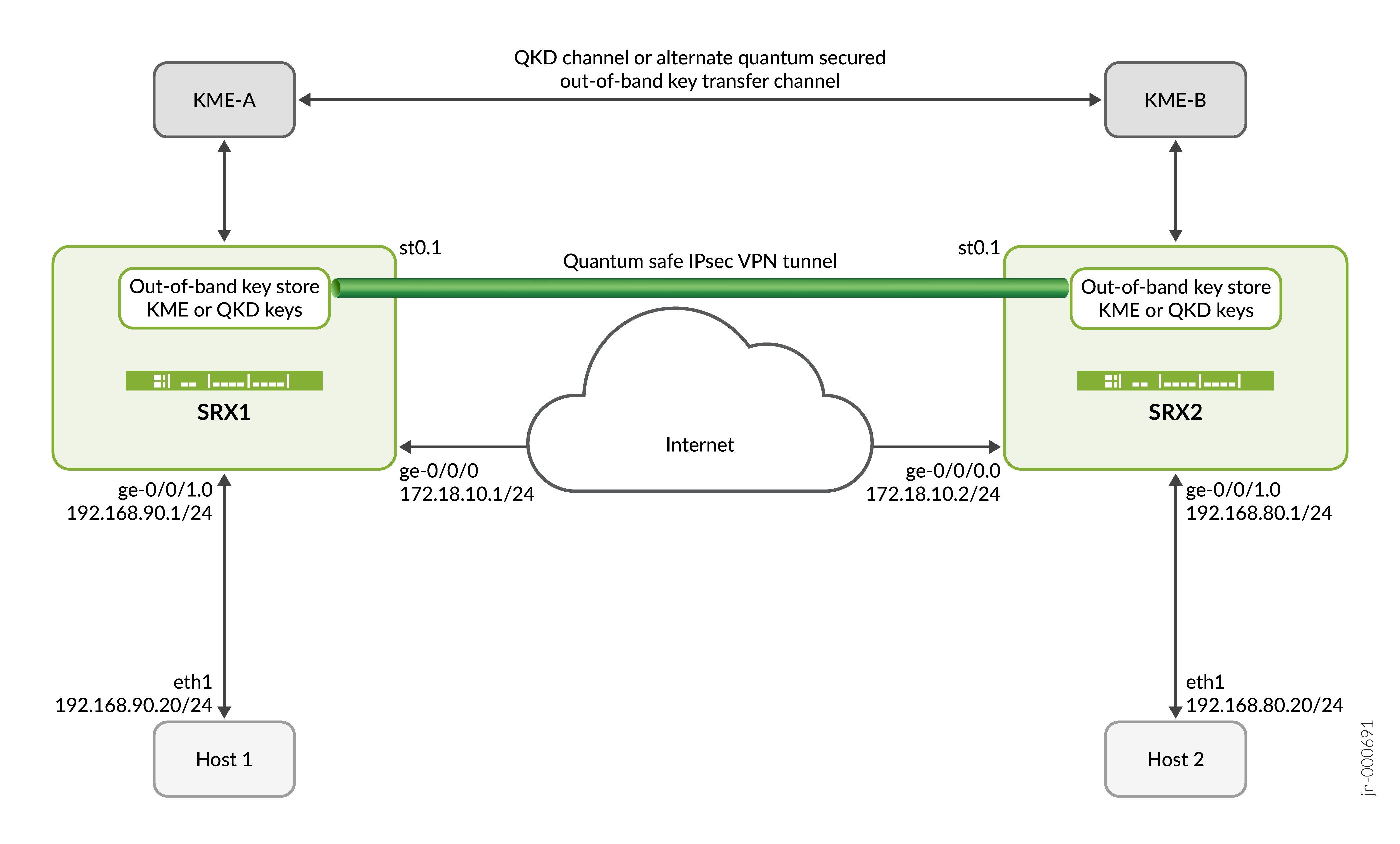
Configuração passo a passo em dispositivos de firewall da Série SRX
Para ver configurações de amostra completas no DUT, veja:
Essa configuração é aplicável aos dispositivos SRX1 e SRX2. Para outros dispositivos, você deve fazer as alterações de configuração específicas do dispositivo apropriadas.
-
Configure as interfaces.
[edit interfaces] user@srx# set ge-0/0/0 unit 0 family inet address 172.18.10.1/24 user@srx# set st0 unit 1 family inet user@srx# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24
-
Configure um perfil chave do tipo quantum-key-manager com os parâmetros necessários ou recomendados.
Defina o certificado ca, configure a URL do servidor KME, configure o SAE-ID a ser usado até o final local, configure o certificado correspondente para o SAE-ID local e configure o certificado CA previamente definido.
[edit security pki] user@srx# set ca-profile ROOT_CA_CERT ca-identity RootCA
[edit security key-manager profiles] user@srx# set km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net
[edit security key-manager profiles] user@srx# set km_profile_1 quantum-key-manager local-sae-id SAE_A user@srx# set km_profile_1 quantum-key-manager local-certificate-id SAE_A_CERT user@srx# set km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT
Configure a VPN IPsec de site para site. Isso inclui a configuração das zonas de segurança, políticas de segurança e certificados relevantes para autenticar identidades de dispositivos e seus links de comunicação.
[edit security zones] user@srx# set security-zone untrust host-inbound-traffic system-services ike user@srx# set security-zone untrust interfaces ge-0/0/0.0 user@srx# set security-zone vpn interfaces st0.1 user@srx# set security-zone trust host-inbound-traffic system-services ping user@srx# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@srx# set from-zone trust to-zone vpn policy vpn_out match source-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@srx# set from-zone trust to-zone vpn policy vpn_out match application any user@srx# set from-zone trust to-zone vpn policy vpn_out then permit user@srx# set from-zone vpn to-zone trust policy vpn_in match source-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@srx# set from-zone vpn to-zone trust policy vpn_in match application any user@srx# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security ike proposal] user@srx# set IKE_PROP authentication-method pre-shared-keys user@srx# set IKE_PROP dh-group group14 user@srx# set IKE_PROP authentication-algorithm sha-256 user@srx# set IKE_PROP encryption-algorithm aes-256-cbc user@srx# set IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@srx# set IKE_POL proposals IKE_PROP user@srx# set IKE_POL pre-shared-key ascii-text ipsec-test
[edit security ike gateway] user@srx# set IKE_GW ike-policy IKE_POL user@srx# set IKE_GW address 172.18.10.2 user@srx# set IKE_GW external-interface ge-0/0/0.0 user@srx# set IKE_GW local-address 172.18.10.1 user@srx# set IKE_GW version v2-only user@srx# set IKE_GW ppk-profile km_profile_1
[edit security ipsec proposal] user@srx# set IPSEC_PROP protocol esp user@srx# set IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@srx# set IPSEC_PROP encryption-algorithm aes-256-cbc user@srx# set IPSEC_PROP lifetime-seconds 2400
[edit security ipsec policy] user@srx# set IPSEC_POL proposals IPSEC_PROP
[edit security ipsec vpn] user@srx# set IPSEC_VPN bind-interface st0.1 user@srx# set IPSEC_VPN ike gateway IKE_GW user@srx# set IPSEC_VPN ike ipsec-policy IPSEC_POL user@srx# set IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@srx# set IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 user@srx# set IPSEC_VPN establish-tunnels immediately
Verificação
Esta seção fornece uma lista de comandos de exibição que você pode usar para verificar o recurso neste exemplo.
| Comando | Tarefa de verificação |
|---|---|
|
mostrar segurança ike detalhes de associações de segurança |
|
|
mostrar detalhes das associações de segurança ipsec de segurança |
|
|
mostrar estatísticas de segurança ipsec |
Verifique as estatísticas de criptografia e descriptografia do IPsec. |
|
mostrar detalhes dos perfis dos principais gerentes de segurança |
Verifique as principais estatísticas de perfil. |
|
ping 192.168.80.20 fonte 192.168.90.20 contagem 5 |
Ping do HOST 1 para HOST 2 ou vice-versa. |
- Verifique os SAs de IKE
- Verifique os SAs IPsec
- Verifique as estatísticas do IPsec
- Verificar o perfil do gerente-chave
- Ping do HOST 1 para HOST 2 ou vice-versa
Verifique os SAs de IKE
Propósito
Verifique os SAs de IKE.
Ação
Desde o modo operacional, entre no show security ike security-associations detail comando para ver os SAs IKE.
user@srx> show security ike security-associations detail IKE peer 172.18.10.2, Index 21, Gateway Name: IKE_GW Role: Initiator, State: UP Initiator cookie: 5a417d46cef3207d, Responder cookie: 57b9a17516bee31b Exchange type: IKEv2, Authentication method: Pre-shared-keys Local gateway interface: ge-0/0/2.0 Routing instance: default Local: 172.18.10.1:500, Remote: 172.18.10.2:500 Lifetime: Expires in 3445 seconds Reauth Lifetime: Disabled IKE Fragmentation: Enabled, Size: 576 SRG ID: 0 Remote Access Client Info: Unknown Client Peer ike-id: 172.18.10.2 AAA assigned IP: 0.0.0.0 PPK-profile: km_profile_1 Optional: No State : Used Algorithms: Authentication : hmac-sha256-128 Encryption : aes256-cbc Pseudo random function: hmac-sha256 Diffie-Hellman group : DH-group-14 Traffic statistics: Input bytes : 783 Output bytes : 831 Input packets: 2 Output packets: 2 Input fragmented packets: 0 Output fragmented packets: 0 IPSec security associations: 2 created, 0 deleted Phase 2 negotiations in progress: 1 IPSec Tunnel IDs: 500003 Negotiation type: Quick mode, Role: Initiator, Message ID: 0 Local: 172.18.10.1:500, Remote: 172.18.10.2:500 Local identity: 172.18.10.1 Remote identity: 172.18.10.2 Flags: IKE SA is created IPsec SA Rekey CREATE_CHILD_SA exchange stats: Initiator stats: Responder stats: Request Out : 0 Request In : 0 Response In : 0 Response Out : 0 No Proposal Chosen In : 0 No Proposal Chosen Out : 0 Invalid KE In : 0 Invalid KE Out : 0 TS Unacceptable In : 0 TS Unacceptable Out : 0 Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0 Res Verify SA Fail : 0 Res Verify DH Group Fail: 0 Res Verify TS Fail : 0
Significado
Os Role: Initiator, State: UPcampos e IPSec security associations: 2 created, 0 deleted Phase 2 negotiations in progress: 1PPK-profile: km_profile_1Flags: IKE SA is created os campos mostram que os SAs IKE foram criados com sucesso.
Verifique os SAs IPsec
Propósito
Verifique os SAs IPsec.
Ação
Do modo operacional, entre no show security ipsec security-associations detail comando para ver os SAs IPsec.
user@srx> show security ipsec security-associations detail ID: 500003 Virtual-system: root, VPN Name: IPSEC_VPN Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2 Traffic Selector Name: ts1 Local Identity: ipv4(192.168.90.0-192.168.90.255) Remote Identity: ipv4(192.168.80.0-192.168.80.255) TS Type: traffic-selector Version: IKEv2 Quantum Secured: Yes PFS group: N/A SRG ID: 0 DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: IPSEC_POL Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0 Multi-sa, Configured SAs# 0, Negotiated SAs#: 0 Tunnel events: Fri Mar 31 2023 01:41:52: IPsec SA negotiation succeeds (1 times) Location: FPC 0, PIC 0, KMD-Instance 0 Anchorship: Thread 1 Distribution-Profile: default-profile Direction: inbound, SPI: 0xd1e1549c, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1916 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1349 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21 Direction: outbound, SPI: 0xb5883167, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 1916 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 1349 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits) Anti-replay service: counter-based enabled, Replay window size: 64 Extended-Sequence-Number: Disabled tunnel-establishment: establish-tunnels-immediately IKE SA Index: 21
Significado
Os Quantum Secured: Yescampos e IPsec SA negotiation succeeds (1 times)Policy-name: IPSEC_POLtunnel-establishment: establish-tunnels-immediately IKE SA Index: 21 os campos mostram que os SAs IPsec são criados com sucesso.
Verifique as estatísticas do IPsec
Propósito
Verifique as estatísticas do IPsec.
Ação
Do modo operacional, entre no show security ipsec statistics comando para ver as estatísticas do IPsec.
user@srx> show security ipsec statistics ESP Statistics: Encrypted bytes: 780 Decrypted bytes: 780 Encrypted packets: 5 Decrypted packets: 5 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
Os ESP Statistics campos e os campos AH Statistics mostram as estatísticas do IPsec.
Verificar o perfil do gerente-chave
Propósito
Verifique o perfil do gerente chave.
Ação
Do modo operacional, insira o show security key-manager profiles detail comando para visualizar o perfil do gerente chave.
user@srx> show security key-manager profiles detail Name: km_profile_1, Index: 3, Type: Quantum-key-manager Configured-at: 31.03.23 (01:40:50) Time-elapsed: 0 hrs 11 mins 30 secs Url: https://www.kme_a-qkd-server.net Local-sae-id: SAE_A Local-certificate-id: SAE_A_CERT Trusted-cas: [ ROOT_CA_CERT ] Peer-sae-ids: N/A Default-key-size: N/A Request stats: Received: 1 In-progress: 0 Success: 1 Failed: 0
Significado
Os Name: km_profile_1 campos e os campos Quantum-key-manager mostram o perfil chave do gerente.
Ping do HOST 1 para HOST 2 ou vice-versa
Propósito
Verifique a conectividade do HOST 1 ao HOST 2.
Ação
Do modo operacional, entre na ping 192.168.80.20 source 192.168.90.20 contagem 5 para visualizar a conectividade do HOST 1 ao HOST 2.
user@HOST1# ping 192.168.80.20 source 192.168.90.20 count 5 PING 192.168.80.20 (192.168.80.20): 56 data bytes count 5 64 bytes from 192.168.80.1: icmp_seq=0 ttl=64 time=0.998 ms 64 bytes from 192.168.80.1: icmp_seq=1 ttl=64 time=1.594 ms 64 bytes from 192.168.80.1: icmp_seq=2 ttl=64 time=1.395 ms 64 bytes from 192.168.80.1: icmp_seq=3 ttl=64 time=1.536 ms 64 bytes from 192.168.80.1: icmp_seq=4 ttl=64 time=1.838 ms --- 192.168.80.1 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 0.998/1.472/1.838/0.277 ms Data traffic is successfully flowing between the HOSTs
Significado
A PING 192.168.80.20 (192.168.80.20): 56 data bytes count 5 confirmação da conectividade do HOST 1 ao HOST 2.
Apêndice 1: Definir comandos em todos os dispositivos
Definir saída de comando em todos os dispositivos.
Definir comandos no SRX1
set security pki ca-profile ROOT_CA_CERT ca-identity RootCA set security key-manager profiles km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net set security key-manager profiles km_profile_1 quantum-key-manager local-sae-id SAE_A set security key-manager profiles km_profile_1 quantum-key-manager local-certificate-id SAE_A_CERT set security key-manager profiles km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.1/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.2 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.1 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Definir comandos no SRX2
set security pki ca-profile ROOT_CA_CERT ca-identity RootCA set security key-manager profiles km_profile_1 quantum-key-manager url https://www.kme_a-qkd-server.net set security key-manager profiles km_profile_1 quantum-key-manager local-sae-id SAE_B set security key-manager profiles km_profile_1 quantum-key-manager local-certificate-id SAE_B_CERT set security key-manager profiles km_profile_1 quantum-key-manager trusted-cas ROOT_CA_CERT set interfaces ge-0/0/0 unit 0 family inet address 172.18.10.2/24 set interfaces st0 unit 1 family inet set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/0.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit set security ike proposal IKE_PROP authentication-method pre-shared-keys set security ike proposal IKE_PROP dh-group group14 set security ike proposal IKE_PROP authentication-algorithm sha-256 set security ike proposal IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal IKE_PROP lifetime-seconds 3600 set security ike policy IKE_POL proposals IKE_PROP set security ike policy IKE_POL pre-shared-key ascii-text ipsec-test set security ike gateway IKE_GW ike-policy IKE_POL set security ike gateway IKE_GW address 172.18.10.1 set security ike gateway IKE_GW external-interface ge-0/0/0.0 set security ike gateway IKE_GW local-address 172.18.10.2 set security ike gateway IKE_GW version v2-only set security ike gateway IKE_GW ppk-profile km_profile_1 set security ipsec proposal IPSEC_PROP protocol esp set security ipsec proposal IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec proposal IPSEC_PROP lifetime-seconds 2400 set security ipsec policy IPSEC_POL proposals IPSEC_PROP set security ipsec vpn IPSEC_VPN bind-interface st0.1 set security ipsec vpn IPSEC_VPN ike gateway IKE_GW set security ipsec vpn IPSEC_VPN ike ipsec-policy IPSEC_POL set security ipsec vpn IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set security ipsec vpn IPSEC_VPN establish-tunnels immediately
Apêndice 2: Mostrar saída de configuração no DUT
Mostre a saída de comando no DUT.
SRX1
user@srk1# show security pki
ca-profile ROOT_CA_CERT {
ca-identity RootCA;
}
user@srk1# show security key-manager
profiles {
km_profile_1 {
quantum-key-manager {
url https://www.kme_a-qkd-server.net;
local-sae-id SAE_A;
local-certificate-id SAE_A_CERT;
trusted-cas ROOT_CA_CERT;
}
}
}user@srk1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@srk1# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srk1# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srk1# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srk1# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$Nadwg4aUH.5Nds4aUiHuO1RhrvWxVs4"; ## SECRET-DATA
user@srk1# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.2; external-interface ge-0/0/0.0; local-address 172.18.10.1; version v2-only; ppk-profile km_profile_1;
user@srk1# show security ipsec proposal IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc; lifetime-seconds 2400;
user@srk1# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srk1# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 192.168.80.0/24;
}
establish-tunnels immediately;SRX 2
user@srx2# show security key-manager
profiles {
km_profile_1 {
quantum-key-manager {
url https://www.kme_a-qkd-server.net;
local-sae-id SAE_B;
local-certificate-id SAE_B_CERT;
trusted-cas ROOT_CA_CERT;
}
}
}user@srx2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
family mpls;
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
ge-1/0/0 {
unit 0 {
family mpls;
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}user@srx2# show security zones
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone vpn {
interfaces {
st0.1;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
}user@srx2# show security policies
from-zone trust to-zone vpn {
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}user@srx2# show security ike proposal IKE_PROP authentication-method pre-shared-keys; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@srx2# show security ike gateway IKE_GW ike-policy IKE_POL; address 172.18.10.1; external-interface ge-0/0/0.0; local-address 172.18.10.2; version v2-only; ppk-profile km_profile_1;
user@srx2# show security ike policy IKE_POL proposals IKE_PROP; pre-shared-key ascii-text "$9$P5z6/Cu1EyP5F/CuB1-VwYgJDi.TF/"; ## SECRET-DATA
user@srx2# show security ipsec policy IPSEC_POL proposals IPSEC_PROP;
user@srx2# show security ipsec vpn IPSEC_VPN
bind-interface st0.1;
ike {
gateway IKE_GW;
ipsec-policy IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}
establish-tunnels immediately;Exemplo: Configure a topologia IPsec AutoVPN com segurança quântica usando o perfil chave do gerente de chave quântica
Use este exemplo de configuração para proteger uma infraestrutura IPsec AutoVPN configurando o perfil chave do gerente de chave quântica.
O Hub, Spoke 1 e Spoke 2 usam perfis chave de gerenciamento de chave quântica para se comunicarem com KME Hub, KME Spoke 1 e KME Spoke 2 para buscar as chaves QKD e estabelecer túneis de VPN IPsec.
Tempo de leitura |
Menos de uma hora. |
Tempo de configuração |
Menos de uma hora. |
- Pré-requisitos de exemplo
- Antes de começar
- Visão geral funcional
- Visão geral da topologia
- Ilustração de topologia
- Configuração passo a passo no hub
- Configuração passo a passo em dispositivos spoke
- Verificação
- Apêndice 1: Definir comandos em todos os dispositivos
- Apêndice 2: Mostrar saída de configuração no DUT
Pré-requisitos de exemplo
Requisitos de hardware |
|
Requisitos de software |
Versão Junos OS 22.4R1 ou posterior. |
Antes de começar
Benefícios |
|
Recursos úteis |
|
Saiba mais |
|
Experiência prática |
|
Saiba mais |
Visão geral funcional
Tabela 20 fornece um resumo rápido dos componentes de configuração implantados neste exemplo.
| IPsec VPN | Implante uma topologia de VPN IPsec hub-and-spoke onde os spokes são conectados por túneis VPN que enviam tráfego pelo hub. Esses túneis VPN são configurados posteriormente para usar chaves quânticas, tornando-os túneis VPN com segurança quântica. |
| Gateway IKE | Estabeleça uma conexão segura, o gateway IKE usa a política de IKE para se limitar ao grupo configurado de CAs (ca-profiles) enquanto valida o certificado. |
| Propostas | |
| Proposta de IKE | Defina os algoritmos e as chaves usadas para estabelecer a conexão IKE segura com o gateway de segurança por pares. O IKE cria os SAs dinâmicos e os negocia para o IPsec. |
| Proposta de IPsec | Liste protocolos, algoritmos e serviços de segurança a serem negociados com o peer IPsec remoto. |
| Políticas | |
| Política de IKE | Definir uma combinação de parâmetros de segurança (propostas de IKE) a serem usados durante a negociação da IKE. |
| Política de IPsec | Contenha regras e políticas de segurança para permitir o tráfego de VPN em grupo entre as zonas especificadas. |
| Política de segurança | Permite que você selecione o tipo de tráfego de dados para proteger por meio dos SAs IPsec.
|
Perfis |
|
| Perfil chave | Definir como os dispositivos SRX se comunicam com os dispositivos KME para recuperar as chaves QKD do servidor KME externo. Os principais perfis estão configurados no hub (HUB_KM_PROFILE_1) e spokes (SPOKE_1_KM_PROFILE_1 e SPOKE_2_KM_PROFILE_1) separadamente. Configure SPOKE-1 e para aplicativos e SPOKE-2 serviços para recuperar chaves QKD do servidor externo.
|
| Perfil do PPK | Indique qual perfil chave usar para estabelecer SAs de IKE ou IPsec com segurança quântica fazendo referência ao perfil chave no gateway IKE. |
| Certificados | |
| Certificado de CA | Verifique a identidade dos dispositivos e autenticar o link de comunicação entre eles. |
| Certificado local | Gere o PKI e inscreva-o com o certificado ca para verificação. |
| Certificado KME | Certificado de terceiros gerado pelo fornecedor. |
| Zonas de segurança | |
| confiança | Segmento de rede na zona de host. |
| desconfiança | Segmento de rede na zona de servidor de destino. |
| VPN | Segmento de rede por meio do qual o hub e os spokes interagem. |
Tarefas primárias de verificação |
Verifique se os SAs IKE e IPsec estabelecidos são seguros em quantum. |
Visão geral da topologia
Neste exemplo, protegemos os túneis de VPN IPsec hub-and-spoke usando chaves quânticas geradas por dispositivos KME de terceiros. Os dispositivos KME (KME-Hub, KME-Spoke 1 e KME-Spoke 2) estão conectados entre si por meio de um canal quântico altamente seguro e capaz de identificar ameaças. Usando este canal, os dispositivos Hub e Spoke recuperam chaves quânticas de seu dispositivo KME correspondente e as fundem com as chaves existentes para tornar os túneis VPN quânticos seguros.
Componentes de topologia |
Função |
Função |
|---|---|---|
Hub |
Firewall da Série SRX capaz de estabelecer túneis IPsec | Responde à negociação de IKE ou IPsec SA e estabelece túneis de IPsec com segurança quântica usando a chave QKD do dispositivo SPOKE-1SPOKE-2QKD KME-HUB e . |
SPOKE-1 |
Firewall da Série SRX capaz de estabelecer túneis IPsec | Inicia a negociação de IKE ou IPsec SA e estabelece túneis de IPsec com segurança quântica com hub usando chave QKD do KME-SPOKE-1 dispositivo QKD. |
SPOKE-2 |
Firewall da Série SRX capaz de estabelecer túneis IPsec | Inicia a negociação de IKE ou IPsec SA e estabelece túneis de IPsec com segurança quântica com hub usando chave QKD do KME-SPOKE-2 dispositivo QKD. |
HOST-1 |
O host dentro da zona confiável ou do lado LAN é SPOKE 1Host 1 protegido por SPOKE 1. |
Inicia o tráfego do lado do cliente em direção HOST-3 |
HOST-2 |
O host dentro da zona confiável ou do lado LAN é SPOKE 2Host 2 protegido por SPOKE 2. |
Inicia o tráfego do lado do cliente em direção HOST-3 |
HOST- 3 |
Hospedar dentro da zona confiável ou do lado LAN do hub. Host 3 é protegido por Hub. |
Responde ao tráfego do lado do cliente de HOST-1 e HOST-2 |
KME-HUB |
Dispositivo QKD de terceiros | Fornece chaves QKD em resposta às principais solicitações da HUB |
KME-SPOKE-1 |
Dispositivo QKD de terceiros | Fornece chaves QKD em resposta às principais solicitações da SPOKE-1 |
KME-SPOKE-2 |
Dispositivo QKD de terceiros | Fornece chaves QKD em resposta às principais solicitações da SPOKE-2 |
Ilustração de topologia
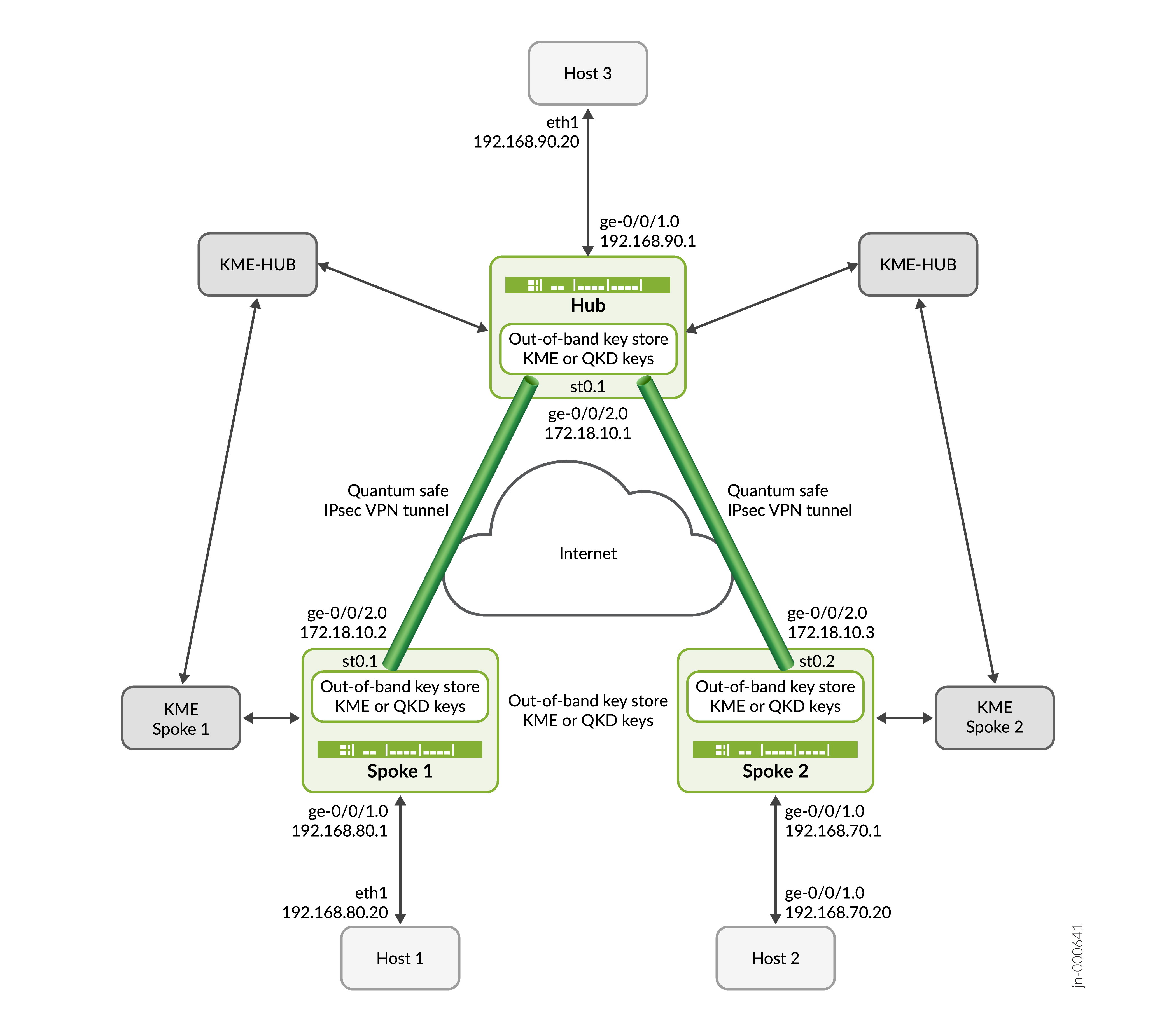
Configuração passo a passo no hub
Para obter configurações de amostra completas nos dispositivos hub e spoke, veja:
Configure as interfaces de hub.
[edit interfaces] user@hub# set ge-0/0/2 unit 0 family inet address 172.18.10.1/24 user@hub# set ge-0/0/1 unit 0 family inet address 192.168.90.1/24 user@hub# set st0 unit 1 family inet
Configure o hub-spoke da VPN IPsec. Isso inclui a configuração das zonas de segurança, políticas de segurança e certificados relevantes para autenticar identidades de dispositivos e seus links de comunicação.
Configure o hub para obter o certificado ca do servidor CA ou carregue um certificado de CA disponível localmente no dispositivo.
Nota:Os certificados KME precisam ser configurados conforme instruções de um fornecedor terceirizado.
Configure a proposta e a política de IPsec. Configure a política, a proposta e o gateway IKE para a VPN IPsec.
[edit security zones] user@hub# set security-zone untrust host-inbound-traffic system-services ike user@hub# set security-zone untrust interfaces ge-0/0/2.0 user@hub# set security-zone vpn interfaces st0.1 user@hub# set security-zone trust host-inbound-traffic system-services ping user@hub# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@hub# set from-zone trust to-zone vpn policy vpn_out match source-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@hub# set from-zone trust to-zone vpn policy vpn_out match application any user@hub# set from-zone trust to-zone vpn policy vpn_out then permit user@hub# set from-zone vpn to-zone trust policy vpn_in match source-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@hub# set from-zone vpn to-zone trust policy vpn_in match application any user@hub# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki] user@hub# set ca-profile Root-CA ca-identity Root-CA user@hub# set ca-profile Root-CA enrollment url url-to-CA-server user@hub# set ca-profile Root-CA revocation-check disable
user@hub> request security pki ca-certificate enroll ca-profile Root-CA
user@hub> request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa user@hub> request security pki local-certificate enroll certificate-id HUB_CRT challenge-password password domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA user@hub> request security pki local-certificate load certificate-id SAE_HUB filename SAE_HUB.cert key SAE_HUB.key
[edit security ike proposal] user@hub# set HUB_IKE_PROP authentication-method rsa-signatures user@hub# set HUB_IKE_PROP dh-group group14 user@hub# set HUB_IKE_PROP authentication-algorithm sha-256 user@hub# set HUB_IKE_PROP encryption-algorithm aes-256-cbc user@hub# set HUB_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@hub# set HUB_IKE_POL proposals HUB_IKE_PROP user@hub# set HUB_IKE_POL certificate local-certificate HUB_CRT
[edit security ike gateway] user@hub# set HUB_IKE_GW local-address 172.18.10.1 user@hub# set HUB_IKE_GW ike-policy HUB_IKE_POL user@hub# set HUB_IKE_GW external-interface ge-0/0/2.0 user@hub# set HUB_IKE_GW local-identity distinguished-name user@hub# set HUB_IKE_GW dynamic ike-user-type group-ike-id user@hub# set HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper user@hub# set HUB_IKE_GW version v2-only
[edit security ipsec proposal] user@hub# set HUB_IPSEC_PROP protocol esp user@hub# set HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@hub# set HUB_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec vpn] user@hub# set HUB_IPSEC_VPN bind-interface st0.1 user@hub# set HUB_IPSEC_VPN ike gateway HUB_IKE_GW user@hub# set HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL user@hub# set HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 user@hub# set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0
[edit security ipsec policy] user@hub# set HUB_IPSEC_POL proposals HUB_IPSEC_PROP
Configure o perfil chave do gerente de chave quântica para recuperar chaves quânticas do dispositivo KME-Hub correspondente.
[edit security key-manager profiles] user@hub# set HUB_KM_PROFILE_1 quantum-key-manager url kme-server-urlset security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_HUB user@hub# set HUB_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_HUB_CERT user@hub# set HUB_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
Vincule o perfil chave do gerente de chave quântica como o perfil ppk de gateway IKE para tornar os túneis vpn quânticos seguros.
[edit security ike gateway] user@hub# set HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Configuração passo a passo em dispositivos spoke
Para obter configurações de amostra completas nos dispositivos, veja:
Essa configuração é aplicável para dispositivos Spoke 1 e Spoke 2, você deve fazer as alterações de configuração específicas do dispositivo apropriadas.
Configure as interfaces de spoke.
[edit interfaces] user@spoke# set ge-0/0/2 unit 0 family inet address 172.18.10.2/24 user@spoke# set ge-0/0/1 unit 0 family inet address 192.168.80.1/24 user@spoke# set st0 unit 1 family inet
Configure o hub-spoke da VPN IPsec. Isso inclui a configuração das zonas de segurança, políticas de segurança e certificados relevantes para autenticar identidades de dispositivos e seus links de comunicação.
Configure o hub para obter o certificado ca do servidor CA ou carregue um certificado de CA disponível localmente no dispositivo.
Nota:Os certificados KME precisam ser configurados conforme instruções de um fornecedor terceirizado.
Configure a proposta e a política de IPsec. Configure a política, a proposta e o gateway IKE para a VPN IPsec.
[edit security zones] user@spoke# set security-zone untrust host-inbound-traffic system-services ike user@spoke# set security-zone untrust interfaces ge-0/0/2.0 user@spoke# set security-zone vpn interfaces st0.1 user@spoke# set security-zone trust host-inbound-traffic system-services ping user@spoke# set security-zone trust interfaces ge-0/0/1.0
[edit security policies] user@spoke# set from-zone trust to-zone vpn policy vpn_out match source-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match destination-address any user@spoke# set from-zone trust to-zone vpn policy vpn_out match application any user@spoke# set from-zone trust to-zone vpn policy vpn_out then permit user@spoke# set from-zone vpn to-zone trust policy vpn_in match source-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match destination-address any user@spoke# set from-zone vpn to-zone trust policy vpn_in match application any user@spoke# set from-zone vpn to-zone trust policy vpn_in then permit
[edit security pki] user@spoke# set ca-profile Root-CA ca-identity Root-CA user@spoke# set ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll user@spoke# set ca-profile Root-CA revocation-check disable
user@spoke> request security pki ca-certificate enroll ca-profile Root-CA
user@spoke> request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa user@spoke> request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <password> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA user@spoke> request security pki local-certificate load certificate-id SAE_SPOKE_1 filename SAE_SPOKE_1.cert key SAE_SPOKE_1.key
[edit security ike proposal] user@spoke# set SPOKE_1_IKE_PROP authentication-method rsa-signatures user@spoke# set SPOKE_1_IKE_PROP dh-group group14 user@spoke# set SPOKE_1_IKE_PROP authentication-algorithm sha-256 user@spoke# set SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc user@spoke# set SPOKE_1_IKE_PROP lifetime-seconds 3600
[edit security ike policy] user@spoke# set SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP user@spoke# set SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW address 172.18.10.1 user@spoke# set SPOKE_1_IKE_GW local-address 172.18.10.2 user@spoke# set SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL user@spoke# set SPOKE_1_IKE_GW external-interface ge-0/0/2.0 user@spoke# set SPOKE_1_IKE_GW local-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW remote-identity distinguished-name user@spoke# set SPOKE_1_IKE_GW version v2-only
[edit security ipsec proposal] user@spoke# set SPOKE_1_IPSEC_PROP protocol esp user@spoke# set SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 user@spoke# set SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc
[edit security ipsec vpn] user@spoke# set SPOKE_1_IPSEC_VPN bind-interface st0.1 user@spoke# set SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW user@spoke# set SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 user@spoke# set SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24
[edit security ipsec policy] user@spoke# set SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP
Configure o perfil chave do gerenciador de chaves quânticas para recuperar chaves quânticas do dispositivo spoke correspondente.
[edit security key-manager profiles] user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_1-qkd-server.net user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_1 user@spoke# set SPOKE_1_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_1_CERT user@spoke# set profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA
Vincule o perfil chave do gerente de chave quântica como o perfil ppk de gateway IKE para tornar os túneis vpn quânticos seguros.
[edit security ike gateway] user@spoke# set SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1
Se você terminar de configurar o dispositivo, entre no commit modo de configuração.
Verificação
Esta seção fornece uma lista de comandos de exibição que você pode usar para verificar o recurso neste exemplo.
| Comando | Tarefa de verificação |
|---|---|
|
mostrar segurança ike detalhes de associações de segurança |
Verifique os SAs de IKE. |
|
mostrar detalhes das associações de segurança ipsec de segurança |
Verifique os SAs IPsec. |
|
mostrar estatísticas de segurança ipsec |
Verifique as estatísticas de criptografia e descriptografia do IPsec. |
|
mostrar detalhes dos perfis dos principais gerentes de segurança |
Verifique as principais estatísticas de perfil. |
|
ping 192.168.90.20 fonte 192.168.80.20 contagem 4 |
Ping do Host 1 para Host 3. |
|
ping 192.168.90.20 fonte 192.168.70.20 contagem 4 |
Ping do Host 2 para Host 3. |
- Verifique os SAs de IKE
- Verifique os SAs IPsec
- Verifique as estatísticas do IPsec
- Verificar o perfil do gerente-chave
- Ping do Host 1 para Host 3
- Ping do Host 2 para Host 3
Verifique os SAs de IKE
Propósito
Verifique os SAs de IKE.
Ação
Desde o modo operacional, entre no show security ike security-associations detail comando para ver os SAs IKE.
user@hub> show security ike security-associations detail
IKE peer 172.18.10.3, Index 2161, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: bccc74c70f0b81b9, Responder cookie: 872d364f15b29c28
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Lifetime: Expires in 3464 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2661
Output bytes : 2586
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500446
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.3:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke_2.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0
IKE peer 172.18.10.2, Index 2162, Gateway Name: HUB_IKE_GW
Role: Responder, State: UP
Initiator cookie: 5e17d5924c619788, Responder cookie: 15f1e3c4252ba6f8
Exchange type: IKEv2, Authentication method: RSA-signatures
Local gateway interface: ge-0/0/2.0
Routing instance: default
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Lifetime: Expires in 3464 seconds
Reauth Lifetime: Disabled
IKE Fragmentation: Enabled, Size: 576
Remote Access Client Info: Unknown Client
Peer ike-id: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
AAA assigned IP: 0.0.0.0
PPK-profile: HUB_KM_PROFILE_1
Optional: No
State : Used
Algorithms:
Authentication : hmac-sha256-128
Encryption : aes256-cbc
Pseudo random function: hmac-sha256
Diffie-Hellman group : DH-group-14
Traffic statistics:
Input bytes : 2645
Output bytes : 2586
Input packets: 5
Output packets: 5
Input fragmented packets: 4
Output fragmented packets: 4
IPSec security associations: 2 created, 0 deleted
Phase 2 negotiations in progress: 1
IPSec Tunnel IDs: 500447
Negotiation type: Quick mode, Role: Responder, Message ID: 0
Local: 172.18.10.1:500, Remote: 172.18.10.2:500
Local identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=hub.juniper.net
Remote identity: C=us, DC=juniper, ST=california, L=sunnyvale, O=juniper, OU=security, CN=spoke.juniper.net
Flags: IKE SA is created
IPsec SA Rekey CREATE_CHILD_SA exchange stats:
Initiator stats: Responder stats:
Request Out : 0 Request In : 0
Response In : 0 Response Out : 0
No Proposal Chosen In : 0 No Proposal Chosen Out : 0
Invalid KE In : 0 Invalid KE Out : 0
TS Unacceptable In : 0 TS Unacceptable Out : 0
Res DH Compute Key Fail : 0 Res DH Compute Key Fail: 0
Res Verify SA Fail : 0
Res Verify DH Group Fail: 0
Res Verify TS Fail : 0 Significado
A saída de amostra confirma os SAs IKE.
Verifique os SAs IPsec
Propósito
Verifique os SAs IPsec.
Ação
Do modo operacional, entre no show security ipsec security-associations detail comando para ver os SAs IPsec.
user@hub> show security ipsec security-associations detail
ID: 500446 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.3
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.70.0-192.168.70.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Fri Jul 21 2023 00:31:08: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0xcf48c0c9, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2778 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2161
Direction: outbound, SPI: 0x86c9ba76, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2778 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2161
ID: 500447 Virtual-system: root, VPN Name: HUB_IPSEC_VPN
Local Gateway: 172.18.10.1, Remote Gateway: 172.18.10.2
Traffic Selector Name: ts1
Local Identity: ipv4(192.168.90.0-192.168.90.255)
Remote Identity: ipv4(192.168.80.0-192.168.80.255)
TS Type: traffic-selector
Version: IKEv2
Quantum Secured: Yes
PFS group: N/A
Passive mode tunneling: Disabled
DF-bit: clear, Copy-Outer-DSCP Disabled, Bind-interface: st0.1, Policy-name: HUB_IPSEC_POL
Port: 500, Nego#: 0, Fail#: 0, Def-Del#: 0 Flag: 0
Multi-sa, Configured SAs# 0, Negotiated SAs#: 0
Tunnel events:
Fri Jul 21 2023 00:31:08: IPsec SA negotiation succeeds (1 times)
Location: FPC 0, PIC 0
Anchorship: Thread 1
Distribution-Profile: default-profile
Direction: inbound, SPI: 0x4275d756, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2772 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2162
Direction: outbound, SPI: 0xe37b5568, AUX-SPI: 0
, VPN Monitoring: -
Hard lifetime: Expires in 3464 seconds
Lifesize Remaining: Unlimited
Soft lifetime: Expires in 2772 seconds
Mode: Tunnel(0 0), Type: dynamic, State: installed
Protocol: ESP, Authentication: hmac-sha256-128, Encryption: aes-cbc (256 bits)
Anti-replay service: counter-based enabled, Replay window size: 64
Extended-Sequence-Number: Disabled
tunnel-establishment: establish-tunnels-responder-only
IKE SA Index: 2162Significado
A saída de amostra confirma os SAs IPsec.
Verifique as estatísticas do IPsec
Propósito
Verifique as estatísticas do IPsec.
Ação
Do modo operacional, entre no show security ipsec statistics comando para ver as estatísticas do IPsec.
user@hub> show security ipsec statistics ESP Statistics: Encrypted bytes: 1560 Decrypted bytes: 1560 Encrypted packets: 10 Decrypted packets: 10 AH Statistics: Input bytes: 0 Output bytes: 0 Input packets: 0 Output packets: 0 Errors: AH authentication failures: 0, Replay errors: 0 ESP authentication failures: 0, ESP decryption failures: 0 Bad headers: 0, Bad trailers: 0 Invalid SPI: 0, TS check fail: 0 Exceeds tunnel MTU: 0 Discarded: 0
Significado
A saída de amostra confirma as estatísticas do IPsec.
Verificar o perfil do gerente-chave
Propósito
Verifique o perfil do gerente chave.
Ação
A partir do modo operacional, entre no show security key-manager profiles detail comando e verifique o Success campo na opção Request stats .
user@hub> show security key-manager profiles detail
Name: HUB_KM_PROFILE_1, Index: 6, Type: Quantum-key-manager
Configured-at: 21.07.23 (00:14:00)
Time-elapsed: 0 hrs 19 mins 24 secs
Url: https://kme.juniper.net:8080
Local-sae-id: SAE_HUB
Local-certificate-id: SAE_HUB_CERT
Trusted-cas: [ ROOT_CA_CERT ]
Peer-sae-ids: N/A
Default-key-size: N/A
Request stats:
Received: 2
In-progress: 0
Success: 2
Failed: 0
Significado
A saída de amostra confirma o perfil de gerente de chave quântica.
Ping do Host 1 para Host 3
Propósito
Verifique a conectividade do Host 1 ao Host 3.
Ação
Do modo operacional, entre no ping 192.168.90.20 source 192.168.80.20 count 5 comando para visualizar a conectividade do Host 1 ao Host 3.
user@host1# ping 192.168.90.20 source 192.168.80.20 count 5 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms 64 bytes from 192.168.90.20: icmp_seq=4 ttl=64 time=1.515 ms --- 192.168.90.20 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
A saída de amostra confirma a conectividade do Host 1 ao Host 3.
Ping do Host 2 para Host 3
Propósito
Verifique a conectividade do Host 2 ao Host 3.
Ação
Do modo operacional, entre no ping 192.168.90.20 source 192.168.80.20 count 5 comando para visualizar a conectividade do Host 2 ao Host 3.
user@host2# ping 192.168.90.20 source 192.168.70.20 count 5 PING 192.168.90.20 (192.168.90.20): 56 data bytes 64 bytes from 192.168.90.20: icmp_seq=0 ttl=64 time=2.151 ms 64 bytes from 192.168.90.20: icmp_seq=1 ttl=64 time=1.710 ms 64 bytes from 192.168.90.20: icmp_seq=2 ttl=64 time=1.349 ms 64 bytes from 192.168.90.20: icmp_seq=3 ttl=64 time=1.597 ms 64 bytes from 192.168.90.20: icmp_seq=4 ttl=64 time=1.759 ms --- 192.168.90.20 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/stddev = 1.349/1.702/2.151/0.290 ms Data traffic is successfully flowing between the HOSTs
Significado
A saída de amostra confirma a conectividade do Host 2 ao Host 3.
Apêndice 1: Definir comandos em todos os dispositivos
Definir saída de comando em todos os dispositivos.
Definir comandos no hub
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id HUB_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id HUB_CRT challenge-password <password> domain-name hub.juniper.net email hub@juniper.net subject DC=juniper,CN=hub.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_HUB filename SAE_HUB.cert key SAE_HUB.key set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager url https://www.kme_hub-qkd-server.net set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_HUB set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_HUB_CERT set security key-manager profiles HUB_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal HUB_IKE_PROP authentication-method rsa-signatures set security ike proposal HUB_IKE_PROP dh-group group14 set security ike proposal HUB_IKE_PROP authentication-algorithm sha-256 set security ike proposal HUB_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal HUB_IKE_PROP lifetime-seconds 3600 set security ike policy HUB_IKE_POL proposals HUB_IKE_PROP set security ike policy HUB_IKE_POL certificate local-certificate HUB_CRT set security ike gateway HUB_IKE_GW local-address 172.18.10.1 set security ike gateway HUB_IKE_GW ike-policy HUB_IKE_POL set security ike gateway HUB_IKE_GW external-interface ge-0/0/2.0 set security ike gateway HUB_IKE_GW local-identity distinguished-name set security ike gateway HUB_IKE_GW dynamic ike-user-type group-ike-id set security ike gateway HUB_IKE_GW dynamic distinguished-name wildcard C=us,DC=juniper set security ike gateway HUB_IKE_GW ppk-profile HUB_KM_PROFILE_1 set security ike gateway HUB_IKE_GW version v2-only set security ipsec proposal HUB_IPSEC_PROP protocol esp set security ipsec proposal HUB_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal HUB_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP set security ipsec vpn HUB_IPSEC_VPN bind-interface st0.1 set security ipsec vpn HUB_IPSEC_VPN ike gateway HUB_IKE_GW set security ipsec vpn HUB_IPSEC_VPN ike ipsec-policy HUB_IPSEC_POL set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 local-ip 192.168.90.0/24 set security ipsec vpn HUB_IPSEC_VPN traffic-selector ts1 remote-ip 0.0.0.0/0 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.1/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.90.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Definir comandos no Spoke 1
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_1_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_1_CRT challenge-password <password> domain-name spoke_1.juniper.net email spoke_1@juniper.net subject DC=juniper,CN=spoke_1.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_SPOKE_1 filename SAE_SPOKE_1.cert key SAE_SPOKE_1.key set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_1-qkd-server.net set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_1 set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_1_CERT set security key-manager profiles SPOKE_1_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_1_IKE_PROP dh-group group14 set security ike proposal SPOKE_1_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_1_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_1_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_1_IKE_POL proposals SPOKE_1_IKE_PROP set security ike policy SPOKE_1_IKE_POL certificate local-certificate SPOKE_1_CRT set security ike gateway SPOKE_1_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_1_IKE_GW local-address 172.18.10.2 set security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL set security ike gateway SPOKE_1_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_1_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_1_IKE_GW ppk-profile SPOKE_1_KM_PROFILE_1 set security ike gateway SPOKE_1_IKE_GW version v2-only set security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_1_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_1_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_1_IPSEC_POL proposals SPOKE_1_IPSEC_PROP set security ipsec vpn SPOKE_1_IPSEC_VPN bind-interface st0.1 set security ipsec vpn SPOKE_1_IPSEC_VPN ike gateway SPOKE_1_IKE_GW set security ipsec vpn SPOKE_1_IPSEC_VPN ike ipsec-policy SPOKE_1_IPSEC_POL set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 local-ip 192.168.80.0/24 set security ipsec vpn SPOKE_1_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.2/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.80.1/24 set interfaces st0 unit 1 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.1 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Definir comandos no Spoke 2
set security pki ca-profile Root-CA ca-identity Root-CA set security pki ca-profile Root-CA enrollment url https://ca-server.juniper.net/certsrv/mscep/mscep.dll set security pki ca-profile Root-CA revocation-check disable request security pki ca-certificate enroll ca-profile Root-CA request security pki generate-key-pair certificate-id SPOKE_2_CRT size 2048 type rsa request security pki local-certificate enroll certificate-id SPOKE_2_CRT challenge-password <password> domain-name spoke_2.juniper.net email spoke_2@juniper.net subject DC=juniper,CN=spoke_2.juniper.net,OU=security,O=juniper,L=sunnyvale,ST=california,C=us ca-profile Root-CA request security pki local-certificate load certificate-id SAE_SPOKE_2 filename SAE_SPOKE_2.cert key SAE_SPOKE_2.key set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager url https://www.kme_spoke_2-qkd-server.net set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager local-sae-id SAE_SPOKE_2 set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager local-certificate-id SAE_SPOKE_2_CERT set security key-manager profiles SPOKE_2_KM_PROFILE_1 quantum-key-manager trusted-cas Root-CA set security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures set security ike proposal SPOKE_2_IKE_PROP dh-group group14 set security ike proposal SPOKE_2_IKE_PROP authentication-algorithm sha-256 set security ike proposal SPOKE_2_IKE_PROP encryption-algorithm aes-256-cbc set security ike proposal SPOKE_2_IKE_PROP lifetime-seconds 3600 set security ike policy SPOKE_2_IKE_POL proposals SPOKE_IKE_PROP set security ike policy SPOKE_2_IKE_POL certificate local-certificate SPOKE_2_CRT set security ike gateway SPOKE_2_IKE_GW address 172.18.10.1 set security ike gateway SPOKE_2_IKE_GW local-address 172.18.10.3 set security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL set security ike gateway SPOKE_2_IKE_GW external-interface ge-0/0/2.0 set security ike gateway SPOKE_2_IKE_GW local-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW remote-identity distinguished-name set security ike gateway SPOKE_2_IKE_GW ppk-profile SPOKE_2_KM_PROFILE_1 set security ike gateway SPOKE_2_IKE_GW version v2-only set security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp set security ipsec proposal SPOKE_2_IPSEC_PROP authentication-algorithm hmac-sha-256-128 set security ipsec proposal SPOKE_2_IPSEC_PROP encryption-algorithm aes-256-cbc set security ipsec policy SPOKE_2_IPSEC_POL proposals SPOKE_2_IPSEC_PROP set security ipsec vpn SPOKE_2_IPSEC_VPN bind-interface st0.2 set security ipsec vpn SPOKE_2_IPSEC_VPN ike gateway SPOKE_2_IKE_GW set security ipsec vpn SPOKE_2_IPSEC_VPN ike ipsec-policy SPOKE_2_IPSEC_POL set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 local-ip 192.168.70.0/24 set security ipsec vpn SPOKE_2_IPSEC_VPN traffic-selector ts1 remote-ip 192.168.90.0/24 set interfaces ge-0/0/2 unit 0 family inet address 172.18.10.3/24 set interfaces ge-0/0/1 unit 0 family inet address 192.168.70.1/24 set interfaces st0 unit 2 family inet set security zones security-zone untrust host-inbound-traffic system-services ike set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone vpn interfaces st0.2 set security zones security-zone trust host-inbound-traffic system-services ping set security zones security-zone trust interfaces ge-0/0/1.0 set security policies from-zone trust to-zone vpn policy vpn_out match source-address any set security policies from-zone trust to-zone vpn policy vpn_out match destination-address any set security policies from-zone trust to-zone vpn policy vpn_out match application any set security policies from-zone trust to-zone vpn policy vpn_out then permit set security policies from-zone vpn to-zone trust policy vpn_in match source-address any set security policies from-zone vpn to-zone trust policy vpn_in match destination-address any set security policies from-zone vpn to-zone trust policy vpn_in match application any set security policies from-zone vpn to-zone trust policy vpn_in then permit
Apêndice 2: Mostrar saída de configuração no DUT
Mostre a saída de comando no DUT.
Hub
A partir do modo de configuração, confirme sua configuração entrando noshow security pki ca-profile Root-CA, , show security ike proposal HUB_IKE_PROPshow security key-manager, show security ike policy HUB_IKE_POL, show security ike gateway HUB_IKE_GW, show security ipsec proposal HUB_IPSEC_PROP, show security ipsec policy HUB_IPSEC_POL, show security ipsec vpn HUB_IPSEC_VPN, show security zones security-zone untrust, show security zones security-zone truste show security policies from-zone trust to-zone vpnshow security policies from-zone vpn to-zone trustshow interfaces comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@hub# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@hub# show security key-manager
profiles {
km_profile_1 {
static {
key-id ascii-text "$9$7VNs4UDkPT3Hq9A01yrWLxNYoPfTz3924"; ## SECRET-DATA
key ascii-text "$9$RraElM7NbwgJ-VkPTFAtxNdws4GUHqmTaZ36AtOBwY24UHfTz9A0JGu1IhrlGDjHmTFn/9p0fT39p0hc-VwgGiPfzn9pJGqfQnpurev8xds2aDjqX7"; ## SECRET-DATA
}
}
HUB_KM_PROFILE_1 {
quantum-key-manager {
url https://www.kme_hub-qkd-server.net;
local-sae-id SAE_HUB;
local-certificate-id SAE_HUB_CERT;
trusted-cas Root-CA;
}
}
}
user@hub# show security ike proposal HUB_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@hub# show security ike policy HUB_IKE_POL
proposals HUB_IKE_PROP;
certificate {
local-certificate HUB_CRT;
}user@hub# show security ike gateway HUB_IKE_GW
ike-policy HUB_IKE_POL;
dynamic {
distinguished-name {
wildcard C=us,DC=juniper;
}
ike-user-type group-ike-id;
}
local-identity distinguished-name;
external-interface ge-0/0/2.0;
local-address 172.18.10.1;
version v2-only;
ppk-profile HUB_KM_PROFILE_1;
user@hub# show security ipsec proposal HUB_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@hub# show security ipsec policy HUB_IPSEC_POL proposals HUB_IPSEC_PROP;
user@hub# show security ipsec vpn HUB_IPSEC_VPN
bind-interface st0.1;
ike {
gateway HUB_IKE_GW;
ipsec-policy HUB_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.90.0/24;
remote-ip 0.0.0.0/0;
}user@hub# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@hub# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@hub# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@hub# show security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@hub# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
st0 {
unit 1 {
family inet;
}
}Spoke 1
A partir do modo de configuração, confirme sua configuração entrando noshow security pki ca-profile Root-CA, , show security ike proposal SPOKE_1_IKE_PROPshow security key-manager profiles SPOKE_1_KM_PROFILE_1, show security ike policy SPOKE_1_IKE_POL, show security ike gateway SPOKE_1_IKE_GW, show security ipsec proposal SPOKE_1_IPSEC_PROP, show security ipsec policy SPOKE_1_IPSEC_POL, show security ipsec vpn SPOKE_1_IPSEC_VPN, show interfaces, show security zones security-zone untruste show security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security policies from-zone vpn to-zone trust comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@spoke1# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@spoke1# show security key-manager profiles SPOKE_1_KM_PROFILE_1
quantum-key-manager {
url https://www.kme_spoke_1-qkd-server.net;
local-sae-id SAE_SPOKE_1;
local-certificate-id SAE_SPOKE_1_CERT;
trusted-cas Root-CA;
}user@spoke1# show security ike proposal SPOKE_1_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke1# show security ike policy SPOKE_1_IKE_POL
proposals SPOKE_1_IKE_PROP;
certificate {
local-certificate SPOKE_1_CRT;
}user@spoke1# show security ike gateway SPOKE_1_IKE_GW ike-policy SPOKE_1_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.2; version v2-only; ppk-profile SPOKE_1_KM_PROFILE_1;
user@spoke1# show security ipsec proposal SPOKE_1_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke1# show security ipsec vpn SPOKE_1_IPSEC_VPN
bind-interface st0.1;
ike {
gateway SPOKE_1_IKE_GW;
ipsec-policy SPOKE_1_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.80.0/24;
remote-ip 192.168.90.0/24;
}user@spoke1# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
}
}
}
st0 {
unit 1 {
family inet;
}
} user@spoke1# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@spoke1# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@spoke1# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}user@spoke1# security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}Spoke 2
A partir do modo de configuração, confirme sua configuração entrando noshow security pki ca-profile Root-CA, , show security ike proposal SPOKE_1_IKE_PROPshow security key-manager profiles SPOKE_1_KM_PROFILE_1, show security ike policy SPOKE_1_IKE_POL, show security ike gateway SPOKE_1_IKE_GW, show security ipsec proposal SPOKE_1_IPSEC_PROP, show security ipsec policy SPOKE_1_IPSEC_POL, show security ipsec vpn SPOKE_1_IPSEC_VPN, show interfaces, show security zones security-zone untruste show security zones security-zone trustshow security policies from-zone trust to-zone vpnshow security policies from-zone vpn to-zone trust comandos. Se a saída não exibir a configuração pretendida, repita as instruções de configuração neste exemplo para corrigi-la.
user@spoke2# show security pki ca-profile Root-CA
ca-identity Root-CA;
enrollment {
url https://ca-server.juniper.net/certsrv/mscep/mscep.dll;
}
revocation-check {
disable;
}user@spoke2# show security key-manager profiles SPOKE_2_KM_PROFILE_1
quantum-key-manager {
url https://www.kme_spoke_2-qkd-server.net;
local-sae-id SAE_SPOKE_2;
local-certificate-id SAE_SPOKE_2_CERT;
trusted-cas Root-CA;
}user@spoke2# show security ike proposal SPOKE_2_IKE_PROP authentication-method rsa-signatures; dh-group group14; authentication-algorithm sha-256; encryption-algorithm aes-256-cbc; lifetime-seconds 3600;
user@spoke2# show security ike policy SPOKE_2_IKE_POL
##
## Warning: Referenced proposal is not defined
##
proposals SPOKE_IKE_PROP;
certificate {
local-certificate SPOKE_2_CRT;
}
user@spoke2# show security ike gateway SPOKE_2_IKE_GW ike-policy SPOKE_2_IKE_POL; address 172.18.10.1; local-identity distinguished-name; remote-identity distinguished-name; external-interface ge-0/0/2.0; local-address 172.18.10.3; version v2-only; ppk-profile SPOKE_2_KM_PROFILE_1;
user@spoke2# show security ipsec proposal SPOKE_2_IPSEC_PROP protocol esp; authentication-algorithm hmac-sha-256-128; encryption-algorithm aes-256-cbc;
user@spoke2# show security ipsec policy SPOKE_2_IPSEC_POL
proposals SPOKE_2_IPSEC_PROP;
[edit]
user@spoke2# show security ipsec vpn SPOKE_2_IPSEC_VPN
bind-interface st0.2;
ike {
gateway SPOKE_2_IKE_GW;
ipsec-policy SPOKE_2_IPSEC_POL;
}
traffic-selector ts1 {
local-ip 192.168.70.0/24;
remote-ip 192.168.90.0/24;
}user@spoke2# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 172.18.10.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 192.168.90.1/24;
address 192.168.80.1/24;
address 192.168.70.1/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 172.18.10.1/24;
address 172.18.10.2/24;
address 172.18.10.3/24;
}
}
}
st0 {
unit 1 {
family inet;
}
unit 2 {
family inet;
}
}
user@spoke2# show security zones security-zone untrust
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/0.0;
ge-0/0/2.0;
}user@spoke2# show security zones security-zone vpn
interfaces {
st0.1;
st0.2;
}
user@spoke2# show security zones security-zone trust
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
ge-0/0/1.0;
}
user@spoke2# show security policies from-zone trust to-zone vpn
policy vpn_out {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
user@spoke2# show security policies from-zone vpn to-zone trust
policy vpn_in {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}